Modeling of Priority Queueing Service in Discrete Event Systems Using Hybrid
Petri Nets
Ming-Hung Lin and Li-Chen Fu
Dept. of Computer Science and Information Engineering, National Taiwan University,
Taipei, Taiwan, R.0.C
E-mail: lichen@ccms.ntu.edu.tw ABSTRACT
In this paper, we proposed a Hybrid Petri Net (HPN) that extends the framework of the original colored gen- eralized stochastic Petri Net by hiding queues in special places. The Hybrid Petri Net contains ordinary tokens and control tokens. Both of ordinary tokens and con- trol tokens can be exogenous, or can be obtained by a Markovian movement of a token from one place to an- other place after firing of transition. A control token forces an ordinary token to move instantaneously to another place according to a Markovian routing rule. We show that this new class of Petri Net has product form stationary solution, and establish the non-linear token flow equations that govern it. The stability of Hybrid Petri Net is discussed in this new context.
1 Introduction
The queueing services represent an example of a much broader class of interesting dynamic systems, which, refer to as "systems of flow." It acts as a very im- portant role in a discrete event system. The use of queueing networks as introduced in the several famous papers for modeling and performance analysis of com- puter and communication systems are widespread since it allows an extremely efficient solution compared with any other analysis approach. Nowadays, a formal ap- proach such as Petri Nets enable one to describe com- plex discrete event systems precisely and thus allows one to perform both qualitative and quantitative anal- ysis, scheduling and discrete-event control of them. In fact, Petri Net is a very compact representation of Markov techniques and queues, in particular, however, the problem is usually the huge size of the state space. The alternative approach is to incorporate the queues into the high-level specification, namely, Net- Level. However, the ordinary Petri Nets cannot repre- sent queueing disciplines as in queueing networks. On the other hand, the ordinary Petri Nets allow for the use of synchronization and forkljoin behavior both of that cannot be described in queueing networks. Com- bining Queueing Networks and Petri Nets have been studied a t a few of papers. Falko and Peter [l] pro- posed queueing Petri Nets with product form solu- tion. They introduced product form QPN which com- bine PSPN and PQN in one model formalism, namely
the QPN formalism. firthermore, they presented an arrival theorem and discussed exact aggregation in PQPNs. However, in that model formalism, the Petri Net and Queueing Network are loosely couple. Nev- ertheless, it also serves as a good tutorial paper. Erol Gelenbe et 4 2 , 3, 41 proposed a G-network includ- ing negative and positive customers. The G-network is a good original approach, but some important items have not been considered. Such as a new negative may be generated to indicate the positive has finished its service.
In this paper, we proposed a Hybrid Petri Net (HPN) that extends the framework of the original col- ored generalized stochastic Petri Net by hiding queues in special places. The Hybrid Petri Net contains or- dinary tokens and control tokens. Both of ordinary tokens and control tokens can be exogenous, or can be obtained by a Markovian movement of a token from one place to another place after firing of transition. A control token forces an ordinary token t o move instan- taneously to another place according t o a Markovian routing rule. We show that this new class of Petri Net has product form stationary solution, and estab- lish the non-linear token flow equations that govern it. The stability of Hybrid Petri Net is discussed in this new context.
The organization of this paper is
as follows. Sec-
tion 2 describes the model of queueing service using Hybrid Petri Net. In Section 3 we will prove that this new class of Petri Nets have product form. Due to the non-linearity of the traffic equations for these mod- els, the existence and uniqueness of their solution have to be addressed. In addition, a product form of non- preemptive priority queueing also be discussed. Sec- tion 4 is concluding remark.2 The Model
We proposed a Hybrid Petri Net (HPN) that ex- tends the framework of the original colored general- ized stochastic Petri Net by hiding queues in special places. The Hybrid Petri Net contains ordinary tokens and control tokens. Both of ordinary tokens and con- trol tokens can be exogenous, or can be obtained by a Markovian movement of a token from one place to an- other place after firing of transition. A control token
i
\
Immediate hausitton/ P $ i
Finite InGmte tuned timed tramtion trrnationtoken (Control or Ordinary) \Joining subnet _.._._.__ Control token .... ...
