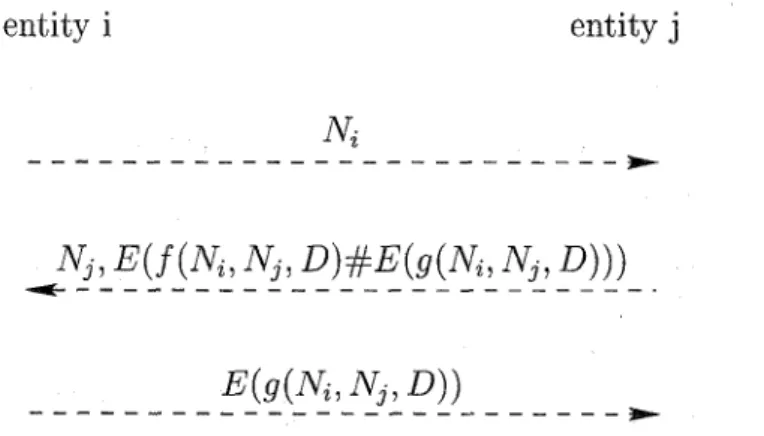Efficient End-to-End Authentication Protocols for
Mobile Networks
Cheng-Hsin Chang: Kwei Tuf and Kwang-Cheng Cheni
Abstract
For conventional authentication protocols, distribution of session keys and maintenance of large databases are seri- ous problems especially for large-scale wireless networks. ID-based authentication protocol eliminates the problem while it contributes the heavy computation load. We pro- pose a hybrid end-to-end authentication and key agree- ment (AKA) protocol which provides authentication and key exchange between both end entities. It not only elimi- nates the drawbacks of conventional protocols but also re- duces the computation load. Services of message confiden- tiality, caller ID confidentiality, service request intractabil- ity, and fraud control are provided. Roaming and han- dover, are also taken into consideration here.
1
Introduction
With dramatic development of mobile networks, more and more information is transmitted via radio communications. While wireless communication is inherently less private than wire-line communication since wireless (radio) com- munication
For conventional approaches t o achieve privacy and au- thentication, it is necessary for the communication entities to share a session key which is known to no one else. This is done by sending the key in advance in secure way. How- ever, a private conversation among entities with no prior contact is a common occurrence. Thus, the key distribu- tion problem is a major obstacle to large-scale networks.
In modern large-scale telecommunication networks, it is required that each entity is able to communicate with ar- bitrary entities through the network. However, key man- agement is a serious problem in private-key cryptosystem (e.g., DES or triple DES) and public-key cryptosystems (e.g., RSA), if the system contains a vast amount of enti- ties.
In 1984, Shamir proposed the concept of an ID-based system [2], i.e., an ID-based cryptosystem and an ID-based
*The author is with Powerchip Semiconductor Corp., 12, Li-Hsin t T h e author is with LinCom Corporation, 1020 Bay Area Blvd., $The author is with the Department of Electrical Engineering, National Tsing Hua University, Hsinchu, Taiwan 30043, R.O.C.
E-mail:chenkc@euler.ee.nthu.edu.tw
RD. 1, Hsinchu, Taiwan, R.O.C. E-mai1:keynesOccmail.psc.com.tw #200, Houston, U.S.A.
signature scheme, as a countermeasure for key manage- ment in large-scale networks. No public directory is re- quired in the system. Tsujii and Itoh [5] proposed an ID-based cryptosystem based on the discrete logarithm problem. Most recently, Harn and Yang [6] also proposed
three identity-based cryptographic schemes based on the discrete logarithm problem in GF(p), where p is a large prime. Their scheme is based on the Agnew
et
al. digitalsignature scheme [4], which was due to ElGamel’s signa- ture scheme [3], and can provide user identification, digital signature, and key distribution.
Now, wireless networks are being driven by the massive need for providing network access to mobile computing devices. Therefore, the radio link between the portables
and an array of ports is susceptible to eavesdropping. In earlier papers [8], [9] and [lo], several protocols employed conventional or public-key cryptographic technology to ac- complish key agreement and authentication. Several con- cerns or requirements are also addressed in [ll], and [12]. However, authentication and privacy are generally linked together since the derivation of a “session key” for an en- cryption algorithm is often an integral part of the authen- tication process [ll]. The access control and derivation of a session key form a single activity called Authentication
and Key Agreement (AKA) from the designer’s perspec-
tive. This is our major concern. Thus, the subsequent use of the session key t o encrypt the traffic of users can be treated as a separate topic.
