Image Hiding Based on a Hybrid Technique of VQ Compression and Discrete Wavelet Transformation
全文
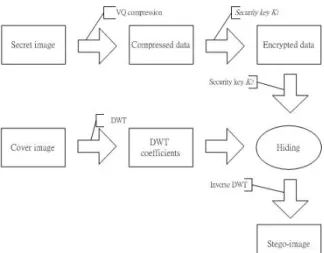
(2) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. Figure 2) of the proposed method picks up fixed images I1 , I 2 , ..., I n , which have different color distributions, to become an image pool. Before hiding the secret image, the t images I1 , I 2 , ..., I t which have similar color histograms to. codeword in the codebook. Then the mapping codewords are combined together to become the recovered image RI.. 2.2. DWT (Discrete Wavelet Transform) DWT transforms an image from spatial domain into frequency domain by a series of calculating. The simplest and most frequently used method is Haar DWT. Haar DWT has two processes: vertical process and horizontal process. Suppose I is an image with m × n pixels and I dwt is the transformed result of. the secret image will be selected from the image pool to train the codebook. Thus, the codebook trained by these t images has similar color distribution to the codebook trained by the original secret image.. I after Haar DWT. Let Ci , j be the pixel at the i-th column and j-th row of I. and Ci′, j. be the. transformed coefficient at the i-th column and j-th row of I dwt . Thus, for 1-level Haar DWT Ci′, j is defined as follows: Vertical process: Ci′, j = (C2i-1, j+C2i, j)/2,. C′n = (C2i-1, j-C2i, j)/2. (1) 2. Horizontal process: Ci′, j = (Ci, 2j-1+Ci, 2j)/2,. +i, j. C′ n = (Ci, 2j-1-Ci, 2j)/2. (2) i, + j 2. Figure 1: The flow chart of encryption process. For each process, the resulted image is divided into high and low frequency bands. The part of addition is in low frequency band, and the part of subtraction is in high frequency band. Low frequency band is denoted as L, and high frequency band is denoted as H. After 1-level DWT, image I dwt is. Before training the codebook from the selected images I1 , I 2 , ..., and I t , employ LBG algorithm to train k blocks from the blocks of the secret image (for example, k=16). The blocks of the images I 1 , I 2 , ..., I t are divided into k groups by the k blocks. divided into 4 frequency bands: LL1, HL1, LH1 and HH1. LL1 is low frequency band. HH1 is high frequency band. HL1 and LH1 are middle frequency bands between LL1 and HH1.. trained from the secret image with k-mean. Each block of the image pool calculates the Euclidean distance with the initial k blocks. Then, assign each block to the group where the Euclidean distance is minimal.. 3. The proposed method The proposed method is divided into two processes: encryption process and decryption process. The two processes are introduced in detail in the following subsections.. 3.1. Encryption process The proposed encryption process includes two procedures: gray-level secret image compression procedure and data hiding procedure. Figure 1 shows the flow chart of the proposed encryption process. 3.1.1. Secret Image Compression Procedure. The proposed method uses VQ to compress the secret image. In image hiding, if a codeword of the codebook is destroyed, all the referred blocks will be destroyed. Moreover, in order to reduce the quantity of data embedded in the cover image, the proposed method does not embed the codebook into the cover image. Therefore, the codebook training (as shown in. Figure 2: Codebook training with an image pool. Suppose that Np is the total blocks of the secret. 314.
