907
Anonymous Password Based Authenticated Key Exchange
with Sub-Linear Communication
*HSIAO-YING LINAND WEN-GUEY TZENG
Department of Computer Science National Chiao Tung University
Hsinchu, 300 Taiwan
E-mail: {lrain.cis92g@; wgtzeng@cs.}nctu.edu.tw
In this paper we propose a new anonymous password-based authenticated key ex-change protocol. The communication cost of our protocol is sub-linearO N( ),which improves a previous one of O(N) cost, where N is the number of users in the system. We show that the session key is secure against an active adversary in the random oracle model and identity anonymity is secure against a semi-honest adversary in the standard model.
Keywords: password based authentication, anonymous authentication, private
informa-tion retrieval, authenticated key exchange, homomorphic encrypinforma-tion
1. INTRODUCTION
There are many websites that users can access via Internet to obtain information. Some websites would like to restrict access of their valuable data so that only authorized users can obtain them. Authentication is an essential part for a system to control access. A user’s identity is authenticated by showing what secret he possesses. There are two types of secrets: long random string and password. The authentication system of using a long random string can be very secure if properly designed and used. However, it is impossi-ble for a user to remember a long random string. Thus, a user needs an auxiliary device to store his long random secret and sometimes to provide computing capability. In prac-ticality, users may prefer to use rememberable passwords. Thus, we focus on identity authentication based on passwords.
In some cases, a user is concerned about his privacy, such as, his interested informa-tion, access behavior, etc. Equivalently, the user does not want his identity to be known by a system when he retrieves data from the system. Identity anonymity and authentica-tion seem conflicting since the system needs a user’s identity for authenticaauthentica-tion and the user does not want to reveal his identity. However, an anonymous authentication protocol provides a solution.
In this paper we propose a new anonymous password-based authenticated key ex-change (APAKE) protocol. The communication cost of our protocol is sub-linear O( N), which is better than the O(N) cost of a previous scheme [14], where N is the number of users in the system. In our protocol, the system and a user share a long-term password for Received June 7, 2007; revised December 21, 2007; accepted March 20, 2008.
Communicated by Chi-Jen Lu.
* Research partially supported by the National Science Council of Taiwan, R.O.C. under grant No. NSC 95-2221-E-009-031 and Taiwan Information Security Center at NCTU (TWISC@NCTU No. 96-2219-E-009 013).
authentication. The system authenticates a user’s identity without knowing it. Also, a session key is established between the system and the user for later secure communica-tion. For security analysis, we show that the session key is secure against an active ad-versary in the random oracle model and identity anonymity is secure against a semi- honest adversary in the standard model.
Related work. Bellovin and Merrit proposed a PAKE protocol and proved its
secu-rity against the dictionary attack [3]. Since then, many researchers proposed provably secure PAKE protocols [1, 2, 4, 6, 7, 12].
Viet, et al. [14] proposed the first APAKE protocol. The protocol is based on the oblivious transfer protocol of Chu and Tzeng [9] because the anonymity property is simi-lar to choice concealment in the oblivious transfer protocol. The communication cost is
O(N). The security levels of session key and identity anonymity of the protocol are the
same as ours.
2. PRELIMINARIES
There is a system server S which has a set of users {U0, U1, …, UN-1}. Without loss of generality, we assume that the identity of user Ui is i. We arrange the users into an L × L rectangle such that user Ui is in row ix = ⎣i/L⎦ and column iy = i mod L, where N = L2. The server S shares a long-term password πi with each user Ui, 0 ≤ i ≤ N − 1. Assume that each password is drawn from a dictionary according to a distribution Dπ. An APAKE protocol is executed by S and a user Ui. Each execution of the protocol is called a ses-sion.
2.1 Adversaries
An adversary A is a probabilistic Turing machine. We consider two types of adver-saries. For security of identity anonymity, the adversary is the server S who wants to fig-ure out who he is talking to. This adversary is semi-honest, which means that it follows every step of the protocol, but does extra computation in order to retrieve the user’s iden-tity. For security of session keys, the adversary is an active outsider, who can remove, modify, or inject messages during an execution of the protocol.
The possible attacks of an adversary are modeled by the following three oracles. − Execute(Ui, S). This oracle models the eavesdropping (passive) attack. By issuing an
Execute(Ui, S) query, the adversary initiates a new and genuine session s between Ui and S and gets the transcripts of s.
− Send(s, C, m). C is either the server S or a user Ui. This oracle models an active attack. It returns the response message of C when C on session s receives message m.
