Cheating Prevention in Visual Cryptography
Chih-Ming Hu and Wen-Guey Tzeng
Abstract—Visual cryptography (VC) is a method of encrypting
a secret image into shares such that stacking a sufficient number of shares reveals the secret image. Shares are usually presented in transparencies. Each participant holds a transparency. Most of the previous research work on VC focuses on improving two param-eters: pixel expansion and contrast. In this paper, we studied the cheating problem in VC and extended VC. We considered the at-tacks of malicious adversaries who may deviate from the scheme in any way. We presented three cheating methods and applied them on attacking existent VC or extended VC schemes. We improved one cheat-preventing scheme. We proposed a generic method that converts a VCS to another VCS that has the property of cheating prevention. The overhead of the conversion is near optimal in both contrast degression and pixel expansion.
Index Terms—Cheat-preventing, cheating, secret sharing, visual
cryptography.
I. INTRODUCTION
E
VEN with the remarkable advance of computer tech-nology, using a computer to decrypt secrets is infeasible in some situations. For example, a security guard checks the badge of an employee or a secret agent recovers an urgent secret at some place where no electronic devices are available. In these situations the human visual system is one of the most convenient and reliable tools to do checking and secret recovery. Therefore, Naor and Shamir [19] invented the visual cryptography (VC) in which a secret image (printed text, pic-ture, etc.) is encrypted in a perfectly secure way such that the secret can be decoded directly by the human visual system.VC is a method of encrypting a secret image into shares such that stacking a sufficient number of shares reveals the secret image. Shares are usually presented in transparencies. Each par-ticipant holds a transparency (share). Unlike conventional cryp-tographic methods, VC needs no complicated computation for recovering the secret. The act of decryption is to stack shares and view the image that appears on the stacked shares simply.
A -visual cryptography scheme [denoted as -VCS]
is a visual secret sharing scheme such that stacking any or more shares reveals the secret image, but stacking fewer than shares reveals not any information about the secret image.
VC has been studied intensively since the pioneer work of Noar and Shamir [19]. Most of the previous research work on VC focused on improving two parameters: pixel expansion and Manuscript received September 29, 2005; revised May 10, 2006. This work was supported in part by the National Science Council of Taiwan under Grant NSC-94-2213-E-009-110. The associate editor coordinating the review of this manuscript and approving it for publication was Dr. Ercan E. Kuruoglu.
The authors are with the Department of Computer Science, Na-tional Chiao-Tung University, Hsinchu, Taiwan 30050, R.O.C. (e-mail: andyhu@cs.nctu.edu.tw; wgtzeng@cs.nctu.edu.tw).
Digital Object Identifier 10.1109/TIP.2006.884916
contrast [5], [6], [8], [11], [13], [16], [23]. In these cases, all participants who hold shares are assumed to be semi-honest, that is, they will not present false or fake shares during the phase of recovering the secret image. Thus, the image shown on the stacking of shares is considered as the real secret image. Nevertheless, cryptography is supposed to guarantee security even under the attack of malicious adversaries who may deviate from the scheme in any way. We have seen that it is possible to cheat [12], [14], [18], [26] in VC, though it seems hard to imagine. For cheating, a cheater presents some fake shares such that the stacking of fake and genuine shares together reveals a fake image. With the property of unconditional security, VC is suitable for sending highly classified orders to a secret agent when computing devices may not be available. The secret agent carried some shares, each with a pre-determined order, when de-parting to the hostile country. When the headquarter decides to execute a specific order, it can simply send another share to the agent so that the agent can recover what the order is. We can see that it would be terrible if the dispatched share cannot be veri-fied due to a cheater’s attack.
A VCS would be helpful if the shares are meaningful or identifiable to every participant. A VCS with this extended characteristic is called extended VCS (EVCS) [2], [19]. A -EVCS is like a -VCS except that each share dis-plays a meaningful image, which will be called share image hereafter. Different shares may have different share images. At first glance, it seems very difficult to cheat in EVCS because the cheater does not know the share images that appear on the genuine shares and, thus, has no information about the distributions of black and white pixels of the share images. This information is crucial for cheating in VC. In this paper we show that it is still possible to cheat in EVC.
A. Our Contributions
In this paper, we study the cheating problem in VC and EVC. We present three cheating methods and apply them on existent VC or EVC schemes. Although, the revealed secret is an image, our attacks are not like the attacks against watermarks, such as the Stirmark attack, which makes watermarks undetectable. Our attacks are to reveal fake images to cheat honest participants. Our attacks are more like the man-in-the-middle attack in cryp-tography. In fact, our attacks are very general for all kinds of VCSs without cheating-prevention mechamism.
