This article was downloaded by: [National Chiao Tung University 國立交通大學] On: 25 April 2014, At: 22:36
Publisher: Taylor & Francis
Informa Ltd Registered in England and Wales Registered Number: 1072954 Registered office: Mortimer House, 37-41 Mortimer Street, London W1T 3JH, UK
Journal of the Chinese Institute of Engineers
Publication details, including instructions for authors and subscription information:
http://www.tandfonline.com/loi/tcie20
Universal share for the sharing of multiple images
Wen‐Pinn Fang ab & Ja‐Chen Lin ca
Department of Computer Science , National Chiao Tung University , Hsinchu, Taiwan 300, R.O.C. Phone: 886–35721490 E-mail:
b
Department of Computer Science and Information Engineering , Yuanpei University , Hsinchu, Taiwan 300, R.O.C.
c
Department of Computer Science , National Chiao Tung University , Hsinchu, Taiwan 300, R.O.C.
Published online: 04 Mar 2011.
To cite this article: Wen‐Pinn Fang & Ja‐Chen Lin (2007) Universal share for the sharing of multiple images, Journal of the
Chinese Institute of Engineers, 30:4, 753-757, DOI: 10.1080/02533839.2007.9671301 To link to this article: http://dx.doi.org/10.1080/02533839.2007.9671301
PLEASE SCROLL DOWN FOR ARTICLE
Taylor & Francis makes every effort to ensure the accuracy of all the information (the “Content”) contained in the publications on our platform. However, Taylor & Francis, our agents, and our licensors make no
representations or warranties whatsoever as to the accuracy, completeness, or suitability for any purpose of the Content. Any opinions and views expressed in this publication are the opinions and views of the authors, and are not the views of or endorsed by Taylor & Francis. The accuracy of the Content should not be relied upon and should be independently verified with primary sources of information. Taylor and Francis shall not be liable for any losses, actions, claims, proceedings, demands, costs, expenses, damages, and other liabilities whatsoever or howsoever caused arising directly or indirectly in connection with, in relation to or arising out of the use of the Content.
This article may be used for research, teaching, and private study purposes. Any substantial or systematic reproduction, redistribution, reselling, loan, sub-licensing, systematic supply, or distribution in any
form to anyone is expressly forbidden. Terms & Conditions of access and use can be found at http:// www.tandfonline.com/page/terms-and-conditions
ABSTRACT
To share numerous grey-valued images (or numerous color-valued images), this study presents a system with a universal share. A company organizer can use this universal share to attend the recovery meeting of any shared image. No storage space is wasted; i.e. for each shared image, the total storage space occupied by all generated shares (including the universal share) is identical to the image size.
Key Words: image sharing, LSB hiding.
* C o r r e s p o n d i n g a u t h o r . ( T e l : 8 8 6 - 3 5 7 2 1 4 9 0 ; E m a i l : wpfang@cis.nctu.ed.tw)
The authors are with the Department of Computer Science, National Chiao Tung University, Hsinchu, Taiwan 300, R.O.C., and W. P. Fang is currently at Department of Computer Science and Information Engineering, Yuanpei University, Hsinchu, Taiwan 300, R.O.C.