When the adversary wants to start a fake session s for C, it executes Send(s, C, “start”) oracle and gets the first message responded by C for the session s.
− Reveal(s). This oracle models the misuse of the session key by some party in the ses-sion. It returns the session key of a genuine session s if the session key of s has ever been established.
by the server S and a user Ui and a fake session involves an adversary who intends to impersonate. The adversary can inject false or modified messages into a fake session by
Send queries. He tries to trick S or Ui to accept him, or to obtain information about the session key.
We require the Reveal oracle work for genuine sessions. The goal of a fake session is for impersonation. If the adversary successfully impersonates in a fake session, he has already had the session key. If the adversary fails to impersonate in a fake session, there will be no common session key between the adversary and the other party. Thus, there is no point to ask the other party to reveal his session key for this fake session.
2.2 Hard Problems
Let G be a cyclic group and g be a generator of G. The CDH problem is to compute
gxy from given gx and gy. Let
, ( )
cdh
g G t
Succ be the best probability that a t-time bounded Turing machine solves the CDH problem. The CDH assumption is that the probability
, ( )
cdh
g G t
Succ is negligible for any polynomial-time t.
Let G and G1 be two cyclic groups of order n = q1q2, where q1 and q2 are large
primes with bit length λ. Let g be a generator of G and e: G × G → G1 be a bilinear map.
The subgroup decision (SD) problem is to determine whether an element x ∈ G is order
q1 or n without knowing the factoring of n. Let Advsdn ( )t be the greatest advantage
among all t-time bounded Turing machines solving the SD problem. The SD assumption is that no probabilistic polynomial-time Turing machine can solve the SD problem with a non- negligible probability.
2.3 The BGN Cryptosystem
Our protocol uses the BGN cryptosystem [5], which is semantic secure if the SD assumption holds. The BGN cryptosystem has the properties of additive and one-time mul- tiplicative homomorphisms. These properties are important for our construction. The following is a brief description of the BGN cryptosystem. It has two encryption functions
E and E1 that work over G and G1 respectively.
− KeyGen(1λ): Given a security parameter λ, the tuple (n, g, G, G1, e) is generated such
that the tuple is the parameters for the SD problem in section 2.2 and the length of q1,
q2 is λ bits. We choose another generator g′ of G and compute h = (g′)q2. Then, the
pub-lic key is pk = (n, g, h, G, G1, e) and the secret key is sk = (q1, q2).
− E(pk, m): Choose a random number r ∈ Z*
n and compute the ciphertext C = gmhr, where m ∈ {0, 1, …, q2 − 1}. For practicality, the message space should be small enough.
− D(sk, C): Compute C′ = C q1 = (gmhr)q1 = (gq1)m and then exhaustively search m from g q1 and C′.
− E1(pk, m): Choose a random number r ∈ Z*n and compute the ciphertext C = e(g, g)m⋅ e(g, h)r, where m ∈ {0, 1, …, q
2 − 1}.
− D1(sk, C): Compute C′ = Cq1 = (e(g, g)m ⋅ e(g, h)r)q1 = (e(g, g)q1)m and then exhaustively
search m from e(g, g)q1 and C′.
E(pk, m1) ⋅ E(pk, m2) = gm1hr1 ⋅ gm2hr2 = gm1+m2hr1+r2,
which is an encryption of m1 + m2. Similarly, E1 is additive homomorphic.
The encryption E is multiplicative homomorphic. However, the multiplication of two messages can be executed once only. The execution result of message multiplication is a ciphertext over G1. Although we can continue to perform message addition over G1,
no more message multiplication is possible. The message multiplication is as follows. For two ciphertexts C1 = gm1hr1 and C2 = gm2hr2 over G, we compute
1 2
1 2
( , ) ( , )r ( , )m m ( , ) ,r
C e C C= ×e g h =e g g ⋅e g h %
which is an encryption of m1m2 (over G1), where r is randomly chosen from Z*n and r% =
m1r2 + m2r1 + r1r2 loggh + r.
Modification for our setting. We add one parameter ω = e(g, g)q1 into the public
key. We assume that this addition does not affect the security of the BGN cryptosystem.
3. SECURITY REQUIREMENTS
An APAKE protocol ∏ should meet the following security requirements for authen-tication, anonymity and session keys (AKE security).