We propose a generic method that converts a VCS to another VCS that has the property of cheating prevention (also called cheat-preventing VCS). The overhead of the conversion is near optimal. Our contributions are summarized as follows.
1) We propose three cheating methods against VC or EVC schemes. The first two methods are applied to attack 1057-7149/$25.00 © 2006 IEEE
against cheating robustly. By these criteria, we propose a generic method that converts any VCS to another VCS with the property of cheating prevention. Our conversion is very efficient and incurs little overhead compared with the original VCS. The degression in contrast of the converted VCS is almost optimal. For each pixel of the secret image, we add two additional subpixels to the encoded subpixels only, no matter how many the encoded subpixels are. The rest of this paper is organized as follows. The models for VCS, EVCS, and cheating behaviors in VC are discussed in Section II. We then describe three cheating methods, each with its distinct cheating behavior in Section III. In Section IV, we survey some previous cheat-preventing schemes and show how to attack and improve them. Finally, we present an effi-cient and generic transformation from any VCS to a cheat-pre-venting VCS that is measurably better than all previous schemes in Section V.
B. Previous Work
Naor and Shamir [19] proposed a -VCS. Many
im-provements and extensions follows [1]–[3], [5], [6], [8], [10], [11], [13], [15]–[17], [22]–[25]. For example, Ateniese et al. [1] proposed an elegant VCS for general access structures based on the cumulative array method. Tzeng and Hu [22] proposed a new definition for VC, in which the secret image can be either darker or lighter than the background.
Naor and Pinkas [18] showed some methods of authentica-tion and identificaauthentica-tion for VC. Their scenario focuses on au-thentication and identification between two participants. Yang and Laih [26] proposed two cheat-preventing methods. Their first method needs an on-line TA (Trusted Authority) to verify the shares of participants. Their second method is a transforma-tion from a VCS (but not a -VCS) to a cheat-preventing VCS on which the stacking of two shares reveals the verifica-tion image. The method needs to add extra subpixels for each pixel in the secret image.
Horng et al. [14] proposed a cheating method against some VC schemes. In their cheating method, the cheater needs to know the exact distribution of black and white subpixels of the shares of honest participants. Based on this characteristic, they proposed a cheat-preventing method to prevent the cheater from obtaining the distribution. However, we show that the knowledge of the distribution is not a necessary condition for a successful cheat. They also proposed another cheat-preventing method in which the stacking of the genuine share and verifica-tion share reveals the verificaverifica-tion image in some small region. We show that it is possible to attack the method.
is an access structure if and . The access
structure for -secret sharing is that
if and only if , where is the number of participants in .
A. Visual Cryptography Scheme
The secret image consists of a collection of black and white pixels. To construct shares of an image for participants, we need to prepare two collections, and , which consist of Boolean matrices. A row in a matrix in and cor-responds to subpixels of a pixel, where 0 denotes the white subpixel and 1 denotes the black subpixel. For a white (or black) pixel in the image, we randomly choose a matrix from (or , respectively) and assign row of to the corresponding po-sition of share . Each pixel of the original image will be encoded into pixels, each of which consists of sub-pixels on each share. Since a matrix in and constitutes only one pixel for each share. For security, the number of ma-trices in and must be huge. For succinct description and easier realization of the VC construction, we do not construct and directly. Instead, we construct two basis ma-trices and and then let and be the set of all matrices obtained by permuting columns of and , respectively.
Let be the vector of “bitwise-OR” of rows
of , where is an Boolean matrix and
is a set of participants. Let be the Hamming weight of row vector . For brevity, we let
. Let , where
is a black pixel in share and is the dimension of .
Similarly, , where is a white pixel in
share . Note that all white (or black) pixels in a share have the same Hamming weight. We use “ ” to denote “the stacking of shares and .” The “stacking” corresponds to the bitwise-OR operation “ ” of subpixels in shares and . The definition of VC [1] for an access structure is as follows. Definition 2.1: Let be an access structure.
Two collections (multisets) and of Boolean
ma-trices constitute a -VCS if there exist a value
and a set satisfying the following.
1) Any qualified set can
re-cover the secret image by stacking their shares. Formally,
for any , , whereas,
for any .
2) Any forbidden set has
no information on the secret image. Formally, the two
collections , of matrices obtained
by restricting each matrix in to rows
, are indistinguishable in the sense that they contain the same matrices with the same frequencies.
