Routing Path Selection Algorithm Based On Price Mechanism In Ad-Hoc Network
全文
(2) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. distribution and power consumption. To combine with price mechanism, we make the source node pay virtual currency when it transmits data packets and occupies resources of other nodes. Each mobile device gets benefits from relaying data packets for other nodes. Therefore, each mobile device is willing to forward data packets for other nodes. In the following sections, we present functions to transform resources into virtual currency. Different resource has different transformation function.. power, and computer efficiency in each node are limited. Hence, nodes should not waste their resources. These nodes don’t have the responsibility to relay data packets for others. Therefore, how to make other nodes willing to relay the packets becomes an important issue.. 1.2. Price mechanism Since to make the nodes willing to relay the packets is important in mobile ad hoc network, a price mechanism is proposed [3] by Buttyan et al. The price mechanism uses virtual currency. The function of price mechanism is that some node must pay virtual currency to intermediate nodes for relaying data packets. Nodes who help to relay data packets will receive virtual currency. In other words, if nodes don’t relay data packets, they can’t get any virtual currency. Then, these nodes have no virtual currency to send their data packets. Therefore, the price mechanism can make mobile devices help each other. On the contrary, mobile device won’t help others will be isolated. In mobile ad hoc network, price mechanism can be used in different domains. Qiu et al. proposed [2] an algorithm based on price mechanism to optimal bandwidth allocation. This algorithm can make nodes set their prices dynamically and maximize the benefits of nodes relaying data packets for others. However, the way of transforming resources into virtual currency was not mentioned. Maximizing the benefits for intermediate nodes will increase the cost paid by the source node. Hence, we propose a new algorithm considering both routing path selection algorithm and price mechanism. To take more factors into account for selecting a route with price mechanism needs further studied. Our algorithm also proposes the functions to transform resources into virtual currency. By using price mechanism, nodes are willing to relay data packets for other nodes. Therefore, routing path selection algorithm with price mechanism can be more reasonable. The remainder of this paper is organized as follows. Section 2 describes the proposed algorithm about routing path selecting and price mechanism (RSPM). Section 3 presents simulation results. Finally, the conclusions are drawn in Section 4.. 2.1. Evaluation function Each routing path is composed of intermediate nodes. We count intermediate nodes’ payment before counting the total payment of a routing path. In an intermediate node, there are three resources to be considered. In the following, we introduce how to transform these resources of an intermediate node into virtual currency. 2.1.1. Bandwidth support. Bandwidth support is the free bandwidth of a node. The total bandwidth of different mobile devices is different. In our mechanism, we prefer to choose the intermediate node with larger free bandwidth. If we choose an intermediate node with small free bandwidth, its bandwidth may be all occupied soon. Hence, the intermediate node cannot send or relay packets. Therefore, we have to choose intermediate nodes with less bandwidth occupation. The function defined as follows is used in the proposed algorithm for transforming bandwidth resources into virtual currency. Re quest_Bandwidths F1 ( j ) = , j ∈ γ s_k , Free_Bandwidth j. Re quest_Bandwidths ≤ Free_Bandwidth j , Free_Bandwidth j = Total_Band width j − Used_Bandwidth j. where F1 is the ratio which is used to convert bandwidth resource into virtual currency. γs_k is the set of intermediate nodes which help to rely data packets from source node s to destination node in the k-th re-established routing path between the source node and the destination node. Request_Bandwidths is the bandwidth which source node s requests. Total_Bandwidthj is the bandwidt.h which intermediate node j owns. Used_Bandwidthj is the bandwidth which intermediate node j has been used. There are some features in the function F1. A node with small free bandwidth that satisfies the route request still can be selected as intermediate node of routing path, but the charge of this node increases, due to limited resource. Hence, the higher free bandwidth is, the smaller the value of F1 is. It means that the cost of F1 depends on the amount of free bandwidth. So this function encourages the source node to select the nodes with more free. 2. The proposed algorithm In MANETs, a source node needs to send data packets to the destination node which is out of the transmission range. Due to each mobile device has limited and different resources, mobile device should not waste their resources to relay data packets for other mobile devices without getting any benefit. Therefore, a price mechanism is used to attract other mobile devices to relay data packets for others. In the proposed algorithm, it considers three resources: bandwidth support, traffic load. 810.
