A Robust Watermarking Technique for Still Image Using Compression Concept and Coefficient Difference
全文
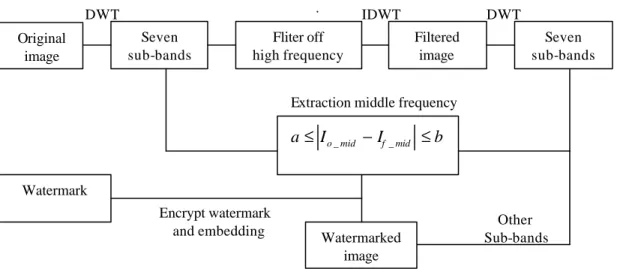
(2) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. However, the schemes have lower robustness than the former ones [9]. In this paper, we utilize the concept of compression based on the aspects we mentioned above and embed a watermark into the coefficients difference between the middle frequency of the original image and the compression one. The proposed scheme provides a robust characteristic and maintains good visual quality of an image. Moreover, the watermark is designed to be extracted without the original image so that the application is more feasible in practice. The rest of this paper is organized as follows. In Section 2, the related background is introduced. In Section 3, the details of the proposed algorithm are described. The experimental results are shown in Section 4. Finally, the conclusions are drawn in Section 5.. The energy of the three sub-bands (HL1, LH1, HH1) is relatively small and less than 1% of the total energy [11]. Moreover, human visual system is less sensitive to noise in high resolution bands and in those bands having orientation of 45 degrees [4]. Hence, these sub-bands of high frequency can be modified or removed suitably based on the concept of compression we mentioned above and the modified image will not cause noticeable artifacts.. 3. The proposed algorithm This section will illustrate the proposed scheme in detail. The embedding and extraction process of the proposed scheme are described in Section 3.1 and Section 3.2 respectively.. 3.1. Watermark embedding process. 2. Wavelet transformation It is well-known that the significant portions of an image are concentrated in low frequency. Hence, watermarking information should not be embedded into low frequency to avoid causing noticeable artifacts. Furthermore, in order to survive lossy compression, the important information of a watermark should not be embedded into high frequency of an image [8]. Thus the best way is to embed a watermark into middle frequency component of an image. The hierarchical structure of wavelet transform provides us a straightforward analysis way to embed watermark into an image. Moreover, it also provides excellent spatial-frequency localization for analyzing image features such as edges or textured areas [13]. Nowadays, many researchers have explored and developed the utility of the wavelet transform. Moreover, wavelet transform has replaced DCT and become a main technique in JPEG2000 compression standard. Fig. 1 shows a two-level wavelet decomposition of an image. First, an image is decomposed into four sub-bands (LL1, HL1, LH1, HH1), where L (H) represents the low (high) sub-band and the subscript denotes the pyra mid level index. Furthermore, LL, LH, HL and HH represent the approximation, the horizontal detail, the vertical detail and the diagonal detail of an image respectively. The sub-band LL1 can be further decomposed into four sub-bands (LL2, HL2, LH2, HH2). The process is iterated several times that depends on user’s applications. Furthermore, the energy of each sub-band can be computed by the following formula: 1 M N 2 (1) E= ∑ ∑ y (i , j ) , MN i =1 j =1 where M and N represent the size of the sub-band and y signifies the wavelet coefficients of the image.. 2 456. The original image X is a gray-level image with M by N pixels. The watermark W is a binary image with S by T pixels. They are defined as follows: X = {x( i, j) | 0 ≤ i ≤ M−1, 0≤ j ≤ N−1, 0≤ x( i, j) ≤ 255}, (2). and W = {w(k, l) | 0 ≤ k ≤ S −1, 0 ≤ l ≤T −1, 0 ≤ w( k, l) ≤1}, (3). First, the proposed embedding technique decomposes an image into seven sub-bands by wavelet transform. Then a filter is used to filter off high frequency components base on the concept of compression. Finally, the watermark is embedded into the coefficients difference between the middle frequency of the original image and the filtered one. The watermark embedding process is depicted as follows. Step 1: Generate a pseudo random bit-sequence by using a seed and form the same size matrix as the watermark, i.e., S ={s(k, l) | 0 ≤ k ≤ S −1, 0 ≤ l ≤T −1, 0 ≤s(k, l) ≤1}, (4). Step 2: Encrypt the watermark by a bit-wise logical exclusive-OR (XOR) operation with S, i.e.,. Step 3: Step 4: Step 5: Step 6: Step 7:. sw( k, l ) = w( k, l ) ⊕ s ( k, l ). (5) Decompose the original image into seven sub-bands by using the DWT. Filter off one of three high sub-bands (HL1, LH1, and HH1). Perform the inverse wavelet transform and obtain the filtered image. Decompose the filtered image into seven sub-bands by using the DWT. Extract and compare the coefficient difference between the middle frequency of.
