Classification-based Image Watermarking Using Rank Order in the Wavelet Domain
全文
(2) been considered significantly. Consequently, the method of Barni cannot perform well robust capability. In [8], the algorithm of Wang was proposed to achieve both perceptual invisibility and robustness. The algorithm of Wang inserted watermarks into the middle-frequency range to reach both imperceptibility and robustness. Paqueta et. proposed a quantization-based method in the wavelet domain for image authentication [1]. The method of Paqueta also considered the characteristics of HVS while embedding watermarks. The method of Paqueta embedded watermarks by modifying 64 coefficients in separate subbands. Previous methods have failed in finding robust features in individual subbands at the same level, without considering the relationships among subbands at the same level. Hence it inspired us to propose the CIWROW technique, which looks for the features among details subbands at the same level. The CIWROW technique also uses a nonlinear transformation (median operator) to get the feature of each detail subband. The distances between these features are then employed to classify the wavelet blocks into three categories. The distinct watermark-embedding algorithm is designed for each category. Observing the experimental results, the CIWROW technique achieves both perceptual invisibility and robustness. The rest of this paper is organized as follows. Section 2 presents the CIWROW technique. First, Section 2 introduces the representation of a gray-level image and watermarks, and then reviews the wavelet decomposition. Next, watermark embedding and watermark extraction are presented in Section 2. Subsequently, Section 3 shows experimental results. Finally, Section 4 gives discussions and conclusions.. 2. The CIWROW Technique 2.1 Image Denotation A gray-level image, X, with size L × K can be defined by X = [xρ]L×K, where xρ ∈{0, 1, …, 255}. That is, xρ represents the pixel value located at position ρ = (i, j) over X, where i ∈{0, 1, …, L-1} and j ∈{0, 1, …, K-1}. Fig. 1 shows that is segmented into ⎢ L ⎥ ⎢ K ⎥ nonoverlapped blocks with ⎢8⎥ × ⎢ 8 ⎥ ⎣ ⎦ ⎣ ⎦. size 8 × 8. For example, b21 stands for a block that the center pixel in the block is located at position (2, 1) on X. Let b21(r, c) denote the gray level of a pixel at the position (r, c) in the block b21. As a result, these nonoverlapped blocks in X can be denoted by. {. ⎣⎦. ⎣ ⎦ },. Φ = bij i =1,L, L , j =1,L, K 8 8. (1). where each bij is of size 8 × 8. Let a 2D binary image represent a watermark, W, in the experiment of the paper. The image can be represented by a binary sequence in a row-major fashion. The watermark is denoted by W = (w1 , w2 , L , wk , L , wm ) ,. where m represents the size of W and wk ∈ {-1, 1}. original image X in spatial domain b21 (1,1). b21 (1,8). b11. b12. …. b. b21. b22. …. b. M b⎢ L ⎥. ⎢ 8 ⎥ ,1 ⎣ ⎦. b21 (r, c). b21 (8,8). M. b⎢ L ⎥. ⎢ 8 ⎥ ,2 ⎣ ⎦. ⎢K ⎥ 1, ⎢ ⎥ ⎣8⎦. ⎢K ⎥ 2,⎢ ⎥ ⎣8⎦. M …. b⎢ L ⎥ ⎢ K ⎥ ⎢ ⎥, ⎢ ⎥ ⎣8⎦ ⎣ 8 ⎦. bσ k =(ik , jk ). Fig.1 The segmented image in spatial domain.. 2.2 Wavelet Transformation Fig. 2 illustrates that each nonoverlapped block bij in Φ for an image X is decomposed through Discrete Wavelet Transform (DWT). Let Bij represent the corresponding wavelet block consisting of eight coefficients. Moreover, Bij(r, c) stands for the coefficient at the position (r, c) on the block Bij. Fig. 3(a) shows bij is transformed through DWT in two levels. Each wavelet block Bij at each level consists of four bands (components): low-low band (LL1), low-high band (LH1), high-low band (HL1), and high-high band (HH1). LL1 band can be further divided into four subbands: low-low subband (LL2), low-high subband (LH2), high-low subband (HL2), and high-high subband (HH2). Generally, HL2, LH2, HH2, HL1 and LH1 are called middle-frequency components (subbands). For convenience to describe the computations to wavelet blocks, let bρ k be transformed by DWT to obtain the corresponding wavelet block B ρ k . Further let B ρl ,kθ be a subband at resolution level l = 1, 2 and with orientation θ ∈ {1, 2, 3, 4} = {LL, HL, LH, HH}. The coefficient B ρl ,kθ (r, c) is at position (r, c) in the subband B ρl ,kθ . In this paper, features are obtained by calculating the wavelet coefficients belonging to the three detail bands at level 2. When the block B ρ k is selected to be embedded, the CIWROW technique modifies the wavelet coefficients being in the three detail bands B ρ2,kθ for θ = 2, 3, and 4. Fig. 3(b) exhibits an example for the three detail bands.. 2.3 Watermark Embedding -2-. (2).
