A Dynamic Bandwidth Allocation Scheme for
ATM
Networks
Zsehong Tsai, Wen-der Wang! Jin-Fu Changt
Dept. of Electrical EngineeringNational Taiwan University Taipei, Taiwan, R.O.C.
Abstract
A multiple link and multiple traffic type ATM network environment is considered. In order to efficiently utilize network resource a t low network management cost, we propose a dynamic bandwidth allocation scheme using call admissible regions as a control basis. The allocated band- width for a t r d c stream belonging to a Virtual Path is set t o be an integer multiple of the basic required bandwidth of a single call, which is carried by a Virtual Channel. In addition, the system state vector, a tuple of the number of calls of each traffic type, is required to be within the call admissible region such that the GoS for all traffic types is satisfied. We propose a generic mathematical model for the analysis of our dynamic bandwidth allocation scheme. Using the obtained analytical formulas, the bandwidth u- tilization and management cost (measured in normalized bandwidth update frequency) of two simple experimen- tal networks are obtained. We conclude that by carefully selecting the bandwidth allocation unit, one can signifi- cantly reduce the network management cost in bandwidth adjustment and still maintain high utilization, even under a heterogeneous traffic environement.
1
Introduction
The most outstanding feature of
ATM
network is it-s flexibility in supporting a wide range of services. It is allowed in ATM networks t o directly multiplex cell stream-
s with various characteristics into the transmission links. However, it is certainly impossible t o accept all connec- tion requests without limitations. Therefore the network needs t o determine whether t o accept a connection request on a call-by-call basis. Such a decision process is often referred t o as Connection Acceptance Control[GriSO] or
*This work W M supported by the Telecommunication Laborat-
ria, Ministry of Communication, under grant TG80-1302.
tThe author w a s with the Dept. of E.E., National Taiwan Uni- versity during this study, and works at the Product Development Division of the TAICOM SYSTEMS LIMITED whm this article is
published
Dept. of Electrical Engineering$ National Central University Chung-li, Taiwan, R.O.C.
Admission Control. Under a well-designed connection ac- ceptance control policy, the cell-level Grade-of-Service can be guaranteed and the resource( bandwidth) usage could be highly efficient. However, call request processing can still be a significant load of network management if the bandwidth allocation procedure has t o be performed at each call connection. Fortunately, the ATM networks em- ploy the concept of Virtual Path(VP) and Virtual Chan- nel(VC) and allow bandwidth management at both VP and VC levels. With bandwidth management at the VP level, it is possible t o reduce the bandwidth management load significantly. For example, in [OhS92], [OST88], and [SOT90], a dynamic scheme for VP bandwidth control has been proposed for single-link, single-traffic-type systems. In their work, both the management load and link utiliza- tion are found to be highly related t o the V P bandwidth control policy.
In this paper, we extend the dynamic bandwidth al- location scheme for a multiple-link, multiple-traffic-type system. Both the bandwidth allocation scheme and the mathematical model are generic and can be employed a- long with a variety of connection acceptance control poli- cies. In addition, we also investigate the effect of this bandwidth allocation scheme on various system perfor- mance measures and provide two optimization rules for different network requirements.
2
Dynamic Bandwidth Allocation
Scheme
In traditional circuit-switched or STM-based networks where the required bandwidth for each call is determin- istic, the connection acceptance control is simple. In or- der t o accept an incoming call, the residual capacity of each transmission link on the designated route needs t o be larger or equal t o the requested bandwidth. One can thus control the bandwidth of a traffic stream as follows. The allocated bandwidth for the traffic stream can be set t o be an integer multiple of the basic bandwidth required by a single call, where the integer can be said t o be the
bandwidth allocation unit. When the bandwidth is com- pletely used by the succeeding calls and a new connection request is issued, the network reallocates bandwidth to the stream. If the bandwidth is not available, the reallocation fails and the subsequent calls will be blocked.