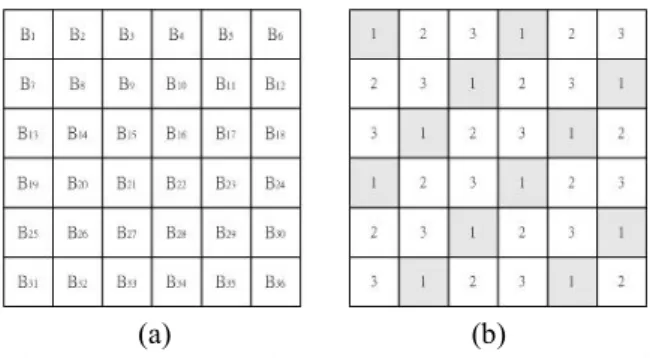
(3) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. k. image. Then N = N , where Ni is block number ∑ i p i =1. of the i-th group when the k initial blocks are trained from the secret image. Let there be Nc codewords in the codebook, where N c is predefined. For each group, there are. Ni. Np. × Nc. represented image. blocks to be trained by LBG algorithm. Then sort these image blocks from (0, 0, …, 0) to (255, 255, …, 255) by calculating minimal Euclidean distance with (0, 0, …, 0). Finally, combine all represented blocks of each group together to become a codebook.. bits into the coefficients of DWT. Figure 4 shows how the encrypted data and checking bits are embedded into the DWT coefficients. The encrypted data is embedded into the position ‘3’ of the DWT coefficient and the checking bit is embedded into the position ‘2’ of the DWT coefficient. For increasing the security of the hidden image, the robust image hiding method based on VQ also uses a security key K2 to be a seed of the pseudo random number generator. Then use K2 to decide the starting bit for the hidden indices in DWT coefficients.. 3.1.2. Data hiding processing.. For considering the security, before hiding the compressed data of the secret image, the proposed method generates a security key K1. The size of security key K1 is larger than 512 bits. K1 is used to be a seed of the pseudo random number generator to generate a binary string S. Then use XOR (exclusive OR) operation on S and each index in the compressed data to generate the encrypted data. Then, the encrypted data can be hided into the cover image. In order to enhance the robustness, this paper divides the blocks of the secret image into three levels (as shown in Figure 3). The blocks marked by 1 are the most important. The blocks marked by 2 or 3 are minor. When the secret image is hidden, the indices of the 1-marked image blocks should be hidden in the area where the data are not easy to be broken. The indices of the 2-marked or the 3-marked image blocks can be hidden in the place where the data are easier to be broken. Thus, when the indices of the 2-marked or the 3-marked image blocks are broken, they can be predicted by the 1-marked image blocks.. Figure 4: Embedding encrypted data checking bits into DWT coefficients. and. Since each pixel is similar to its neighbors in an image, when the checking bits are used to check the embedded indices and some errors are found, the proposed method can predict the error blocks by using other correct blocks around each error one. The DWT coefficients of LL1 sub-band are usually not easy to be broken by some common used image processing. But the coefficients of HL1, LH1 and HH1 sub-bands do. Thus, when even parity checking bits find some errors of the indices, each mapped error block can be predicted by using the 1-marked blocks around it.. 3.2. Decryption process In the decryption process (as shown in Figure 5), the proposed method uses the same image pool as encryption process to train the codebook. The authorized participants use the keys K1, K2 and k initial codewords of the secret image to training the codebook. Thus, the codewords of each group are the same as the codewords in the encryption process.. (a) (b) Figure 3: (a) Secret image and (b) three levels of image blocks of the secret image In the proposed method, the cover image I c is transformed by 1-level DWT. Thus, the transformed I c is divided into 4 frequency bands: LL1, HL1, LH1 and HH1. The indices of the 1-marked image blocks of the secret image are hidden in the LL1 and the indices of the image blocks belonged to be 2-marked and the 3-marked, respectively, are hidden in the HL1 and LH1. The proposed method also checks even parity for each hidden index and hides the checking. Figure 5: The flowchart of decryption process In next step, transfer the stego-image I s with 1-level DWT and decrypt the indices of the secret image from the coefficients of 1-level DWT stego-image I s with security key K2. Thus, the. 315.