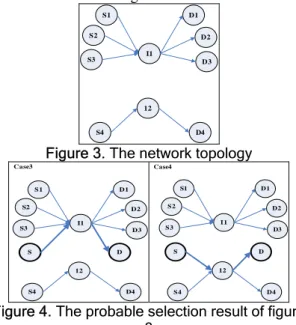
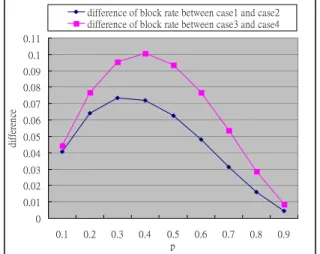
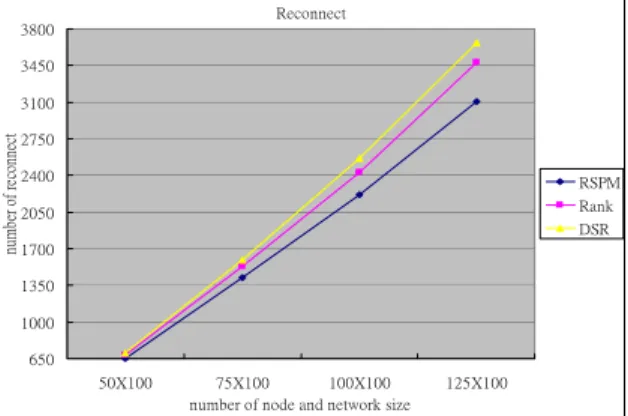
(3) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. contrast, this route request selects I2 to be the intermediate node.. bandwidth to be intermediate nodes. 2.1.2. Traffic load distribution. The traffic load distribution of node j means the total number of routing paths through the node j. If an intermediate node supports more than one routing path, its traffic load distribution becomes higher and the resource occupation of this node is heavy. If this intermediate node moves out of communication range, the routing paths through this intermediate node need to be rebuilt. Hence, the load of network increases. Therefore, we propose a function to distribute routing paths and reduce the traffic load distribution of each node. The following function is used to transform traffic load distribution into virtual currency and is defined as: F2 ( j ) =. (. exp Traffic_Lo ad_Distrib ution j. Case1. S1. S2. I1. S. D2. S2. D. S. where F2 is the ratio of traffic load distribution of intermediate node j. Normalization_Constant is set to exp(Max_Traffic_Load_Distribution). Max_Traffic_Load_Distribution is the upper bound of the each intermediate node’s traffic load distribution. Traffic_Load_Distributionj is the total number of routing paths through intermediate node j. The function F2 also has some features. When a new routing path selects the intermediate node that many routing paths have gone through, it needs to pay higher virtual currency. Oppositely, it can select the intermediate node which a few routing paths through it. Using function F2, the intermediate node with few routing path through will be selected. Hence, the load of network will be more balance. An example is used to explain the purpose of the function F2. S and D present the source node and the destination node, respectively. In this example, we set Max_Traffic_Load_Distribution to 6. Assume the network topology is as shown in Figure 1. The traffic load distribution of intermediate node I1 is 2, due to two routing paths through I1. The traffic load distribution of intermediate I2 is 1, due to one routing path through I2.. D3. D2. D. S3. D3. qp 3 + qp > qp 2 + qp 2 where 0 < q < 1 and 0 < p < 1 Then we reduce the above function as follows: 2 p +1 > 2 p . Since the value of p is larger than 0, qp 3 + qp > qp 2 + qp 2 is always established. This result proves that case 2 has better performance on block rate than case 1. Hence, using the function F2 can really distribute the routing path and also reduce the block rate. The following example describes the advantage of routing path distribution. Let the current routing states be as shown in Figure 3. S1. D1. S2. D2. I1. S3. D3. 12. S4. D4. Figure 3. The network topology. D1 Case3. I1. I1. Figure 2. The probable selection result of figure 1 However, by using the function F2, case 2 will be selected. In the following, we explain that function F2 can really distribute the routing path and has a better block rate. Let q be the probability of all routing paths through one intermediate node be dropped. Let p be the probability of one communication really to be blocked when the original routing path is dropped. Then we can define that the blocked probability of the all communication in these two case as qp 3 + qp in case 1 and qp 2 + qp 2 in case 2. Suppose that. ). S2. D1. 12. S3. ). S1. S1. 12. , j ∈ γ s_k , Normalizat ion_Constant exp Traffic_Lo ad_Distribution j ≤ Normalizat ion_Cons tant,. (. Case2. D1. D2. Case4. S1. S1. D1. S2. D2. I1. S3. D3. D1. S2. D2. I1. S3. D3. I2 S. S3. D3. S. D. Figure 1. The network topology Assume that there is a new route request form S to D. There are two routing paths can be selected. If we randomly select a routing path, two cases might occur as shown in Figure 2. In Case 1, this new route request selects I1 to be the intermediate node. In. S4. D. 12. 12. D4. S4. D4. Figure 4. The probable selection result of figure 3 Now a new route request is sent from S to D. Two possible cases can be happened as shown in Figure 4. Using the function F2 we will select the case 4 to be. 811.
