Received May 13, 1997; accepted March 10, 1998. Communicated by Jean-Lien C. Wu.
*This work was supported in part by the National Science Council, Taiwan, R.O.C., under contract NSC-87-2213-E-324-003.
Constructing Perfect Secret Sharing Schemes for General
And Uniform Access Structures
HUNG-MIN SUNAND SHIUH-PYNG SHIEH+
Department of Computer Science and Information Engineering National Cheng Kung University
Tainan, Taiwan 701, R.O.C. E-mail: hmsun@mail.ncku.edu.tw
+Department of Computer Science and Information Engineering
National Chiao Tung University Hsinchu, Taiwan 300, R.O.C. E-mail: ssp@csie.nctu.edu.tw
A perfect secret sharing scheme allows a secret K to be shared among a set of partici-pants in such a way that only qualified subsets of participartici-pants can recover the secret, and unqualified subsets of participants obtain no information regarding the secret. In this paper, we propose a construction of perfect secret sharing schemes with uniform, generalized ac-cess structures of rank 3. Compared with other constructions, our construction has some improved lower bounds on the information rate. In addition, we also generalize the con-struction to perfect secret sharing schemes with uniform, generalized access structures of constant rank.
Keywords: cryptography, information security, secret sharing schemes, threshold schemes, information theory, access structures
1. INTRODUCTION
In a secret sharing scheme, a secret is broken into pieces, called shares, where each participant keeps a share. A secret sharing scheme allows the secret K to be shared among a set of participants P in such a way that only qualified subsets of participants can collabo-rate with their secret shares to recover the secret [1-4]. A special case of secret sharing schemes is the threshold scheme [5, 6], in which all groups of participants of at least some fixed size are qualified. Secret sharing schemes have many applications in different areas, such as access control, launching a missile, and opening a bank vault or a deposit box. For a more detailed description of secret sharing schemes and a wide discussion of their applications, we refer the reader to the excellent survey papers [3, 7]. A current and com-plete bibliography can also be found online [4]. The secret K is chosen by a special participant, called the dealer, who is responsible for computing and distributing the shares. The collection of subsets of participants that can reconstruct the secret in this way is called access structure G. G is usually monotone, that is, if X Œ G and X Õ X¢ Õ P, then X¢ Œ G. A minimal qualified subset Y Œ G is a subset of participants such that Y¢ œ G for all Y¢ à Y,
Y¢ π Y. The basis of G, denoted by G0, is the family of all minimal qualified subsets. Let 2P denote the collection of all subsets of P. For any G0 Õ 2P, the closure of G0 is defined as cl (G0) = {X¢ : $ X Œ G0, X Õ X¢ Õ P}. Therefore, an access structure G is the same as the closure of its basis G0, cl(G0). A secret sharing scheme is perfect if unqualified subsets of participants obtain no information regarding the secret [8, 9]. This means that the prior probability p(K = K0) is equal to the conditional probability p(K = K0 | given any or fewer secret shares of an unqualified set). With the entropy function H [10], we can state the requirements of a secret sharing scheme as follows:
(1) any qualified subset can reconstruct the secret: "XŒG H(K | X ) = 0; and
(2) any unqualified subset has no information on the secret: "XœG H(K | X ) = H(K).
To efficiently implement a perfect secret sharing scheme, it is important to keep the length of the shares as small as possible. Let K be the secret space and S be the maximum share space. The information rate of a secret sharing scheme is defined as the ratio of the length of the secret to the maximum length of shares, that is, r = log2 |K| / log2 |S| [2]. There are other, different approaches to measuring the efficiency of a secret sharing scheme, such as the average information rate [11] and the dealers randomness approaches [12, 13]. The average information rate of a secret sharing scheme is the ratio between the length of the secret and the arithmetic mean of the length of all shares [11]. The dealers randomness is the number of random bits required by the dealer to set up a secret sharing scheme [12, 13]. In this paper, we will only focus on the information rates of perfect secret sharing schemes. Given any access structure G, Ito et al. [1, 14] showed that there exists a perfect secret sharing scheme to realize the structure. Benaloh and Leichter [15] proposed a different algorithm to realize secret sharing schemes for any given monotone access structure. In both constructions, the information rate decreases exponentially as a function of n, the number of participants. Since then, many researchers have studied the perfect secret shar-ing scheme for graph-based access structure G with basis G0, where G0 is the collection of pairs of participants corresponding to edges [8, 9, 16-18]. Stinson [18] proved that, for any graph G with n vertices having maximum degree d, there exists a perfect secret sharing scheme for the access structure based on G in which the information rate is at least 2 / (d + 1). Dijk [9] showed that Stinsons lower bound is tight because he proved that there exist graphs having maximum degree d such that the optimal information rate is at most 2 / (d + 1 - e) for all d ≥ 3 and e > 0.
