The Optimal Investment Strategy of Information Security
CHUN-HSIUNG LIAO, National Cheng Kung University CHUN-WEI CHEN, National Cheng Kung University JA-WAY HUNG, National Cheng Kung University
This study analyzes an optimal investment strategy for information security (IS) for a profit-maximizing online monopoly when it is facing attacks from cyber criminals by considering a network security theoretical model with time-varying characteristics. The intangible profit of security investment is transformed into a measurable sales benefit by using a successful entry ratio that links the relationships among IS investment, security improvement, and increases in consumer demand. The dynamic optimization technique is adopted to analyze optimal network security investments for enterprises. It is found that there exists a unique optimal IS investment level. This investment strictly increases with market potential and degree of threat, but the increment strictly decreases with changes in market potential and the degree of threat. The benefit-cost ratio of investment versus threat is strictly concave in regard to threat degree. Next, in a finite time frame, an optimal investment in information security monotonically decreases over time until the end of the time period whenever the discount rate is low.
Finally, it is also found that the optimal upgrade time to invest in information security occurs when a monopoly’s gross profits in two generations of products are the same.
Categories and Subject Descriptors: K.4.4 [Electronic Commerce]: Security General Terms: Economics, Security, Theory
Additional Key Words and Phrases: Information security, threat degree, cyber attack, investment strategy, upgrade time
ACM Reference Format:
Liao,C. H., Chen, C. W., and Hung, J.W. 2010. The Optimal Investment Strategy of Information Security Architecture.
1. INTRODUCTION
Computer technology and the Internet play a ubiquitous role in economic activities related to consumption and transactions. Home shopping Home economics has been booming in recent decades since public consumption behavior has substantially changed. Recently, J.P. Morgan (2011) surveyed the e-commerce industry in the U.S.
and found that the number of people who shop online keeps increasing, with 38 percent buying at least once per month, and the percentage of people who don’t shop online declined to 12 percent in 2010 from 20 percent in 2007. In particular, higher income consumers shop online the most often, with 34 percent of those making
$100,000 or more shopping online at least three times per month.
As of 2009, e-commerce was 3.9 percent of all U.S. retail sales, up from 1.4% in 2002 (J.P. Morgan, 2011). This report also forecasted that e-commerce revenue would grow to $680 billion in 2011 worldwide, up 18.9 percent from 2010 revenue. Further, it predicted that online retail commerce in the U.S. alone will grow 13.2 percent to
$187 billion, and global e-commerce revenue will hit a whopping $963 billion by 2013.
Similarly, Cisco Systems Inc. (2011) conducted interviews with 32 e-retailers that sell internationally to define the priorities, processes and individual market complexities involved in international e-commerce. The report forecasted that global e-commerce, including travel and auto purchases as well as online retail sales, will increase 13.5%
annually for the next four years and reach an estimated $1.4 trillion in 2015. The sophistication of the e-commerce infrastructure, such as Internet connection capabilities, delivery services and payment systems, plays an important role when retailers consider enter the online market of their country or region.
Online transactions are always under substantial hacker threats. Symantec (2010) surveyed more than 2,100 enterprises’ chief information officers and information technological (IT) managers from 27 countries and released the findings of its global state of enterprise security study.
Author’s addresses: C.H. Liao, Institute of Telecommunications Management and Department of Communication and Transportation Management, National Cheng Kung University, Tainan, TAIWAN;
C.W. Chen, Department of Communication and Transportation Management, National Cheng Kung University, Tainan, TAIWAN; J.W. Hung, Department of Communication and Transportation Management, National Cheng Kung University, Tainan, TAIWAN.