(4) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. our solution.. resource into virtual currency can be as follows. 2. ⎛ Distance j,j +1 ⎞ ⎟ , j,j + 1∈ γ s_k F3 ( j ) = ⎜⎜ ⎟ ⎝ Max_Distance ⎠. In Figure 5, we set the value of q to be 0.5. Figure 5 shows the difference of block rate of versus probability of case 1 and case 2, and cas3 and case4. The performance of block rate is better, when the traffic load distribution of each intermediate node is more balance.. where F3 is the function of power consumption used to convert resource into virtual currency. Distancej,j+1 is the distance between intermediate node j and j+1. Max_Distance is max distance of communication range of j. The advantage of function F3 is described as follows. When the total distance between the source and the destination node is same, the higher the number of intermediate node, the lower the cost function of power consumption is lower. Hence, the function F3 allows the routing path with high number of intermediate node to be used in order to reduce the cost. According to these functions we proposed, the mobile user can evaluate the cost of each resources occupation. Then the source node counts the total cost it has to pay, when it selects an appropriate routing path.. difference of block rate between case1 and case2 difference of block rate between case3 and case4. 0.11 0.1 0.09 0.08. difference. 0.07 0.06 0.05 0.04 0.03 0.02 0.01 0 0.1. 0.2. 0.3. 0.4. 0.5 p. 0.6. 0.7. 0.8. 0.9. Figure 5. The relationship between p and difference of block rate The curves show that routing path distribution has a better performance on reducing block rate. By using function F2 it distributes the routing paths and balances the traffic load distribution of each intermediate node.. 2.2. Cost Function According to the node’s resources, we transform the resources of each intermediate node into virtual currency. The total virtual currency that each intermediate node can get is by adding function F1, F2, and F3 together. We sum all the virtual currency that intermediate nodes can get. Then, we can count the payment that source node should pay. The cost function of routing path is defined as follows:. 2.1.3. Power consumption. To transmit data packets to the next intermediate node consumes battery power. Here, we suppose that mobile device can adjust their power when mobile device transmits data packets to the received node. The battery power is very important to the mobile device. If there is no power, the mobile device can’t communicate with other mobile devices. If the next intermediate node is far away from the intermediate node, it consumes more power to transmit data packet to the next intermediate node. Therefore, it is better to choose next intermediate node close to the request node and to reduce the consumption of power. The free space propagation model [12] is used to predict received signal strength when the transmitter and receiver have a clear line-of-sight path between them. Suppose that the distance between the transmitter node and the receiver node is d. The strength of the signal received can be defined as follows. Pr (d ) =. 