A Serial Access Control MAC for IEEE 802.11 Ad Hoc
Networks
*
Shih-Chang Huang
†Department of Computer Science and Information Engineer National Formosa University
Yunlin, Taiwan, ROC Email :schuang@nfu.edu.tw
Abstract- This paper proposes a novel contention-free
medium access control approach for the IEEE 802.11 wireless ad
hoc networks. Stations are arranged to access the medium one by
one during the Announcement Traffic Indication Messages (ATIM) window, which is used by every station in IEEE 802.11 ad hoc networks to announce the existence of buffered frames. The proposed approach can dynamically shift the boundary between the ATIM window and the data transmission window to improve the bandwidth utilization. Furthermore, the stations in power-saving (PS) mode can enter the active state just in time to receive data and return to the sleep state as fast as possible. The proposed approach can easily apply to the infrastructure mode of IEEE 802.11 wireless networks. Simulation results show that the proposed approach can have better bandwidth utilization and fewer queuing buffers than IEEE 802.11. Stations can achieve
the object of collision free without retransmitting packets.*†
Keyword: 802.11, contention-free, MAC, bandwidth utilization,
energy efficiency.
I. INTRODUCTION
The IEEE 802.11 wireless local area networks [1] have been widely deployed in home, enterprises buildings, or public place. The wireless technique can provide users who are under the radio coverage freely access the networks by mobile devices without being limited by either the locations of physical network access ports, which are set up in the wired network or the locations of the alternating current (AC) power on the wall.
However, the wire-free of the mobile devices brings new issues. At first, the AC power is replaced by batteries. Due to the limited power resource on the batteries, prolonging the operation duration of a mobile device needs to save the unnecessary power consumption. In the communication, a simple power-saving (PS) mode which properly disables the wireless interfaces of a mobile device has designed in the standard to save the power of idly medium monitoring. The PS mode is also called as sleep mode. In order to save more power, much advance research has been proposed to control the sleep period [3][4][5][6][7] for saving power.
Secondly, the transmission medium changes to the open radio space. Stations contend the medium to get the opportunities of packet transmission. The packet collision probability will increase when the number of stations in the
*
This work was supported in part by the National Science Council, Taiwan, ROC, under grant NSC98-2218-E-150-001.
†
Corresponding Author. email :schuang@nfu.edu.tw
network grows. Packet retransmission not only reduces the bandwidth utilization but also wastes the precious energy of the battery. Although a random back-off mechanism is designed to avoid packet collision in the IEEE 802.11 WLANs standard, the problem of packet collision still causes long transmission delay, poor bandwidth utilization [8] and worsens the long-term fairness [9].
Thus, the time slot approach [10] is proposed for exclusive medium access. In the time slot approach, the network bandwidth is divided into multiple time slots as the time division multiple access (TDMA). Each station is assigned to a dedicate time slot, which is an exclusive period for data transferring. In this approach, a fixed ATIM window size is still used for reserving slots to stations. However, fixed ATIM window size is another reason that reduces bandwidth utilization and energy efficiency in the IEEE 802.11 WLANs standard.
From the observation of both contention-based and slot-based approaches, this paper proposes a novel slot-slot-based approach to improve the bandwidth utilization and energy efficiency of the approaches which use fixed ATIM window size and free the collision problem caused by contention-based approaches. The proposed approach modifies the random back-off mechanism in the IEEE 802.11 WLANs standard and schedules the medium access sequence of stations to eliminate the packet collision problem in the ad hoc networks. The fairness on medium access is also considered. At last, we also discuss the mechanism to apply the proposed approach to the infrastructure mode of IEEE 802.11 wireless network environment.
The rest of this paper is organized as follows. In the section 2, we detail the mechanism of proposed approach. Section 3 gives the simulation results of our proposed approach to exhibit the strong point of our approach. Finally, the conclusions are given in section 4.
II. THE SERIAL ACCESS CONTROL(SAC)
This section will give the detail operation of the Serial Access Control MAC in the ad hoc network. The delay time to successfully announce the ATIM frame is also analyzed. At last, the SAC is applied to the infrastructure mode wireless network.