2
A
Hybrid End-to-End
AKA
Pro-
tocols
In order to eliminate the requirements of a large database t o hold all the session keys which are used to establish con- nections for conventional approaches, and the heavy load contributed by the exponential computations of ID-based authentication protocol. We propose a hybrid protocol and use cache to maintain the session keys set up by the mod- ified ID-based authentication protocol.
Furthermore, the end-to-end authentication is also our concern. With link authentication, two entities must be directly linked. If two entities are far apart, they have
to authenticate with any neighboring entity ( e . g . , switch),
and have t o set up the session key with it. Thus, the message is vulnerable a t each intermediate entity and it
is inefficient since each intermediate entity on the routing path has to decrypt and encrypt the message once. Here, we construct our hybrid protocol with the modified ID- based protocol part [6] and a canonical protocol part [7].
server
k
user i
2.1
The Modified ID-Based Protocol Part
First of all, we briefly introduce the initiation phase, user registration phase, and application phase of the ID-based cryptosystem.In the initiation phase, the KAC selects a large prime p, and primitive element a of G F k ) publicly. An odd random z E [ l , p
-
11 is also selected as its private key and the public key, Y = a" mod p. In the user registration phase, the KAC computes an extended identity E I D i foruser i as
E I D , = h ( I D , ) ,
and the signature (r,, s a ) of E I D , as
si = ( E I D i - kiri)z-' mod (p - 1)
where ri = akt mod p and ki E [ l , p - 11 is random. Fi- nally, challenge-response procedure is applied in user iden- tification phase. The challenge and response are as follows respectively:
W
=Y y
mod p2
=W S i
mod pAnd, the identification procedure is to verify if
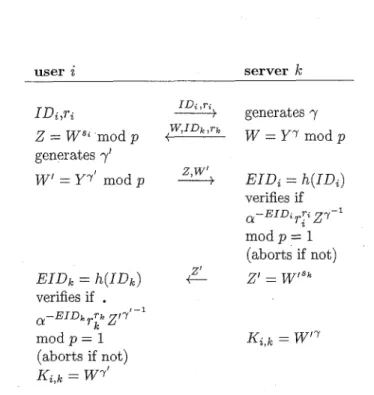
Mutual authentication in large-scale networks can be achieved by adding another ID-based user identification scheme in the opposite direction. Anyway, the negotiation of setting up a session key is also necessary due to the connection of two entities. In such case, we embed Diffie- Hellman key exchange protocol [l] at the end of mutual authentication. Table 1 shows such simple mutual authen- tication of user i and server
k
where h ( ) represents the hash function chosen by the KAC. Steps are executed from top to bottom.However, this simple protocol cannot resist some attacks from the intermediate node if user
i
and server IC are di-rectly linked. Assume the caller which invokes the con- nection knows the identity of the called entity. The inter- mediate node can still replace the identity of the caller, and the corresponding challenge and response. Thus, the session key set up is the same for caller and the intermedi- ate node. And, the sensitive information is disclosed if the caller sends it out immediately after authentication. Table 2 provides a more secure protocol to resist such an attack in an intuitive way. Here, E ( K , M ) and D ( K , M ) denotes the encryption and decryption algorithm with the key, K ,
and the message, M .
IDi,ri
Z
= W s ; mod p generatesy'
W' = Y y ' mod p EIDk = h ( I D k ) verifies if.
