Operating System Exam (For Grade 2000)
Class Name Student ID
一、For each of the following statements, Choosing True or False (24 marks)
1. Binary semaphores are those that are used by no more than two threads.
2. The Banker's algorithm is a way of preventing deadlock .
3. A multi-level indexed file permits faster random access than a contiguously allocated file.
4. An atomic operation is a machine instruction or a sequence of instructions that must be executed to completion without interruption.
5. Deadlock is a situation in which two or more processes (or threads) are waiting for an event that will occur in the future.
6. Starvation is a situation in which a process is denied access to a resource because of the competitive activity of other, possibly unrelated, processes.
7. While a process is blocked on a semaphore's queue, it is engaged in busy waiting.
8. Mutual exclusion can be enforced with a general semaphore whose initial value is greater than 1.
9. External fragmentation can be prevented (almost completely) by frequent use of compaction, but the cost would be too high for most systems.
10. A page frame is a portion of main memory.
11. The working set of a process can be changed in response to actions by other processes.
12. Thrashing will never be a problem if the system has 1 GB of real memory.
13. A printer is an example of a logical resource.
14. Versions of OS/360 are still widely used today.
15. When an executing process is stopped by the scheduler, it is said to be blocked.
16.Interrupts are used to achieve a typical timesharing OS.
二、Multiple Choice Questions (30 marks)
For each of the following questions, There is only one correct answer.
1. What is the purpose of system calls?
a) System calls allow user-level processes to gain resources from the operating system.
b) System calls are the standard interface between a user process and a kernel process.
c) System calls allow user-level processes to request services of the operating system.
d) There is no real purpose to system calls.
2. Threads belonging to the same process share the a) stack b) data section
c) register set d) thread ID
3. In
Many-to-One
thread model,
What would happen if a thread in a multithreaded process makes a blocking system call ? ba) the other threads of the process would continue to run b) the entire process would get blocked
c) the blocking thread will get killed
d) the blocking thread will never get to run again
4. Which of the following Operating systems uses preemptive scheduling?
a) Mac OS 8 b) Windows 3.x
c) Windows 2000 d) DOS 6.0
5. A measure of the number of processes completed per time unit is called a) throughput b) waiting time
c) response time d) CPU utilization 6. One of the problems with priority scheduling is
a) aging b) starvation
c) process death d) average waiting time
7. Consider the following reference strings
I :{0, 2, 4, 1, 1, 4, 5, 7} ; II :{2, 3, 2, 5, 6, 3, 2, 6}
If the FIFO page replacement algorithm with 3 frames is applied,which of the two reference strings will result in fewer page faults?
a) reference string I b) reference string II
c) both will have the same number of faults d) can’t determine from the given data.
8.In a time-sharing system, which of the following is the best criterion for CPU scheduling.
a) Minimize CPU utilization b) Maximize CPU utilization c) Maximize system throughput d) Minimize response time.
9.The initial value of semaphore S is 2. if the value is -1 at present, how many processes are blocked on this semaphore .
a) 1 b) 2 c) 3 d) 4
10. A system is in a deadlock, if its resource allocation graph a) contains a cycle
b) doesn’t contain a cycle
c) contains a cycle and there is just one instance of every resource d) has at least one outgoing edge from any one of the process nodes
11. Preemption of resources can be enforced to prevent occurrence of deadlocks, but this can’t be applied to all the resource types, as preemption might leave the resource in an undetermined state.
Which of the following resources can’t hence be preempted?
a) CPU registers b) memory space c) tape drive d) all of the above
12. In the page replacement scheme a reference string is
a) the number of frames allocated to a process b) a string of memory references
c) a string of I/O references d) the times spent on each page-fault service 13. Which disk space allocation method supports direct access without external fragmentation? d a) linear b) contiguous
c) linked d) indexed
14. A system is said to be ___________ if it can continue to function even when a node or nodes in the system fail.
a) networked b) distributed c) real time d) fault-tolerant
15. Considering a system, which uses virtual memory. At what point can address binding be done?
a) compile time b) load time
c) execution time d) can be any of the above
16. Which of the following is NOT associated with segments?
a) two dimensional view of memory b) fixed size
c) easy sharing of data or code d) external fragmentation
17. Pages can be shared between processes having common reentrant code. Here reentrant code means
a) self-modifying code
b) code which keeps going in and out of memory c) non-self-modifying code
d) code containing shared data variables
18. The time to position the head on the disk is the a) seek time. b) access time.
c) transmission time d) rotational latency
19. _____________ presents a uniform device-access interface to the I/O subsystem, much as system calls provide a standard interface between the application and the operating system.
a) Kernel b) A set of device drivers c) Bus d) Operating system
20. What is the name of the table containing information about all open files?
a) file allocation table b) open-file table c) file table d) file access table 三、Consider the following set of processes: (10marks)
Process Burst-Time Priority P1 15 4 P2 3 8 P3 7 5
P4 5 2
P5 1 6
P6 2 6
The processes are assumed to have arrived in the order P1, P2, P3, P4, P5, P6, all at time 0.Use FCFS, SJF, Round Robin (quantum is 2), Priority(low numbers have high priority). For each of the algorithms:
1 Draw a Gantt chart
2. What is the average waiting time for each of the scheduling algorithms? 3. What is the average turnaround time for each of the scheduling algorithms?