Fig. 1. (0; 4)-VCS and the structures of subpixels.
The value is called pixel expansion, which is the number of subpixels that each pixel of the secret image is encoded into in each share. The value is called contrast. The higher the contrast, the more visible by human eyes the secret image. The first property (contrast) ensures that the recovered image shows difference between the white pixels and the black pixels. The second property (security) ensures that nothing about the image can be recovered from the shares of participants in a for-bidden set.
The following shows an example of VC.
1) Example 2.1: Let ,
and then
. The two basis matrices
and
form a -VCS with contrast . The shares ,
, and , and the stackings of them are given in Fig. 1. In the above example, each pixel of the secret image is en-coded as four subpixels in each share. To encode a white (or black) pixel, we assign row of (or , respectively) to share , . In order to ensure security, the order of the subpixels of a pixel is randomly permuted (simultaneously per-muted for all shares). This is equivalent to randomly choosing a matrix from (or , respectively).
An extended VCS is a VCS such that each share has a mean-ingful share image.
2) Example 2.2: Fig. 2 shows an EVCS for the access struc-ture of Example 2.1. The share images of , , and are , , and , respectively. Note that shows no infor-mation about the secret .
B. Cheating in VC
There are two types of cheaters in our scenario. One is a ma-licious participant who is also a legitimate participant,
namely, , and the other is a malicious outsider ,
where . In this paper, we show that not only an can cheat, but also an can cheat under some circumstances.
A cheating process against a VCS consists of the following two phases:
Fig. 2. (0; 4)-EVCS.
Fig. 3. Example of cheating a (2,2)-VCS.
1) fake share construction phase: the cheater generates the fake shares;
2) image reconstruction phase: the fake image appears on the stacking of genuine shares and fake shares.
In order to cheat successfully, honest participants who present their shares for recovering the secret image should not be able to distinguish fake shares from genuine shares. A reconstructed image is perfect black if the subpixels associated to a black pixel of the secret image are all black. Most proposed VC schemes have the property of perfect blackness. For example, the recon-structed secret images in Example 2.1 are all perfectly black. We only consider to cheat the participants who together do not constitute a qualified set. Since all participants together in a qualified set can recover the real secret image in perfect black-ness already, it is not possible to cheat them.
1) Example 2.3: Fig. 3 shows how to cheat participants in
a (2,2)-VCS. Since reveals the fake image , is
cheated to believe that the secret image is . Although successfully reveals the fake image, the real secret
image also appears on due to the property of
perfect blackness for secret images. The participants of a quali-fied set , in this example, cannot be cheated.
A successful cheat against a VCS is defined as follows. By the general practice for security analysis, the cheater is required to succeed with a significant probability only.
Definition 2.2: For a -VCS with basis matrices and , an or an cheats successfully if it finds a fake image and generates fake shares satisfying the following.
1) For , the stacking of their
shares and the fake shares reveals the fake image. If the
cheater is an , some is the cheater, .
2) The fake shares cannot be distinguished from the genuine shares. Formally, for each fake share (FS), there is a share
Fig. 4. Cheating method CA-1, initiated by anMP.
Fig. 5. Example of cheating a (4,4)-VCS by an MP.
such that the subpixels of FS are identically distributed as those of .
III. THREECHEATINGMETHODS
Our first cheating method is initiated by an , while the second cheating method is initiated by an . Both of them apply to attack VC. Our third cheating method is initiated by an
and applies to attack EVC. A. Cheating a VCS by an
The cheating method CA-1, depicted in Fig. 4, applies to at-tack any VCS. Without loss of generality, we assume that is the cheater. Since the cheater is an , he uses his genuine share as a template to construct a set of fake shares which are indistinguishable from its genuine share. The stacking of these fake shares and reveals the fake image of perfect blackness.
We see that, for , the stacking
of their shares reveals no images. Thus, the stacking of their shares and the fake shares reveals the fake image due to the per-fect blackness of the fake image.
1) Example 3.1: Fig. 5 shows how to cheat the par-ticipants in a (4,4)-VCS. There are four shares , ,
, and in the (4,4)-VCS. is assumed to be the
. By CA-1, one fake share is generated. Since
or , we see that
or reveals the
fake image . Thus, and or are cheated to believe
that is the secret image.
Fig. 6. Cheating method CA-2, initiated by an MO.
For some prominent - and -VCSs [5], [6], [19],
the numbers of black and white subpixels in a pixel are almost
equal. The cheater needs only fake share
to cheat successfully.
