Contents lists available atScienceDirect
Pervasive and Mobile Computing
journal homepage:www.elsevier.com/locate/pmc
Review
From wireless sensor networks towards cyber physical systems
Fang-Jing Wu
a,
Yu-Fen Kao
b,
Yu-Chee Tseng
a,∗aDepartment of Computer Science, National Chiao Tung University, Hsinchu, 30010, Taiwan bDepartment of Information Management, Chung Hua University, Hsinchu, 30010, Taiwan
a r t i c l e i n f o Article history:
Received 28 July 2010
Received in revised form 22 March 2011 Accepted 29 March 2011
Available online 15 April 2011 Keywords:
Cyber physical system Internet technology Mobile ad hoc network Pervasive computing Sensing and actuation Wireless sensor network
a b s t r a c t
In the past two decades, a lot of research activities have been dedicated to the fields of
mobile ad hoc network (MANET) and wireless sensor networks (WSN). More recently, the cyber physical system (CPS) has emerged as a promising direction to enrich the interactions
between physical and virtual worlds. In this article, we first review some research activities in WSN, including networking issues and coverage and deployment issues. Then, we review some CPS platforms and systems that have been developed recently, including health care, navigation, rescue, intelligent transportation, social networking, and gaming applications. Through these reviews, we hope to demonstrate how CPS applications exploit the physical information collected by WSNs to bridge real and cyber spaces and identify important research challenges related to CPS designs.
© 2011 Elsevier B.V. All rights reserved.
Contents
1. Introduction... 398
2. Communication issues of WSNs... 399
2.1. Network formation... 399
2.2. Data gathering... 400
2.3. Query and reply processing... 401
3. Coverage and deployment issues of WSNs... 401
3.1. Coverage and connectivity solutions... 402
3.2. Energy-conserving and scheduling strategies... 402
3.3. Mobile sensor solutions... 402
4. Moving from WSN to CPS: applications and platforms... 403
4.1. Health-care applications... 404
4.2. Navigation and rescue applications... 405
4.3. Intelligent Transportation Systems (ITSs)... 405
4.4. Social networking and gaming applications... 406
5. Features and technical challenges of CPS... 406
5.1. Networking issues... 407
5.2. Cross-domain interference avoidance... 407
5.3. QoS and cloud computing... 407
5.4. Location-based services and beyond... 408
5.5. Monitoring services and beyond... 408
5.6. Security and privacy challenges... 408
6. Conclusions... 408
Acknowledgements... 409
References... 409
∗Corresponding author.
E-mail address:yctseng@cs.nctu.edu.tw(Y.-C. Tseng).
1574-1192/$ – see front matter©2011 Elsevier B.V. All rights reserved. doi:10.1016/j.pmcj.2011.03.003
1. Introduction
In the past two decades, wireless communication and network has been one of the fastest-growing research areas. Significant progress has been made in the fields of mobile ad hoc network (MANET) and wireless sensor networks (WSN) [1]. More recently, the cyber physical system (CPS) has emerged as a promising direction to enrich to-human, human-to-object, and object-to-object interactions in the physical world as well as in the virtual world. Apparently, CPS would adopt, and even nurture, the areas of MANET and WSN because more sensor inputs and richer network connectivity may be needed. It is thus desirable to review what has been developed in these fields, project what may happen in the field of CPS, and identify what needs to be researched further. This article intends to serve these purposes by identifying the unique features of WSN, raising some CPS critical examples, and then pointing out the future challenges of CPS. To build some foundations, we first review some existing results of WSN. This part is to provide some preliminaries of WSN and establish the necessary connections between WSN and CPS. It also helps identify key techniques in WSN which may be useful for CPS and foresee what issues need to be researched further in CPS.
MANET is made possible by the maturity of embedded computing technologies and wireless communication technologies. As a special form of MANET, WSN is further made possible by adopting more micro-sensing MEMS technologies, thus allowing more interactions between a network and its surrounding physical environment. Inertial motion sensing, environmental factor sensing, biosignal sensing, vehicle information sensing, and location sensing have all been widely discussed. In particular, many smart phones have included inertial sensors (e.g. accelerometer and e-compass) and GPS receivers as built-in components. Mobility, or known as mobile sensing, has been introduced to WSNs, thus opening up more opportunities to collect dynamic information from our daily life.
While MANET, WSN, and CPS are quite similar in many networking aspects, there are some major differences. Generally, MANET is for supporting ad hoc communications or extending the coverage of infrastructure networks [2]. WSN is designed particularly for delivering sensor-related data. CPS typically involves multiple dimensions of sensing data, crosses multiple sensor networks and the Internet, and aims at constructing intelligence across these domains. Below, we compare the features of MANET, WSN, and CPS.
