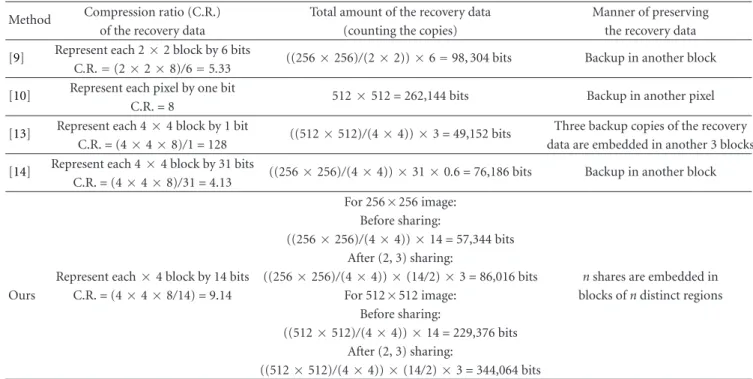
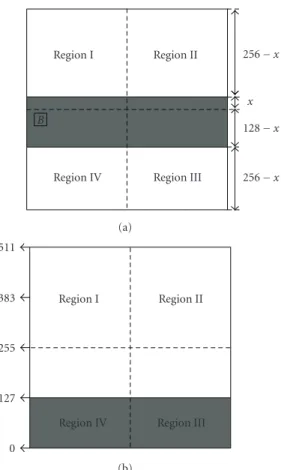
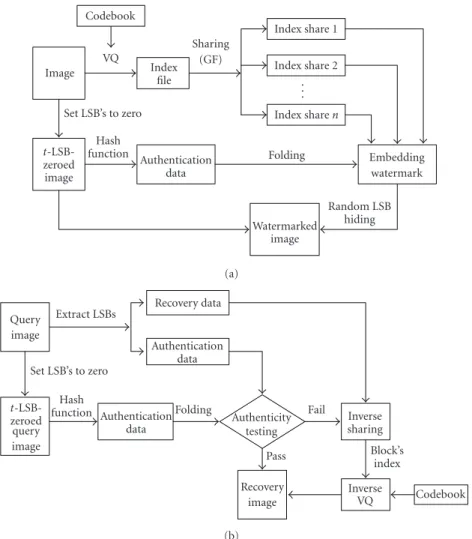
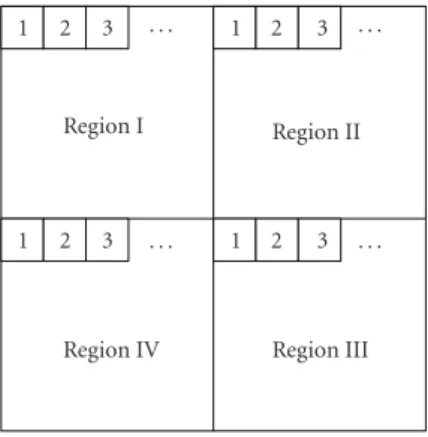
A Sharing-Based Fragile Watermarking Method for Authentication and Self-Recovery of Image Tampering
全文
數據

相關文件
For periodic sequence (with period n) that has exactly one of each 1 ∼ n in any group, we can find the least upper bound of the number of converged-routes... Elementary number
In Section 3, we propose a GPU-accelerated discrete particle swarm optimization (DPSO) algorithm to find the optimal designs over irregular experimental regions in terms of the
The existence and the uniqueness of the same ratio points for given n and k.. The properties about geometric measurement for given n
In this section, we consider a solution of the Ricci flow starting from a compact manifold of dimension n 12 with positive isotropic curvature.. Our goal is to establish an analogue
Numerical experiments are done for a class of quasi-convex optimization problems where the function f (x) is a composition of a quadratic convex function from IR n to IR and
Then, it is easy to see that there are 9 problems for which the iterative numbers of the algorithm using ψ α,θ,p in the case of θ = 1 and p = 3 are less than the one of the
A subgroup N which is open in the norm topology by Theorem 3.1.3 is a group of norms N L/K L ∗ of a finite abelian extension L/K.. Then N is open in the norm topology if and only if
In section 4, based on the cases of circular cone eigenvalue optimization problems, we study the corresponding properties of the solutions for p-order cone eigenvalue



![Figure 8: A comparison of the recovered images of [ 10 , 13 , 14 ] and the proposed method, with tampering or cropping in the same region: (a) 25% of a 512 × 512 watermarked image Barbara (W) is replaced; (b) the recovered image of [ 10 ]; (c) the recovere](https://thumb-ap.123doks.com/thumbv2/9libinfo/7890192.155589/13.900.134.773.106.789/comparison-recovered-tampering-watermarked-barbara-replaced-recovered-recovere.webp)