Application of Fractal Image Model to Visible Watermarking
全文
(2) distortion, it therefore is perceptually invisible to human eyes. In [2], a DCT-based approach is proposed. In the approach, an image block is selected and then from twelve predetermined pairs of mid-frequency transform coefficients one of them is chosen. To embed a bit, the difference of the coefficients is modified to be positive or negative according to the bit value. In [3], the multi-resolution technique is applied to watermarking. In the approach, both original image and watermark are decomposed by the multi-resolution method. Then the different resolution components of the watermark are added to the corresponding resolution in the decomposed original image. In [4], a fractal-based approach is proposed where the concept of fractal image compression is applied to binary image watermarking. In the approach, to embed a watermark fractal codes are skillfully divided into two subsets. Each subset represents a bit value, 0 or 1. To retrieve the embedded watermark, the fractal code of image block is found and the bit value of watermark is assigned according to the subset which the fractal code belongs to. Up to present, the proposed watermarking approaches as in [1-4] try to embed the watermark itself into the original image. In general, the watermark takes large amount of memory. In this paper, a fractal image model based approach is proposed to visible watermarking where only several bytes are required to represent a watermark. This paper is organized as follows: In Section 2, the fractal image model is reviewed. Next, the proposed approach is described. Then a simulation result is given in Section 4. Finally, conclusions and further researches are made in Section 5.. 2. Fractal Image Model A fractal image model is a set of affine transformations. With the fractal model, two objectives in image processing can be achieved: compression and representation. For image compression, a fractal model is found to represent an image block. Since the fractal model requires less bytes than that for the original image block, it achieves the goal of image compression. As for image representation, the fractal model gives an image called attractor through iterated function system (IFS) [5,6]. In other words, a set of affine transformation represents an image and therefore the information of generated image can be persevered in its corresponding affine transformations. This is the idea to be used in the proposed approach. The fractal model which represents an image is reviewed in the following. Let a set of affine transformations denote as 2/9.
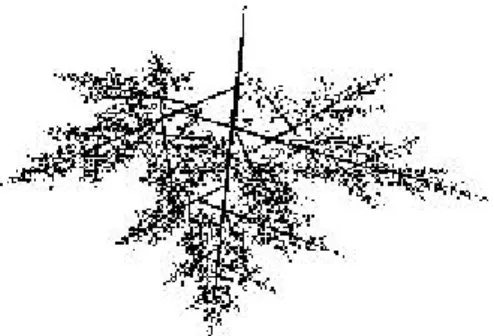
(3) a Tk ( x) = k ck. bk e x+ k dk fk . (1). for 1 ≤ k ≤ n , where x is a point in the R 2 plane and n is the total number of transformations. If Tk are contracting mappings, then an attractor can be obtained through IFS [5,6]. In general, IFS can be classified as deterministic IFS and random IFS. Since the deterministic IFS generally takes much memory capacity [5], thus the random IFS is employed here to relieve the problem of memory capacity. Given a set of probabilities p = { p1 , p 2 , L , p n } where the probability p k is associated to Tk , the way that random IFS works is described as follows. Given an arbitrary initial point x 0 , a transformation, say T j , is chosen according to p. Then a new point x1 is found after transformation T j . This process completes one iteration in random IFS. In the second iteration, a transformation is randomly selected and the new point x1 replaces the initial point x 0 to obtain x 2 . Iteratively, x k is found through a randomly chosen transformation and point x k −1 . The attractor of random IFS is the collection of points {x k , for 0 ≤ k ≤ N } where N is the total number of iterations. Here we use the example “maple leaf” to demonstrate random IFS. The affine transformations used in the example are given as follows. 0.49 T1 ( x ) = 0.0 0.27 T2 ( x ) = − 0.4 0.18 T3 ( x ) = 0.5 0.04 T4 ( x ) = 0.5. 0.01 25 x+ 0.62 − 2 0.52 0 x+ 0.36 56 − 0.73 88 x+ 0.26 8 − 0.01 52 x+ 0.0 32. (2). With the set of probabilities p1 = p 2 = p 3 = p 4 = 1 4 , the image obtained from random IFS with 20,000 iterations is shown in Figure 1.. 3/9.
