Performance Evaluation of the IEEE 802.11 based wireless multihop networks
全文
(2) ABSTRACT The IEEE 802.11 protocol is the most popular standard for local area network.. It is widely. assumed to be the lower layer protocol in testbeds and simulations for wireless multi-hop ad-hoc networks, although, it is not designed for multi-hop networks.. While it is used to support the. wireless multi-hop ad-hoc network, some serious interference problems happen, all which are derived from the MAC layer.. In this paper, we analyze the influence of RTS/CTS transaction and the binary. exponential backoff scheme in the wireless multi-hop ad-hoc networks.. Through the simulation. results, by turning RTS/CTS transaction on or off and by using the backoff scheme with the same contention window, we find that the performance of the multi-hop networks would improve.. 1. INTRODUCTION. Wireless multi-hop ad-hoc networks are required when a stationary communication infrastructure, such as a base station, does not exist or has been destroyed.. Nodes in this kind of the. networks communicate with each other through multi-hop wireless links.. At the same time, each. node has to act as a router: forwarding packets for other nodes.. As a consequence, many researches. focus on the design of dynamic routing protocols that can efficiently search routes between two communication nodes. Because media is a shared resource in wireless networks, controlling access to the media efficiently is a complicated task.. Many MAC layer protocols have been proposed.. MAC layer protocol is a popular MAC layer protocol.. IEEE 802.11. Therefore, many simulations and testbeds for. designing routing protocols both adopt IEEE 802.11 MAC layer protocol as the MAC layer protocol. However, IEEE 802.11 MAC layer protocol was not designed for multi-hop ad-hoc networks.. Thus,. in [1]-[3], the authors did not think that IEEE 802.11 MAC protocol could work well in multi-hop ad2.
(3) hoc networks.. At he same time, they showed that TCP instability problem and TCP unfairness. condition will occur when we use IEEE 802.11 MAC layer protocol as the MAC layer protocol in multi-hop ad-hoc networks.. In the first place, TCP instability problem in multi-hop wireless. networks can degrade the TCP throughput performance seriously.. In the second place, TCP. unfairness problem means that one TCP connection might be completely shut down even if it starts much earlier than the competing TCP traffic. Certainly, we want to reveal the problems but not to change IEEE 802.11 MAC layer protocol too much.. And we think that RTS/CTS transaction is one reason of these problems.. Accordingly,. in this paper, we present the results of the simulations with turning RTS/CTS transaction function off. In addition, the binary exponential backoff scheme always favors the latest successful node.. Than,. we attempt to change the backoff scheme with the binary exponential increase to the backoff scheme always with the same contention range.. Through the simulation results, we will comprehend that the. change of the backoff scheme has positive influence on instability problem.. In the end, we will. compare the simulation results in the conditions of one two-nodes session and one four-nodes session, with the simulation results in the condition of two three-nodes sessions.. And we will find whether. these two cases both suffer the unfairness problem or not.. 2. OVERVIEW OF IEEE 802.11 STANDARD. In 1997 the IEEE adopted the first standard for WLANs, IEEE Std 802.11-1997, and this standard was revised in 1999. wired LAN.. The IEEE 802.11 was designed to look and feel like any IEEE 802. Like any 802.x protocol, IEEE Std 802.11 defines a medium access control (MAC). sublayer, MAC management protocols and services, and three physical (PHY) layers.. It allows. multiple vendors to develop interoperable LAN products for the globally available 2.4 GHz industrial, scientific, and medical (ISM) band. 3.
(4) To accomplish the task of similarity to wired LANs, IEEE 802.11 is designed to the same interface as IEEE 802.3.. IEEE 802.11 operates under the IEEE 802.2 logical link control (LLC). sublayer, providing all of services required supporting that sublayer.. Using the IEEE 802.2 interface. guarantees that protocol layers above LLC need not be aware of the network that is actually transporting their data. The air link is the radio or infrared link between WLAN transmitters and receivers.. Because. WLAN transmissions are not confined to a wire, there may be concerns that the data carried by a WLAN is not private, not protected. broadcast for all to hear. mobility.. This concern is certainly valid; the data on a WLAN is. The other significant difference a WLAN has from a wired LAN is. This is both the source of the benefits of a WLAN and the cause of much of the internal. complexity. The goals of the IEEE 802.11 standard is to describe a WLAN that delivers services previously found only in wired networks, e.g., high throughput, highly reliable data delivery, and continuous network connections.. It specifies wireless connectivity for fixed, portable, and moving nodes in a. geographically limited area.. As in any IEEE 802.x standard such as 802.3 (CSMA/CD) and 802.5. (token ring), the 802.11 standard defines both the physical (PHY) and medium access control (MAC) layers.. However, the 802.11 MAC layer also performs functions that are usually associated with. higher layer protocols (e.g., fragmentation, error recovery, mobility management, and power conservation).. These additional functions allow the 802.11 MAC layer to conceal the unique. characteristics of the wireless PHY layer from higher layers. In 1999, at roughly the same time, the IEEE issued 802.11a and 802.11b.. These two standards. and the original IEEE Std 802.11 differ only in the physical layer of their architecture.. 4.
