國 立 交 通 大 學
資訊科學與工程研究所
博 士 論 文
適用於無線網路之使用者認證協定
User Authentication Protocols in Wireless Networks
with Petri Net Verification
研 究 生:曾蕙如
適用於無線網路之使用者認證協定
User Authentication Protocols in
Wireless Networks with Petri Net Verification
研 究 生: 曾蕙如
Student:
Huei-Ru
Tseng
指導教授: 簡榮宏 博士
Advisor: Dr. Rong-Hong Jan
國 立 交 通 大 學
資 訊 科 學 與 工 程 研 究 所
博 士 論 文
A D i s s e r t a t i o n
S u b m i t t e d t o D e p a r t m e n t o f C o m p u t e r S c i e n c e
C o l l e g e o f C o m p u t e r S c i e n c e
N a t i o n a l C h i a o Tu n g U n i v e r s i t y
i n p a r t i a l F u l f i l l m e n t o f t h e R e q u i r e m e n t s
f o r t h e D e g r e e o f
D o c t o r o f P h i l o s o p h y
i n
C o m p u t e r S c i e n c e
M a y 2 0 1 0
H s i n c h u , Ta i w a n , R e p u b l i c o f C h i n a
適 用 於 無 線 網 路 之 使 用 者 認 證 協 定
研究生: 曾蕙如 指導教授: 簡榮宏 博士
國 立 交 通 大 學 資 訊 科 學 與 工 程 研 究 所
摘 要
無線網路產業歷經多年發展,發展重心在於提供客戶獨一無二的資訊應用服務的技術。 對於無線網路而言,其技術核心在於資源的存取-滿足使用者隨時隨地皆能存取遠端資源的 行動生活應用需求。然而電腦犯罪活動卻隨著資訊科技的發展日益猖獗。因此,建構一個安 全的資訊/通訊環境乃為當務之急。針對無線網路資源的存取,伺服器必須能有效地認證遠端 使用者的身份。近年來無線感測網路(wireless sensor networks, WSNs)已經是無線網路研究中重要的議題 之一,它是由許多散佈於各地的感測節點(sensor nodes)所組成,主要用以蒐集各種環境資料, 例如溼度、壓力、溫度等。每個節點皆有監控偵測物理環境的能力,並藉由無線通訊的方式, 將所蒐集之資訊回傳至基地台(base station)或是應用系統的後端平台(backend)。因應無線感測 網路無所不在(ubiquity)的應用需求增加,使用者應能即時存取儲存於感測節點的資訊。因此, 感測節點所收集之資訊應該採取安全機制來加以保護,避免未經授權的使用者非法取得。 本論文中,我們將闡述無線安全領域的發展現況,與多種無線網路中的使用者認證協定 (user authentication protocols)。同時針對使用者認證之安全架構與安全需求加以說明。再者, 我們提出數種適用於無線網路之使用者認證協定,其中包括植基於密碼方法的使用者認證協 定(password-based user authentication protocols)、植基於生物特徵方法的使用者認證協定 (biometrics-based user authentication protocols) , 以 及 自 我 憑 證 方 法 的 使 用 者 認 證 協 定
(self-certificate-based user authentication protocols)。
針對植基於密碼方法的使用者認證協定,我們提出兩種認證協定。協定一乃運用 LU 矩 陣分解法(LU decomposition),讓使用者透過開放式通訊網路進行認證與存取網路服務。此協 定的特性包括動態更改密碼、相互認證(mutual authentication)、使用者匿名(user anonymity), 與金鑰協議(key agreement)等。協定二主要是適用於無線感測網路的使用者認證協定,能讓 使用者以低運算量來即時存取感測節點的資訊。
針對植基於生物特徵方法的使用者認證協定,我們提出一個適用於智慧卡(smart cards) 的使用者認證協定。此協定能允許伺服器驗證使用者之生物特徵的同時,亦能保護使用者隱 私。此外,我們將此協定與秘密分享方法結合,擴充為多人生物特徵認證協定(multi-party biometrics-based user authentication protocol)-即(t, n)-門檻式多人認證協定,在此協定中,必 須提出至少 t 個以上之使用者生物特徵、密碼,與智慧卡,方可重建認證金鑰(authentication key)。
針對植基於自我憑證方法的使用者認證協定,我們提出一個適用於無線感測網路的認證 協定,提供使用者與感測節點相互認證與金鑰協議,同時,金鑰分配中心(key distribution center, KDC)亦可撤銷金鑰對。在此協定中,使用者首先傳送資料要求封包予其傳輸範圍內的感測節 點,感測節點認證通過,即可回傳使用者所要求之資料。平均而言,我們假設使用者傳輸範 圍內有 n 個感測節點。在攻擊者截取 n 個感測節點當中 t 個節點的情況下,此協定仍然可以 維持其安全性。此外,我們利用派翠網路(Petri nets)來建立模型並分析所提出的協定,並證明 其可抵禦多種攻擊模式。
User authentication protocols in wireless
networks with Petri net verification
Student: Huei-Ru Tseng Advisor: Dr. Rong-Hong Jan Department of Computer Science
National Chiao Tung University
Abstract
The wireless industry, over the last few years, has undergone a tremendous amount of change, which is brought about through the introduction of a never ending stream of technologies all designed to provide unique services that customers will purchase. For wireless networks, at the heart of all the technologies introduced is access—being able to access services regardless of where the end user is physically located. While wireless networks are very convenient for users, their widespread use creates new challenges from a security point of view. To control access to wireless networks, it is essential for the server to authenticate the remote users.
A variant of the wireless networks is wireless sensor networks (WSNs). In WSNs, there are spatially distributed sensors which cooperatively monitor environ-mental conditions, such as humidity, pressure, temperature, motion, or vibration, at different locations. Each sensor node has the ability to monitor the physical world and return the sensed information to base stations or at the backend of the application system via wireless communication. With the increasing ubiquity of WSNs, real-time data could be accessed from every sensor node. Hence, secu-rity measures should be taken to protect the collected secrets in order to prevent un-authorized users from gaining the information.
In this dissertation, we introduce recent developments in the field of wireless se-curity and investigate several user authentication protocols in wireless networks. A detailed explanation of security frameworks and security requirements for authen-tication will be given. We design several user authenauthen-tication protocols in wireless
networks, including two kinds of password-based user authentication protocols, a biometrics-based user authentication protocol, and a self-certificate-based user authentication protocol.
For password-based user authentication, we propose two password-based user authentication protocols, namely protocol-I and protocol-II. The protocol-I is a password-based user authentication protocol using LU decomposition, which au-thenticates remote users and allows legitimate users to access network services over an open communication network. This protocol possesses many merits, including freely changeable passwords, mutual authentication, user anonymity, and session key agreement. The protocol-II is a password-based user authentication protocol for WSNs, which allows legitimate users to query sensor data at any of the sensor node in an ad hoc manner and imposes very little computational overhead.
For biometrics-based user authentication, we propose a biometrics-based re-mote user authentication protocol using smart cards. The protocol fully preserves the privacy of the biometric data of each user while allowing the server to verify the correctness of the users’ biometric characteristics without knowing the ex-act values. In addition, the proposed protocol is later extended to a multi-party biometrics-based remote user authentication protocol by incorporating a secret sharing component. This extended protocol is essentially a (t, n)-threshold multi-party authentication protocol. Any group of t or more users can together recon-struct the authentication key with their own biometric data, passwords, and smart cards but no group of less than t users can.
For self-certificate-based user authentication, we propose a self-certificate-based user authentication protocol for WSNs, which can deal with authenticated queries involving multiple sensor nodes, achieve mutual authentication and key agreement between users and sensor nodes, and provide a key distribution center (KDC) to revoke compromised key pairs. In this protocol, a user can send data requests to the sensor nodes within his communication range and receives valid responses if the requests are legitimate. On average, there are n sensors in the communication
range of the user. The proposed protocol still works well even if the adversary captures t nodes out of n nodes in the WSNs. Moreover, security of these proposed protocols is modelled and analyzed with Petri nets. Our analysis shows that the protocols can defend notorious attacks.