(4) Figure 1. “Maple leaf” after 20,000 iterations This example demonstrates that the image of “maple leaf” can be represented by affine transformations Tk and the set of probabilities p. Therefore, the information in Tk and p is as good as that in the image of “maple leaf” itself.. 3. The Proposed Approach Note that a fractal image model has equivalent information as its corresponding image. We propose a fractal-based approach to visible watermarking which is totally different from approaches as in [1-4]. In those proposed approaches, the information of each pixel in watermark is embedded into the original image. The proposed approach, however, embeds the equivalent information of watermark, instead of watermark itself, into the original image. The equivalent information is inherent in the fractal image model of watermark and therefore is composed of affine transformations Tk and a set of probabilities p. It takes just several bytes to store the equivalent information of watermark. For example, if the image “maple leaf” found in the previous section is considered as a watermark, with equal probability for each Tk at most 24 bytes is required to be embedded into the original image. The number of bits to store Tk can be reduced if a lossless compression algorithm such as Huffman coding [5] is applied. Based on the fractal image model, we propose an approach to visible watermarking which is given as follows. Assume the watermark to be embedded can be arbitrarily chosen. The embedding process is described as follows. Step 1:. Choose an original image where a watermark is embedded.. Step 2:. Determine a set of affine transformations Tk , for 1 ≤ k ≤ n , to represent the. watermark to be embedded. Step 3:. Give a set of probabilities p whose element p k is associated to Tk . When p k are 4/9.
(5) equal, this step is not required since p k can be found as 1 n . Step 4:. Encode n, elements of Tk , and p if needed. In this step, a permutation technique can. be applied. Step 5:. Embed coded n, Tk , and p in the original image. The embedding approach can be. any appropriate approach in spatial domain or transform domain. Step 6:. Provide the key to indicate where the encoded information in Step 4 is embedded.. In the extracting process, the provided key is used to retrieve n, Tk and p if needed. Then apply random IFS to generate the embedded watermark. Though the proposed approach assumes an arbitrary watermark, it can be easily extended to a predetermined watermark by applying fractal compression scheme [5,6] on the watermark. In this case, several sets of affine transformations are found and stored where each set of affine transformation is corresponding to one image block of the given watermark. Moreover, the original image is not required to extract the embedded watermark since the collage theorem [6] gives same final iterated image with any initial condition.. 4. Simulation Results In this section, the 512 × 512 image Baboon shown in Figure 2 is given as an example to validate the proposed approach. Since the encoded information n, Tk , and p is very important in the retrieval process, they, especially for n and Tk , should not be changed or the watermark embedded cannot be retrieved appropriately. In order to protect the embedded data as much as possible, we use Method 1 in [7]. This approach is implemented in the wavelet transform domain and reported robust in JPEG compression, median filtering, and additive noise. For details, one may consult [7]. Follow the implementation steps given in Section 3. The simulation is performed. First, image Baboon shown in Figure 2 is considered as the original image. Second, “Fern” is used as watermark in the simulation, whose affine transformations are. 5/9.
(6) 0.86 0.03 0.0 T1 ( x ) = x+ − 0.03 0.86 1.5 0.2 − 0.25 0.0 T2 ( x ) = x+ 0.21 0.23 1.5 − 0.15 0.27 0.0 T3 ( x ) = x+ 0.25 0.26 0.45 0.0 0.0 0.0 T4 ( x ) = x+ 0.0 0.17 0.0 Third,. the. probabilities. associated. with. T1 ,. T2 ,. T3 ,. (3). and. T4. are. given. as. p1 = 0.83, p 2 = 0.08, p 3 = 0.08, and p 4 = 0.01 , respectively. Fourth, use 2 bits to encode n as 11 and 8 bits for each element of Tk and p . The total number bits used to represent the watermark “Fern” is 224. Obviously, the number of bits can be significantly reduced if a lossless compression algorithm such as Huffman coding is applied, since much redundancy occurs among elements in the embedded data. Fifth, the encoded data obtained in Step 4 is then embedded in HL subband by Method 1 in [7]. With the embedded intensity m = ±20 , the simulation results with various values of α and different quality of JPEG compression are summarized in Table 1 where peak signal-to-noise ratio (PSNR) and the number of error bits, N e , for each case are given as well. From Table 1, it indicates that the embedded data can be retained perfectly if the quality of JPEG compression is beyond 20%. As reported in [7], it is robust to JPEG compression. Finally, provide a key to indicate where the data is embedded. The watermarked Lena with JPEG compression of 40% quality is shown in Figure 3 whose PSNR is 33.27 dB. By the provided key, the extracting process is performed. First, the fractal image model of embedded watermark “Fern” is extracted and decoded. Then, the embedded watermark is obtained by random IFS. After 20,000 iterations, the watermark is found as in Figure 4. Note that there is no need to use original image to extract the watermark, if the fractal image model can be obtained appropriately, since the collage theorem [6] gives same final iterated image with any initial condition.. 6/9.
