IEEE Region 10 Confennoe, Tencon 92 11th
-
13th November, 1992 Melbourne. AustraliaTraffic Modeling for Mobile Cellular Systems
Le-Pond Chin
and
Jin-Fu
Chang'
Electrical Engineering Department
National
Taiwan
University
Taipei, Taiwan
10764
Abstract
In this paper traffic modeling for mobile cellular systems is discussed. To reflect reality, hand-offs from and to adjacent cells are included in the model. Performance measures such as channel throughput and call blocking probability are derived through approximation. Compare with simulation, the approximated results show very good degree of accuracy.
1
Introduction
In the past few years, mobile communications have received considerable attention from people of various professions. As far as research is concerned, there have been works done in channel characterization e.g.[1]-[2], modulation and coding techniques e.g.[3]-[5], frequency assignment e.g.[6]-[8], and channel access techniques e.g.[9]-[ll].
Performance evaluation of a mobile communication system requires first reasonable and practical traffic modeling. Within any specific cell, there are basically three types of mobiles: active, registered and idle. An active mobile is a mobile who is currently occupying a voice channel and communicating. A registered unit is the one whose transceiver has been switched on and is ready to receive any possible incoming call or to initiate a call request. An idle mobile is a mobile whose equipment is currently powered off.
A
mobile of any of these three types can freely enter or leave a cell. An active mobile must follow a hand-off procedure to enter an adjacent cell from the cell it is currently residing. Hand-off is a very important design issue in mobile communication systems. Taking hand-off traffic into account, so far there are not too many studies on the performance evaluation of a mobile communication system'Correspondence Addressee
91
reported in the literature. The works reported in [lO]-[11] are two of the very few stduies and have laid a good foundation for performance evaluation of a mobile communication system to include the effect of hand-off traffic. We shall in this paper continue the prior effort and propose another traffic model for mobile communication system. Our approach is to divide the users into three types, i.e., active, registered, and idle, as we have mentioned in the above. The inclusion of idle users in the model would help to reflect the real situation since users having returned to workplace or residence no longer need to keep their handsets on. There are also users who switch on their phonesets only when they wish to communicate.
2
System
Model
Suppose we are working with a system in which each cell is given C channels to carry voice communications. Suppose all the voice signals are digitized and packed into constant length parcels called cells or packets. In order to efficiently transport these voice packets we slice the channel time of each channel into fixed length slots and the transmission of each voice packet consumes exactly one slot. We further assume that all the channels operate synchronously in such a way that slot boundaries in different channels are synchronized. A voice communication once granted a channel shall occupy the channel till it is finished.
We shall observe the system behavior at slot boundaries. At the end of a specific time slot we assume that an active user will need a hand-off to a neighboring cell with probability a h , will finish communication and become registered with probability a,
,
and will remain in the cell and continue to be active with probability a, = 1-
a h-
a,. A registered user will initiate a call request with probabilityB,,
will became idle with probabilitypi,
and will move to a neighboring cell with probability,&.
When a registered mobile moves to an adjacent cell it is treated as an idle unit in the new cell and has t o register again if it wishes to remain in registered state. Likewise for an idle mobile it will become registered with probabilityy T , will remain idle in the same cell with probability 7;
,
and move t o an adjacent cell with probability Y h . We use N.,N,,
andN;
to denote the number of active, registered, and idle mobiles in a cell.Should an active user handed over from an adjacent cell find no channel available in the new cell, hand-off blocking occurs and the call is discontinued and dropped. The blocked mobile then changes its status from active to registered. Similarly, if a newly initiated call request can not be accommodated, it is rejected. Let Nh denote the number of active mobiles handed off from neighboring cells in a time slot, we assume Nh follows Poisson distribution with mean
h
.
LetNj,
denote the number of idle users migrated from neighboring cells, we also assume thatNi,
is Poisson distributed with meanA .
Using our proposed model, we have derived through approximation results such as system utilization, hand-off blocking probability, and new call rejection rate. Due to the restriction on the length of a submitted paper, we have no space to include the mathematical treatment in this paper. People instersted in the derivation of these results can contact us for a complete copy of the manuscript.
