IEEE Transactions on Consumer Electronics, Vol. 54, No. 3, AUGUST 2008
Contributed Paper
Manuscript received June 10, 2008 0098 3063/08/$20.00 © 2008 IEEE 1148
Securing Traffic at QoS-aware Residential
Gateway Using Biometric Signatures
Pei-Chen Tseng, Jing-Wein Wang, Member, IEEE, and Wen-Shyang Hwang, Member, IEEE
Abstract —Home networks are becoming ubiquitous.
Multimedia is a primary home network application that is challenging bandwidth capabilities with respect to QoS and also creating issues regarding authorized access to the home network and its digital content. To deal with these issues, this study presents an embedded QoS-aware residential gateway (EmQRG) in the home network which classifies forwarded traffic for optimal use of bounded network bandwidth resources and, instead of traditional password methodology, requires bimodal biometric recognition of users. A laboratory EmQRG testbed with bimodal biometric recognition system (BBRS) is implemented via class-based queuing (CBQ) bandwidth management in a 3-PC network including a real DiffServ-capable CBQ-capable router, CCD camera and optical fingerprint reader. Novel computational methods are used for face and fingerprint analysis and recognition. It is confirmed that combining two biometric modalities improves performance, particularly for the false acceptance rate (FAR) that is considered the most serious home security problem. Experimental results demonstrate efficiency and robustness of both the EmQRG and the BBRS1.
Index Terms — Home Network, QoS, Embedded System, Biometric Identification.
I. INTRODUCTION
The number of microprocessor-embedded network-capable devices is increasing rapidly in the home. This together with broadband convergence networking (BcN) and inter-networked home devices is making the digital home network a ubiquitous 24-7 computing and communication environment [1]-[2]. A home gateway/residential gateway (HG/RG) is needed to interconnect multiple home devices to one another and to the Internet. Further, multimedia issues necessitate a means to manage user accounts for legal access to digital contents whether stored within the home network or stored in commercial libraries. Such security tasking must have suitable priority but without unnecessary disruption in the rest of the network. Good QoS should include suitable allocation of resources in the network (e.g. bandwidth, priority) so that data gets to its destination quickly and consistently. Real-time
1Supported under Grant No. MoE 0940071581N by National Kaohsiung
University of Applied Sciences and the Ministry of Education, Taiwan, ROC. Pei-Chen Tseng and Wen-Shyang Hwang are now with Department of Electrical Engineering, National Kaohsiung University of Applied Sciences, Kaohsiung, Taiwan (e-mail: peichen@wshlab2.ee.kuas.edu.tw, wshwang@mail.ee.kuas.edu.tw ).
Jing-Wein Wang is now with Institute of Photonics and Communications, National Kaohsiung University of Applied Sciences, Kaohsiung, Taiwan (e-mail: jwwang@cc.kuas.edu.tw ).
applications such as video play and VoIP are usually given higher priority than other applications. However, exceptionally high priority must be given to security tasks such that they have the right to interrupt many but not all media and similar data tasks.
Various groups including OSGi, DHWG, CELF, DLNA, UPnP forum, and RIAA are driving convergence of the digital home network for interoperability of multimedia networking and legal security/action in the home network. Their emphases can be summarized as follows:
z Interoperability of media management and control between different types of multimedia devices;
z QoS management for digital content, especially bandwidth and delay sensitive applications such as audio/video (AV) streams, voice, and games;
z User recognition based on biometric signatures.
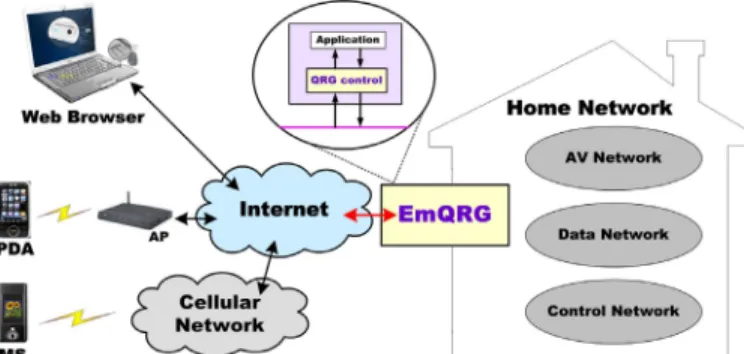
This paper supports these objectives in a twofold manner. Firstly, based on our previous work [3] on a DiffServ-QoS bandwidth management mechanism during network congestion, we introduce an embedded QoS-aware residential gateway (EmQRG) in the home network to classify forwarded traffic for optimal use of bounded network bandwidth resources. EmQRG is verified experimentally in real-time via class-based queuing (CBQ) bandwidth management in a real DiffServ-capable CBQ-capable router, whereas our earlier QRG system was implemented only via Mrouter-PC emulation. Secondly, this paper protects digital content by a bimodal biometric recognition system (BBRS) using combined face and fingerprint traits. BBRS in conjunction with EmQRG is evaluated experimentally by the system shown in Fig. 1.