I. INTRODUCTION
In an (n, n) image sharing system (Thien and Lin, 2002; Thien and Lin, 2003a; and Wu et al., 2004),
n shares {L1, L2, ..., Ln} are created for a given image,
e.g., Lena. The image can be revealed when all n shares are received, while less than n shares reveal nothing about the image. With sharing, nobody (even the company organizer) can view the image without attending a public meeting. Therefore, sharing is a safety process that is valuable in a company where no employee/investor alone should be trusted. Significantly, the original image can be discarded after the sharing; moreover, each of the n shares is 1/n of the size of the given image. Therefore, the sharing process does not waste storage space. To share another image, Monkey (which is grey-valued iff Lena is grey-valued), another n shares {M1, M2,
..., Mn} are similarly created. Each
employee/part-ner of a company can thus obtain a share from each image related to his job/investment. Consequently, if a company organizer obtains 1 share from each of the 100 important images shared, then he will have difficulty managing his 100 shares. Share manage-ment becomes increasingly difficult as the number of images rises. This study proposes the use of a
“universal” share for a company’s organizer by com-bining sharing and hiding (Lie and Chang, 1999; Maniccam and Bourbakis, 2004; Thien and Lin, 2003a; Wang et al., 2001; and Wu and Liu, 2003). The organizer only has to take the unique share (a single share with a compact size, see the top of Fig. 1 (c) and 2(c)) to attend the recovery meeting for any image. Although the method described here handles grey images, it can also be applied to color images by processing the three color components one by one. The color version was also found satisfactory, but its processing steps are not shown here to save space.
Below are reviewed some reported methods dealing with multiple secret images. The paper (Chan and Chang, 2005) is well-proved and mathematically sound; but it is not used here because (Chan and Chang, 2005) has no experiment data. Tsai et al. (2002) proposed an elegant method using visual cryp-tography and LSB hiding for multiple secret images. For C(4,2) = 6 secret images of size 200 × 200 each, Tsai et al. hid the corresponding 6 × 200 × 200 bytes using only four stego images (each of size 600 × 600 and about 42.5dB in PSNR), of which any two can be combined to extract one of the six secret images. For our universal approach, assume that n = 4 shares are created for each image. The storage space before hid-ing the generated shares, is 200 × 200 × ((1/4) × 1 + (3/4) × 6) = 4.75 × 200 × 200 bytes, where (1/4) × 1=1/n is for the universal share, and (3/4) × 6 = ((n – 1)/n) × 6 is for the non-universal shares of the six secret images. Our system thus saves more space than that of (Tsai et al., 2002) (the ratio is 4.75 : 6, before
754 Journal of the Chinese Institute of Engineers, Vol. 30, No. 4 (2007)
hiding). If the generated shares are also hidden, then the total space for the stego images is 4 × 4.75 × 200
× 200 = 19 × 200 × 200 bytes to obtain stego images of PSNRs much better than 42.5 dB; compared with 4 × 600 × 600 = 36 × 200 × 200 bytes to obtain 42.5dB stego images in (Tsai et al., 2002). However, the recovered secret images in (Tsai et al., 2002) are without loss, while ours are lossy.
Feng et al. (2005) presented a gorgeous method for sharing multiple secret images based on summing up the variables used in the sharing polynomials. Their method uses, for instance, 5 shares {a, b, c, d,
e}, and can reveal secret image 1 using {a, b, c}, and
secret image 2 using {a, d, e}, and secret image 3 using some other combination of shares. The total size of the sharing result using Feng et al.’s method is typically 1-2 times the total size of the input secret images. That is, their method causes size expansion. By contrast, our method has a size reduction effect, because the total size of our sharing result is even
smaller than the total size of the input secret images. More precisely, the size of our sharing result is only [(1/n) × 1 + (n –1)/ n × S]/S = (1 –(1 – S–1
)/n) × 100% of the input, where S denotes the number of secret images, and n denotes the number of shares for each secret image. Therefore, our method has an advan-tage in economy of size. However, like Ref. (Tsai et
al., 2002), Ref. (Feng et al., 2005)’s method can
achieve lossless recovery of the secret images. As for the encoding or decoding speed, Ref. (Feng et al., 2005) is slower than our method (because the degree of their sharing polynomial is one degree higher than ours), while Ref. (Tsai et al., 2002) is faster than our method (because they use logic operations to achieve sharing, which are faster than the operations needed in the polynomial approach).