(5) 3. RELATED WORK. Over the past few years, lots of researches that related to wireless multihop ad-hoc networks have been concentrated on the topic of ad-hoc routing algorithms.. And the testbeds and simulation. environments respective of these algorithms adopt IEEE 802.11 MAC protocol as the protocol of MAC layer.. Although the IEEE 802.11MAC protocol is the standard for wireless LANs, it was not. designed for multihop networks.. Hence, in [1]-[3], the authors pinpointed the question: Whether the. IEEE 802.11MAC protocol is able to work well in multihop wireless ad-hoc networks?. In their. viewpoints, even thought 802.11MAC protocol could support some ad-hoc network architectures, it is not intended to support the wireless mobile ad-hoc network. serious problems in an IEEE 802.11 ad-hoc network. problems.. Just as they said, there still exist several. To sum up, we conclude two main types of. Full discussion will be presented in the next paragraph.. The first type of problems is about one-session self-interference. comes from the interaction of the nodes in the session. to one node failing to reach its adjacent node. in MAC layer.. And we find that this problem is always due. This triggers a route failure.. And the failure is rooted. The authors indicated that two problems in MAC layer cause the intermediated node. unable to reach its next hop. problem.. As it names, the interference. One of the two problems is collision, and the other is exposed station. And the latter one leads to RTS/CTS transaction.. When a single TCP session was. established with no background traffics in fixed nodes ad-hoc network environment, an expected steady throughput in the connection should be observed.. But, it does not seem to be the case.. Because intermediated nodes send RTS frames or respond CTS frames to their adjacent nodes, those adjacent nodes will defer when they are sending data traffics.. At the same time, the nodes, which. have one node between them and these intermediated nodes, will also defer.. Thus, the traffic of one. pair of nodes that does not interfere with the traffic of another pair of nodes will break off. As soon as one node in the session tries to contact its adjacent node and the number of successive failures 5.
(6) exceeds the value of the retry count, the MAC layer reports a link breakage.. And the node will. restart a route discovery procedure and simultaneously no data can be sent during this period. Usually, it causes a timeout in the TCP sender.. Then the TCP session has to wait until a route. becomes available again. When there are no other factors to influence the session in the simulation environment, the cause rooted in MAC layer of a session can also affect the throughput of a session itself.. It really makes us. to think that whether the IEEE 802.11MAC protocol is able to function well in multihop wireless adhoc networks.. So, in this paper, we will try to present that if we could have improvement on the. throughput of one session by means of adjusting some parameters in IEEE 802.11 standard. The second type of problems is about multi-session interference. presented the unfairness between two sessions.. In [1]-[3], the authors. The results showed that with the IEEE 802.11 MAC. layer protocol, simultaneous TCP traffic might suffer from severe unfairness, and even between connections with the same number of hops.. The authors of [1]-[3] presented that the reason of two-. session interference is still rooted in MAC layer by illustrating the multi-layer traces. two-node session and a three-node session for simulation.. They use a. In their simulation result, however, the. two-node session starts its communication latter, and it gains twice of throughput as one session and has stronger influence on throughput of the other. down to about zero.. Even, the throughput of the three-nodes session is. The result of their simulations is that, in a carrier sense wireless network, the. interfering range and sensing range are typically larger than that at which receivers are willing to accept a packet from the same transmitter.. When a node of three-node session sends a RTS frame to. its adjacent node in the same session, it may be unable to receive CTS frame because of the inference from the other two-node session.. No sooner does the node try to contact its adjacent node and the. number of successive failures exceeds the value of the retry count, than the MAC layer reports a link breakage.. Then it will restart a route discovery procedure.. 6. But the three-node session is almost.