• Authentication An adversary A successfully impersonates as a user Ui if the server S
accepts a fake session s and establishes a common session key s with A for session s. Similarly, an adversary A successfully impersonates as the server S if any user U who interacts with A accepts and establishes a common session key for a fake session s. Let
SuccS-auth(A) (SuccU-auth(A), resp.) be the probability that S(U, resp.) accepts and
estab-lishes a se be the advantage that A guesses Reveal(s) correctly (determining whe ssion key with A. We say that ∏ is (t, ε)-secure for authentication if for any t-time bounded adversary A, both SuccS-auth(A) and SuccU-auth (A) are less than ε.
• Anonymity Let ViewS(Ui) be the view of S for an interaction session with user Ui. We
say that ∏ meets the security of anonymity if for any 0 ≤ i, j ≤ N − 1, and any polyno-mial-time bounded server S, ViewS(Ui) and ViewS(Uj) are polynomially
indistinguish-able.
• AKE security The AKE security is defined by the AKE game. The adversary is al-lowed to query Execute(S, Ui), Send(s, C, m) and Reveal(s) oracles for collecting
in-formation. At the end, A queries the Test(s) oracle which returns either a session key of s or a random number with equal probability, where s is a fresh and genuine session between the server S and a user Ui. By a fresh s, we mean that Reveal(s) is never
que-ried by A. Let Advake(A)ther it is a real session key or a random number.) We say that
∏ is (t, ε)-AKE-secure if for any t-time bounded adversary A, Advake(A) < ε.
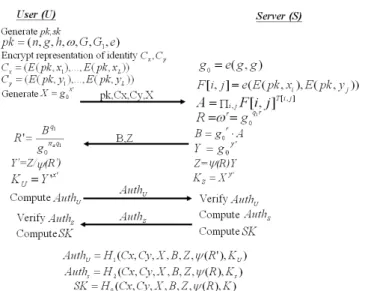
4. OUR APAKE PROTOCOL
The main idea of our protocol comes from symmetric private information retrieval (SPIR) in which a user looks up some data from a server’s database, but does not reveal
which data he selects. On the other hand, the server does not want the user to learn other data.
In our protocol, a user uses his identity as the chosen index to retrieve the corre-sponding password stored in the server. The passwords stored in the server are re-ar- ranged in an L × L table T, such that the password πi of user Ui is in row ix = ⎣i/L⎦ and
column iy = i mod L, i.e. T[ix, iy] = πi. The identity sent by the user is encrypted and the
retrieved data is encrypted also (i.e. the corresponding password is in encrypted form). To prevent the user from obtaining a password that does not belong to him, the server adds a random value to the retrieved data before sending the encrypted data back to the user. Thus, only the valid and as-claimed user can use his password to get the random value from the retrieved data. This random value is needed for computing the session key.
Let ψ be a hash function from {0, 1}l to G
0, and H0, H1, H2 be hash functions from
{0, 1}* to {0, 1}l for some positive integer l, which are the public parameters of the
sys-tem. The user Ua with the password πa can be anonymously authenticated by S by
exe-cuting our APAKE protocol described as follows. 1. Ua does the following:
• Generate the key pair (pk, sk) and give a zero knowledge proof φ1 for validation of the
key pair1, where pk = (n, g, h, ω, G, G
1, e) and sk = (q1, q2) such that every element in
G1 can be expressed as a l-bit string.
• Represent the identity a by two indicator bitstrings (x0x1 … xL-1) and (y0y1 … yL-1) of
row position ax and column position ay respectively. Denote the representation as
βa = (x0x1 … xL-1, y0y1 … yL-1)2.
• Encrypt each bit of (x0x1 … xL-1, y0y1 … yL-1) as
Cx = (E(pk, x0), E(pk, x1), …, E(pk, xL-1)),
Cy = (E(pk, y0), E(pk, y1), …, E(pk, yL-1)).
We use zero knowledge proofs φ2 to guarantee the format of the encrypted identity
rep-resentation3.
• Compute X = e(g, g)x′, where x′ ∈ Z
n is randomly selected.
• Send (pk, Cx, Cy, X, φ1, φ2) to S.
2. After receiving (pk, Cx, Cy, X) from Ua, S does the following:
• Verify correctness of φ1 and φ2.
• Compute an L × L (filtering) table F, where F[i, j] = e(E(pk, xi), E(pk, yj)) = E1(pk, xiyj),
for 0 ≤ i, j ≤ L − 1. We see that F[i, j] = E1(pk, 1) if and only if both xi and yj are 1.
There is exactly one E1(pk, 1) in F.
