IP
IP
IP
IP
Student Yu-Lung Lee
Advisor Chien-Chao Tseng
A Thesis
Submitted to College of Computer Science
National Chiao Tung University
in partial Fulfillment of the Requirements
for the Degree of
Master
in
Computer Science
July 2009
IP
IP
IP IP Address IP IP IP Address IP Address IP Address IP Address IP Address IP IP Address IP Address IP IP Address IP IP Address IP Address IP Address
IP Address MAC Address Port Number IP Address
IP Address IP Address IP
Address Authenticator
IP Management Server IP Address Authenticator IP Address traffic
Authenticator IP Management Server Dynamic Host Control Protocol (DHCP) IP Address
IP Management Server IP Address MAC Address IP Management Server IP Address Assignment Table IP Address
IP Address IP Address IP Address IP Address MAC Address
IP Management Server IP Assignment request
MAC Address IP Address IP
Address Assignment Table
802.1X Authenticator Authenticator IP Address MAC Address Port Number
Authenticator Supplicant State Table Supplicant State Table Authenticator IP Address
IP Address
Design and Implementation of an IP Management Scheme to
Enforce Legal Use of IP Addresses
Student Yu-Lung Lee Advisor Dr. Chien-Chao Tseng
Degree Program of Computer Science
National Chiao Tung University
Abstract
In this thesis, we propose an IP management scheme to enforce
the legal use of IP addresses in the IP network. The IP network uses IP
addresses as the identities of network devices. Therefore, each device
needs a unique IP address so that devices can communicate with one
another in the network. When two or more devices use the same IP
address in the same network domain, an IP Conflict problem occurs and
the host with a legal IP address may not be able to access the IP
network. Therefore, we propose an IP management scheme that can
resolve the IP Conflict problem by managing all IP addresses and
controlling the use of each IP address. As a consequence, it can not only
assure the access right of legal users but also block the illegal use of IP
addresses. Furthermore, it allows a device to configure its IP address
either statically or dynamically without registering the address
beforehand.
The basic idea of the proposed scheme is to bind users, IP
addresses, MAC addresses and port numbers dynamically so that we
can manage all IP addresses and control the use of each IP address
without a priori information on the bindings. Furthermore, in order to
resolve the IP conflict problem the proposed scheme will also block
illegal users at network entry points, namely Authenticators, which
could be situated at Ethernet switches or wireless access points.
The proposed scheme employs an IP Management Server to
management all IP addresses and augments Authenticators to allow
only the traffic from legal users with correct IP addresses. Furthermore,
the proposed scheme also adopts an extended Dynamic Host Control
Protocol (DHCP) for Authenticators to communicate with the IP
Management Server to offer the maximum flexibility in using IP
addresses.
The IP Management Server records the bindings of IP addresses
with both user accounts and MAC addresses in an IP Address
Assignment Table. The bindings between IP address and user accounts
could be statically or dynamically; that is, a user could either
pre-subscribe permanently or acquire dynamically an IP address when
needs. On the other hand, the binding between an IP address and a
MAC address is done dynamically by the IP Management Server when
the server receives an IP Assignment request from the MAC address
used by a legal user.
Different from the Authenticator in 802.1X, the Authenticator in
our scheme bind user accounts to IP addresses, MAC addresses and Port
numbers in their Supplicant State Tables. With Supplicant State Tables,
Authenticators can ensure legal use of IP addresses, protecting legal
users but blocking illegal users.
We have implemented the proposed scheme to verify its
effectiveness. The experimental results show that the proposed scheme
indeed can enforce legal use of IP addresses with maximum flexibility.
Keywords IP Networks DHCP IP Management Dynamic IP
... iii Abstract. ... v ... .viii ... ….ix ... xii ... 1 1.1 ... 1 1.2 ... 2 1.3 ... 3 ... 4 2.1 User Authentication... 4
2.1.1 Web Login + RADIUS ... 4
2.1.1.1 RADIUS ... 5 2.1.1.2 RADIUS ... 6 2.1.1.3 RADIUS ... 7 2.1.2 IEEE 802.1X ... 8 2.1.2.1 EAP ... 10 2.1.2.2 EAPOL ... 11 2.1.2.3 IEEE 802.1X ... 12 2.1.3 IEEE 802.11i... 14
2.2 Dynamic Host Configuration Protocol (DHCP) ... 15 2.2.1 DHCP Server Behavior... 16 2.2.2 DHCP Client Behavior ... 17 2.2.3 DHCP ... 17 2.2.4 DHCP ... 19 ... 22 3.1 ... 22
3.2 IP/MAC Binding on DHCP Server ... 22
3.3 IP/MAC Binding on Switch or AP... 23