誌謝
首先感謝指導教授簡榮宏博士六年來的諄諄教誨與耐心教導,使學生在學術 研究與待人處事上受益良多,感謝之情非筆墨所能形容,浩浩師恩,心版永銘, 在此獻上最高的敬意與謝忱。同時,學生也非常感謝口試委員交通大學資訊工程 學系楊武教授與陳榮傑教授、清華大學資訊工程學系黃能富教授與孫宏民教授、 臺灣科技大學資訊管理系吳宗成教授對本論文不吝批評與指正,使本論文更臻完 善,在此深表感激。我也要特別感謝周澤民教授與德國 Passau University 的 Hermann De Meer 教 授對於我在學術方面的指導,也感謝 Passau University 的 Computer Networks and Computer Communications 實驗室成員,陪伴我在德國的研究生活。謝謝計算機 網路實驗室所有成員在課業的提攜與生活上的照顧,也謝謝在求學生涯中,曾經 鼓勵與支持我的朋友。 同時我也感謝財團法人漢儒文教基金會、財團法人宗倬章先生教育基金會、 財團法人世豐善智慈善事業基金會、英業達 OKWAP 教育基金會、臺北縣政府、 雅虎奇摩無名小站、東森媒體集團,以及臺灣網路認證股份有限公司所提供的獎 助學金,讓我在求學生涯中,更能無後顧之憂的專心於研究工作。 最後,感謝我的家人,在我求學生涯中,無微不至的照顧與關懷,讓我毫無 牽掛地專注於學業,給予我最溫暖的愛與不間斷的支持與鼓勵。在此願將完成論 文的喜悅與大家分享。
Acknowledgements
A lot of people have contributed to this dissertation, and made my entire stay at NCTU as enjoyable and fulfilling as it has been. Most of all, I would like to thank my advisor Professor Rong-Hong Jan for having his door always open and for helping me to direct my research and to stay focused. Then, I would like to express great gratitude to Professor Wuu Yang, Professor Rong-Jaye Chen, Professor Nen-Fu Huang, Professor Hung-Min Sun, and Professor Tzong-Chen Wu, who gave me a lot of great advice in this dissertation.
Next, I would like to convey my thanks to Professor Emery Jou, who gave me constructive suggestions and has taught me many things, especially in security algorithms. I would also like to thank to everyone in DAAD, NSC, and in particular Professor Hermann De Meer and his entire wonderful research group at Passau University for giving me the opportunity to do research in Germany. The summer spent in this group was truly fantastic. Thanks also to all members of Computer Network Lab for their assistance and kindly helping both in the research and the daily life during these years.
Moreover, I would like to thank the Han-Ru Foundation, the Tzong Jwo Jang Educational Foundation, the Sheh Fung Good Deed and Wisdom Charity Foundation, the OKWAP Inc., the Taipei County Government, the Yahoo! Inc., the Eastern Multimedia Group, and the TWCA Inc. for providing scholarships for me.
Finally, I would like to dedicate this dissertation to my family for their great love and support in all stages of my life.
Contents
Abstract (in Chinese) i
Abstract (in English) iii
Acknowledgements (in Chinese) vi
Acknowledgements (in English) vii
Contents viii
List of Tables xi
List of Figures xiii
1 Introduction 1
2 Preliminaries 5
2.1 Mathematical problems . . . 5
2.2 LU decomposition . . . 7
2.3 Secret sharing method . . . 8
2.4 Related works . . . 8
2.4.2 Biometrics-based user authentication . . . 11
2.4.3 Self-certificate-based user authentication . . . 12
3 Password-based user authentication protocol 14 3.1 Protocol-I: Password-based user authentication protocol using LU decomposition . . . 14
3.1.1 Registration phase . . . 15
3.1.2 Login-and-authentication phase . . . 16
3.1.3 Password-change phase . . . 19
3.2 Protocol-II: Password-based user authentication protocol for WSNs 19 3.2.1 Registration phase . . . 20
3.2.2 Login-and-authentication phase . . . 20
3.2.3 Password-change phase . . . 21
3.3 Security analysis . . . 22
3.3.1 Correctness . . . 22
3.3.2 Petri net model . . . 23
3.3.3 Security properties . . . 23
3.3.4 Functionality . . . 33
3.4 Efficiency analysis . . . 34
4 Biometrics-based user authentication protocol 37 4.1 Proposed protocol . . . 38
4.1.1 Registration phase . . . 38
4.1.2 Login-and-authentication phase . . . 39
4.1.3 Password-change phase . . . 41
4.2.1 Registration phase . . . 43
4.2.2 Login-and-authentication phase . . . 44
4.3 Security analysis . . . 46
4.3.1 Petri net model . . . 47
4.3.2 Security properties . . . 48
4.4 Efficiency analysis . . . 54
5 Self-certificate-based user authentication protocol 57 5.1 Proposed protocol . . . 58
5.1.1 Pre-deployment phase . . . 59
5.1.2 Login-and-authentication phase . . . 61
5.1.3 User-controlled key change phase . . . 63
5.1.4 Key revocation phase . . . 65
5.2 Security analysis . . . 65
5.2.1 Petri net model . . . 65
5.2.2 Security properties . . . 66
5.2.3 Functionality . . . 70
5.3 Efficiency analysis . . . 70
6 Conclusion and future works 75
Bibliography 77
Vita 84
List of Tables
1.1 Formal definition of a Petri net . . . 3
2.1 Notations . . . 6
3.1 Definitions of places for protocol-I . . . 28
3.2 Definitions of transitions for protocol-I . . . 29
3.3 Definitions of places for protocol-II . . . 29
3.4 Definitions of transitions for protocol-II . . . 30
3.5 Comparison of authentication protocols . . . 34
3.6 Evaluation parameters . . . 34
3.7 Performance of the protocol-I . . . 35
3.8 Performance comparison between Wong et al.’s protocol and the protocol-II . . . 36
4.1 Definitions of places . . . 50
4.2 Definitions of transitions . . . 51
4.3 Evaluation parameters . . . 56
4.4 Performance comparison between Fan and Lin’s protocol and the proposed protocol (per user) . . . 56
4.5 Performance comparison between Fan and Lin’s protocol and the proposed protocol (for the server) . . . 56
5.1 Formal definition of a self-certificate . . . 59
5.2 Definitions of places . . . 68
5.3 Definitions of transitions . . . 69
5.4 Comparison of user authentication protocols for WSNs . . . 71
5.5 Performance comparison in the pre-deployment phase . . . 72
5.6 Performance comparison in the login-and-authentication phase . . . 73
List of Figures
3.1 The login-and-authentication phase of the password-based user au-thentication protocol using LU decomposition. . . 18 3.2 The login-and-authentication phase of the password-based user
au-thentication protocol for WSNs. . . 22 3.3 A Petri net model of the password-based user authentication
protocol-I. . . 24 3.4 A Petri net model of the password-based user authentication
protocol-I under an attack scenario. . . 25 3.5 A Petri net model of the password-based user authentication
protocol-II. . . 26 3.6 A Petri net model of the password-based user authentication
protocol-II under an attack scenario. . . 27 4.1 The login-and-authentication phase of the proposed protocol. . . . 42 4.2 The login-and-authentication phase of the multi-party
authentica-tion protocol. . . 47 4.3 A Petri net model of the proposed biometrics-based user
4.4 A Petri net model of the proposed biometrics-based user authenti-cation protocol under an attack scenario. . . 49 5.1 The pre-deployment phase of the proposed protocol. . . 61 5.2 The login-and-authentication phase of the proposed protocol. . . . 63 5.3 A Petri net model of the proposed self-certificate-based user
authen-tication protocol. . . 66 5.4 A Petri net model of the proposed self-certificate-based user
authen-tication protocol under an attack scenario. . . 67 5.5 Broadcasting message format from a user to sensors in the
login-and-authentication. . . 73 5.6 Transmitting message format from a sensor to a user in the
Chapter 1
Introduction
The wireless industry, over the last few years, has undergone a tremendous amount of change, which is brought about through the introduction of a never-ending stream of technologies all designed to provide unique services that customers will purchase. However, wireless network security is still a major impediment to further deployment of the wireless networks. Security mechanisms in wireless networks are essential to protect data integrity and confidentiality, authentication, user privacy, quality of service, and continuity of service. For wireless networks, at the heart of all the technologies introduced is access—being able to access services regardless of where the end user is physically located. The rapid growth of wireless communication means that security issues in wireless networks are of increasing practical importance. Therefore, to control access to wireless networks, it is essential for the server to authenticate the remote users. A remote user authentication protocol is a mechanism that authenticates remote users and allows legitimate users to access network services over an open communication network.