Fig. 1. Network architecture of EmQRG. Peripheral units are equipped with one or more biometric recognition devices (e.g. CCD camera, fingerprint reader, etc) for access control of home network digital content.
The architecture shows that the EmQRG interconnects the Internet and a home network that includes an AV network, a data network and a control network. Legal access from within
P.-C. Tseng et al.: Securing Traffic at QoS-aware Residential Gateway Using Biometric Signatures 1149
or without the home is ensured by bimodal biometric recognition of the user prior to sharing of home network data. This is similar to using a user name and password, but BBRS uses biometric data to perform identification. Under BBRS, both the user’s face and fingerprint biometric data are captured by suitable hardware that is connected to a host computer. In this study, CCD camera and optical fingerprint reader connect to a generic host computer (Fig. 1 “web browser”). BBRS security initialization requires that each authorized user provides clear images of face and fingerprints (two, one finger each hand). Screen display with sample data can be seen in Fig. 9(a) for the Client and Fig. 9(b) for the Data Server. The Data Server facial image includes both visible and invisible watermarks, to help prevent insertion of false identification into the BBRS database [4]. Face and fingerprint data are fed to the Data Server computer (Fig. 6) via the EmQRG through the home Ethernet. The EmQRG serves as a control center which performs security tasks, coordinates information sharing of digital content, translates communication protocols among the various home devices, works as a gateway to external networks and performs the DiffServ-QoS traffic classification mechanism. The EmQRG assigns forwarded traffic to an appropriate class for optimized treatment in compliance with user-specified priorities. The classified traffic is then sent to the appropriate destination through a DiffServ-capable CBQ-capable network.
CBQ provides fine granularity of bandwidth sharing and traffic priority control, including session level, thereby enabling service level guarantees for individual flows and aggregate traffic. In Fig. 1, received data come from the web browser and are processed by the Data Server. The Data Server contains a database of selected features for authorized users. The Data Server generates GO/NG decisions for the web browser by comparing its database with the biometric data that accompanies any new request for data access.
Traditional computer-based identification relies on user-remembered data such as a password or pin code. Alternately, the user carries an identifying physical object e.g. a card, key, token or RFID. Biometric identification relies on biological traits intrinsic to the user, for example the (relatively) unique patterns contained the user’s face, fingerprint, palmprint, palm-dorsa, pores, veins or iris. Face and fingerprint are the most common biometric traits used for personal identification. Fingerprint identification is the oldest scientific biometric identification method. The high level of data in a fingerprint allows quick reduction of possible matches to a small number, even in a large database. Facial recognition is more difficult because of the relatively low levels of data and data-contrast available in the face. The third most common biometric ID uses voice patterns, but voice biometrics have proven difficult to employ reliably.
Fingerprint-based methods have proven so reliable that some commercial mobile devices and e-notebooks incorporate built-in fingerprint recognition devices. Fingerprints can be used in home networks [5]-[6], but digital fingerprinting requires contacting a communal physical surface, which
presents contagion issues like during the recent SARS epidemic. Further, reliance on a single biometric provides only limited security. Improved security is obtained by using a second biometric. This study uses both fingerprint and facial recognition, i.e. a two-mode or bimodal biometric recognition system (BBRS). If voice or other parameters such as iris or skin pore pattern can be brought into play, then the system could be expanded to higher x-modal levels. Multi-modal biometric recognition shows great promise for access security in the home network.
This paper considers only a bimodal face/fingerprint system. Section II presents the DiffServ-QoS mechanism and the bimodal recognition algorithm. Implementation and experimental results are in sections III and IV. Finally conclusions and future work are summarized in section V.