3.4 NCTU Dormitory Network Management System... 24
3.5 IEEE 802.1X with IP Address Management ... 26
3.6 ... 27
3.7 ... 28
IP IP ... 30
4.1 ... 30
4.1.1 Supplicant State Table ... 32
4.1.2 IP Address Assignment Table... 34
4.1.3 Dynamic IP Assignment Mechanism ... 36
4.1.4 Extended DHCP Message... 39
4.2 Analysis of Proposed Scheme... 40
4.2.1 IP Address Assignment and Access Control... 41
4.2.1.1.1 Static IP Address with Pre-subscribed... 41
4.2.1.1.2 Static IP Address without Pre-subscribed... 43
4.2.1.1.3 Static conflicting IP Address with Non-subscribed ... 45
4.2.1.1.4 Static Non-conflicting IP Address with Non-subscribed... 48
4.2.1.2 Dynamic IP Address Acquisition... 50
4.2.1.2.1 Pre-subscribed IP Address ... 50 4.2.1.2.2 Non-subscribed IP Address... 53 4.2.2 IP Address Releasing... 55 4.3 ... 57 IP IP ... 58 5.1 ... 58 5.2 ... 59 5.3 User ... 60 5.4 Supplicant ... 61 5.5 Authenticator ... 62 5.6 DHCP Server ... 65 ... 68 6.1 ... 68 6.2 ... 70 ... 71
Figure 2-1 Web Login for User Authenticator ... 5
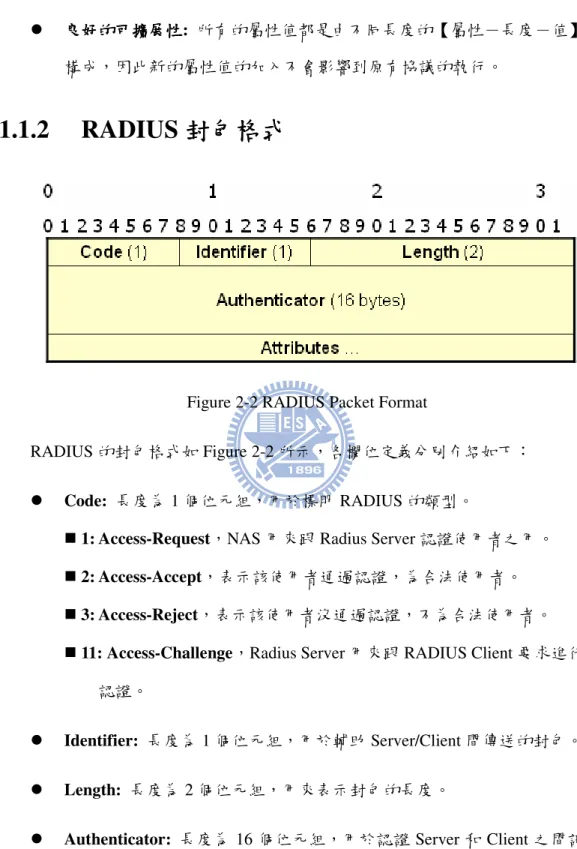
Figure 2-2 RADIUS Packet Format ... 6
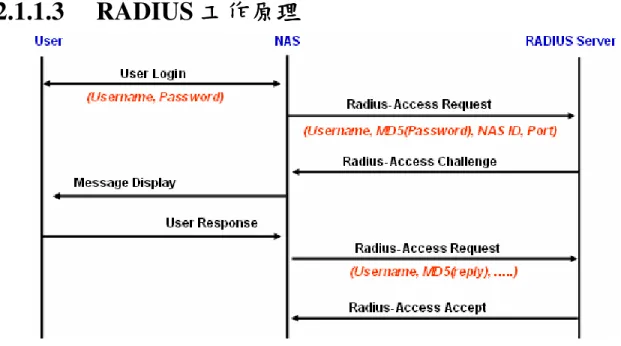
Figure 2-3 RADIUS Authentication Flow ... 7
Figure 2-4 IEEE 802.1X Authentication Flow... 9
Figure 2-5 EAP Packet Format... 10
Figure 2-6 EAPOL Packet Format...11
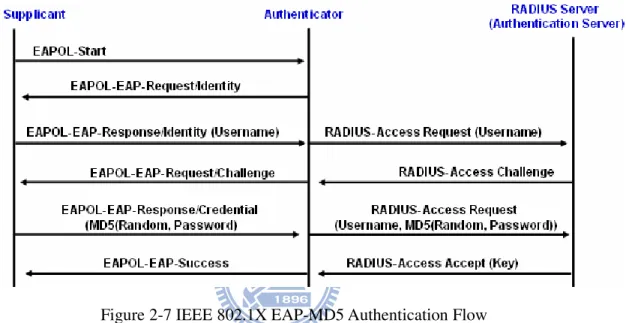
Figure 2-7 IEEE 802.1X EAP-MD5 Authentication Flow ... 13
Figure 2-8 IEEE 802.11i Authentication Flow... 15
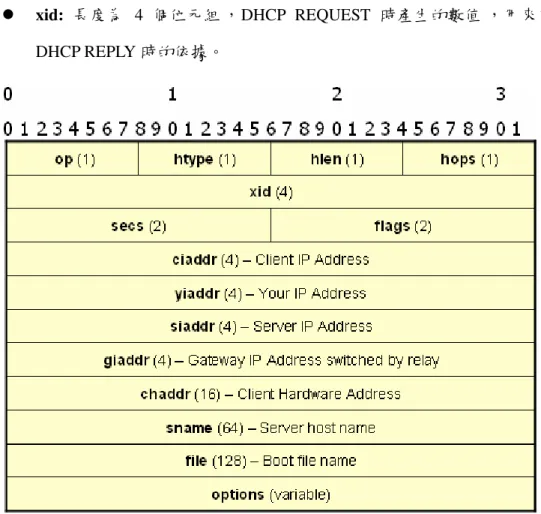
Figure 2-9 DHCP Packet Format... 18
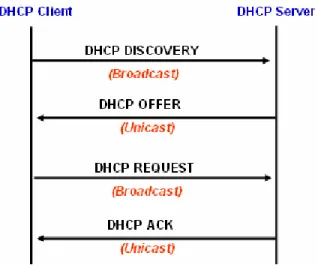
Figure 2-10 DHCP Packet Flow... 20
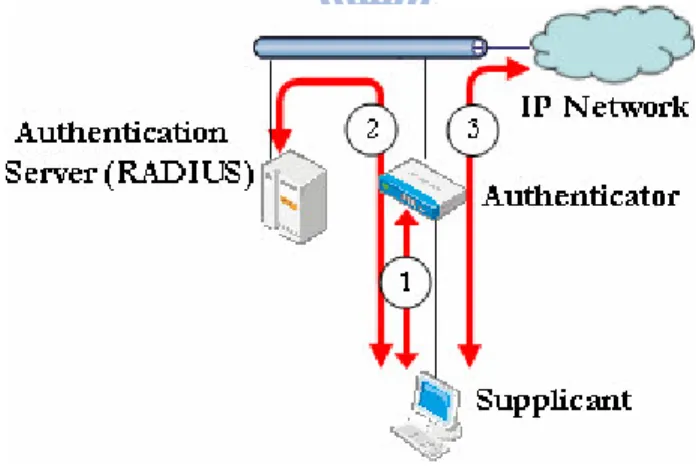
Figure 3-1 IP/MAC Address Binding ( [22] ) ... 22
Figure 3-2 NCTU Dormitory Network IP Address Apply Flow ... 25
Figure 3-3 IEEE 802.1X with IP Address Management Scheme... 26
Figure 3-4 ( [24] )... 27
Figure 4-1 IP Management Scheme concept overview ... 32
Figure 4-2 Supplicant State Table on Authenticator... 32
Figure 4-4 IP Management Protocol with Extended DHCP Scheme ... 37
Figure 4-5 Extended DHCP Message Format... 39
Figure 4-6 Static IP Address with Pre-subscribed IP Address... 42
Figure 4-7 Static IP Address without Pre-subscribed IP Address... 44
Figure 4-8 Static conflicting IP Address with Non-subscribed IP Address .... 46
Figure 4-9 Static Non-conflicting IP Address with Non-subscribed IP Address ... 49
Figure 4-10 User acquires subscribed IP Address with Dynamic IP Address Acquisition... 51
Figure 4-11 User acquires IP Address with Dynamic IP Address Acquisition 53 Figure 4-12 IP Address Releasing ... 56
Figure 5-1 System architecture of proposed scheme implementation... 58
Figure 5-2 Network Environment of proposed scheme implementation... 59
Figure 5-3 User Account Apply Flow... 60
Figure 5-4 Supplicant Login Flow... 61 Figure 5-5 Authenticator System Flow of proposed scheme implementation 63 Figure 5-6 DHCP Server System Flow of proposed scheme implementation 66
1.1
(Internet)
(network device) e-mail Skype IP Network IP Address ID (network domain) IP Address IP Address IP Address IP Address IP IP Address IP Address Dynamic Host Configuration Protocol (DHCP)[1] Server IP
Address IP Address
IP Address
(static configuration) (dynamic acquisition) IP Address
IP Address
1.2
IP Network IP Address IP Address IP Address IP Address IP Address : IP Address Routable IP Address IP Address IP Address IP Address IP Address IP Address IP Address IP Address IP Address IP Address
IP Address
IP Address IP
Address
1.3
IP Network MAC Address
IP Network IP Address
IP Address IP Address
IP Address MAC Address IP Network IP Address - Dynamic Host Configuration Protocol
(DHCP) IP Address IP Address
IP Address
2.1 User Authentication
2.1.1 Web Login + RADIUS
Web Login + Remote Authentication Dial In User Service (RADIUS)[2] Figure 2-1
Web Server
RADIUS Server RADIUS protocol Web Server Web Server
RADIUS protocol
Figure 2-1 Web Login for User Authenticator
2.1.1.1 RADIUS
RADIUS RFC2865[2] RFC2866[3] (network entrance) (authentication server) (authentication) (authorization) (accounting) User Datagram Protocol (UDP)[4] Port 1812 Port 1813
Client/Server : Network Access Server (NAS )
RADIUS Server Client RADIUS
Server RADIUS Server
: (Shared Secret Key) Client/Server
Client/Server
:
2.1.1.2 RADIUS
Figure 2-2 RADIUS Packet Format RADIUS Figure 2-2
Code: 1 RADIUS
1: Access-Request NAS Radius Server
2: Access-Accept 3: Access-Reject
11: Access-Challenge Radius Server RADIUS Client
Identifier: 1 Server/Client
Length: 2
Attributes: Type Length Value Type [5]
1: User-Name Length >=3
2: User-Password Length 18-130
4: NAS-IP-Address Length 6 NAS IP Address
8: Framed-IP-Address Length 6 IP Address
18: Reply-Message Length >=3 RADIUS Client
26: Vendor-Specific Length >=7