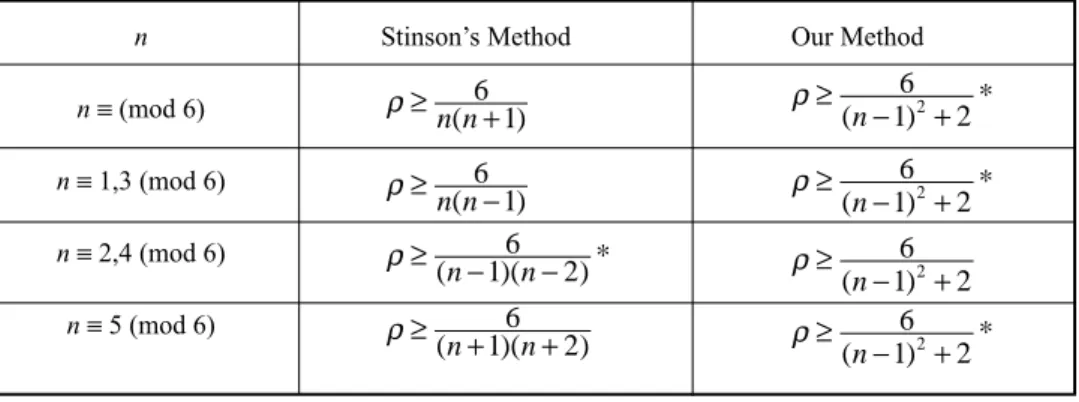
The rank of an access structure G is the maximum cardinality of a minimal qualified subset. An access structure is uniform if every minimal qualified subset has the same cardinality. Therefore, a graph-based access structure is a uniform access structure with rank 2. Perfect secret sharing schemes with access structures of rank three were studied by Stinson [17]. He applied Steiner systems to construct perfect secret sharing schemes with access structures of rank three. The constructed secret sharing scheme has the information rate ρ ≥(n−1)(6n−2) if G is uniform and n ∫ 2, 4 (mod 6), where n is the number of
participants. Note that if n doesnt satisfy the condition n ∫ 2, 4 (mod 6), it is necessary to find an n¢ > n such that n¢ ∫ 2, 4 (mod 6). In this paper, we propose a construction of perfect secret sharing schemes with uniform access structures of rank three. The lower bound of the information rate of the proposed scheme is 162 2
(n− ) + . Compared with Stinsons construction, our construction has some improved lower bounds on the informa-tion rate. In addiinforma-tion, we also extend our idea which constructs perfect secret sharing schemes with uniform access structures of rank three to construct perfect secret sharing schemes with access structures of constant rank m.
This paper is organized as follows. In section 2, we first introduce the construction of secret sharing schemes for graph-based access structures. Section 3 gives the construction of perfect secret sharing schemes with uniform access structures of rank 3 and evaluates the information rate of the constructed scheme. In section 4, we propose an efficient decompo-sition construction of secret sharing schemes with uniform access structures of rank m. Finally, we conclude this paper in section 5.
2. CONSTRUCTION FOR GRAPH-BASED ACCESS STRUCTURES
A uniform access structure of rank m is the access structure in which the size of each element in G0 is equal to m. Therefore, the graph-based access structure can be considered to be the case of rank 2. In this section, we first introduce the construction of secret sharing schemes for graph-based access structures [18]. An access structure based on a graph consists of the closure of a graph, where a vertex denotes a participant and an edge denotes a minimal qualified pair of participants. Suppose G is a graph with vertices V(G), edges E(G), and maximum degree d. Stinson [18] showed that there exists a perfect secret sharing scheme with information rate r = 2 / (d + 1). In the following, we will propose a construction for graph-based access structures.
