Lossless Data Hiding of Color Images Using Pixel
Decomposition and Phase Difference
*CHANG-LUNG TSAI1, KUO-CHIN FAN2, THOMAS CHIANG CHUANG3
AND CHAR-DIR CHUNG4
1Department of Computer Science
Chinese Culture University Taipei, 111 Taiwan
2Department of Computer Science and Information Engineering
National Central University Chungli, 320 Taiwan
3President, Van Nung University
Chungli, 320 Taiwan
4Department of Electrical Engineering
National Taiwan University Taipei, 106 Taiwan
Recently, the use of data hiding in hiding annotations, confidential data, or side in-formation into multimedia attracts the attention of researchers in various fields, espe-cially in digital library. One of the essential tasks in digital library is the digitization of arts together with the corresponding textural descriptions. Although there are some stan-dard interleaving algorithms for hiding the relating textural description into an image or video, the textural information is still prone to be accessed and extracted by hackers. Most of the traditional data hiding schemes focus on the recovery of covert information. The common shortcoming is that the original image will be distorted due to the process-ing of bit-substitution, quantization and truncation. In this paper, three novel data hidprocess-ing methods are proposed. The first two methods are implemented based on pair-wise logical computation (PWLC) and pixel decomposition by treating R, G, B bands and the inten-sity component as spatial domains and the third method is implemented by considering and utilizing the phase difference information in the hue and saturation components in the HSI color system. All of the three methods can achieve the goals of complete recov-ering of covert information and lossless reconstruction of original image simultaneously. In addition, it also obtains high data hiding capacity and good visual quality. Experi-mental results demonstrate the feasibility and validity of our proposed method in the data hiding of color images.
Keywords: data hiding, digital library, pair-wise logical computation, phase difference, content authentication
1. INTRODUCTION
Content authentication, authorization and monitoring of data transmission become more and more important in networking society, especially for those unprotected infor-mation which can be downloaded from the public websites or digital library systems
Received July 14, 2005; revised September 19, 2005; accepted October 31, 2005. Communicated by Tzong-Chen Wu.
[1-5]. Most of the arts stored in a library are presented in the color form, such as ancient oil paintings, color paintings and portraits. The digitization of these precious arts is thus a must in a digital library. The digitization task is not only limited to the scanning and compressing of color images. Footnotes, annotations, or side information relating to the processed image have also to be digitized. Traditional methods resolve the digitization problem by treating the two sources (color image and relating textural description) sepa-rately. It will result in certain degree of problem in the file management of digital library because two separate files (one image file and one text file) have to be prepared to repre-sent the same source. The ultimate way to resolve this problem is to utilize data hiding techniques to hide the textural description into the corresponding image. Most of the tra-ditional data hiding schemes focus on the recovery of covert information. The common shortcoming is that the original image will be distorted due to the processing of bit-sub-stitution (such as LSB), quantization, and truncation (such as DCT). The hidden informa-tion can be completely recovered, but the original host image will be distorted. Therefore, the complete recovery of hidden data and lossless reconstruction of original host image have to be accomplished simultaneously to remedy the shortcoming, especially in the practical application of digital library.
As we know, the performance of data hiding techniques is evaluated mainly based on the criteria of the visual quality of stego-image and the data hiding capacity. Since little change of hue and saturation components will distort the image dramatically, most of existing color image data hiding techniques are manipulated solely on the intensity component. The disadvantage is lower data hiding capacity.
In [6], Wu and Tsai proposed a data hiding scheme which is implemented based on image differencing. The hidden information is embedded into LSBs of the cover image. The algorithm not only can hide large amount of data imperceptibly but also make lower noticeable changes in the stego-image. In addition, it offers a simple way to accomplish cryptography. However, the host image will be distorted and cannot be recovered com-pletely. In [7], Tzeng et al. proposed an adaptive data hiding scheme which is imple-mented based on color ordering and mapping in palette images. The hidden information is embedded by replacing it with its neighboring color. The performance of this algorithm is satisfactory which demonstrates the least distortion, good security protection and in-detectability of hidden information. However, the data hiding capacity is still not high enough. In [8], Lin et al. proposed a color image data hiding method which is imple-mented based on PSNR calculation and palette generation. It maintains the quality of the host image and accommodates for a large quantity of secret information. However, the best condition of their manipulated PSNR is only around 39 dB. Besides, the data hiding capacity is not satisfactory. In [9], Kassim et al. proposed a data hiding scheme which utilizes SPIHT with partially linked spatial oriented trees. Their performance is quite similar as described in [8].
In this paper, three novel data hiding methods are proposed to achieve the goals of complete recovering of covert information and lossless reconstruction of the original image. The first method is implemented by directly decomposing a color image into R, G, and B bands and then transforming each of the three bands into several binary bit planes. Previously proposed PWLC data hiding scheme [10] is lastly operated on each of the binary bit plane. As to the second method, it is very similar to the first method. The dif-ference is that only the intensity component of a color image in the HSI color system is
considered as the band to be transformed. The third method is implemented by consider-ing and utilizconsider-ing the phase difference of hue and saturation components in the HSI color system. Experimental results demonstrate the feasibility and validity of our proposed method in the data hiding of color images. All three methods can obtain high data hiding capacity and good visual quality.
The rest of the paper is organized as follows. In section 2, the three proposed color image data hiding methods are presented. The rationale behind each method, such as pair-wise logical computation, pixel decomposition and phase difference, are also ad-dressed in the section. Experimental results are illustrated in section 3 to demonstrate the feasibility and validity of our proposed data hiding mechanism. Finally, concluding re-marks are given in section 4.
2. THE PROPOSED METHODS
In our previous work, a lossless data hiding mechanism called PWLC [10] was pro-posed for the data hiding of binary images, which will be used as the basic data hiding mechanism in the first two methods. To extend the applicability of PWLC data hiding in secure transmission and digital library, the PWLC is incorporated with band and pixel decompositions respectively for solving the data hiding problem of color images on which the first two proposed methods are based. As to the third method, it is imple-mented by considering and utilizing the phase difference of hue and saturation compo-nents in the HSI color system.