2.1.1.3 RADIUS
Figure 2-3 RADIUS Authentication Flow
Figure 2-3 RADIUS Authentication Flow RADIUS
NAS NAS UDP/IP
Access-Request RADIUS Message
IP Address RADIUS Server
RADIUS Server Access-Reject NAS Message Type18 Reply-Message
NAS NAS RADIUS Server
RADIUS Server Access-Accept NAS IP Address NAS [7]
2.1.2 IEEE 802.1X
IEEE 802.1X[8]
(Port-Based Network Access Control)
Virtual Local Area Network (VLAN)[9] IEEE 802.1X
IEEE 802.1X Extensible Authentication Protocol over LAN
(EAPOL) [10]
(Port-Level Authentication)
RADIUS IEEE 802.1X Supplicant
Authenticator Authentication Server [11]
Supplicant: Authenticator
Authenticator Supplicant IEEE 802.1X Microsoft Windows XP [12]
Authenticator: Supplicant Supplicant Supplicant Authentication Server Authenticator Supplicant Authentication Server
Authenticator Supplicant
Authentication Server: Supplicant
Authenticator Supplicant
Authentication Server Authenticator
Supplicant Authenticator
Figure 2-4 IEEE 802.1X Authentication Flow
Figure 2-4 IEEE 802.1X Authentication Flow Supplicant Authenticator ( ) Authenticator Supplicant
Authentication Server ( )
Authenticator Supplicant Authenticator ( ) Supplicant traffic Authenticator
IEEE 802.1X IEEE (EAP Extensible Authentication Protocol)[13] EAP
(PPP Point-to-Point Protocol)[14]
EAP PPP
IEEE 802.1X EAP (EAPOL EAP over LAN) EAP
2.1.2.1 EAP
IEEE 802.1X EAP PPP
EAP Figure 2-5 [15]
Figure 2-5 EAP Packet Format
Packet Code: 1 EAP
1: EAP Request
2: EAP Response
3: EAP Success
4: EAP Failure
Length: 2 EAP
EAP Type: 1 EAP EAP Type
0x01: Identity 0x02: Notification
0x03: Nak (Response Only) 0x04: MD5-Challenge
0x05: One-Time Password (OTP) 0x06: Generic Token Card
0x07: Transport Level Security (TLS)
2.1.2.2 EAPOL
EAPOL IP IEEE 802.1X
7.6 EAP EAPOL
Authenticator Supplicant EAPOL Authenticator Authenticator Ethernet Type 0x888E EAPOL
EAPOL Figure 2-6 [15]
Protocol Version: 1 IEEE 802.1X 0x01
Packet Type: 1 EAPOL EAP
EAPOL
0x00: EAP-Packet EAP Packet Body
Length Packet Body Packet Body EAP
0x01: EAPOL-Start EAPOL EAP
Packet Length 0
0x02: EAPOL-LogOff EAPOL EAP
Packet Length 0
0x03: EAPOL- Key EAPOL Key
EAP Packet Length 0
Packet Body Length: 2 Packet Body
Packet Type 0x00 Packet Length 0
Packet Body: Packet Type 0x00 EAP
2.1.2.3 IEEE 802.1X
IEEE 802.1X Supplicant Authenticator EAPOL EAP Authenticator Authentication Server
EAP-MD5 EAP-TLS[16] EAP-TTLS[17] EAP-AKA[18]
EAP-MD5
Figure 2-7 EAP-MD5
Figure 2-7 IEEE 802.1X EAP-MD5 Authentication Flow
Supplicant Authenticator EAPOL-Start IEEE 802.1X
Authenticator Supplicant EAPOL-EAP-Request/Identity Supplicant Username Authenticator
Supplicant Username EAPOL-EAP-Response/Identity Authenticator
Authenticator EAPOL-EAP-Response/Identity RADIUS Access-Request Authentication Server
Authentication Server Challenge EAP-Request/ MD5-Challenge RADIUS Access-Challenge Authenticator Authenticator EAPOL-EAP-Request/MD5-Challenge
Supplicant Supplicant
Supplicant EAPOL-EAP-Request/MD5-Challenge
Challenge MD5 Challenged-Password EAPoL-EAP-Response/MD5-Challenge Authenticator Authenticator Challenge Challenged Password Username
RADIUS Access-Request Authentication Server Authentication Server
Authentication Server MD5 Supplicant RADIUS Access-Accept RADIUS Access-Reject Authenticator
Authenticator Authentication Server
EAPOL-EAP Success EAPOL-EAP Failure Supplicant
2.1.3 IEEE 802.11i
IEEE 802.11i[19] Robust
Security Network (RSN) RSN
IEEE 802.1X EAPOL
Integrity Protocol (TKIP) Advanced Encryption Standard (AES) IEEE 802.11i IEEE 802.1X EAPOL-Key
(4-Way Pairwise-Key Handshaking and Two-Way Group-Key Handshaking)
Figure 2-8 IEEE 802.11i Authentication Flow
Figure 2-8 IEEE 802.11i Authentication Flow STA IEEE 802.1X STA AP Pairwise Master Key (PMK) 4-way handshake Pairwise Transient Key Security Association (PTKSA) PTKSA Pairwise Transient Key (PTK) STA MAC Address AP MAC Address
STA AP PTKSA
2.2
Dynamic Host Configuration Protocol (DHCP)
IP Network IP Address
IP Address Dynamic Host Configuration Protocol (DHCP )[1] IP Address
IP Address
(DHCP Server) (DHCP Client) DHCP Server IP
Network DHCP Client DHCP DHCP Client DHCP DHCP Server IP “ ” DHCP Server DHCP Client
2.2.1 DHCP Server Behavior
DHCP Server : DHCP DISCOVER: DHCP Client IP Address IP AddressDHCP REQUEST: DHCP OFFER DHCP Client
IP DHCP Client
DHCP DECLINE: DHCP Client DHCP Server IP
Address DHCP
Server DHCP OFFER DHCP DISCOVER IP Address
DHCP RELEASE: IP Address DHCP Client
IP Address DHCP Client DHCP Server DHCP Server IP Address
Option Unicast DHPC ACK DHCP Client
2.2.2 DHCP Client Behavior
DHCP Client
DHCP OFFER: DHCP Server Unicast DHCP Client
DHCP DISCOVER IP Address
DHCP ACK: DHCP Server DHCP Client DHCP REQUEST
DHCP INFORM Server Identifier IP Address DHCP Client
DHCP NACK: DHCP Server DHCP Client Client
