行政院國家科學委員會專題研究計畫(第二年)進度報告
具位置知覺之無線隨意行動網路的設計與實作
子計畫二:具位置知覺之無線隨意行動網路的繞徑協定
Design & Implement Location-Aware of Mobile Ad Hoc Networks
Sub-Project(2): Location-Aware Routing Protocols for Mobile Ad Hoc Networks
計畫編號:NSC 90-2213-E-009-049
計畫編號:NSC 91-2213-E-009-020
執行期限:90 年 8 月 1 日至 92 年 7 月 31 日
主持人:曾煜棋 教授 交通大學資訊工程系
摘要:
A mobile ad-hoc network (MANET) is
formed by a cluster of mobile hosts, without the infrastructure of base stations. To deal with the dynamic changing
topology of a MANET, many routing protocols have been proposed. In this paper, we consider the route maintenance problem, which includes two parts: route deterioration and route breakage. In a
MANET, a route may suddenly become broken because only one host roams away. Even if a route remains connected, it may become worse due to host mobility or a better route newly being formed in the system. Existing protocols, however, will stick with a fixed route once it is
discovered, until it is expired or broken. In this paper, we show how to enhance several existing protocols with route optimization and local route recovery
capability. So the routing paths can be adjusted on-the-fly while they are still being used for delivering packets and can be patched in minimum wireless
bandwidth and delay while route errors
occur.
關鍵詞 : mobile ad hoc network
(MANET), mobile computing, routing, route recovery, wireless network.
1. Intr oduction
Routing protocols for a MANET can be classified as proactive and reactive,
depending on how they react to topology changes [4]. Observing that a proactive protocol may pay costs to constructing routes even if mobile hosts do not have such need, thus wasting the limited wireless bandwidth, many researchers have proposed to use reactive-style protocols, where routes are only constructed on-demand. Many reactive protocols, such as Dynamic Source Routing (DSR) [5], Signal Stability-based Adaptive Routing(SSA) [3], and Ad Hoc On Demand Distance Vector Routing (AODV) [8], have been proposed based on such on-demand philosophy. Recently, a hybrid of these two approaches, called
the Zone Routing Protocol (ZRP) [4], is also proposed.
Routing in a reactive protocol typically consists of three parts: route discovery, data forwarding, and route maintenance.
This paper considers the route maintenance problem in a reactive protocol. When a mobile host wants to communicate with another host, it first tries to discover a good route to the destination, on which the data packets are forwarded. Route maintenance, under our definition, should address two issues:
route deterioration and route breakage.
Route deterioration refers to the situation where an existing route becomes worse than other routes due to host mobility. However, in existing protocols, such as [3,4,5,8], a sending host will stick with the discovered route until it is expired or broken, even if some better routes are newly being formed in the system. One straightforward solution is to run the route discovery procedure more frequently to detect such possibility. However, this is very costly as route discovery is typically done by network flooding [7]. This observation has motivated the first work in this paper: we propose to use route optimization to refine or improve the
routes on-the-fly while they are being used
for transmission. Not only can the data packets be sent with less hops and latencies, but also may the chances of route breakage be reduced, lowing the number of times the costly route discovery process being called.
To deal with the route breakage problem,
most existing protocols will send a route error packet back to the source node from the position where breakage is found, which will then invoke another route discovery procedure. However, since route discovery is very costly (in terms of both bandwidth and delay), it should be used with caution. Several recent works have targeted in the direction of reducing the cost of one route discovery [2,6,7]. In this paper, we propose to exploit the
locality of a route to reduce the number of
times that route discovery is activated. We observe that it is very likely that a route is broken because only one relay node leaves its neighbors. This is very similar to the “spatial locality” discussed in [2], which uses prior routes to rebuild new routes. In this paper, we suggest to use a local route recovery to patch a broken route before a
route error packet is sent back to its source node.
2. The Enhancements of
Existing Routing Pr otocols
2.1. Route Optimization for DSR
In DSR, since source routing is used, the routing paths are only kept two places: those source nodes that are currently active in sending messages, and data packet headers. As a result, route
optimization should be achieved based on information therein.
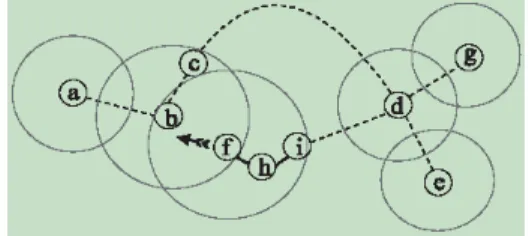
As the MANET topology changes, it is possible for a source node to find out a
better route for another source. For instance, consider the scenario in Fig1. Suppose there is a route from a to e :
a →→ → →→ →→b c d e. Under a promiscuous mode, node f may hear
the packets from b to c . If f has a
route f →→ →→d g. If the hop count from c to d is longer than f to d ,
then f can suggest a better route a→→ → →→ →→b f d e to the source node a .
The route optimization protocol is formally developed below.
It is executed by any node f
receiving a data packet from node b to
node c such that c≠ f .
Figur e 1. An example of r oute optimization in DSR.
2.2. Route Optimization for SSA
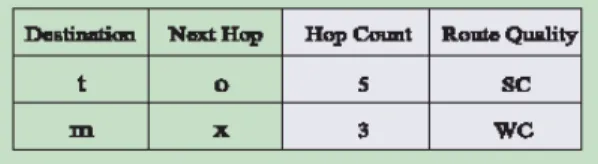
There are two directions to optimize routes in SSA: (i) to find a route of a less hop count, and (ii) to find a route of higher quality (such as from SC to WC).