The study found that 42 percent of organizations rate security their top issue, more than natural disasters, terrorism, and traditional crime combined. Further, 75 percent of organizations had experienced cyber-attacks in the previous 12 months, and 29 percent of enterprises reported that attacks had increased in 2009. These attacks cost businesses an average of $2 million per year. Finally, organizations reported that enterprise security is becoming more difficult mainly as a result of a number of factors such as understaffing, new IT initiatives that intensify security issues and IT compliance issues. High profile attacks in various ways on giant organizations and government agencies, such as Microsoft, eBay, Yahoo, and Amazon.com, the Department of Defense and the Federal Bureau of Investigation, also have made regular headlines (Kesan et al., 2004). Weaver and Paxson (2004) suggested that a worst-case worm could cost anywhere from $50 billion to $100 billion that excludes difficult-to-estimate but quite possibly large additional indirect damage to the U.S. economy.
The types of security attacks include denial of service (DoS), Trojan horses that come with other software, viruses that reproduce themselves by attaching to other executable files, worms that are self-reproducing programs that create copies of themselves and spread by using e-mail address books, logic bombs that are dormant until an event triggers them (e.g., date, user action, random trigger, etc.) (see The Computer Technology Documentation Project, 2001). They exploit weaknesses in security in various forms. Many of these attacks may cause loss of service or system crashes. The consequences may result in damage or destruction of internal data, loss of sensitive information to hostile parties, use of sensitive information to steal items of monetary value or negatively affect an organization's customers, and damage to the reputation of an organization.
Information technology security includes the products and services of firewalls, intrusion detection systems (IDSs), anti-virus software, and intrusion detection systems etc. Network layout can also be used to increase network security. IT security indeed comes with a cost. It was estimated that U.S. companies spent on average $196 per employee per year on security in 2002 (Carey, 2002). CompTIA (2007), based on a survey of more than 1,000 U.S. corporations, revealed that companies spent on average 20 percent of their total technology budget in 2006 on security measures, up from 12 percent in 2004, and nearly one-half of those surveyed planned to continue to increase IT security spending. IT security investments are considered as a compound of system configuration specific costs and operating costs (Mizzi, 2005). System configuration specific costs are typically one-time costs (i.e., sunk costs) for development, testing and implementation of defense solutions that protect information assets from possible threats. Operating costs are represented by annual maintenance (upgrades and patching of the defense solution), training users and network administrators, who monitor the solutions.
Conventional firms, which have been referred as “brick and mortar” firms, such as Coca-Cola, use the Internet as a marketing channel to communicate with their customers if not to sell products. They might be expected to be the least vulnerable to cyber-attacks as they are the least dependent on the Internet to conduct business.
But e-commerce enterprises like Amazon.com and eBay.com run their businesses on
the platform of IT network systems and rely purely on Internet channels to sell their products and services. These firms face increasing network vulnerability because of the risk that the business they conduct via the Internet might be interrupted. The Internet is like the lifeline for enterprises, where they generate revenues and survive in the long run. The guarantee of security network systems is related directly to the success of Internet enterprises (Cavusoglu et al., 2004b).
Investment in information security (IS) architecture is essential for contemporary enterprises that sell products through both physical store channels and online.
However, these investments generally incur high costs. With insufficient IS investment, enterprises may experience the negative effects of cyber attacks upon actual immediate loss like product sales, service quality and even their goodwill related to indirect losses. On the other hand, over-investment in IS does not bring justifiable returns for the investment (Gordon and Loeb, 2002; Hoo, 2000). The indirect losses from security risks usually appear to be more serious, as they have a much longer negative impact on the customer base, supplier partners, and financial market, banks and business alliance relationships, and such costs are almost as high, and sometimes even higher, than the immediate costs caused by the security attacks (Camp and Wolfram, 2004; Dynes, Andrijcic and Johnson, 2006; Rowe and Gallaher 2006). Hence, the optimal security investment for specific security vulnerability and the threat environment of organizations has attracted the attention of academia.
The recent literature on this topic has been mostly focused on the return on investment (ROI) that links the relationship between cost and benefit related to IS investment. This measurement approach is useful for enterprises in regard to presenting the cost versus benefit analysis required for IS-related policies. Bayuk (2001) demonstrated a risk analysis model of ROI-maximizing IS investment and illustrated how much money must be spent to achieve a “reasonable” degree of security. The risk is assumed to be quantifiable as dollar amounts, for example, a loss of revenue streamed from a given order-processing system or manufacturing line.