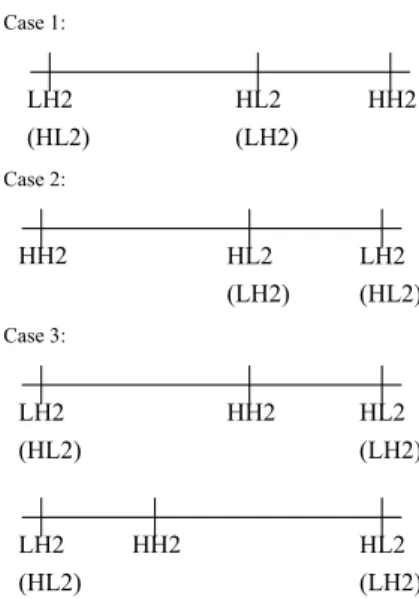
(3) watermark. Fig. 4 illustrates the structure of watermark-embedding algorithm in the CIWROW technique. First, two seeds s1 and s2 are given and then presented in the pseudo-random number generator (PRNG) component for generating a sequence of random positions, (3). where ρk = (ik, jk). In the CIWROW technique, a set, Ψ, comprises m blocks which are randomly selected from Φ by using the PRNG scheme [6]. The set Ψ can be defined by. {b ρ k = (i k , j k ) ρ k ∈ Γ} ,. (4). where k = 1, 2, …, m. That is, |Ψ| = m. Note that each bρ k is of size 8 × 8. In the block diagram, Bσ′ k denotes a wavelet block corresponding to the. spatial block bρ k . blocks in original image X are decomposed by wavelet transform B21 (1,1). B21 (1,8). B11. B12. …. B. B21. B22. …. B. M. M. B⎢ L ⎥. B⎢ L ⎥. ⎢ 8 ⎥ ,1 ⎣ ⎦. B21 (r, c). ⎢ 8 ⎥, 2 ⎣ ⎦. ⎢K ⎥ 1, ⎢ ⎥ ⎣8⎦. HL2. LH2. HH2. …. B⎢ L ⎥ ⎢ K ⎥. X′ BW C. original image. TD. Class 1 Class 2 Class 3. watermarked Image. Fig. 4 The structure of watermark-embedding algorithm in the CIWROW technique. Next, a classification algorithm is designated to determine the ranges of strengths for a modification to a target block to be embedded. In the CIWROW technique, a nonlinear transformation called the median operator is applied to the three detail subbands at level 2 while computing the features for these three subbands. Specifically, the feature for each subband is the median value among the coefficients in the subband. The relationships for the distances between these three features can be divided into three cases as shown in Fig. 5. Here the three symbols LH2, HL2, and HH2 in Fig. 5 represent three medians of coefficients in LH2, HL2, and HH2, respectively.. HL2 (LH2). HH2. Case 2:. HH2. HL2 (LH2). LH2 (HL2). HH2. HL2 (LH2). Case 3:. LH2 (HL2). (a). 2, 2. Bρ k. Bρ k. b ρ′ k. T 1 ,T 2 , T 3 ,T 4. LH2 (HL2). ⎢ 8 ⎥,⎢ 8 ⎥ ⎣ ⎦⎣ ⎦. HH1. 2,3. IDW T. B ρ' k. B ρk. Case 1:. HL1. LH1. Watermark Embedding. DW T. bρk. M. Fig. 2 The segmented image in wavelet domain. LL2. PRNG. ⎢K ⎥ 2, ⎢ ⎥ ⎣8⎦. Bρk =(ik , jk ). B21 (8,8). wk. Seeds: s = ( s1 , s 2 ). X. Γ = {ρ1, ρ2, …, ρk …, ρm},. W. LH2 (HL2). 2, 4. Bρ k. HH2. HL2 (LH2). Fig. 5 The relationships for the distances between these three features can be classified into three cases.. (b). Fig. 3 Components are constituted of a 8 x 8 wavelet image block with level 2.. The classification algorithm, which is named the BWC algorithm, is devised to classify a wavelet block belonging to which class according to the distances between the features of blocks in wavelet domain. The BWC algorithm is described as follows. Step 1. Input an image X. Step 2. Set Classc = φ, for c = 1, 2, 3. Step 3. For each bρ k where ρk = (ik, jk) ∈ {4,. -3-.