A variant of the wireless networks is wireless sensor networks (WSNs). In WSNs, there are spatially distributed sensors which cooperatively monitor envi-ronmental conditions, such as humidity, pressure, temperature, motion, or
vibra-tion, at different locations. It integrates both wireless and sensor technology into a small device, called a sensor node. Each sensor node has the ability to monitor the physical world and return the sensed information to base stations or at the backend of the application system via wireless communication. The collected data can be presented to users either upon inquiries or upon event detection. In general, most queries in WSN applications are issued at the base stations or at the backend of the application system. However, real-time data may no longer be accessed only at the base stations or the gateway nodes. With the increasing ubiquity of WSNs, real-time data could be accessed from every sensor node. For some applications, such as military surveillance, the collected data is highly sensitive. Hence, secu-rity measures should be taken to protect the collected secrets in order to prevent un-authorized users from gaining the information.
Passwords are frequently used in the user authentication protocols because they are easier to remember by users than cryptographic keys. In 1981, Lamport [33] proposed a password authentication protocol that makes use of password tables to verify remote users. However, in Lamport’s protocol, password tables are stored in the remote server, which might be broken into and hence the passwords might be stolen. In order to eliminate the risk of password leakage, a great deal of research, including solutions using smart cards, has been proposed.
A smart card is a tamper-resistant device that contains one or more integrated circuits (ICs) and also may employ one or more of the following machine-readable technologies: magnetic stripe, bar code, contactless radio frequency transmitters, biometric information, encryption and authentication, or photo identification [2]. The integrated-circuit chip (ICC) embedded in the smart card can act as a mi-crocontroller or as a computer. Data are stored in the chip’s memory and can
Table 1.1: Formal definition of a Petri net A Petri net is a 5-tuple, (P, T, F, W, M0) where:
P = {P1, P2, · · · , Pm} is a finite set of places,
T = {T1, T2, · · · , Tn} is a finite set of transitions,
F ⊆ (P × T ) ∪ (T × P ) is a set of arcs (flow relation), W : F → {1, 2, 3, · · ·} is a weight function,
M0 : P → {0, 1, 2, 3, · · ·} is the initial marking,
P ∩ T = Ø and P ∪ T 6= Ø.
A Petri net structure N = (P, T, F, W ) without any specific initial mark-ing is denoted by N.
A Petri net with the given initial marking is denoted by (N, M0).
be accessed to complete various processing applications. The merits of a smart card for password authentication are the simplicity and efficiency of the login and authentication process [66]. Experience has shown that constructing a secure user authentication protocol with smart cards is not trivial because lots of proposed protocols were subsequently broken. Therefore, how to design robust user authen-tication protocols for wireless networks is a critical issue.
This dissertation introduces recent developments in the field of wireless secu-rity and investigates various user authentication protocols in wireless networks. A detailed explanation of security frameworks and security requirements for authen-tication will be given. We design several user authenauthen-tication protocols in wireless networks, including two kinds of password-based user authentication protocols, a biometrics-based user authentication protocol, and a self-certificate-based user authentication protocol. Moreover, Petri nets [53] may be used to infer what an attacker could know if he happens to know certain items in the security protocol. The formal definition of a Petri net [46] is listed in Table 1.1. Petri nets are composed from graphical symbols designating places (shown as circles), transitions
(shown as rectangles), and directed arcs (shown as arrows). The places denote (atomic and composite) data items. The transitions denote decryption or decom-position operations. The directed arcs run between places and transitions. When a transition fires, a composite data item is decomposed or decrypted, resulting in one or more simpler data items. Since we assume an open network environment, all data items in the transmitted messages are assumed to be public, and are known to the attacker. There will be tokens in the places representing the data items in the transmitted messages initially. From this initial marking, we can infer what an attacker can know. Furthermore, we can also experiment what an attacker can know if he knows additional data items from other sources. Therefore, we use Petri nets in the security analysis of the proposed protocols.
The rest of this dissertation is organized as follows. In Chapter 2, we state the basic terms and preliminaries for our dissertation, and briefly review exist-ing user authentication protocols in wireless networks. In Chapter 3, we introduce password-based user authentication protocols. Next, we present a biometrics-based user authentication protocol in Chapter 4. A self-certificate-based user authenti-cation protocol will be described in Chapter 5. Finally, a conclusion is given in Chapter 6.
Chapter 2
Preliminaries
In this chapter, we first state several mathematical problems [43], including the discrete logarithm problem (DLP), the Diffie-Hellman problem (DHP), the elliptic curve discrete logarithm problem (ECDLP), and the computational Diffie-Hellman problem (CDHP). The LU decomposition [68] and secret sharing method [56] will be presented later. Next, we provide a detailed survey of various user authenti-cation protocols. The notations and their corresponding definitions used in this dissertation are listed in Table 2.1.
2.1
Mathematical problems
Now we introduce several mathematical difficult problems as follows.
Definition 1. The discrete logarithm problem (DLP) is defined as follows: given
a prime p, a generator g of Z∗
p, and an element β ∈ Zp∗, find the integer α,
0 ≤ α ≤ p − 2, such that gα ≡ β (mod p).
Definition 2. The Diffie-Hellman problem (DHP) is defined as follows: given
a prime p, a generator g of Z∗
p, and elements gc (mod p) and gs (mod p), find
gcs (mod p).
Table 2.1: Notations Symbol Definition
Ui User i
IDi User i’s or sensor node i’s identity
P Wi User i’s chosen password
T Mi User i’s iris template
(Si, Qi) User i’s or sensor node i’s private/public key pair
Key The sensor gateway-node’s private key
Ki,j The pair-wise key computed by the entity i and entity j
AK The authentication key composed of each user’s password KDC The key distribution center
s The KDC’s private key
Kpub The KDC’s public key
Ks The server’s secret key
SKi The session key computed by a user i and the server
COMMi The set of sensor nodes within the communication range of the user i
CIi User i’s certificate information generated by the KDC
n The number of users that could be supported by the system
T The timestamp
An×n A symmetric key matrix
h(·) A one-way hash function
ET Mi(·) An encryption function with the biometric template T Mi as the
en-cryption key [16, 59]
t A threshold value. At least t users are needed to reconstruct AK for authentication
f (x) A (t-1)-degreed polynomial, where f (x) = (AK + a1x + a2x2+ · · · +
at−1xt−1) mod q
ki A secret share computed by the server, where ki = f (IDi)
⊕ The exclusive-or (XOR) operation
We view G1 as an additive group.
Definition 3. The elliptic curve discrete logarithm problem (ECDLP) is defined
as follows: given Q, R ∈ G1, find an integer x ∈ Zq∗ such that R = xQ.
Definition 4. The computational Diffie-Hellman problem (CDHP) is defined as
follows: given (P, aP, bP ) ∈ G1 for a, b ∈ Zq∗, find abP ∈ G1.
2.2
LU decomposition
In the LU decomposition, an n × n matrix A is written as
A = L · U (2.1)
where L is a nonsingular lower triangular matrix, and U is a nonsingular upper triangular matrix.
We assume that aij = aji, for 1 ≤ i ≤ n and 1 ≤ j ≤ n. Since A is symmetric,
the product of the x-th row of matrix L and the y-th column of matrix U is as same as that of the y-th row of matrix L and the x-th column of matrix U.
For example, given A as follows:
A = 1 2 4 5 2 5 8 9 4 8 15 17 5 9 17 20 (2.2)
we perform elementary row operations to get the lower matrix L and upper matrix
U as follows: L = 1 0 0 0 2 1 0 0 4 0 −1 0 5 −1 −3 −3 and U = 1 2 4 5 0 1 0 −1 0 0 1 3 0 0 0 −1 (2.3)
Given x = 2 and y = 3, we can compute a23 and a32 as follows:
a23= LR(2) · UC(3) =
³
a32= LR(3) · UC(2) =
³
4 0 −1 0 ´·³ 2 1 0 0 ´T = 8 (2.5) Since matrix A is symmetric, a23 = a32. Note that LR(2) denotes the 2nd row
of matrix L and UC(3) denotes the 3rd column of matrix U.
2.3
Secret sharing method
The secret sharing method, was introduced by Shamir in 1979 [56]. Numerous researchers have investigated such methods since then. The goal of sharing a secret is to distribute a secret among a group of users, each of whom is allocated a share of the secret. In a secret sharing method there are one dealer and n users. The dealer gives each user a share of the secret in such a way that any group of t or more users can together reconstruct the secret but no group of less than t users can. Such a system is also called a (t, n)-threshold scheme.
