Semantic Web
?Yuh-Jong Hu, Se-Ting, Chen, and Min-Huei, Yang
Emerging Network Technology (ENT) Lab. Dept. of Computer Science, National Chengchi University
Wen-Shan District, Taipei, Taiwan, 116
{hu, g9011, 9020}@cs.nccu.edu.tw
Abstract. The ultimate goal of semantic web is evolving the existing Web into a new frontier where agents could consume information directly without human intervention. In this paper, we show the issues and chal-lenges on agent trust verification and why they are closely related to the secure trust semantic web. Agent has semantic interactions with its peer agent using trust ontologies and trust policies so the realization of the trusted semantic web is feasible. A real system implementation frame-work will be addressed to demonstrate the feasibility of our proposal.
1
Introduction
Several emerging core technologies being developed that are related to the se-mantic web research. They are agent, peer-to-peer (p2p) or grid computing, ubiquitous computing, and web services. Among them, agent technology is one of the pivoting elements to drive the success of semantic web vision. Because the ultimate goal semantic web is evolving the existing Web into a new frontier where agents could collect and consume well-defined information and make a decision without human too much intervention.
Trust is an important aspect of decision making and particularly influences the specification and implementation of security policy for the WWW [5]. The semantic web is no exception which also needs security based trust policy to ensure the quality of service in its environment. In the semantic web, trust was declared as the top layer on the layer stack. Certainly, it will not be the last one for us to consider. Our focus on trust is in the context of resolving agent’s authentication, authorization, and delegation on the semantic web. This agent trust is as important as context and content provenance trust on the semantic web because information provenance trust always needs agent trust to endorse and verify its trustworthiness. At this moment works on the social trust of the semantic web, such as [4][6][16], are not our emphasis.
It has been an important technique to use digital certificates (or creden-tials) to enforce services access control and identity verification on the WWW. ?This research was supported by Taiwan National Science Council (NSC) under grants
Digital certificates are usually classified as: identity certificate, attribute certifi-cate, and authorization certificate [11]. Using these certificates, we have shown that agent’s authentication, authorization, and delegation problem can be solved on the agent-mediated e-commerce (AMEC) [12]. In this paper, we propose a similar concept to verify agent’s certificates for solving agent authentication, authorization, and delegation on the semantic web.
Several studies have been making some progress on the secure-based semantic web using ontology-based policy language [13][18]. However, the logic founda-tions for ontology and rule are quite different so the expressive power and re-strictions will not be the same. Ontologies are useful for representing taxonomy of shared terms in a concept, whereas rules are useful for representing contin-gent features, such as business or security policies, or the relationship between preconditions, postconditions, and effects [7].
The specific speech-acts and trust criteria for agent’s communication and trust verification are defined as terms in the ontologies. These terms will be en-coded in the rulesets for policy representation and execution via the inference engine. This approach enables one to “build rules on top of ontologies” so that rules can access to ontological definitions for vocabulary primitives to have se-mantic interactions between agents. Of course, agents are allowed to use these terms in the policies to access or to update their knowledge base.
2
Related Study
2.1 Secure Trust Network Approach
In a generic trust management system, the PolicyMaker uses compliance check-ing algorithm to decide whether the certificates constitute a proof that the re-quest complies with the policy [1]. Another trust management language D1LP was proposed to provide a concept of proof-of-compliance for the open large-scale distributed systems [14]. Policies are very important for autonomous sys-tem protection and management. Therefore, a semantic-rich policy language and framework is required to represent and execute these polices. The language for policy representation and reasoning were usually based on ontology language only for security control [13][18].