(7) unable to gain any bandwidth at position where two sessions compete for the use of channel.. The. authors considered that the hidden node problem and the exposed node problem along with the exponential back-off scheme in MAC layer are the major reasons for this kind of problems.. This. kind of problems makes us to deliberate about that whether the IEEE 802.11MAC protocol is suitable for multihop wireless ad-hoc networks. Since IEEE802.11 MAC protocol does not work well for multihop wireless ad-hoc networks, we like to know whether adjusting some parameters of 802.11 MAC protocol can improve phenomenon described in [1]-[3].. The problems needed to be solved will be divided into two parts: one-session. and multi sessions.. Because we want to concentrate the variation of operation in MAC layer, we do. not have to adopt TCP as the transport layer protocol.. We simply function packet-relay in MAC. layer. From the experiments and conclusions of related researches, using RTS/CTS transaction in wireless ad-hoc networks will waste the bandwidth, which triggers a route failure, and the binary exponential backoff scheme will always favor the latest successful node.. Consequently, we could. infer that RTS/CTS transaction and backoff scheme might improve performance.. Thus, we intend to. analyze how RTS/CTS transaction has influence on wireless ad-hoc network with 802.11 MAC layer protocol.. By turning RTS/CTS transaction on or off, we could know that in which status the. performance will be better under different situations: one-session or multi-sessions.. And then, we. will also change the binary exponential backoff scheme to the backoff scheme with the same contention range to understand of whether the performance would become better or not.. In addition. to the factors described above, we will observe the variation of the throughput under different numbers of nodes in two-sessions network situation as well.. The following are the classification of our. simulation. In the first place, we focus on one-session network situation.. 7. We will simulate the session in.
(8) normal conditions, turning RTS/CTS transaction on and the backoff scheme with the exponential distribution.. Then, by turning RTS/CTS transaction off along with the exponential backoff scheme,. we will observe whether the performance of the session becomes better or not.. After these two. simulations, we change the backoff scheme from the exponential distribution to the union distribution. In the same way, we will simulate the two cases: one is to turn the RTS/CTS transaction on and the other is to turn the RTS/CTS transaction off.. That is the whole classification of the one session.. In the second place, we will simulate the multi-session conditions.. We use a two-node session. and a four-node session and observe the interference between them.. In the same way, we turn. RTS/CTS transaction on or off and change the binary exponential backoff scheme to the backoff scheme with the same contention range to have the results of four cases.. By making these changes. and analyzing these results, we can know what influences these factors have on this kind of the case. Furthermore, we attempt to know whether there are any differences between the two three-node multi-session conditions and the condition described in the preceding paragraph. RTS/CTS transaction and the backoff scheme as our variables.. We also adopt. Thus, we simulate four cases like the. cases in the last two paragraphs. Through analyzing the simulation results, we will be able to conclude that the causes of the problems are in the wireless ad-hoc networks with 802.11 MAC protocol.. We present our simulation. results and analysis in the next section.. 4. SIMULATION RESULTS. 4.1 Simulation Environment The results in this section are based on simulations using the OPNET network simulator.. 8.
(9) Optimized Network Engineering Tools (OPNET) is a comprehensive engineering system capable of simulating large communications networks with detailed protocol modeling and performance analysis. Our target network is a wireless multi-hop network. excluding the impact from outside.. We want to spotlight the performance. We adopt a string network topology with seven nodes (from. station 0 to station 6) just as shown in Fig. 4.1.. Because the link-failed problem, which is caused by. mobility, is not our main topic for discussion, those nodes are assumed to be static.. And the link. layer of the simulator implements the complete IEEE 802.11 standard MAC layer protocol DCF in order to accurately model the contention of nodes for wireless medium.. We want the same distances. between neighboring nodes to make sure that the nodes act on the par with themselves in the simulation.. Therefore, all nodes communicate with identical, half-duplex wireless radio links that. have a bandwidth of 1Mbps and also a normal transmission radius of 200m.. To allow a node only to. connect its neighboring nodes, we make the distance between any two neighboring nodes to 150m equally.. And only those nodes between which a communication line exists can communicate directly.. Moreover, we concentrate on the variation in MAC layer, and we do not have to adopt TCP as the transport layer protocol. Therefore, we simply function packet-relay in MAC layer.. When a node. receives a packet, its MAC layer just delivers the packet to the network layer and then the packet goes through the general packet-sending process again for sending to the next node. The packet size is kept at 1024 bytes and each node has a buffer, which is managed in a drop-tail fashion and can hold up to 256000 bits, for packets awaiting transmission.. In addition, the inter-. arrival time, the function of RTS/CTS transaction, and the type of distribution used in the backoff scheme are all under control.. Table 4.1 shows all the parameters used in our simulation.. Table 4.1 Parameters of simulation Topology rang. 2000 m * 2000 m. Packet size. 1024 bytes. Transmission rate. 1 Mbps. Buffer size. 256000 bits. Transmission range. 200 m. Max receive lifetime. 0.5 sec. 9.
