Constrained Wavelet Tree Quantization for
Image Watermarking
Min-Jen Tsai and Chen-Long Lin
Institute of Information Management National Chiao Tung University, R.O.C.
ABSTRACT- This paper investigates the operations of the wavelet tree based quantization and proposes a constrained wavelet tree quantization for image watermarking. The wavelet coefficients of the cover image are grouped into super trees for watermark embedding where quantization is performed. The watermark bits are extracted based on a modulus approach and the minimum mean comparison of the super tree coefficients efficiently distinguishes which super tree is quantized. Without the needs of the requantization index at the decoder, the constrained quantization of the super trees reduces the uncertainty of the maximum likelihood detection. Therefore, the robustness of the proposed scheme can be effectively improved. This study has performed intensive comparison for the proposed scheme with the non-constrained tree quantization method under various geometric and nongeometric attacks. The experiment results demonstrate that the proposed technique yields better performance with higher degree of robustness.
1. INTRODUCTION
Digital image watermarking recently attracts many researchers’ interest since the technique can provide useful schema to protect the author’s copyright and legal users’ possession [1, 2]. Among the approaches, wavelet tree quantization [1] based watermarking has shown strong capability in defying spatial and frequency domain based attacks. The wavelet coefficients of the cover image are grouped into super trees. As the tree marking technique spreads the watermark throughout the low to high frequency part of wavelet trees, it can resist frequency components removal and even geometric attacks in the spatial region [1].
After intensive studies on the wavelet tree quantization approaches, we have nevertheless discovered that the decision based on the error
accumulation for the location estimation of the requantization index at the decoder is not generally consistent with the encoder’s. As a consequence, this mismatch aggravates the watermark distinction, especially while the watermarked data is under attacks. Therefore, this article proposes a constrained wavelet tree quantization algorithm where the distribution of the wavelet tree coefficients is analyzed before watermark embedding. With a novel extraction procedure based on the comparison of super trees, the proposed algorithm can overcome the weakness of the non-constrained quantization methods and effectively improve the performance of the wavelet tree based watermarking algorithm.
This paper is organized in the following order. In Section II, the proposed constrained wavelet tree quantization approach is introduced. The performance analysis and comparison are illustrated in Section III and the conclusion is given in Section IV.
2. THE ALGORITHM
The motivation of the proposed constrained wavelet tree quantization for watermarking algorithm is based on the fact: watermark must be embedded somewhere in the cover image with the trade-off between the image quality and the watermark payload [2, 3]. As the results, we consider the condition that even cover image is under the watermark embedding, the image quality should remain high fidelity with the original [1, 3]. Therefore, the proposed technique and [1] are wavelet tree based quantization mechanism while quantization operation is quite different. [1] will quantize the super tree according to the predefined reference error ε and it intends to quantize the whole super tree without considering the energy distribution of the super trees. The proposed technique will consider the energy distribution among super trees and it will only quantize a small portion of the super tree if necessary (i.e. several bit planes will be removed instead of the whole tree). Therefore, the image quality
won’t be affected significantly to cause apparent visual difference.
For the convenience of illustration, a 512×512 image with wavelet transform of four levels is used for
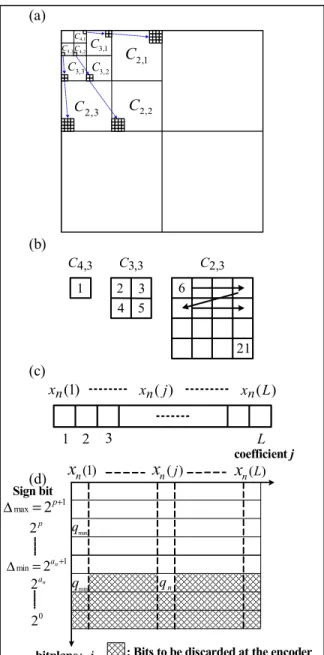
explanation. The decomposition is shown in Fig. 1(a) and each wavelet tree has 21 coefficients as shown in Fig. 1(b). A super tree T is obtained by combining two random selected wavelet trees with total 42 coefficients (L = 42 in Fig. 1(c)). Therefore, there is a total of 1536 (=3×322/2) super trees for this cover image. The watermark sequence is a binary PN (±1) sequence of watermark bits, and each watermark bit is embedded using two super trees; thus the maximum number of watermark bits that can be embedded is 768 (=1536/2). Let the watermark length be Nw, the jth coefficient of the nth tree would be denoted by xn(j) for 1 ≤ j ≤ L and 1 ≤ n ≤ 2Nw. To demonstrate how the quantization of super trees works, a bit plane representation of integer number in binary format is shown in Fig. 1(d). The least significant bitplane (LSB) is denoted by 20, and the most significant bitplane (MSB) is 2p+1 while the sign bit plane is above the MSB plane.