The optimal IS investment is derived at the condition where the dollar amount at risk is equated to the price of security improvement. Gordon and Loeb (2002) constructed a one-period economic model of a risk-neutral firm contemplating the provision of additional security to protect a given information set, such as a list of customers, a strategic plan, or a company website. In their model, the vulnerability of the information set is the probability that without additional security, a threat that is realized will result in the information set being breached and the subsequent loss.
The loss is assumed to be the product of threat and vulnerability. It was shown that increases in vulnerability result in an increase in the optimal IS investment and that the maximum amount a firm should spend is only a fraction of the expected loss due to security breaches. Tanaka, Matsuura and Sudoh (2005) used actual information derived from the security investments of e-local governments in Japan to examine the relationship between the optimal level of investment and vulnerability found in the economic framework of Gordon and Loeb (2002).
Cavusoglu et al. (2004a) considered a game-theoretical model for evaluating the investments in an IS architecture of both a firewall and an IDS and assessed the value of two technologies. A game tree was used to depict the strategies of a firm and a hacker. The firm minimized its investment cost and loss, but the hacker maximized its utility from the intrusion and cost if detected. The intrusion action of the hacker and successful detection using two technologies of the firm were given with probabilities. The expected payoff of each outcome was derived and thus, the firm’s optimal strategies could be found. The study provided a guideline for choosing an alternative security technology in which to invest and concluded that firms should evaluate the value of an additional security mechanism based on already existing controls before estimating its return. Huang et al. (2008) proposed an economics
model of simultaneously distributed and targeted security attacks from multiple external agents with distinct characteristics and derived optimal investments based on the principle of benefit maximization. It was found that not all information security risks are worth protecting against a risk-averse decision maker. Specifically, until the potential loss from a security breach reaches certain level, the firm is better off not investing any money at all in protecting against such a threat. Further, the optimal investment in information security does not always go up with the effectiveness of such investments.
Cavusoglu et al. (2004b) adopted event-study analysis, using security breach announcements from 40 firms trading in the U.S. during 1996-2001, to assess the impact of security breaches on the market values of breached firms. It was found that the breached firms lost an average 2.1% of their market value (equivalently, 1.65 billion per breach) within two days of the announcement. Hence, the market penalizes all firms for security breaches, but smaller firms are penalized more than larger firms when a security breach occurs since the importance of security is more crucial to smaller firms’ survival. Finally, Internet firms are penalized more than conventional firms because of the differential degrees of these firms dependence on the Internet to generate revenues and survive in the long run. Iheagwara et al. (2004) measured the financial benefit of an intrusion detection system (IDS) deployment by incorporating a standard risk analysis framework with the cascading threat multiplier (CTM). The CTM is a security compromise that incurs two types of costs:
the direct cost of lost integrity/confidentiality/availability, and the indirect cost of the compromised component serving as a potential stepping stone for future attacks. The paper tried to capture the second type of CTM costs, which are typically ignored in the classic risk analysis framework. The proposed risk analysis formulas tied the CTM concept into accurate ROI calculation and illustrated an effective decision making process in which they indicated what techniques are appropriate for the cost effective management of IDS in a given environment. Similarly, Iheagwara et al.
(2005) induced multiple metrics that enable risk and cost-benefit assessments for calculating the ROI of information assurance technology investments.
Finally, the alternative approach of financial metric indexes and methodical methods has been used for the evaluation of organizational asset values and to assess the threat and vulnerability of systems. The quantification of an investment, using in combination of several economic indexes, such as ROI, net present value (NPV), and internal rate of return (IRR), resulted in a recommendation for choosing an optimal security solution (Borka and Bojanc, 2008).