(10) The range between nodes. 150m. The mean value of the inter-. controlled. arrival rate The function of RTS/CTS. On or Off. The distribution of the inter-. transaction. controlled. arrival rate. Fig. 4.1 Network topology.. 4.2 Simulation Result. 4.2.1. One seven-node session. We attempt to know whether turning RTS/CTS transaction off and changing the backoff scheme are helpful to solve the instability problem described in [2].. We simulated one seven-node session.. The source node is the station 0 and the destination node is the station 6. time of packets generated by the source node is constant. the packets which waited for transmission were infinite.. In addition, the inter-arrival. And we also assumed that the number of. The session started at 0 second.. Then, we will present the simulation results in the three cases.. The first case was still to turn. RTS/CTS transaction on with the binary exponential backoff scheme. RTS/CTS transaction off with the binary exponential backoff scheme.. In the second case, we turned In the last case, we turned. RTS/CTS transaction off, but made the contention ranges of the backoff scheme the same.. 10. Fig. 4.2 to.
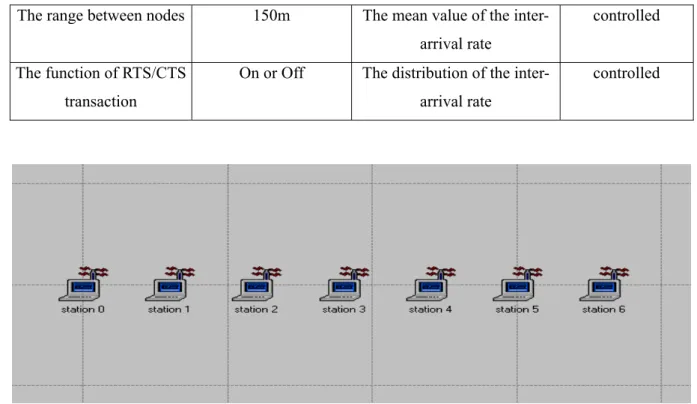
(11) Fig.4.7 following demonstrate the simulation results. We tried to control the load of the session by setting up the mean value of the inter-arrival time of the session.. Through simulating repeatedly, we found that the throughput began to descend when the. mean value was to the extent about 0.028. when the mean value was larger than 0.028.. As a consequence, the instability problem did not appear No matter whether we turn RTS/CTS transaction on or. off, this mean value at which the throughput began to descend was still the same.. Likewise, it was. also the same when the throughput began to down no matter we change the backoff scheme or not. Because the results of individual load in this condition are similar, we choose the result at high load as our represent: the mean value of the inter-arrival time equals to 0.01. First, we compared the results shown in Fig. 4.2 to Fig. 4.5.. And we can find that the. performance became better and better when we turned RTS/CTS transaction off.. Although RTS/CTS. transaction can decrease the probability of collision, it caused extra reservation of channel resource in. Fig. 4.2 RTS/CTS transaction on with the standard backoff (station 0 to 2).. Fig. 4.3 RTS/CTS transaction on with the standard backoff (station 3 to 6).. 11.