四、Consider a computer system with the following hardware characteristics. (12marks) Main memory size = 16 Mbyte
Main memory access time =100 nS Average disk transfer speed = 1 Mbyte/sec Average disk seek plus latency time = 20 mS Smallest addressable unit = 4 bytes (i.e. 1 word)
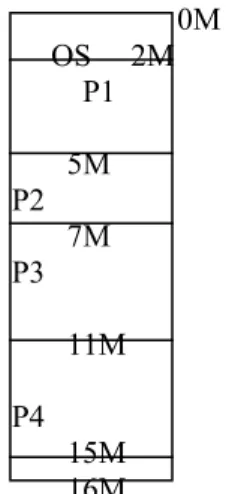
1.Consider an operating system A, which is using contiguous memory allocation scheme. Assuming the entire process, P1 (3 Mbyte), is currently in memory,
(1) At time t1, P1 is to be swapped out of memory, what is the time required to roll out P1 to the disk?
(2) At time t2, shortly after t1, a new process, P5, of size 4 Mbyte, arrived. Given the snapshot of the memory allocation at time t1, shown in figure 1. Can P5 be rolled in?
0M OS 2M
P1 5M P2 7M P3 11M P4 15M 16M
Figure 1. Process Partition Map
2. Consider again another operating system B, which is using a basic paging system (without using demand paging) with a logical address space of 4,096Kbyte and page size of 256Kbyte (or 65536 words, noting that the smallest addressable unit is a word).
(1) How many frames are there in the system?
(2) Show the format of the logical address (i.e. How many bits for page number? How many bits for page offset etc.).
(3) If a translation look-aside buffer (associative register) with an average access time of 20nS is available/implemented in the hardware, assuming a hit ration of 90%, what is the effective memory access time now?
(4) Shortly after t1, where all pages belonging to P1 have swapped out, a new process, P5, of size 4 Mbyte, arrived. Again, referring to the snapshot of the memory allocation at time t1, shown in figure 1.
Can P5 be rolled in?
五、
There are three cooperative processes P1, P2, and P3. They read data , denoted as
a 、 b and c,from the same input device,as shown in figure below. The input device is
an exclusive access device.The first datum(a) must be read by process P1, the second
datum(b) is read by process P2, and the third datum(c) by process P3. These three
processes perform the following calculations:
P1: x = a + b P2: y = a * b P3: z = y + c - a
P1, which is linked to the printer, should print the results of x,y, and z. Write the pseudo code for the three processes, using semaphores to synchronize their activities. (12marks)
六、
Consider a file system,there is a file of size 20MB . For each of the five allocation strategies:contiguous allocation, linked allocation, index-linked allocation(linked scheme) ,two-level indexed allocation and combined scheme allocation(linux ) . assume that the system block size is 4KB, the block pointer is 32 bits .answer these questions:
1.What is maximum
file size supported by each of the allocation strategies ?
2.Assume File Control Block is already in main memory. Calculate how many disk I/O operations are required to access the byte in position 16M+5.5K for each of the allocation strategies。(12marks)
PART II Lab Exam
一、Select the correct answer for the questions (20marks)
1.Which system call creates a new process:
a) fork b) exec c) creat d) nproc
2.What is the meaning of the “execute” permission bit for a directory in LINUX?
a) allows execution of files in that directory
b) allows access to a file in the directory if the file's name is known c) allows listing of directory contents
d) no meaning, as directories are not executable files 3. The shell is simply
a) a command-line interpreter. b) a privileged program.
c) a GUI interface. d) a set of commands.
4. The LINUX operating system handles deadlock by
a) prevention b) avoidance
c) detection d) none of the above
5. The LINUX operating system uses a magic number at the beginning of every file system.What is P1
P2
P3
Non-preemptive input device
Input(a)
Input(c) Input(b)
the purpose of this number?()
a) the size of file b) to count the number of files on the system c) roughly indicate the type of file system d) file protection
6. Consider the following situation on a LINUX system
User A has a file xxx and allows user B to make a symbolic link to this file. Now user A deletes the file from his directory. Which of the following options best describes what happens next?
a) The file gets deleted and B ends up with an invalid link
b) The file remains in A’s disk quota as long as B doesn’t delete the link c) The file ownership is transferred and is moved into B’s disk quota d) A will not be able to delete the file.