• Compute A = ∏i,j F[i, j]T[i, j] = E1(pk, T[ax, ay]) = E1(pk, πa), for 0 ≤ i, j ≤ L − 1.
1 For the validation of the key pair, we consider that the validation of the RSA modulus n should be proved [8]. 2 For example, N = 25 the representation of a = 18 would be β
18 = (00010, 00010), where the row position 18x
= 3 and column position 18y = 3.
3 For each ciphertext, it should be proved that the plaintext is either 0 or 1 [10]. After all ciphertexts are proved as bit-encryptions, the product of all ciphertexts in Cx should be proved as an encryption of bit as well as the
product of all ciphertexts in Cy. Totally, it costs L + 2 zero knowledge proofs for bit encryptions to prove the
validation of the format. From [10], each zero knowledge proof for bit encryption consists 3 elements in G and the proof is non-interactive.
• Randomly select y′, r ∈ Zn and compute B = e(g, g)r ⋅ A = E1(pk, πa + r), R = ωr and Z =
ψ(R) ⋅ e(g, g)y′.
• Compute KS = Xy′.
• Send (S, B, Z) to Ua.
3. After receiving (S, B, Z) from S, Ua computes R′ = Bq1/e(g, g)πaq1, Y′ = Z/ψ(R′), and KU
= Y′x. Compute the authenticator Auth
U = H1(pk, Cx, Cy, X, S, B′, Z, ψ(R′), KU). Send
AuthU to S.
4. After receiving AuthU from Ua, S does the following
• Check whether
AuthU = H1(pk, Cx, Cy, X, S, B, Z, ψ(R), KS). If they are matched, then S accepts Ua and
computes the session key
SK = H0(pk, Cx, Cy, X, S, B, Z, ψ(R), KS).
Otherwise, S rejects and terminates.
• Compute AuthS = H2(pk, Cx, Cy, X, S, B, Z, ψ(R), KS) and send AuthS to Ua
5. After receiving the authenticator AuthS, Ua does the following:
• Check whether
AuthS = H2(pk, Cx, Cy, X, S, B, Z, ψ(R′), KU). If they are matched, set
SK = H0(pk, Cx, Cy, X, S, B, Z, ψ(R), KU). Otherwise, Ua rejects and terminates.
To revoke a user Ui, S resets the password πi to a secret value ⊥, which is unknown
to all users. The revoked user has no valid password anymore. To add a user Uj, S sets the
corresponding entry as πj in his id-password table T.
4.1 Correctness and Security
In this section, we show correctness and security of our protocol. First, correctness is shown in the following theorem.
Theorem 1 After execution of the protocol by both honest parties, a user Ua with the
correct password πa can establish a common session key SK with S.
Proof: In the execution of the protocol, Ua has the password π = πa, we can see that R′ =
(B/(e(g, g))π)q1 = R and Y′ = Z/ψ(R′) = Z/ψ(R) = e(g, g)y. Thus K
U = Y′x = e(g, g)xy = Xy =
KS. Therefore, authenticators are matched and then U can establish the session key SK
with S.
AKE security/Authentication Our protocol can achieve mutual authentication. Briefly
speaking, only the user who knows the correct password can extract R out from B and then extract e(g, g)y from the message Z. Therefore, only the user can compute the same
key KU = (e(g, g)y)x as the one KS computed by the server. On the other hand, only the
server who knows e(g, g)π can compute the key KS such that KS is the same as KU.
For the requirements of AKE security and authentication, our protocol can against off-line dictionary attack. The number of Reveal-queries can be dominated by the num-ber of Execute-queries, since the Reveal oracle only works for the genuine sessions.
The AKE security is independent of the security of the BGN’s cryptosystem. For an adversary who is an outsider of a session, the AKE security still holds even if the adver-sary gets the secret key used in the session. Informally, the reason is that the adveradver-sary is without neither a password table nor the password of the known identity (he can compute by the secret key). Without the password for the identity and the password table, the ad-versary with sk can not compute R and also the key KU or KS. For clarity, we put the proof
details in the appendix.
Theorem 2 Suppose that our APAKE protocol is run with the password distribution Dπ.