1. Network formation: While the formation of a MANET is more likely to be random and can support node mobility, the formation of a WSN is typically field-specific and allows less mobility [3]. On the other hand, the networks of a CPS may cross several fields. Connecting these fields usually relies on the Internet. However, dynamic participation and departure of a sensor network is possible.
2. Communication pattern: A MANET usually supports arbitrary communication patterns, such as unicast, multicast, and broadcast, while a WSN involves more collective communications [4,5], such as convergecast and query-and-response transactions. Thus, the requirements on routing capability are different. CPS may invoke intra-WSN communications. Furthermore, cross-domain communications may happen quite frequently in CPS applications [6]. For example, in flood prevention applications, a group of water-level tracking sensors may need to cooperate with several groups of rain-meters to control the water gates of a dam.
3. Power management: While both MANET and WSN emphasize on energy saving, this is more critical for WSN because sensors are usually deployed in unattended areas [7]. Deeper sleeping modes and redundancy are preferred for WSN, whereas nodes’ sleeping behaviors in MANET are normally by opportunity. Activation of sensors in CPS is likely mission-oriented. For example, a dam control system may have a flood mode and a non-flood mode. Different modes may wake up different groups of sensors.
4. Network coverage: While a MANET only needs to meet some connectivity requirements, a WSN needs to meet both connectivity and some coverage criteria [8]. This leads to a lot of studies on the co-design of coverage and connectivity in WSNs. CPS imposes the same requirements for a WSN, but different levels of connectivity and coverage for different WSNs.
5. Node mobility: Node mobility in a MANET is usually arbitrary. Previously, little mobility has been assumed for a WSN [9,
10]. With the emerging mobile sensing applications, both controllable and uncontrollable mobility has been studied (such as data mule, opportunistic sensing, and vehicular sensing). In CPS applications, sensing data may be collected from static and mobile sensor nodes (such as those in vehicles, smart phones, etc.) with both controllable and uncontrollable mobility.
6. Knowledge mining: A MANET emphasizes only on networking issues. A WSN focuses more on collecting and managing sensing data. However, CPS emphasizes more on how to discover new knowledge across multiple sensing domains and to utilize intelligence properly. For example, a smart grid system [11] may involve power meters, micro-climate sensors, and wind and solar energy metering sensors to make intelligent energy distribution decisions.
7. Quality of services: Quality of data transmissions is essential for MANET, while quality of sensing data is important for WSN. CPS, however, emphasizes more on higher-level QoS, such as availability of networking and sensing data [12], security and confidentiality of sensing data [13], quality of knowledge/intelligence [14], etc.
By integrating WSNs from different domains, CPS represents one of the major driving forces that go beyond the cyber world toward the physical world [15]. Embedded computers and networks monitor and control physical processes, while vice versa physical processes affect the results of computations. Today’s embedding technologies have played key roles to enable rich interactions with real things in a nearly invisible way. Lots of data flows would occur between these two worlds.
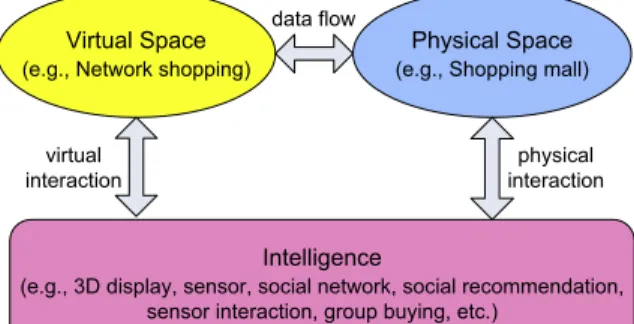
Fig. 1. Data flow and interactions in a CPS application.
On one hand, Internet and cellular networks do help to connect WSNs in distant regions and utilize their sensing data. Much intelligence is needed in future CPS applications. The concept is shown inFig. 1. Taking shopping as an example, a user may walk into a physical shopping mall, look at a set of dinning table and chairs, and wonder whether they would fit into her living room. On the physical space, she may immediately take some photos of the table and chairs. In the virtual space, the system may construct 3D models and use virtual reality techniques to place them (with proper sizes and colors) in her ‘‘virtual’’ living room. She may visualize this via intelligent 3D displays and use inertial sensors to relocate this furniture. Social networks may be involved to collect customers’ comments on the Internet. Her family members may participate in this process. Social recommendation systems may be invoked to suggest other items that may fit with this table (e.g., glassware, silverware, vase, etc.) with discount information. Clearly, a lot of intelligence and interactions are needed to support these scenarios.
Section2reviews some communication issues of WSNs. The coverage and deployment issues of WSNs are addressed in Section3. Then we move toward some application-driven designs of CPSs to discuss how to bridge the physical and the virtual worlds in Section4. We raise some current technologies for designing CPS and point out some future challenges in Section5. Conclusions are drawn in Section6.