A. Ad hoc mode
As the power saving mode in the IEEE 802.11 WLANs standard, the SAC MAC divides the beacon interval into two parts, the ATIM window and the data transmission window. All stations have to propose the transmission request within the ATIM window to reserve the transmission opportunities in the data transmission window. Stations that do not operate in sleep mode also follow this rule. Stations also have to follow the basic back-off mechanism of IEEE 802.11 WLANs standard for medium access.
To free the contention from the original back-off mechanism, SAC sequentially controls the medium access order of stations. Initially, each station Si negotiates with each
other to get a unique number Өi {1, 2, 3, …, n | n is total
number of stations} as its access order in the ATIM windows. Each station sets its back-off counter to Өi - 1. By applying
different back-off time for each station, the objective of contention-free is achieved.
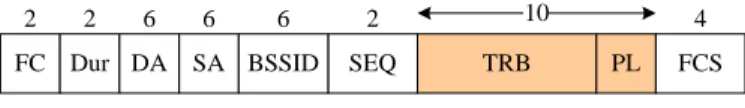
FC Dur DA SA BSSID SEQ TRB PL FCS
2 2 6 6 6 2 10 4
Figure 1 the modified ATIM frame
Two new fields are appended to the ATIM frame for SAC, the TRB (target receiver bitmap) and the PL (packet
length). The frame format of ATIM frame is modified as
Figure 1. TRB is a bitmap used by the sender to indicate which station will receive its data. The sender marks the bit corresponding to each of its receivers to 1 and others to 0. All receivers can be notified by single ATIM frame.
Length of all packets from the ATIM frame sender is summed in the PL field. The PL field helps those stations operating in power-saving state easily to estimate what time they need to enter the active state to send out during the data transmission window. They can enter the sleep mode at the end of ATIM window and wake up just on time. Consequently, when those stations finish all their data transferring, they can go back to sleep mode again to save power.
By staying in the active state during the ATIM window, stations can trace the ATIM frame transmitting order. Stations which have successfully announced the ATIM frames in the ATIM window follow the order that they announce the ATIM frames to access the data transmission window. Stations in PS mode can also compute their wake-up time exactly.
The SAC approach dynamically regulates the length of ATIM window according to the network traffic. To determinate the termination of the changeable ATIM window, the mechanism in the standard must be changed. In SAC approach, a station continuously counts down its back-off counter even zero is reached. Every station Si can
independently use equation (1) to determinate the termination of the ATIM window.
n – (Өi –Ci) = 0 (1)
The Ci in equation (1) is the current back-off counter of Si and
n is total number of stations.
The SAC approach needs well clock synchronization between stations. For avoiding the clock drafting during the ATIM window, all stations adjust their timer and back-off counters whenever an ATIM frame is heard. When the station in the jth position of the access order hears the ATIM frame sent by the station in ith position of the access order, the station will adjust its back-off counter to j – i.
Furthermore, every station needs to estimate whether the remaining bandwidth capacity is still enough before it announces the ATIM frame. A station must give up transmitting ATIM frame if the remaining bandwidth capacity is not enough. By estimating the remaining bandwidth capacity, the circumstance that a station successfully announces and ATIM frame but fails to win the medium during the data transmission window can be avoided.
Br = Bt –BAtim– BData – Bc (2)
The remaining bandwidth capacity of a beacon interval is estimated by equation (2). Br is the remaining bandwidth
capacity in current beacon interval. Bt is the total bandwidth
capacity of one beacon interval. BAtim is the bandwidth
capacity consumed by those ATIM frames that have exchanged in the current ATIM window. BData is the
bandwidth capacity of data, which is accumulated from the PL of successfully transmitted ATIM frame. Bc is the bandwidth
capacity consumed by a station to count down it back-off counter. When a station evaluates the remaining bandwidth capacity, it assumes that all other stations with access order behind itself have no data to send.
To maintain the fairness on medium access, each station
Si rotates its access order every beacon interval by changing its unique ID Өi to (Өi+1) mod n, where n is total number of
stations. Every station also needs to issue a dummy frame every 2 beacon-intervals to proclaim its existence. Otherwise, it will be departed from the network. While a station has been detected departing from the network, the stations with access order larger than the departing station will step forward their access order. While a new station joins, its access order is set to the last one in the access order. This new station broadcasts its join message to other stations. Total number of stations in the network can be updated periodically.