(3) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. the original image and the filtered one by computing a ≤ I o _ mid − If _ mid ≤ b.. 4. The experimental results. Step 8: According to the result of Step 7 and randomly select the candidate locations to embed watermark. The watermark is embedded as follows:. In the following experiments, two gray-level images with size of 256 by 256 are used as the original image, called Lena and Pepper. An institute’s name with size of 32 by 32 is used as the watermark (as shown in Fig 3). The embedded sub-band is HH2. Furthermore, Photoimpact 7.0 is used to perform image processing attacks. First, the watermark is encrypted using a pseudo random bit-sequence generated by a seed. Then the watermark is embedded into the experimental images through the proposed scheme. After embedding the watermark into the images, we can evaluate the quality of the images by PSNR (Peak Signal to Noise Ratio) value. PSNR of the watermarked image is defined as:. I o _ mid (i, j) = I f _ mid (i, j) + ( 2 × sw(k, l) −1) × β, (6) where ß is the visual weight to balance the tradeoff of the robustness of the watermark and the visual quality of the watermarked image. Step 9: Perform the inverse wavelet transform and obtain the watermarked image. Note that the sequence of embedded locations of the watermark should keep as the secret key for subsequent watermark extraction. The watermark embedding diagram is shown as Fig. 2.. PSNR = 10.log. 3.2. Watermark extraction process MSE =. (dB). 10. ,. (10). 1 m× n. m −1. n −1. i=0. j=0. ∑ ∑ (X. 2. ij. − X′) ij. ,. (11). where X ij represents the original image and X ij ′ represents the watermarked image. A large value for PSNR means less difference between the original image and the watermarked one. In general, it is very difficult to recognize the difference between the original image and the watermarked one in vision if the PSNR value is greater than 30 dB. Furthermore, after extracting the watermark, we can evaluate the visually recognizable patterns subjectively. However, the subjective measurement is determined by the factors such as expertise of the viewers, experimental environments, and so on. To evaluate the performance of the proposed method, some objective measures are adopted in this paper and described as follows.. Step 1: Decompose the watermarked image into seven sub-bands by using the DWT. Step 2: Filter off one of three high sub-bands (HL1, LH1, and HH1). Step 3: Perform the inverse wavelet transform and obtain the filtered watermarked image. Step 4: Decompose the filtered watermarked image into seven sub-bands by using the DWT. Step 5: Extract and compare the coefficient difference between the middle frequency of the watermarked image and the filtered watermarked one according to the embedded location and obtain the embedded information, i.e.,. A. Both normalized cross-correlation (NC) coefficient and standard correlation (also referred to as correlation) coefficient are used to judge the similarity between the original watermark and the extracted one exploited in [7]. The NC coefficient is defined as:. 1 if I w _ mid (i, j) ≥ I fw _ mid (i, j) sw′ ( k, l ) = { (7) 0 if I w _ mid (i, j) < I fw _ mid (i, j).. ∑ ∑ w ( i,. Step 6: Generate a pseudo random bit-sequence by the seed and form the same size matrix as the watermark, i.e.,. NC =. S ={s(k, l) | 0 ≤ k ≤ S −1, 0 ≤ l ≤T −1, 0 ≤s( k, l) ≤1}, (8). m. n. i=1. j =1. j ) w′ ( i, j ). (12). .. ∑ ∑ [ w ( i, m. i=1. n. j )]. 2. j =1. On the other hand, the correlation coefficient (CC) is defined as:. Step 7: Decrypt the watermark by a bit-wise logical exclusive-OR (XOR) operation with S, i.e.,. Step 8:. 2. MSE. The watermark extraction procedure doesn’t need the original image. We utilize the sequence of embedded locations and seed to retrieve the watermark. The watermark extraction process is depicted as follows.. w ′ (k , l ) = s w ′( k , l ) ⊕ s ( k , l ) .. 255. ∑ ∑( W ( i, j ) −W ) (W ′( i, j ) − W′) CC =. (9). i=m. ∑. Compare the extracted watermark with the original watermark.. i. 3 457. i= m. j=n. i. j. ∑(W (i , j ) − W ) j =n. j. , 2. ∑∑( i =m. j =n. i. j. W ′ (i , j ) − W′. ). 2. (13).