Before stating the first two proposed methods, the rationale of PWLC has to be ad-dressed. The details of PWLC can be found in [12]. As we know, exclusive-or is a logical operation on which the two possible input combinations, for a given output result, cannot be uniquely determined without knowing one of the two input variables. In order to re-construct the unknown input variables from the output results, we have to assign a known input variable as the reference for deriving the other unknown input variable. Note that the bit value of the reference bit can be either “0” or “1”. The PWLC data hiding is de-signed by selecting the two adjacent pixels with the same value from the host image as the suitable bit pair for performing data hiding.
The execution of exclusive-or operation between the bit pair in the host image and the hidden bit pair of covert information can be summarized by the following equations:
Reference Bit ♁ 1st Host image bit = 1st Embedded bit (1)
Hidden Bit ♁ 2nd Host image bit = 2nd Embedded bit (2)
where the Hidden Bit is the data bit value of the covert information and 1st and 2nd Host
image bits is a bit pair generated fromthe host image with the same value.
The data hiding process is performed from left to right and then top to bottom in the host image, i.e., horizontally, with the covert information.
In order to ensure the information security and save the transmission space, blind detection is usually adopted in designing data hiding algorithms [11]. In our work, the stego-image is directly utilized to extract the covert information without the need of the estimated or predicted original host image. The covert information can be extracted by
performing the reverse operation as follows: Suppose the value of Reference Bit is “1” and 1st and 2nd Host image bits possess the same value, we can derive the values of the 1st
and 2nd Embedded bits from the following equations.
Reference Bit ♁ 1st Host image bit = 1st Embedded bit
B 1 ♁ 1st Host image bit = 1st Embedded bit (3)
If the value of Reference Bit is “0”, Eq. (1) must be derived as the following equation. 1st Host image bit = 1st Embedded bit (4)
From Eq. (3), we can infer that the 1st Host image bit and the 1st Embedded bit are
complement bit pair.
Hidden Bit ♁ 2nd Host image bit = 2nd Embedded bit
B Hidden Bit ♁ 1st Host image bit = 2nd Embedded bit (5)
From Eq. (5), we know that if the 1st Host image bit equals 0, then the Hidden Bit
will be equal to the 2nd Embedded bit. If the 1st Host image bit equals 1, then the Hidden
Bit will be the complement of the 2nd Embedded bit.
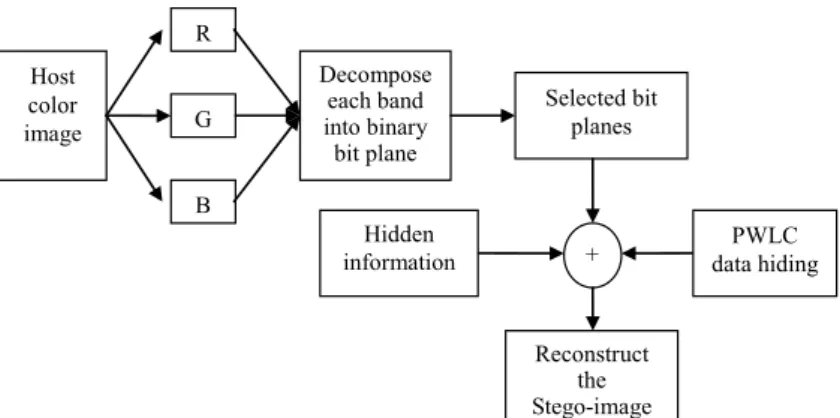
2.1 Method 1: PWLC Data Hiding Utilizing Pixel Decomposition in the RGB Color System
A color image is generally formed by three different bands, such as red, green, and blue, in a color coordinate system. The flowchart of the proposed PWLC based color image data hiding algorithm is shown in Fig. 1. In the proposed algorithm, the PWLC data hiding procedure is performed on R, G, and B bands, respectively. The step-by-step procedure is stated as follows.
Host color image R G B Decompose each band into binary bit plane Selected bit planes + data hidingPWLC Reconstruct the Stego-image Hidden information
Step 1: Determine the number of consecutive “00” or “11” bit pairs as the candidate for performing the data hiding. For instance, if the number of consecutive “00” or “11” bit pairs is “3”, it means that 3 consecutive “00” bit pairs, i.e. 000000, or 3 consecutive “11” bit pairs, i.e. 111111, are the candidate for data hiding. The determination of the number of consecutive “00” or “11” bit pairs for perform-ing data hidperform-ing will be analyzed in section 3.1.
Step 2: Decompose the color image into R, G, and B bands.
Step 3: Decompose each of the R, G, and B band data into binary bit planes. Step 4: Transfer the covert information into binary bit stream.
Step 5: Scan each binary bit plane and label those locations which will be ambiguous during the process of data extraction. The details of the labeling of ambiguous location will be discussed in section 3.1.
Step 6: Select the desired bands and the corresponding bit planes of the selected band for data hiding.
Step 7: Save those information generated in steps 1, 5 and 6 as the control key for per-forming data extraction.
Step 8: Hide the covert information sequentially into those selected bit planes by utiliz-ing the PWLC data hidutiliz-ing mechanism. The data hidutiliz-ing process is performed starting from the first pixel to the last pixel on each selected bit plane row by row and column by column except those labeled locations.
Step 9: Construct the stego-image from the bit planes.
The operation of PWLC in generating the stego-image plays a crucial role in the proposed approach.