Figure 2 shows an example of SAC. There are six stations in it. Station D operates in PS mode. The number denoted on the ATIM frame represents the time units (TUs) to transfer the data with length equal to the PL field. Assume that the capacity of Bt is 250 TUs. Sending an ATIM frame needs
10 TUs. A DCF Interframe Space (DIFS) in the IEEE 802.11 requires 2 TUs, and 1 TUs is needed to count down back-off counter by one.
Initially, their access order is A, B, C, D, E, and F. In the first beacon interval, shown in figure 2(a), there are pending data in station A, B, D, F. The sizes of their pending
data are 60, 30, 50, and 20 TUs. Before A sends the ATIM frame, it estimates the remaining bandwidth capacity Br.
Station A consumes (10 + 2) TUs for its ATIM frame and one DIFS in the ATIM window. The length of its data is 60 TUs but targets to two stations. (60 + 4) TUs are required for its data and 2 DIFSs. Finally, 5 TUs are reserved for the back-off time of other five stations. The Br is 250–(10+2)–
(2+30+2+30)–5=169>0. The bandwidth capacity is still enough and the station A starts to deliver its ATIM frame. The other stations decrease their back-off counters by one and then freeze until current transmission finished. Station B is similar to station A. Station B has Br=126>0. The bandwidth capacity
is still enough. Due to the station C gives up announcing its ATIM frame, all the other stations continuously decrease their back-off counters. While the back-off counter of D reaches 0, it has the Br=63> 0. Station D can also send its ATIM frame.
Finally, station F estimates its Br = 27 > 0 and transfers it data.
Every time a station finishes its data transfer, all stations use the equation (1) to check if the ATIM window is terminated.
ATIM window B C D F E A 30 60 0 1 2 3 4 5 -1 0 1 2 3 4 -2 -1 0 1 2 3 -3 -2 -1 0 1 2 -4 -3 -2 -1 0 1 -5 -4 -3 -2 -1 0 50 20
Data transmission window
30 20 30 30 50 60 30 50 20 1 1 0 0 0 0 60
DIFS ATIM frame Data frame Wakeup
(a) ATIM window B C D F E A 90 50 5 0 1 2 3 4 3 -2 -1 0 1 2 1 -4 -3 -2 -1 0 90
Data transmission window
60 90 4 -1 0 1 2 3 30 0 -5 -4 -3 -2 -1 90 90 2 -3 -2 -1 0 1 50
DIFS ATIM frame Data frame Wakeup
0 1 0 1 0 0 90
(b)
Figure 2 an example of SAC
After station F issues its ATIM frame, all stations sense the end of ATIM window and start the data transmission window. By tracing the packet length of other stations from the ATIM frames, station D enters the PS mode when ATIM window terminates. It renters the active state after station B finishes its data transmission.
In the next beacon interval, shown as figure 2(b), station B, D, E, have data to send and each of their data sizes is 90, 90, and 50. The accessing order rotates and becomes B, C, D, E, F, and A. The operations of station B and D are similar to the first beacon interval. When station E estimates the remaining bandwidth capacity and has Br=-26 < 0, it knows that the
bandwidth capacity is not enough and gives up transferring data in this beacon interval.
B. Waiting time on sending an ATIM frame
Before we evaluate the average waiting time for a station to send an ATIM frame, we define some notations. Assume that CWmin is the minimum contention window. m is
the maximum back-off stage. p is the collision probability of a packet. E[Z] represents the average number of back-off slots before a station successfully delivers a packet. Ivan and Natt [11] deduced that the E[Z] in IEEE 802.11is 1+E[backoff interval], ie.
min 0
1
min min min
2
1
[ ] 1
2
1
(
2) 2
2(1 2 )
i m i m mCW
E Z
CW
p CW
p
CW
p
(4)The probability that station transmits in a random slot, denoted asτ ,
is
]
[
1
Z
E
.Consider the scenario of n stations. When a station transmits an ATIM frame at a time slot and collides with others, there is at least one station transmits ATIM frame at the same time slot. The collision probability p will be formatted as equation (5). 1
)
1
(
1
np
(5) From the equation (5), we have the relation between the packet collision probability p and the number of stations n. The results are shown in table 1.Table 1 - the relation between collision probability and number of stations
n 5 10 15 20 25 30 35 40 45 50 55 60
p 0.29 0.362 0.4 0.428 0.447 0.46 0.47 0.476 0.481 0.484 0.487 0.489
Figure 3 average waiting slots on sending an ATIM frame
For the SAC, because the access order of each station is fixed, the number of back-off slots of each station depends on its position in the access order. For example, the station in the first position is 0, and the second position is 1 and so on. The
maximum number of back-off slots is n. So, the average number of back-off slots for a station is
n ii
n
1)
1
(
1
.Figure 3 shows the average number of waiting slots in the IEEE 802.11 and the SAC approach. The SAC approach obviously reduces more waiting slots than the IEEE 802.11 WLANs standard.