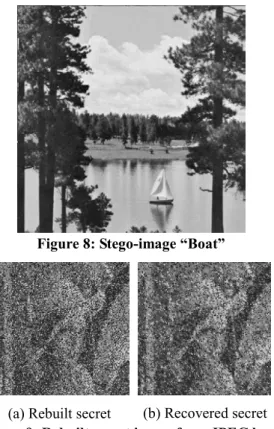
(4) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. modified. The PSNR of the secret images before and after modified are listed in Table 3. Figure 9 shows the secret images which is directly rebuilt from stego-images and the recovered secret images after being repaired by referring to the surrounding 1-marked blocks when the stego-images is compressed by JPEG lossy compression with compression rate 41.8%, respectively.. encrypted data of the secret image are decrypted from the stego-image. For each encrypted data, use security key K1 to decrypt it. Thus, the index data is decrypted. For each index, calculate the even parity check-bits to verify if the index is correct. For the correct indices, use mapped codewords to rebuild the secret image. For the error indices, predict them by the average of the 1-level image blocks around each of the error blocks. Thus, the decryption processing is done.. 4. Experimental results Table 3: The PSNR of the secret image when stego-images are compressed after JEPG lossy compression (unit: dB). (a) Original image “Boat”. Compression rate∗ 1.30 1.53 1.91 2.37 2.88 Secret image 19.65 17.52 15.71 14.06 12.94 (recovered) Secret image 20.45 18.51 16.76 15.01 13.76 (modified). (b) Rebuilt “Boat” after VQ compression with PSNR 33.73dB. Table 1: The PSNR of the secret images after VQ compression (size: 256× 256 pixels) Images Boat Lena Gold Peppers Tiffany. PSNR 33.73 dB 34.49 dB 35.60 dB 34.08 dB 35.89 dB. (c) Original image (d) Rebuilt “Gold” after VQ compression with “Gold” PSNR 35.60 dB Figure 6: VQ compression results. Table 2: The PSNR of stego-images in the experiment (unit: dB) Stego-image Secret image. Boat F16 Splash Baboon. Boat Lena Gold Peppers Tiffany. 34.11 33.99 36.17 33.97 33.89 34.16 33.52 33.64 33.87 34.49 34.40 34.57. 33.90 34.11 33.82 34.38. 33.90 33.55 32.97 34.33. (a). In the experiment, the size of the cover image and the secret image are 512 × 512 and 256 × 256 , respectively. The codebook size is 512. There are several images in the image pool, such as Baboon, Peppers, Tiffany, Boat, F16 and Splash, etc. For each secret image, there are 4 images picked from the image pool which color histograms are similar to the secret image and used to train the codebook. Table 1 shows the PSNR of the reconstructed secret images after VQ compression. When the stego-image is not destroyed, the PSNR of the decrypted secret images are equal to Table 1. The secret images before and after VQ compression with the proposed method are shown in Figure 6. The test images used in this paper are shown in Figure 7. The stego-image is shown in Figure 8. The PSNR of the cover image and the stego-image for hiding different secret images in are listed in Table 2. The secret image recovered from the stego-image after JEPG lossy compression can be. (b). (c). Figure 7: (a) Original secret image “Lena,” (b) rebuilt secret image after VQ compression (PSNR=34.49 dB), and (c) cover image “Boat”. 316.