2.2 Social Trust Network Approach
The social network for web of trust is usually based on recommendation or grad-ing systems [4][6][8]. In particular, technologies like FOAF (Friend Of A Friend) were extensively used as the analysis of trust relationship among peer agents. Since FOAF is used to make assertions about people (agents) and the relation-ships between them, it requires a mechanism to identity the individuals that assertions concern. The mechanism for FOAF can import authorship assurance from other trust networks, such as PGP to achieve this objective. The Inference Web (IW) supports for explaining information provenance. The explanations in-clude information concerning where answers came from, how they were derived,
and how reliable the source was [15]. Even the secure trust network and the social trust network are based on different technologies to derive their respec-tive trust objecrespec-tives, eventually they may still complement to each other for the reinforcement of the complete trust justification.
3
Some Issues and Challenges
Some issues and challenges need to be identified and resolved for the complete-ness of the trust policy expression and inference on the semantic web:
1. Trust criteria specifications: We have to decide what are the trust criteria that can be specified by the ontology languages, e.g., RDF(S) or OWL (see Sect. 4).
2. Policy language design and enforcement: We have to design a semantic rich policy language that has enough expressive power to represent both trust criteria and trust policies. Furthermore, a policy inference engine is required to verify trust criteria and enforce the associated trust policies (see Sect. 5) .
3. Agent communication protocols design and implementation: Agents semantically communicate with each other using agent communication pro-tocols to ensure the trust criteria and policies satisfaction (see Sect. 6). 4. Trust verification system construction: The web of trust is based on
the proofs on the Web. The proof will be a chain of assertions and reasoning rules (or policies) inference in the policy engine. So we have to construct the trust verification system to enable the policy management operations (see Sect. 7).
4
Trust Criteria Specifications
The conceptualization we refer to trust is an abstract model that specifies the cri-teria to achieve agent’s authentication, authorization, and delegation. However, we do not exclude using other trust criteria in this model. The trust concepts use and the constraints on their use will be explicitly defined as trust ontology and encoded as OWL ontology language. In addition, the satisfaction of trust criteria will be defined as trust policies and encoded as RuleML logic language [2]. Furthermore, the trust ontology and the trust rules will be fused together to construct a knowledge base to enforce agent’s trust verification.
4.1 Trust Ontology
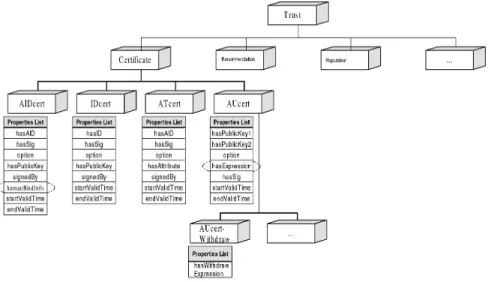
The satisfaction of the certificate theory is a necessary but not a sufficient con-dition for the trust verification. Because we might include other trust aspects of context and content provenance which can not be shown as certification theory. The trust identification endorsement from human h to its agent a can be shown as: h said a speaks for h on identity impersonation. This statement is
encoded as signing operation from human h indicated in agent identity certifi-cate (AIDcert) as humanBindInfo = Sig(P ua)h to ensure nonrepudiation and
liability of agent’s owner (see Fig. 1). The AUcert will be used in the agent’s authority verification, where hasExpression in the AUcert is the authority con-nection to services ontologies or knowledge provenance of specific context and content ontologies.
Fig. 1. The trust ontology defines the terms as a taxonomy of digital certificates for agent and human’s authentication, authorization, and delegation.
4.2 Message Ontology
The message ontology describes the concepts of domain independent outer lan-guage in the agent communication protocols to classify the speech-act performa-tives. The agent communication message consists of outer performative and inner content that are specified by agent communication language (ACL). The outer speech-act performatives shown in the message ontology is domain independent and the inner content might be domain independent, e.g., trust ontologies, or it might be domain dependent, such as services and context ontologies. The sepa-ration of outer performative and inner content allows us to reuse the speech-act performatives and simplify the agent communication protocols design and im-plementation.
5
Policy Language Design
Ontology-based policy language is very restricted to enforce the procedure at-tachment and event-driven operations. Therefore we apply the RuleML rule
language to address the trust policy language design and implementation. On-tology language provides the specifications of trust concepts and criteria while rule language provides the description of agent communication protocols and trust polices enforcement that can not be easily expressed by the ontology lan-guage alone.