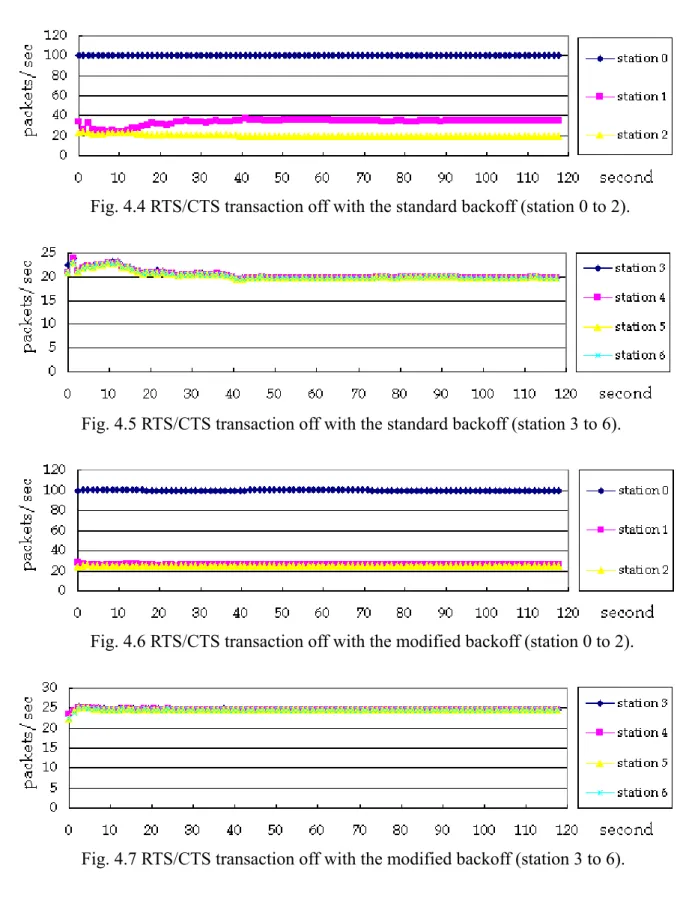
(12) Fig. 4.4 RTS/CTS transaction off with the standard backoff (station 0 to 2).. Fig. 4.5 RTS/CTS transaction off with the standard backoff (station 3 to 6).. Fig. 4.6 RTS/CTS transaction off with the modified backoff (station 0 to 2).. Fig. 4.7 RTS/CTS transaction off with the modified backoff (station 3 to 6). wireless multi-hop ad-hoc networks. load.. It made total performance decreasing tremendously under high. If we use the function, flow control, of TCP, the session would often be dropped.. 12. And once.
(13) the condition happens, the session would restart route discovery. cycle.. Then, it would lead to vicious. In our case, when the mean value of the inter-arrival time was smaller than 0.028, this. phenomenon would show up.. So, we can indicate that turning RTS/CTS transaction off can help out. the instability problem. In addition, we compared the results in Fig. 4.4 to Fig. 4.7.. We can find that the performance. improves when the backoff scheme used the same contention range through the simulations.. When. the backoff scheme used the same contention range, the station 1 has the same probability with the station 0 to send its packets to the station 2.. On the contrary, when the backoff scheme was in the. binary exponential increase, it favored the latest successful station.. In our case, the preceding station. had the larger probability than its next station when the backoff scheme was in the binary exponential increase.. Thus, we conclude that the performance would be a little better when the backoff scheme. used the same contention range.. 4.2.2. Two-node session and four-node session. In this section, we will present the interference between the two-node session and the four-node session. station 2.. In the two-node session, the source node is the station 1 and the destination node is the And in the four-node session, the source node is the station 6 and the destination node is. the station 3. constant.. In addition, the inter-arrival time of packets generated by the two source nodes is. We made the mean packet-generating value of the four-node session to be 0.029 to ensure. that this session would not inference itself.. And we let the four-node session started at 0 second; the. two-node session began 10 second later as well.. In the same way, we obtained the throughput in four. cases: RTS/CTS transaction on with the standard backoff scheme, RTS/CTS transaction on and the backoff scheme with the same contention range forever, RTS/CTS transaction off with the standard backoff scheme, and RTS/CTS transaction on and the backoff scheme with the same contention range. 13.
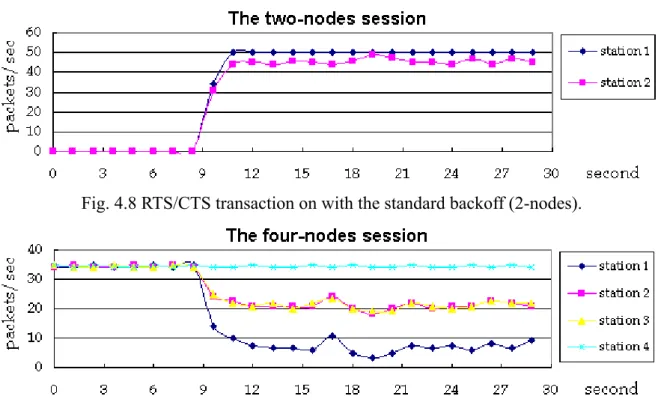
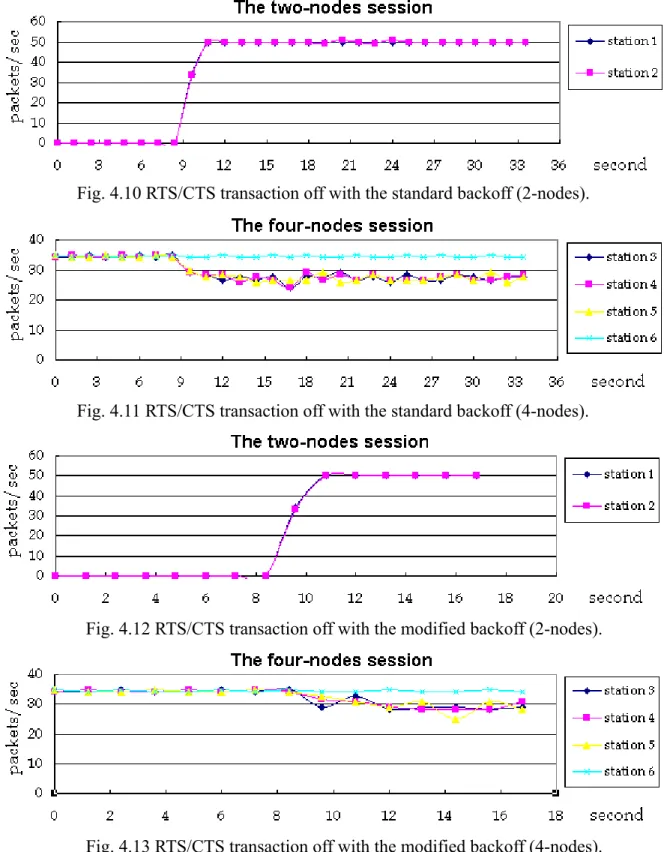
(14) forever.. Fig. 4.8 to Fig.4.13 following demonstrate the simulation results.. We control the load of the two-node session. station 1 are separately 0.05, 0.029 and 0.02 sec. of the multi-session conditions are similar. load.. The mean values of the inter-arrival times of. However, the results of individual load in this kind. As a consequence, we just present the result under high. From Fig. 4.8, we can find the unfairness between these two sessions.. When the two-node. session started to transmit packets, it