7.The Linux command to create a filesystem is
a) mknod b) fdisk
c) format d) mkfs
8. The dup() system call in LINUX comes under a) process system calls b) file system calls c) communications d) memory management 9. The default Linux partition type is
a) vfat b) ext2 c) swap d) dos
10 Which statement is valid in LINUX environment:
a) Foreground process keeps the control of the keyboard and display screen.
b) Background process keeps the control of the keyboard and display screen.
c) We can not suspend a background process.
d) Both A and C.
二、Consider the following LINUX program: (14marks)
#include <stdio.h>
int z = 0;
int main() {
int *a = 0;
int pid = getpid();
if (pid = fork()) {
a = (int *) malloc(100*sizeof(int));
z = pid;
printf(“z1 = %d\n”, z);
} else { a = &z;
*a = pid;
printf(“z2 = %d\n”, z);
}
printf(“all done, pid = %d\n”, pid);
}
Suppose the parent process is pid 2044. The child process is pid 2066. Show the two possible output displays, assuming all the output from a process is displayed together.
三、The following is the source code of Linux system call sys_flock() ,Please briefly describe its functionality, and please show the algorithm flow of flock_lock_file()(16 marks)
/**
* sys_flock: - flock() system call.
* @fd: the file descriptor to lock.
* @cmd: the type of lock to apply.
* Apply a %FL_FLOCK style lock to an open file descriptor.
* The @cmd can be one of * %LOCK_SH -- a shared lock.
* %LOCK_EX -- an exclusive lock.
* %LOCK_UN -- remove an existing lock.
* %LOCK_MAND -- a `mandatory' flock. This exists to emulate Windows Share Modes.
* %LOCK_MAND can be combined with %LOCK_READ or %LOCK_WRITE to allow other * processes read and write access respectively.
*/
asmlinkage long sys_flock(unsigned int fd, unsigned int cmd) {
struct file *filp;
int error, type;
error = -EBADF;
filp = fget(fd);
if (!filp) goto out;
error = flock_translate_cmd(cmd);
if (error < 0) goto out_putf;
type = error;
error = -EBADF;
if ((type != F_UNLCK)
#ifdef MSNFS
&& !(type & LOCK_MAND)
#endif
&& !(filp->f_mode & 3)) goto out_putf;
lock_kernel();
error = flock_lock_file(filp, type,
(cmd & (LOCK_UN | LOCK_NB)) ? 0 : 1);
unlock_kernel();
out_putf:
fput(filp);
out:
return error;
}
/* Try to create a FLOCK lock on filp. We always insert new FLOCK locks * at the head of the list, but that's secret knowledge known only to
* flock_lock_file and posix_lock_file. */
static int flock_lock_file(struct file *filp, unsigned int lock_type, unsigned int wait)
{
struct file_lock *fl;
struct file_lock *new_fl = NULL;
struct file_lock **before;
struct inode * inode = filp->f_dentry->d_inode;
int error, change;
int unlock = (lock_type == F_UNLCK);
/* If we need a new lock, get it in advance to avoid races. */
if (!unlock) {
error = -ENOLCK;
new_fl = flock_make_lock(filp, lock_type);
if (!new_fl) return error;
}
error = 0;
search:
change = 0;
before = &inode->i_flock;
while (((fl = *before) != NULL) && (fl->fl_flags & FL_FLOCK)) { if (filp == fl->fl_file) {
if (lock_type == fl->fl_type) goto out;
change = 1;
break;
}
before = &fl->fl_next;
}
/* change means that we are changing the type of an existing lock, or else unlocking it.*/
if (change) {
/* N.B. What if the wait argument is false? */
locks_delete_lock(before, !unlock);
/*If we waited, another lock may have been added ... */
if (!unlock) goto search;
}
if (unlock) goto out;
repeat:
for (fl = inode->i_flock; (fl != NULL) && (fl->fl_flags & FL_FLOCK);
fl = fl->fl_next) {
if (!flock_locks_conflict(new_fl, fl)) continue;
error = -EAGAIN;
if (!wait) goto out;
error = locks_block_on(fl, new_fl);
if (error != 0) goto out;
goto repeat;
}
locks_insert_lock(&inode->i_flock, new_fl);
new_fl = NULL;
error = 0;
out:
if (new_fl)
locks_free_lock(new_fl);
return error;
}