Here we illustrate how the secret sharing method works. Consider a (t, n)-threshold scheme and a secret value K. The dealer randomly chooses a large prime
q, and selects a (t-1)-degreed polynomial f (x) = (a0+a1x+· · ·+at−1xt−1) mod q in
which a0 = K and a1, a2, . . . , at−1are randomly chosen from a uniform distribution
over the integers in [0, q). Next, the dealer computes the shares for individual users:
k1 = f (ID1), k2 = f (ID2), . . . , kn= f (IDn).
Given any subset of t of these ki values (together with their identities), the
users can find the coefficients of f (x) by interpolation, and then obtain the secret
K = f (0).
2.4
Related works
pro-tocols in wireless networks, including password-based user authentication, biometrics-based user authentication, and self-certificate-biometrics-based user authentication.
2.4.1
Password-based user authentication
In 1981, Lamport [33] proposed the first password authentication protocol for remote users over an insecure channel. Since then, several protocols [11, 12, 13, 15, 21, 22, 23, 25, 29, 31, 32, 37, 38, 39, 45, 48, 49, 57, 64, 65] have been proposed to improve security, efficiency, and functionality. Past experience has shown that constructing a secure user authentication protocol is not trivial because lots of proposed protocols were subsequently broken by well-known attacks [11, 21, 22, 23, 31, 32, 37, 45].
Traditionally, if a remote user wants to log into a server, he has to submit his identity and password to the server. On receiving the login request, the server first checks the validity of the identity and computes a one-way hash value of the received password, and then checks the computed value against the server’s verification table. Since this approach clearly incurs the risk of tampering and the cost of managing the table, several protocols [12, 13, 15, 25, 29, 38, 39, 48, 49, 57, 64, 65] have been proposed that do not depend on a verification table.
Due to the constrained resources in smart cards, the computation and commu-nication overhead must be low in practical implementation. Sun [57] proposed an efficient authentication protocol that adopts only simple hashing operations. In 2002, Chien et al. [13] proposed another authentication protocol that improves on Sun’s in two ways: it achieves mutual authentication and it allows users to choose their passwords freely.
must be encrypted when transmitted over the public network. They have to agree on a session key. Juang [25] proposed an authentication protocol that provides a key agreement function. In various e-commerce applications, user anonymity is also crucial. Das et al. [15] first proposed a dynamic identity-based authentication protocol that preserves user anonymity. However, Chien and Chen [12] pointed out that Das et al.’s protocol [15] fails to protect user anonymity.
In order to reduce the risk of single-point failures, Choi and Youn [14] proposed a novel data encryption and distribution approach based on LU decomposition in 2004. The protocol allows higher security and availability compared with the mir-roring protocol [19, 41, 44], and provides a solution for failures and malicious com-promises of storage nodes, client systems, and user account. Pathan et al. [48, 49] also proposed two bilateral authentication protocols based on LU decomposition. However, their protocols have several security weaknesses, including (1) they can-not resist replay attacks; (2) passwords could be revealed by the server; (3) they cannot preserve user anonymity; and (4) the server and users cannot agree on a session key.
Even though a number of user authentication protocols with smart cards have been proposed, these existing protocols cannot be directly applied to user authen-tication in WSNs due to the limited computational power and energy supply in sensor nodes. In order to achieve better performance, Wong et al. [63] proposed the first password-based user authentication protocol for WSNs. Their protocol is efficient since the protocol participants perform only a few hash operations. Unfortunately, Tseng et al. [58] showed that Wong et al.’s protocol suffers from vulnerabilities to both replay and forgery attacks.
2.4.2
Biometrics-based user authentication
Over the past few years, many researchers have paid a lot of attention to remote user authentication protocols by combining biometrics and passwords [5, 10, 18, 20, 26, 27, 28, 36, 40, 54]. The most commonly used biometric techniques are fingerprint, face, iris, voice, and palm print etc. In 2002, Lee et al. [36] proposed a fingerprint-based remote user authentication protocol using smart cards. In this protocol, the server stores two secret keys and public parameters in a user’s smart card. A user can access the smart card by his own fingerprint. However, Hsieh et al. [20] and Lin and Lai [40] pointed out that Lee et al.’s protocol [36] is vulnerable to impersonation attacks. Therefore, Lin and Lai [40] proposed an improved protocol to enhance the security, which allows users to choose and change their password freely.
In 2007, Khan and Zhang [26] demonstrated that Lin and Lai’s protocol [40] is susceptible to the server spoofing attack since Lin and Lai’s protocol [40] performs only unilateral authentication and there is no mutual authentication between user and remote server. Khan and Zhang [26] proposed an improved protocol which overcomes the weakness of Lin and Lai’s protocol [40].
Recently, Fan and Lin [17] proposed a remote user authentication protocol with privacy protection on biometrics. Their protocol fully preserves the privacy of the biometric data of each user while allowing the server to verify the correctness of the users’ biometric characteristics without knowing the exact values. However, in Fan and Lin’s protocol [17], if an attacker eavesdrops a message sent by a legitimate user and replays it to log to the system in a later session, the server needs to perform one asymmetric decryption operation, one symmetric encryption operation, and two symmetric decryption operations to detect the replay login
request. Therefore, dramatic increase in the number of replay login requests will certainly result in exhausting the server’s resources. Furthermore, their protocol cannot allow users to change their passwords. If a user’s password is compromised or a user wants to change the password for any reasons, there is no way to change the password. The only option for the user is to apply for a new card, which is an inefficient solution. In addition, compared with a regularly changed password, a fixed password is more vulnerable.
2.4.3
Self-certificate-based user authentication
In 2001, Perrig et al. [50] proposed security protocols for WSNs (SPINS), pro-viding important security primitives: authenticated and confidential communica-tion, and authenticated broadcast. They designed an authenticated routing pro-tocol and a secure node-to-node key agreement propro-tocol. User authentication in WSNs was proposed by Benenson et al. [7] in 2004. They investigated several se-curity issues in WSNs, including access control, and also introduced the notion of (t, n)-threshold authentication, which means the authentication succeeds if the user can be successfully authenticated with at least (n − t) out of n sensors. The rest of the sensors could be compromised or out of order. Thereafter, Benenson et al. [9] proposed the first solution to the user authentication problem in the presence of node-capture attacks. Their protocol is based on public-key cryptography, and is designed for a sensor node to authenticate the users.
In 2006, Banerjee and Mukhopadhyay [6] proposed authenticated querying in WSNs that is based on symmetric keys. The protocol can deal with queries involv-ing multiple sensors. However, identifyinvolv-ing the involved sensor nodes and floodinvolv-ing the access requests turn out to be very challenging for WSNs. Later, Wang and
Li [60] proposed a distributed user access control mechanism under a realistic adversary model for sensor networks. The protocol, which is based on an elliptic-curve cryptosystem (ECC), is divided into local authentication, which is conducted by the local sensors, that is, those sensors that are located physically close to the user, and remote authentication, which is based on the endorsement of the local sensors.
In order to achieve better performance, Wong et al. [63] proposed the first password-based user authentication protocol for WSNs. Compared with earlier works, their protocol is efficient since the protocol participants perform only a few hash operations. Unfortunately, Tseng et al. [58] showed that Wong et al.’s protocol suffers from vulnerabilities to both replay and forgery attacks and pro-posed an improved protocol. However, these protocols [58, 63] can only solve the access-control problem for individual sensor nodes, but not for the whole sensor networks.
Recently, Jiang et al. [24] proposed a user authentication protocol based on the self-certified-key cryptosystem [51] and used ECC to establish pair-wise keys between users and sensor nodes. However, the self-certified-key cryptosystem is not without security flaws. Lee and Kim [35] showed that the self-certified-key cryptosystem cannot provide explicit authentication for the public key. An attacker can produce a seemingly valid self-certified key with a third party’s identity. This bogus key cannot be distinguished from a valid one until successful communication with the real owner of the identity. To solve the bogus key problem, they introduced the self-certificate for the self-certified key. It is a user-generated certificate for the authentication of the self-certified key.
Chapter 3
Password-based user
authentication protocol
In this chapter, we propose two password-based user authentication protocols, namely protocol-I and protocol-II. The protocol-I is a password-based user authen-tication protocol using LU decomposition, which authenticates remote users and allows legitimate users to access network services over an open communication net-work. This protocol possesses many merits, including freely changeable passwords, mutual authentication, user anonymity, and session key agreement.
The protocol-II is a password-based user authentication protocol for WSNs, which allows legitimate users to query sensor data at any of the sensor node in an ad hoc manner and imposes very little computational overhead. Moreover, security of the proposed protocols is modelled and analyzed with Petri nets. Our analysis shows that the protocols can defend notorious attacks.