Watermark embedding: The embedding procedure of
the proposed algorithm is similar to [1] but the major difference is the design of a minimum quantization step size ∆min. As shown in Fig. 1(d), the quantization step will be 1
2an+ if the quantization index qn is less than qmin. Therefore, there are L(an+1) bits quantized in the bit plane formation.
Quantization error of super tree coefficient xn(j) is defined as ) ( )] ( [ ) (j Q x j x j en = n qn − n where Q
[
xn(j)]
=round(xn(j))an+1 The total quantization error is∑
= = L j n n n q e j 1 ) ( ) ( εfor super tree Tn. The reference error ε is estimated before the watermark embedding. The index qn is found while (ε2n-1(qn) ≥ ε or ε2n(qn) ≥ ε) and qn≤ qmax. However, the minimum quantization step ∆min will be applied if the total energy of the super trees is less than the reference ε or 2an+1<∆min . Such an approach guarantees every quantized super tree is at least ∆min and no more than ∆min for the super tree with low energy. Therefore, the energy distribution of the super trees is concerned during the implementation of the algorithm. In the similar fashion, ∆max is also applied if qn= qmax and is shown in Fig. 1(d). The watermark embedding is according to the watermark sign bit. If wn = -1, then T2n-1 is quantized, otherwise T2n is quantized.
Watermark extraction: The advantage of ∆min design is that we can guarantee the quantized area of the super (a) 1 , 2 C 2 , 2 C 3 , 2 C 3 , 3 C C3,2 1 , 3 C 3 , 4 C C4,2 1 4, C (b) 3 , 3 C 2 3 4 5 3 , 2 C 6 21 3 , 4 C 1 (c) ) 1 ( n x xn( j) xn(L) 2 3 L 1 (d)
Fig. 1. (a)Wavelet transform in four level
pyramidal decomposition and its subbands. (b)The 21 coefficients of a wavelet tree. (c)Ordered coefficients for a super tree by combining two groups of wavelet trees. (d)Constrained quantization of the nth super tree with respect to a quantization index q at the n
encoder. coefficient j bitplane: i ) 1 ( n
x
x
n( j)x
n(L) 0 2 Sign bit n a 2 1 min=2 + ∆ an 1 max=2+ ∆ p max q min q: Bits to be discarded at the encoder
p
2
n
tree will certainly be larger than or equal to ∆min. Unlike non-constrained quantization approaches, the proposed method holds prior knowledge regarding the format of the quantizer, which due to its indication of certain bit plane values, will be fully removed. Since one tree is quantized and the other is not, they exhibit a large enough statistical difference which will be used for watermark extraction. Therefore, it is not crucial to find the exact location of the ∆′n at the decoder but to seek the tree coefficient distributions, especially the bits within the planes below ∆min. That is to say the constrained quantization operation at least removes all the bits located from the bit plane 20 to 2an . Therefore, the decoder will perform a modularization process first for watermark extraction.
We define x′2n-1(j)m and x′2n(j)m as the modularization results of x′2n-1(j) and x′2n(j), where x′2n-1(j) and x′2n(j) are coefficients of tree pair p′n(T ′2n-1 , T ′2n) at the decoder where 1 ≤ n ≤ 2Nw and 1 ≤ j ≤ L . Since the constrained quantization is performed for every quantized super tree, the goal of the decoder is to identify which tree within the tree pair p′n( T ′2n-1, T ′
2n) is quantized based on the distribution of the tree coefficients of x′2n-1(j) and x′2n(j). Since the bits from the bit plane 0
2 to 2anare removed by the operation of constrained quantization for the super tree, the decoder can simplify the judgment by checking the distribution of the coefficients from x′2n-1(j)m and x′2n(j)m. Therefore, there is an assumption at the decoder: the coefficient values x′2n-1(j)m and x′2n(j)m which are close to 0 or close to ∆min are probably quantized at the encoder.