The semantic web’s context and content provenance can be represented as named RDF graphs and shown as triples or RDF/XML expressions [3]. The named graph are signed and published on the semantic web for information con-sumers to evaluate specific graphs trustworthy based on associated trust policies. Even there is TRIPLE for RDF-based rule language representation [17] but these RDF-based policies are not easily defined and declared compared with RuleML logic rule language.
OWL is a description logic (DL) ontology language that creates the equation for ontology = taxonomy + axioms [2]. However, the axioms in the ontology equation primarily provides ontology integrity and subsumption verification of class and property. OWL rules language (ORL) provides the Horn logic program for the possible establishment of an unifying policy language including both description logic and Horn logic programs as the knowledge representation [10]. 5.1 Trust Policy and RuleSet
The generic rulesets can be shown as reaction rule and derivation rule. Fur-thermore, the derivation rule can be subclassified as fact and query (including integrity rule). RuleML is a well-known rule markup language that provides explicitly indicates reaction rule to trigger action or derivation rule to derive implicit information from the inference engine [2].
Our policy is a high level abstraction of strategy that can be defined as a combination of rulesets, which directly used by agent to activate possible ac-tions, such as inference, verification. We proposed three policies for agent’s trust verification: authentication, authorization, and delegation. Obviously, each trust policy can be directly executed in the rule-based inference engine. The selection criteria to decide which ruleset for which trust policy is based on the require-ments of service provider or service requester on the trust verification process shown as follows:
– Authentication Policy: The authentication policy was proposed to verify the integrity of identity certificate and the trustworthiness of the certification authority. The objectives of this policy are to enforce the cryptographic operations and furthermore to understand the syntactics and semantics of the digital certificates.
– Authorization Policy: The authorization policy was designed for the access control of services and resources.
– Delegation Policy: The purpose of delegation policy is to ensure that the delegation requester, i.e., delegatee, is under appropriate control on using his authorization certificate.
5.2 Combining Trust Policies with Trust Ontologies
The combining logic rules with ontologies is one of the most well-known unsettled problems in the semantic web research. Based on the preliminary results in [7], we choose knowledge fusion mechanism to build trust policies on top of trust ontologies. This approach enables the agents using trust policies to have access the primitives and variables defined in the OWL’s trust and related ontologies so that agents might have coherent knowledge representations.
The reason for us to express these trust policies as RuleML instead of OWL or ORL is the restriction of ontology language to describe classes with their properties relationships [9] [10]. Another reason is the restriction of ontology language for the procedure attachment to activate trust policy or to invoke cryptographic operations in the agent communication protocols.
6
Agent Communication Protocols
The philosophy of our agent communication language (ACL) design is different from other existing studies, such as FIPA. In FIPA’s ACL, the separation of outer speech-act performative from its inner content makes the agent to have an integral part of semantic communication message impossible. Furthermore, it is not easy for agent to verify whether the message semantic was really captured by another agent using the Believe Desire Intention (BDI) model [19].
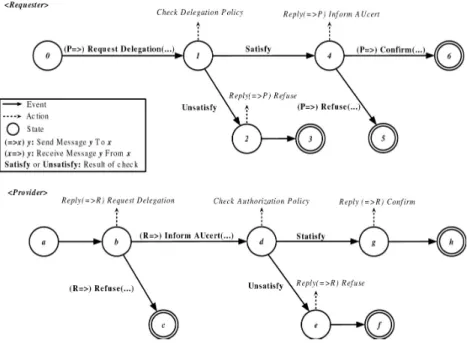
Our ACL is defined as combination of ontology language and rule language, where ontology language defines the trust and service concepts in terms of classes hierarchy with associated properties while rule language defines the policies for trust control. In addition, the agent communication protocols are defined as reaction rules implemented as finite state machines (FSMs) (see Fig. 2) based on the ACL. The trust verification processes depend on three agent communication protocols selection, i.e., authentication, authorization, and delegation. Each of these agent communication protocols uses the ontologies and policies we have defined before to indicate the exact message passing semantics (see Sect. 4 and Sect. 5.1).
