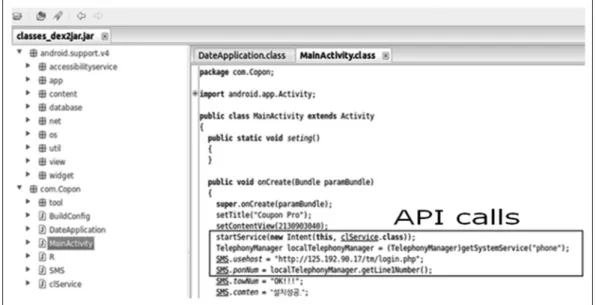
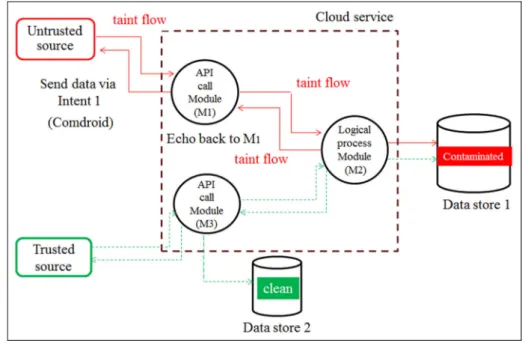
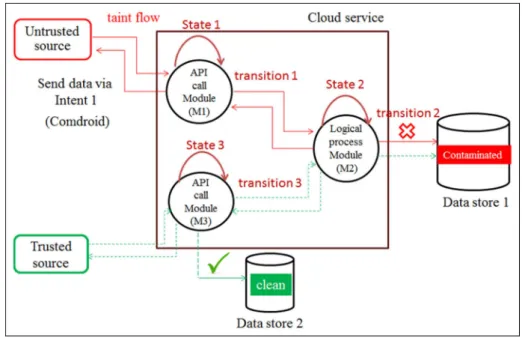
Using malware for software-defined networking-based smart home security management through a taint checking approach
全文
數據


相關文件
It is concluded that the proposed computer aided text mining method for patent function model analysis is able improve the efficiency and consistency of the result with
Besides, we also classify the existing RFID protection mechanisms to solve the different personal privacy threats in our security threat model.. The flowchart of security threat
Through the enforcement of information security management, policies, and regulations, this study uses RBAC (Role-Based Access Control) as the model to focus on different
“ Customer” ,employs the fuzzy analytic hierarchy process (FAHP) to develop a systematic model for the evaluations of knowledge management effectiveness , to reach the goal
Moreover, through the scholar of management, Michael Porter's Five Forces Analysis Model and Diamond Model make the analysis of transport industry at port, and make the
The study was based on the ECSI model by Martensen et al., (2000), combined with customer inertia as a mediator in the hope of establishing a customer satisfaction model so as
To enhance the generalization of neural network model, we proposed a novel neural network, Minimum Risk Neural Networks (MRNN), whose principle is the combination of minimizing
Based on the Technology Acceptance Model (TAM), the study was undertaken to understand whether the characteristics of social networking, which are defined as external variables