We assume that P = {p1, p2, ..., pn} is the set of participants corresponding to the vertices of graph G, and that the secret K = (K1, K2) is taken randomly from GF(q2), where q is a prime and q ≥ n. Let f(x) = K2x + K1(mod q). yi is computed from f(x) as follows:
yi = f(i - 1)(mod q), for i = 1, ..., n.
It is clear that given yi and yj, for i π j, f(x) can be determined uniquely. Therefore, if one can get two or more yis, he can recover the secret K. However, if one has no knowl-edge of any yi, he can obtains no information about the secret. Note that if one can get one yi, he can obtain some information about the secret.
The dealer selects n random numbers, r1, ..., rn, over GF(q). The share of participant pi is given by
Si = <ai,1, ..., ai,t, ..., ai,n>, where 1 £ t £ n,
ai,t = ri (mod q) if t = i,
ai,t is empty if t π i and p pi tis not an edge of G.
Theorem 1: The constructed secret sharing scheme satisfies the dollowing conditions: (1) any qualified subset can reconstruct the secret:
"XŒG H(K | X ) = 0; and
(2) any unqualified subset has no information about the secret: "XœG H(K | X ) = H(K).
Proof:
(1) Let X be a subset of participants, and let X Œ G. Then, there exists pi, pj Œ X (i π j) such that p pi j is an edge of G. Therefore, participant pi owns ai,i = ri and ai,j = rj + yj, and
participant pj owns aj,j = rj and aj,i = ri + yi. Thus, participant pi and participant pj can recover yi and yj, and can then recover f(x) and secret K.
(2) Let X be a subset of participants, and let X œ G. Therefore, for any pair of participants pi, pj Œ X(i π j), p pi jis not an edge of G. We assume that X can recover yi. Therefore
there exists participant pi who owns ai,i = ri and participant pj who owns aj,i = ri + yi. Thus, p pi j is an edge of G. This is a contradiction of the condition that p pi jis not an
edge of G. Hence, X cannot recover any yi. That is, X obtains no information about
secret K. o
The share of participant pi is an n-dimensional vector. Except that ai,js (for all j,
p pi jœ E(G)) are empty, every ai,j is over GF(q). Therefore, the length of share Si is log(qdi+1), where di is the degree of vertex pi of G. The maximal length of the shares is log(qd+1), where d is the maximum degree of G. The length of the secret is log(q2). Thus, the information rate of the secret sharing scheme is r = ( 2+ ⋅⋅1log) logq = +21.
d q d
Time Complexity: Here, we evaluate the time complexity for constructing the secret shar-ing scheme based on a graph G. It is clear that the computation of yis, for i = 1, ..., n, can be achieved in O(n) time complexity. The dominant part is the assignment of the shares, Sis. For these shares, Sis, there are n2 entries in total. Therefore, the construction can be achieved in O(n2) time complexity.
3. CONSTRUCTION FOR UNIFORM ACCESS STRUCTURES OF RANK THREE
In the section, we will propose the construction of perfect secret sharing schemes with uniform access structures of rank 3 and evaluate the information rate of the constructed scheme. Assume that P = {p1, p2, ..., pn} is the set of participants, and that the secret K = (K1, K2, K3, K4, K5, K6) is taken randomly from GF(q6), where q is a prime and q ≥ 2n. Let f(x) = K6x5 + K5x4 + K4x3 + K3x2 + K2x + K1(mod q). yi be computed from f(x) as follows:
yi = f(i - 1) (mod q), for i = 1, ..., 2n.
Thus, if he can get six or more yis, he can recover f(x) and then secret K. However, if he has no knowledge of any yi, he can obtain no information about the secret.
We define Gi, for 1 £ i £ n, as the graph with vertices V(Gi) and edges E(Gi), where V(Gi) = {pj | for all pj, where {pi, pj, pk} Œ G0} and E(Gi) = {p pj k | for all p pj k, where
{pi, pj, pk} ΠG0}. The dealer selects 2n random numbers, r1, ..., r2n, over GF(q). As in the construction presented in section 2, there exists a secret sharing scheme realizing Gi in which the secret is (r1 + yi, rn+i + yn+i) and the share of participant pj is Sj(Gi) for pj ΠV(Gi).