(4) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. where W is the original watermark and W ′ is the extracted watermark. Their corresponding mean values are W and W ′ respectively.. results with 50% of the image has been removed. Although the image quality is degraded greatly, the extracted watermarks are still very good.. B. The bit error rate (BER) is computed as:. 4.4. Mixed filtering. BER. N. = W. x. We test the robustness of the proposed method by mixing smoothing with sharpening. Table 6 shows the extracted results of applying mixed filtering attack. The test results show the proposed method can also survive the filter attack.. e. ⋅. W. ,. (14). y. where Ne denotes the number of bits that has different values in the extracted watermark compared to the original one, W and W denote the length and x. y. 4.5. Noise adding. width of image respectively [7]. No error bit means the extracted watermark is identical with the original one. Table 1 shows the PSNR values of the watermarked images and the results of watermark extraction respectively. It is obvious that the watermarked images maintain very good visual quality and the embedded watermark has perfectly extracted from the watermarked image. On the other hand, we use several image processing tools, including lossy JPEG and JPEG2000 compression methods, scaling, cropping, mixed filtering and, nois e adding, to evaluate the robustness of the proposed scheme.. In the experiment, we evaluate the robustness by adding Gaussian noise on the watermarked image. Table 7 shows the results of adding Gaussian noise with variance 100. The experimental result is still good. It indicates that the proposed scheme is remarkable robust to noise attack.. 5. Conclusions In the paper, we propose a robust watermarking technique by using the concept of compression to embed a watermark into the coefficients difference between the middle frequency of the original image and the compression one. On the other hand, by a pseudo random bit-sequence generated by a seed to encrypt the watermark, the security has strongly enhanced. Furthermore, the watermark is designed to be extracted without the original image so that the application is more feasible in practice. Experimental results show that the scheme not only meets the requirements of the imperceptibility and security, but also features the robustness against various signal processing attacks such as JPEG and JPEG2000 lossy compression techniques, scaling, cropping, mixed filtering and, noise adding.. 4.1. JPEG and JPEG2000 compression techniques Compression is a common application which appears often for saving the bandwidth of transmission and the capacity of storage. JPEG compression technique is popular among image compression for still image. Recently, JPEG2000 compression technique has been used widely as a result of its excellent performance in compression. Table 2 and Table 3 show the results after JPEG and JPEG2000 compression with a quality factor of 10% respectively. Obviously, the extracted watermarks are nearly the same with the original watermark.. 6. References [1] N. Nikolaidis and I. Pitas, “Robust image watermarking in the spatial domain,” Signal Processing, vol. 66, no. 3, pp. 385-403, 1998. [2] D.-C. Lou and J.-L. Liu, “Steganographic method for secure communications,” Computers & Security, vol. 21, no. 5, pp. 449-460, 2002. [3] S.-C. Chu, J. F. Roddick, Z.-M. Lu and J.-S. Pan, “A digital image watermarking method based on labeled bisecting clustering algorithm,” IEICE Transactions on Fundamentals, vol. E87-A, no. 1, pp. 282-285, Jan. 2004. [4] M. Barni, F. Bartolini, and A. Piva, “Improved wavelet-based watermarking through pixel-wise masking,” IEEE Transactions on Image Processing, vol. 10, no. 5, pp. 783-791, May 2001.. 4.2. Scaling In the experiments, the watermarked images are first reduced to 1/4 of its original size. In order to detect the watermark, the reduced image is recovered to its original dimension. From Table 4, the proposed method is also robust against the scaling attack.. 4.3. Cropping This is a very common attack because in many cases the attacker is interested in a small portion of the watermarked images. Table 5 shows the extracted. 4 458.