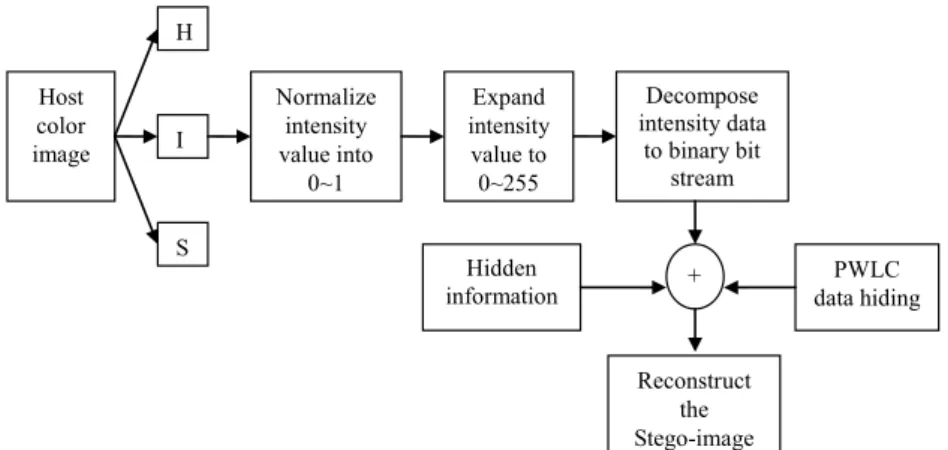
2.2 Method 2: PWLC Data Hiding by Considering Only the Intensity Component in the HSI Color System
A color image in the RGB color system can be transformed to the HSI color system through the following equation.
1 , 3 R G B I = + + 2 , 2 R G I = − 4 2 3 B R G I = − − (6) 1, I =I 2 2 2 3, S= I +I ⎟⎟ ⎠ ⎞ ⎜⎜ ⎝ ⎛ = − 2 3 1 tan I I H (7) Derived from Eq. (7), we can obtain the following result,
4 6 4 4 4 5 5R2 B2 G2 GR GB RB S = + + − − − , 2 2 cos 2 . 2 2 sin 2 R B G R B H R B G R B − ⎛ ⎞ ⎜ − − ⎟ ⎝ ⎠ = − ⎛ ⎞ ⎜ − − ⎟ ⎝ ⎠ (8)
There is an occurrence probability of 2G = R + B or R = B which will cause some manipulation problem like data overflow. The hue component ranges from 0° to 360°
(2π). For the ease of processing, all of the H, S, and I components will be normalized and ranged from 0 to 1.0 by applying the Matlab processing software. It means that once a color image has been depicted in the HSI color system, the three component values will range from 0 to 1 according to the transformation. As the hue varies from 0 to 1.0, the corresponding colors vary from red, through yellow, green, cyan, blue, magenta, and then back to red. Hence, the hue value of red color can be either 0 or 1.0. As saturation varies from 0 to 1.0, the corresponding colors (hues) will vary from unsaturated (shades of gray) to fully saturated (no white component). As the intensity value, or brightness, varies from 0 to 1.0, the corresponding colors become increasingly brighter.
In this subsection, a color image data hiding method is proposed by performing the PWLC data hiding on the intensity component of HSI color system only. The flowchart of the proposed data hiding method is shown in Fig. 2. To suit our need, the normalized intensity value (from 0 to 1.0) has to be expanded to the range of 0~255 first. Then, de-compose the expanded intensity component into 8 binary bit planes. Last, perform the PWLC data hiding on the desired binary bit plane.
Host color image H I S Normalize intensity value into 0~1 Decompose intensity data to binary bit stream Expand intensity value to 0~255 Hidden information + Reconstruct the Stego-image PWLC data hiding
Fig. 2. The flowchart of PWLC data hiding in the HSI color system. A step-by-step procedure of the proposed method 2 is stated as follows.
Step 1: Determine the number of consecutive “00” or “11” bit pairs for performing the data hiding.
Step 2: Represent a color image in theHSI color system.
Step 3: Expand the intensity value of each pixel in the color image from 0~1.0 to 0~255 such that intensity band can be represented by 8 binary bit planes.
Step 4: Transfer the covert information into binary bit stream.
Step 5: Scan each binary bit plane and label those locations which will be ambiguous during the process of data extraction.
Step 6: Select the desired bands and the corresponding bit planes of the selected band for data hiding.
Step 7: Save those information generated in steps 1, 5 and 6 as the control key for per-forming data extraction.
Step 8: Hide the covert information sequentially into those selected bit planes by using the PWLC data hiding mechanism. The data hiding process is performed start-ing from the first pixel to the last pixel on each selected bit plane row by row and column by column except those labeled locations.
Step 9: Construct the stego-image from the bit planes.
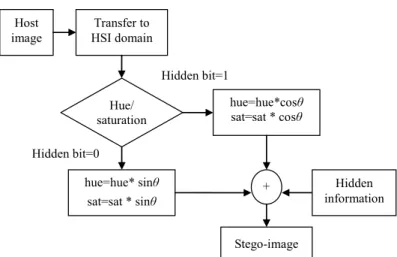
2.3 Method 3: Phase Difference Data Hiding in the HSI Color System
In this subsection, a novel data hiding method is proposed which is implemented based on phase difference between sine and cosine transformations in both of the hue and saturation components in theHSI color system. Even though the saturation component is independent of the degree of the hue component, it is still treated as the hue component. Since there is a π/2 phase difference between sine and cosine signals, the data hiding can be designed by utilizing the phase difference of sine and cosine signals as exploited in the following equation.
⎟ ⎠ ⎞ ⎜ ⎝ ⎛ − = 2 cos sinθ θ π (9) Suppose 0 ≤ θ ≤ 2π, the hue component can be denoted as 0 ≤ Hue(θ) ≤ 1. The saturation component can also be denoted as 0 ≤ Saturation(S) ≤ 1. The rationale of the proposed phase difference-based data hiding scheme is hidden behind the following cri-teria.
Criterion 1: Determine a fixed value “θ” for data hiding whose value should be small.
Although the value of “θ” dose not depend on the content of hidden bit, its value had better within the range of 0° < θ ≤ 15° in order not to make significant change of the hue and saturation components and achieve the goal of perception distortion after data hiding.
Criterion 2: If the hidden information bit is “1”, multiply cos(θ) by the hue or saturation
component. If the hidden information bit is “0”, multiply sin(θ) by the hue or saturation component.