3.1
Protocol-I: Password-based user
authentica-tion protocol using LU decomposiauthentica-tion
phases: registration, login-and-authentication, and password-change phases.
3.1.1
Registration phase
Suppose a new user Ui with the identity IDi wants to register with a server for
remote-access services. Ui will take the following steps:
Step R1: Ui randomly chooses his password P Wi and sends the pair (IDi, h(P Wi)) to
the server in person or through an existing secure channel.
Step R2: Upon receiving the registration message, the server generates two random numbers xi, yi between 1 and n, and selects the xi-th row from matrix L
(denoted as LR(xi)), the xi-th column from matrix U (denoted as UC(xi)),
and the yi-th column from matrix U (denoted as UC(yi)). Next, the server
computes the pair (Kxiyi, θi) as follows: (⊕ means the exclusive-or operation)
Kxiyi = LR(xi) · UC(yi) (3.1)
θi = h(IDi⊕ Kxiyi) ⊕ h(P Wi) ⊕ h(Ks) (3.2)
Then the server issues a smart card containing (Kxiyi, θi, UC(xi), vi, h(·), g, p)
to Ui, where vi = h(Ks) ⊕ yi.
In the registration and password-change phases, in order to keep a user’s pass-word secret and resist insider attacks, the user transmits his passpass-word in hashed form, rather than as plain text. Note that Pathan et al.’s protocols [48, 49] make use of plain text for transmitting passwords. In addition, the system parameters g and p, where g is a generator of order q and p is a prime number which is divisible by q − 1, used for computing a session key, have to be embedded in the smart card for later use.
3.1.2
Login-and-authentication phase
When Ui wants to log in to the system, Ui first attaches the smart card and
inputs his password P W∗
i . The details are presented as follows.
Step L1: The smart card generates a random number r and computes the pair (Hi, Si)
as follows:
Hi = Kxiyi ⊕ h(r ⊕ T ) (3.3)
Si = θi⊕ h(P Wi∗) ⊕ r (3.4)
where T is the current timestamp. Next, the smart card generates a random number a and computes the pair (ri, Ri):
ri = ga mod p. (3.5)
Ri = h(θi⊕ ri) (3.6)
After that, the smart card encrypts (IDi, ri, UC(xi), vi, T ) with Ri and
com-putes Ci:
Ci = θi⊕ h(IDi⊕ Kxiyi) ⊕ h(P W
∗ i ) ⊕ Ri
= h(Ks) ⊕ Ri (3.7)
Finally, the smart card sends the login message Mi = (Ci, ERi(IDi, ri, UC(xi)
, vi, T ), Hi, Si, T ) to the server.
Step L2: Upon receiving the login request Mi, the server computes Ri = Ci⊕ h(Ks),
and decrypts ERi(IDi, ri, UC(xi), vi, T ) with Ri. Then the server checks the
validity of IDi and verifies whether the time interval (T0−T ) ≤ ∆T , where T0
delay. If so, the server computes (vi ⊕ h(Ks)), which is denoted as yi, and
computes the triple (Kyixi, t, r
0) as follows:
Kyixi = LR(yi) · UC(xi) (3.8)
t = h(IDi⊕ Kyixi) (3.9)
r0 = S
i⊕ T ⊕ h(Ks) ⊕ t (3.10)
After that, the server checks whether the equation holds as follows:
Kyixi ?
= Hi⊕ h(r0) (3.11)
If equation (3.11) holds, the server generates a random number b and com-putes rs:
rs= gb mod p. (3.12)
The server constructs the authenticated session key SKi:
SKi = rib = gab mod p. (3.13)
Finally, the server sends ERi(Kyixi ⊕ rs, ri+ 1, T00) to Ui.
Step L3: After receiving the message ERi(Kyixi⊕rs, ri+1, T
00), the new user U
idecrypts
the message to obtain Kyixi ⊕ rs, and verifies whether (T000 − T00) ≤ ∆T ,
where T000 is the current timestamp. If so, U
i checks whether decrypted data
contains the value ri+ 1. If so, Ui uses Kxiyi to compute rs as follows:
rs = (Kyixi⊕ rs) ⊕ Kxiyi (3.14)
Next, Ui generates the authenticated session key SKi as follows:
User i Server L1. Input P W∗ i Compute Hi = Kxiyi⊕ h(r ⊕ T ) Si= θi⊕ h(P W∗ i) ⊕ r ri = ga mod p Ri = h(θi⊕ ri) Encrypt (IDi, ri, UC(xi), vi, T ) with Ri Compute Ci = θi⊕ h(IDi⊕ Kxiyi) ⊕h(P W∗ i ) ⊕ Ri Send Mi= (Ci, ERi(IDi, ri, UC(xi) , vi, T ), Hi, Si, T )
to the server → L2. Receive Mi
Compute Ri = Ci⊕ h(Ks) Decrypt ERi(IDi, ri, UC(xi), vi, T ) Check IDi Verify (T0− T ) ≤ ∆T Compute yi= vi⊕ h(Ks) Kyixi = LR(yi) · UC(xi) t = h(IDi⊕ Kyixi) r0 = S i⊕ T ⊕ h(Ks) ⊕ t Verify Kyixi ? = Hi⊕ h(r0) Compute rs= gb mod p Construct SKi = rib = gab mod p L3. Receive ERi(Kyixi⊕ rs, ri+ 1, T00) ← Send ERi(Kyixi⊕ rs, ri+ 1, T00) Decrypt ERi(Kyixi ⊕ rs, ri+ 1, T00) Verify (T000− T00) ≤ ∆T Check ri+ 1 Compute rs= (Kyixi⊕ rs) ⊕ Kxiyi Construct SKi = rsa= gba= gab
Figure 3.1: The login-and-authentication phase of the password-based user au-thentication protocol using LU decomposition.
Then Ui uses SKi to communicate with the server. A high-level depiction of
the login-and-authentication phase in the proposed protocol is illustrated in Figure 3.1.
3.1.3
Password-change phase
When Ui wants to change his password P Wi to P Wi0, the following steps will
be performed.
Step P1: Ui sends the triple (IDi, h(P Wi), h(P Wi0)) to the server. As in the
registra-tion phase, these private data should be submitted in person or via a secure channel.
Step P2: Upon receiving the password-change message, the server computes θ0
i as fol-lows: θ0 i = θi⊕ h(P Wi) ⊕ h(P Wi0) = h(IDi⊕ Kxiyi) ⊕ h(P W 0 i) ⊕ h(Ks) (3.16)
Next, the server replaces θi with θ0i in the smart card.
As in the registration phase, the user has to transmit his password in hashed form in this phase to keep his password secret and withstand insider attacks.
3.2
Protocol-II: Password-based user
authenti-cation protocol for WSNs
In the proposed protocol, authorized users can access any of the sensor nodes in WSNs using mobile devices, such as PDAs, PCs, etc. Before issuing a query to a sensor node, a user has to register at the sensor gateway (GW) via a secure channel. Upon successful registration, the user can login to a nearest sensor login-node to retrieve sensor data. The proposed protocol is divided into three phases: registration, login-and-authentication, and password-change phases. Note that the registration and the password-change phases are performed via a secure channel.
3.2.1
Registration phase
Suppose a new user Ui with the identity IDi wants to register with a GW for
retrieving sensor data. Ui will take the following steps:
Step R1: Ui randomly chooses his password P Wi and sends the pair (IDi, h(P Wi)) to
the GW through a secure channel.
Step R2: Upon receiving the registration message, the GW stores the dataset (IDi, h(P Wi), T )
in its database. Then, the GW replies to the user successful registration. Fi-nally, the pair (IDi, T ) is then distributed to all the sensor nodes.
3.2.2
Login-and-authentication phase
When Ui wants to retrieve sensor data, Ui first inputs his/her password P Wi∗.
The details are presented as follows. Step L1: Ui computes A as follows:
A = h(h(P W∗
i) ⊕ T0) (3.17)
where T0 is the current timestamp. Next, U
i sends the triple (IDi, A, T0) to
a login-node.
Step L2: Upon receiving the login request (IDi, A, T0), the login-node first checks
whether IDi is in the list of datasets (IDi, T ). If not, the login-node then
sends REJ-LOGIN to Ui. Otherwise it computes C for the user:
C = h(A ⊕ T00) (3.18)
where T00is the current timestamp. Then, the login-node sends (ID
i, C, T00, T0)
Step L3: After receiving the message (IDi, C, T00, T0), the GW first checks whether
(IDi, T0) is in the database. If IDi is not in the database or (IDi, T0) is
already contained in the database, the GW sends REJ-LOGIN to the login-node. Otherwise, it checks whether the transmission delay is within the allowed time interval. If (T000− T00) ≥ ∆T or (T00− T0) ≥ ∆T , the GW sends
REJ-LOGIN to the login-node. Otherwise, it computes the pair (A∗, C∗) for
verification.