In sum, the above literature on network security investment mainly has dealt with the benefit and cost effectiveness of the investment, using quantitative metrics.
In particular, the non-financial benefits of security investments such as improved image, gain of customer trust, prevented security breaches, impact on operations, mission performance, or customer satisfaction are difficult to evaluate. Tsiakis and Stephanides (2005) referred to these gray areas as “intangibles” or “soft” returns and suggested that they are usually the most significant parts in terms of cost, but are the hardest to prove. However, the probability, frequency and size of true network security loss and benefits have remained difficult to identify and estimate, and the investment decisions based on the benefits and costs have seldom been discussed.
This study analyzes the optimal investment strategy of IS architecture for a monopoly firm that sells the products through sales points on the Internet while facing cyber criminals with a probability of hacker attacks. In the event that a successful attack occurs, the website breaks down, and the firm is out of the market.
The firm decides a monetary IS investment to avoid the attacks to reduce security threat probability which is a function of the investment and threat degree. The cost of security investment is an endogenous part of the benefit of e-commerce revenues.
A population of consumers has a valuation distribution for the product offered by the firm. This study analyzes the optimal IS investment for the firm as well as its increment and benefit-cost ratio related to market potential and threat degree. Next, when the model is extended to a finite time frame, the firm maximizes its aggregate profits. The population of consumers across periods varies with an awareness diffusion process which is a function of the attractiveness of the firm’s website and word of mouth among consumers. The word of mouth effect increases the size of consumers due to the security improvement and in turn, increases the firm’s revenues. The optimal IS investments with a discount rate across time periods are derived. Finally, in the case where time is in infinitely continuous duration, the timing when the monopoly firm upgrades its security investment is dealt with.
The paper is structured as follows: Section 2 deals with the benchmark model of the firm’s IS investment selection in a single period. Section 3 extends the model in a dynamic setup, and Section 4 addresses the timing decision for the security upgrade.
Finally, a brief conclusion is provided in the last section.
2. THE BENCHMARK MODEL
This study considers a monopoly firm M that sells the products to maximize its profit through sales points on the Internet. Suppose cyber criminals exist such that the probability of hacker attacks is defined as θ, θ [0,1]. In the event that a successful attack occurs, the website breaks down, and M loses all revenues derived from the Internet. M decides z, z > 0, as the monetary investment in information security to avoid the attacks and to retain a good customer reputation.
2.1 Security threat probability function
Security threat probability function ST( , ) z is based on the assumption that M faces depending on security investment z and threat degree θ. It is assumed that ST is monotonically decreasing and strictly concave in z such that ST/ z 0, and
2 2
/ 0 ST z
. Namely, M reduces threat probability through investment (i.e., ST is monotonically strictly decreasing in z), and the decrease in threat probability increases with per dollar IS investment. This implies that there is increasing scale to IS investment in the reduction of security threat. It is also assumed that
( , ) 0
ST z if z→∞. Hence, ST(θ, z) can be reduced to zero if M sufficiently invests in information security or if it is in the long run. Security threat probability function is defined by1
( , )
ST z ez(1),
where is a positive adjustment variable, 0. Note that probability of the security threat is equal to the probability of hacker attacks (i.e., ST = θ) when no investment is made (i.e., z = 0).
2.2 Successful entry ratio
The first step to have online transactions between M and its customers is that potential customers successfully access the website. The probability that potential customers access the website, successful entry ratio, can be written as
1 Gordon and Loeb (2002) distinguished the security threat probability function into two broad classes:
linear and nonlinear in threat, but the former one is not realistic. In this study, nonlinear security threat probability function is adopted for the optimal return-on-investment analysis.
(1 ) [ ( , )] ( , ) [ ( , )]
SER ST z ST z ST z ,
where (1) and [ST( , )] z are the probabilities of no hacker threat without/with IS investment, respectively, and the third term
( , ) [ ( , )]
ST z ST z is the probability of unsuccessful attacks at given levels of hacker threat and IS investment. Note that SER is within the interval of [0, 1]. Here it is implicitly assumed that the probability of entering M’s website is equal to the probability that the website is intact from hacker attack. Rearranging the above equation,
(1 ) [1 ( , )] [ ( , )].
