中國「資訊作戰」的類型分析--呂爾浩、魏澤民Update:2018/05/02
全文
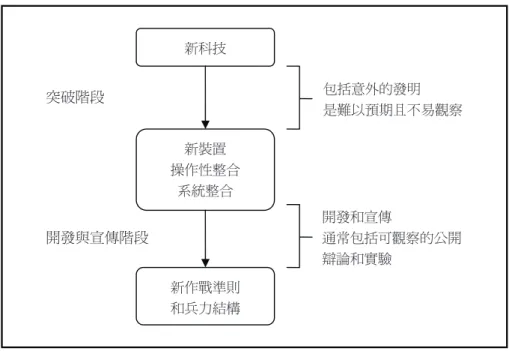
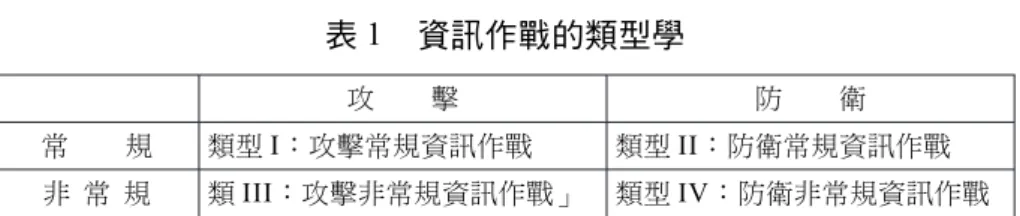
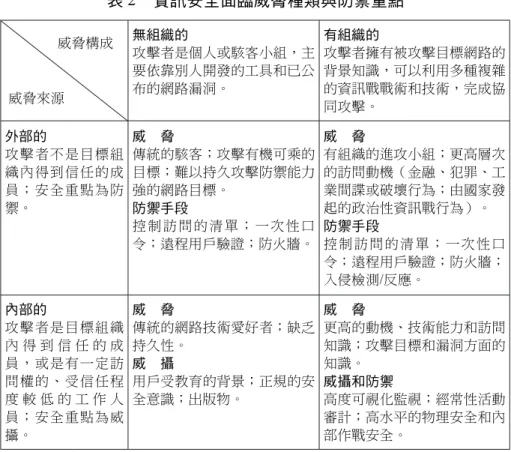
數據

相關文件
Menou, M.著(2002)。《在國家資訊通訊技術政策中的資訊素養:遺漏的層 面,資訊文化》 (Information Literacy in National Information and Communications Technology (ICT)
In digital systems, a register transfer operation is a basic operation that consists of a transfer of binary information from one set of registers into another set of
Teacher / HR Data Payroll School email system Exam papers Exam Grades /.
Classifying sensitive data (personal data, mailbox, exam papers etc.) Managing file storage, backup and cloud services, IT Assets (keys) Security in IT Procurement and
• The unauthorized disclosure of information could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or
• The unauthorized disclosure of information could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or
Service Level Agreement – ensure at least 99.7% availability of the WiFi service, support four-hour response time and four-hour service recovery with active monitoring,
Through the help of this study, the inconvenient of insufficient information of biological pilot plant can be improved, the manufacture security can be promoted, and the