call. If a call arrives when x; = x:, implying that the allo- cated bandwidth is completely utilized by connected calls, then the bandwidth needs t o be reallocated and
4
shall be increased by s. On the contrary, if a call terminates such that xi turns to be equal to xi-
s, then an amount Unfortunately, the situation is much more complicatedin ATM-based networks, in which a call can not be char- acterized simply by a deterministic bandwidth value, but rather by a set of traffic descriptors, e.g., average bit rate, peak bit rate, burstiness and burst length. Bandwidth assignment ia hence not an easy task. A call can be ac-
cepted only if the resultant cell loss probabilities on the links of its route are below a preset constraint. Most of the previous works are devoted to achieving high efficiency of direct multiplexing, yet still guaranteeing cell-level Grade- of-Service (GoS). In these articles, for example, [Hui88], [KHBSl], and [MSSSl], call admissible sets(regions) con- cerning the mixture of heterogeneous traffics are often re- garded as significant results. A call admissible set is a set of multidimensional state vectors, of which each element indicates the number of calls of a stream. State vectors in the call admissible set are said to be “feasible”. Con- sequently, the call acceptance control mechanism can be simplified t,o a procedure of checking the feasibility of the resultant state vector to determine whether a call shall be accepted.
The call admissible regions turn out to be dependent on the t r d c parameters, priority control mechanisms, and bandwidth assignment algorithms. In order to simplify the bandwidth control mechanisms, some articles have pro- posed the use of virtual bandwidth [GriSO, MSTSL]. The
of bandwidth shall be released and xi is decreased by s. By keeping the two records z, and x:, a connection es- tablishment procedure combining the dynamic bandwidth control and the connection acceptance control can be effi- ciently realized.
For example, if we implement the dynamic bandwidth allocation scheme on the VP-level bandwidth control, the VC connection request could be processed ~LB follows: When the number of calls x, is smaller than xi, then GoS is guaranteed and the VC is established without further processing. If xi I= z:, the network tries t o add bandwidth to this VP by increasing x: to xi
+
s. In allocaling band- width, the network simply checks whether the st,ate vector composed of z: is feasible. Such a connection establish- ment procedure is found to be efficient if the bandwidth increment size is large.Intuitively, one can predict that the usage of the network resources is less efficient than the call-by-call allocation s-
trategy, because bandwidth may be allocated but is not immediately used. However, the bandwidth managemen- t cost is also reduced since the bandwidth adjustment is not evoked at each call connection or termination. We will concentrate on the decision of appropriate sizes of band- width allocation units to reduce the processing cost, with- out significantly losing the efficiency of resource usage.
3
The Mathematical Model And
virtual bandwidth of a call is defined t o be the link capac- ity divided by the maximum number of acceptable calls,
provided only this type of calls are accepted. There are
Analytical Results
other different definitions of virtual bandwidth [GANSl],
but the basic concepts are similar. In the following, we adopt the concept of virtual bandwidth t o explain our bandwidth allocation scheme and take it as a performance measuring basis.
that the num- ber of calls in the network shall not lead to violation of the cell-level GOS requirements, the dynamic bandwidth allocation scheme needs to be employed along with an ap- propriate call acceptance control policy designed for ATM
By using the multiple-link, multiple traffic-type system model, it is possible to study the effect of network topol- ogy, and interaction between different traffic types. The termZink used in the following paragraphs could represent a physical transmission line, or a
VP
with deterministic bandwidth-since the ,.all acceptance control
3.1
System
~
~
~
~
~
i
~
t
i
~
~
~
networks. For connection acceptance control, the number of calls of a stream, say stream-i, denoted as E,, needs to be monitored. As the dynamic control scheme is em- ployed, an additional parameter xi is required to indicate the allocated bandwidth. We define xi to be the smallest integer multiple of s which is greater than or equal to xi, where a is an integer calledbandwidth allocutionunit. Thus the bandwid%h allocated for the stream is then implicitly equal to xi times the virtual bandwidth of that type of
The considered system is a network consisting of a set of links indexed from 1 to R, which conveys traffics of various types. The capacity of link r (for r = 1 , 2 , . - - , R ) is
C,.
Here we do not assume any specific topology. A fixed routing strategy is assumed. Routing in this network is defined by the path traversed by calls of a given traffic stream. A call is lost if it is blocked by any of the links in its path, and no call buffering is allowed. We also define the following trafiic parameters.
L
traffic types are assumed. Calls of a type have i- dentical traflic descriptors and have identical cell-level churucteristics, e.g., distributions of cell arrival pro- cess, burst sire and burstineas.The (virtual) bandwidth requirement for each call of type
I
is defined t o be bi.The network supports
N
traffic streams. Calls of a stream should belong to the same type, traverse i- dentical routes, and have identical cull-level charac- teristics, e.g., distributions of call holding time. Thecall arrival and service completion of different streams are mutually independent. All call arrival processes are Poisson and call holding time is exponentially dis- tributed.