2. Communication issues of WSNs
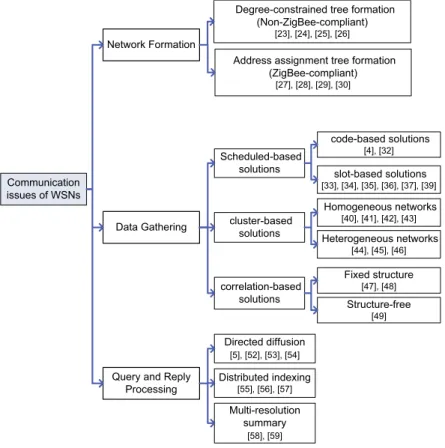
The design of a WSN emphasizes more on how it is formed and how sensing data is retrieved. Below, we discuss three fundamental operations of a WSN: (i) network formation, (ii) data gathering, and (iii) query and reply processing. A summary of these reviews is inFig. 2.
2.1. Network formation
Many WSN platforms have been developed recently, such as MICA, Imote2, and TelosB [16]. Several chip venders provide such solutions [17,18]. For inter-operability, ZigBee [19] and IEEE 802.15.4 [20] have been defined. Performance studies of these protocols are conducted in [21,22]. ZigBee relies on a distributed address assignment to form a tree network. Before forming a network, three parameters need to be specified: maximum number of children of a router (Cm), maximum number of child routers of a router (Rm), and the maximum depth of the network (Lm). Note that a child can be a router or an end device, so Cm
≥
Rm. Such a tree can also be used in a mesh network as a backbone for basic routing. However, Cm and Rm enforce a ZigBee tree as a bounded-degree tree. In graph theory, forming a degree-constrained spanning tree from anarbitrary graph is NP-complete [23]. Ref. [24] proposes polynomial-time graph algorithms when additional connectivity and maximum degree of a graph are given, but this work does not consider the depth constraint. Ref. [25] introduces an approximation algorithm, which can find a spanning tree with a maximum degree of O
(
K+
log|
V|
)
, where K is the degree constraint and V is the set of nodes in the graph. The result is not applicable to ZigBee because it does not consider the depth constraint and the number of children of a node is not bounded. In [26], a polynomial time algorithm is proposed to construct a spanning tree with a bounded degree and a bounded diameter. However, this algorithm is designed for complete graphs.Under the ZigBee tree formation rules, a WSN may experience that orphan problem [27]. Given Cm
,
Rm and Lm, somenodes may be rejected from joining a ZigBee tree. A node is said to become an orphan node when it cannot associate with any parent router but there are still unused address spaces available in the network. In [27], the orphan problem is formulated as two subproblems: (1) bounded-degree-and-depth tree formation (BDDTF) problem and (2) end-device maximum matching
(EDMM) problem. The former is for connecting routers and the latter is for connecting end devices. It is proved that BDDTF
is NP-complete, but EDMM is computationally feasible.
To relieve the orphan problem, [28] proposes to use the addressing rules for an n-dimensional hypercube. Interestingly, when the network structure is close to an n-cube, this scheme can effectively reduce the address space waste. However, when the n-cube is incomplete, orphans may still exist. In [29], a distributed algorithm for ID assignment is proposed. It
Fig. 2. Categories of communication issues in WSNs.
starts by assigning long unique IDs and organizes nodes in a tree structure. This pre-processing helps compute the size of the network. Then, unique IDs are assigned with the minimum number of bits. Observing that most schemes assume a random topology, [30] considers a special ‘‘long-thin’’ WSN topology and proposes efficient address assignment and routing schemes. A long-thin topology is very useful in sensing fields such as water pipes, river banks, and hiking routes, which consist of multiple long linear paths.
2.2. Data gathering
Since the main function of a WSN is to gather information, peer-to-peer communications are less important. Conversely,
convergecast, where a sink node needs to gather a set of nodes’ sensing data, would appear more frequently than other
communication patterns. Below, we classify such solutions into three categories: (A) schedule-based solutions, (B) cluster-based solutions, and (C) correlation-cluster-based solutions. The schedule-cluster-based solutions arrange communication timing with reducing latency and energy consumption as the goal. The cluster-based solutions partition sensor nodes into groups, each with a group leader, with prolonging network lifetime as the goal. The correlation-based solutions exploit spatial and temporal redundancies of sensing data to reduce the transmission cost.