Theorem 3.1: The in CA-1 successfully cheats any VCS.
Proof: Contrast. Let and be the basis ma-trices of a VCS and the pixel expansion is . For,
, . By
the construction of CA-1, for a white pixel of the fake image, the weight of the OR-vector of and the fake shares
is equal to . For a black pixel
of the fake image, the weight of the OR-vector of
and the fake shares is equal to . Thus, the contrast property is satisfied and the fake image appears.
Indistinguishability. The fake shares are generated according to . Each pixel in the fake shares has the same number of white and black subpixels as those in . Also, those subpixels are randomly distributed for each fake share. Thus, the fake shares are indistinguishable from .
B. Cheating a VCS by an
Our second cheating method CA-2, depicted in Fig. 6, demonstrates that an can cheat even without any genuine share at hand. The idea is as follows. We use the optimal (2,2)-VCS to construct the fake shares for the fake image. Then, we tune the size of fake shares so that they can be stacked with genuine shares.
Now, the only problem is to have the right share size for the fake shares. Our solution is to try all possible share sizes. In the case that the gets one genuine share, there will be no such problem. It may seem difficult to have fake shares of the same size as that of the genuine shares. We give a reason to show the possibility. The shares of a VCS are usually printed in transparencies. We assume that this is done by a standard printer or copier which accepts only a few standard sizes, such as A4, A3, etc. Therefore, the size of genuine shares is a fraction, such as 1/4, of a standard size. We can simply have the fake shares of these sizes. Furthermore, it was suggested to have a solid frame to align shares [19] in order to solve the alignment problem during the image reconstruction phase. The can simply choose the size of the solid frame for the fake shares.
Fig. 7. Example of cheating a (4,4)-VCS by anMO.
Therefore, it is possible for the to have the right size for the fake shares.
1) Example 3.2: Fig. 7 shows that an cheats a (4,4)-VCS. The four genuine shares , , , and are those in Fig. 5 and the two fake shares are and . For clarity, we put here to demonstrate that the fake shares are indistin-guishable from the genuine shares. We see that the stacking of fewer than four genuine shares and two fake shares shows the fake image .
Theorem 3.2: The in CA-2 successfully cheats a VCS if the right share size is obtained.
Proof: Contrast. For , let
. Since and are two
shares of the optimal -VCS, and
. By CA-2, the distribution of subpixels of the genuine shares are random and independent of that of the
fake shares. For the white pixel in , we have,
with high probability
Also, due to the perfect black property in recovering the fake
image, we have . Thus, the contrast
property in is satisfied and the fake image
appears.
Indistinguishability. We assume that the size of and is correct. By the construction of CA-2, the fake shares are indistinguishable from the genuine ones.
C. Cheating an EVCS by an
In the definition of VC, it only requires the contrast be non-zero. Nevertheless, we observe that if the contrast is too small, it is hard to “see” the image. Based upon this observation, we demonstrate the third cheating method CA-3, depicted in Fig. 8, against an EVCS. The idea of CA-3 is to use the fake shares to reduce the contrast between the share images and the back-ground. Simultaneously, the fake image in the stacking of fake shares has enough contrast against the background since the fake image is recovered in perfect blackness.
Let be the threshold for contrast that human eyes distinguish the image from the background. The value varies for different
Fig. 8. Cheating method CA-3 against an EVCS.
sizes, contrasts and types of share images. We conduct some ex-periments to obtain empirically. We consider four types of pic-tures (in Fig. 9) with four different sizes ( : 200 100 pixels, : 200 200 pixels, : 400 200 pixels, and : 400 400 pixels) and four different contrasts (1/4, 1/9, 1/16, and 1/25). The values in Table I represent the number of black sub-pixels which we should add for each pixel of the fake shares in order to reduce the contrast between the background and the share images to be less than . The larger the size and contrast of the image are, the more black subpixels we need to add to the fake shares. Most EVCSs do not have a large contrast, we can easily cheat them by adding a small number of black subpixels to the pixels of the share images in the fake shares.
1) Example 3.3: Fig. 10 shows the results of cheating
a -EVCS, where , and
. In this example, is
the cheater who constructs a fake share with share image
in substitute for to cheat . reveals the
fake image .
Theorem 3.3: The in CA-3 successfully cheats an EVCS by producing fake shares with meaningful share images if the is correct.
Proof: By Step 3 in CA-3, the share image appears on the fake share.