C. Infrastructure mode extension
Applying the SAC approach to the infrastructure mode of IEEE 802.11 wireless network is simple. All stations in the infrastructure mode follow the access order to transfer packets in every beacon interval. Stations which have no packet to send or are in the PS mode give up the transmitting opportunities. Each station with packets to send will keep on monitoring whether it transmitting time arrives. The access order of stations also rotates every beacon interval to maintain the fairness on medium access.
Beacon Interval Beacon Interval Beacon Interval
A B C D 1 3 4 2 1 3 4 2 1 3 4 2
Figure 4 an example of SAC (infrastructure mode)
Figure 4 shows a simple scenario of the infrastructure mode. Four stations are in this example. The initial access order is A, B, C, and D. The station C operates in PS mode. It enters the active state to listen to the medium every 2 beacon intervals. In the first beacon interval, all stations will send packets following the access order. In the second beacon interval, the access order rotates and becomes B, C, D, and A. Because station C enters the power-saving mode, its next station D skips station D and starts to send data. In the third beacon interval, access order rotates again. Four stations operate as the first beacon interval.
III. SIMULATION RESULTS
The results are simulated by using Pythagor 1.2 [12] which is an advanced WLANs Simulator for the IEEE 802.11 protocol created by Dr. Dimitris El. Vassis. Pythagor is a window based simulator and is an open source code.
In this section, the bandwidth utilization, queue length, collision, ATIM windows size will be evaluated. The simulation parameters are shown as table 2.
Figure 5 shows the influence of packet generation rate. Forty stations with constant packet generation rate are simulated. The packet generation rate is ranged from 5 ~ 12 packets per second. Figure 5(a) shows the bandwidth utilization. The bandwidth utilization of SAC increases as the packet generation rate grows. It becomes moderate when packet generation rate is more than 10 packets per second. The bandwidth utilization is about 70%. These results prove that freeing the contention is helpful to increase bandwidth
utilization. For the IEEE 802.11 WLANs, it becomes moderate when packet generation rate is more than 6 packets per second. Its bandwidth utilization is only 50%.
Table 2 - the simulation parameters
Data rate (Mb/s) 2
Packet generation rate(packets/sec) 8, 10, 12
Constant Packet Size (bits) 4000
IEEE 802.11ATIM window size (ms) 25
Beacon interval 100
Slot time (us) 9
Figure 5(b) shows the results of queue length. By fairly change the access order and freeing the possible packet collision, SAC can deliver the packets more efficiently than the original contention mechanism in IEEE 802.11 standard.
(a)
(b)
Figure 5 the influence of packet generation rate on bandwidth utilization and queue length
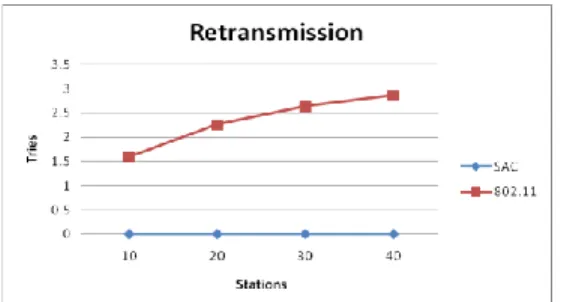
Figure 6 shows the average number of packet retransmission (from 10 to 40 stations, packet generation rate is 12 packets/sec). For the IEEE 802.11 standard, the number of tries is relative to the network load. Even the network load is only 10 stations, the number of average retransmission tries in the IEEE 802.11 standard still needs 1.5 times. When number of stations grows to 40, the number of retransmission becomes triple of 10 stations. By applying the serial access and the remaining bandwidth capacity estimating, SAC does not waste bandwidth on packet retransmission.