-.
, i tokenFigure 1: Forking subnet and joining subnet forces an ordinary token to move instantaneously to another place according to a Markovian routing rule.
In our proposed Hybrid Petri Net, there are two special elementary types of subnet as shown in Fig. 1 in spit of ordinary places and transitions, namely, join- ing subnet and forking subnet. The service time of joining subnet is infinite. The service time of fork- ing subnet follow some probability distribution. The service time of forking subnet is zero. When a token enter a joining subnet, the token will receive no service from the server and will stay in subnet for blocking. In our queueing services model, we allow work both to be moved from a subnet t o another without service, and destroyed, under the effect of control token which are either exogenous, or generated by the ordinary tokens after service. Before presenting our queueing model the necessary terminology is introduced. Let,
C = number of token classes.
K= number of subnet (resources modeled as queueing centers or infinite server).
S k c = mean number of external visits made by a class
c ordinary token a t subnet k .
Zkc= mean number of external visits made by a class
c control token a t subnet k .
Nkc= number of class c E (1,.
...
c)
tokens at subnetk .
v k c = mean number of visits made by a class ordinary
token a t subnet k .
R k c = mean service demand rate per visit for a class c ordinary token a t subnet k
As shown in Fig. 2, a token(contro1 token or ordi- nary token) of class which leaves forking subnet i (after finish service) goes to subnet j as a token of class 1 with probability p ( i , j ) ( k , l ) , it may depart from the network with probability P ( i ) ( k ) = 1 -
E,
x l p ( z , j ) ( k , l ) . A token (control token or ordinary token) of class k whichp‘
?&hi &m
Figure 2: A queueing service model of Jackson Queue- ing Network
...
.3?L
... .!!or. ...1 2
fie4
zl”l 1
...
Figure 3: A queueing service model of a production network
leaves joining subnet i (after finish service) goes t o sub- net j as a token of class 1 with probability zero.
The arriving control token triggers the instanta- neous passage of a token(contro1 token or ordinary to- ken) of class k from joining subnet i t o class 1 of some other subnet j with probability q ( i , j ) ( k ,
I).
With prob- ability Q ( i ) ( k ) = 1 -E.
El
q ( i , j ) ( I C , l ) , it forces a to- ken to leave the network. After triggering the instan- taneous passage of a token, the arriving control token is destroyed. The arriving control token triggers the instantaneous passage of a token(contro1 token or or- dinary token) of class IC from forking subnet i to class1 of some other subnet j with probability zero. When a token(contro1 token or ordinary token) of class k which leaves forking subnet i (after fin- ish service)
,
it generates a new control token from forking subnet i to class 1 of some other subnet j with probability u(i,j)(k,Z). it may not generate a new control token into the network with probabilityV ( i ) ( k ) =
l-Ej
x l u ( i , j ) ( k , l ) When a token(contro1 token or ordinary token) of class k which leaves join-\
@chine 2,.,-,,-,-,
Machine 1
--
Figure 4: A queueing service model of share resource
ing subnet i (after finish service)
,
it generates a new control token from joining subnet i t o classI
of some other subnet j with probability zero.3 Analysis Result
The system as a whole is Markov because we assume the arrival processes are all Poisson and service pro- cesses are exponential, therefore, there can be following types of transitions.
1 No changes in system state.
2 An external visit made by a control(ordinary) cus- tomer, at forking(joining) queue k.
3 An external yisit made by a control customer at join- ing queue k
,
and the control customer triggers the instantaneous passage of a control(ordinary) cus- tomer from joining queue k’ t o forking(joining, out- side) queue k.
4 Transfer of a control(ordinary) token (after service) from forking subnet k* to forking(joining, outside network) subnet k”
.
A new control token generated from forking subnetk*
outside the network, when the control(ordinary) token leaves forking subnetk* (after service)
.
5 Transfer of a control(ordinary) token (after service) from forking subnet k* to forking(joining, outside network)subnet
IC”.