Contrast. Since the fake shares are constructed by the same way of CA-1, the recovered fake image in perfect blackness appears on the stacking of shares. Furthermore, the share images of the fake shares are invisible since we have added an enough number of black subpixels to blur them.
Indistinguishability. The proof is the same as that of Theorem 3.1 except that we have to show that honest participants cannot identify fake shares. Since share images are used for identifi-cation, honest participants will not know the exact shapes of share images. They care only about the content of share images. Therefore, the cheater who is a legitimate participant can create
TABLE I
NUMBER OFADDEDBLACKSUBPIXELS FOR THEPICTURES INFIG. 9 WITHDIFFERENTSIZES ANDCONTRASTS
Fig. 10. Example of cheating a(0; m)-EVCS.
reasonable share images on fake shares according to his own share to cheat other participants.
IV. ATTACKS AND IMPROVEMENT ONPREVIOUS CHEAT-PREVENTINGMETHODS
There are two types of cheat-preventing methods [26]. The first type is to have a trusted authority (TA) to verify the shares of participants. The second type is to have each participant to verify the shares of other participants. In this section, we present attacks and improvement on four existent cheat-pre-venting methods.
A. Attack on Yang and Laih’s First Cheat-Preventing Method The first cheat-preventing method of Yang and Laih [26] needs a TA to hold the special verification share for detecting
fake shares. It generates shares , where
is the verification share. If shows the verification image that is known to all participants, the share is genuine.
Let and be the basis matrices of a -VCS. They
assign pixels to shares by four sets , , , and
which are the sets of all -matrices obtained
by permuting the columns of
.. . .. . .. . .. .
respectively. Pixels are assigned to shares by a random matrix in , where indicates the pixel in the verification image and indicates the pixel in the secret image. We see that the verifi-cation image shall appear on if the share is genuine since the first two subpixels reveals the verification image.
Our attack, depicted in Fig. 11, involves two malicious par-ticipants. Without loss of generality, we assume that they are and . and together constructs a fake share such that
reveals the verification image and cheats other participants.
We see how the attack works.
1) reveals the verification image. The reason is that the first two subpixels (before permutation) of and are the same. The first two subpixels of are the same as those of . Thus, the verification image appears on . The details are as follows.
For the white pixel of the verification image, the first two pairs of subpixels in and are (1,1) and (0,0) by and , the corresponding subpixels in are the same as
Fig. 11. Cheat against Yang and Laih’s cheat-preventing Method.
those in by Step 2 in the fake share construction phase.
Thus, the pixel of is white since shows
whiteness in the pixel. For the black pixel of the verification image, the first two pairs of subpixels in and are (0,0) and (1,1) by and , the corresponding subpixels in
are the same as those in . Thus, the pixel of is black since shows blackness in the pixel.
2) For ,
reveals the fake image. For the white pixel of the fake image, the pixel in is the same as that in by Step 1. Thus, the pixel in is white. For the black pixel of the fake image, the subpixels 1 and 0 of is changed to 0 and 1 in (see Step 2). Thus, the white pixel, containing subpixels
of is changed to a black pixel, containing subpixels
in . Thus, the fake image appears on .
3) are indistinguishable by other participants. For each pixel, the numbers of black and white subpixels in the pixels of and are the same since the only change
is to swap subpixels and in to and in . Thus,
and look the same and other participants cannot dis-tinguish them.
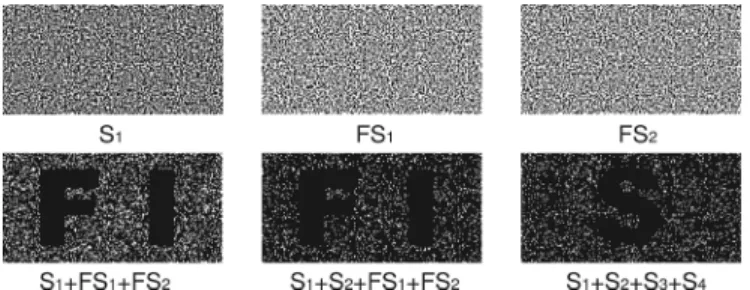
Fig. 12. Example of cheating the cheat-preventing (3,3)-VCS of Yang and Laih.
1) Example 4.1: Fig. 12 shows the results of cheating a (3,3)-VCS of Yang and Laih. We see that all shares including the fake share pass verification by revealing the correct
verification image . Since reveals a fake image
, is cheated.