The share of participant pi is given by Si = < ri, rn+i, ai,1, ..., ai,t, ..., ai,n >, where 1 £ t £ n,
ai,t = Si(Gt) if pi ΠV(Gt) and ai,t is empty otherwise.
Theorem 2: The constructed secret sharing scheme satisfies the following conditions: (1) any qualified subset can reconstruct the secret:
"XŒG H(K | X ) = 0; and
(2) any unqualified subset has no information about the secret: "XœG H(K | X ) = H(K).
Proof:
(1) Let X Œ G be a subset of participants. Then, there exists pi, pj, pk Œ X (i π j π k) such that {pi, pj, pk} Œ G0. Participant pi owns ri, rn+i, Si(Gj), and Si(Gk). Participant pj owns rj, rn+j, Sj(Gi), and Sj(Gk). Participant pk owns rk, rn+k, Sk(Gi), and Sk(Gj). From Sj(Gi) and Sk(Gi), they can recover ri + yi, rn+i + yn+i because p pj k is an edge of Gi. From Si(Gj) and
Sk(Gj), they can recover rj + yj, rn+j + yn+j because p pi kis an edge of Gj. From Si(Gk)
and Sj(Gk), they can recover rk + yk, rn+k + yn+k because p pi j is an edge of Gk. Thus,
participants pi, pj and pk can recover yi, yn+i, yj, yn+j, yk and yn+k, and can then recover f(x) and secret K.
(2) Let X œ G be a subset of participants. Therefore, there does not exist any three partici-pants pi, pj and pk in X such that {pi, pj, pk} Œ G0. We assume that X can recover yi. Hence, there exists participant pi who owns ri, and participants pj and pk who can re-cover ri + yi. Thus, p pj k is an edge of Gi and {pi, pj, pk} Œ G0. This is a contradiction of
the condition that {pi, pj, pk} œ G0. That is, X obtains no information about yi, for 1 £ i
The share of participant pi is Si = < ri, rn+i, ai,1, ..., ai,t, ..., ai,n >. Because ai,t = Si(Gt) for pi ΠV(Gt), the length of ai,t is equal to log(pdi(Gt)+1) if pi ΠV(Gt), where di (Gt) is the degree of vertex pi in Gt. Hence, the length of share Si is equal to log( ).
( ( ) ) : q d Gi t t pi Gt + + ∑ ∈ 1 2 Because the length of the secret is equal to log(q6), the information rate of the secret sharing scheme is
ρ = ∑ ⋅ + + ⋅ = ∑ + + ∈ ∈ 6 1 2 6 1 2 log { ( ( ) ) } log { ( ( ) )} . : : q Max d G q Max d G i t p G i t t t p G i t i t i t
In the worst case when pi Œ Gt (for 1 £ t £ n and t π i) and di(Gt) = n - 2, the information rate of the secret sharing scheme is ρ= −162+2
(n ) .
Compared with the lower bound studied by Stinson [17], our lower bound is better than Stinsons lower bound in some cases. The comparison can be seen in Table 1.
We demonstrate the use of our method in the following example.
Let P = {p1, p2, p3, p4, p5} and G0 ={ {p1, p2, p3}, {p1, p2, p5}, {p1, p3, p4}, {p2, p4, p5}, {p3, p4, p5} }. We construct
G1 with V(G1) = {p2, p3, p4, p5} and E(G1) = {p p2 3, , p p2 5 p p3 4}, G2 with V(G2) = {p1, p3, p4, p5} and E(G2) = {p p1 3, , p p1 5 p p4 5}, G3 with V(G3) = {p1, p2, p4, p5} and E(G3) = { p p p p p p1 2, , 1 4 4 5},
G4 with V(G4) = {p1, p2, p3, p5} and E(G4) = { p p p p p p1 3, , 2 5 3 5}, and
G5 with V(G5) = {p1, p2, p3, p4} and E(G5) = { p p p p p p1 2, , 2 4 3 4} as follows.