Suppose “θ” equals π/36 (~5°), cos(θ) will be 0.9962 and sin(θ) is 0.0872. Thus, the value of hue*cos(θ) will range from 0 to 0.9962 and the value of hue*sin(θ) range from 0 to 0.0872. The original hue components with values below 0.0872 might be ambiguous and should be labeled before performing data hiding and data extraction. As to data ex-traction, if the value of the stego-hue component is larger than 0.0872, the hidden infor-mation bit can be identified as “1”. Otherwise, the hidden inforinfor-mation will be identified as “0” for those stego-hue components with value below 0.0872. It is a trade off between the value of “θ” and the performance of data hiding which means that if the value of “θ ” decreases, the performance of data hiding will be uplifted.
A flowchart of the proposed data hiding method is shown in Fig. 3. The step-by-step procedure of the proposed method is stated as follows.
Host image Transfer to HSI domain Hue/ saturation hue=hue*cosθ sat=sat * cosθ hue=hue* sinθ sat=sat * sinθ Hidden bit=1 Hidden bit=0 + Hidden information Stego-image
Fig. 3. The flowchart of phase difference data hiding on hue component in the HSI color system.
Step 1: Represent a color image in theHSI color system.
Step 2: Determine the value of “θ” for data hiding. The criterion for choosing the value of “θ” as described in criterion 1.
Step 3: Mark those possible ambiguous hue/saturation components.
Step 4: Save the information generated in steps 2 and 3 as the control key for perform-ing data extraction.
Step 5: Transfer the hidden information into a binary bit stream.
Step 6: Embed the hidden bit stream into the hue or saturation component according to the phase difference data hiding criteria as mentioned in the previous paragraph.
Step 7: Construct the stego-image from the bit planes.
2.4 Data Extraction
In this subsection, we will present the process of hidden data extraction on which the original host image can be reconstructed losslessly. The hidden data extraction proc-ess of the first two methods (method 1 and method 2) is performed mainly based on the PWLC hidden data extraction principle. The details of the PWLC hidden data extraction process can be found in [12]. However, method 1 is performed on the RGB color system, whereas method 2 is performed on the intensity component (I) of HSI color system. The step-by-step procedure of the hidden data extraction process of method 1 and method 2 can be stated as follows.
Step 1: Retrieve the information for data extraction from the control key. The retrieved information includes the selection of bit planes to be embedded, the number of consecutive “00” or “11” bit pairs selected for performing the data hiding, and the detection of labeled locations.
Step 3: Perform the PWLC data extraction process on the embedded bit planes to ex-tract the covert information.
Step 4: Reconstruct the host image and hidden information.
The original host image can be losslessly reconstructed in the data extraction proc-ess by performing the above steps.
As to the hidden data extraction process of method 3, it is performed mainly based on the characteristics of the π/2 phase difference between sine and cosine signals on the HSI color system. The step-by-step procedure can be stated as follows.
Step 1: Retrieve the information for data extraction from the control key. The retrieved information includes the value of “θ” and the detection of labeling locations.
Step 2: Perform the phase difference data extraction process on the stego-hue or stego- saturation component to extract the covert information.
Step 3: Reconstruct the host image and hidden information. 3. EXPERIMENTAL RESULTS
In this section, experimental results are illustrated to demonstrate the feasibility and validity of our proposed approach in data hiding. Various images, such as Cameraman, Lena, Airplane, Boat, Peppers, and Barbara, are chosen as the test images.
3.1 Preliminary Experimental Analysis
Prior to the application of the proposed method, the characteristics of the eight bi-nary bit planes decomposed from red, green, and blue bands of a color image are ana-lyzed. By performing the data hiding process on those less significant bit planes, the change in the visual quality of the embedded bit plane is almost unnoticeable. It is the reason why we choose those less significant bit planes (5th ~ 8th bits level) for performing
the data hiding.
Since there are only two pixel values “0” and “1” in each binary bit plane, the bit stream presented in the form of 000001 or 111110 (with the form of 3 consecutive “00” or “11” bit pairs being selected) might be ambiguous while performing the covert infor-mation extraction. For example, if we choose the last “00” bit pair in a 3 consecutive “00” bit pairs of the host image data for data hiding. The embedded result should be ei-ther 000010 or 000001. However, ei-there might be 000010 or 000001 existing in the origi-nal host image which is not the candidate for data hiding. Hence, we have to distinguish these two cases to avoid ambiguity by labeling the ambiguous locations. To completely recover the covert information, those ambiguous bit locations have to be labeled and be skipped in the processes of data hiding and data extraction. After that, the PWLC data hiding process is employed to those valid host image bit pairs that possess consecutive “00” or “11” bit pairs and the last bit pair is chosen for performing the PWLC data hiding process. Under normal distribution, the occurrence probability (OPSC) of S consecutive “00” or “11” bit pairs can be calculated as follows:
2 1 2S
OPSC= (10)
i.e., the occurrence probability of three consecutive “00” or “11” bit pairs is 1/26 (equals
to 0.015625). Thus, an image with size 512 * 512, the theoretical data hiding capacity in a normal-distributed bit plane is 512 * 512 * 0.015625 * 2 (“00” and “11” bit pairs) which equals 8192 bits. In fact, the occurrence of three consecutive “00” or “11” bit pairs of the 8th bit plane in the test images are a little higher than the theoretical value. The
occur-rence probability of the ambiguous locations with bit stream “000001” or “111110” is equal to 0.015625. Suppose the size of a color image is 512 * 512, there will be 6,291,456 bits (3 bands * 512 * 512 * 8 bits) in the image. If the bit planes of an image are normally distributed with the size of M by N, the data hiding capacity (DHC) of each bit plane by selecting S consecutive “00” or “11” bit pairs for data hiding is,
2 1 . 2S
M N
DHC= ∗− (11) Suppose the host image I(x, y) contains M rows and N columns. If we select R bit planes (can be the combinations of bit planes decomposed from red, green, or blue bands) and S consecutive “00” or “11” bit pairs for data hiding, the maximum data hiding capac-ity (DHC) of our proposed data hiding scheme can be calculated as
2 1 . 2S
R M N
DHC≤ ∗ −∗ (12) If the information of those labeling locations of ambiguity bits is saved as the header, the DHC is calculated as Eq. (12).