SER ST z ST z
2.3 Market potential
Customers value products differently due to variety of income and preferences. There are N0 representative customers in the market. Without loss of generality, suppose that the consumer has a valuation of the product, v, and f(v) is the probability density function of the valuation. Assume that the product’s value is full information to customers. A customer buys the product only if its price is set less than its value.
Hence, M’s market potential can be written as:
( ) 0 ( ) .
v p
N p N f v dv
Note that N(p) is a non-decreasing function of price. Then M’s demand would be N(p)×SER.
2.4 Optimal investment versus threat
Monopolist decides the levels of IS investment z to maximize its profit from the sales on the Internet. The problem becomes
0
( 1)
[ ( ) ( )]
. . ( ) ( )
(1 ) [1 ( , )] [ ( , )]
( , ) .
v p
z
Max N p SER p c z
s t N p N f v dv
SER ST z ST z
ST z e
(1) where p is market price, and c is the average cost of the production, (i.e., (pc) is the unit gross earned).
Since security threat probability function ST is monotonically decreasing in z, and M’s profit is concave in z. An interior optimal level of investment in information security can be found by solving for z* in the first order condition given by (1). Let
) (
*
z denote this optimal yield:
) (
* z
12 2 ~
3 4
~2
~
)}
1 ( 8 )]
1 4 6 ( {[
]}
1 ) 2 ( ) 1 ( 2 [ { ln 1
N N
N ,
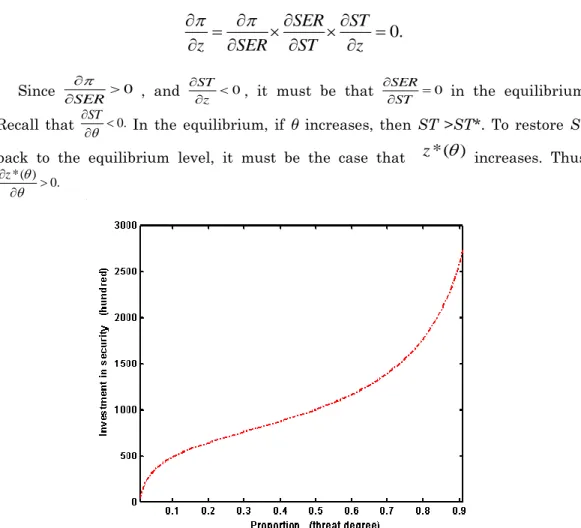
where N~ N p( ) ( p c ) .Plot z*() on the plane of the threat degree and the optimal investment (see Figure 1).2 The figure pattern demonstrates that the optimal investment in security is strictly increasing with the degree of threat. The positive relationship between θ and z*() can be easily verified in general forms by the first order condition in (1), which is
SER ST 0.
z SER ST z
Since 0
SER
, and ST 0
z
, it must be that SER 0 ST
in the equilibrium.
Recall that ST 0. In the equilibrium, if θ increases, then ST >ST*. To restore ST back to the equilibrium level, it must be the case that z*( ) increases. Thus,
*( ) 0.
z
Figure 1. Relationship between investment in security and threat degree In the intervals of low hacker threat and high hacker threat, the slopes of the optimal IS investment are steep, and equivalently, the increments of the optimal IS investment per unit of hacker threat are high. In the interval of intermediate hacker threat, the increment of the optimal IS investment per unit of hacker threat is low.