II. DIFFSERV-QOSMECHANISM AND BIOMETRIC
ALGORITHM
A. DiffServ-QoS Mechanism
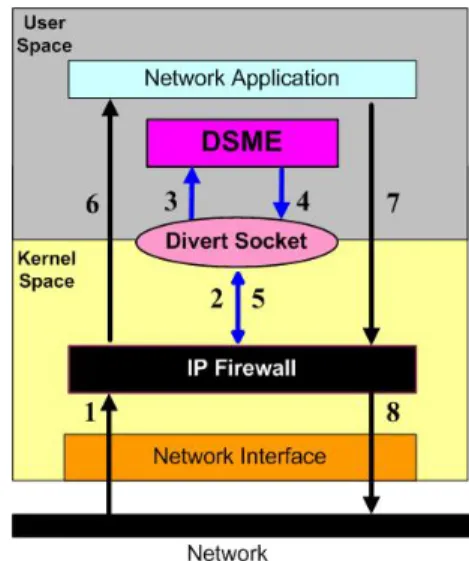
The proposed DiffServ-QoS service architecture is based on a methodology whereby the EmQRG classifies forwarded traffic, marking each data packet for special treatment according to preset behavior aggregates. Each behavior aggregate is identified by a single DiffServ codepoint (DSCP) contained in the packet header. Within the DiffServ-capable network, packets are forwarded according to the per-hop behavior (PHB) associated with the DiffServ codepoint.
Fig. 2. Packet processing scenario by DSME via IP firewall.
Generally, traffic coming into the home network is already packetized with an IP header. It is passed to the kernel stack according to the network, after which the packets are injected into the network. In the employed OS, the IP firewall is located in the bottom of the IP stack. The IP firewall can filter incoming and outgoing IP packets that travel through the IP stack according to the firewall rules. To allow or deny IP packets to the IP stack, the IP firewall also provides flow accounting, flow shaping and flow redirection. Consequently the IP firewall is used to implement the so-called DSME
P.-C. Tseng et al.: Securing Traffic at QoS-aware Residential Gateway Using Biometric Signatures 1155
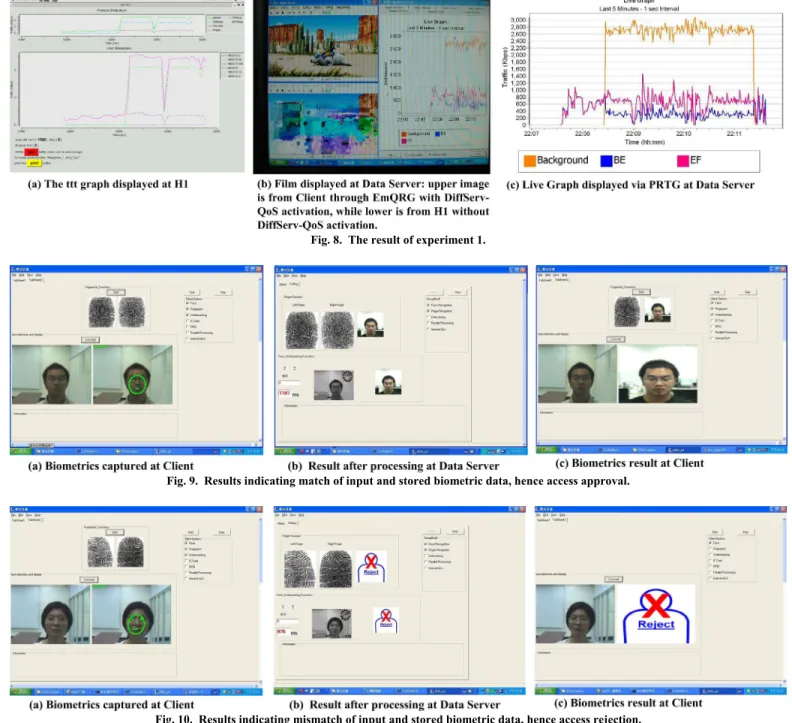
Fig. 8. The result of experiment 1.
Fig. 9. Results indicating match of input and stored biometric data, hence access approval.
Fig. 10. Results indicating mismatch of input and stored biometric data, hence access rejection.