(A) Schedule-based solutions: An inherent problem of data gathering is the funneling effect [31], where contentions occur more seriously as data reaches the sink area. Such solutions arrange codes/channels/slots for sensor nodes along data collection trees to mitigate interference. Refs. [4,32] use multiple codes to help relieve the contention problem. Ref. [4] shows how to connect sensors as a balanced reporting tree and how to assign CDMA codes to sensors to relieve interference among sensors. The work [32] aims to minimize the overall energy consumption subject to a bounded data reporting interval. Dynamic programming algorithms are proposed by assuming that sensors can receive multiple packets at the same time. However, using CDMA is somewhat too strong for WSNs.
Time-based scheduling has been widely studied. A typical approach is to use a staggered wake-up schedule (or ladder
pattern). In [33], an energy-efficient and low-latency MAC, called DMAC, is proposed. Sensors are connected by a tree and stay in a sleep state for the most of the time. Nodes wake up in a staggered manner along the tree. Similarly, [34] schedules sensors by taking their traffic loads into account. Each parent periodically broadcasts an advertisement containing a set of empty slots. Child nodes request empty slots according to their demands. Ref. [35] extends DMAC to a multi-parent scheme. To reduce reporting latency, a node can choose a proper parent with the earliest wake-up time to relay data. In [36], a distributed convergecast algorithm is proposed. The basic idea is to connect nodes by a spanning tree and then reduce the
tree into multiple lines. For each line, transmissions are scheduled in a bottom–up manner. Ref. [37] presents a centralized solution to increase the degree of transmission parallelism. However, since ZigBee enforces that a node can only wake up twice per superframe, the solutions in [36,37] are not ZigBee-compatible.
A beacon-enabled IEEE 802.15.4/ZigBee tree network is widely adopted, where a superframe structure is used for the power-saving purpose. Each superframe is composed of an active portion and an inaction portion. Routers have to choose different times for their active portions to avoid collisions. In the revised IEEE 802.15.4 [38], a router can select one active portion as its outgoing superframe and, based on the active portion selected by its parent, its incoming superframe is decided. In the beginning of an outgoing/incoming superframe, a router is expected to transmit/receive a beacon to/from its child/parent router. How to choose collision-free superframes among routers is left as an open issue in ZigBee. In [39], a reception-based staggered solution is proposed.
(B) Cluster-based solutions: Hierarchical structures are exploited in such solutions. Ref. [40] proposes a Low-Latency
Adaptive Clustering Hierarchy (LEACH) protocol to cluster sensor nodes in a distributed manner. Each sensor node
independently decides to be a cluster head or not based on its remaining energy. Cluster heads are responsible for collecting local sensing data. LEACH cannot guarantee the desired number of cluster heads and their distribution. The centralized LEACH-C [41] tries to minimize the sum of distances between non-cluster heads and their nearest cluster heads. A CDMA-TDMA hybrid scheme is proposed in [42] to enhance LEACH, where each node only needs to broadcast at its the maximum power to compete as a cluster head.
The above schemes have assumed that each member node can reach its cluster head in one hop and each cluster head can reach the sink node also in one hop. Ref. [43] relaxes these constraints by allowing multi-hop data gathering. Heterogeneous nodes are considered in [44,45]. A multi-hop polling schedule for clusters is proposed in [44]. Ref. [45] points out the biased
energy consumption rate (BECR) phenomenon among cluster heads in a heterogeneous WSN. In single-hop gathering, cluster
heads farther away from the sink node will deplete energies faster. In multi-hop gathering, cluster heads closer to the sink node will deplete energies faster. Considering QoS, [46] proposes three application-specific criteria: (i) throughput, (ii) end-to-end delay, and (iii) energy consumption. For intra-cluster data gathering, only partial nodes are allowed to report so as to meet the desired throughput requirement. For inter-cluster data gathering, cluster heads report delay-sensitive data through shortest paths and report other data through a reporting tree to meet delay and energy requirements.
(C) Correlation-based solutions: Sensing data are usually spatially or temporally correlated. Exploiting data correlations can reduce data gathering cost [47,48]. Ref. [49] proposes a structure-free aggregation based on spatial correlations of sensing data. Temporal correlations are considered in [49], where a randomized waiting scheme is proposed. Surveys of such solutions are available in [50].
2.3. Query and reply processing
Query-and-reply communications are fundamental issues in WSNs [51]. We categorize such solutions into three types: (A) directed diffusion, (B) distributed indexing, and (C) multi-resolution summary.