Unlike our method, Refs. (Tsai et al., 2002) and (Feng et al., 2005) have no super share (the share for company organizer). Therefore, our method can be utilized when the boss of a company wishes to control
(a) (b) (c)
Fig 1. A sharing result for n = 8. (a) initial image Lena; (b) modified image Lena*, which contains the image U, from which all extracted ai values are in the range 0-250 (see Eq. (1)); (c) the 8 shares that can recover (b) together; the top-most share in (c) is the universal share, which is identical to the image U.
(a) (b) (c)
Fig 2. Another sharing result for n = 8. (a) initial image Monkey; (b) the modified image Monkey*; (c) the 8 shares that can recover (b) together; the top-most share is identical to the top-most share in Fig. 1(c).
of U are less than 251, as they are used later in Eq. (1)). This image U, whether noisy or not, has 8pq/n bits, which are embedded into the p × q image Lena by the least-significant-bits (LSB) replacement method (Lie and Chang,1999; Maniccam and Bourbakis, 2004; Thien and Lin, 2002; Thien and Lin, 2003a; Thien and Lin, 2003b; Wang et al., 2001). For instance, if n
≥ 8, then Image U has at most p × q bits, so U can be hidden using the least-significant-bits (1 bit per pixel) of Lena, which has p × q pixels. If 4 ≤ n ≤ 7, then U is hidden using the last two bits of Lena’s pixels. After embedding, Lena becomes a distorted image called Lena*. Since only some less-important bits of Lena are replaced (assuming n ≥4), the distortion is invis-ible when comparing Lena* and Lena.
2. Partitioning Each Sector
Decompose Lena* into non-overlapping sectors of n pixels each (8n bits per sector). Then share the 8n bits of each sector among the n shares. To save paper length, we assume n = 8 below; other values of
n are handled analogously.
(i). The LSBs of the n = 8 pixels of the sector form an 8-bit number, called a0. Notably, a0 < 251 by
Sec. II.1.
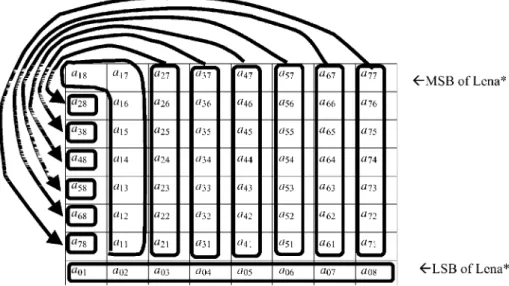
(ii). The remaining 8 × 7 = 56 bits of the sector are then partitioned into another 7 numbers {a1, ...,
a7} of 8 bits each (see Fig. 3); i.e., {ai = (ai1, ai2,
..., ai8)|1 ≤ i ≤ 7}. For 1 ≤ i ≤ 7, Fig. 3 ensures
that the most significant bit (MSB) ai1 of every
ai = (ai1, ai2, ..., ai8) is the bit next to the LSB of
a Lena* pixel. This property avoids visible dam-age to the imdam-age Lena* if the bit value of some
ai1 is changed from 1 to 0 so that all ai stay in
the 0-250 range before utilizing Eq. (1) (as noted below Eq. (1)).
3. Sharing
We already have {a0, a1, ..., a7}. Affix to each
Share k, where 0 ≤ k ≤ n – 1 = 7, a value
f(k)=(a0 + a1k + a2k2 + ... + an – 1kn – 1) mod 251,
(1)
4. Using the Universal Share U
The company organizer keeps Share 0, whose value is f(0) = a0 for each sector. Since the set {a0}
is formed of the LSB of image Lena*, it is also formed of image U, because U is embedded in Lena’s LSB to obtain Lena* in Sec. II.1. Hence, Share 0 is identical to U, the image created earlier by the organizer. This statement is true even if Lena is replaced by any other image (e.g., Monkey). Share 0, i.e. image U, is thus the desired universal share.