A new control token generated from forking subnet IC* to joining subnet I C ‘ , when a control(ordinary) token leaves forking subnet k* (after service) .The new control token triggers the instantaneous passage of a control(ordinary) token from joining subnetk‘
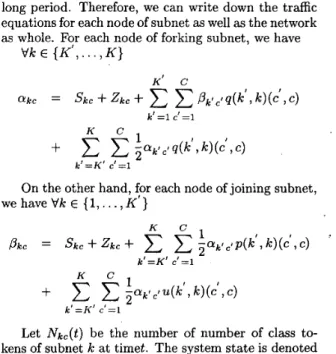
to forking(joining, outsidelong period. Therefore, we can write down the traffic equations for each node of subnet as well as the network as whole. For each node of forking subnet, we have
V k E { K ‘ ,
...,
K }K’ C
On the other hand, for each node of joining subnet, wehaveVkE {1,
...,
K ‘ }K C .
Let Nkc(t) be the number of number of class to- kens of subnet
k
at timet. The system state is denotedas
{Nll(t),...,Nlc(t),...,NKl(t),...,N~c(t)T
L
0). We assume the arrival process is Poisson and the service time distributions are exponential, we can have only the following events happening in an incremental time interval
At.
It satisfies a system of Chapman-Kolmogorov equations, and its steady-state distribution p [ N ] = ~ [ N I I , ..
.
,
N K C ] = limt-,op[Nll(t) =NI,.
.
.,
N K G ( ~ ) = NKC] To begin with, we define the following notations;fi
=
(N11,..
. , N l C , .. .
, N K 1 , .. .
, N K C ) i k c =(0,.
. .
,
N k c , ..
.? 0)fi-
1 k c = ( N i l , ..
.
,
Nit,..
.,
Nkc - 1,...,
N K C )N
+
f k c = ( N I ~ , . . . , N ~ c , . . . , N ~ ~+
1, . . . , N K c)
we focus our attention on the change in system state
fi
in an incremental time intervalAt.
There- fore, P [ f i ‘ ( t+
Wl
K C K C : k = l c=l k = l c = l K C ! k = l c = l K C k = l c = l K C K + l Cp[fi(t)
+ ik.c.
-ik..c..
+
iktCt
-ikc]
R k * , * p ( k * , k ” ) ( C * , c ” ) u ( k * , k ’ ) ( C * , c ( ) q ( k * , k’)(c*,c()@)
Rearranging terms in Eq 1, dividing the equation by At, taking limits, dropping the time parameter and setting the derivative of the joint probability density function to zero; we obtain Eq 2
IC c IC c: IC c:
k = l c=l k = l c=l k = l c=l
IC c
Rk*,*p(k* , k ” ) ( C * , ; ) U ( k * , k ’ ) ( C * , c ( ) g ( k * , k‘)(C*, : [ a )
Product Form
Consider the fol!owing of non-linear equations Eq 3 and E q 4 : V k E { K ,
...,
K } ,K C
Theorem 1 If a non-negative solution A k c and R k c
exist such that A k c < R k c for V C E (1,.
. .
,
c}
,
thenProof : we omit the proof, which follows similar tech- nique [2, 3, 4, 8, 71.
Stability
Unlike Jackson networks, the token flow eqvations of the model we consider are nonlinear. Therefore, is- sues of existence and uniqueness of the solutions have to be examined. In particular, our essential result de- pends on the existence of solution(Eq 3 4). Thus, the existence and uniqueness of solutions t o these traffic equations is central to our work. Note that if existence is established, then uniqueness follows easily for a sim- ple reason. We are dealing with the stationary solution of a system of Chapman-Kolmogorov equations, which is known to be unique, if it exists.
Theorem 2 The solution { A k c , R k c } for vc E { 1,
.
. .
,
C}
,
V k E { 1,. . .
,
K },
always exists.Proof I we omit the proof, which follows similar tech- nique [2, 3, 4, 8, 71.
Theorem 2 provides grounds for computing the ar- rival rates of tokens and signals to each subnet, since it guarantees that these can always be found by solving the nonlinear equation. This issue is only a basis for determining whether the network solution in steady- state can be obtained. Indeed. it is easy to imagine situations where once the arrival rate are computed, on discovers that the network is unstable.