m o d p = 1 (aborts if not) Ki,k = W y ' a - E I D ~ r p Z l Y ' - l I D ; ,T; w , I D k ,Tk generates y W = Y r mod p 2, W'---+
EIDi = h ( I D i ) a - E I D ; r p 2 y - l verifies if m o d p = 1 (aborts if not) Z'z/
= w/skc
Table 1: A simple mutual authentication protocol with key exchange entitv i entitv i IDi,ri
Z
= W s i m o d p generates y' W' =Yr'
mod p Ki,j = WY' E I D j = h ( I D j )2'
= D ( K i , j ,2:)
verifies if a - E I D j r r ~ zd-l II m o d p = 1 (aborts if not) I D , ,r+ w > ( I D J ) > T J Z,W'+
verifies if generates y W = Y Y m o d p E I D , = h ( l D , ) a - E I D . r r ~ y - l m o d p = 1 (aborts if not) K3,, = W",z:
z;
=E(K,,,, W f S J )Table 2: Modified mutual authentication and key agree- ment protocol
MU
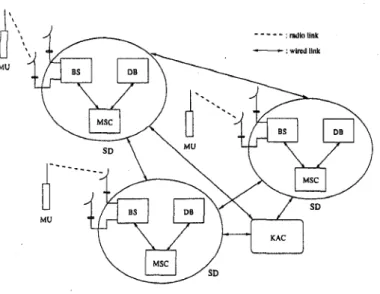
Figure 2 : System architecture for the GSM and PCS like communication systems
portable unit's equipment, and makes E I D as the output
of an non-invertible function with U I D and P I D as its
inputs, e.g.,
EID
= h ( U I D11
P I D ) , where h ( ) is an one- way hash function and11
stands for concatenation. Thus, the verification of subscriber equipment is also accompa- nied with the entity authentication.Usually, party anonymity and caller confidentiality are maintained by substitution of an entity's identity by a temporary identity which is updated upon every new call. In order to overcome the problem of location registration which performed by the network for a particular mobile station. That is to effectively hide the real identity from attackers needs to protect the identity even when the sub- scriber just roams into a VSD and no temporary identity is present. The public key cryptographic technique, i.e., RSA scheme
,
is used to improve the caller ID confiden- tiality. Here, g ( e , m ) is used to denote all the ciphertext of m encrypted using public key e.The two AKA protocols are illuminated respectively as follows:
Link Authentication Protocol
Whenever a call is made after an entity roams into a VSD, the authentication process is initiated. The portable unit (entity) authenticates with the VSD and sets up a session key. An temporary identity is also assigne'd to the entity. We call it t h e initial p a r t of the
authentication protocol. Given the session key and the temporary identity of the entity are present, an efficient protocol is provoked and we call it t h e basic part of the protocol. For reducing the exchange of information between HSD and VSD, the generation of the signature pair ( T , s ) for the mobile unit can depend on his identity, account number, and the life time of the account. Thus, successful authentication denotes the correctness of his identity, equipment identity and etc.
Table 3 and
4,
which are similar to Table 2 , show the initial and basic parts of the protocol respectively. Here, the variable, ymin is as follows:if T I D i
<
S D I D je n t i t y 1
m , = U I D , I I P I D , I I f N F O c, = g(e,.m, II rJ
2 = mod p
generates a random number 7'
CV' = Y7' mod p
E I D , = h(SDID,)
2' 11 T I D , = D(K,,, 2:)
verifies if a-ErD,~:Z'"-' mod p = 1
(aborts if not) records ( T I D , , KaJ)
for next call
K,,, = Wl'(= Y7.7')
VSD 3
generates a random number m, ll r, = s(d,,c,)
checks I N F O to see i f expired
W = Y7 mod p
E I D , = h(m,)
(aborts if not)
Z: = E(K,,,, W'"' I1 T I D , )
records (TID,, K, ,, UID,* I N F O ) for next call
.% ~v.(soro, IT, --+ 2.W' verifies if a- E r of ' Z7-' mod p = I K,,, = W'T(= Y7l') &
Table 3: The initial part of link authentication protocol
e n t i t y i VSD j
generates a random number -( extracts K,., t , = E(K,,, 7 0 70 m, = D ( K , , , c , ) verifies if mi = (hln 0 S D I D , 0 1,) I[ T I D ; (abort if not) extracts TID; from mi
records ( T I D ; , K , J )
for next call
--+ I',TIDi extracts K,,i,flVFO according to T I D i
checks I N F O to see if expired
generates a random number 7
assigns a temporary ID, TIDI ti = E(Kj,,, 7 0 70
C, = E(Kj,i, (7" 0 S D I D j 0 t j ) [I T I D : )
Ir, verifies if t , = t ,
(abort if not)
records (TID:, K ,,,, U I D , , I N F O ) for next call
Table 4: The basic part of link authentication protocol
End-to-End Authentication Protocol
In order to achieve end-to-end security and protect all the signaling information, an extra link encryption is necessary. Thus, our end-to-end authentication pro- tocol consists of end-to-end section and link section. The former is used to authenticate the called entity and the latter is used to authenticate the VSD by the caller. Whenever a call is made after an entity roams into a VSD, the authentication process is initiated. First, the portable unit (entity) authenticates with the
VSD
and sets upa
session key which is used t o encrypt the signaling information. After successfully authenticated, VSD forwards the challenge of caller to called entity if both entities do not have a shared key, or VSD challenges caller and forwards its response to called entity given that a session key is shared by both2.2
The Canonical Protocol
Part
The modified ID-based mutual authentication protocol re- quires more than three modular exponentiations. Even though one exponentiation, i.e., the challenge, doesn’t need to be done in real time, the computational load is still heavy especially for a portable unit. Thus, we adopt t h e canonical protocol which can resist chosen ciphertext at- tacks, oracle session attack, and parallel session attack as
an alternative part of our hybrid protocol. Figure 1 shows the general form of the canonical protocol. The function,
E ( ), denotes a symmetric one-key encryption algorithm.