3. µ j_k = ∑ (Fi (j) × Z ) , j ∈ γ s_k i =1. λs = ∑ k. ∑µ. j∈γ s_k. j_k. where µj_k the price for each intermediate node j charges for relaying data packets. λs the source node s should pay to all the intermediate nodes for relaying its data packets. Z is the max price of each resource. The resources of each intermediate node itself are bandwidth support, traffic load distribution and power consumption. According to the cost function, we define λs as the total virtual currency which the source node should pay.. Pt G t G r λ2. 2.3. Objective Function. (4π )2 d 2 L. When a source node transmits data packets, it should pay virtual currency to the intermediate nodes for relaying data packets. Our algorithm minimizes the cost that a source node should pay. If the payment of a routing path is the lowest, the proposed algorithm will select this routing path. Based on estimation of the cost of each routing. where Pt is the transmitted power. Pr(d) is the received power. The transmitter antenna gain denotes as Gt. Gr is the receiver antenna gain. L is the system loss factor. λ is the wavelength in meters. From the above function, we can assume that the received power relates to the distance between the transmitter and the receiver. Hence, the function to transform. 812.
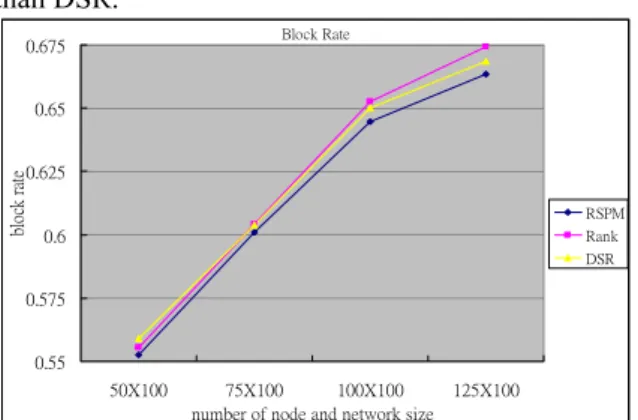
(5) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. path, our algorithm selects the routing path with minimum virtual currency. In this routing path, each intermediate node has the appropriative resources. No resources can be wasted. Then, the objective function of routing path selection algorithm can be defined as: min{λs_i}, i= 1, 2, … m m is the total number of routing paths from the source node to the destination node From the rule mentioned above, the source node could pay minimum virtual currency and get an appropriate routing path. Then, all the routing paths can be distributed and the drop rate can be reduced.. pay, the reconnection times and the block rate of routing path. Our algorithm can make each source node get an appropriate routing path by paying the minimization payment. In addition, reducing the reconnection times can decrease the network traffic. Avoiding the block of routing path can give the source node a stable connection state. Figure 6 shows that our algorithm can select the routing path with minimum virtual currency. Our algorithm is beneficial for sender node. In addition, it shows that when the density of network is higher, the payment of our algorithm is cheaper, compared to other algorithms. The proposed algorithm is about 10.95% ~ 22.47% cheaper in virtual currency than DSR.. 3. Simulation. Payment 1750. Table 1 lists the parameters [16] of our simulation environment. In (Table 1a), the simulation parameter, M×N indicates that there are M nodes placed in the N×N(m2) area. For example, 50×100 indicates that there are 50 nodes in the 100×100(m2) area. The transmission range is the maximum communication distance between any two nodes. The movement speed of nodes is denoted as Node Speed. A node has 70% probability to keep the original direction in next time cycle. Each node owns different bandwidth. In (Table 1b), requested transmission bandwidth of messages is between 15 and 25 KB. The rate of routing path request is about 100 percentages of nodes. It indicates that all nodes will send the route request each time. Each routing path needs to be maintained randomly 2 to 6 seconds to finish the transmission of data packets. We set the maximum virtual currency that each resource can get is 100 vc, where vc is the unit of virtual currency. The total simulation time is 300 seconds. Table 1. Simulation