A∗ = h(h(P Wi) ⊕ T0) (3.19)
C∗ = h(A∗⊕ T00) (3.20)
The GW verifies if C∗ ?= C. If so, the GW stores T0in the database and sends
ACC-LOGIN to the login-node and the login-node also sends ACC-LOGIN to Ui. Otherwise, the GW sends REJ-LOGIN to the login-node. A high-level
depiction of the login-and-authentication phase in the proposed protocol is illustrated in Figure 3.2.
3.2.3
Password-change phase
When Ui wants to change his password P Wi to P Wi0, the following steps will
be performed.
Step P1: Ui sends the triple (IDi, h(P Wi), h(P Wi0)) to the GW. As in the registration
phase, these private data should be submitted in person or via a secure channel.
Step P2: Upon receiving the password-change message, the GW first checks whether (IDi, h(P Wi)) is correct. If IDi is not in its database or h(P Wi) is not
User i GW Login-node L1. Input P W∗ i A = h(h(P W∗ i) ⊕ T0) Send (IDi, A, T0)
to the login-node → L2. Receive (IDi, A, T0)
Check IDi C = h(A ⊕ T00)
Send (IDi, C, T00, T0)
L3. Receive (IDi, C, T00, T0) ← to the GW
Check IDi
Check transmission delay
A∗= h(h(P W i) ⊕ T0) C∗= h(A∗⊕ T00) C∗ ?= C Store T0 Send ACC-LOGIN to the login-node
Receive ACC-LOGIN ← and Ui → Receive ACC-LOGIN
Figure 3.2: The login-and-authentication phase of the password-based user au-thentication protocol for WSNs.
correct, the GW sends REJ-CHANGE to Ui. Otherwise, it updates the
cor-responding dataset with (IDi, h(P Wi0), T∗), where T∗ is the current
times-tamp. Then, the GW replies to Ui successful password change. Finally, the
new pair (IDi, T∗) is then distributed to all the sensor nodes.
3.3
Security analysis
In this section, we use Petri nets [53] to model and analyze the proposed proto-cols. Security properties of the protocols will be specified. We also show that our proposed protocols can resist several notorious attacks. In addition, we provide a comparative study with other authentication protocols.
3.3.1
Correctness
According to equation (3.10), we first derive the equation as follows:
r0 = S
= θi⊕ h(P Wi∗) ⊕ r ⊕ T ⊕ h(Ks) ⊕ t = h(IDi⊕ Kxiyi) ⊕ h(P Wi) ⊕ h(Ks) ⊕ h(P W ∗ i ) ⊕ r ⊕ T ⊕ h(Ks) ⊕ t = h(IDi⊕ Kxiyi) ⊕ r ⊕ T ⊕ t = h(IDi⊕ Kxiyi) ⊕ r ⊕ T ⊕ h(IDi⊕ Kyixi) = r ⊕ T (3.21)
Since the protocol-I employs LU decomposition, Kxiyi = Kyixi. That is, h(IDi⊕
Kxiyi) ⊕ h(IDi⊕ Kyixi) = 0. Therefore, r0 = r ⊕ T .
Using equation (3.21), we verify equation (3.11) as follows:
Kyixi = Hi⊕ h(r
0)
= Kxiyi ⊕ h(r ⊕ T ) ⊕ h(r ⊕ T )
= Kxiyi (3.22)
3.3.2
Petri net model
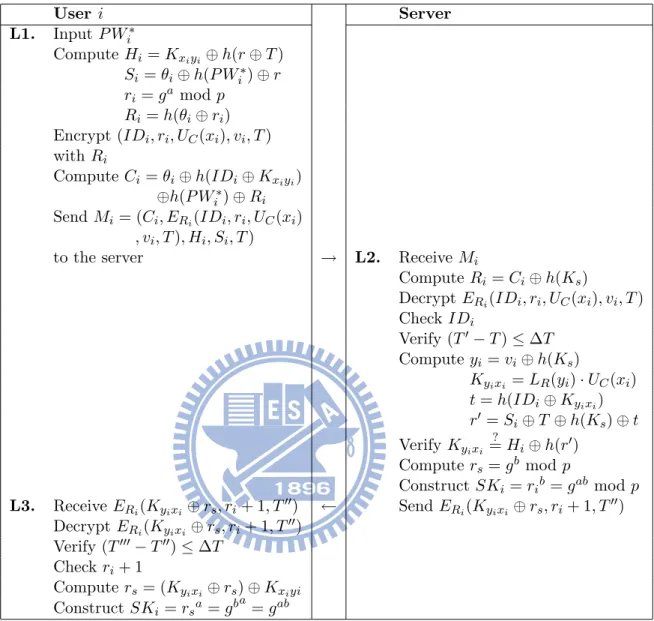
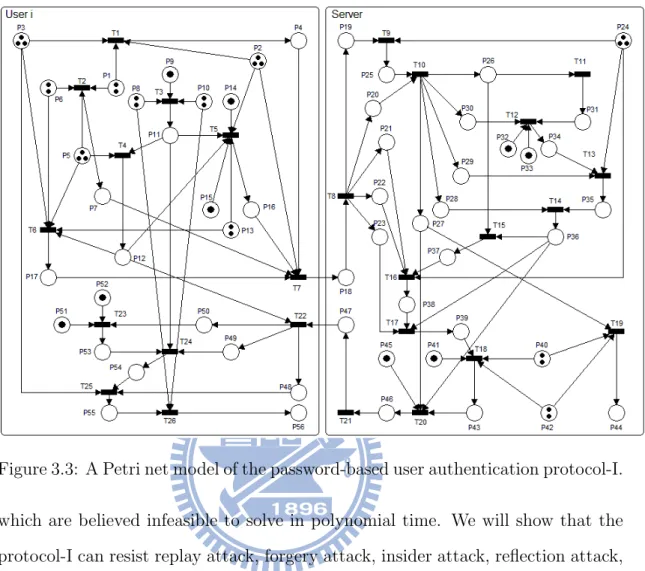
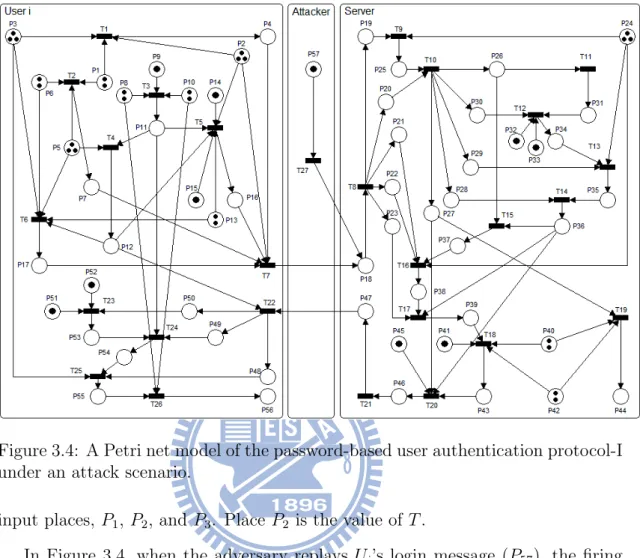
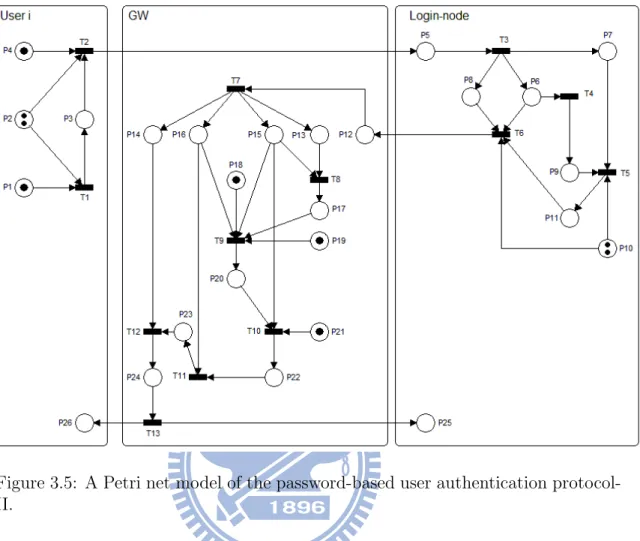
The Petri net models of the protocol-I and protocol-II are illustrated in ure 3.3 and Figure 3.5, respectively. We also construct attack scenarios in Fig-ure 3.4 and FigFig-ure 3.6 for the protocol-I and protocol-II, respectively. The defi-nitions of the places and transitions used in these models are listed in Table 3.1, Table 3.2, Table 3.3, and Table 3.4, respectively. We use the platform independent Petri net editor 2 (PIPE2) [1] to simulate the proposed protocols. The simulation results for the protocol-I and the protocol-II are bounded, which could be realized in hardware [52].