The economic meanings for the phenomena are provided as follows: In a low hacker threat stage, the monopoly needs to spend lots of resources on information security infrastructures such as equipment, firewalls and antivirus software. These investments are seen as the “sunk cost” of the IS investment. Once the IS infrastructures are built up, less resources are needed in additional IS protection, such as upgrading of old IS safeguards and educating extra IT employees regarding the stage of an intermediate hacker threat. In a high hacker threat stage, the
2 In Figure 1, the numerical values of 0.000000001,(pc)1and N p( )100, 000are assumed. The z*()are plotted with the level of threat degree θ between 0.1 to 0.9.
monopoly’s revenue loss due to hacker attack substantially hikes if no IS investment is done, and hence, the optimal IS investment per unit of hacker threat will increase.
It is generally recognized in the literature that the concept of ROI is widely used to measure the effectiveness of security processes (Surmacz, 2002; Newman, 2003;
Leach, 2003; Berinato, 2002). However, the risk of cyber attacks has been ignored in calculating quantitative ROI values. Moreover, how the benefit-cost ratio fluctuates with threat degree is more interesting. The threat degree divided by the level of monetary IS investments (i.e., θ/z*() is the inverse of the slope for the optimal
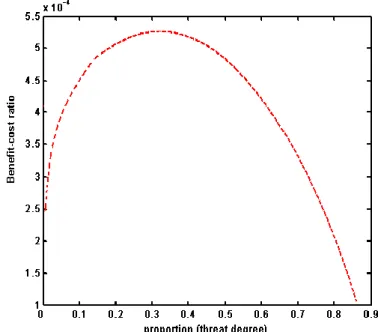
investment curve to the origin in the above figure). The relationship between benefit- cost ratio and the levels of threat degree is illustrated in Figure 2.
Figure 2. Relationship between benefit-cost ratio and threat degree
The benefit-cost ratio illustrates the efficiency of IS investment against hacker attack at different levels of threat degree. The above benefit-cost ratio curve is strictly concave in regard to threat degree, and the marginal increase in the benefit- cost ratio is strictly decreasing in regard to threat degree. Namely, in the equilibrium, the degree of hacker threat defended by each dollar spent on IS investment strictly decreases with the threat degree. This property stems from the assumption of strictly concave security threat probability on IS investment.
COROLLARY 1. The information security investment benefit-cost ratio of a profit- maximizing monopoly is strictly concave in regard to threat degree.
This corollary implies that there exists a unique optimal effective security investment level when the degree of threat is within the intermediate level. At a low degree of threat, it would be inefficient for the monopoly to invest a lot in purchasing expensive information security safeguards. Similarly, in the case of a high threat degree, less security improvement is achieved with additional investment.
Economic intuition mainly lies on decreasing marginal return to information security investment, which is consistent with the preliminary empirical work done by Tanaka et al. (2005). The results were similar to a conclusion that managers allocating an information security budget should normally focus on information which falls into the midrange of vulnerability as demonstrated from theoretical analysis (Gordon and Loeb, 2002). Tanaka et al. (2005) showed empirical evidence
that the security investment level is greater than usual not when an information set is highly vulnerable but rather when it is vulnerable at a medium level.
2.5 Numerical analysis of market potential
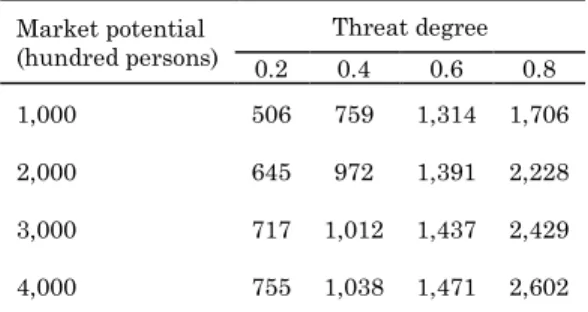
In this subsection, the impact of market potential on the optimal IS investment is proceeded by the following numerical analyses. The level of the optimal IS investment is calculated for different levels of market potential and degrees of threat (see Table 1). Table 1 reveals that the larger market potential is, the greater the IS investment is in equilibrium. An explanation is provided as follows: When market potential is large, the demand the monopoly has is large. As a result, the loss it faces will be larger when a hacker attack is successful, i.e. shutting down its online sales.