V. CONCLUSIONS AND FUTURE WORK
A QoS-aware Residential Gateway (EmQRG) was embedded in an experimental home network implemented in real-time via class-based queuing (CBQ) bandwidth management in a real DiffServ-capable CBQ-capable router. The EmQRG classified forwarded traffic under congested bandwidth-limited experimental conditions. Experimental results showed EmQRG maintained excellent QoS. A bimodal (face and fingerprint) biometric recognition system (BBRS) was embedded in the EmQRG testbed. BBRS authorized users were correctly accepted in 92.17% of a series of real-time experiments, while false acceptance rate (FAR) was a low 0.94%. Recognition speed of our laboratory testbed BBRS was easily adequate for real-time use. Further improvements in speed and accuracy are believed easily
attainable but were not investigated in this proof-of-concept study. It is confirmed that combining two biometric modalities improves performance, particularly for the FAR parameter that is so important in home network security. The present BBRS requires the capture/analysis of 100 or more facial images, each with slightly different pose and lighting. Future work will reduce system training requirements, possibly by employment of a generic learning approach [24].
REFERENCES
[1] J. Park, K. Lee, D. Park, and K. Moon, “QoS-aware bridge for high-speed powerline communication and ethernet,” IEEE Transactions on
Consumer Electronics, vol. 53, no. 1, pp. 50-54, Feb. 2007.
[2] S. G. Choi, D. O. Kang, and J. W. Lee, “A media distribution system supporting priority-based QoS in a home network,” The 8th
International Conference on Advanced Communication Technology, ICACT 2006 , vol. 3, pp. 1532-1536, Feb. 2006.
IEEE Transactions on Consumer Electronics, Vol. 54, No. 3, AUGUST 2008 1156
[3] W. S. Hwang and P. C. Tseng, “A QoS-aware residential gateway with bandwidth management,” IEEE Transactions on Consumer Electronics, vol. 51, no. 3, pp. 840-848, Aug. 2005.
[4] A. Lumini and D. Maio, “Adaptive positioning of a visible watermark in a digital image,” IEEE International Conference on Multimedia and
Expo, ICME 2004, vol. 2, pp. 967-970, Jun. 2004.
[5] P. Corcoran and A. Cucos, “Techniques for securing multimedia content in consumer electronic appliances using biometric signatures,”
IEEE Transactions on Consumer Electronics, vol. 51, no. 2, pp.
545-551, May 2005.
[6] P. Corcoran, C. Iancu, F. Callaly, and A. Cucos, “Biometric access control for digital media streams in home networks,” IEEE
Transactions on Consumer Electronics, vol. 53, no. 3, pp. 917-925,
Aug. 2007.
[7] L. F. Chen, H. Y. Mark Liao, J. C. Lin, and C. C. Han, “Why recognition in a statistics-based face recognition system should be based on the pure face portion: a probabilistic decision-based proof,”
Pattern Recognition, vol. 34, pp. 1393-1403, 2001.
[8] A. Martinez, “Recognizing imprecisely localized, partially occluded, and expression variant faces from a single sample per class,” IEEE
Transactions on Pattern Analysis and Machine Intelligence, vol. 24,
no. 6, pp. 748-763, Jun. 2002.
[9] K. Messer, J. Kittler, M. Sadeghi, M. Hamouz, A. Kostyn, S. Marcel, S. Bengio, F. Cardinaux, C. Sanderson, N. Poh, Y. Rodriguez, K. Kryszczuk, J. Czyz, L. Vandendorpe, J. Ng, H. Cheung, and B. Tang, “Face authentication competition on the BANCA database,” ICBA,
Lecture Notes in Computer Science, vol. LNCS 3072, pp. 8-14, Jul.
2004.
[10] M. St¨orring, “Computer vision and human skin colour,” PhD dissertation, Faculty of Engineering and Science, Aalborg University, 2004.
[11] C. Garcia and G. Tziritas, “Face detection using quantized skin color regions merging and wavelet packet analysis,” IEEE Transactions on
Multimedia, vol.1, no. 3, pp. 264-277, Sep. 1999.
[12] S. Mallat, A Wavelet Tour of Signal Processing, 2nd ed., Academic Press, 2001.
[13] Christopher J. C. Burges, “A tutorial on support vector machines for pattern recognition,” Data Mining and Knowledge Discovery, vol. 2, no. 2, pp. 121-167, 1998.