2 1 2 -1 ( 2 ) 2 S S R M N DHC − ∗ ∗ − ≤ (13) If we denote the DHC by utilizing the concept of entropy, Eqs. (12) and (13) can be transformed as shown in the following equations.
, 2 1 2 1 1, 1 2 log 2 m n DHC i j S S R i j R i j H ≤ − = = ∗ ∗− ∗ ⎛⎜ ∗ ∗− ⎞⎟ ⎝ ⎠
∑
(14) 2 1 2 1 , 2 1 2 1 1, 1 ( 2 ) log ( 2 ) 2 2 S S m n DHC i j S S R i j R i j H ≤ − = = ∗ ∗ −− − ∗ ⎛⎜ ∗ ∗ −− − ⎞⎟ ⎝ ⎠∑
(15) 3.2 Experimental ResultsShown in Fig. 4 are the original color image and the corresponding red, green, blue, hue, intensity, and saturation data of the test image Lena.
Method 1:
The stego-images generated by PWLC data hiding on different combinations of bit planes in the red, green, or blue band of Lena test image is shown in Fig. 5.
(a) (b) (c) (d) (e) (f) (g) Fig. 4. Test image of Lena, (a) original image; (b) red band; (c) green band; (d) blue band; (e)
in-tensity component image; (f) hue component image; (g) saturation component image.
(a) (b) (c) (d) (e) (f) Fig. 5. Different stego-Lena-test images with data being embedded in different combination of bit
planes decomposed from red, green, and blue bands, (a) embed 24740 bits in all of the 8th
bit plane of red, green and blue bands, (b) embed 24538 bits in all of the 7th bit plane of red,
green and blue bands, (c) embed 49278 bits in the both of the 7th and 8th bit planes of red,
green and blue bands, (d) embed 41206 bits in the 7th and 8th bit planes of red and blue
bands and 8th bit plane of green band, (e) embed 58038 bits in the 6th, 7th and 8th bit planes
of red and blue bands and 8th bit plane of green band, (f) embed 49271 bits in the 7th and 8th
bit planes of red band, 8th bit plane of green band and 6th, 7th and 8th bit planes of blue band.
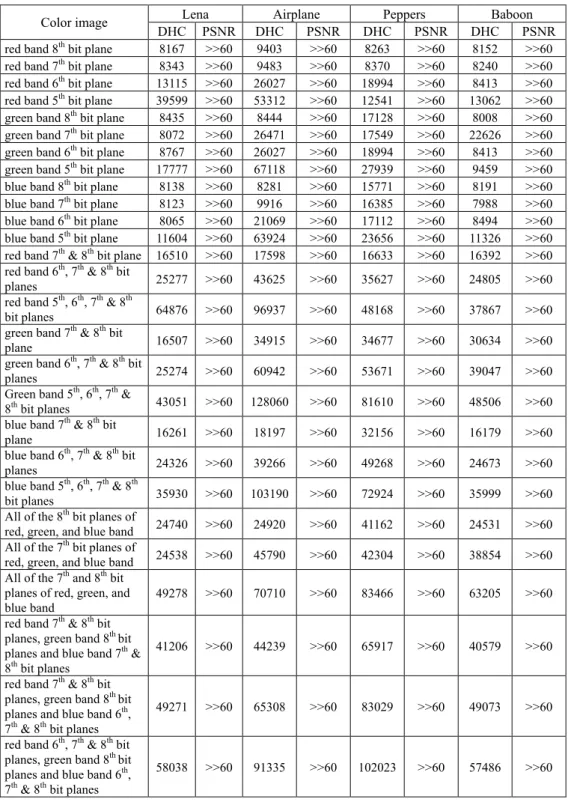
The statistical data hiding capacity of Lena, Airplane, Baboon, and Peppers test im-ages are summarized and tabulated in Table 1 where the PSNR of all stego-imim-ages are much larger than 60 dB.
The reason why almost all PSNR values are much larger than 60 dB is due to the fact that the hidden information are embedded in the less significant bits in which the obtained mean square error is relatively small comparing with the size (M * N) of the test image. Therefore, the PSNR value will be very large. Another reason that results in the large PSNR value is the low ratio of data hiding rate and all of them are merely about 0.129%-2.035% per bit. Experimental results demonstrate that our proposed PWLC data hiding utilizing pixel decomposition in the RGB color system and in intensity component of the HSI color system can obtain very good performance in visual quality. However, the highest data hiding capacity is obtained by performing the PWLC data hiding utiliz-ing the hue and saturation components in the HSI color system. As the hidden informa-tion is embedded in the intensity component of the HSI color system, the data hiding capacity is close to the data hiding capacity of hiding data in merely one band of the RGB color system or gray-scale image calculated by Eq. (10). Hence, the performance of data hiding capacity performed in the R, G, and B bands will be much better than that performed in the HSI color system because there are more selections of combinations and hidden places for data hiding in the RGB color system.
By carefully analyzing Table 1, we find that the test images of Airplane and Peppers demonstrate higher data hiding capacity than that of Lena and Baboon. Besides, hiding information in the bit planes of green or blue band obtains higher data hiding rate than
Table 1. Experimental results of data hiding capacity (DHC) and PSNR generated from method 1 in different bit plane combinations of red, green, and blue bands of Lena, Airplane, Baboon and Peppers test images.