(A) Directed diffusion: Directed diffusion [5] is a popular paradigm followed by much research work. Sources owning sensing data publish what they have, and sinks with interests in specific pieces of data subscribe to them. A query is routed to a specific location if it has geographic information embedded in it; otherwise, it may be flooded. However, the flooding overhead is extremely high because interests must be refreshed periodically. Ref. [52] proposes a light directed diffusion, where control messages are only distributed locally. Ref. [53] extends directed diffusion to provide QoS; the main idea is to specify real-time or best-effort traffic in ‘‘interest’’ packets. Similarly, application-specific deadlines are considered with a prioritized scheduling policy in [54]. For example, a bio-detection event may have an earlier deadline than a surveillance event. Note that not only deadline information but also distances away from destinations are considered to prioritize packets. (B) Distributed indexing: Features may be indexed to facilitate data search. The idea of geographic hashing is explored in [55]. A hash function is used to map event names to locations. Events may be further grouped spatially by their name types. In [56,57], distributed indexing of features and multi-resolution range queries are explored to provide spatially distributed hierarchies of indices.
(C) Multi-resolution summary: In some applications, accurate sensing data is not always needed. Users may request a rough overview periodically, i.e., a low-resolution report, and query in-depth data occasionally, i.e., a high-resolution report. We thus need in-network multi-resolution query-and-reply solutions. In [58], a lossy, gracefully degrading storage model is described to support progressive and long-term in-network query processing. Using a wavelet-based summarization, it achieves (a) low communication overhead for multi-resolution summarization, (b) highly efficient drill-down search over such summaries, and (c) use of network storage through load-balancing and progressive aging of summaries. In [59], a framework is proposed to organize sensor nodes hierarchically and establish multi-resolution summaries through spatial and temporal compressions. In the space domain, only lower-resolution summaries are sent to the sink; higher-resolution summaries are stored in the network and can be obtained via queries. In the time domain, historical data stored in sensor nodes exhibits a finer resolution for more recent data and a coarser resolution for older data.
3. Coverage and deployment issues of WSNs
Given a WSN, the coverage problem asks how well a sensing field is monitored or tracked by sensors. The deployment
types: (i) coverage and connectivity solutions, (ii) energy-conserving and scheduling strategies, and (iii) mobile sensor solutions.
3.1. Coverage and connectivity solutions
Maintaining both coverage and connectivity is essential for a WSN. Sensors are assumed to have fixed sensing and communication ranges. In [60], the coverage problem is formulated as a decision problem. Given a set of sensors deployed in a field, the problem is to determine if the area is sufficiently k-covered, in the sense that every point in the field is covered by at least k sensors, where k is an integer. Rather than directly determining the coverage of each location, [60] looks at how the perimeter of each sensor’s sensing range is covered and proposes an efficient polynomial-time solution. Ref. [8] studies the relationship between coverage and connectivity. To determine the coverage level, it looks at how intersection points between sensors’ sensing ranges are covered. It claims that a region is k-covered by a set of sensors if all intersection points between sensors and between sensors and the boundary of this region are at least covered. Further, it proves that k-covered implies k-connected when sensors’ communication ranges are not less than twice their sensing ranges. The Coverage
Configuration Protocol (CCP) [8] can provide different coverage levels and maintain network connectivity even when the communication ranges are more than twice their sensing ranges. Also, it allows some sensors to go to sleep when they are not needed. When the communication ranges are less than twice the sensing ranges, [8] proposes a connectivity-maintaining protocol, such that all active nodes form a backbone and all inactive nodes are directly connected to at least one active node. An improvement is further proposed in [8].
Protocols allowing an arbitrary relationship between sensing ranges and communication distances are proposed in [61]. Not only putting sensors to sleep, the work also tunes nodes’ transmission powers. Necessary and/or sufficient conditions for a WSN to be k-covered and k-connected and to be k-covered and 1-connected are presented. It simultaneously addresses the issues of coverage, connectivity, power management, and power control under one framework. Ref. [62] analyzes the relationship between deploying density and coverage and connectivity by the percolation theory. It raises the
sensing-coverage phase transition (SCPT) and the network-connectivity phase transition (NCPT) problems. Imagining that sensor
deployment is similar to rain drops falling on a field, SCPT asks the probability of the first occurrence of complete coverage that spans the entire network, while NCPT asks the probability of the first occurrence of a connected component that spans the entire network. Based on a Poisson process, this work gives some theoretical analyses. Ref. [63] extends [62] to a 3D WSN.
3.2. Energy-conserving and scheduling strategies
Sensors are usually deployed with redundancy. Therefore, properly scheduling their on-duty time while maintaining the required coverage level is critical. We categorize such solutions into two types: (A) cover set scheme and (B) opportunistic selection scheme. The former is to find a multi-set such that each set provides the basic coverage, while the latter chooses sets by a randomization technique.
(A) Cover set scheme: How to find multiple mutually exclusive sets of sensor nodes such that each set completely covers the field has been proved to be NP-complete in [64], where a greedy heuristic is proposed. Allowing nodes to have different sensing and transmission ranges, [65] shows how to find a minimum connected subset that covers a region of interest.