(4) 5, …, L-4} × {4, 5, …, K-4}. Step 4. Compute B ρ2,θ = DWT( bρ k ) where θ. c. dLmin. k. c. dLmax. Step 5.. > max{ med. k. 2, 2. , med. ρk. 2,3. ρk. < min{. 2, 2. 2,3. k. k. med ρ , med ρ } ) k. else Class3 = Class3 ∪ { B ρ2,θ }. k. Step 7. Output three classes, Classc for c = 1, 2, and 3. Here the paper proposes an algorithm called the TD algorithm which determines four thresholds, T1, T2, T3, and T4, before watermark embedding and extraction. Specifically, these four thresholds are used in the CIWROW technique while altering a target block for embedding a watermark bit. Note that these four thresholds should be secured against pirates for protecting image copyrights. In addition, these four thresholds are also provided during watermark extraction. Consequently, the CIWROW technique extracts watermarks without original images. The TD algorithm is presented in the following. Step 1. Input Classc for c = 1, 2, 3. Step 2. For c = 1 to 3. Step 3. For each block B 2,cθ ∈ Classc.. d2 d3. Step 3.2.. abs ( med. = ρ kc. ρ kc. dL. − med. min{d 2. =. max{d 2. ρ kc. , d3. ρ kc. where. ρ kc. − med. and dL. ρ kc. = ρ kc. ρ kc. 2, 2 ρ kc. 2,3 = abs ( med c ρk. Calculate dS dS. and d 3. ρ kc. 2, 4. ρ kc. c. =. ∀B. min 2,θ. ρ kc. c dS max =. ∈ Classc. ).. max. ρk. where. k. Γ. Step 4.2. Calculate B ρ2,θ for θ = {2, 3, 4} = {HL, k. LH, HH}. Step 4.3. If ( B ρ ∈ Class1 ) k. If (wk = 1 and ( dS. ρ 1k. < T1 or dLρ1 < T1 ) ) k. then ( modify the coefficients in 2,4 Bρ until dS 1 , dL 1 > T1 ); Goto Step ρk. ρk. 4.6. else if (wk and ( dS 1 > T1 or dL 1 > T1 ) ) ρ ρ k. =. -1. k. k. k. If (wk = 1 and ( dS. ρ k2. < T2 or dLρ 2 < T2 ) ) k. then ( modify the coefficients in 2,4 Bρ until dS 2 , dL 2 > T2 ); Goto Step σk. k. σk. 4.6. elseif(wk = -1 and (dS. ρ k2. > T2 or dLρ 2 > T2 ) ) k. then ( modify the coefficients in B ρ2,4 k. until dS 2 , dL 2 < T2 ); Goto Step 4.6. ρ ρ. c}. ρk. ρ kc. Step 1. Input an image X and a watermark W. Step 2. Given two seeds (s1, s2) to generate Γ. Step 3. According to Γ, to find Ψ which includes the target blocks to be embedded. Step 4. For k = 1 to m Step 4.1. Compute B ρ = DWT( bρ k ) where ρk ∈. k. } ρ kc. {dS. Subsequently, the watermark embedding algorithm used in the CIWROW technique is described as follows. Note that IDWT denotes the inverse of DWT.. Step 4.4. If ( B ρ ∈ Class2). ρk. ∀B 2,cθ ∈ Classc. Step 6. Output T1, T2, T3, and T4.. k. , d3 c }.. {dS. .. until dS 1 , dL 1 < T1 ); Goto Step 4.6. ρ ρ. Step 3.3. End For-loop. Step 2.1. End For-loop. c c Step 4. Compute dS min , dS max , dLcmin , dLcmax using dS min. ⎫ ⎫⎪ ∀B 2,1θ ∈ Class1 ⎬ ⎬ ρk ⎭ ⎪⎭. then ( modify the coefficients in B ρ2,4. 2, 4 ) ρ kc. ρ kc. ⎫ ⎧ ∀B 2,1θ ∈ Classc ⎬∪⎨ dL 1 ρk ⎭ ⎩ ρk. ⎧⎪ ⎧ ⎫ ⎫⎪ T3 = median ⎨ ⎨ dS 3 ∀B 2,3θ ∈ Class3 ⎬ ⎬ ρk ⎪⎩ ⎩ ρ k ⎭ ⎪⎭. k. ρk. Compute d 2. ρk. ⎧⎪ ⎧ ⎫ ⎫⎪ T4 = median ⎨ ⎨ dL 3 ∀B 2,3θ ∈ Class3 ⎬ ⎬ ρk ⎪⎩ ⎩ ρ k ⎭ ⎪⎭. then Class2 = Class2 ∪ { B ρ2,θ }.. Step 3.1.. {dL c }. ⎧⎪ ⎧ ⎫ ⎫⎪ ⎫ ⎧ T2 = median ⎨ ⎨ dS 2 ∀B 2,2θ ∈ Class2 ⎬∪⎨ dL 2 ∀B 2,2θ ∈ Class2 ⎬ ⎬ ρk ρk ⎪⎩ ⎩ ρ k ⎭ ⎪⎭ ⎭ ⎩ ρk. }). else 2 ,4. max. ∀B 2,cθ ∈ Classc. ⎧⎪ ⎧ T1 = median ⎨ ⎨ dS 1 ⎪⎩ ⎩ ρ k. then Class1 = Class1 ∪ { B ρ2,kθ }. If ( med ρ k. =. ρk. Calculate T1, T2, T3, and T4 by using. k. 2 ,4. {dL c }. ρk. θ = 2, 3, 4. Step 6. If ( med ρ. max. ∀B 2,cθ ∈ Classc ρk. k. = {1, 2, 3, 4} = {LL, HL, LH, HH}. Step 5. Calculate three medians among HL2, LH2, and HH2, respectively, by using 2 ,θ 2,θ med ρ = median{ B ρ ( r , c ) | 1 ≤ r , c ≤ 2} ,. =. k. k. Step 4.5. If ( B ρ ∈ Class3). }. k. If (wk = 1 and ( dS. -4-. ρ k3. < T3 or dLρ 4 < T4 ) ) k.