got most resource of the channel and made the throughput of the four-node session down to zero.. It was just the unfairness phenomenon described in [1] and [3].. From Fig. 4.8 to Fig 4.11, we can find that these sessions, which did not turn the RTS/CTS transactions on, have better throughput than those, with the RTS/CTS transactions on. result is predictable.. Obviously, the. The traffic between the station 3 and the station 4 did not affect the traffic. between the station 1 and the station 2 when the station 1 was sending packets to the station 2.. Fig. 4.8 RTS/CTS transaction on with the standard backoff (2-nodes).. Fig. 4.9 RTS/CTS transaction on with the standard backoff (4-nodes).. 14. But,.
(15) Fig. 4.10 RTS/CTS transaction off with the standard backoff (2-nodes).. Fig. 4.11 RTS/CTS transaction off with the standard backoff (4-nodes).. Fig. 4.12 RTS/CTS transaction off with the modified backoff (2-nodes).. Fig. 4.13 RTS/CTS transaction off with the modified backoff (4-nodes). the RTS/CTS transaction made one of these two traffics to wait for the other. of the channel.. This caused the waste. In such an event, not only the throughput of the four-node session but also the. 15.
(16) throughput of the two-node session decreased, especially, when the station 1 was the source station. It made the station 2 to be able to get more resources of the channel when it contends with the station 3 under high load.. Accordingly, we conclude that the RTS/CTS transaction is not suitable in wireless. multi-hop ad-hoc network. But as for the backoff scheme, from Fig. 4.10 to Fig. 4.13, we found that this factor has little influence on the interference of these two sessions.. Therefore, we think that the backoff scheme of. one session just affects the session itself, like the effect of the backoff scheme we demonstrated at the preceding section.. 4.2.3. Two three-node sessions. In this section, we will the performance in normal case: no source nodes near the location where the interference exists.. We used two three-node sessions to simulate this kind of the case.. In the. first one session, the source node is the station 1 and the destination node is the station 3.. And in the. second session, the source node is the station 6 and the destination node is the station 4.. The inter-. arrival time of packets generated by the two source nodes is the exponential distribution.. In addition,. the mean packet-generating value of the second session is 0.035 to ensure that this session would not inference itself.. And the second session to start at 0 second; the first session began 10 second later.. We observed the throughput in four cases, whether turn RTS/CTS transaction on or not and whether the backoff scheme is with the binary exponential increase or in the same union backoff range forever.. We also controlled the load of the first session.. Then, we made the mean packet-. generating value of station 1 to be separately 0.05 and 0.035 second.. We chose these two values as. the loads of the first session because we attempted to observe the separate results whether the sessions were in the same loads or not.. We only show the results of the case, which the mean packet-. generating value is 0.05, in Fig. 4.14 to Fig. 4.19.. 16.