The errors between │∆min- x′2n-1(j)m│ and │∆min- x′2n(j)m│are probably produced by the quantization, rounding errors or attacks and should be removed as much as possible in order not to interfere with the judgment. Under such condition, a mechanism is designed to remove the errors from │∆min- x′2n-1(j)m│ and │∆min- x′2n(j)m│ where the scalar quantization with rounding operation is applied [4]. The detailed operation can be expressed as:
where Zl(j) = pow2( (int)[log(x′l(j)m)/log 2]+1) and l = 2n-1, 2n, j = 1, 2,..., L. The ambiguous portion of x′ 2n-1(j)m and x′2n(j)m values will be removed by this operation and the remaining values x′2n-1(j)mq and x′2n(j)mq will be utilized to identify the watermark bit
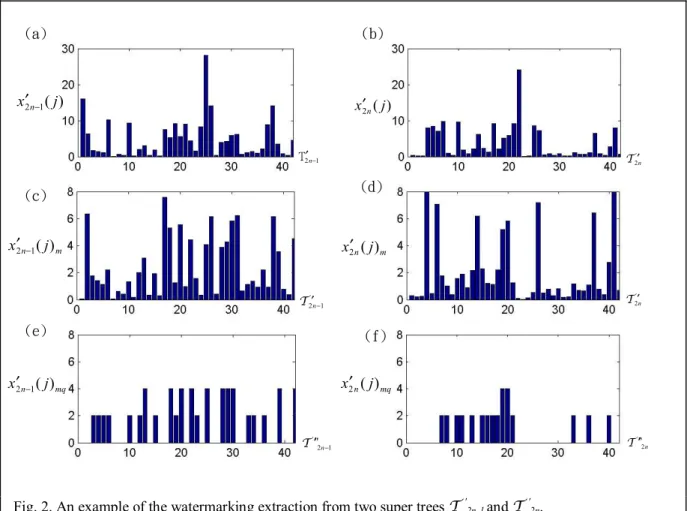
w′n. In addition, if x′l(j)mq =∆min, x′l(j)mq will be reset as 0 to remove the uncertainty of quantized coefficients. Fig. 2 is the example of the watermarking extraction from two super trees. Fig. 2(a) and Fig. 2(b) shows the coefficients values (x′2n-1(j), x′2n(j), j = 1,2,...,42) of two super tree (T ′
2n-1, T′2n) respectively. Fig. 2(c) and Fig. 2(d) are the modularized values (x′2n-1(j)m, x′2n(j)m) for tree (T ′
2n-1, T ′2n) where ∆min= 8. Therefore, all the coefficients of (x′2n-1(j)m, x′2n(j)m) are between 0 and 8. Fig. 2(e) and Fig. 2(f) represents the scalar quantized coefficients (x′2n-1(j)mq, x′2n(j)mq) for the coefficient of (x′2i-1(j)m, x′2i(j)m). In consequence, the decision of watermark bit w′n is computed from Mean( T′mq2n-1) and Mean( T′mq
2n). Since ( Mean(T′mq2n-1) = 1.52 )> ( Mean(T ′mq
2n) = 0.81 ), w′n will be extracted as the value = 1.
To quantify the existence of the watermark after all watermark bits are extracted from the decoder, the normalized correlation coefficient ρ(W,W′)[3] will be examined in order to identify the existence of the watermark. The coefficient value is within -1 and 1. The existence decision is “yes” if ρ(W,W′) ≥ ρT and “no” if ρ(W,W′)<ρT . The threshold ρT is chosen based on the probability of false positive error Pfp which is computed by [5]: ∑ ⋅ − = + × = − w N T w N n n E n w N E w fP P P n N P 2 / ) 1 ( ) 1 ( ρ
In this study, the correlation threshold ρT is chosen to be 0.23 for a false positive probability Pfp of 1.03x10
-7given N
w =512 in order to have the performance
0 , if x′l(j)m = 0 Zl(j) , if x′l(j)m ≧ Zl (j)-Zl(j)/4 = ′ mq l j x( ) Zl(j)- Zl(j)/2 , otherwise TABLE I
COMPARISON OF THE PROPOSED METHOD AND THE METHOD OF [1]
[1] Proposed Approach
Method
Attack Lena Peppers Goldhill Lena Peppers Goldhill (A) 0.15 0.23 0.34 0.45 0.44 0.37 (B) NA NA NA 0.37 0.29 0.23 (C) 0.21 -0.06 0.36 0.32 0.23 0.27 (D) 0.23 0.24 0.35 0.38 0.33 0.36 (E) NA NA NA 0.43 0.32 0.41 (F) 0.26 0.29 0.29 0.27 0.35 0.36 (G) o.25 0.25 0.28 0.29 0.26 0.31 (H) 0.52 0.38 0.64 0.51 0.27 0.51 (I) 0.11 0.18 0.22 0.24 0.29 0.25 (J) 0.24 0.25 0.25 0.30 0.38 0.30 (K) 0.24 0.15 0.17 0.25 0.25 0.26 (L) 0.64 0.56 0.74 0.89 0.91 0.92 (M) 0.46 0.39 0.62 0.87 0.63 0.89
comparison with data in [1].