7
Trust Verification Systems
The trust verification system (TVS) is the kernel for agent to enable the au-thentication, authorization, and delegation processes. This TVS is very similar to the generic expert system (ES). However, the ES is a closed system so it is impossible to exchange, relocate, and interoperate the facts or rules with an-other one. We also do not expect the ES(s) to interoperate with each an-other and still preserve the consistency and integrity features of the terms and variables specified in its knowledge base.
Fig. 2. The FSM for service provider agent and service requester agent on executing the request delegation protocols. Some of arc labels, such as (un)satisfy, are for agent’s internal status control so they are not speech-acts.
7.1 The SMAS
In our TVS, agent uses the Semantic Multi-Agent System (SMAS) to decode and encode each agent communication message exchanging in the agent com-munication protocols (see Fig 3). The message’s semantics are processed in two steps. In the first step, each incoming message is parsed to verify whether it is satisfied the ontology schema’s integrity and consistency. In the second step, the message’s internal information semantics is further examined by the decision-making agent, e.g., SIPF (see Sec. 7.2) to decide whether the message is satisfied the requirements of each activated trust policy. Then, the response message will be generated by the message creator agent and the message compressor agent according to the existing ontology schema.
7.2 The SIPF
We have built the internal semantic information processing framework (SIPF) to realize what will be the possible functional module on agent’s trust verification system (see Fig. 4). This SIPF is an event driven operation framework for a decision-making agent to further discover the semantic information that can not be extracted by the message processor in the SMAS. The SIPF is also responsible for the creation of each message’s inner content with deep semantics that will be embedded in each outgoing message generated by the message creator agent.
Fig. 3. Each incoming or outgoing agent communication message is decoded or en-coded, then verified by the SMAS to ensure its satisfaction of the ontology schema’s integrity and consistency.
Fig. 4. The decision-making agent carries out the major function of the internal se-mantic information processing framework (SIPF).
There are two major modules in the SIPF, i.e., the communication mod-ule (CM) and the decision and inference modmod-ule (DIM). The CM consists of the message processor and the action controller. The message processor is in charge of two things: the low level message passing and the composition of agent communication message; the action controller’s kernel is the Jess forward infer-ence engine which executes the reaction rules w.r.t. each FSM, then invoke the associated trust policy for verification.
The DIM is responsible for each message’s semantic information extraction, derivation, and inference. The DIM includes the policy loader, the policy pro-cessor, the constraint checker, the crypto propro-cessor, and the data transformer. The policy loader downloads each policy with associated rulesets indicated by the action controller, then sends to the policy processor for further classification and processing. So main function of the policy processor is to analyze the rule-sets embedded in each trust policy and send to the respective inference engine. Once the rulesets and facts are all set, then one of the inference engines, i.e., FaCT, Jess, or Mandarax, will be invoked.
Rules and Facts Collection There are three generic rule categories for each trust policy, i.e., derivation rule, integrity rule, and reaction rule. The derivation rule and integrity rule will be sent to the constraint checker using the Man-darax backward inference engine to derive an answer or to check the constraint integrity. As the reaction rule, it will be sent to the Jess inference engine for fur-ther processing. The facts are collected from three sources: agent communication message, reputation data, and cryptographic data.
8
Conclusion
This paper is on the agent’s trust verification on the semantic web. We ex-amine the issues and challenges on agent’s trust verification when we enable agent semantically communicate with each other to achieve this objective via agent communication protocols. For agent trust verification, the focus is on the context of resolving agent’s authentication, authorization, and delegation using certificate theory. The trust criteria and verification constraints (or policies) are specified respectively by OWL ontology language and RuleML rule language. We pointed out the differences on the expressive power of these two languages for trust criteria and trust policies. We expect to have a unifying semantic web language similar to ORL (OWL rule language) which can combine the expressive power of description logic and Horn logic to mitigate this problem in the near future.
