A study on information security management system evaluation - assets, threat and vulnerability
全文
數據
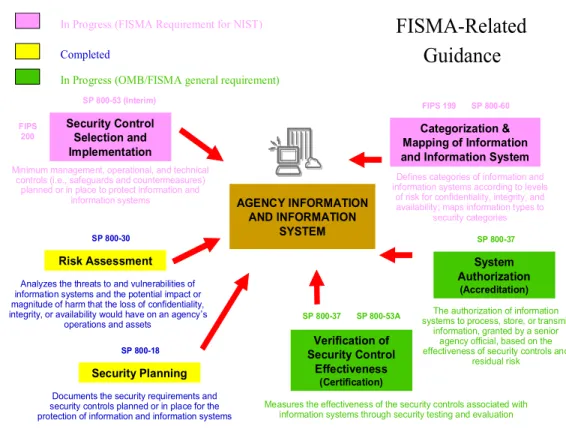
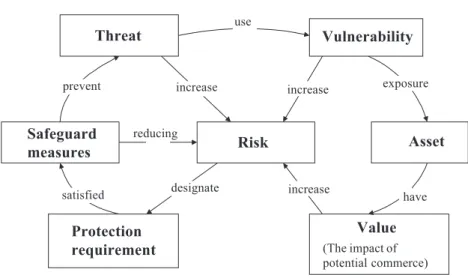
相關文件
Management Committees/ School Management Committees of their sponsored schools (hereafter collectively referred to as “school governance authority”) in formulating specific
The MNE subject, characterised by its (i) curriculum structure; (ii) curriculum aims; (iii) learning and teaching strategies; and (iv) curriculum contents, can enhance the
Apart from spelling out clearly the curriculum objectives, content and learning strategies of moral and national education, related curriculum resources and
Teacher / HR Data Payroll School email system Exam papers Exam Grades /.
Classifying sensitive data (personal data, mailbox, exam papers etc.) Managing file storage, backup and cloud services, IT Assets (keys) Security in IT Procurement and
The roles of school management and technical support staff on implementing information and network security measures... Security
Service Level Agreement – ensure at least 99.7% availability of the WiFi service, support four-hour response time and four-hour service recovery with active monitoring,
Skype provide better security than most VoIP system and PSTN. – Just because most VoIP system and PSTN do not provide any
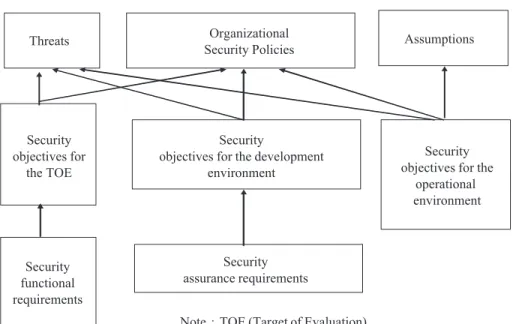
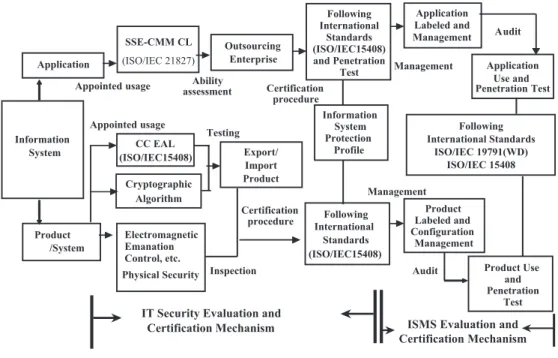
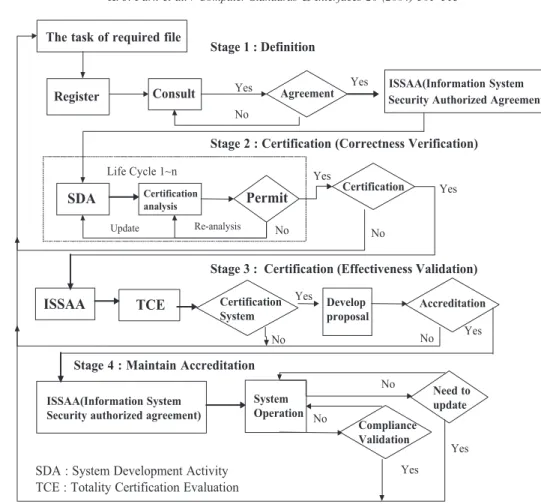
![Fig. 3.4 [25 – 27] . In this paper, we proposed the information system security certification mechanism as indicated in Fig](https://thumb-ap.123doks.com/thumbv2/9libinfo/7925570.156960/11.816.419.747.643.992/fig-paper-proposed-information-security-certification-mechanism-indicated.webp)