For any adversary A with a time bound t with less than qsSend-queries, qeExecute-
que-ries, qg hash queries to ψ, and qh hash queries to {H0, H1, H2}, we have
0 1 0 1 0 1 2 2 2 , 2 2 - 2 , 2 - 2 , 6( ) 4 6( ) ( ) 18 ( ) 24 ( 2 ) , 2 ( ) ( ) ( ) 3 ( ) 4 ( 2 ) , 2 ( ) ( ) 3 ( ) 4 ( 2 ) 2 g ake s cdh s e s h g G e l g S auth s cdh s e s h g G e l C auth s cdh s e s h g G e l q q q q q q t n n q q q q q q t n n q q q q q t n π π π τ τ τ + ≤ + + × + + + + ≤ + + × + + + + ≤ + + × + + Adv Succ Succ Succ Succ Succ A D A D A D 2 ( ) , g q n +
where τe is the computational time for an exponentiation in G1, g0 = e(g, g) is a generator
in G1 and Dπ(τ) is denoted for the probability of the most probable set of τ passwords.
Anonymity Here we show that the server cannot distinguish the views of interacting
Table 1. Comparison.
Computation of user Computation of server Communication round
Ours (4 N+4)ρ (N + 3)ρ + Nδ O N 4 ( )
[14] 4ρ (2N + 2)ρ O(N) 3
* Computation cost is measured in the number of modular exponentiation and the number of pairing denoted as ρ and δ respectively.
Theorem 3 Our APAKE protocol is anonymous against the semi-honest server if the
BGN’ cryptosystem is semantic secure.
Proof: Assume that the server S can distinguish two transcripts from two users Ua and Ub
with advantage ε. Then we can use S to break the semantic security of the BGN’s crypto-system with advantage ε.
Let {pka, Cxa, Cya, X′, AuthUa}, {pkb, Cxb, Cyb, X″, AuthUb} be transcripts of Ua, Ub.
Since both users have the correct passwords and AuthUa, AuthUb are generated by the
ran-dom oracle H1, the server S can not gain information from the authenticators. The
distri-butions of X′ and X″ are identical. Since pk is chosen randomly and independent of the users, pka and pkb are identically distributed. The only place where can be used for
dis-tinguishing is the encrypted identity representation. If the server can distinguish the en-crypted identity representation, we can use the server to break the semantic security of the BGN’s cryptosystem as follows.
Let the ith, jth bits of indicator bitstrings of row positions ax and bx be different, and
the kth, sth bits of the indicator bitstrings of column positions ay and by be different. That
is, 0 2 2 0 2 2 0 2 2 0 2 2 ( ... ... ..., ... ... ...), ( ... ... ..., ... ... ...), a i i j j k k s s b i i j j k k s s x x x x x y y y y y x x x x x y y y y y β β − − − − − − − − = = u u v v u u v v ,
where u= −1 u v, = −1 vfor ,u v∈{0, 1}. Set m0=u m, 1=u as the messages. The chal-lenge ciphertext is C = E(pk, mc) where c ∈ {0, 1}. If u = v, we set the encrypted identity
representation (Cx, Cy) as (E(pk, x0), …, E(pk, xi-2), E(pk, mc), E(pk, xi), …, E(pk, xj-2), E(pk, _ mc), E(pk, xj), …, E(pk, y0), …, E(pk, yk-2), E(pk, mc), E(pk, yk), …, E(pk, ys-2), E(pk, _ mc), E(pk, ys), …).
Otherwise, we set the encrypted identity (Cx, Cy) representation as (E(pk, x0), …, E(pk, xi-2), E(pk, mc), E(pk, xi), …, E(pk, xj-2), E(pk, _ mc), E(pk, xj), …, E(pk, y0), …, E(pk, yk-2), E(pk, _ mc), E(pk, yk), …, E(pk, ys-2), E(pk, mc), E(pk, ys), …),
where E(pk, _mc) = E(pk, 1)/E(pk, mc). If the server answers that the user is Ua, we output
0 as the answer to the semantic security game. If the server answers that the user is Ub,
we output 1 as the answer to the semantic security game. If c = 0, C = E(pk, m0) = E(pk,
u). Therefore, (Cx, Cy) is the encrypted identity representation of βa. If c = 1, C = E(pk,
m1) = E(pk,
_
probability 1/2 + ε to give a correct answer, we have probability 1/2 + ε to output c cor-rectly. The advantage of breaking the semantic security is thus ε. 4.2 Efficiency
The communication complexity of our protocol is dominated by (O N ciphertext ) size. Each encryption needs 2 modular exponentiations. The computation cost of a user is
( )
O N encryptions and 4 modular exponentiations in G1. The computation cost of the
server is N + 3 modular exponentiations in G1 and N pairing computation. The round
complexity of our protocol is 4.
We compare our result with the mutual authenticated version of [14] in Table 1.