Table 1. Bounds on the information rate for uniform access structures of rank three on n participants for n ≥≥≥≥≥ 5, where * denotes the method which has the better bound.
n Stinsons Method Our Method
n ∫ (mod 6) n ∫ 1,3 (mod 6) n ∫ 2,4 (mod 6) n ∫ 5 (mod 6) ρ ≥ 6+ 1 n n( ) ρ ≥ 6− 1 n n( ) ρ ≥ − 6 − 1 2 (n )(n )* ρ ≥ + 6 + 1 2 (n )(n ) ρ ≥ −162+2 (n ) * ρ≥ −6 + 12 2 (n ) * ρ≥ −162+2 (n ) * ρ≥ −162+2 (n )
Graph G1-G5 p3 p2 p5 p4 p1 p3 p5 p4 Graph G1 Graph G2 p2 p1 p5 p4 p1 p3 p1 p2 p1 p5 Graph G3 Graph G4 p1 p3 p1 p2 p1 p4 Graph G5
Let the secret K = (K1, K2, K3, K4, K5, K6) be taken randomly from GF(q6), where q is a prime and q ≥ 10.
Let f(x) = K6x5 + K5x4 + K4x3 + K3x2 + K2x + K1 (mod q) and yi = f (i -1) (mod q), for i = 1, ..., 10. The dealer selects 10 random numbers ris (1 £ i £ 10) from GF(q). Each pair of (ri + yi, rn+i + yn+i) is shared by the secret sharing scheme with access structure Gi, and the share of participant pj is Sj(Gi) for pj Œ V(Gi).
The share of participant pi is given by
S1 = < r1, r6, -, S1(G2), S1(G3), S1(G4), S1(G5) >, S2 = < r2, r7, S2(G1), -, S2(G3), S2(G4), S2(G5) >, S3 = < r3, r8, S3(G1), S3(G2), -, S3(G4), S3(G5) >, S4 = < r4, r9, S4(G1), S4(G2), S4(G3), -, S4(G5) >, S5 = < r5, r10, S5(G1), S5(G2), S5(G3), S5(G4), - >.
Obviously, {p1, p2, p5} can recover y1, y2, y5, y6, y7, and y10, and can then recover K. The lengths of Si(Gj)s can be tabulated as follows.
Therefore, the length of each share Si is equal to log(q12), and the information rate of the secret sharing scheme is ρ= ⋅⋅126 loglogq =12.
q
Time Complexity: Here, we evaluate the time complexity for constructing a secret sharing scheme with a uniform access structure of rank three. First, it is clear that the computation of yis, for i = 1, ..., n, can be achieved in O(n) time complexity. On the other hand, to construct a secret sharing scheme with a uniform access structure of rank three on n
j=2 j=3 j=4 j=5
i=1 log(q3) log(q3) log(q2) log(q2)
i=2 log(q3) log(q2) log(q2) log(q3)
i=3 log(q3) log(q2) log(q3) log(q2)
i=4 log(q2) log(q2) log(q3) log(q3)
i=5 log(q2) log(q3) log(q2) log(q3)
participants, we need to construct n secret sharing schemes for n graphs (each n -1 vertices). From section 2, we know that the time complexity for constructing a secret sharing scheme for a graph with n -1 vertices is O((n -1)2). Because the complexity O(n(n -1)2) is equiva-lent to the complexity O(n3), the construction of a secret sharing scheme with a uniform access structure of rank three can be achieved in O(n3) time complexity.
4. CONSTRUCTION FOR UNIFORM ACCESS
STRUCTURES OF RANK
m
In this section, based on the same concept used in the construction of the secret shar-ing schemes with uniform access structures of rank 3, we propose an efficient decomposi-tion construcdecomposi-tion of secret sharing schemes with uniform access structures of rank m. Let G be a uniform access structure of rank m on n participants. Assume that P = {p1, p2, ..., pn} is the set of participants, and that the basis of G is G0. We can decompose G0 into the union
of Gis, for 1 £ i £ n, where Gi = {X : X Œ G0 and X contains participant pi}. Thus, G = cl(G0) = cl(G1) »...» cl(Gn). We define Gi* = {X : X » {pi} Œ Gi}. Therefore, each cl(Gi*) is a uniform access structure of rank m - 1. We assume that secret K = (K1, K2, ..., Km), where each Ki, for 1 £ i £ m, is taken randomly from GF(qh(m-1)), which is the secret space of the secret sharing schemes with uniform access structures of rank m - 1. Note that h(i) is a function which indicates that the secret space of the secret sharing schemes with uniform access structures of rank i is GF(qh(i)). The dealer selects a polynomial f(x) of degree m◊h(m - 1) -1 with coefficients K and computes yi as follows: yi = f(i - 1)(mod q), for i = 1, ..., n◊h (m - 1).