(B) Opportunistic selection scheme: The probe-based density control algorithm [66] adopts this approach. Nodes are initially in sleep mode. When waking up, they broadcast a probing message within a certain range. If no reply is received within a pre-defined period, they have to remain active. The coverage degree (density) is controlled by sensors’ probing ranges and wake-up rates. However, this approach has no guarantee of complete coverage and thus may have blind holes. Ref. [67] also randomly selects sensors to meet the required coverage. It forces a minimum distance between any pair of active sensors so as to maintain network connectivity. The round-based scheme [68] divides the time axis into equal length rounds. Each node randomly generates a reference time in each round. In addition, the whole area is divided into grids. For each grid, we have to compute a schedule based on its reference time such that the grid is covered by at least one sensor at any moment of a round. A node’s on-duty time in each round is the union of the schedules of all grids covered by it. This scheme must rely on accurate time synchronization. This is improved by [69], which proves that it is sufficient to only look at the intersection points of nodes’ coverage perimeters. This significantly reduces the computational complexity and leaves no blind holes. The result in [69] includes several decentralized protocols that support multi-layer coverage and can balance nodes’ energy costs.
3.3. Mobile sensor solutions
In the past, WSNs are assumed to be static. Recently, mobility was introduced to WSNs. This improves network capability in many aspects, such as automatic node deployment, flexible topology adjustment, and rapid event reaction. We classify such solutions into two types. The first type of solutions try to relocate nodes to help form/enhence a WSN (e.g., coverage and connectivity). The second type of solutions address the path-planning issues for data ferries to relay data and/or extend network lifetime.
Table 1
Comparison of mobility management methods for mobile sensors.
Sub-type Hybrid WSN Probabilistic sensing Coverage issue Connectivity issue Energy issue
Virtual force [70] Deploy nodes ✓ ✓ ✓
Repulsive force [71] Deploy nodes ✓ ✓
Gradient [72] Deploy nodes ✓ ✓
Voronoi [73] Deploy nodes ✓ ✓
1-coverage [74] Deploy nodes ✓ ✓ ✓ ✓
k-coverage [75] Deploy nodes ✓ ✓ ✓ ✓
Obstacle avoidance [76] Deploy nodes ✓ ✓
Island [77] Enhance network ✓ ✓
Block tree [78] Enhance network ✓
Bidding [79] Enhance network ✓ ✓
Event motion [80] Enhance network ✓
Connectivity restoration [81]
Enhance network ✓ ✓
Relocation [82] Dispatch nodes ✓ ✓
Navigation [83] Dispatch nodes ✓ ✓
Load balance [84] Dispatch nodes ✓ ✓
Deadlock [85] Dispatch nodes ✓
Table 2
Comparison of path-planning methods for data ferries.
Sub-type Distributed nature Single-hop collection Communication time Energy issue Probabilistic contact
Single ferry [86] Relaying ✓ ✓
Multiple ferries [87] Relaying ✓ ✓
Touching points [88] Relaying ✓
Probability [89] Relaying ✓ ✓ ✓
Opportunistic [90] Relaying ✓ ✓
Recursive [9] Lifetime ✓
Routing tree [10] Lifetime ✓
Aggregation [91] Lifetime ✓
1-hop collection [92] Lifetime ✓ ✓
SDMA [93] Lifetime ✓ ✓ ✓
1-hop navigation [94] Lifetime ✓ ✓ ✓
k-hop navigation [95] Lifetime ✓ ✓
Energy-aware Voronoi [96]
Lifetime ✓ ✓
The first type can be further divided into three sub-types. The first sub-type is to help adjust the topology. For example, researchers have applied the virtual force concept and some graph approaches to achieve this goal. The second sub-type is to help enhance coverage and connectivity of a WSN. The third sub-type is to guide mobile sensor nodes to desired locations.
Table 1gives a summary of existing results.
The second type can be further divided into two sub-types. The first sub-type is to find paths for relaying messages for static/isolated nodes. Such paths may be adaptive or probabilistic ones. The second sub-type is to help prolong the network’s lifetime.Table 2summarizes results of existing work.