Hence, the IS investment made by the monopoly will increase with the level of market potential. This is the case where large e-commerce firms such as Yahoo and Amazon have invested substantial amounts of resources on information security designed to protect them against cyber-crimes.
Table 1. The optimal IS investment level for different levels of market potential and degrees of threat Market potential
(hundred persons)
Threat degree 0.2 0.4 0.6 0.8
1,000 506 759 1,314 1,706
2,000 645 972 1,391 2,228
3,000 717 1,012 1,437 2,429 4,000 755 1,038 1,471 2,602
COROLLARY 2. The optimal investment in information security strictly increases with market potential and degree of threat.
Next, the increment of the optimal IS investment level is calculated when the size of market potential increases, as shown in Table 2. It can be seen that this increment decreases with the increase in market potential. The reasons for this also include the
“sunk cost” of IS investment and the increasing scale of IS investment.
Table 2. The increments of optimal IS investment levels for different levels of change in market potential and degree of threat
Change in market potential (hundred persons)
Threat degree 0.2 0.4 0.6 0.8
1,000→2,000 139 213 77 522
2,000→3,000 72 40 46 201
3,000→4,000 38 26 34 173
COROLLARY 3. The increment of the optimal information security investment strictly decreases with changes in market potential and degree of threat.
In the above discussions, the relationships among the optimal investment, threat and market potential are revealed. Hence, the optimal investment strategies in information security for monopolist are summarized as follows:
PROPOSITION 1. Consider a profit-maximizing monopoly that sells products online and faces an attack from cyber criminals. There exists a unique optimal investment
level for the monopoly in information security. This optimal investment strictly increases with market potential and degree of threat, but the increment of the optimal investment strictly decreases with the change in market potential and degree of threat. Finally, the benefit-cost ratio of investment versus threat is strictly concave in regard to threat degree.
The positive relationship between the optimal investment and market potential and degree of threat is consistent with the findings of Cavusoglu et al. (2004b) in that the more dependent a firm is on the Internet, the more significant the consequences of an attack will be on the financial health of that firm.
3. OPTIMAL INVESTMENT IN A DYNAMIC SETUP
In this section, the time factor is incorporated in the optimal investment in information security of a monopoly in a dynamic setup. The monopoly is intended to maximize aggregate profits in a finite time period. The demand for the products sold on-line is affected by the degree of website quality improvement with regard to attractiveness and as a result of word of mouth among consumers.
3.1 Awareness diffusion
Consider a profit-maximizing monopoly that offers a product on-line in a finite time frame {1, 2, …, T}. Let N0 be the initial population of potential consumers for the product. A consumer purchases the product only if he is aware of the existence of the monopoly and if the price is no greater than his willingness to pay. Let yt be the set of the population who are aware of the monopoly at time t. Then kt is the percentage of the awareness population at time t, namely, kt y Nt 0.
Note that an unaware consumer never purchases the product from the monopoly.
The rest of the population who is unaware of the monopoly at time t, N0-yt, can be informed either by word of mouth or by the increase in the quality of the monopoly’s website. An investment zt by the monopoly at time t promotes its website by spending on higher information security, advertisements in protocol websites, and better layouts in the website for user browsing, etc. Let g(zt) be the attractiveness to consumers due to the quality improvement of the monopoly’s website with the investment zt. Assume that g(0) = 0; g’(zt) > 0, and g’’(zt) < 0. Namely, the attractiveness function form is in concavity, and there is a saturation level at some point. Word of mouth for the product is diffused at the rate of w, 0<w<1, among the consumers who purchase the product. The information communication among the consumers increases the size of the awareness population. Hence, awareness diffusion among the population across periods can be written as
1 [1 1][ ( ) 1].
t t t t t t
k k k k g z wk
The above equation implicitly assumes that all potential consumers are homogeneous with respect to information diffusion.