Thus, if one can get m◊h(m - 1) or more yis, he can recover f(x) and then secret K. However, if one has no knowledge of any yi, he can obtain no information about the secret. We use Y1, Y2, ..., Yn over GF(qh(m-1)) to denote these n◊h(m - 1) yis. The dealer selects n random numbers R1, R2, ..., Rn over GF(qh(m-1)). We assume that there exists a secret sharing scheme realizing cl(Gi*), in which the secret is Ri + Yi and the share of participant pj is Sj (Gi*).
The share of participant pi is given by
Si = < Ri, Si(G1*), ..., Si(Gi-1*), Si(Gi+1*), ..., Si(Gn*) >.
Thus, the constructed secret sharing scheme is a perfect secret sharing scheme with access structure G. Summarizing, we have the following theorem.
Theorem 3: The constructed secret sharing scheme satisfies the following conditions: (1) any qualified subset can reconstruct the secret:
"XŒG H(K | X ) = 0; and
(2) any unqualified subset has no information on the secret: "XœG H(K | X ) = H(K).
Time Complexity: Here, we will evaluate the time complexity for constructing a secret sharing scheme with a uniform access structure of rank m. First, it is clear that we can use a polynomial of degree m! - 1 to compute all yis, for i = 1, ..., n. Thus, the computation of yis can be achieved in O(n◊m!), which is smaller than the time complexity of the following part. On the other hand, to construct a secret sharing scheme with an access structure of rank m on n participants, we need to construct n secret sharing schemes with access struc-tures of rank m - 1 on n - 1 participants. Let O(T(m, n)) be the time complexity for constructing a secret sharing scheme with an access structure of rank m on n participants. Then, O(T(m, n)) = O(m◊T(m - 1, n - 1)). Thus, O(T(m, n)) = O(m◊◊◊3◊T(2, n - m + 2)). Because O(T(2, n - m + 2)) = O((n - m + 2)2), it is clear that O(T(m, n)) = O m( ! (n m ) ).
2 2
2
⋅ − +
5. CONCLUSIONS
Based on the secret sharing schemes with graph-based access structures, we have proposed an efficient construction to realize the perfect secret sharing schemes with uni-form access structures of rank 3. Given any uniuni-form access structure of rank 3, with basis
G0, the information rate of the constructed secret sharing scheme is equal to 6 1 2 Max d G i t p G i t i t { ( ( ) )} , : + + ∑ ∈ where G
i is the graph with vertices V(Gi) = {pj | for all pj, where{pi, pj, pk} ΠG0} and edges E(Gi) = { p pj k| for all p pj k, where {pi,pj, pk} ΠG0}. In the worst case, the lower bound 162 2
(n− ) + can be achieved, where n is the number of participants. Compared with Stinsons construction, our construction has some improved lower bounds on the information rate. In addition, we have also proposed a construction of perfect secret sharing schemes for uniform access structures of rank m.
REFERENCES
1. M. Ito, A. Saito and T. Nishizeki, Secret sharing scheme realizing general access structure, in Proceedings of IEEE Globecom87, Tokyo, 1987, pp. 99-102.
2. D. R. Stinson, An explication of secret sharing schemes, Designs, Codes and Cryp-tography Vol. 2, No. 4, 1992, pp. 357-390.
3. G. J. Simmons, ed., An introduction to shared secret and/or shared control schemes and their application, in Contemporary Cryptology, The Science of Information Integrity, IEEE Press, 1992, pp. 441-497.
4. D.R. Stinson, Bibliography on secret sharing schemes, Available online, http://bibd. unl.edu/~stinson/ssbib.html
5. A. Shamir, How to share a secret, Communications of the ACM, Vol. 22, No. 11, 1979, pp. 612-613.
6. G. R. Blakley, Safeguarding cryptographic keys, in Proceedings of American Fed-eration of Information Processing Societies 1979 National Computer Conference, Vol. 48, 1979, pp. 313-317.