To achieve these goals, we modify the routing table used in the SSA to one as shown in Fig2. The hop-count field is the
length to the corresponding destination. The route quality field indicates the
quality of the route. These two fields can be filled when the ROUTE_REPLY packet returns from the destination to the source, using the hop_list and PREF fields.
Also, to help finding a shorter route, each data packet must indicate the remaining hops that it has to traverse. Thus, we modify the data packet format as shown in
Fig3, by adding a hop_count field.
Through this information, it is possible for other nodes to tell if they can suggest shorter routes or not.
Figur e 2. The modified r outing table used in SSA. The modified par t is shown in gr ay.
Figur e 3. The new for mat of data packet used in SSA.
For instance, suppose there are data packets being transmitted along the path:
a→→ → →b c d (refer to Fig4). When a node, say f , hears a data packet sent
by b and it has a better route from f
to d , node f can send a packet to
packet destined for d to it instead of to
node c . The protocol is formally
developed as follows. It is executed by any node f when receiving a data
packet from node b to node c such
that c≠ f .
Figur e 4. An example of r oute optimization in pr otocols using next-hop r outing such as SSA
and AODV.
2.3. Route Optimization for AODV
The AODV protocol also follows the next-hop routing style. So the route optimization is similar to the SSA protocol. Both the routing table and the data packet need to have a hop-count field. The only difference is that the AODV does not have the link quality information, but it has a destination-sequence-number field. A larger sequence number means a fresher route, so this may also mean a route of less chance being broken. The protocol shown below is a slight
modification of the one for SSA.
2.4. Route Optimization for ZRP
In ZRP, a node always knows the best route to any node in its local zone, so no route optimization is needed for intra-zone routing. On the inter-zone part, a modified DSR protocol is used.
For instance, consider a MANET using ZRP with radius = 2. Suppose there is a route from a to e : (refer to Fig5). Note that only border nodes are registered in a route, so in Fig5 node c is a border node of b’s zone. Suppose there is another route
... ...
f → → → → →i d g, and the border count from f to d is less than that from c to d. If f hears the packets from b to e, f can figure out a better route
... ... ...
a→ → → → → → → →b f i d e
and recommend the route to the source a.
Figur e 5. A r oute optimization example for the ZRP pr otocol
successfully deliver data packets to the destination e, the route has violated the original ZRP protocol’s definition because node f is not a border node of node b(the hop count is 1, which may be less than the radius). This can be resolved as follows. Node a still transmits data packets using the new route recommended by f. When f receives a data packet from b with itself as the border, it will find out from its
intra-zone routing table that h should be a border node of b leading to i. So f can replace itself by h in the packet header and forward the data packet to h (now the new route will become
... ... ...
a → → → → → → → →b h i d e). Then intra-zone routing will be used to forward the data packet to h. On h receiving the data packet, the similar scenario will be discovered by h, who will further modify the route in the data packet. This will keep on going until the packet arrives at e. Now the route already follows the ZRP style, so node e will send a ROUTE_REPLY with this modified route to a.
We now formally present the protocol. The protocol is executed by any node f receiving a data packet from b to c destined to e such that c≠ f .
3. Conclusions
In this paper, we have shown how to perform route optimization for four MANET routing protocols, namely DSR, SSA, AODV, and ZRP. The original protocols will use a fixed route between a pair of node to deliver data packets, until it is broken. We show how to enhance these protocols with route optimization such that better routes can be formed on-the-fly while the original route is being used for transmission. So data packets will not experience delays even under route optimization. Our route optimization may lead to unstable routes due to host
mobility (e.g., going back and forth between two routes), thus wasting the wireless bandwidth. Hence one direction that deserves further investigation is to perform route optimization only when the new route is shorter as well as more stable (which may be determined from, say, signal strength). Recently, an independent work [1] also suggests a similar approach. As a route becomes broken, route
recovery can be performed. Since such an event will be sent to the source host, the source host will initiate a route
optimization request when some criteria is satisfied.
4. Refer ences
[1]. Z.~Cai, M.~Lu, and C.~Georghiades. Optimized Reparation Based on
Sequenced Number Routing for Ad Hoc Networks. IASTED Int'l Conf. on Parallel and Distributed Computing and Systems, pages 302--306, 1999.
[2]. R.~Castaneda and S.~R. Das. Query Localization Techniques for On-Demand Routing Protocols in Ad Hoc Networks. Proc. ACM MOBICOM '99, Aug. 1999. [3]. R.~Dube, C.~Rais, K.~Wang, and S.~Tripathi. Signal stability based adaptive routing for ad--hoc mobile
networks. IEEE Personal Communications, Feb. 1997.
[4]. Z.~J. Haas and M.~R. Pearlman. The zone routing protocol for ad--hoc
networks. Internet draft RFC
(http://www.ietf.org/html.charters/manet-c harter.html), Nov. 1997.
[5]. D.~Johnson and D.~Maltz. Dynamic Source Routing in Ad Hoc Wireless Networks in Mobile Computing, T. Imielinski and H. Korth eds, pages 153--181. Kluwer Academic, 1996. [6]. Y.-B. Ko and N.~H. Vaidya.
Location-Aided Routing (LAR) in Mobile Ad Hoc Netwroks. Proc. ACM
MOBICOM '98, Aug. 1998.
[7]. S.-Y. Ni, Y.-C. Tseng, and J.-P. Sheu. The Broadcast Storm Problem in a Mobile Ad Hoc Network. Proc. ACM
MOBICOM '99, Aug. 1999.
[8]. C.~Perkins. Ad--Hoc on--Demand Distance Vector Routing. Internet draft RFC
(http://www.ietf.org/html.charters/manet-c harter.html), Nov. 1997.