4. Moving from WSN to CPS: applications and platforms
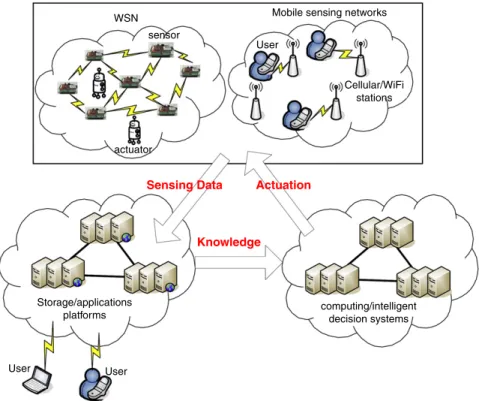
Cyber-physical systems bridge the cyber world (e.g., information, communication, and intelligence) to the physical world through lots of sensors and actuators. A CPS may consist of multiple static/mobile sensor and actuator networks integrated under an intelligent decision system. For each individual WSN, the issues such as network formation, network/power/mobility management, security, etc. would remain the same. However, CPS is featured by cross-domain sensor cooperation, heterogeneous information flow, and intelligent decision/actuation. In this section, we will review some CPS applications and make observations from these prospects. The concept is illustrated inFig. 3. For example, a CPS can facilitate greenhouse asset management through the deployment of multiple WSNs [97]. Each WSN is composed of multiple sensors and actuators to form a climate control system with lighting, cooling, heating, carbon dioxide generating, watering, and fertilizing subsystems. Thus, light intensity, temperature, humidity, and density of carbon dioxide need to be collected and reported. The decision system will transform these sensing data into high-level knowledge (e.g., the proportion of each type of fertilizers) to trigger actuators to maintain good environmental factors in the greenhouse. Note that multiple actuations may coexist (e.g., the cooling subsystem may cowork with the carbon dioxide generating subsystem). Efforts on sensor–actuator and actuator–actuator coordinations can be found in [98,99]. Robotic actuators are introduced in [100]. Below, we review some CPS applications and platforms.Table 3gives a summary of these efforts.
WSN Mobile sensing networks User Cellular/WiFi stations actuator sensor
Sensing Data Actuation
Knowledge
Storage/applications
platforms computing/intelligentdecision systems
User User
Fig. 3. A CPS architecture model.
Table 3
Comparison of CPS applications & platforms.
Reference Functionality & application Sensor type Heterogeneous information flows
[101] Physical rehabilitation & telemedicine ECG, EMG, EEG, SpO2, accelerometer, & tilt sensors
BSNs/GPRS/Bluetooth/WLAN
M-Health [102] Security & telemedicine ECG & PPG BSNs/Bluetooth/GPRS
ANGELAH [103] Elder assistance Video camera, audio, RFID, & smart door lock
WSN/WiFi [104–107] Emergency navigation Light, smoke, & temperature sensors WSN FireGrid [6] Emergency navigation Temperatures,heatflux,
&gas(O2,CO,&CO2)
WSN/Internet
CarWeb [108] Traffic monitoring & mining GPS 3G/WiMAX/Internet
Nericell [109] Traffic monitoring Accelerometer, microphone & GPS, GSM/GPRS/EDGE/Internet
VTrack [110] Route planning GPS & WiFi 3G/WiFi/Internet
[111] Transit tracking Accelerometer & GPS 3G/Internet
BikeNet [112] Experience sharing among bikers Accelerometer, microphone, GPS, magnetometer, CO2, & Temperature
WSN/GSM/GPRS/Bluetooth/WiFi /Inetrnet
ParkNet [113] Parking Ultrasonic & GPS Cellular/WiFi/Internet
[114] Traffic light control RFID WiFi
CenceMe [12] Social networking Accelerometer & GPS Cellular/WiFi
[115] Social networking Camera & accelerometer WiFi
Micro-Blog [116] Social networking GPS, WiFi, & GSM WiFi/GSM/cellular
Video game [117] Video game Accelerometer & compass BSN
[118] Social game Accelerometer & compass BSN/WiFi/3G
4.1. Health-care applications
Cross-Domain Sensing: Future health-care applications would benefit from wearing small sensors by patients [119]. ECG (electrocardiogram), EMG (electromyography), EEG (electroencephalography), SpO2, accelerometer, and tilt sensors are adopted for physical rehabilitation in [101]. Ref. [102] considers security issues in telemedicine when multiple body sensor networks (BSNs) coexist. The system uses ECG and PPG (photoplethysmogram) sensor and designs an authentication mechanism to verify whether two nodes belong to the same BSN through the timing information of users’ heartbeats, which may uniquely represent an individual. Ref. [103] proposes an innovative elder assistance framework, termed AssistiNG ELders
At Home (ANGELAH), which probes passing-by volunteers to provide prompt help to elders in emergency situations. Heterogeneous information flow: The rehabilitation system in [101] has a 3-tier network architecture to monitor the physiological signal of remote patients. The lowest tier is a ZigBee body sensor network connecting to ECG, EMG, EEG, etc.
The middle tier contains GPRS/Bluetooth/WLAN connecting to personal devices (e.g., PDA, cell phone, and PC), which serves as sinks for local BSNs. The upper tier is a broadband network connecting servers to record and analyze collected data from individual patients and issue recommendations, if necessary. In [101], heterogeneous networks are used to connect video cameras, sound sensors, RFID readers, and smart appliances (e.g., smart door lock). Clearly, multi-tier networks are widely used in CPS applications.