Ni
andNj
are nounces which are the challenges of entity i and j , respectively. D stands for the parameter indicat- ing or tied to the direction of the flow. Here, we assume function E ( ) is one-way with cryptographic strength, andthe intuitive but unproven notion that f ( ) and g ( ) are cryptographically separate.
#
can be any bit-operation function.This protocol can also resist the attack mentioned above by intermediate node. The session key used to en- crypt and decrypt does not appear the figure, and is gen- erated by the modified ID-based authentication protocol. The requirements forf()
and g ( ) is not addressed here.entity
i
entity j
Ni
Figure 1: Canonical protocol with minimal number of en- crypt ion
2.3
The efficiency analysis
Our above analysis guarantees the hybrid protocol to resist the attacks by intermediate nodes, and thus, end-to-end authentication is achieved. However, efficiency is our ma-
jor concern and depends on the hat ratio of the cache which
is used to store the used session keys generated by the modified ID-based protocol. An auxiliary strategy, called
per-entity caching, is proposed for storing the latest used
private session keys. The object of caching is to reduce the computation and communication loads of authentica- tion protocol in exchange of memory costs. It will be very useful when the requests t o or from some specific entities are more relatively frequent than other entities.
Analytical models are established, and three different replacement policies of cache are investigated based on
reasonable assumptions [13]. Without considering expz- ration of session keys, it is demonstrated that Least R e - cently Used (LRU) scheme provides the highest cache hit
ratio. Asymptotic analysis and simulations are also pro- vided t o verify the analysis of hit ratio. This investigation also shows that LRU scheme provides a better capability of reusing session keys, and is the best countermeasure with smallest size of cache to achieve a fixed hit ratio.
3
AKA
Protocols for Mobile Net-
works
Easy access to radio links makes wireless communication susceptible to the exposure of sensitive information and fraudulent use of the services. These threats may come from outsiders or insiders due to the collection of informa- tion on the radio link or the privilege t o access system’s secret information. Two AKA protocols are proposed to provide services such as message confidentiality, caller
ID
confidentiality, call intractability, and fraud control on mo- bile network, end-to-end authentication instead of link au- thentication is also the achievement we reach.
3.1
System Architecture
As shown in Figure 2, the portable unit (entity) commu- nicates through radio with base stations (BS) which are connected to mobile switching centers (MSC). The MSC is a bridge to the existing wireline network. Another signifi- cant component, the authentication center (AC)
,
performs the vital authentication process for each call requested. MSCs, BSs, and the AC collectively form a service domain (SD). Each service domain is owned by a service provider and may cover a metropolitan area or even a larger re- gion. Here, we assume the SDs are not mutually trusted. Any entity which wants to have the wireless communica- tion services needs to register itself with a SD, called h o m e service d o m a i n (HSD), and becomes a visiting subscriber to another SD, called visiting service d o m a i n (VSD).3.2
AKA Protocol for Mobile Networks
Here, we propose two different authentication protocols. One provides only link-to-link encryption and authentica- tion while the other provides end-to-end encryption and authentication. The former relies heavily on the existing wireline network while the later reduces the complexity of the wireline network but adds some loads on the portable unit. The basic protocols applied are based on the hybrid protocol in the above section.Similar t o the procedure in the ID-based authentication protocol, each subscriber obtains a signature pair (r, s) of its own E I D , and a unique identification, U I D , with its HSD upon registration phase. The signature pair is stored in the portable unit and s is physically protected from ex- posure. If we assign P I D as the unique identity of the
entities. The protocol how VSD challenges caller en- tity is shown in Table 5. After called entity verifies and returns its response to caller, the authentication is complete.