3.3.3
Security properties
Figure 3.3: A Petri net model of the password-based user authentication protocol-I. which are believed infeasible to solve in polynomial time. We will show that the protocol-I can resist replay attack, forgery attack, insider attack, reflection attack, and parallel session attack. We will also analyze the following security properties: anonymity, mutual authentication, forward secrecy, and known-key security. Theorem 1. The proposed protocol-I can resist a replay attack.
Proof. Assume an adversary eavesdrops the login message sent by Ui and uses
it to impersonate Ui when logging into the system in a later session. However, the
replay of Ui’s previous login message will be detected by the server since the user
has already bound the timestamp T into the login message according to equation (3.3), and the server will verify the validity of the timestamp T used by Ui. As
Figure 3.4: A Petri net model of the password-based user authentication protocol-I under an attack scenario.
input places, P1, P2, and P3. Place P2 is the value of T .
In Figure 3.4, when the adversary replays Ui’s login message (P57), the firing
sequence is given below: T27 → T8 → T9 → T10 → T11. However, there is a
dead-lock in the transition T12 since the server detects that the timestamp in the login
message is not fresh. Therefore, the adversary cannot replay the login message. However, there seems to be one potential security threat common to most existing timestamp-based user authentication protocols. That is, an adversary could imper-sonate a legitimate user by replaying that user’s previous login message within the allowed time interval ∆T . This threat can be solved by the additional requirement that T is not reused by Ui within ∆T . 2
Figure 3.5: A Petri net model of the password-based user authentication protocol-II.
Proof. If the adversary wants to impersonate Ui, he has to create a valid
login message (C∗ i, ER∗
i(IDi, r
∗
i, UC(xi), vi, T∗), Hi∗, Si∗, T∗), where T∗ is the current
timestamp. First he has to choose a random number r∗ and compute the pair
(H∗ i, Si∗) as follows. H∗ i = Kxiyi⊕ h(r ∗⊕ T∗) (3.23) S∗ i = θi⊕ h(P Wi) ⊕ r∗ (3.24)
As shown in Figure 3.3, computing Hi is defined in transition T1, which has three
input places, P1, P2, and P3. Place P3 is the value of Kxiyi. Computing Si is
Figure 3.6: A Petri net model of the password-based user authentication protocol-II under an attack scenario.
value of θi and place P6 is the value of P Wi∗.
Because having no idea about Kxiyi, θi, and P Wi, the adversary cannot forge a
valid login message and hence cannot launch a forgery attack. 2 Theorem 3. The proposed protocol-I can resist an insider attack.
Proof. In the protocol-I, when Ui wants to resigter with a server for
remote-access services, he has to submit (IDi, h(P Wi)) instead of (IDi, P Wi), as in Pathan
et al.’s protocols [48, 49]. Due to the employment of the one-way hash function h, it is considered practically impossible for the server to derive the user’s password
P Wi from the hashed value [55]. That is, even the server does not know P Wi.
Obviously, the protocol-I can prevent the insider attack. 2
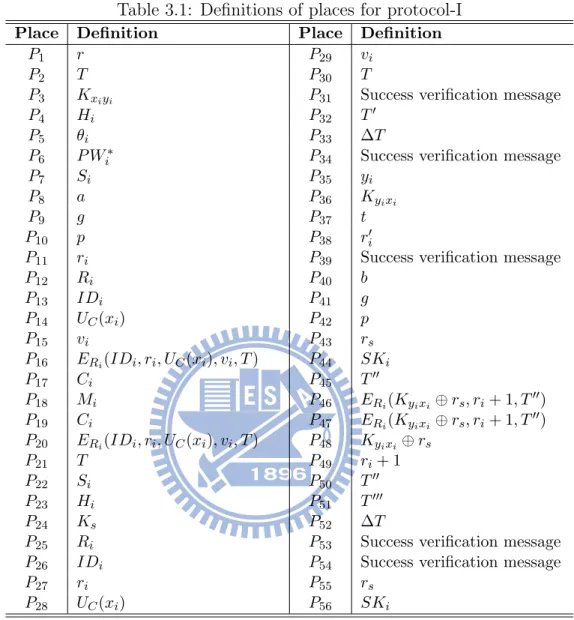
Table 3.1: Definitions of places for protocol-I
Place Definition Place Definition
P1 r P29 vi
P2 T P30 T
P3 Kxiyi P31 Success verification message
P4 Hi P32 T0
P5 θi P33 ∆T
P6 P Wi∗ P34 Success verification message
P7 Si P35 yi
P8 a P36 Kyixi
P9 g P37 t
P10 p P38 r0i
P11 ri P39 Success verification message
P12 Ri P40 b P13 IDi P41 g P14 UC(xi) P42 p P15 vi P43 rs P16 ERi(IDi, ri, UC(xi), vi, T ) P44 SKi P17 Ci P45 T00 P18 Mi P46 ERi(Kyixi⊕ rs, ri+ 1, T00) P19 Ci P47 ERi(Kyixi⊕ rs, ri+ 1, T00) P20 ERi(IDi, ri, UC(xi), vi, T ) P48 Kyixi ⊕ rs P21 T P49 ri+ 1 P22 Si P50 T00 P23 Hi P51 T000 P24 Ks P52 ∆T
P25 Ri P53 Success verification message
P26 IDi P54 Success verification message
P27 ri P55 rs
P28 UC(xi) P56 SKi
Proof. A reflection attack is one in which, when a user sends a login message
to a server, the adversary eavesdrops the message and sends it (or a modified version of the message) back to the user. In the proposed-I, the adversary cannot fool the server since he has to know the server’s secret key Ks in computing Ri,
Table 3.2: Definitions of transitions for protocol-I
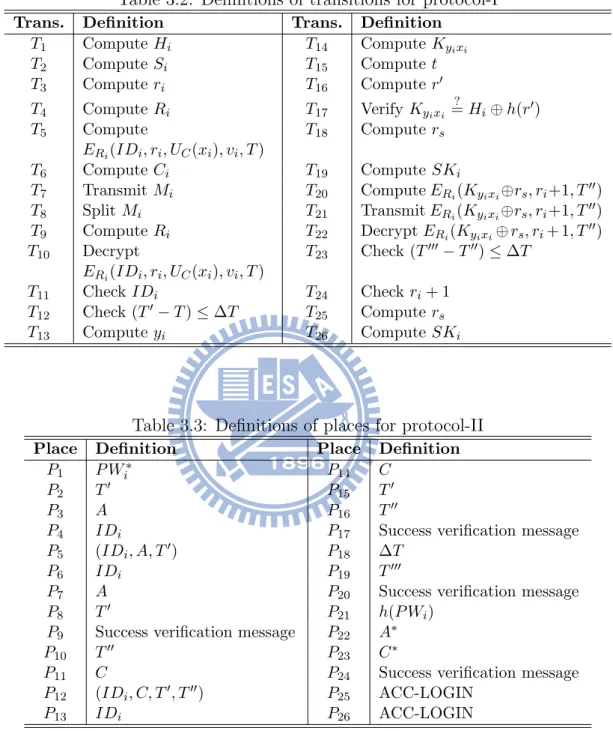
Trans. Definition Trans. Definition
T1 Compute Hi T14 Compute Kyixi T2 Compute Si T15 Compute t T3 Compute ri T16 Compute r0 T4 Compute Ri T17 Verify Kyixi ? = Hi⊕ h(r0) T5 Compute ERi(IDi, ri, UC(xi), vi, T ) T18 Compute rs T6 Compute Ci T19 Compute SKi T7 Transmit Mi T20 Compute ERi(Kyixi⊕rs, ri+1, T00) T8 Split Mi T21 Transmit ERi(Kyixi⊕rs, ri+1, T00) T9 Compute Ri T22 Decrypt ERi(Kyixi⊕ rs, ri+ 1, T00) T10 Decrypt ERi(IDi, ri, UC(xi), vi, T ) T23 Check (T000− T00) ≤ ∆T T11 Check IDi T24 Check ri+ 1 T12 Check (T0− T ) ≤ ∆T T25 Compute rs T13 Compute yi T26 Compute SKi
Table 3.3: Definitions of places for protocol-II
Place Definition Place Definition
P1 P Wi∗ P14 C
P2 T0 P15 T0
P3 A P16 T00
P4 IDi P17 Success verification message
P5 (IDi, A, T0) P18 ∆T
P6 IDi P19 T000
P7 A P20 Success verification message
P8 T0 P21 h(P Wi)
P9 Success verification message P22 A∗
P10 T00 P23 C∗
P11 C P24 Success verification message
P12 (IDi, C, T0, T00) P
25 ACC-LOGIN
P13 IDi P26 ACC-LOGIN
illustrated in Figure 3.3, computing Ri is defined in transition T9, which has two
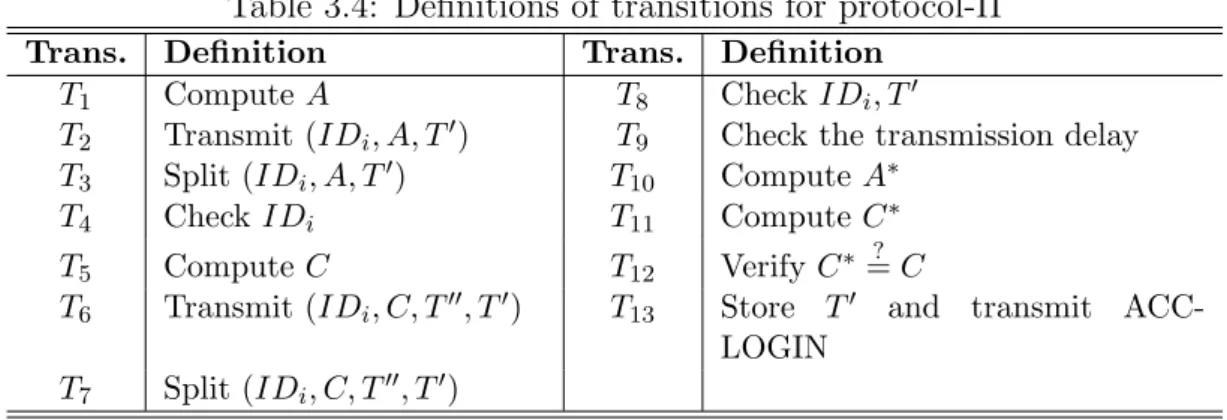
Table 3.4: Definitions of transitions for protocol-II
Trans. Definition Trans. Definition
T1 Compute A T8 Check IDi, T0
T2 Transmit (IDi, A, T0) T9 Check the transmission delay
T3 Split (IDi, A, T0) T10 Compute A∗
T4 Check IDi T11 Compute C∗
T5 Compute C T12 Verify C∗ ?= C
T6 Transmit (IDi, C, T00, T0) T
13 Store T0 and transmit
ACC-LOGIN
T7 Split (IDi, C, T00, T0)
that the protocol-I can withstand the reflect attack. 2
Theorem 5. The proposed protocol-I can resist a parallel-session attack.
Proof. In the protocol-I, an adversary cannot impersonate a legitimate user