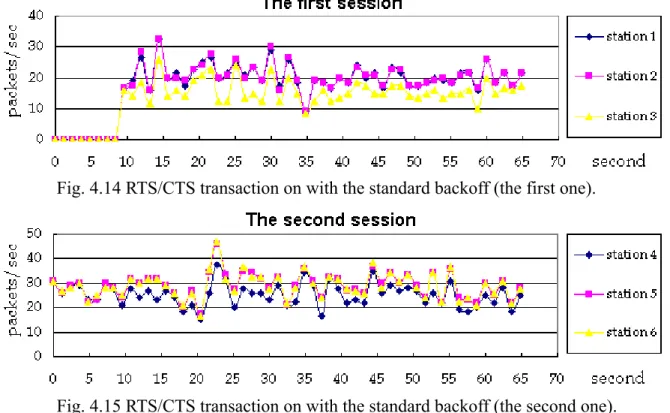
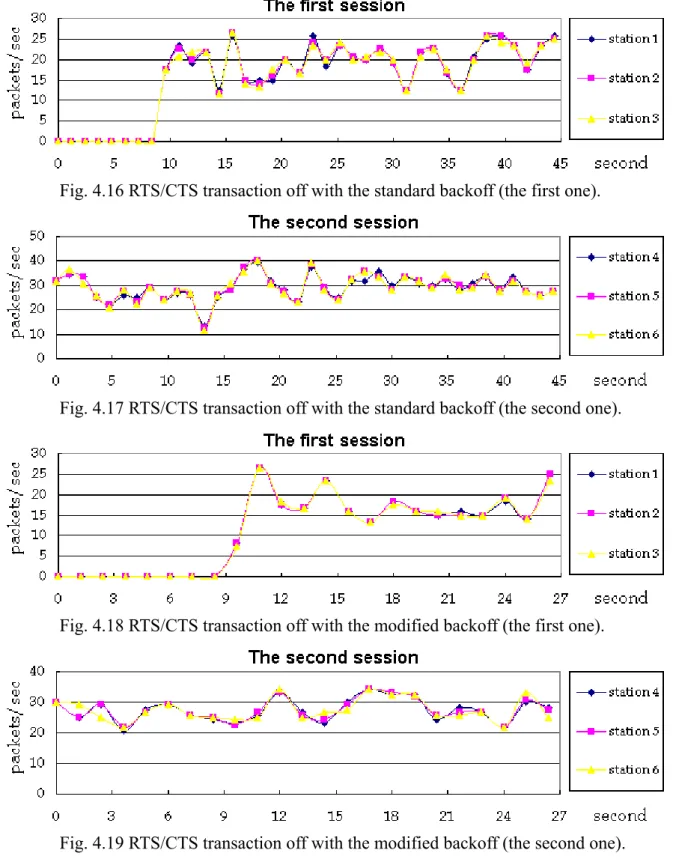
(17) At first, we considered if the unfairness condition indeed existed.. From the results shown in. Fig. 4.14 to Fig 4.19, we find that this condition did not appear in this kind of the case. see that it was reasonable.. It is easy to. Unlike the condition in the past section, these two sessions have to. contend the use of the channel in the same time.. Each of these two sessions did not have its source. node in the location where the interference may exist.. Consequently, RTS/CTS transaction did not. have influence strong enough on the contention between the station 3 and the station 4. we can compare the throughput under the different loads. station 4 shared the channel with the ratio of their load.. In addition,. We can find that the station 3 and the. It is the same as in a wired network.. And. this result made us ignore with the unfairness problem especially in the normal case. Although we know that the unfairness problem does not appear in the normal case by comparing the results shown in the preceding section and in this section so far.. We want to know whether the. Fig. 4.14 RTS/CTS transaction on with the standard backoff (the first one).. Fig. 4.15 RTS/CTS transaction on with the standard backoff (the second one).. 17.
(18) Fig. 4.16 RTS/CTS transaction off with the standard backoff (the first one).. Fig. 4.17 RTS/CTS transaction off with the standard backoff (the second one).. Fig. 4.18 RTS/CTS transaction off with the modified backoff (the first one).. Fig. 4.19 RTS/CTS transaction off with the modified backoff (the second one). performance would become better while we turn RTS/CTS transaction off.. These figures show that. the performance became better when the sessions proceed with no RTS/CTS transaction.. 18. With the.