3
Numerical Examples and Discussions
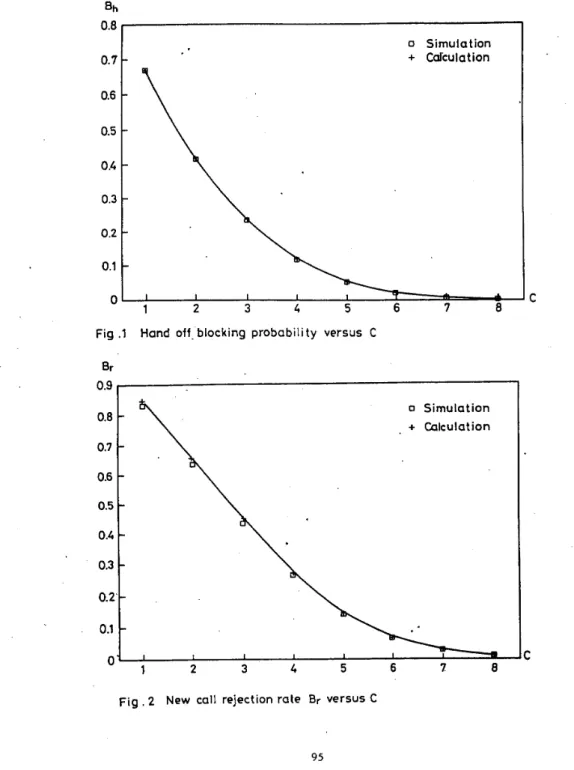
Shown in Figs. 1-2 are the numerical examples obtained from the results we derived. We also conduct computer simulations based on our assumptions stated in Sec. 2 to see how accurate that our appoximated analysis can offer. We witness in Figs. 1-2 that the accuracy is extremely good. The parameters used in these examples are a h = 0.006,a, = 0.3,h =
0.02,pa = 0.4,
A
= 0.02,Ph = 0.005,yh = 0.004,yi = o.l,TT = 0.5.Fig. 1 plots hand-off blocking probability Bh versus C while Fig. 2 plots local call rejec- tion rate
B,
versus C. The way that Bh and B, behave against C is intuitively reasonable. Figs. 1-2 can be used in determining the number of channels needed in a cell in order to satisfy our requirements on Bh andB,.
Once C is determined, we can then compute 9. For example suppose if B h = 0.01 andB,
= 0.02 then C = 5 and 71 = 0.68.Furthermore when C is determined, we can also calculate the number of customers in a cell. Base on this we can then determine for example cell size.
References
[l]
R.
C. French, “The effect of fading and shadowing on channel reuse in mobile ra- dio,”IEEE Trans. on Vehicular Technology, vol. VT-28, pp. 171-181, Aug. 1979.[2]
G.
K.
Chan, “Propagation and coverage prediction for cellular radio systems,”IEEE
Trans. on Vehicular Technology, vol. VT-40, pp. 665-670, Nov. 1991.[3] Y. Akaiwa and Y. Nagata, “Highly efficient digital mobile communications with linear modulation method,” IEEE J. Selected Areas in Communications, vol. SAC-5, pp. 890- 895, June 1957.
[4] Y. Yamano, S. Saito,
H. Suzuki and T.
Nojima, “Performance of x/4QPSK transmission
for digital mobile radio applications,” Proc.IEEE Globecom, pp.
12.6.1-12.6.5, Dallas,Tx,
NOV. 27-30, 1989.[5] A. Fukasawa,
T.
Sato, T . Yashida, andM.
Kawabe, “Adaptive error control scheme for high speed data transmission through a fading channel,” in 36th IEEE Vehicular Technology Conf., May 1986, pp. 256-261.[6]
D.
Cox andD.
Reudink, “A comparison of some channel assignment strategies in large scale mobile communication systems,” IEEE Trans. on Communications, vol. COM-20, pp. 190-195, Apr. 1972.[7] G. Falciaseca,
M.
Frullone, G. Riva, M. Sentinelli andA.
Serra, “Investigation on a dynamic channel allocation for high capacity mobile radio systems,” in 38th IEEE Ve- hicular Technology Conf., June 1988, pp. 176-181.[SI J. C-I. Chuang, “Autonomous adaptive frequency assignment for TDMA portable radio systems,” IEEE Trans. on Vehicular Technology, vol. VT-40, pp. 627-635, Aug. 1991. [9]
D.
J. Goodman, “Cellular packet communications,” IEEE Trans. on Communications,vol. COM-38, pp. 1272-1280, Aug. 1990.
[lo]
D.
Hong and S.S.Rappaport, “Traffic model and performance analysis for cellular mobile radiotelephone systems with prioritized and nonprioritized hand-off procedures,” IEEE Trans. on Vehicular Technology, vol. VT-35, pp. 77-92, Aug. 1986.[I 11 S.S. Rappaport, “The multiplecall hand off problem in high-capacity cellular commu- nication systems,” IEEE Trans. on Vehicular Technology, vol. VT-40, pp. 546-557, Aug. 1991.
Bh
0.8
0.7 0.60.5
0.4
0.3 0.2 0.1 0 2 3 56
7 8 1Fig .l Hand off. blocking probability versus C Br
0.9
I
ition I021
C
CF i g . 2 New call rejection rate Br versus