5. DISCUSSION AND CONCLUSION
Our protocol is secure against the off-line dictionary attack. For the on-line diction-ary attack, the general solution is to limit the number of trials from a particular source, such as IP.
In this paper, we propose an anonymous password based key exchange protocol with sub-linear communication complexity, which is better than the previous result. It is interesting that how to achieve anonymity against the malicious server or how to achieve AKE security without the random oracle.
A Proof of Theorem 2
Proof: We define a sequence of games from the real AKE game G0 to the final game G5.
To bound the probability of the adversary winning in the real AKE game, we bound the probability in one of those games at first (specifically, game G3). Then we analyze the
differences between successive games.
Game G0: This is the real protocol in the random oracle model. We consider the
follow-ing three events”
• S0 (for semantic security), which occurs if the adversary can correctly guess the bit
used in the Test-query.
• SA0 (for S-authentication), which occurs if U accepts for a fake session.
• UA0 (for U-authentication), which occurs if S accepts for a fake session.
Advake(A) = 2Pr[S0] − 1
SuccS-auth(A) = Pr[SA0]
SuccU-auth(A) = Pr[UA0]
In each game Gi, we analysis the events SAi, UAi, and the restricted event RSi = Si ∧¬ SAi
Game G1: In this game, we simulate the hash oracles (ψ, H0, H1, H2) by maintaining lists
Λψ, ΛH, Λ′H (where the hash functions H′0, H′1, H′2 will appear in the Game G3). We also
simulate all real players would do for all queries (the Send-queries, the Execute-queries, the Reveal-queries and the Test-queries). From this simulation, the game is perfectly in-distinguishable from the real one.
Game G2: We cancel some games:
• collisions on the partial transcripts ((pk, Cx, Cy, X), (S, B, Z)). There is at least one
hon-est party involved in the transcription. Thus one of X or (B, Z) is truly uniformly dis-tributed.
• collisions on the output of ψ.
We denote the above events as Coll2 and bound the probability by the birthday paradox:
Pr[Coll2] 2 2 ( ) ( ) . 2 2 g e s q q q n n + ≤ +
GameG3: We compute the session key SK and the authenticators AuthS, AuthU using the
private oracles H′0, H′1, H′2 respectively.
AuthS = H′1(pk, Cx, Cy, X, S, B, Z) AuthU = H′2(pk, Cx, Cy, X, S, B, Z) SK = H′0(pk, Cx, Cy, X, S, B, Z)
Since the computations of SK and authenticators are without KS and KU, and the password
is not used anymore, we can simplify the rules as follows: • In step 2, S does the follows:
− randomly select r, ~r ∈ Zn and compute B = e(g, g)re(g, h)~r, − randomly select rz ∈ Zn and compute Z = e(g, g)rz.
The games G3 and G2 are indistinguishable unless some specific hash queries are
asked, denoted as AskH3, which can be split as the following events:
− AskH13: A queries H1(pk, Cx, Cy, X, S, B, Z, ψ(R), KS) or H1(pk, Cx, Cy, X, S, B, Z, ψ(R), KU) for some execute transcript ((pk, Cx, Cy, X, AuthU) (S, B, Z, AuthS)).
− AskH2w13: A queries H2(pk, Cx, Cy, X, S, B, Z, ψ(R), KS) or H2(pk, Cx, Cy, X, S, B, Z,
ψ(R), KU) for some execute transcript ((pk, Cx, Cy, X, AuthU) (S, B, Z, AuthS)), where
some user has accepted, but the event AskH13 didn’t happen.
− AskH0w123: A queries H0(pk, Cx, Cy, X, S, B, Z, ψ(R), KS) or H0(pk, Cx, Cy, X, S, B, Z,
ψ(R), KU) for some execute transcript ((pk, Cx, Cy, X, AuthU) (S, B, Z, AuthS)), where
some user has accepted and the server has accepted in some session, but the events
AskH13 and AskH2w13 didn’t happen.
ad-versary, then they can not be guessed by the adversary better than randomly guessing. In the similar way, the session key SK and a random value can not be distinguished by the adversary better than random guessing. That is
3 3 3 1 Pr[ ] , Pr[ ] , Pr[ ] . 2 2 2 s s l l q q A ≤ A ≤ RS = S U
To bound Pr[AskH3], We analyze the probability of the event AskHi happening in other game Gamei and the differences of Pr[AskHi] between those games.