For the i t h stream, the following parameters are giv- en:
A; = mean arrivalrate
=
service rate=
traffic type to which the calls of stream i belongAi
Pi
Pa =
-
,
traffic intensitysi = bandwidth allocation unit di
=
(bill 6 i 2 , *.
* I 6 i R ) 1, 0, otherwise if link r is in a stream i path wherea;,
=
For each link r ( r
=
1,. . . , R ) , a call admissible set denoted as f& can be defined. sl, is a set of L-dimensional vectors of nonnegative integers. Here Sr, could be convex or nonconvex. The only assumption on it is the coordinateconuezity, which sustains aa long as the call completion is never blocked (see [Aei78]). We follow the definition of coordinate convexity given in [JoVSl].
Definition : Let y 3 (yl,ya,
- -
a , y ~ ) and 62 is a subsetof the set of L-tuples of nonnegative integers. The set R is coordinate convex if the following proposition holds:
3.2
System Steady-State Behavior
In
the following, the system state, denoted as x,
and the link state, denoted as yr,
( T=
1 , 2 , . 1-,
R), are defined.X ~ ( ( Z ~ , Z ~ , - - - , Z N ) , where% isthenumberofactive calls from stream i.
Yr 3 (Yrlryr21'..lytL)l where SJ is derived from the state vector x by the following equation:
N
yrl =
rzi/sil
siair
l ( t i=
I ) , r = i , 2 ,.,
R
I = 1 , 2 , . . . , L (1) i = l
1, if t i
=
I 0, otherwise. whereI ( k =
I )=
Besides, the following notations are defined for conve- nience.
1
b x + e , E Z l , ~ a , ~ ~ * , ~ ; + l , * . . , z ~ 0 X - e ,
I
Z ~ , Z ~ , * - . , Z ,-
~ , * * - , z NThe state space of x
,
denoted aa A,
can now be defined as follows.A
=
{XI
Yr E Sa, for T=
1 , 2 ,- -
,
R, where eachcomponent y,r of y+ is given
by equation (1) ] (2)
The definition of A implies that the cell-level perfor- mance on each link is guaranteed, provided that the present state x falls in A
.
Since A is constructed on the basis of R,, it inherits the property of coordinate con- vexity. The coordinate convexity of A makes it easier to evaluate the system performance.Define X(t) to be the system state a t time t. X(t) is a continuous-time stationary Markov process which takes on values from the state space A
.
The transition rate from state x, to state q , denoted as q(xm1xn), a r e given byA;, if x,, = x,+e, and xn E A is the a-th component of x,. otherwise
x,, if Xn = xm-ei, X m E A a d x i
{ o
(3)dxm, xn)
=
The equilibrium state distribution p(x) should satisfy the equilibrium equations:
p(xn) q(xn,xm) = P ( X m ) q ( X m , X n ) r X, E A (4)
X,EA X,EA
Then we proceed to find the equilibrium state probabil- ity p ( x ) . Due to reversibility( p a n 9 2 ] ) , the local balance equations lead to
P ( X ) A i = P(X
+
ei) Pi (.i+
1) 1Using equation (5) repeatedly, one can build up a product form solution of the state probability as follows:
for x , x
+
e; E A. ( 5 )for x E A
3.3
System Performance
In this subsection, three measures of the system per- formance are used: The call blocking probability for each stream, the average link utilization, which represents the efficiency of network resources, and the normalized band- width update frequency, which indicates the network man- agement cost on adjusting bandwidth for traffic streams.
We define two sets of states for stream i: and A,.
K;
z
(XI.
E A and x+
ei $! A) (8)A; E {xlx E A -
K;
and z i / s ; is an integer} (9) The definition ofK;
implies that the incoming calls of stream a are lost when the state x is in&.
The defini- tion of Ai implies that in these states, the incoming calls of stream i are accepted while the bandwidth should be reallocated for stream i.For stream a, the call blocking probability, denoted as
B,, is given by
Ba = A x ) . (10)
X E Ki
The expectation of z;, E ( z ; ) (i = 1,2,
- -
-,
N),
is derived as follows.Owing to the coordinate convexity, equation (11) can be written as
Hence E ( z ; ) can be related to B; by the following equa- tion.
E ( z ; ) = f i (1 - B i ) (13)
On link r, the average bandwidth occupation is given by
E:,
6,, bt, E ( z i ) . Summing over all links and divid- ing it by total link capacity, one obtains the average link utilization of the whole system, denoted as Uz.Note that the numerator in equation (14) can be re- garded as the summation of E ( z ; ) weighted by a factor The probability that an incoming stream-i call necessi- ~ : = 1 birbt,.
tates bandwidth reallocation, denoted as F;, is given by F; = p ( x ) .