(5) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. compressed stego-image. The recovered secret image is easier to be recognized than the directly rebuilt secret image. Finally, the proposed method also proposes a new method to train codebook without the original image. Only a few information of the original image is given, then the codebook can be trained with an image pool. Thus, this can be used in many applications based on VQ.. References [1]. C. C. Chang, D. C. Lin, and T. S. Chen, “An Improved VQ Codebook Search Algorithm Using Principal Component Analysis,” Journal of Visual Communication and Image Representation, Vol. 8, No. 1, 1997, pp. 27-37.. [2]. T. S. Chen, C. C. Chang, and M. S. Hwang, “A Virtual Image Cryptosystem Based upon Vector Quantization,” IEEE Transactions on Image Processing, Vol. 7, No. 10, October 1998, pp. 905-910.. [3]. K. L. Chung, C. H. Shen, and L. C. Chang., “A Novel SVD and VQ Based Image Hiding Scheme,” Pattern Recognition Letters, Vol. 22, 2001, pp. 1051-1058.W. C. Du, and W. J. Hsu, “Adaptive Data Hiding Based on VQ Compressed Images,” IEE Proceedings-Vision, Image and Signal Processing, Vol. 150, No. 4, 2003, pp. 233-238.. [4]. Y. C. Hu, and C. C. Chang, “A Progressive Codebook Training Algorithm for Image Vector Quantization,” The Fifth Asia-Pacific Conference on Communications (APCC '99), Vol. 2, pp. 936-939, 1999.. [5]. H. Jiwu, and Y. Q. Shi, “Embedding Gray Level Images,” The 2001 IEEE International Symposium on Circuits and Systems (ISCAS 2001), Vol. 5, 2001, pp. 239-242.. [6]. R. Y. Li, J. Kim, and N. Al-Shamakhi, “Image Compression Using Transformed Vector Quantization,” Image and Vision Computing, Vol. 20, No. 1, January 2002, pp. 37-45.. [7]. Y. Linde, A. Buzo and R. M. Gray, “An Algorithm for Vector Quantization,” IEEE Transactions on Communications, Vol. 28, Jan. 1980, pp. 84-95.. [8]. J. S. Pan, F. H. Wang, L. Jain, and I. Nikhil, “A Multistage VQ Based Watermarking Technique with Fake Watermarks,” Lecture Notes in Computer Science, Vol. 2613, January 2003, pp. 81-90.. Figure 8: Stego-image “Boat”. (b) Recovered secret (a) Rebuilt secret Figure 9: Rebuilt secret image from JPEG lossy compressed stego-image (compression rate of the stego-image is 107 × 100% ≈ 41.80% ) 256 In the experimental result, the quality of the recovered secret image is more than 33.7(as shown in Figure 11) if the stego-image is not destroyed. If the stego-image is destroyed by JEPG lossy compression, the PSNR of the modified secret images are higher than the recovered secret images. If the compression rate is below 34.50%, the secret image is hard to recovery from the stego-image. It is because the LL band of DWT coefficients is broken when the stego-image is compressed. Thus, the proposed method can improve the quality of the secret image which the stego-image is destroyed.. 5. Conclusions This paper proposes an image hiding method based on VQ compression and DWT. The proposed method improves the enshrouding, security and robustness of image hiding. For the enshrouding, the PSNR of the stego-images are higher than 33dB. For the security, the proposed method needs some information to recover the secret image. The information is transferred to the authorized participants with secure encryption methods, such as DES, in transmission. For the robustness, the secret image can be rebuilt from the JPEG lossy. 317.
(6)
數據
相關文件
We proposed a deep learning model which achieves state-of-the-art performance on the cyclone rapid intensification task relying solely on satellite images, which to the best of
Creating New Images From the Outline
In this research, we use conventional RGB (Red, Green, Blue) images as input data. The conventional RGB image is demosaiced from raw image by using the color interpolation
T transforms S into a region R in the xy-plane called the image of S, consisting of the images of all points in S.... So we begin by finding the images of the sides
• Zero-knowledge proofs yield no knowledge in the sense that they can be constructed by the verifier who believes the statement, and yet these proofs do convince him..!.
– Change Window Type to Video Scene Editor – Select Add → Images and select all images – Drag the strip to the “1st Frame” in Layer
Chou, “The Application on Investigation of Rice Field Using the High Frequency and High Resolution Satellite Images (1/3)”, Agriculture and Food Agency, 2005. Lei, “The Application
Barrett, “On the Road to China: The Continental Relocation of Sacred Space and its Consequences,” in Images, Relics and Legends: Essays in Honor of Professor Koichi Shinohara,