The complete framework for agent’s trust verification were proposed and implemented to demonstrate the feasibility of our proposal. In this framework, agents semantically communicate with each other using agent communication protocols to exchange facts and rules to achieve the trust verification objective.
References
1. Blaze, M., J. Feigenbaum, and M. Strauss, Compliance Checking in the PolicMaker Trust Management System, Proc. of the Financial Cryptography’98, LNCS 1465, 1998, 254-274.
2. Boley, H., S. Tabet, and G. Wagner., Design Rationale of RuleML: A Markup Language for Semantic Web Rules, Proceedings of the First Semantic Web Working
Symposium, SWWS’01, Stanford, CA., 2001, 381-402.
3. Carroll, J. J., et al., Named Graphs, Provenance and Trust, HP Laboratories
Bris-tol, HPL-2004-57, 2004.
4. Golbeck, J., J. Hendler, and B. Parsia, Trust Networks on the Semantic Web,
WWW 2003, Budapest, Hungary, May 20-26, 2003.
5. Grandison, T. and M. Solman, A Survey of Trust in Internet Applications, IEEE
Communications Survey, Fourth Quarter 2000, 2-16.
6. Grant, Jan, Recommendation systems as a basis for trust on the Semantic Web,
W3C Semantic Web Advanced Development for Europe (SWAD-Curope) Report 11.1, http://www.w3.org/2001/sw/Europe/reports/trust/issues.html.
7. Grosof, N. B., et al., Description Logic Programs: Combining Logic Programs with Description Logic, WWW2003, Budapest, Hungary, May 20-26, 2003, 48-57. 8. Guha, R., Open Rating Systems, http://tap.stanford.edu/tap/papers.html. 9. Horrocks, I., et al., SWRL: A Semantic Web Rule Language Combining OWL and
RuleML, http://www.daml.org/2003/11/swrl/rules-all.html
10. Horrocks, I. and P. F. Patel-Schneider, A Proposal for an OWL Rules Language,
WWW2004, May 17-22, 2004, New York, NY USA.
11. Hu, Y.-J., Some Thoughts on Agent Trust and Delegation, The Fifth International
Conference on Autonomous Agents, Montreal, Canada, May 28 - June 1, 2001,
489-496.
12. Hu, Y.-J., Trusted Agent-Mediated E-Commerce Transaction Services via Digital Certificate Management, Electronic Commerce Research Journal, 3(3-4), July-Oct., 2003.
13. Kagal, L., T. Finin, and A. Joshi, A Policy Based Approach to Security for the Semantic Web, ISWC 2003, LNCS 2870, 2003, 402-418.
14. Li, N., B. Grosof, and J. Feigenbaum, Delegation Logic: A Logic-based Approach to Distributed Authorization, ACM Transactions on Information and System
Se-curity, 6, 2003, 128-171.
15. McGuinness, L. D. and P. P. da Silva, Trusting Answers on the Web, Mark T. Maybury editor, New Directions in Question Answering, AAAI/MIT Press, 2004. 16. Richardson, M., R. Agrawal, and P. Domingos, Trust Management for the Semantic
Web, ISWC 2003, LNCS 2870, 2003, 351-368.
17. Sintek, M. and S. Decker, TRIPLE - A Query, Inference, and Transformation Language for the Semantic Web, ISWC 2002, Sardinia, June 2002.
18. Tonti, G., et. al., Semantic Web Languages for Policy Representation and Rea-soning: A Comparison of KAoS, Rei, and Ponder, ISWC 2003, LNCS 2870, 2003, 419-437.
19. Wooldridge, M., Semantic Issues in the Verification of Agent Communication Lan-guages, Autonomous Agents and Multi-Agent Systems, 3, 9-31, 2000, 9-31.