Non-preemptive Priority Queueing
So far, we only identifies the token classes of our Hybrid Petri Net. However in real-life, we often encounter sit-
uations where certain tokens are given a greater privi- lege. They receive their services before others. The ar- riving tokens belong t o one of different priority classes. We adopt the convention that the larger the value of the index associated with the priority group, the higher is the so-called priority associated with that group. Then, we associate with a token from priority group a numerically valued priority function at the time in- stant. The choice is made in favor of that token with largest valued priority function. Thus, all ties are bro- ken on an FCFS basis.
A token of class c who arrives at the subnet IC, let us consider the waiting time of the arriving token as the following :
1 When a class c token ayives, the probability that the token finds a class c token in services is Pkc’ =
Akc’ Rkcl, therefore the mean residual service time y is given by weighted sum of the residual service time of each class. y =
cct=l
c
A,,! R,,I 22 The mean total service time of tokens in the same class c before the arriving token. That is NkcRkc. 3 The mean tota1,service time of tokens in the higher priority class c before the arriving token. That is
CNkc’
c’=c+l R k c ’ .
4 The mean total, service time of tokens in the higher priority class c arriving during the token is waiting in queue. That is
E:::+,
W k , ! Rkcl. Then, wehave
(6)
7
w k c =
c
( l
-
Ec=c+l
Pkc’-
C c ’ = c P k c ‘ ),
In addition, we can get the following.Theorem 3 The product form of non-preemptive priority queueing can be described as
K C
Proof: we omit the proof.
4 Concluding Remark
In this paper, we describes the model of queueing service using Hybrid Petri Net. We will prove that this new class of Petri Nets have product form. Due t o the non-linearity of the traffic equations for these models, the existence and uniqueness of their solution have also t o be addressed. In addition, a product form of non-preemptive priority queueing also be discussed. So far we consider a stable queueing system in our hybrid Petri Net model. However in real-applications,
it is encountered that situations where the input pa- rameter of system model changed very frequently. The balance equations may not exist and steady-state behavior may be violated. We review the Markov chain xk that is irreducible, aperiodic and time- homogeneous is said t o be ergodic. For an ergodic Markov chain, the limiting probabilities always exist and are independent of the initial state probability.
.
When we estimating not long run or not steady state, measures of performance. The following should be con- sidered.1 For fixed time interval, different random number will lead t o different performance. The random number depends on the time interval and initial conditions, such as the initial marking status of Petri Nets. 2 For the random number, we can have the assump-
tion that the random number can be estimated as a general statistical distribution plus some bias. As time is increased, the estimator becomes more pre- cise. The bias will be reduced.
Finally, there are many future work. One is develop- ment of throughput approximation technique based on interpolation or MVA [5]. The others are t o study the queueing under the environment where steady-state behavior is violated.
REFERENCES
Falko Bause and Peter Buchholz, L‘Queueing Petri Nets with Product Form Solution”, Performance Evaluation, Vol. 32, pp. 265-299, 1998.
Erol Gelenbe, LLProduct-Form Queueing Networks with Negative and Positive Customers”,
J.
Appl. Prob.,
Vol. 28, pp. 656-663, 1991.Erol Gelenbe, LLG-Networks with Triggered Cus- tomer Movement
”,
J. Appl. Prob.,
Vol. 30, pp. Jean-Michel Fourneau, Erol Gelenbe and Rina Suros, “G-Networks with Multiple Classes of Neg- ative and Positive Customers”, Theoretical Com- puter Science, Vol. 155, pp. 141-156, 1996. Matteo Sereno,‘‘
Approximate Mean Value Anal- ysis for Stochastic Marked Graphs.”, IEEE Tran. on Software E n y . , Vol. 22, No. 9, Sep. 1996. pi). 742-748, 1993.654-664.
Alan A. Desrochers and Robert Y. AI-Jaar, “Ap- plication of Petri Nets in Manufacturing Systems: Modeling, Control, and Performance Analysis.”, IEEE Press.
[7] Ng Chee Hock, “Queueing Modeling Fundamen- [8] Leonard Kleinrock, “Queueing Systems Volume 1 : [9] Leonard Kleinrock, “Queueing Systems Volume 2
: Computer Applications
.”,
John Wiley & Sons Press.tals.”, John Wiley