(5) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. [5] D.-C. Lou and T.-L. Yin, “Adaptive digital. watermarking using fuzzy clustering technique,” IEICE Transactions on Fundamentals, vol. E84-A, no. 8, pp. 2052-2060, Aug. 2001.. [12]. [6] I. J. Cox, J. Kilian, F. T. Leighton, and T. Shamoon, “Secure spread spectrum watermarking for multimedia,” IEEE Transactions on Image Processing, vol. 6, no. 12, pp. 1673-1687, Dec. 1997. [7] M.-S. Hsieh, D.-C. Tseng, and Y.-H. Huang, “Hiding digital watermarks using multiresolution wavelet transform,” IEEE Transactions on Industrial Electronics, vol. 48, no. 5, Oct. 2001. [8] C.-T. Hsu and J.-L. Wu, “Multiresolution watermarking for digital image,” IEEE Transactions on Circuits and System-II: Analog and Digital Signal Processing, vol. 45, no. 8, pp. 1097-1101, Aug. 1998. [9] Peter H. W. Wong, Oscar C. Au, and Y. M. Yeung, “A novel blind multiple watermarking technique for images,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 13, no. 8, pp. 813-830, Aug. 2003. [10] Y. Wang, J. F. Doherty, and R. E. Van Dyck, “A wavelet-based watermarking algorithm for ownership verification of digital images,” IEEE Transactions on Image Processing, vol. 11, no. 2, pp. 77-88, Feb. 2002. [11] Y.-S. Kim, O. H. Kwon, and R. H. Park, “Wavelet based watermarking method for digital images using. [13]. [14]. [15]. [16]. [17]. the human visual system”, Proceedings of the IEEE International Symposium on Circuits and System, 1999, vol. 4, pp. 80-83. W. Zeng and B. Liu, “A statistical watermark detection technique without using original images for resolving rightful ownerships of digital images,” IEEE Transactions on Image Processing, vol. 8, no. 11, pp. 1534-1548, Nov. 1999. P. Meerwald and A. Uhl, “A survey of waveletdomain watermarking algorithms,” Proceedings of SPIE, Electronic Imaging, Security and Watermarking of Multimedia Contents III, vol. 4314, San Jose, CA, USA, Jan. 2001. D.-C. Lou and J.-L. Liu, “A robust watermarking scheme based on the just-noticeable-distortion,” Journal of Chung Cheng Institute of Technology, vol. 31, no. 2, pp. 11-22, May 2003. D. Zhao, G. Chen, and W. Liu, “A chaos-based robust wavelet-domain watermarking algorithm,” Chaos, Solitons and Fractals, vol. 22, pp. 47-54, Oct. 2004. L.-H. Chen and J.-J. Lin, “Mean quantization based image watermarking,” Image and Vision Computing, vol. 21, pp. 717-727, 2003. D.-C. Lou and C.-H. Sung, “A steganographic scheme for secure communications based on the chaos and euler theorem,” IEEE Transactions on Multimedia, vol. 6, no. 3, June 2004. LL2. HL2. LH2. HH2. HL1. Original image LH1. HH1. Fig. 1 Two-level wavelet decomposition of an image .. DWT Original image. Seven sub-bands. IDWT. Fliter off high frequency. DWT Filtered image. Seven sub-bands. Extraction middle frequency. a ≤ I o _ mid − If _ mid ≤ b Watermark Encrypt watermark and embedding. Watermarked image. Fig. 2 The diagram of watermark embedding process.. 5 459. Other Sub-bands.
(6) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. Fig. 3 The experimental images and the watermark, (a) Lena, (b) Pepper, (c) an institute name.. Lena Pepper. Table 1. The watermarked image under no attack and the results of extraction. No attack Extraction results PSNR NC CC 46.74 1 1 46.71 1 1. BER 0 0. Table 2. The watermarked image with a JPEG compression quality factor of 10% and the results of extraction. JPEG attack Extraction results PSNR NC CC BER Lena 29.14 1 1 0 Pepper 28.56 1 1 0 Table 3. The watermarked image with a JPEG2000 compression quality factor of 10% and the results of extraction. JPEG2000 attack Extraction results PSNR NC CC BER Lena 23.67 1 1 0 Pepper 21.26 1 1 0 Table 4. The watermarked image by scaling attack and the results of extraction. Scaling attack Extraction results PSNR NC CC Lena 31.19 1 1 Pepper 29.29 1 1. BER 0 0. Table 5. The watermarked image by cropping 50% and the results of extraction. Cropping attack Extraction results PSNR NC CC Lena 8.45 1 1 Pepper 7.22 1 1. BER 0 0. Table 6. The watermarked image by mixed filtering attack (sharpening + blurring) and the results of extraction. Mixed attack Extraction results PSNR NC CC BER Lena 28.13 1 1 0 Pepper 25.61 1 1 0 Table 7. The watermarked image by adding Gaussian noise with variance 100 and the results of extraction. Noise attack Extraction results PSNR NC CC BER Lena 10.26 1 1 0 Pepper 10.5 1 1 0. 6 460.
(7)
數據
相關文件
Hence, code for each non zero AC coefficient is composed of a basecode (corresponding to runlength/category) and a code corresponding to offset in.. Standard tables vs
6 《中論·觀因緣品》,《佛藏要籍選刊》第 9 冊,上海古籍出版社 1994 年版,第 1
We do it by reducing the first order system to a vectorial Schr¨ odinger type equation containing conductivity coefficient in matrix potential coefficient as in [3], [13] and use
Understanding and inferring information, ideas, feelings and opinions in a range of texts with some degree of complexity, using and integrating a small range of reading
Promote project learning, mathematical modeling, and problem-based learning to strengthen the ability to integrate and apply knowledge and skills, and make. calculated
Wang, Solving pseudomonotone variational inequalities and pseudocon- vex optimization problems using the projection neural network, IEEE Transactions on Neural Networks 17
volume suppressed mass: (TeV) 2 /M P ∼ 10 −4 eV → mm range can be experimentally tested for any number of extra dimensions - Light U(1) gauge bosons: no derivative couplings. =>
Define instead the imaginary.. potential, magnetic field, lattice…) Dirac-BdG Hamiltonian:. with small, and matrix