3. EXPERIMENTS AND DISCUSSION
To test the robustness of the proposed algorithm, both nongeometric and geometric processing attacks are performed for the watermarked images of Lena, Goldhill and Peppers under the same condition as [1] did. The results of experiments are tabulated in Table I for comparison. Within the table, the correlation values of watermarked Lena, Goldhill and Peppers are listed respectively for both methods. NA means not available for the quotation. The blackened boxes indicate the correlation values below the threshold ρT value of 0.23 and fail to detect the embedded watermarks.
Within Table I, the attacks are listed as following: attack(A) is JPEG compression with quality factor (QF) of 30 and attack(B) is JPEG attack with QF=25. Attack(C) is SPIHT [6] compression at bit rate 0.3 bpp.
Attack(D) is the median filter attack with mask size of 4x4 and Attack(E) is the median filter attack with mask size of 5x5. Two types of pixel shifting of 9 pixels are for attack(F) and(G). Attack(F) is a circular shift operation and attack(G) is a deletion of lines followed by duplication of the adjacent lines. Attack(H) is 4 least significant bitplanes removal from the wavelet coefficients in the transform domain. Attack(I) is 4 multiple watermarking attack. The rotation and scaling attack is for (J) of -0.75 degree and (K) of 1 degree. Attack(L) is Gaussian filtering and attack(M) is sharpening attack.
From Table I, all correlation values under the proposed approach are higher than the threshold of 0.23 but data from [1] are not all above the threshold. In summary, we can clearly see that the proposed technique has superior or comparable performance in every aspect compared with data from [1].
Fig. 2. An example of the watermarking extraction from two super trees T ′
2n-1 and T ′2n. (a) the super tree coefficients of T ′
2n-1 (b) the super tree coefficients of T ′2n (c) the modularized super tree coefficients of T ′
2n-1 (d) the modularized super tree coefficients of T ′2n (e) the quantized coefficients of T ″
2n-1 , mean = 1.52 (f) the quantized coefficients of T ″2n, mean = 0.81
1 2′n− T T ′2n ) ( 1 2 j x′n− ( ) 2 j x′n m n j x2′ ( ) m n j x2′ −1( ) mq n j x2′ ( ) mq n j x2′ −1( ) (b) (d) (e) (f) 1 2′n− T T ′2n n 2 " T ′ 1 2− ′n " T (a) (c)
4. CONCLUSION
This study has investigated the operations of the wavelet tree based quantization and proposes a constrained wavelet tree quantization algorithm for watermarking. The watermarked images by the proposed technique can resist high degree of wide range geometric and nongeometric attacks. Intensive studies and large image data set evaluations in this research have shown that the proposed technique provides superior performance to the published statistics from the non-constrained quantization based method. To conclude, the proposed algorithm effectively improves the robustness of the watermarking technique for the wavelet tree based approach.
ACKNOWLEDGMENT
This work was supported by the National Science Council in Taiwan, Republic of China, under Grant NSC93-2416-H009-009, NSC94-2416-H009-018 and NSC95-2416-H-009-027.
REFERENCES
[1] S.-H. Wang and Y.-P. Lin, “Wavelet tree quantization for copyright protection watermarking”, IEEE Trans. Image Processing, vol. 13, no. 2, pp. 154-165, Feb, 2004.
[2] I. J. Cox, J. Kilian, F. T. Leighton, and T. Shamoon, “Secure spread spectrum watermarking for multimedia,” IEEE Trans. Image Processing, vol. 6, pp. 1673-1678, Jan. 1997.
[3] B. Chen and G. Wornell, “Quantization Index Modulation: a class of provably good methods for digital watermarking and information embedding”, IEEE Trans. on Information Theory , vol. 47, pp. 1423–1443, May, 2001.
[4] M.-J. Tsai, K.-Y. Yu, and Y.-Z. Chen, “Wavelet packet and adaptive spatial transformation of watermark for digital image authentication,” in Proc. IEEE ICIP, vol. 1, 2000, pp. 450 -453.
[5] D. Kundur and D. Hatzinakos, “Digital watermarking, using multiresolution wavelet decomposition,” in Proc. IEEE ICASSP, vol. 5, 1998, pp. 2869-2972.
[6] A. Said and W. A. Pearlman, “A new, fast, and efficient image codec based on set partitioning in hierarchical trees,” IEEE Trans. Circuits Syst. Video Technol., vol. 6, pp. 243-250, June 1996.