3.2 Dynamic Demand
The monopoly’s demand at time t is the subset of the awareness population who has the willingness to pay no less than the price of the product. Namely, N p( )kt,
where ( ) 0 ( )
v p
N p N f v dv
and f(v) are the probability density function of the valuation. Assume that the consumer who purchased the product at previous period t-1 continuously purchases at the same price level at time t. The expected newadoptions at the time t are:
[ ( ) 1]
e
t t t
y N p k y
, where kt kt 1 kt
is given by the awareness diffusion equation above.
3.3 Policy Implication
The monopoly maximizes the net present value of its cash flows from time 1 to T.
Denote byyte as the expected product sales at time t, by c as unit cost of the product, and by r the discount rate. The optimal investment decision of the monopoly in this dynamic setup is
1
1
1 1
[( ) ]
. . [ ( ) ]
[1 ][ ( ) ].
T
rt e
t t
e
t t t
t t t t
Max e p c y z dt
s t y N p k y
k k g z wk
(2)
By the maximum principle, the Hamiltonian in current values is
1 2
( , te, t) t t te t t H TR p y k z y k ,
where TR(.) is the gross profit, and t1 and t2 are the adjoint (co-state) variables which represent the value of the shadow price for an expected adopter and an existing user, respectively.
The optimality conditions to the problem in (2) deliver:
2 2 '
1 t t 1 t (1 t 1) ( )t 0
t t
k
H k g z
z z
and 1 0.
e t t
y
H TR
p p p
Hence,
2
1
1
(1 ) '( )
t
t t
k g z
and
1 .
t
e e
t t
TR
TR p
y y
p
Note that t1 and t2 are neither zero nor infinity. Therefore, there must be an internal solution. By taking the derivative of t2 with respect to time t and by the first order condition, H kt rt2t2, we obtain:
2 1
2 1
"( )(1 ) '( )
[ '( )(1 )]
t t t t
t
t t
g z k z g z k
g z k
and
2 2 1 2
e
t t
t t t t
t t t
y k
r dTR
dk k k
,
where
•
.
zdz dt Then equating the above two equations,
1 1
2
1 1
"( )(1 ) '( ) 1
[ ] .
[ '( )(1 )] '( )(1 )
e
t t t t t t
t
t t t t t t t
g z k z g z k k TR y
g z k r k g z k k k
Note that when t
t
k k
(1kt1)w[ ( )g zt wkt1], then
1
1 1
"( )
(1 ) '( )(1 )[ ].
'( )
e
t t
t t t t
t t t
g z dTR y
z r k w g z k
g z dk k
Substitute t1 into the above equation,
1
"( )
(1 ) .
'( )
t
t t
g z
z r k w
g z
Note that g’ (zt) >0 and g’’ (zt) < 0. If discount rate r is low enough such that r-(1- kt-1)w < 0, then z• 0.Namely, the investment in information security monotonically decreases along with the time but it is nonzero until the end of time T. Therefore,
PROPOSITION 2. When the discount rate is low (such that r (1 kt1)w) or there is a zero discount rate, the optimal investment in information security monotonically decreases over time until the end of the time period.
The proposition holds because of decreasing marginal improvement by security investments. Moitra and Konda (2000) found that as the investment in security increases, the survivability of firms from security breaches increases rapidly at first and then more slowly at higher levels of investments.
4. OPTIMAL INVESTMENT TIME IN SECURITY UPGRADE
The section considers the problem in which monopoly M decides when to upgrade its security investment from generation I to generation II (e.g., Windows OS; Cisco Integrated Services Routers) in an infinitely continuous time frame from 0 to T. Let tc represent the terminal time for security investment for generation I. Assume that consumers in generation I continue to purchase the product in generation II regardless of the security upgrade. Namely, II ( ) I ( ).
e c e c
y t y t Also, the expected new added adoptions (or sales sit) in time t are a function of price, unit cost and investment in information security
( ) ( , , ), , .
e i
i i i i
dy t G p c z i I II
dt