(5) then ( modify the coefficients in B ρ2,2 or k. 2,3 Bρ k until dS 3 < T3 and dL 3 < T4 ). ρ ρ k. PRNG. k. elseif (wk = -1 and (dS. ρ k3. > T3 or dLρ 4 > T4 ) ) k. then ( modify the coefficients in B ρ2,2 or k. 2,3 Bρ k. Step 4.6.. until dS 3 > T3 and dL 3 > T4 ). ρ ρ k. k. bρ′ k. Compute. =. Seeds: s = ( s1 , s 2 ). IDWT( B ρ′ k. ). where B ρ′ k represents the watermarked block in the wavelet domain. Step 4.7. End for-loop ′ Step 5. Output the watermarked image X .. 2.4 Watermark Extraction Fig. 6 displays the block diagram of watermark extraction utilized in the CIWROW technique. The watermark extraction algorithm estimates the watermark without original images, and is described as follows. ′. Step 1. Input a watermarked image X , two seeds (s1, s2), and four thresholds T1, T2, T3, and T4. Step 2. Use two seeds (s1, s2) to generate the set Γ. Step 3. Find the watermarked blocks bρ′ k according to Γ. Step 4. For k = 1 to m Step 4.1. Compute B ρ′ = DWT( bρ′ k ) where ρk ∈. b ρ' k. T 1 , T 2 , T 3, T 4. DW T. B ρ' k Watermark. X′. k. LH, HH}. Step 4.3. If ( B ρ′ ∈ Class1 ) k. If ( dS. ρ 1k. < T1 and dLρ1 < T1 ) k. then wˆ k = - 1 else wˆ k = 1 . Step 4.4. If ( B ρ′ ∈ Class2 ) k. If ( dS. ρ k2. < T2 and dLρ 2 < T2 ) k. then wˆ k = - 1 else wˆ k = 1 . Step 4.5. If ( B ρ′ ∈ Class3 ) k. If ( dS. ρ k3. < T3 and dLρ 4 < T4 ) k. then wˆ k = - 1 else wˆ k = 1 . Step 4.6. End for-loop. Step 5. Output the estimated watermark Wˆ . Similarly, the estimated watermark can be denoted by Wˆ = ( wˆ 1 , wˆ 2 ,L , wˆ k ,L , wˆ m ) where wˆ k ∈ {-1, 1} .. -5-. Wˆ. Extraction. watermarked image or manipulated watermarked image. Fig. 6 The block diagram of watermark extraction algorithm in the CIWROW technique.. 3. Experimental Results In this experiment, a 64 × 64 binary image shown in Fig. 7(a) is adopted to be the signature of copyright owner.The length of a watermark is 64 × 64, i.e., m = 64 × 64 The index PSNR (Peak Signal to Noise Ratio) is employed to measure the imperceptible quality of watermarked images, and is defined by 2. PSNR = 10 log( 255 ) , MSE. (5). where MSE =. 1 L×K. L K. (. ∑ ∑ xij − xij′. i =1 j =1. ). 2. .. (6). Furthermore, BCR (Bit Correction Rate) is an index for evaluating the quality of estimated watermarks, and is specified by. k. Γ. Step 4.2. Calculate B ρ′ 2,θ for θ = {2, 3, 4} = {HL,. estimated watermark. wˆ k. m. BCR (W , Wˆ ) = 1 -. ∑w k =1. k. - wˆ k. 2m. .. (7). Note the BCR (W , Wˆ ) ∈ [0, 1] and the BCR value indicates the similarity between W and Wˆ . Fig. 7(b) and (c) show the original Lena image with size 512 × 512 and its watermarked version, respectively. The PSNR and BCR for the attack-free case are 41.25 and 1.0, respectively. Meanwhile, Fig. 7(b) is very similar to (c) by visual perception. Therefore, imperceptible capability of the CIWROW technique is acceptable. After presenting the original Lena image to the TD algorithm, these four thresholds are T1 = 1, T2 = 1.0625, T3 = 0.375, and T4 = 1.4375. Besides the examination to the attack-free case, the robustness of the CIWROW technique is also assessed by common image-processing operations including brighten, cropping, painting, noising, histogram equalization, and JPEG2000 compression. Fig. 8 exhibits the results of a robustness examination for the CIWROW technique while using Lena image. Here these four thresholds are the same as those used in the attack-free case. Observing the results, we.