Game G4: We embed a random Diffie-Hellman instance (P, Q) into the game. P is g0rp
for some rp ∈ Zn, and Q is g0rq for some rq ∈ Zn, where g0 = e(g, g) is a generator of G1.
The computational Diffie-Hellman problem is to compute the value g0rprq, denoted as
CDHg0,G1(P, Q).
• In step 1, U computes X by randomly selecting rx ∈ Zn and X = Prx. • We modify the oracle ψ:
For queries to ψ, randomly select rg ∈ Zn and output Qrg. We excluded the cases X = 1 and the output of ψ is 1. Therefore,
4 3
Pr[AskH ] Pr[AskH ] qg qs qe.
n n
+
− ≤ +
GameG5: We cancel some games in which the following conditions hold. For the same
partial transcript ((pk, Cx, Cy, X), (S, B, Z)), there exist two distinct elements R1, R2, such
that (Cx, Cy, X, S, B, Z, ψ(R1), K1), (Cx, Cy, X, S, B, Z, ψ(R2), K2) are both in ΛH. We
de-note this event as CollH5 and therefore, |Pr[AskH4] − Pr[AskH5]| ≤ Pr[CollH5].
Lemma 1 If for some partial transcript (pk, Cx, Cy, X, S, B, Z), there are two different
π1, π2 such that the following conditions hold
• 1 1 1 2 1 2 0 0 , . q q B B R R gπ gπ = =
• (pk, Cx, Cy, X, S, B, Z, ψ(R1), Ki) are both in ΛH for i = 1, 2. • Ki = CDHg0,G1(X, Z/ψ(Ri)) for i = 1, 2.
Then one can solve the computational Diffie-Hellman problem:
0 1
2
5 ,
Pr[CollH ]≤gh×Succcdhg G (t+τe).
Proof: Assume that there exist such π1, π2, then K1 = CDHg0,G1(X, Z/ψ(R1)), K2 = CDHg0,G1
(X, Z/ψ(R2)) where ψ(R1) = Qra, ψ(R2) = Qrb. Note that
As a result, we can have 0 1 1 , 2 ( , ) ( )u g G K CDH P Q K =
where u = (rx(rb − ra)-1. By random guessing two hash queries among qh queries, 0 1
2
5 ,
Pr[CollH ]≤gh×Succcdhg G (t+τe). To analysis Pr[AskH5], we divide AskH15 into three subcases.
• AskH1-passive5: In this case, both parties are simulated. Thus we have the following
lemma:
Lemma 2 If for some passive partial transcript (pk, Cx, Cy, X, S, B, Z), there exists (pk, Cx, Cy, X, S, B, Z, ψ(R), K), in ΛH, one can solve the computational Diffie-Hellman prob-lem:
0 1
5 ,
Pr[ 1 ] cdh ( 2 ).
h g G e
AskH −passive ≤g ×Succ t+ τ
Proof: Since both parties are simulated, X = Prx, Z = g
0rz, ψ(R) = Qrg. Thus one can have
K = CDHg0,G1(X, Z/ψ(R)) = P rz/CDH g0,G1(P, Q) rxrg and compute CDHg0,G1(P, Q) = (P rz/K)u where u = (rxrg)-1. • AskH1-WithS5: This event models the attack that an adversary wants to impersonate U
to S. To generate the authenticator, the adversary ask H1 for some ((pk, Cx, Cy, X, S, B, Z, ψ(R), K). Without any collision on ψ’s output, R is determined uniquely. Since Bq1 = R × g0πq1, π is determined uniquely. Thus each authenticator sent by the adversary can
only contain one password information. Pr[AskH1-WithS5] ≤ Dπ(qs)
• AskH1-WithU5: This event models the attack that an adversary wants to impersonate S
to U. To generate the authenticator, the adversary ask H2 for some ((Cx, Cy, X, S, B, Z,
ψ(R), K). Each authenticator sent by the adversary can only contain one password in-formation.
Now, we have
0 1
5 ,
Pr[AskH1 ]≤gh×Succcdhg G(t+2 ) 3τe + Dπ( ).qs
For the event AskH2w15, we can analysis the two sub-events AskH2w1-passive5 and
AskH2w1-With U5, since U has been authenticated by AuthU. The last event is AskH0w125,
which is AskH0w12-passive5 since U and S have been authenticated by AuthU and AuthS
respectively. As a consequence, we have
0 1
5 ,
Pr[AskH ] 3≤ gh×Succcdhg G(t+2 ) 3τe + Dπ( ).qs
Combining all the above equations, one can get the announced result.
