Data Hiding and Image Authentication for Color-Palette Images
全文
數據

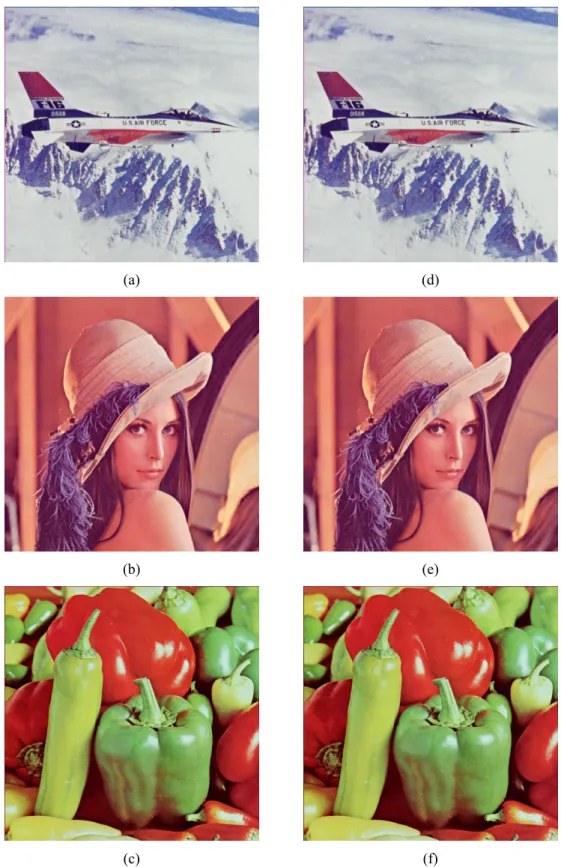

相關文件
In the third quarter of 2013, visitor arrivals increased by 6.6%; per-capita spending of visitors grew by 4.6%; exports of gaming services rose by 13.3% in real terms; guests of
The economy of Macao expanded by 21.1% in real terms in the third quarter of 2011, attributable to the increase in exports of services, private consumption expenditure and
In taking up the study of disease, you leave the exact and certain for the inexact and doubtful and enter a realm in which to a great extent the certainties are replaced
In this research, we use conventional RGB (Red, Green, Blue) images as input data. The conventional RGB image is demosaiced from raw image by using the color interpolation
Upon reception of a valid write command (CMD24 or CMD25 in the SD Memory Card protocol), the card will respond with a response token and will wait for a data block to be sent from
We do it by reducing the first order system to a vectorial Schr¨ odinger type equation containing conductivity coefficient in matrix potential coefficient as in [3], [13] and use
Wang, Solving pseudomonotone variational inequalities and pseudocon- vex optimization problems using the projection neural network, IEEE Transactions on Neural Networks 17
Define instead the imaginary.. potential, magnetic field, lattice…) Dirac-BdG Hamiltonian:. with small, and matrix
