Research Express@NCKU - Articles Digest
Research Express@NCKU Volume 14 Issue 3 - June 4, 2010
[ http://research.ncku.edu.tw/re/articles/e/20100604/3.html ]
A Healthcare Monitoring Architecture with Adaptive
Security Policies
Yueh-Min Huang
1*, Meng-Yen Hsieh
2, Han-Chieh Chao
3, Shu-Hui Hung
1National Cheng Kung University1 Providence University2 National Ilan University3 huang@mail.ncku.edu.tw
IEEE JSAC 27(4) May 2009
D
ue to the rapid progress of wireless network technology, healthcare systems can remotely monitor the elderly or chronic patients in their residence. This research adopts a secure sensor-based healthcare architecture built over three heterogeneous wireless networks. Adaptive security schemes are designed and built on the proposed architecture to protect sensing data transmitted through a variety of wireless technology. Using the proposed architecture, we implement a prototype, and effectively validate the proposed security mechanism.Figure 1: Adaptive security policies applied to the healthcare monitoring system.
The secure sensor-based healthcare architecture is divided into three different heterogeneous networks. The sensor network is the first tier, including two different sensing systems. The wearable sensing system, namely WSS, formed with the cloth belt and chest belt is comfortable to patient's body. The system coated the Bluetooth
transmission component and a number of bio-sensor to collect patients' physiological signals. Environmental wireless sensor nodes, called WSM, are distributed over the rooms of patient living buildings to catch the
environmental physical parameters. The WSS and WSM are authenticated to safely send physical sensing data, and to access other network tiers. The second tier is a mobile computing network, organized by a number of mobile computing devices, denoted as MCD (e.g. PDA, notebook) This tier as a wireless local area network connects a fixed base station with multi-hop ad hoc wireless connection. One MCD with sufficient computing capability can capture and analyze physical sensing data from WSS or WSM. However, without significant storage capacity, it cannot store long-term sensing data for months or years. By the infrastructure mode, any MCD can route sensing data to the back-end base station in WLAN. The back-end Internet layer is the third tier, consisting of application services in a fixed server to process and store a variety of sensing data from MCDs. The database in the server can be stored long-term and a large number of patient's physiological and environmental sensing data. Figure 1 represents the adaptive security mechanisms applied the three network tiers to protect sensing data over various wireless technologies
Security Protocol between WSS and MCD: Since one MCD in PicoNet can connect multiple WSSs, the value
of a group-based session identity is as the hashing value with the MCD identity and the access code of one PicoNet channel:
Research Express@NCKU - Articles Digest
GSIDMCD : GSIDMCD : GSIDMCD = Hash(MCDindex CACp)。
Although the Bluetooth defines the authentication, confidentiality, and key generation with the SAFER+
cryptographic algorithm, the middle attacks and reply attacks could be occurred such that sensing data received by MCD is not correct. The WSS adapts the AES encryption method to modify the authentication process to enhance the Bluetooth transmission security, while the security is designed to the HCI (Host Controller Interface) of the Bluetooth standard. Four adjustable situations apply the 128-bit AES block encryption and message authentication code method to data transmission in the Bluetooth physical layer. There are the None mode, CBC-MAC mode, AES-CTR mode, and AES-CCM mode. The detail description for each mode is as the follows:
Polynomial-based symmetric encryption between WSM and MCD: Two WSM nodes achieve the point-to-point secure communication using polynomial-based encryption technology. The environmental sensing data is not important as the patient physiological sensing data, moreover, environmental sensor nodes are limited with computing and storage capacity. Therefore, using t-degree polynomial technique is more suitable than other symmetric encryption schemes for that one WSM and one MCD establish a shared key to data transmission. A 3-degree polynomial is defined as:
, where x1, x2, and x3 are variables.
When the value of one of three variables representing some location, LOC, is fixed, the MCD and the WSM can generate one common shared key using the t-degree bivariate polynomial after exchanging their ID code.
Symmetric encryption methods between two valid MCD devices:
Valid MCDs must be authenticated by the third-party CA to gain a symmetric key shared with the CA, and a pair of public/private key. To exchange data, any two of MCDs need first to establish a common key. For example, one patient held MCDi deliver sensitive data to the physical sensing to one nurse held MCDj Device. Suppose that an authenticated MCD shares a common key with the CA. If the two MCDs know the route, and be able to connect each other, the steps of establishing a common key between them as follows:
Research Express@NCKU - Articles Digest
If the two MCDs need to discover a route, the ARAN protocol is the appropriate solution. Suppose MCDi discovers a route to MCDj (Route: MCDi→A→B→MCDj).Through routing request packets (RREQ), the authenticated request procedures are as follows:
The authenticated reply procedures are as follows:
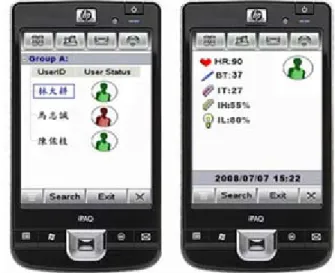
Figure 2: (Left)Group-based Monitoring;(Right) physiology records and physical parameters for an individual
Software implementation
The MCD applications are designed with a graphical interface to show the physiological and environmental sensing data. The applications supporting the HTTP protocol are implemented by Java API. As the heart beat or body temperature for a monitored person goes too high or low, the application will change the individual color from green to red as shown in Figure 8 (Left). Users can choose the screen of a patient, watching his own sensing data. Figure 8 (Right) shows an individual record consisting of heart beat rate (HR), body temperature (BT), indoor temperature (IT), indoor relative humidity (IH), and indoor relative light (IL). Moreover, the SOS/ emergency call out function or an alert message in the application has been raised up while records show unstable over a threshold value. Through the HTTP
connection, back-end applications implemented by Microsoft ASP.NET technology collect all important physical records from a great number of MCDs, storing them into a database for long-term storage and analysis.
System Security Analysis
Research Express@NCKU - Articles Digest
The enhanced Bluetooth encryption uses the hardware-accelerated AES cryptography instead of the SAFER+ encryption algorithm, reducing eavesdropping and attacks from malicious nodes. Two WSM nodes can achieve key agreement using a location-based t-degree bivariate polynomial. The WSMs in one location (LOC) need (t •1) log2q bits memory to store t+1 coefficients while each coefficient costs log2q bits. However, without
re-constructing the polynomial, a secure bivariate polynomial for a location scale should be used with the polynomial degree of satisfaction: 0≤N-2≤t, where N is the number of nodes in the LOC. Because the number of different coefficients for the polynomial is distributed, the minimum polynomial degree t* must satisfy the inequality:
, where N2 is the maximum number of WSM nodes in one location of the open area. In the mobile computing network tier, two valid MCD can establish a shared symmetric key through ARAN. Suppose the probability of compromising one MCD is p. A route path between the MCDi and MCDj consists m participants. The probability that the MCDs cannot establish a shared key, Keyi,j, with the route can be calculated as: Pc=1-(1-p)m。
Consequently, this research proposes adaptive security mechanisms applied to a sensor-based healthcare
monitoring system. We protect the sensing data and the privacy of data transmission in the heterogeneous wireless networks. In the future, the system will support secure IPv6 network to achieve the ability of pervasive access.