B. Attacks on Horng et al.’s Cheat-Preventing Methods In the first cheat-preventing method of Horng et al. [14], each participant has a verification share . The share’s s are generated as usual. Each is divided into regions ,
, . Each region of is designated for
verifying share . The region of shall reveal the
verification image for verifying the share of . The ver-ification image in is constructed by a (2,2)-VCS. Although the method requires that the verification image be confidential, we show that it is still possible to cheat.
Assume that knows the regions of the verification share . generates a fake share to cheat as follows. The pixels of in the region are the same as those in . The rest pixels of (outside the region ) are constructed by CA-1. As a result, the correct verification image appears on the region
of and believes that is a genuine share.
By CA-1, the stacking of and other genuine shares reveals a reasonable fake image. Moreover, even the cheater does not know the verification region assigned to a participant, the attack is still possible. Since the verification share is divided into regions, each verification region is small for a fairly large . We choose a simple fake image. The probability that no overlapping between the fake image and the region occurs is high. By
setting the background pixels in from , shows
the verification image in the verification region of . By our proposed attacks, we conclude the following principle on using verification images.
1) Essential Principle: The verification images should be confidential and spread over the whole region of a share.
Horng et al.’s second cheat-preventing method uses the ap-proach of redundancy [14]. It uses a -VCS to imple-ment a -VCS cheat-preventing scheme. The scheme needs no on-line TA for verifying shares. The scheme generates
shares by the -VCS for some integer , but
dis-tributes only shares to the participants. The rest of shares are destroyed. They reason that since the cheater does not know the exact basis matrices even with all shares, the cheater cannot suc-ceed. However, our three cheating methods do not need to use
another cheat-preventing -VCS. The stacking of any two shares reveals the verification image. This is how share verification is done.
Let and be the basis matrices of a -VCS. Their
method constructs four sets , , , of
-matrices obtained by permuting the columns of the following four matrices, respectively:
.. . ... .. . ... .. . ... .. . ...
The pixel expansion of this construction is
and contrast is , where
is the contrast of the original VCS without cheating prevention. By our observation [22], what the human eyes care about is contrast, no matter whether the image is darker or lighter than the background. Therefore, we gave a new definition VCS for VC based on this observation and made improvements on some types of access structures [22]. Our improvements are appli-cable to Yang and Laih’s cheat-preventing method. It reduces
the pixel expansion to . Moreover, since the
verification image can be made public to all participants, we can let the verification image appear on the shares. By this, we can
further reduce the pixel expansion to .
Our improvement is based on the following three theorems, which are proven in [22].
-VCS , and are basis matrices for a
-VCS , where and are obtained from and by
deleting the same columns.
Theorem 4.3: [22] (Inverse property) Let
be an access structure. If and are basis matrices for a
-VCS , and are basis matrices for a -VCS
, where and .
We denote the left appended matrices in as
sub-matrices , where , .
Each sub-matrix consists of two columns counting from left to right. Based on Theorems 4.1–4.3, we can exchange the
roles of and , and also and , and delete
common columns. Furthermore, we delete all columns having one “0” only for the case that the verification image may not appear on the shares. By these steps, the pixel expansion of
the appended matrices is reduced to .
Let . The basis matrices for a
cheat-preventing -VCS using Yang and Laih’s cheat-preventing method are as follows:
We reduce the pixel expansion of the left appended matrices from 12 to 3, as follows:
Fig. 13. Improved (3,3)-VCS for Yang and Laih’s cheat-preventing method.
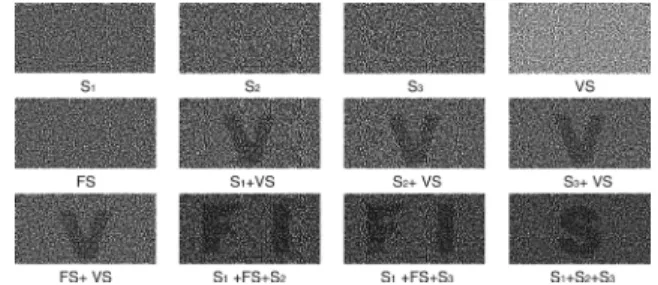
1) Example 4.2: Fig. 13 shows the results of the improved cheat-preventing (3,3)-VCS . We see that the stacking of any two shares reveals the verification image . reveals the reversed verification image and shows the verification image.
V. GENERICTRANSFORMATION FORCHEATINGPREVENTION By the attacks and improvement in previous sections, we pro-pose that an efficient and robust cheat-preventing method should have the following properties.