parameters (a) Network parameters number of nodes 50×100,75×100, & network size 100×100,125×100 (m2) transmission range 10 m node speed (X,Y axis) ±0.1, ±0.3, ±0.5, ±0.7 m/sec bandwidth of nodes 150 -200 KB/sec Max_Traffic_Load_Distribution 6 Max_Distance 10 m (b) Route parameters requested transmission bandwidth 15 - 25 of message KB/sec rate of route request 100 % life time of routing path 2 - 6 sec maximum virtual currency of 100 vc resource simulation time 300 sec Our algorithm compares with the DSR algorithm and rank-based routing path selection algorithm. All competing algorithms are simulated in the same environment. The effects our algorithm takes care are the average virtual currency each source node should. virtual currency (vc). 1550. 1350. RSPM. 1150. Rank. DSR 950. 750. 550 50X100. 75X100. 100X100. 125X100. number of node and network size. Figure 6. The average payment of each routing path selected by three algorithms From Figure 7, one can see that the proposed algorithm, RSPM, has better performance on the number of reconnect in routing path. In other words, the proposed algorithm reduces the traffic of network. It can reduce the traffic of network about 6.89% ~ 15.2% compared to DSR. Reconnect 3800 3450. number of reconnect. 3100 2750 2400. RSPM. 2050. Rank DSR. 1700 1350 1000 650 50X100. 75X100 100X100 number of node and network size. 125X100. Figure 7. The number of reconnecting routing path by three algorithms In Figure 8, RSPM has lower block rate of routing path. The rank-based routing path selection algorithm, denoted as rank, sometimes can not decide the only one routing path for transmitting data packets to destination node because of too many routes with the same rank value. Then, it uses random policy to generate the routing path. However, the proposed algorithm can determine the only one routing path for transmitting data packets. Therefore, our algorithm has better performance on block rate of routing path. RSPM is about 0.76% ~ 1.16% better. 813.
(6) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. than DSR.. Oct., 1994. [6] J. Broch, D.A. Maltz, D.B. Johnson, Y.C. Hu, J. Jetcheva, “A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols”, in Proc. of the ACM/IEEE MOBICOM’98, pp.85-97, Oct., 1998. [7] P. Johansson, T. Larsson, N. Hedman, B. Mielczarek, M. Degermark, “Scenario-based Performance Analysis of Routing Protocols for Mobile Ad-hoc Networks”, in Proc. of the ACM/IEEE MOBICOM’99, pp.195-206, Aug., 1999. [8] D.B. Johnson, D.A. Maltz, “Dynamic Source Routing in Ad Hoc Wireless Networking”, in Mobile Computing, pp.153-181,1996. [9] C.E. Perkins, E.M. Royer, “Ad Hoc On-Demand Distance Vector Routing”, in Proc. of the IEEE WMCSA’99, pp.90-100, Feb., 1999. [10] Z.J. Haas, M.R. Pearlman, P. Samar, “The Zone Routing Protocol (ZRP) for Ad Hoc Networks”, draft-ietf-manet-zone-zrp-04.txt, Internet-Draft, IETF, Aug., 2002. [11] D. Turgut, B. Turgut, S.K. Das, R. Elmasri, “Balancing loads in mobile ad hoc networks”, in Proc. of the 10th International Conf. on Telecommunications 2003, vol. 1, pp.490-495, Feb., 2003. [12] I.S. Hwang, C.C. Yeh, C.Y. Wang, “Link stability, loading balance and power control based multi-path routing (SBPMR) algorithm in ad hoc wireless networks”, in Proc. of the 10th International Conf. on Telecommunications 2003, vol. 1, pp.406-413, Feb., 2003. [13] N. Milanovic, M. Malek, A. Davidson, V. Milutinovic, “Routing and security in mobile ad hoc networks”, Computer, vol. 37, pp.61-65, Feb., 2004. [14] D.B. Johnson, D.A. Maltz, Y.C. Hu, “The Dynamic Source Routing Protocol for Mobile Ad Hoc Networks (DSR)”, IETF Mobile Ad Hoc Networks Working Group, Internet Draft, work in progress, Apr., 2003. [15] C.E. Perkins, E.M. Belding-Royer, S.R. Das, “Ad Hoc On-Demand Distance Vector (AODV) Routing”, IETF Mobile Ad Hoc Networks Working Group, Internet Draft, work in progress, Feb., 2003. [16] M.S. Jian, P.L. Wu, C.N. Lee, “On-demand flow regulated routing for ad-hoc wireless network”, in Proc. of the 5th international symposium on WPMC, vol. 2, pp.242-246, Oct., 2002. Block Rate. 0.675. 