Lena Airplane Peppers Baboon Color image
DHC PSNR DHC PSNR DHC PSNR DHC PSNR
red band 8thbit plane 8167 >>60 9403 >>60 8263 >>60 8152 >>60
red band 7thbit plane 8343 >>60 9483 >>60 8370 >>60 8240 >>60
red band 6th bit plane 13115 >>60 26027 >>60 18994 >>60 8413 >>60
red band 5thbit plane 39599 >>60 53312 >>60 12541 >>60 13062 >>60
green band 8thbit plane 8435 >>60 8444 >>60 17128 >>60 8008 >>60
green band 7thbit plane 8072 >>60 26471 >>60 17549 >>60 22626 >>60
green band 6th bit plane 8767 >>60 26027 >>60 18994 >>60 8413 >>60
green band 5th bit plane 17777 >>60 67118 >>60 27939 >>60 9459 >>60
blue band 8thbit plane 8138 >>60 8281 >>60 15771 >>60 8191 >>60
blue band 7thbit plane 8123 >>60 9916 >>60 16385 >>60 7988 >>60
blue band 6th bit plane 8065 >>60 21069 >>60 17112 >>60 8494 >>60
blue band 5th bit plane 11604 >>60 63924 >>60 23656 >>60 11326 >>60
red band 7th & 8thbit plane 16510 >>60 17598 >>60 16633 >>60 16392 >>60
red band 6th, 7th & 8th bit
planes 25277 >>60 43625 >>60 35627 >>60 24805 >>60 red band 5th, 6th, 7th & 8th
bit planes 64876 >>60 96937 >>60 48168 >>60 37867 >>60 green band 7th & 8th bit
plane 16507 >>60 34915 >>60 34677 >>60 30634 >>60 green band 6th, 7th & 8th bit
planes 25274 >>60 60942 >>60 53671 >>60 39047 >>60 Green band 5th, 6th, 7th &
8th bit planes 43051 >>60 128060 >>60 81610 >>60 48506 >>60
blue band 7th & 8th bit
plane 16261 >>60 18197 >>60 32156 >>60 16179 >>60 blue band 6th, 7th & 8th bit
planes 24326 >>60 39266 >>60 49268 >>60 24673 >>60 blue band 5th, 6th, 7th & 8th
bit planes 35930 >>60 103190 >>60 72924 >>60 35999 >>60 All of the 8th bit planes of
red, green, and blue band 24740 >>60 24920 >>60 41162 >>60 24531 >>60 All of the 7th bit planes of
red, green, and blue band 24538 >>60 45790 >>60 42304 >>60 38854 >>60 All of the 7th and 8th bit
planes of red, green, and blue band
49278 >>60 70710 >>60 83466 >>60 63205 >>60 red band 7th & 8th bit
planes, green band 8th bit
planes and blue band 7th &
8th bit planes
41206 >>60 44239 >>60 65917 >>60 40579 >>60
red band 7th & 8th bit
planes, green band 8th bit
planes and blue band 6th,
7th & 8th bit planes
49271 >>60 65308 >>60 83029 >>60 49073 >>60
red band 6th, 7th & 8th bit
planes, green band 8th bit
planes and blue band 6th,
7th & 8th bit planes
hiding information in the bit planes of red band. Among all experiments of data hiding, the stego-Airplane color image possesses the highest data hiding capacity by embedding information in the combination of 5th, 6th, 7th and 8th bit planes in the green band. The
lowest data hiding capacity occurs when embedding information on the 7th bit plane of
blue band of Baboon test image.
Since the perception of human being is more sensitive to green color and less sensi-tive to blue color, the performance of data hiding were also extensively experimented and analyzed on different combinations of bit planes from red, green and blue bands. As to the test image Peppers, the combination of green and blue bands achieve higher data hiding capacity than that of the red band alone. Although the perception of human being is more sensitivity to green band and less sensitive to blue band, those images embedded in the green and blue bands possess higher PSNR value and can satisfy the requirement of the Human Visual System (HVS). However, the difference is insignificant in real ex-perimental results because the data hiding rate is not high enough to demonstrate the theoretical claim.
Method 2:
The experimental result of PWLC data hiding by considering only the intensity component in the HSI color system is tabulated in Table 2 and shown in Fig. 6, respec-tively.
(a) (b) (c) (d) (e) (f) (g) Fig. 6. Different stego-Lena-test images with data being embedded in intensity component in HSI
color system, (a) embed 8140 bits in the 8th bit plane, (b) embed 8337 bits in the 7th bit
plane, (c) embed 13124 bits in the 6th bit plane, (d) embed 39622 bits in the 5th bit plan, (e)
embed 16477 bits in the 7th and 8th bit planes, (f) embed 29601 bits in the 6th, 7th and 8th bit
planes, (g) embed 69223 bits in the 5th, 6th, 7th and 8th bit planes.
Table 2. The experimental data of data hiding capacity and PSNR datum generated from method 2 by hiding data in different bit planes of the intensity compo-nent of the HSI color system.
Lena Airplane Peppers Baboon
Color image DHC PSNR DHC PSNR DHC PSNR DHC PSNR 8th bit plane 8140 >>60 8269 >>60 8196 >>60 8119 >>60 7th bit plane 8337 >>60 16059 >>60 8142 >>60 11450 >>60 6th bit plane 13124 >>60 27215 >>60 8417 >>60 8738 >>60 5th bit plane 39622 >>60 72621 >>60 15919 >>60 15798 >>60
7th and 8th bit plane 16477 >>60 24328 >>60 16338 >>60 19569 >>60
6th, 7th and 8th bit plane 29601 >>60 51543 >>60 24755 >>60 28307 >>60
The data hiding capacity of embedding hidden information in the intensity compo-nent of the HSI color system is lower than that in the hue and saturation compocompo-nents. However, there is little difference of data hiding capacity between hiding information in the RGB color system and hiding information in the intensity component of the HSI color system. If the hidden information is embedded in the 8th bit plane of the intensity
component in the HSI color system, the data hiding capacity of all test images are all around 8,200 bits where Airplane gets the highest data hiding rate. The reason of the lit-tle difference between all test images while hiding data in the 8th bit plane is because the
bit value of “0” or “1” of the least significant bit is nearly normally distributed for most of the images. By considering the test images of Lena, Airplane, Peppers, and Baboon, Peppers and Baboon possess more colorful visualization and the distribution of red, green and blue information in the two images is more balanced. Hence, the embedding of information in the 6th, 7th, or 8th bit plane individually will generate only very little
dif-ference in data hiding capacity. However, if the data hiding is performed in the 5th, 6th, 7th,
or 8th bit plane individually, there is significant difference in the data hiding capacity of
the test images of Lena and Peppers. Especially, if the data hiding is performed in the 5th
bit plane of Airplane test image, the data hiding capacity is extremely high and achieves 72,621 bits.