During the recovery phase, when all n shares are collected, recover the values {a0, ..., an – 1} from
{f(0), ..., f(n – 1)} using Lagrangian interpolation polynomials. This is an ordinary, routine procedure used in the sharing field, as described in Refs. (Wu
et al., 2004; Feng et al., 2005) The modified image,
(regardless OR irrespective) of whether it is Lena* or Monkey*, can thus be recovered sector-by-sector.
III. EXPERIMENTS
Assume that n = 8. Fig. 1(a) depicts the input image Lena, and the company organizer arbitrarily creates his own share (the top-most noisy image U in Fig 1(c), whose pixel values are all below 251). Fig. 1(b) is the modified image Lena*, which not only hides the entire image U in its LSB, but also has the property that all ai extracted from it are in the range
0-250 (see the explanations in Sec. II.2 and II.3). Then, Lena* is shared. Share 0 is the given image U, and the remaining n –1= 7 shares are generated us-ing k = 1, 2, ..., n – 1 in Eq. (1). All 8 shares are shown in Fig. 1(c). These 8 shares can together re-cover the Lena* displayed in Fig. 1(b). Fig. 2 shows another experiment in which Lena is replaced by Monkey. Its Share 0 (the top-most noisy image in 2(c)) is identical to Share 0 in Fig. 1(c), because both are identical to U.
IV. SUMMARY
In summary, our sharing method is space-saving and with a convenient universal share. The advantages are achieved by tolerating an invisible distortion in the
756 Journal of the Chinese Institute of Engineers, Vol. 30, No. 4 (2007)
Fig 3 Partition of a sector of Lena* (see Section II.2). (a) the grouping of bits, (b) an example illustrating (a).
recovered images. For instance, the recovered images in Figs. 1(b) and 2(b) are 52.5 dB in PSNR, when be-ing compared with the original images in Figs. 1(a) and 2(a). As a remark, our program can be run repeat-edly to handle any number of secret images, for instance, 1000 secret images, without the need for reprogramming. Additionally, the universal share U can be non-noisy,
because U can be any kind of image, including ordi-nary photos. Hence, only non-universal shares, which always look noisy, need post-processing hiding.
ACKNOWLEDGMENTS
The anonymous reviewers are thanked for their
Scheme Using Largrange’s Interpolation,”
Jour-nal Systems and Software, Vol. 76, No. 4, pp.
327-339.
Lie, W. N., and Chang, L. C., 1999, “Data Hiding in Images with Adaptive Numbers of Least Signifi-cant Bits Based on the Human Visual System,”
International Conference on Image Processing,
Kobe, Japan, Oct., Vol. 4, pp. 286-290.
Maniccam, S. S., and Bourbakis, N., 2004, “Lossless Compression and Information Hiding in Images”,
Pattern Recognition, Vol. 37, No. 3, pp. 475-486.
Thien, C. C., and Lin, J. C., 2002, “Secret Image Sharing,” Computers & Graphics, Vol. 26, No. 5, pp. 765-770.
Thien, C. C., and Lin, J. C., 2003a, “An Image-Shar-ing Method with User-Friendly Shadow Images,”
Wang, R. Z., Lin, C. F., and Lin, J. C., 2001, “Image Hiding by Optimal LSB Substitution and Genetic Algorithm,” Pattern Recognition, Vol. 34, No. 3, pp. 671-683.
Wu, M., and Liu, B., 2003, “Data Hiding in Image and Video: I. Fundamental Issues and Solutions,” IEEE
Transactions on Image Processing, Vol. 12, No.
6, pp. 685- 695.
Wu, Y. S., Thien, C. C., and Lin, J. C., 2004, “Shar-i n g a n d H “Shar-i d “Shar-i n g S e c r e t I m a g e s w “Shar-i t h S “Shar-i z e Constraint,” Pattern Recognition, Vol. 37, No. 7, pp. 1377-1385.
Manuscript Received: Oct. 13, 2005 Revision Received: Nov. 03, 2006 and Accepted: Dec. 15, 2006