DHCP DISCOVER IP Address [20]
2.2.3 DHCP
DHCP Figure 2-9
op: 1 DHCP Client DHCP Server
1 2
htype: 1 Ethernet 1
hlen: 1 Ethernet 6
hops: 1
xid: 4 DHCP REQUEST DHCP REPLY
Figure 2-9 DHCP Packet Format
flags: 2 bit 1 DHCP Server
Broadcast DHCP Client
ciaddr: 4 DHCP Client IP
Address
yiaddr: 4 DHCP Server DHCP Client
DHCP OFFER DHCP ACK DHCP Client IP Address
Server DHCP OFFER DHCP ACK DHCP NACK Server IP Address
giaddr: 4 DHCP
Relay Agent IP Address 0
chaddr: 16 DHCP Client (MAC
Address)
sname: 64 DHCP Server 0x00
file: 128 DHCP Client
Trivial File Transfer Protocol (TFTP)[21]
options: (Vendor-Specific Area)
( Netmask Gateway DNS )
2.2.4 DHCP
Figure 2-10 DHCP DHCP Client DHCP DHCP Client DHCP Server : DHCP Client IPAddress DHCP Client Broadcast DHCP DISCOVER DHCP Server
DHCP Server DHCP Client DHCP DISCOVER DHCP Server DHCP OFFER
DHCP Client ( IP Address ) Unicast DHCP Client
Figure 2-10 DHCP Packet Flow
DHCP Client DHCP Server DHCP OFFER DHCP Client DHCP Server DHCP Server IP Address DHCP REQUEST Server Identifier Broadcast
DHCP Server DHCP Client DHCP REQUEST Server Identifier IP Address
DHCP Server DHCP ACK DHCP Client DHCP ACK DHCP OFFER
DHCP Client DHCP ACK DHCP Client IP Address
DHCP
DHCP Client IP Address Unicast DHCP REQUEST
IP Address Request IP Address DHCP Server IP Address Server Identifier
DHCP REQUEST DHCP Server DHCP Client DHPC ACK DHCP NAK
3.1
IP Network IP Address ID IP Address IP Address IP Address IP3.2 IP/MAC Binding on DHCP Server
Figure 3-1 IP/MAC Address Binding ( [22] )
Figure 3-1 IP/MAC Address Binding IP Address MAC
Address IP Address
IP Address IP IP
Address
DHCP Server IP Address IP & MAC Binding DHCP Server DHCP Server IP Address
Address IP Address IP Address IP Address : MAC Address IP Address IP Address IP Address IP Address Switch/AP IP Address IP Address
MAC Address IP Address IP/MAC Address Binding rule IP Address
3.3 IP/MAC Binding on Switch or AP
Figure 3-1 Switch/AP Supplicant
IP & MAC Binding Switch/AP Switch/AP IP Address MAC Address MAC Address IP Address
Address Switch/AP IP Address Switch/AP IP Address : MAC Address IP Address IP Address IP Address
IP Address MAC Address
IP Address MAC Address IP Address
3.4
NCTU Dormitory Network Management System
Figure 3-2 [23] IP Address
IP Address MAC Address IP Address
IP Address
Server, DNS) IP Address
Figure 3-2 NCTU Dormitory Network IP Address Apply Flow : IP Address IP Address IP Address MAC Address IP Address IP Address IP Address Switch/AP IP Address IP Address
IP Address MAC Address
IP Address MAC Address IP Address
3.5 IEEE 802.1X with IP Address Management
Figure 3-3 IEEE 802.1X with IP Address Management Scheme Figure 3-3 IEEE 802.1X with IP Address Management Scheme
Supplicant IEEE 802.1X
Radius Server Supplicant IP Address Radius Protocol Access Accept Authenticator Authenticator
IP Address Supplicant IP Address Supplicant [7]
:
Supplicant IP Address IP Address
3.6
Figure 3-4 ( [24] )
DHCP IP Address IP
Address IP Address IP Address
MAC Address IP Address
Figure 3-4 IP Address MAC Address Simple Network Management Protocol (SNMP) Layer 3 Switch Layer 3 Switch
Access Control List (ACL) IP Address MAC Address
: IP Address IP Address IP Address IP Address IP Address IP Address
MAC Address IP Address
MAC Address IP Address MAC Address
3.7
IP Address
IP Address IP Address
IP Address MAC Address IP Address MAC Address
IP
IP
4.1
IP : IP Address IP Address IP Address IP Address : IP Address : IP Address IP Address IP Address IP Address IP Address IP Address IP AddressAuthenticator IP Management Server Table IP Address IP Address
Supplicant State Table: Authenticator Supplicant State
Table Authenticator Supplicant
IP Address Assignment Table: IP Management Server IP
Address Assignment Table Authenticator Supplicant IP Address
Dynamic IP assignment mechanism
Dynamic IP assignment Authenticator IP Management Server IP Management Protocol IP Address
Figure 4-1 concept overview Supplicant Authenticator Authenticator Supplicant State Table
Authenticator Supplicant IP Management Server IP Address Assignment Table
Authenticator Supplicant IP Address Supplicant Authenticator Authentication Server Authenticator
Supplicant User Account User Account IP Management Protocol
Figure 4-1 IP Management Scheme concept overview
4.1.1 Supplicant State Table
Figure 4-2 Supplicant State Table on Authenticator Authenticator Supplicant
Authenticator Supplicant
Authenticator Supplicant Supplicant Authenticator
User Account:
Table User Account Supplicant User Account
IP Management Server Supplicant User Authentication Table
IP Address:
Table IP Address Supplicant IP Address
Supplicant IP
Management Server Supplicant IP Address
MAC Address:
Table MAC Address Supplicant MAC Address