1) It does not rely on the help of an on-line TA. Since VC emphasizes on easy decryption with human eyes only, we should not have a TA to verify validity of shares.
2) The increase to pixel expansion should be as small as pos-sible.
3) Each participant verifies the shares of other participants. This is somewhat necessary because each participant is a potential cheater.
4) The verification image of each participant is different and confidential. It spreads over the whole region of the share. We have shown that this is necessary for avoiding the de-scribed attacks.
5) The contrast of the secret image in the stacking of shares is not reduced significantly in order to keep the quality of VC.
6) A cheat-preventing method should be applicable to any VCS.
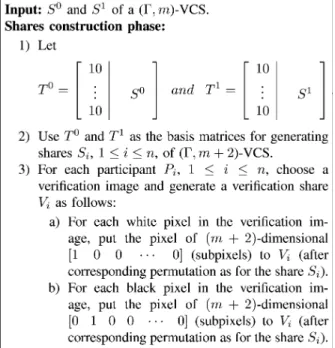
We now present a generic transformation from a VCS to another cheat-preventing VCS. The resultant cheat-preventing VCS meets all the above requirements. The idea is similar to the first cheat-preventing method of Yang and Laih [26]. But, we let each participant hold a verification share. Our cheat-preventing scheme needs no help from an on-line TA. The verification image for each participant is different and known to the participant only.
Our transformation is quite efficient and almost optimal as it adds only two subpixels for each pixel of the original image. That is, if the pixel expansion of the VCS is , the pixel expan-sion of the transformed VCS is . The contrast is slightly
reduced from to . Our
transformation is depicted in Fig. 14. It generates two shares for each participant. One is the secret share and the other is the ver-ification share. Let and be the basis matrices of a
-VCS. At first, we create two -dimensional
basis matrices and . The transformed -VCS
uses and as the basis matrices to generate shares for the participants as usual. Then, for each participant , it gen-erates a verification share for a chosen verification image. For each white pixel in the verification image, it puts the pixel
Fig. 14. Our generic transformation for VCS with cheating prevention.
Fig. 15. Example of a transformed VCS with cheating prevention.
of -dimensional to (after
corre-sponding permutation as for the share ). For each black pixel in the verification image, it puts the pixel of
-dimen-sional to (after corresponding
per-mutation as for the share ). We see that the verification image is encoded into the first two subpixels. If participant wants to verify the share of participant , he checks whether shows his verification image.
1) Example 5.1: Fig. 15 shows a transformed -VCS with cheating prevention, where
and . The verification
images for participants , , and are , , and ,
respectively. Note that the simple verification images are for demonstration only. By our proposed principle in Section IV-B, we should use more complicated verification images.
Theorem 5.1: The algorithm in Fig. 14 transforms any -VCS to another -VCS with cheating prevention,
. For each white pixel of the ver-ification image, the first two subpixels of is
. Thus, the black and white pixels of the veri-fication image have a positive contrast and can see the
veri-fication image in .
Each participant has his own private verification image, which is not known to other participants. Since the first two subpixels (before permutation) of all shares are the same, a participant even with all shares cannot know the positions of black pixels of the verification image of participant , . Therefore, cannot produce a fake share such that shows the verification image of . Participant cannot cheat participant for . Furthermore, we see that collaboration of some participants cannot succeed to cheat, either.
VI. CONCLUSION
We have proposed three cheating methods against VCS and EVCS. We examined previous cheat-preventing schemes and found that they are either not robust enough or still improvable. We presented an improvement on one of these cheat-preventing schemes. By our attacks, we pointed out an essential principle for a robust cheat-preventing VCS. We finally proposed an effi-cient transformation of VCS for cheating prevention. Our trans-formation incurs minimum overhead on contrast and pixel ex-pansion. It only added two subpixels for each pixel in the image and the contrast is reduced only slightly.
REFERENCES
[1] G. Ateniese, C. Blundo, A. De Santis, and D. R. Stinson, “Visual cryp-tography for general access structures,” Inf. Comput., vol. 129, no. 2, pp. 86–106, 1996.
[2] ——, “Extended capabilities for visual cryptography,” Theoret. Comput. Sci., vol. 250, no. 1–2, pp. 143–161, 2001.
[3] I. Biehl and S. Wetzel, “Traceable visual cryptography,” in Proc. 1st Int. Conf. Information Communication Security, 1997, vol. 1334, LNCS, pp. 61–71.
[4] C. Blundo and A. De Santis, “Visual cryptography schemes with per-fect reconstructions of black pixels,” Comput. Graph., vol. 22, no. 4, pp. 449–455, 1998.