By carefully observing the experimental figures, we find that the visual quality of the stego-images generated by hiding covert information on the 8th bit plane is always the
best because least visual quality degradation will be generated in the least significant bit. However, the data hiding capacity will be the lowest because the distribution of bit “0” and bit “1” is approaching normal distribution. As to the hiding of the covert information in the 6th or 7th bit plane, the data hiding capacity will be a little higher than that in the
hiding in the 8th bit plane.
Method 3:
The experimental result of phase difference data hiding in the HSI color system is tabulated in Table 3 and shown in Fig. 7, respectively.
(a) (b) (c) (d) (e)
Fig. 7. Different stego-Lena-test images with data being embedded in different components in HSI color system, (a) embed 131283 bits in hue component, (b) embed 130909 bits in saturation component, (c) embed 131283 bits in hue component and 130909 bits in saturation compo-nent respectively, (d) the embedded hue image, (e) the embedded saturation image.
The data hiding performed in the hue and saturation components will change the image content and hence affect the visual quality. If the developed data hiding methods can not achieve lossless reconstruction, it is difficult to completely recover the host im-age. Hence, most of the existing color image data hiding methods are implemented based
Table 3. The experimental data of data hiding capacity and PSNR datum generated from method 3 by hiding data in the hue and saturation components of the HSI color system.
Hue Saturation Hue & saturation
Color image DHC PSNR DHC PSNR DHC PSNR Lena 131283 38.38 130909 38.033 262192 37.182 Airplane 130449 38.61 131448 39.28 261897 38.14 Peppers 131455 46.082 131428 43.74 262833 41.14 Baboon 130826 40.774 131428 45.554 261995 39.04 on the transformation of intensity from the spatial domain to the frequency domain and then manipulate the DCT or DFT data hiding on the frequency domain of the intensity data. The common shortcoming is the lower data hiding capacity. In this work, we also try to embed the hidden information in the hue and saturation components. Shown in Fig. 7 is the stego-Lena image on which the proposed data hiding method is performed on the hue and saturation components. From the experimental results, we find that the data hid-ing capacity of those performed in the hue and saturation components are higher than those performed in the red, green, and blue components.
Experimental Comparisons:
In comparing the performance of the three proposed data hiding methods, the phase difference data hiding method in the HSI color system achieves the highest data hiding capacity and PWLC data hiding utilizing pixel decomposition in the RGB color system is the second. The data hiding capacity of the PWLC data hiding by considering only inten-sity component in the HSI color system is the lowest.
The performance comparison between our proposed methods and those proposed by Wu [6] and Lin [8] are tabulated in Table 4. From the table, we can claim that our pro-posed methods not only produce very good visual quality but also possess satisfactory data hiding capacity. The performance of our proposed data hiding methods is indeed superior to those proposed in [6] and [8] in terms of visual quality and data hiding ca-pacity. Moreover, our proposed data hiding methods will not result in information loss. As proposed in [8], since a 256 * 256 * 256 color image has to be downgraded to 256 colors first before manipulation, it will thus result in information loss and distort the vis-ual qvis-uality of original host images. As for [6], since image differencing operations are
Table 4. Performance comparison of visual quality between our proposed data hiding methods and the two methods proposed in [6] and [8].
PSNR (dB) Color Image
Wu [6] Lin [8] Our method 1 Our method 2 Our method 3 Lena NA 39.17 >>60 >>60 38.38
Airplane NA 39.30 >>60 >>60 38.61
Peppers 36.15 39.19 >>60 >>60 46.082
Mandrill 40.44 NA NA NA NA
operated by the replacement of gray value, it will also distort the visual quality of host images. Although the performance of the two proposed methods in [6] and [8] in terms of visual quality and data hiding capacity is acceptable, it is still not suitable in the ap-plication of digital library.
In [7], Tzeng et al. proposed the technique by utilizing color ordering and color mapping for data hiding. Since the test images adopted in [7] are different from others, we can only theoretically compare the performance. The best PSNR in [7] is 60.6 dB with 93 bits embedded in a color image with size 100 * 224 and the hiding rate is about 0.004152 per pixel. The lowest PSNR in [7] is 36.9 dB with 21475 bits embedded in a color image with the size of 256 * 256 and the hiding rate is about 0.3318 bit per pixel. As to our proposed methods, the best PSNR is over 61 dB with 8,065 bits embedded in the 7th bit plane of Lena’s blue band and the hiding rate is about 0.03077 bit per pixel.
The lowest PSNR is 37.182 with 262192 bits embedded in both of the hue and saturation components in the HSI color system and the hiding rate is about 1.0002 bit per pixel. From the experimental data, the performance of our proposed methods is a little better than that in the method proposed in [7] in terms of visual quality and data hiding capacity. Moreover, the host image will more or less be distorted as applying the data hiding method proposed in [7] because hidden information is embedded by replacing it with its neighboring color. As to our proposed methods, they all can achieve the goal of reversi-ble and lossless reconstruction of original host images.
4. CONCLUSIONS
The issue of lossless reconstruction of original host images is especially important in the application of digital library. In digital library, it is a trend to hide side information or annotation relating to the host images (such as art painting). In such application, the hidden data has to be extracted without damaging the visual quality of the reconstructed original host images in the data extraction process.
In this paper, three methods are proposed to achieve the goal of reversible and loss-less data hiding. The rationale of the first two proposed data hiding methods is imple-mented based on the concept of pixel decomposition and PWLC data hiding mechanism. In the two proposed methods, our previously proposed PWLC data hiding mechanism is utilized to perform data hiding on those binary bit planes generated from the less signifi-cant part of color images and from the intensity component of the HSI color system, re-spectively. As to the third method, it is implemented based on the phase difference be-tween sine and cosine transformations in both of the hue and saturation components in the HSI color system. Experimental results demonstrate that the data hiding capacity and the visual quality of stego-images generated by the proposed methods are better than that of other existing methods.
Although the data hiding capacity of the methods performing in frequency domain are lower than those performed in the spatial domain, we will still focus our research on the improvement of data hiding capacity in the frequency domain. In addition, due to the gradual popularization of flash, animation and 3D mesh in websites, video games, and movies, we also plan to develop robust data hiding methods for those media.