Supplicant Supplicant
Authenticator
Port:
Port Supplicant
Pairwise Transient Key Security Association (PTKSA) Supplicant Supplicant Authenticator
Wired Port Supplicant Authenticator Port Number; Wireless Port Supplicant Authenticator Four Way Handshake PTKSA
Supplicant
Table Status Supplicant Supplicant Supplicant
Status
Connected: Supplicant Authenticator
Supplicant Authenticator
Auth: Supplicant Authenticator
IP Address Supplicant Authenticator
Static: Supplicant Static IP Address
Authenticator IP
Address Supplicant IP Address
Dynamic: Supplicant Authenticator
Supplicant IP Address
4.1.2 IP Address Assignment Table
Authenticator Supplicant IP Address
IP Management Server ,
Supplicant IP Address , IP Management Server IP Address
IP Address Assignment Table static dynamic static
Table dynamic IP Address Supplicant IP Address
Table
Figure 4-3 IP Address Assignment Table on IP Management Server Figure 4-3 IP Management Server IP Address Assignment Table
User Account:
Table User Account
Authentication Server
Supplicant IP Address ;
IP Address Supplicant
IP Address:
Table IP Address Supplicant
IP Address Supplicant IP Address ; IP Address Supplicant IP Address
MAC Address:
MAC Address
Status:
Table Status Supplicant IP Address Supplicant IP Address Supplicant IP Address Release
; IP Management Server IP
Address Status
Inactive: static Supplicant
IP Address Authenticator
Subscribed: static Supplicant
IP Address Authenticator IP Address
Non-Subscribed: dynamic Supplicant
IP Address IP
Management Server IP Address
4.1.3 Dynamic IP Assignment Mechanism
Dynamic IP Assignment Mechanism DHCP Message Format Authenticator IP Management Server IP Management Protocol
DHCP Server IP Management Server
Protocol IP Management Protocol User Account Authenticator User Account Supplicant State Table
Figure 4-4 IP Management Protocol with Extended DHCP Scheme
Supplicant Authenticator Authenticator Supplicant Status Table Supplicant MAC Address Supplicant
Authenticator Wired Port Supplicant Authenticator Port Number; Wireless Port Supplicant Authenticator 4-Way Handshake PTKSA
User Authenticator Supplicant Supplicant ; Authenticator Supplicant
Static IP Address configuration Dynamic IP Address acquisition Authenticator Supplicant
IP Address Supplicant Static IP Address configuration; Supplicant DHCP DHCP DISCOVERY DHCP REQUEST Supplicant Dynamic IP Address acquisition
Supplicant Authenticator
Authenticator Supplicant IP Address MAC Address DHCP Message DHCP DISCOVERY DHCP REQUEST DHCP Server Supplicant Static IP Address configuration
IP Address Supplicant Static IP Address; Supplicant Dynamic IP Address acquisition IP Address “0.0.0.0” DHCP Server DHCP DISCOVERY DHCP REQUEST IP Address MAC Address IP Address Assignment Table
Supplicant IP Address Authenticator Supplicant IP Address IP Address IP Address; Supplicant
IP Address IP Address “0.0.0.0”
Authenticator DHCP Server DHCP Message Client IP Address Supplicant IP Address Supplicant State Table IP Address MAC Address Port Supplicant
4.1.4 Extended DHCP Message
Figure 4-5 DHCP Message Format
“ciaddr” “yiaddr” “chaddr” options “uaname”
Authenticator DHCP Server :
Figure 4-5 Extended DHCP Message Format
ciaddr: DHCP Client IP Address
Supplicant IP Address
yiaddr: DHCP Client DHCP Client
IP Address DHCP Server IP Address Assignment Table Supplicant IP Address
DHCP OFFER DHCP ACK
chaddr: DHCP Client Hardware Address
Supplicant Hardware Address
uaname: Supplicant User Account
4.2 Analysis of Proposed Scheme
DHCP Message Format IP Address Authenticator Supplicant
IP Address Assignment and Access Control
Static IP Address configuration Authenticator:
IP Address IP Address IP Address IP Address IP Address IP Address IP Address IP Address
Dynamic IP Address acquisition Authenticator:
Supplicant DHCP Dynamic IP Address Authenticator
IP Address
Supplicant DHCP Dynamic IP Address Authenticator
IP Address
IP Address Releasing
4.2.1 IP Address Assignment and Access Control
Authenticator IP Address
Static IP Address configuration Dynamic IP Address acquisition
4.2.1.1 Static IP Address Configuration
Authenticator Static IP Address configuration IP Address Static IP Address
4.2.1.1.1 Static IP Address with Pre-subscribed
IP Address IP Address Supplicant
Figure 4-6 Supplicant IP Address
Supplicant Authenticator Authenticator Supplicant Authentication Server
Authenticator Supplicant Authenticator Supplicant Supplicant IP Address Authenticator Supplicant IP Address
Figure 4-6 Static IP Address with Pre-subscribed IP Address
Authenticator DHCP REQUEST DHCP Server Supplicant IP Address MAC Address DHCP
Message “ciaddr” “chaddr” “uaname”
DHCP Server DHCP DISCOVERY DHCP Server DHCP Message “uaname” “chaddr” Supplicant