entity i VSD j
generates a random number 7‘
extracts K,,k F ~ = r j ) ) t
G = E(&, (%in 8 U I D i @ t i ) ) % forwards ci,T,y’,UIDi to entity k verifies if t, = tk
+
receives response tk from entity k(aborts if not)
generates a random number rj
t, = E( Ki,kp 7 8 7‘)
Table 5: Challenge to caller from VSD which is in place of called entity
Given that there is already a session key shared by the portable unit and VSD, VSD first identifies the portable unit before allowing it to access mobile net- work. Table 6 shows how VSD identifies the caller entity given a session key Ki,j is present.
e n t i t y a VSD 3
generates a random number 7‘ % extracts Kl,, according to TID,
extracts K,,] (I- generates a random r, = r /I t
ti = E(K,,j,-/ 8 7‘) verifies if t, = E(K,,,, 7 8 7‘)
(aborts if not)
assigns a temporary ID, T I D :
records ( T I D ; , K,,,, UID,, IiVFO)
for next call
E(K,,..TrD:l
extracts TID:
records (TID:, IT,,>)
for next call
Table 6: Protocol for identification of caller
4
Conclusion
The security analysis [13] is not addressed here, and the security of our protocols is based on computing discrete logarithm over GF(p), factoring a large prime product, and deriving the unknown key of the symmetric encipherment algorithm. Two protocols, link and end-to-end authentica-
tion, for mobile networks are based on the hybrid protocol and proposed here. End-to-end authentication protocol can resist the attacks from insiders, while requires an ad- ditional protocol to protect signaling information. With high cache hit ratio, the computation load is significantly reduced.
References
W. Diffie and M. E. Hellman. “New directions in cryptography.” IEEE trans. Info. Theo y , vol. IT-22,
A. Shamir, “Identity-Based Cryptosystem and Signa- ture Scheme”
,
in Advances in Cryptology: Proceedingsof Cypto ’84, Berlin, West Germany: Spring-Verlag,
T. ElGamal, “A Public Key Cryptosystem and a Sig- nature Scheme Based on Discrete Logarithms,” IEEE Trans. Info. Theory, Vol. IT-31,no.4, pp.468-472, July 1985.
G. B. Agnew, R. C. Mullin, and S. A. Vanstone, “Im- proved Digital Signature Scheme Based on Discrete Exponentiation”
,
Electronics Letters,Shigeo Thujii, and Toshiya Itoh, “An ID-Based Cryp- tosystem Based on the Discrete Logarithm Problem”,
IEEE
J.
on Selected Areas in Comm., vo1.7, no.4, May 1989.Lein Harn and Shoubao Yang, “ID-based crypto- graphic Schemes for User Identification, Digital Sig- nature, and Key Distribution” IEEE J. Select. Areas
Comm., Vol. 11, no. 5, pp. 757-760, June 1993. Ray Bird, I. Gopal, Amir Herzberg, Philippe A. Jan- son, Shay Kutten, Refik Molva, and Moti Yung, “Sys- tematic Design of a Family of Attack-Resistant Au- thentication protocols” IEEE
J.
Select. Areas Comm.,Vol. 11, no. 5 , pp. 679-692, June 1993.
H. Y. Lin and L. Harn “Authentication in Wireless Communications”
,
Proceedings, IEEE Glo becom ’93,pp. 550-553, December, 1993.
Kwei Tu, “An ID-Based Authentication Scheme in Wireless Communications”
Michael
J.
Beller, Li-Fung Chang, and Yacov Yacobi, “Privacy and Authentication on a Portable Commu- nications System”, IEEE J. on Sel. Areas in Comm. ~01.11, no.6, pp. 821-829, Aug. 1993.Dan Brown, “Techniques for Privacy and Authenti- cation in Personal Communication Systems”, IEEE Personal Communications, v01.2, no.4, pp. 6-10, Au- gust 1995.
Joseph E. Wilkes “Privacy and Authentication Needs of PCS”
,
IEEE Personal Communications, v01.2, no.4, pp. 11-15, August 1995.C. H. Chang, “Efficient End-to-End Authentication Protocols for Mobile Networks”, Master thesis, Tsing Hua Univ., 1996.
pp.644-654, NOV. 1976.