Figure 6 the average packet retransmission
Finally, we show the ATIM window size in figure 7. The traffic is simulated in Poisson distribution and the packet generation rate is 10 packets per second with constant packet size 4000 bits. The size of ATIM window in the IEEE 802.11 WLANs is fixed. A research in [13] shows that IEEE 802.11 WLANs standard has best bandwidth utilization when the length of the ATIM window was approximately 25% of the beacon interval.
SAC approach changes the ATIM windows dynamically according to the network load. By compact the duration of ATIM window, we can have better bandwidth utilization as the results shown in figure 5(a). For the IEEE 802.11 WLANs standard, the fixed length ATIM window lowers the bandwidth utilization.
Figure 7 compare the ATIM window size IV. CONCLUSIONS
This paper proposes a contention-free and high bandwidth utilization medium access control approach to improve the IEEE 802.11 WLANs standard. In the proposed approach, the access order of stations is scheduled and the ATIM window size changes dynamically to improve the bandwidth utilization. The fairness to access the medium is also considered. Transferring data size is piggyback on the ATIM frame so that all PS mode stations in our approach can enter the active state just in time to save their energy. Besides, the proposed approach can simply be applied to the infrastructure mode network environment. Simulation results show that our proposed approach can increase the bandwidth utilization and achieve better power efficiency than the IEEE 802.11 standard.
V. REFERENCE
[1] IEEE Std 802.11, “Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications”, Nov 1999.
[2] M. Liu, M.T. Liu, “A power-saving scheduling for IEEE 802.11 mobile ad hoc network”, In Proceedings of IEEE
International Conference on Computer Networks and Mobile Computing(ICCNMC 2003) , pp.238-245, Oct
2003.
[3] H.P. Lin, S.C. Huang, R.H. Jan, ”A power-saving scheduling for infrastructure-mode 802.11 wireless LANs”, Computer Communications, vol. 29, no. 17, pp. 3483-3492, Nov 2006.
[4] E.S. Jung, N.H. Vaidya, “An energy efficient MAC protocol for wireless LANs”, In Proceedings of IEEE
Twenty-first Annual Joint Conference of the Computer and Communications Societies, vol. 3, pp.1756-1764,
June 2002.
[5] R. Krashinsky, and H. Balakrishnan, ”Minimizing Energy for Wireless Web Access with Bounded Slowdown”, In
Proceedings of the 8th Annual Iinternational Conference on Mobile Computing and Networking, pp.119-130, Sep
2002.
[6] A. Sheth, and R. Han, ”Adaptive Power Control and Selective Radio Activation For Low-Power Infrastructure-Mode 802.11 LANs”, In Proceedings of
23rd International Conference on Distributed Computing Systems Workshops (ICDCSW’03), pp.812-817, May
2003.
[7] S.C. Huang, R.H. Jan, and W. Yang, “SCPS: A self-configuring power-saving protocol for wireless ad hoc networks”, Computer Networks: International Journal of
Computer and Telecommunications Networking, vol.
52, Issue 6, pp.1328-1342, April 2008.
[8] Q. Pang, V. Leung, and S.C. Liew,“ Improvement of WLAN Contention Resolution by Loss Differentiation”,
IEEE Transactions on Wireless Communications, 2006
[9] K. Medepalli and F. A. Tobagi, “On Optimization of CSMA/CA based Wireless LANs: Part I - Impact of Exponential Back-off”, In Proceedings of IEEE
International Conference on Communications (ICC’06),.
vol 5, pp.2089-2094, Jun 2006.
[10] A. Bhardwaj, Divya, and S. Sofat, “An Efficient Energy Conserving Scheme for IEEE 802.11 ADHOC Networks”,
In Proceedings of International Conference on Wireless and Optical Communications Networks(WOCN '07),
pp.1- 5, Jul 2007.
[11] I.N. Vukovic, and N. Smavatkul, “Saturation throughput analysis of different back-off algorithms in IEEE802.11”,
In Proceedings of 15th International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC 2004), vol 3, pp. 1870-1875, Sep 2004.
[12] http://www.icsd.aegean.gr/telecom/Pythagor/index.htm [13] H. Woesner, J.P. Ebert, M. Schlager and A. Wolisz,
“Power Saving Mechanisms in Emerging Standards for Wireless LANs : The MAC Level Perspective”, IEEE