REFERENCES
1. C. Rauber, J. O. Ruanaidh, and T. Pun, “Secure distribution of watermarked images for a digital library of ancient papers,” in Proceedings of the2nd ACM Conference on Digital Libraries, 1997, pp. 123-130.
2. F. Mintzer, “Developing digital libraries of cultural content for internet access,”
IEEE Communications Magazine, Vol. 37, 1999, pp. 72-78.
3. J. Jiang and A. Armstrong, “Data hiding approach for efficient image indexing,” IEE
Electronics Letters, Vol. 38, 2002, pp. 1424-1425.
4. Y. Hu, S. Kwong, and J. Huang, “Using invisible watermarks to protect visibly wa-termarked images,” in Proceedings of IEEE International Symposium on Circuits
and Systems, Vol. 5, 2004, pp. 584-587.
5. C. L. Tsai, K. C. Fan, C. D. Chung, and T. C. Chuang, “Reversible and lossless data hiding with application in digital library,” in Proceedings of the IEEE 38th
Interna-tional Carnahan Conference on Security Technology, 2004, pp. 226-232.
6. D. C. Wu and W. H. Tsai, “Spatial-domain image hiding using image differencing,” in IEE Proceedings of Vision, Image, and Signal Processing, Vol. 147, 2000, pp. 29-37. 7. C. H. Tzeng, Z. F. Yang, and W. H. Tsai, “Adaptive data hiding in palette images by
color ordering and mapping with security protection,” IEEE Transactions on
Com-munications, Vol. 52, 2004, pp. 791-800.
8. M. H. Lin, Y. C. Hu, and C. C. Chang, “Both color and gray scale secret images hid-ing in a color image,” International Journal of Pattern Recognition and Artificial
Intelligence, Vol. 16, 2002, pp. 697-713.
9. A. A. Kassim and W. S. Lee, “Embedded color image coding using SPIHT with par-tially linked spatial orientation trees,” IEEE Transactions on Circuits and Systems
for Video Technology, Vol. 13, 2003, pp. 203-206.
10. C. L. Tsai, K. C. Fan, C. D. Chung, andT. C. Chuang, “Data hiding of binary images using pair-wise logical computation mechanism,” in Proceedings of IEEE
Interna-tional Conference on Multimedia and Expos, Vol. 2, 2004, pp. 951-954.
11. C. Rey and J. L. Dugelay, “Blind detection of malicious alterations on still image using robust watermarks,” in Proceedings of IEE Seminar on Secure Images and
Image Authentication, 2000, pp. 7/1-7/6.
12. C. L. Tsai, H. F. Chiang, K. C. Fan, and C. D. Chung, “Reversible data hiding and lossless reconstruction of binary images using pair-wise logical computation mecha-nism,” Pattern Recognition, Vol. 38, 2005, pp. 1993-2006.
Chang-Lung Tsai (蔡昌隆) received the B.S.E.E degree from the Chung-Cheng Institute of Technology in 1988 and then served with the National Security Bureau of Taiwan. In 1992, he received the scholarship from government and studied at the Uni-versity of Southern California. In 1994, he graduated with the M.S.E.E. degree and received the Outstanding Academic Awards from USC. In 2006, he received the Ph. D. degree of Electrical Engineering from National Central University of Taiwan. Cur-rently, he serves with the Department of Computer Science at Chinese Culture University of Taiwan. His research interests focus on signal processing, remote sensing image processing, and data hiding.
Kuo-Chin Fan (范國清) was born in Hsichu of Taiwan in 1959. He graduated from National Tsing Hua University with the B.S.E.E. degree in 1981. He received the M.S.E.E. and Ph.D. from University of Florida in 1985 and 1989, respectively. He served at National Central University starting from 1989. Cur-rently, he is the professor of Department of Computer Science and Information Engineering and the director of Communication Research Center. Dr. Fan is the Editor of Journal of Computers, Journal of Information Science and Engineering, and the Interna-tional Journal of Computer Processing of Oriental Language. He was the former chairman of Image Processing and Pattern Recognition Society of Taiwan and is the Governing Board Member of International Association of Pattern Recognition (IPPR). He received consecutive three Outstanding Researcher award from National Science Council of Taiwan from 1998 to 2005. His research interests focus on biometrics verification, video surveillance, document analysis, and computer vision.
Thomas Chiang Chuang (莊暢) was born in Taiwan, R.O.C. He received his Ph.D. degree in Electrical Engineering from the University of California, Los Angles in 1981. He has worked for many internationally well-known companies like Eastman Kodak, DuPont and Raytheon. He joined Van Nung Institute of Tech-nology as an Associated Professor in the Department of Com-puter Science and Information Engineering in 2002 and promoted to professor in 2005. His current research interests include laser electro optics, image processing, natural language processing, and pattern recognition.
Char-Dir Chung (鐘嘉德) received the B.S. degree in Elec-trical Engineering from the National Taiwan University, Taipei, in 1983, and the M.S. and Ph.D. degrees in Electrical Engineer-ing from the University of Southern California, Los Angeles, in 1986 and 1989, respectively. From 1989 to 1992, Dr. Chung was with the LinCom Corporation, Los Angeles, where he worked on analytical and simulation modeling of scientific and military sat-ellite communication systems. From 1992 to 2005, he joined the faculty of the National Central University in Taiwan. Since 2005, he has been on the faculty of the National Taiwan University, where he is now a Professor of the Electrical Engineering Department and the Graduate Institute of Communication Engineering. His current research interests include digital modulation theory, wireless communications, spread spectrum communications and sta-tistical signal processing. He has published more than 50 journal and conference papers and holds two patent rights in these areas.


![Table 4. Performance comparison of visual quality between our proposed data hiding methods and the two methods proposed in [6] and [8]](https://thumb-ap.123doks.com/thumbv2/9libinfo/8838683.238202/15.892.186.711.840.966/table-performance-comparison-quality-proposed-methods-methods-proposed.webp)