MAC Address IP Address Assignment Table Supplicant IP Address
Supplicant IP Address
IP Address Assignment Table Supplicant
IP Address DHCP Message “ciaddr” IP Address DHCP Server Status
Subscribed “chaddr” MAC Address MAC Address IP Address DHCP ACK “yiaddr”
Authenticator
Authenticator DHCP ACK “yiaddr”
DHCP REQUEST “ciaddr” “yiaddr” Supplicant IP Address
“yiaddr” IP Address Supplicant State Table Supplicant IP Address Status Static
Supplicant traffic
4.2.1.1.2
Static IP Address without Pre-subscribed
IP Address Supplicant Static IP Address IP Address
Figure 4-7 Supplicant IP Address
IP Address Message :
Supplicant Authenticator Authenticator Supplicant Authentication Server
Figure 4-7 Static IP Address without Pre-subscribed IP Address Authenticator Supplicant Authenticator Supplicant Supplicant IP Address Authenticator Supplicant IP Address
Authenticator DHCP REQUEST DHCP Server Supplicant IP Address MAC Address DHCP Message “ciaddr” “chaddr”
“uaname”
DHCP Server DHCP DISCOVERY DHCP Server DHCP Message “uaname” “chaddr” Supplicant
MAC Address IP Address Assignment Table Supplicant IP Address
Supplicant IP Address
IP Address IP Address Assignment Table Supplicant IP Address
DHCP Message “ciaddr” IP Address DHCP Server 0.0.0.0 DHCP ACK “yiaddr”
Authenticator
Authenticator DHCP ACK “yiaddr”
DHCP REQUEST “ciaddr” “yiaddr” 0.0.0.0 Supplicant IP Address
“yiaddr” IP Address Supplicant State Table Supplicant IP Address Supplicant traffic
4.2.1.1.3 Static conflicting IP Address with Non-subscribed
user Supplicant Static IP Address DHCP Server IP Address Assignment Table IP Address
Figure 4-8 Supplicant IP Address DHCP Server IP Address Assignment Table IP Address
Message :
Supplicant Authenticator Authenticator Supplicant Authentication Server
Authenticator Supplicant Authenticator Supplicant Supplicant IP Address Authenticator Supplicant IP Address
Authenticator DHCP REQUEST DHCP Server Supplicant IP Address MAC Address DHCP Message “ciaddr” “chaddr”
“uaname”
DHCP Server DHCP DISCOVERY DHCP Server DHCP Message “uaname” “chaddr” Supplicant
MAC Address IP Address Assignment Table Supplicant IP Address
Supplicant IP Address
IP Address Assignment Table
IP Address DHCP Message “ciaddr” Supplicant IP Address IP Address
IP Address Supplicant IP Address IP Address DHCP Server
0.0.0.0 DHCP ACK “yiaddr” Authenticator Authenticator DHCP ACK “yiaddr”
DHCP REQUEST “ciaddr” “yiaddr” 0.0.0.0 Supplicant IP Address
“yiaddr” IP Address Supplicant State Table Supplicant IP Address Supplicant traffic
4.2.1.1.4 Static Non-conflicting IP Address with Non-subscribed
IP Address guest user Supplicant Static IP Address DHCP Server IP Address Assignment Table IP Address
Figure 4-9 Supplicant IP Address DHCP Server IP Address Assignment Table IP Address
Message :
Supplicant Authenticator Authenticator Supplicant Authentication Server
Authenticator Supplicant Authenticator Supplicant Supplicant IP Address Authenticator Supplicant IP Address
Authenticator DHCP REQUEST DHCP Server Supplicant IP Address MAC Address DHCP Message “ciaddr” “chaddr”
Figure 4-9 Static Non-conflicting IP Address with Non-subscribed IP Address DHCP Server DHCP DISCOVERY DHCP Server DHCP Message “uaname” “chaddr” Supplicant
MAC Address IP Address Assignment Table Supplicant IP Address
Supplicant IP Address
IP Address Assignment Table
IP Address IP Address
IP Address Supplicant IP Address IP Address DHCP Server
Supplicant User Account IP Address MAC Address
Table Status
Non-Subscribed DHCP Server DHCP Message “ciaddr” Supplicant IP Address DHCP ACK “yiaddr”
Authenticator
Authenticator DHCP ACK “yiaddr”
DHCP REQUEST “ciaddr” “yiaddr” Supplicant IP Address
“yiaddr” IP Address Supplicant State Table Supplicant IP Address Status Static
Supplicant traffic
4.2.1.2 Dynamic IP Address Acquisition
Authenticator DHCP Dynamic IP Address
IP Address
4.2.1.2.1 Pre-subscribed IP Address
IP Address DHCP Dynamic IP Address Supplicant
Figure 4-10 Supplicant DHCP
IP Address Message :
Supplicant Authenticator Authenticator Supplicant Authentication Server
Figure 4-10 User acquires subscribed IP Address with Dynamic IP Address Acquisition
Authenticator Supplicant Supplicant DHCP Dynamic IP Address Authenticator Supplicant DHCP DISCOVERY
Authenticator Supplicant IP Address Authenticator DHCP REQUEST DHCP Server
Supplicant MAC Address DHCP Message “chaddr” “uaname” “ciaddr” 0.0.0.0 Supplicant DHCP
DHCP Server DHCP DISCOVERY DHCP Server DHCP Message “uaname” “chaddr” Supplicant
MAC Address IP Address Assignment Table Supplicant IP Address
Supplicant IP Address
IP Address Assignment Table Supplicant IP Address DHCP Message “ciaddr” 0.0.0.0 DHCP Server Status Subscribed “chaddr” MAC Address MAC Address
Table Supplicant IP Address DHCP ACK “yiaddr” Authenticator