XE A;
The overall bandwidth reallocation frequency is given by
xzl
F;
Xi. Normalizing it by the total cali arrival rate, one obtains the normalized bandwidth update frequency, denoted as F.(16)
4
Numerical Results And Opti-
E:'=,
Fi X iF =
CL14
mizat
ion
Rules
In order to investigate the effect of the dynamic band- width allocation scheme, we first study a single link system in the following scenario.
The transmission link has a capacity of 150 Mbps, corre- sponding to the transmission capability of a SONET STS- 3c line. The link accommodates two traffic streams. The first stream consists of CCITT El circuit-emulated VCs which has a capacity of 2.048 Mbps. The second stream is composed of CCITT E-3 circuit-emulated VCs with ca- pacity equal t o 34.368 Mbps. Since a E 3 circuiit occupies more than one fifth of the link capacity, the value of 3 2 is
always set to 1. Conversely, the bandwidth of E-1 is quite small, therefore the value of SI can be set to be in the range from 1 t o 17. The maximum value 17 is nearly the ratio of E 3 bandwidth to E-1 bandwidth. Our consider- ation is that further increasing of 31 has similar effect as
simply using E-3.
The offered traffic load for stream i, denoted as ai, is defined to be the traffic intensity fi multiplied by basic bandwidth requirement b,. All offered traffic loads are giv-
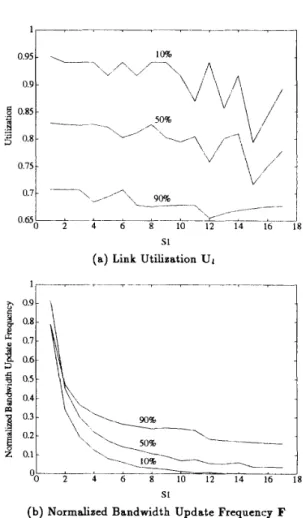
en in Mbps. The total offered traffic load of the 2 streams is 200 Mbps. The proportion of stream-2 load is set to be lo%, 50%, and 90%. The utilization and bandwidth update frequency are shown in Figure l ( a ) and (b), re- spectively. As the proportion of offered traffic load of E-3 increases from 10% to go%, the resultant utilization Ul decreases and F increases. As the E-3 traffic dominates, the variance of U1 to 31 is small. It is found that the u-
tilization does not decrease monotonically with respect to
SI. The difference in utilization under various s1 could be as large as 0.15, and the difference in normalized band- width update frequency could be up to 0.8. That is, the performance could vary significantly with different values of 3%. Therefore the selection of is of critical importance. In spite of the large variance of utilization, the peak val- ues are pretty close, with the difference of a t most 5%. In addition, the normalized bandwidth update frequency is nearly 1.0 for small values of SI. However, as s1 increases
to 6, the bandwidth update frequency soon settles down to a small value. As a result, it is possible t o choose an appropriate value of s1 such that the bandwidth update frequency is dramatically reduced, while the utilization does not degrade significantly.
Opthisation Rules
Based on the above observations, an intuitive way to choose is proposed. The basic idea
is
to find the maxi- mum Ul within the region where the value of F is accept- able.Optimization Problem 1
max U[
S i (17)
subject to F
5
F'where F' is a given constant, 0
<
F'5
1.0 The solution of this optimization problem, if any, guar- antees an acceptable frequency of bandwidth update. However, under some traffic conditions, there could be no feasible solutions. The search of s; according to (17) is called optimization rule 1. Alternatively, relative con- straints could be set instead of absolute constraints. One can set constraint on U[ and minimize F. As depicted before, the utilization reaches maximum a t s; = 1. Hence one can constrain U1 to be slightly lower than the maxi- mum value. The second type of optimization problem can now be described as follows.Optimization Problem 2
~-
min F (18)
6 ;
subject to U1
2
K* x U ~ ( M ~ = )where U ~ ( M ~ = ) is U2 obtained under S i = 1,
and K* is a given constant, 0
< K*
5
1.0 The search of si according t o (18) is referred to as o p timization rule 2. Since it is impossible t o predict the behavior of U[ with respect to si, the only way to ob- tain the optimal solution of either problem is exhaustively search the entire set of si's.In the following the results obtained with the two op- timization rules are presented. Let there be two streams, where stream 1 is
E-1
type and stream 2 is E 3 type. The offered traffic load of stream 2 is 10 Mbps and the offered traffic load of stream 1 is varied from 50 Mbps to 140 Mbp- s. Shown in Figure 2 are the utilization and normalized bandwidth frequency versus E-1 load. Both optimization rules are used. The constant F* for rule 1 is set to be 0.4, while the constant K' for rule 2 is 0.98. The curves of U[ and F for s; = 1, ( i = 1,2) are also presented. As depict- ed previously, s, = 1 leads to largest values of both U2 and F. The maximum degradation of U[ under the two rules, however, does not exceed 2%. Note that U2 under optimization rule 1 is higher than that under rule 2 with F' = 0.4 andK'
= 0.98. On the other hand, F with s i = 1 is nearly 1.0, while the values of F under rule 1 and rule 2 are about 0.4 and 0.1, respectively. This implies that one can reduce F significantly while at the same time retainshigh utilization. Using optimization rule 1, the reduction of F is about 0.6, and the loss of U2 is around 0.5%. Using optimization rule 2, the reduction of F is about 0.9, and the loss of U2 is around 2%. One c a n select one of the two rules according to his need.