(19) same reason in the past section, RTS/CTS transactions reserve unnecessary channel resource.. As a. matter of fact, it decreases the throughput a little. Admittedly, RTS/CTS transaction is helpful to avoid the collision.. In wireless multi-hop ad-hoc network, however, it may waste more channel. resource than what it saves.. Therefore, we think that RTS/CTS transaction is not a suitable function. in this kind of the condition. About the backoff scheme, from the simulation results, this factor did not affect the interference of these two sessions very much.. Because the binary exponential backoff scheme favored the latest. successful node, it just caused a little unfairness when the two sessions under different loads. Therefore, the backoff scheme of one session just affects the session itself.. This is the similar effect. of the backoff scheme we showed in the past two sections.. 5. CONCLUSIONS. In this paper, we have shown the influence of the RTS/CTS transaction and the standard backoff scheme on the performance in wireless multi-hop ad-hoc networks. with turning RTS/CTS transaction on or off. be with the same contention range forever.. We performed the simulations. We also simulated while making the backoff scheme to Then, we performed the simulations by controlling these. factors in the three cases: one seven-nodes session, one two-nodes session and one four-nodes session, and two three-nodes sessions. From the results of the simulation, we know that turning RTS/CTS transaction off will make the performance in wireless multi-hop ad-hoc network better, no matter which one of the case we simulated in. resource.. It is because RTS/CTS transaction caused unnecessary reservation of the channel. It decreases the total throughput.. The effect of RTS/CTS transaction wasting the channel. resource is larger than what the channel resource is reserved.. Among these three cases, the effect of. RTS/CTS transaction is more obvious in the multi-session cases. 19. This is reasonable.. Because of the.
(20) position of the two sessions, there was no serious interference between these two sessions. turning RTS/CTS transaction off was suitable in the cases.. Hence,. As a whole, turning RTS/CTS transaction. off is good for the performance. As for the backoff scheme, through the simulation results in case one, we observed that making the backoff scheme with the same contention range can only improve the situation of the instability problem.. But, it did not have any benefits to the unfairness problem.. Furthermore, we compared the simulation results of the two multi-session cases. find that the unfairness problem did not appear in the third cases. happened when there are source nodes near the contention position.. And we can. The unfairness problem just. So, we do not need to deal with. the unfairness problem.. REFERENCES [1]. S. Xu, T. Saadawi.. Does IEEE 802.11 MAC Protocol Work Well in Multi-hop Wireless Ad Hoc. Networks? IEEE Communication Magizine, Vol. 39, No.6, June, 2001, pp. 130-137. [2]. S. Xu, T. Saadawi.. Revealing and solving the TCP instability problem in 802.11 based multi-. hop mobile ad hoc networks.. Vehicular Technology Conference, 2001.. VTC 2001 Fall.. IEEE VTS 54th, Vol. 1, 2001, pp. 257-261. [3]. S. Xu, T. Saadawi. networks.. Revealing TCP unfairness behavior in 802.11 based wireless multi-hop. Personal, Indoor and Mobile Radio Communications, 2001 12th IEEE International. Symposium, Vol. 2, pp. E-83-E-87. [4]. Cali, F., Conti, M. and Gregori, E... IEEE 802.11 protocol: design and performance evaluation. of an adaptive backoff mechanism.. Selected Areas in Communications, IEEE Journal, vol. 18. issue: 9, pp. 1774 -1786, Sept. 2000. [5]. Bob O’Hara and Al Petrick. Information Network.. THE IEEE 802.11 handbook: a designer’s companion, Standards. IEEE Press, 1999.. 20.
(21)
數據

相關文件
A factorization method for reconstructing an impenetrable obstacle in a homogeneous medium (Helmholtz equation) using the spectral data of the far-field operator was developed
A factorization method for reconstructing an impenetrable obstacle in a homogeneous medium (Helmholtz equation) using the spectral data of the far- eld operator was developed
You are given the wavelength and total energy of a light pulse and asked to find the number of photons it
In this paper, we build a new class of neural networks based on the smoothing method for NCP introduced by Haddou and Maheux [18] using some family F of smoothing functions.
volume suppressed mass: (TeV) 2 /M P ∼ 10 −4 eV → mm range can be experimentally tested for any number of extra dimensions - Light U(1) gauge bosons: no derivative couplings. =>
incapable to extract any quantities from QCD, nor to tackle the most interesting physics, namely, the spontaneously chiral symmetry breaking and the color confinement..
• Formation of massive primordial stars as origin of objects in the early universe. • Supernova explosions might be visible to the most
The difference resulted from the co- existence of two kinds of words in Buddhist scriptures a foreign words in which di- syllabic words are dominant, and most of them are the