Authenticator DHCP ACK “yiaddr” DHCP REQUEST “ciaddr”
Supplicant DHCP “ciaddr” 0.0.0.0 “yiaddr” Supplicant “yiaddr”
IP Address “yiaddr” IP Address Supplicant State Table Supplicant IP Address Status
4.2.1.2.2 Non-subscribed IP Address
IP Address guest user DHCP Dynamic IP Address Supplicant
Figure 4-11 Supplicant DHCP Dynamic
IP Address Message :
Figure 4-11 User acquires IP Address with Dynamic IP Address Acquisition Supplicant Authenticator Authenticator Supplicant
Authentication Server Authenticator Supplicant Supplicant DHCP Dynamic IP Address Authenticator Supplicant DHCP DISCOVERY
Authenticator Supplicant IP Address Authenticator DHCP REQUEST DHCP Server
Supplicant MAC Address DHCP Message “chaddr” “uaname” “ciaddr” 0.0.0.0 Supplicant DHCP
DHCP Server DHCP DISCOVERY DHCP Server DHCP Message “uaname” “chaddr” Supplicant
MAC Address IP Address Assignment Table Supplicant IP Address
Supplicant IP Address
IP Address Assignment Table Supplicant IP Address DHCP Message “ciaddr” 0.0.0.0
DHCP Server IP Address
IP Address IP Address DHCP ACK “yiaddr” Authenticator Supplicant User Account
MAC Address IP Address Table
Status Non-Subscribed Authenticator DHCP ACK “yiaddr”
Supplicant DHCP “ciaddr” 0.0.0.0 “yiaddr” Supplicant “yiaddr”
IP Address “yiaddr” IP Address Supplicant State Table Supplicant IP Address Status
Dynamic Supplicant traffic
4.2.2 IP Address Releasing
Authenticator Supplicant DHCP RELEASE Supplicant Supplicant Static IP Address DHCP Dynamic IP Address DHCP Message DHCP Server IP Address Release
Figure 4-12 Supplicant
Authenticator Supplicant Supplicant
Message :
Authenticator Supplicant DHCP RELEASE Supplicant
Authenticator Supplicant State Table Supplicant IP Address MAC Address DHCP Message “ciaddr” “chaddr”
DHCP RELEASE DHCP Server Supplicant State Table
Figure 4-12 IP Address Releasing
DHCP Server Authenticator DHCP RELEASE DHCP Server DHCP Message “ciaddr” “chaddr” Supplicant
IP Address MAC Address IP Address Assignment Table
Table Status Inactive; DHCP DHCP Server IP Address Table ;
4.3
IP :
Authenticator Supplicant State Table Authenticator Supplicant
IP Management Server IP Address Assignment Table Authenticator Supplicant IP Address
Dynamic IP Assignment Mechanism DHCP Message Authenticator IP Management Server IP Management Protocol
Authenticator DHCP Message “ciaddr” “chaddr” options “uaname”
Authenticator Supplicant DHCP Server DHCP Message “yiaddr”
Supplicant State Table Supplicant
DHCP Server Authenticator DHCP
“ciaddr” “chaddr” “uaname” IP Address Assignment Table Supplicant IP Address DHCP Message “yiaddr” Authenticator
IP
IP
5.1
Figure 5-1System architecture of proposed scheme implementation Web Login +
RADIUS IP Address
IP Address Web Server Authenticator IP Address Supplicant Web Server
RADIUS IP
DHCP Server IP Address Assignment Table Supplicant IP Address Supplicant DHCP Message
Supplicant IP Address MAC Address Authenticator Supplicant State
Table Supplicant Figure 5-1
5.2
Figure 5-2 Supplicant Authenticator Authenticator Authenticator Radius Server Supplicant DHCP Server Supplicant
Figure 5-2Network Environment of proposed scheme implementation Authenticator IP Address 192.168.1.1
IP Address Authenticator IP Address Supplicant Authenticator DHCP IP Address
192.168.1.11~192.168.1.20 Radius Server IP Address
Supplicant IP Address 192.168.1.21~192.168.1.30
Supplicant
Radius Server Linux Open Source FreeRadius[25] Authenticator DHCP Server
5.3 User
Figure 5-3User Account Apply Flow
User Figure 5-3 User
Radius Server [26]
IP Address IP Address
IP Address IP Address MAC Address DHCP Server IP Address Assignment Table
5.4 Supplicant
Figure 5-4Supplicant Login Flow
IP Address Authenticator IP Address Supplicant Authenticator
Authenticator Radius Server Radius Server
Supplicant Authenticator
Authenticator IP Address Supplicant MAC Address DHCP Server DHCP Server
IP Address Supplicant Authenticator IP Address
Supplicant IP Address
Supplicant Authenticator
IP Address IP
Address Authenticator Supplicant IP
Address IP Address IP Address
5.5 Authenticator
Figure 5-5 Authenticator Authenticator Supplicant State Table Supplicant
Supplicant MAC Address Supplicant Port Number Supplicant State Table
IP Address IP Address Supplicant Authenticator Authenticator
Radius Server
Radius Server Authenticator
Supplicant Authenticator Supplicant
DHCP Message DHCP Server IP Address IP Address
Supplicant IP Address DHCP
Message “ciaddr” IP Address “chaddr”
Supplicant MAC Address “uaname” Supplicant IP Address DHCP Message “ciaddr” 0.0.0.0 “chaddr” Supplicant MAC Address “uaname”
Authenticator DHCP Message Unicast DHCP DISCOVERY/DHCP REQUEST DHCP Server DHCP Server DHCP OFFER/DHCP ACK Authenticator
Supplicant IP Address DHCP