In order to illustrate the validity of the multiple-link system model, we study another example with two par- allel links as shown in Figure 3. Stream 3 and stream 4 are E-3 traffic streams and traverse link 1 and 2, respec- tively. Stream 0 is composed of
E
l
calls and can traverse either link. The routing ficility decides the route for each incoming stream-0 call according to a random number, with probability q to link 1. Then stream 0 is implicitly separated into two independent streams, stream 1 and 2. Therefore the average link utiliiation U[ and the normal- ized bandwidth update frequency F of this system can be obtained using the model and analytical results presentedin Section 3. It is found that one can " i i e the av- erage link utilization by using a line search algorithm to find the optimal routing probability 9 ' .
The optimized results of this two-parallel-link system are presented in Figure 4. Suppose both links have c ~ r pacity 150 Mbps. The offered traffic loads are set to be
a0 = 200 Mbps, a3 = 10 Mbps, and a4 = 40 Mbps. First, the line search algorithm is used to find q' under all pos- sible values of bandwidth allocation units si's. Then the optimization rule can be employed to find optimal band- width allocation units. In this figure, only the results with
si = 1 (i = 1,
. .
.,
4), and those obtained using optimiza- tion rule 2 with constant K* are shown. Again, the loss in utiliiation U2 is quite small, while the reduction in nor- malized bandwidth update frequency F is significant.5
Conclusions
In this paper, a dynamic bandwidth allocation scheme is studied. Under the scheme, the bandwidth allocation size is set to be an integer multiple of the basic bandwidth requirement. Hence the bandwidth control and the con- nection acceptance control do not need to be done on a call-by-call basis. A control procedure combining the dy- namic allocation scheme and the connection acceptance control is also discussed. Besides, the analytical and nu- merical results are presented. In the numerical examples, it is found that the dependence of the system performances on the values of bandwidth allocation units can not be predicted intuitively. Therefore it is necessary to search the entire set of bandwidth allocation units to find o p timal values. Two optimization rules are proposed: one maximizes the utilization subject to acceptable values of the normalized bandwidth update frequency, and the oth- er minimizes the normalized bandwidth update frequency subject to acceptable degradation in utilization. One can
employ any one of the rules and set the constraint param- eters to meet his purpose.
As
a result, the dynamic allo- cation scheme could be highly efficient in resources usage, and at the same time reduce the bandwidth management cost significantly.[TlSSO] TlSl.5/90-001 R1, Broadband Aspects of ISDN, Baseline Document, Draft, August 1990.
[Wan921 W. D. Wang, Design and Analysis of The Labeled- Multiplexer in ATM Networks, Master Dissertation, National Taiwan Univ., June 1992.
References
[Aei78] J. M. Aein, “A Multi-user-class, Blocked-calls- cleared, Demand Access Model,” IEEE Trans. Com- mun., Vol. COM-26, pp.378-385, Mar. 1978. [CC1891 CCITT Recommendation 1.121, Broadband Aspects [GANSl] R. GuCrin, H. Ahmadi, and M. Naghshieh, “Equiva- location in High Speed Networks,” IEEE J. Selec- 1991.
of ISDN, Blue Book, Geneva, Switserland, 1989. lent Capacity and Its Application to Bandwidth Al-
t. Areas Commun., vo1.9, N O . ~ , pp.968-981, Sept. 1 W O
_ _ -. l ~ - -__-. ~ ~ - _ . 8 0.85
[GriSO] T. R. Griffiths, ”Analysis of a Connection Accep- tance Strategy for Asynchronous Transfer Mode Net-
1990.