7. G. J. Simmons, W. A. Jackson and K. M. Martin, The geometry of shared secret schemes, Bulletin of the Institute of Combinatorial Applications, Vol. 1, 1991, pp. 71-88. 8. E. F. Brickell and D. R. Stinson, Some improved bounds on the information rate of
perfect secret sharing schemes, Journal of Cryptology, Vol. 5, No. 3, 1992, pp. 153-166.
9. M. van Dijk, On the information rate of perfect secret sharing schemes, Designs, Codes and Cryptography, Vol. 6, No. 2, 1995, pp. 143-169.
10. R. W. Hamming, Coding and Information Theory, Englewood Cliffs, Reading, NJ: Prentice-Hall, 1986.
11. K. M. Martin, New secret sharing schemes from old, Journal of Combinational Math-ematics and Combinatorial Computing, Vol. 14, 1993, pp. 65-77.
12. C. Blundo, A. De Santis and U. Vaccaro, Randomness in distribution protocols, In-formation and Computation, Vol. 131, No. 2, 1996, pp. 111-139. [A preliminary version appeared in Automata, Languages and Programming, 21st International Colloquium, S. Abiteboul and E. Shamir, eds., Lecture Notes in Computer Science Vol. 820, 1994, pp. 568-579.]
13. C. Blundo, A. Giorgia Gaggia and D. R. Stinson, On the dealers randomness required in secret sharing schemes, Designs, Codes and Cryptography, Vol. 11, No. 2, 1997, pp. 107-122. [A preliminary version appeared in Advances in Cryptology - EUROCRYPT
94, A. De Santis, ed., Lecture Notes in Computer Science Vol. 950, 1995, pp. 35-46.] 14. M. Ito, A. Saito and T. Nishizeki, Multiple assignment scheme for sharing secret,
Journal of Cryptology, Vol. 6, No. 1, 1993, pp. 15-20.
15. J. Benaloh and J. Leichter, Generalized secret sharing and monotone functions, in Advances in Cryptology-Crypto88 Proceedings, Lecture Notes in Computer Science, Vol. 403, Springer-Verlag, Berlin, 1990, pp. 27-35.
16. C. Blundo, A. De Santis, D.R. Stinson and U. Vaccaro, Graph decompositions and secret sharing schemes, Journal of Cryptology, Vol. 8, 1995, pp. 39-63.
17. D. R. Stinson, New general lower bounds on the information rate of secret sharing schemes, in Advance in Cryptology-CRYPTO 92, Lecture Notes in Computer Science, Springer-Verlag, Vol. 740, 1993, pp. 168-182.
18. D. R. Stinson, Decomposition constructions for secret sharing schemes, IEEE Trans-actions Information Theory, Vol. IT-40, No. 1, 1994, pp. 118-125.
Hung-Min Sun ( ) received his B.S. degree in ap-plied mathematics from National Chung-Hsing University in 1988, his M.S. degree in applied mathematics from National Cheng Kung University in 1990, and his Ph.D. degree in computer science and information engineering from National Chiao Tung University in 1995, respectively. He was an associate professor with the Depart-ment of Information ManageDepart-ment, Chaoyang University of Tech-nology from 1995 to 1999. Currently he is teaching at the Depart-ment of Computer Science and Information Engineering, National Cheng Kung University. His research interests include reliability theory, computer security, cryptography, and information theory. Shiuh-Pyng Shieh ( ) received the M.S. and Ph.D. degrees in electrical engineering from the University of Maryland, College Park, in 1986 and 1991, respectively. He is currently a professor with the Department of Computer Science and Informa-tion Engineering, NaInforma-tional Chiao Tung University. From 1988 to 1991, he participated in the design and implementation of the B2 Secure XENIX for IBM, Federal Sector Division, Gaithersburg, Maryland, USA. He is also the designer of the SNP (Secure Net-work Protocols). Since 1994, he has been a consultant for the Com-puter and Communications Laboratory, Industrial Technology Re-search Institute, Taiwan, in the area of network security and dis-tributed operating systems. He is also a consultant for the National Security Bureau, Taiwan. Dr. Shieh has been on the organizing committees of a number of conferences, such as the International Computer Symposium, and the International Conference on Parallel and Dis-tributed Systems. Recently, he is the general chair of 1998 Network Security Technology Workshop, the program chair of 1999 Mobile Computing Conference and 1997 Informa-tion Security Conference (INFOSEC 97). His research interests include internetworking distributed operating systems, and network security.