[14] J. W. Wang, “Precise face segmentation for recognition,” IEEE
International Conference on Image Processing, ICIP 2006, pp.
2045-2048, Oct. 2006.
[15] L. Torres and J. Vilá, “Automatic face recognition for video indexing applications,” Pattern Recognition, vol. 35, pp. 615-625, Mar. 2002. [16] Z. Sun, G. Bebbis, and R. Miller, “Object detection using feature subset
selection,” Pattern Recognition, vol. 37, pp. 2165-2176, Nov. 2004. [17] A. Ross, S. Dass, and A. Jain, “A deformable model for fingerprint
matching,” Pattern Recognition, vol. 38, pp. 95-103, Jan. 2005. [18] Y. Chen, S. Dass, A. Ross, and A. Jain, “Fingerprint deformation
models using minutiae locations and orientations,” Proceedings of the
seventh IEEE Workshop on Applications of Computer Vision, WACV/MOTION, vol. 1, pp. 150-155, Jan. 2005.
[19] L. Sha, F. Zhao, and X. Tang, “Fingerprint matching using minutiae and interpolation-based square tessellation fingercode,” IEEE
International Conference on Image Processing, ICIP 2005, vol. 2, pp.
41-44, Sep. 2005.
[20] D. Batra, G. Singhal, and S. Chaudhury, “Gabor filter based fingerprint classification using support vector machines,” Proceedings of the IEEE INDICON 2004, First India Annual Conference, pp. 256-261, Dec.
2004.
[21] C. Y. Hsu and J. W. Wang, “Fingerprint recognition using kernel subregion of fingerprint image,” CVGIP2006, Oral Section, Taoyuan Taiwan, Aug. 2006.
[22] P. C. Tseng, J. K. Shiung, C. T. Huang, S. M. Guo, and W. S. Hwang, “Adaptive car plate recognition in QoS-aware security network,” The
Second IEEE International Conference on Secure System Integration and Reliability Improvement, SSIRI 2008, Jul 2008.
[23] R. O. Duda, P. E. Hart, and D. G. Stork, Pattern Classification, 2nd ed., Wiley Press, 2000.
[24] J. Wang, K. N. Plataniotis, J. Lu, and A. N. Venetsanopoulos, “On solving the face recognition problem with one training sample per subject,” Pattern Recognition, vol. 39, pp. 1746-1762, 2006.
Pei-Chen Tseng was born in Hualien, Taiwan, in
1968. She graduated from National Taipei Institute of Technology in Electronic Engineering in 1990. From 1990 to 2001 she worked for Siemens as a telecommunication engineer, including five years as a testing engineer in EWSD switching systems, one year as a technical support engineer in switching systems, one year as a technical specialist in mobile telecommunication systems, and almost five years as a RF engineer in mobile telecommunication systems. Studying at the National Kaohsiung University of Applied Sciences, Kaohsiung, Taiwan, she received a B.S. in electrical engineering in 2002, a M.S. in 2004, and is currently pursuing a Ph.D. with a focus on communication, protocol, multimedia, and networking. Her research interests include home networking, network security, and GSM/GPRS/CDMA telecommunication systems. She is a student member of IEEE.
Jing-Wein Wang received B.S. and M.S. degrees in
Electronic Engineering from National Taiwan University of Science and Technology in 1986 and 1988, respectively, and a Ph.D. degree in Electrical Engineering from National Cheng Kung University, Taiwan, in 1998. From 1992 to 2000 he was a principal project leader at Equipment Design Center of PHILIPS, Taiwan. In 2000, he joined the faculty of National Kaohsiung University of Applied Sciences, where he is currently an associate professor in the Institute of Photonics and Communications. His current research interests are combinatorial optimization, pattern recognition, wavelets, and biometric applications. He is a member of IEEE.
Wen-Shyang Hwang received B.S., M.S., and Ph.D.
degrees in Electrical Engineering from National Cheng Kung University, Taiwan, in 1984, 1990, and 1996, respectively. He is currently a professor of Electrical Engineering, and the chairman of department of computer science and information engineering in National Kaohsiung University of Applied Sciences, Taiwan. His current research interests are in the fields of storage area networks, WDM Metro-ring networks, performance evaluation, multimedia wireless communication, mesh networks, software design for embedded systems, Internet QoS, and Internet applications. He is a member of IEEE.