Since the adversary is t time-bounded, the number of queries is polynomial bounded. Simulator simulates for hash queries, Send-queries, and Execute-queries. Answering the
Execute-queries is the most time-consuming among all kind of queries since the simula-tor needs to simulate the whole execution of the protocol. However, it still takes polyno-mial time. Therefore, the simulation is in polynopolyno-mial time.
REFERENCES
1. E. Modiano, “An adaptive algorithm for optimizing the packet size used in wireless ARQ protocols,” Wireless Networks, Vol. 5, 1999, pp. 279-286.
2. M. Abdalla and D. Pointcheval, “Simple password-based encrypted key exchange protocols,” in Proceedings of the 2005 Conference on Topics in Cryptology: The
Cryptographer’s Track at RSA, 2000, pp. 191-208.
3. M. Bellare, D. Pointcheval, and P. Rogaway, “Authenticated key exchange secure against dictionary attacks,” in Proceedings of Advances in Cryptology, 2000, pp. 139-155.
4. S. M. Bellovin and M. Merritt, “Encrypted key exchange: Password-based protocol secure against dictionary attacks,” in Proceedings of the IEEE Symposium on
Re-search in Security and Privacy, 1992, pp. 72-84.
5. S. M. Bellovin and M. Merritt, “Augmented encrypted key exchange: A pass-word-based protocol secure against dictionary attacks and password file compro-mise,” in Proceedings of the 1st ACM Conference on Computer and
Communica-tions Security, 1993, pp. 325-341.
6. D. Boneh, E. J. Goh, and K. Nissim, “Evaluating 2-dnf formulas on ciphertexts,” in
Proceedings of the 2nd Theory of Cryptography Conference, 2005, pp. 325-341.
7. V. Boyko, P. D. MacKenzie, and S. Patel, “Provably secure password authenticated key exchange using diffie-hellman,” in Proceedings of Advances in Cryptology, 2000, pp. 156-170.
8. E. Bresson, O. Chevassut, and D. Pointcheval, “New security results on encrypted key exchange,” in Proceedings of the 7th International Workshop on Theory and
Practice in Public Key Cryptography, 2004, pp. 145-158.
9. J. Camenisch and M. Michels, “Proving in zero-knowledge that a number is the product of two safe primes,” in Proceedings of Advances in Cryptology, 1999, pp.
107-122.
10. C. K. Chu and W. G. Tzeng, “Efficient k-out-of-n oblivious transfer schemes with adaptive and non-adaptive queries,” in Proceedings of the 8th International
Work-shop on Theory and Practice in Public Key Cryptography, 2005, pp. 172-183.
11. J. Groth, R. Ostrovsky, and A. Sahai, “Perfect non-interactive zero knowledge for np,” in Proceedings of Advances in Cryptology, 2006, pp. 339-358.
12. J. S. Hwu, R. J. Chen, and Y. B. Lin, “An efficient identity-based cryptosystem for end-to-end mobile security,” IEEE Transactions on Wireless Communications, Vol. 5, 2006, pp. 2586-2593.
13. S. Jiang and G. Gong, “Password based key exchange with mutual authentication,” in Proceedings of 11th International Workshop on Selected Areas in Cryptography, 2004, pp. 267-279.
14. V. Miller, “The weil pairing, and its efficient calculation,” Journal of Cryptology, Vol. 17, 2004, pp. 235-261.
15. D. Q. Viet, A. Yamamura, and H. Tanaka, “Anonymous password based authenti-cated key exchange,” in Proceedings of the 6th International Conference on
Cryp-tography in India, 2005, pp. 244-257.
Hsiao-Ying Lin (林孝盈) is currently a Ph.D. student in Department of Computer Science, National Chiao Tung Univer-sity, Taiwan. She received her B.S. degree in Computer Science and Engineering from National Sun Yat-Sen University, 2003; and M.S. degree in Computer Science from National Chiao Tung University, 2005. Her current research interests include applied cryptography and information security.
Wen-Guey Tzeng (曾文貴) received his B.S. degree in Computer Science and Information Engineering from National Taiwan University, Taiwan, 1985; and M.S. and Ph.D. degrees in Computer Science from the State University of New York at Stony Brook, USA, in 1987 and 1991, respectively. He joined the Department of Computer and Information Science (now, De-partment of Computer Science), National Chiao Tung University, Taiwan, in 1991 and works there till now. Dr. Tzeng’s current research interests include cryptology, information security and network security.