5
0.80 75 works,” PKOC. GLOBECOM, pp.505.4.1-505.4.7,
....
3
[Hui88] J . Y. Hui, “Resource Allocation for BroadbandNetworks,” IEEE Trans. Commun., vo1.6, No.9, pp.1598-1608, Dec. 1988.
[JoVSl] S. Jordan and P. Varaiya, “Throughput in Multiple Service, Multiple Resource Communication Network-
s,” IEEE Trans. Commun., vo1.39, No.8, pp.1216- 1222, Aug. 1991.
[KHBSl] H. Krijner, G. HCbuterne, P. Boyer, and A. Gravey, “Priority Management in ATM Switching Nodes,” IEEE J. Select. Areas Commun., Vo1.9, No.3, pp.418427, Apr. 1991.
[MSSSl] T. Murase, H. Susuki, S. Sato and T. Takeuchi, “A Call Admission Control Scheme for ATM Networks Using a Simple Quality Estimate,” IEEE J. Selec- t. Areas Commun., Vo1.9, No.9, pp.1461-1470, Dec. 1991.
[MSTSl] T. Murase, H. Susuki, and T. Takeuchi, “A Call Ad- mission Control for ATM Networks Based on Individ- ual Multiplexed Traffic Characteristics,” Proc. ICC, [OhS92] S. Ohta and K.-I. Sato, “Dynamic Bandwidth Con- trol of the Virtual Path in an Asynchronous Trans- fer Mode Network,’’ IEEE Trans. Commun., Vo1.40, pp.6.3.1-6.3.6, 1991. No.7, pp.1239-1247, July 1992. 2 0.9 - C
$7
o.8- 0.7 -8
0.6- 3f
0.4- p?3
0.5 -1
0.3 -G
7 0.2- 2 0.1 - O k - SI(b) Normalized Bandwidth Update Frequency F [OST88] S. Ota, K.-I. Sato, I. Tokizawa, “A Dynamically Con-
trollable ATM Transport Network Based on the Vir- tual Path Concept,” Proc. GLOBECOM, pp.39.2.1- 39.2.5, 1988.
[SOT901 K.I. Sato, S. Ohta and 1. Tokisawa, “Broad-band AT- M Network Architecture Based on Virtual Paths,”
IEEE
Trans. Commun. vo1.38, No. 8, pp. 1212- 1222, Aug. 1990.Figure 1: Performance versus Bandwidth Allocation Unit
( 2 ) optunmbon Rule 1 (3) optunvxbon Rule 2 0.9
g
o.8- .g-
0.7-3
4
0.6- 48
0.5 U 0.4- 0.3 O.Zo- 050 60 . 70 380 90 L 100 -110 120 I 130 140 Offered Lmd of E; 1 Traffk (a) Link Utilisation Uil
r
7
-?
- - - 0.9 0.8- 0.7 0.6-q
0.5 - - -Offered Lcad of E-1 Traffic
(b) Normalized Bandwidth Update Frequency F Figure 2: Performance versus Offered Load of Stream 1, Under Both Optimieation Rules. a1 = 50
-
140 Mbps,a2 = 10 Mbps, F' = 0.4, K' = 0.98. (1) Sl=S2=1 (2) optunmhon Rule 1 - (3) 0pt1111mhm Rule 2 stream 3 Link 1 stream 1
I
-
Routing Facility \~-
Link 2 .%em 2 stream41
. I--'
r--
K'
(2) Optuniznhon Rule 2 (1) s1=s2=1!
I//
---A 50 100 150 200 250 300Offered Load of ElTraffic (a) Average Link Utilisation U L
I
-
-
-
.
-
-\---
-
-. (1) s1=s2=1 (2) Optunlwthon Rule 2 m 50 100 150 200 250 Offered L a d of E- 1 Traffic(b) Normalised Bandwidth Update Frequency F Figure 4: Performance versus Offered Load of E-1
Traffic-
s, with Optimal Routing Probability, under Optimization Rule 2. a0 = 15-
300 Mbps, a3 = 10 Mbps, a4 = 40Mbps, K' = 0.98.
Figure 3:
Routing