0.65. block rate. 0.625 RSPM. 0.6. Rank DSR. 0.575. 0.55 50X100. 75X100 100X100 number of node and network size. 125X100. Figure 8. The block rate of routing path. 4. Conclusions We have proposed an algorithm using the price mechanism in routing path selection. Such an approach makes each mobile device select appropriate routing path for transmission and allows intermediate nodes to get benefits. In the proposed algorithm, the transmission payment of source node is about 10.95% ~ 22.47% cheaper than DSR. The traffic load distribution of network can be reduced about 6.89% ~ 15.2%. The block rate of route request is about 0.76% ~ 1.16% better than DSR. In the future, we will further consider security problems for transmission in mobile ad hoc network. Furthermore, we will incorporate them into our algorithm to enhance the privacy and security for transmission.. References [1] M.S. Jian, C.C. Chen, C.N. Lee, “Ad Hoc On-Demand Resource Management Using Improved Rank-Based Fitness Assignment”, in Proc. of the 6th international symposium on WPMC, vol. 2, pp.256-258, Oct., 2003. [2] Y. Qiu, P. Marbach, “Bandwidth allocation in ad hoc networks: a price-based approach”, in Proc. of the INFOCOM 2003, 22th Annual Joint Conf. of the IEEE Computer and Communications Societies, vol. 2, pp.797-807, April, 2003. [3] L. Buttyan, J.P. Hubaux, “Nuglets: a virtual currency to stimulate cooperation in self-organizing mobile ad hoc networks”, Tech. Rep, DCS/2001/001, Swiss Federal Institute of Technology, Jan., 2001. [4] X. Zhang, L. Jacob, “Adapting zone routing protocol for heterogeneous scenarios in ad hoc networks”, in Proc. of the International Conf. on Parallel Processing 2003, pp.341-348, Oct., 2003. [5] C.E. Perkins, P. Bhagwat, “Highly Dynamic Destination-Sequenced Distance-Vector Routing (DSDV) for Mobile Computers”, in Proc. of the ACM SIGCOMM’94, vol. 24, no. 4, pp.234-244,. 814.
(7)
數據
相關文件
Responsible for providing reliable data transmission Data Link Layer from one node to another. Concerned with routing data from one network node Network Layer
Microphone and 600 ohm line conduits shall be mechanically and electrically connected to receptacle boxes and electrically grounded to the audio system ground point.. Lines in
Given a graph and a set of p sources, the problem of finding the minimum routing cost spanning tree (MRCT) is NP-hard for any constant p > 1 [9].. When p = 1, i.e., there is only
“Ad-Hoc On Demand Distance Vector Routing”, Proceedings of the IEEE Workshop on Mobile Computing Systems and Applications (WMCSA), pages 90-100, 1999.. “Ad-Hoc On Demand
In an ad-hoc mobile network where mobile hosts (MHs) are acting as routers and where routes are made inconsistent by MHs’ movement, we employ an associativity-based routing scheme
• As RREP travels backwards, each node sets pointer to sending node and updates destination sequence number and timeout entry for source and destination routes.. “Ad-Hoc On
Since the sink is aware of the location of the interested area, simple greedy geographic routing scheme is used to send a data request (in the form of
This project integrates class storage, order batching and routing to do the best planning, and try to compare the performance of routing policy of the Particle Swarm