Message “yiaddr” “ciaddr” IP Address Authenticator Supplicant
Authenticator
IP Address Supplicant State Table Supplicant IP Address Supplicant
Supplicant IP Address DHCP
Address Authenticator Supplicant
Authenticator “yiaddr” IP
Address IP Address Supplicant State Table Supplicant IP Address Supplicant IP Address
IP Address Authenticator IP Address Supplicant
5.6 DHCP Server
Figure 5-6 DHCP Server DHCP Server IP Address Assignment Table IP Address
Authenticator IP Address DHCP Message DHCP Message “ciaddr” “chaddr” “uaname” IP Address Supplicant MAC Address IP Address
Assignment Table Supplicant IP
Address
Supplicant IP Address “ciaddr” IP Address 0.0.0.0 Supplicant
IP Address DHCP Message “yiaddr” Supplicant IP Address “ciaddr” IP Address
Supplicant IP Address IP
Address IP Address DHCP Message
“yiaddr” Supplicant IP Address
Supplicant IP Address DHCP Message “yiaddr” 0.0.0.0 DHCP Message
Authenticator
Figure 5-6DHCP Server System Flow of proposed scheme implementation Supplicant IP Address IP Address Assignment Table “ciaddr” IP Address
0.0.0.0 Supplicant IP Address DHCP
Server IP Address
IP Address DHCP Message “yiaddr”
DHCP Message “yiaddr” 0.0.0.0 “ciaddr” IP Address Supplicant IP Address
IP Address IP Address
IP Address DHCP Message “yiaddr” 0.0.0.0
DHCP Server IP
Address IP Address DHCP Message “yiaddr” DHCP Message Authenticator
6.1
IP Supplicant
Authenticator Supplicant State Table Authenticator Supplicant
Dynamic IP assignment IP Management Server Supplicant IP Address IP Management Server
IP Address Assignment Table Supplicant IP Address Authenticator IP Address
Supplicant State Table Supplicant IP Address Supplicant
State Table IP Address
IP IP
IP
IP Address :
IP Address IP Address
: IP Management Server IP Address Assignment Table Routable IP Address
IP Address
: Authenticator Supplicant State Table Supplicant
:
IP Address IP Address
IP Address IP Address
6.2
IP Management Server IP Address Assignment Table Table User Account
IP Address IP Address IP Address
IP Address IP Address Assignment Table User Account IP Address IP Address Authenticator IP Address IP Address IP Address IP Address IP Address IP Address
[1] R. Droms, “Dynamic Host Configuration Protocol,” RFC 2131, March, 1997.
[2] C. Rigney, S. Willens, A. Rubens, W. Simpson, “Remote Authentication Dial
In User Service (RADIUS),” RFC 2865, June, 2000
[3] C. Rigney, “RADIUS Accounting,” RFC 2866, June, 2000 [4] J. Postel, “User Datagram Protocol,” RFC 768, 28, August, 1980
[5] Radius Types. Available:
http://www.iana.org/assignments/radius-types
[6] R. Rivest, “The MD5 Message-Digest Algorithm,” RFC 1321, April, 1992 [7] RADIUS From Wikipedia. Available:
http://en.wikipedia.org/wiki/RADIUS
[8] IEEE 802.1 Working Group, “Port-Based Network Access Control,” IEEE Standard 802.1X-2004, December 2004.
[9] Virtual LAN From Wikipedia. Available:
http://en.wikipedia.org/wiki/VLAN
[10] IEEE 802.1X From Wikipedia. Available:
http://en.wikipedia.org/wiki/IEEE_802.1X
[11] P. Congdon, B. Aboba, A. Smith, G. Zorn, J. Roese, “IEEE 802.1X Remote
Authentication Dial In User Service (RADIUS) Usage Guidelines,” RFC 3580, September 2003
[12] IEEE 802.1X . Available:
http://www.microsoft.com/taiwan/technet/community/columns/cableguy/cg0402.a spx
[13] B. Aboba, L. Blunk, J. Vollbrecht, J. Carlson, “Extensible Authentication
Protocol (EAP),” RFC 3748, June 2004
[14] W. Simpson, “The Point-to-Point Protocol (PPP),” RFC 1661, July 1994
[15] . Available:
http://loda.zhupiter.com/WirelesSecurity.htm
[16] D. Simon, B. Aboba, R. Hurst, “The EAP-TLS Authentication Protocol,” RFC
5216, March 2008
Transport Layer Security Authenticated Protocol Version 0 (EAP-TTLSv0),” RFC 5281, August 2008
[18] J. Arkko, H. Haverinen, “Extensible Authentication Protocol Method for 3rd Generation Authentication and Key Agreement (EAP-AKA),” RFC 4187, January 2006
[19] IEEE 802.11 Working Group, “Amendment 6: Medium Access Control (MAC)
Security Enhancements,” IEEE Standard 802.11i-2004, July 2004.
[20] Dynamic Host Configuration Protocol From Wikipedia. Available:
http://en.wikipedia.org/wiki/Dhcp
[21] K. Sollins, “THE TFTP PROTOCOL (REVISION 2),” RFC 350, July 1992
[22] IP & MAC Address Binding. Available:
http://ftp.qno.cn/Doc/Technical/FVR9416_IP&MAC_Binding_Setting.pdf
[23] NCTU Dormitory Network IP Address Apply. Available:
http://www.cc.nctu.edu.tw/dorm/apply_ip.html [24] . Available: http://www.kyu.edu.tw/93/epaperv7/001.pdf [25] FreeRadius . Available: http://freeradius.org/ [26] FreeRadius . Available: http://rd.tyc.edu.tw/modules.php?name=Tutorial&mode=visit&tid=10


![Figure 3-1 IP/MAC Address Binding ( [22] )](https://thumb-ap.123doks.com/thumbv2/9libinfo/8625262.191848/35.918.201.707.517.680/figure-ip-mac-address-binding.webp)