by creating a valid login message in another on-going run from the honest run since the server’s response message ERi(Kyixi ⊕ rs, ri + 1, T00) is encrypted with
Ri, which is unknown to the adversary. Therefore, the protocol-I can resist the
parallel-session attack. 2
Theorem 6. The proposed protocol-I can provide user anonymity.
Proof. If an adversary eavesdrops the login message, he cannot extract the
user’s identity from the ciphertext ERi(IDi, ri, UC(xi), vi, T ) since it is encrypted
with Ri, which is unknown to the adversary. In addition, due to the use of the
nonce and the timestamp in the login phase, the login messages submitted to the server are different in the login sessions. As shown in Figure 3.3, computing
ERi(IDi, ri, UC(xi), vi, T ) is defined in transition T5, which has six places, P2, P11,
P12, P13, P14, and P15. Place P2 is the value of T and place P11 is the value of
ri = ga mod p. Hence, it is difficult for the adversary to discover a user’s identity.
Theorem 7. The proposed protocol-I can provide mutual authentication.
Proof. The protocol-I uses the Diffie-Hellman key exchange algorithm to achieve
mutual authentication between the server and a user. Ui and the server securely
exchange riand rsin the login and authentication phases, respectively. As a result,
the authenticated session key is established as follows:
SKi = rbi = rsa= gab mod p (3.25)
As illustrated in Figure 3.3, computing SKi is defined in transition T19 and T26,
which are computed by the server and Ui, respectively. Therefore, Ui and the
server can use the authenticated session key SKi in subsequent communications.
2
Theorem 8. The proposed protocol-I can provide perfect forward secrecy.
Proof. Perfect forward secrecy means that the disclosure of the long-term
se-cret key material (e.g., server’s sese-cret key Ks and user’s password P Wi) does not
compromise the secrecy of the agreed keys in earlier runs. In the protocol-I, perfect forward secrecy is ensured since the Diffie-Hellman key exchange algorithm is used to establish the authenticated session key gab. Even if the adversary knows the
server’s secret key Ks, he is only able to obtain ga and gb from earlier runs. As
shown in Figure 3.3, computing ri(= ga mod p) and rs(= gb mod p) is defined in
transition T3 and T18, respectively.
However, based on the difficulty of the discrete logarithm problem and the Diffie-Hellman problem, it is computationally infeasible to compute the authenti-cated session key gab from ga and gb. Thus, the protocol-I provides perfect forward
secrecy. 2
Proof. Known-key security means that the compromise of a session key will not
lead to further compromise of other secret keys or session keys. Even if a session key gab is revealed to an adversary, he still cannot derive other session keys since
they are generated from the random numbers ga0
and gb0
based on Diffie-Hellman key exchange algorithm. Hence, the protocol-I can achieve known-key security. 2 Now we will show that the protocol-II can resist replay attack, forgery attack, and insider attack.
Theorem 10. The proposed protocol-II can resist a replay attack.
Proof. Assume an adversary eavesdrops the login message sent by Ui and uses
it to impersonate Ui when logging into the system in a later session. However,
the replay of Ui’s previous login message will be detected by the server since the
user has already bound the timestamp T0 into the login message according to
equation (3.17), and the GW will checks whether (IDi, T0) exists in the database.
If (IDi, T0) is already in the database, it means that this user has already login to
this system at time T0. The GW then rejects the user’s login request. As shown
in Figure 3.5, computing A is defined in transition T1, which has two input places,
P1 and P2. Place P2 is the value of T0.
In Figure 3.6, when the adversary replays Ui’s login message (P27), the firing
sequence is given below: T14 → T3 → T4 → T5 → T6 → T7. However, there
is a deadlock in the transition T8 since the server detects that the timestamp in
the login message is not fresh. Therefore, the adversary cannot replay the login message. Hence, the attacker cannot launch a replay attack. 2
Theorem 11. The proposed protocol-II can resist a forgery attack.
Proof. In the protocol-II, even if the attacker gains the list stored in the sensor
in the sensor login-node. The hash values are useless to an attacker. In order to forge a login message, the attacker has to know the user’s password, due to equation (3.17). However, it is difficult to derive the user’s password from the hashed value A. It is considered practically impossible for an attacker to derive the user’s password from the hashed value [55]. Because having no idea about the user’s password, the adversary cannot forge a valid login message and hence cannot launch a forgery attack. 2
Theorem 12. The proposed protocol-II can resist an insider attack.
Proof. In the protocol-II, when Ui wants to resigter with a GW for retrieving
sensor data, he has to submit (IDi, h(P Wi)). Due to the employment of the
one-way hash function h, it is considered practically impossible for the GW to derive the user’s password P Wi from the hashed value [55]. That is, even the server does
not know P Wi. Obviously, the protocol-II can prevent the insider attack. 2
3.3.4
Functionality
We summarize the functionality of the proposed-I in this subsection. The crucial criteria in a user authentication protocol are listed below:
C1. Freely chosen password: A user can choose his password freely in the regis-tration phase.
C2. Mutual authentication: The server and a user can authenticate each other. C3. User anonymity: A user’s identity is protected when he logs into the system. No one knows the user’s identity except the server.
C4. Session key agreement: While mutual authentication is established between the server and a user, they can agree on a session key for use in subsequent com-munications.