(6) claim that the CIWROW technique possesses effective robustness to be immune against image-processing attacks under consideration.. [7]. 4. Conclusions This paper has proposed a novel watermarking technique, which is called the CIWROW technique, mainly based on the wavelet transform and a classification approach. Here we have successfully integrated wavelets theory and classification strategy to develop the CIWROW technique. Moreover, the features of classes are analyzed according to the relationships between the three detail bands at level 2 for all wavelet blocks. Experimental results are included in this paper to illustrate that the CIWROW technique is imperceptible and also robust to be immune against common image-processing attacks. Consequently, the CIWROW technique can be applied to the Digital Right Management (DRM) systems for the copyright protection of gray-level images.. Acknowledgements. [8]. 1984. R. L. Rivest, A. Shamir, and L. Adleman, "A method for obtaining digital signatures and public-key cryptosystems," Communications of the Association for Computing Machinery, vol. 21, no. 2, pp. 120-126, February 1978. Y. Wang, J. F. Doherty, and R. E. V. Dyck, "A wavelet-based watermarking algorithm for ownership verification of digital images," IEEE Trans. on Image Processing, vol. 11, no. 2, pp. 77-88, Feb. 2002.. (a). (b). The authors would like to thank the National Science Council of the Republic of China, Taiwan for financially supporting this research under Contract No. NSC 93-2213-E-150-009.. References [1]. [2]. [3]. [4]. [5]. [6]. A. H. Paqueta, R. K. Wardb, and I. Pitas, "Wavelet packets-based digital watermarking for image verification and authentication," Signal Processing, vol. 83, pp. 2117–2132, 2003. H.-H. Tsai and J.-S. Cheng, "Adaptive signal-dependent audio watermarking based on human auditory system and neural networks," Applied Intelligence, vol. 23, no. 3, 2005. J. Grollmann and A. L. Seiman, "Complexity measure for public-key cryptosystems," SIAM Journal on Computing, vol. 17, no. 2, pp. 309-335, April 1988. L. Xie and G. R. Arce, "A class of authentication digital watermarks for secure multimedia communication," IEEE Trans. on Image Processing, vol. 10, no. 11, pp. 1754-1764, Nov. 2001. M. Barni, F. Bartolini, and A. Piva, "Improved wavelet-based watermarking through pixel-wise masking," IEEE Trans. on Image processing, vol. 10, no. 5, pp. 783-791, May 2001. M. Blum and S. Micali, "How to generate cryptographically strong sequences of pseudo-random bits," SIAM Journal of Computing, vol. 13, no. 4, pp. 850-864, Nov. -6-. BCR 1.0 (c). (d). Fig. 7 (a) A stamp binary image. (b) The Original Lena image. (c) The estimated watermark is extracted from (d). (d) Watermarked Lena image is obtained by hiding (a) into (b)..
(7) (a). brighten. (e) painting. (i) histogram equalization. BCR. BCR. 0.9672. 0.8486. (b). (c) cropping. (d). BCR. BCR. 0.9390. 0.7160. (f). (g) noising with 5% impulse. (h). BCR. BCR. 0.8862. 0.9607. (j). (k) JPEG2000 with bitrate 5. (l). Fig. 8 The results of a robustness examination for the CIWROW technique using Lena image. Six common image-processing manipulations are simulated for the robustness examination.. -7-.
(8)
數據


相關文件
In this paper, we build a new class of neural networks based on the smoothing method for NCP introduced by Haddou and Maheux [18] using some family F of smoothing functions.
Using a one-factor higher-order item response theory (HO-IRT) model formulation, it is pos- ited that an examinee’s performance in each domain is accounted for by a
Abstract In this paper, we consider the smoothing Newton method for solving a type of absolute value equations associated with second order cone (SOCAVE for short), which.. 1
We propose a primal-dual continuation approach for the capacitated multi- facility Weber problem (CMFWP) based on its nonlinear second-order cone program (SOCP) reformulation.. The
In this paper we establish, by using the obtained second-order calculations and the recent results of [23], complete characterizations of full and tilt stability for locally
In this paper we establish, by using the obtained second-order calculations and the recent results of [25], complete characterizations of full and tilt stability for locally
Optim. Humes, The symmetric eigenvalue complementarity problem, Math. Rohn, An algorithm for solving the absolute value equation, Eletron. Seeger and Torki, On eigenvalues induced by
Abstract In this paper, we study the parabolic second-order directional derivative in the Hadamard sense of a vector-valued function associated with circular cone.. The