[5] C. Blundo, A. De Santis, and D. R. Stinson, “On the contrast in visual cryptography schemes,” J. Cryptol., vol. 12, no. 4, pp. 261–289, 1999. [6] C. Blundo, P. D’Arco, A. De Santis, and D. R. Stinson, “Contrast op-timal threshold visual cryptography schemes,” SIAM J. Discrete Math., vol. 16, no. 2, pp. 224–261, 2003.
[7] E. F. Brickell and D. R. Stinson, “The detection of cheaters in threshold schemes,” SIAM J. Discrete Math., vol. 4, no. 4, pp. 502–510, 1991. [8] S. Cimato, A. De Santis, A. L. Ferrara, and B. Masucci, “Ideal contrast
visual cryptography schemes with reversing,” Inf. Process. Lett., vol. 93, no. 4, pp. 199–206, 2005.
[13] T. Hofmeister, M. Krause, and H.-U. Simon, “Contrast-optimalk out ofn secret sharing schemes in visual cryptography,” Theoret. Comput. Sci., vol. 240, no. 2, pp. 471–485, 2000.
[14] G.-B. Horng, T.-G. Chen, and D.-S. Tsai, “Cheating in visual cryptog-raphy,” Designs, Codes, Cryptog., vol. 38, no. 2, pp. 219–236, 2006. [15] C.-M. Hu and W.-G. Tzeng, “Compatible ideal contrast visual
cryptog-raphy with reversing,” in Proc. 8th Information Security Conf., 2005, vol. 3650, LNCS, pp. 300–313.
[16] M. Krause and H.-U. Simon, “Determining the optimal contrast for secret sharing schemes in visual cryptography,” Combin., Probab., Comput., vol. 12, no. 3, pp. 285–299, 2003.
[17] R. Ito, H. Kuwakado, and H. Tanaka, “Image size invariant visual cryp-tography,” IEICE Trans. Fundam. A, vol. E 82, no. 10, pp. 2172–2176, 1999.
[18] M. Naor and B. Pinkas, “Visual authentication and identification,” in Proc. Advances in Cryptology, 1997, vol. 1294, LNCS, pp. 322–336. [19] M. Naor and A. Shamir, “Visual cryptography,” in Proc. Advances in
Cryptology, 1994, vol. 950, LNCS, pp. 1–12.
[20] A. Shamir, “How to share a secret,” Commun. ACM, vol. 22, no. 11, pp. 612–613, 1979.
[21] M. Tompa and H. Woll, “How to share a secret with cheaters,” J. Cryptol., vol. 1, no. 2, pp. 133–138, 1988.
[22] W.-G. Tzeng and C.-M. Hu, “A new approach for visual cryptography,” Designs, Codes, Cryptog., vol. 27, no. 3, pp. 207–227, 2002. [23] E. R. Verheul and H. C. A. Van Tilborg, “Constructions and properties
ofk out of n visual secret sharing schemes,” Designs, Codes, Cryptog,, vol. 11, no. 2, pp. 179–196, 1997.
[24] D. Q. Viet and K. Kurosawa, “Almost ideal contrast visual cryptog-raphy with reversing,” in Proc, Topics in Cryptology, 2004, vol. 2964, LNCS, pp. 353–365.
[25] C.-N. Yang, “New visual secret sharing schemes using probabilistic method,” Pattern Recognit. Lett., vol. 25, no. 4, pp. 481–494, 2004. [26] C.-N. Yang and C.-S. Laih, “Some new types of visual secret sharing
schemes,” in Proc. Nat. Computer Symp., 1999, vol. 3, pp. 260–268. Chih-Ming Hu received the B.S. degree in computer and information science from the National Army Military Academy, Taiwan, R.O.C., in 1987, and the M.S. degree in computer and information science from the National Chiao-Tung University, Hsinchu, Taiwan, in 1998, where he is currently pursuing the Ph.D. degree in the Department of Computer Science.
His current research interest is in cryptology.
Wen-Guey Tzeng received the B.S. degree in com-puter science and information engineering from the National Taiwan University, Taipei, Taiwan, R.O.C., in 1985, and the M.S. and Ph.D. degrees in computer science from the State University of New York at Stony Brook in 1987 and 1991, respectively.
He joined the Department of Computer and Infor-mation Science (now the Department of Computer Science), National Chiao-Tung University, Hsinchu, Taiwan, in 1991. His current research interests in-clude cryptology and network security.