(7) Figure 2.. Original Baboon. Figure 3.. Watermarked Baboon. Figure 4. “Fern” after 20,000 iterations. Table 1. Simulation results of the proposed watermarking approach (Baboon) Value of α 0.02. 0.05. 0.1. Quality of JPEG. PSNR. Ne. PSNR. Ne. PSNR. Ne. 10%. 29.29. 34. 29.30. 13. 29.29. 8. 20%. 31.13. 0. 31.13. 0. 31.12. 0. 30%. 32.32. 0. 32.33. 0. 32.32. 0. 40%. 33.27. 0. 33.27. 0. 33.27. 0. 50%. 34.14. 0. 34.14. 0. 34.13. 0. 7/9.
(8) 5. Conclusions and Further Researches This paper presents a fractal-based approach to visible watermarking. In the proposed approach, the fractal image model is employed to represent a visible watermark. Since the fractal image model has the equivalent information of watermark, thus it requires only several bytes to embed into the original image. The proposed approach is effective and efficient in terms of the number of embedded bits. At least three advantages can be obtained in the proposed approach. First, only several bytes associated with the fractal image model of watermark needs to be embedded into the original image, instead of the watermark itself as given in [1-4]. Since the amount of embedded data is significantly reduced, the watermarked image is expected to have high visual quality in general. Second, the original image is not required to extract the embedded watermark. When the watermark can be arbitrarily chosen, any fractal image model is a candidate. When the watermark is predetermined such as the logo of a company, the fractal compression technique can be used to obtain the fractal image model. In this case, there is no need to extract the embedded watermark with the original image since the collage theorem [5,6] guarantees same final iterated image with any initial image. Third, the concept proposed in the paper can be easily extended to gray-level or even to color watermarks [5,6]. As described in the proposed approach, the information of watermark is totally resided in the fractal image model which is formed by affine transformations. Therefore, the elements of affine transformations are vital in the proposed approach. If some are changed, the decoded watermark may be changed. Therefore, to prevent the change of elements in the fractal image model and to understand the effects of the change on the decoded watermark are the key problems to be investigated in further researches.. References [1] R.G. Van Schyndel, A.Z. Tirkel, and C.F. Osborne, “A Digital Watermark,” ICIP, Vol. 2, pp. 86-90, 1994. [2] E. Koch and J. Zhao, “Toward Robust and Hidden Image Copyright Labeling,” Workshop on Nonlinear Signal and Image Processing, Marmaros, Greece, 1995. [3] C.-T. Hsu and J.-L. Wu, “Multiresolution Watermarking for Digital Images,” IEEE Trans. on Circuits and Systems II: Analog and Digital Signal Processing, Vol. 45, No. 8, pp. 1097-1101, 1998. 8/9.
(9) [4] J. Puate and F. Jordan, “Using Fractal Compression Scheme to Embed a Digital Signature into an Image,” SPIE Photonics East’96 Symposium, Boston, MA, 1996. [5] Ning Lu, Fractal Imaging, Academic Press, 1997. [6] M.F. Barnsley, Fractals Everywhere, 2nd Edition, Academic Press, 1998. [7] H. Inoue, A. Miyazaki, A. Yamamoto, and T. Katsura, “A Digital Watermark Technique Based on the Wavelet Transform and Its Robustness on Image Compression and Transformation,” IEICE Trans. Fundamentals, Vol. E82-A, No. 1, pp. 2-10, 1999.. 9/9.
(10)
數據

相關文件
This paper aims the international aviation industry as a research object to construct the demand management model in order to raise their managing
The purpose of this paper is to achieve the recognition of guide routes by the neural network, which integrates the approaches of color space conversion, image binary,
A digital color image which contains guide-tile and non-guide-tile areas is used as the input of the proposed system.. In RGB model, color images are very sensitive
Furthermore, based on the temperature calculation in the proposed 3D block-level thermal model and the final region, an iterative approach is proposed to reduce
Therefore, a study of the material (EPI) re-issued MO model for an insufficient output of the LED chip manufacturing plant is proposed in this paper.. Three material
This paper proposes a set of graph algorithm to improve the application of hill-climbing, Tested to speed up the program execution time is about 3.5 times speed up
Therefore, this research paper tries to apply the perspective of knowledge sharing to construct the application model for the decision making method in order to share the
In this paper, a decision wandering behavior is first investigated secondly a TOC PM decision model based on capacity constrained resources group(CCRG) is proposed to improve