Decision/actuation system: A recommendation system is needed in [101] for doctors and nurses. In ANGELAH [103], there are six roles: Sensing Entity (SE), Actuator Entity (AE), Home Manager (HM), Surveillance Center (SC), Local Responder (LR), and Locality Manager (LM). SEs are sensors deployed in elders’ living spaces. AEs are actuators set up in elders’ living spaces and controlled by HM. For example, cameras in a living room are AEs, which can be triggered by RFID readers when elders’ tags are detected. HMs are local servers at homes for gathering sensing data and controlling AEs. SCs are responsible for coordinating prompt responses and selecting the most adequate volunteers to provide help. When an emergency situation is detected, HM informs SC the emergency level, type, cause, and the kind of assistance that may be needed. LRs are nearby volunteers who are willing to provide prompt help. ANGELAH defines the proximity of LRs by the coverage of network access points. It is worth noticing that multiple elders may need assistance in the same network coverage.
4.2. Navigation and rescue applications
Cross-domain sensing: We define a responsive navigation/rescue system as one which takes real-time sensing observations
into consideration. Ref. [104] considers navigating people in a dangerous region with multiple emergency points and one safe exit. Guiding people in fire emergency to safe exits in 2D/3D environments is discussed in [105,106], where a 3D environment involves multiple floors with stairs. Such systems all need smoke, temperature, and/or humidity sensors. For rescuers, infrared, smoke, camera sensors, and life detectors may be needed [120,121]. Note that rescuers also need navigation services to find lives. The Robobees project [122] intends to develop micro air-robotic insects to facilitate search and rescue in unreachable areas.
Heterogeneous information flows: To find safe navigation paths without passing any obstacle, [104] relies on exchanging attractive and repulsive potentials among sensors and exits. Similarly, exchanging ‘‘altitudes’’ is used in [105,106]. Navigation without location information is discussed in [107], where sensor nodes exchange information cooperatively to identify the medial axes of danger areas. Load-balanced navigation is addressed in [123]. These applications all need lots of sensor-to-sensor, sensor-to-human, and sensor-to-infrastructure communications. While WiFi/ZigBee/IEEE 802.15.4 is commonly assumed in such systems, more complicated networking scenarios are demanded.
Intelligent response system: In next-generation large-scale navigation systems with emergency response and evacuation
supports, both scalability and fault tolerance are important factors. Agent-based approaches allowing computation tasks to be executed in distributed and parallel manners are studied in [124]. For emergency support, FireGrid [6] adopts high performance computing grids. FireGrid has four major components: (1) data acquisition and storage component, (2)
simulation component, (3) agent-based command-control component, and (4) Grid middleware component. In particular, there
is a Data Grading Unit to filter and validate accuracy and reliability of sensing data. The simulation component has a set of computational models to interpret the current status and predict the future status of fires. The computing grids provide access to processing units in parallel by emergency tasks. To support decisions for emergency responders, there are a query manager agent and a set of Command, Control, Communication and Intelligence (C3I) user-interface agents to interact with users. Ref. [125] designs a mechanism to avoid navigation congestion and provides firemen rescue commands to intelligently eliminate key dangerous areas such that the number of trapped people can be reduced.
4.3. Intelligent Transportation Systems (ITSs)
Location tracking and road information sensing: Transportation is key part of our daily life. ITSs are important applications
of CPS [126]. Many ITSs projects [127,128] have been developed. Needless to say, GPS information is a must in ITSs. In [109], accelerometers and microphones in mobile phones are used to annotate traffic conditions in a map, such as braking, bumping and honking, thereby allowing us to search for driving directions with less stress, such as chaotic roads and intersections. Considering GPS outage, [110] uses WiFi interfaces on mobile phones to track nearby APs and their centroids for positioning. To track the locations of public vehicles (e.g., buses), [111] proposes a cooperative model between GPS and accelerometers. BikeNet [112] exploits inertial sensors and air sensors for bikers’ experience sharing. Several projects consider parking applications through GPS, ultrasonic, and ranging sensors [129,130,113].
Heterogeneous networking: OBD [131] and CAN-Bus [132] have been developed for intra-vehicle communications. DSRC/WAVE [133] are defined for V2V and V2R communications. ETC systems [134] are widely deployed for toll collection. Through inter-vehicle communications, rear-end collision prevention is discussed in [135,136]. By collecting real-time car locations, CarWeb [108] shows how to mine the current traffic conditions of road segments including waiting time at intersections.
Monitoring and provisioning systems: It is still a difficult task to accurately measure traffic conditions. VTrack [110] uses mobile phones to help estimate traffic delays, detect hot spots during rush hours, and provide real-time route planning with sparely-sampled GPS data. It applies an intelligent hidden Markov model to estimate vehicle trajectories and eliminate
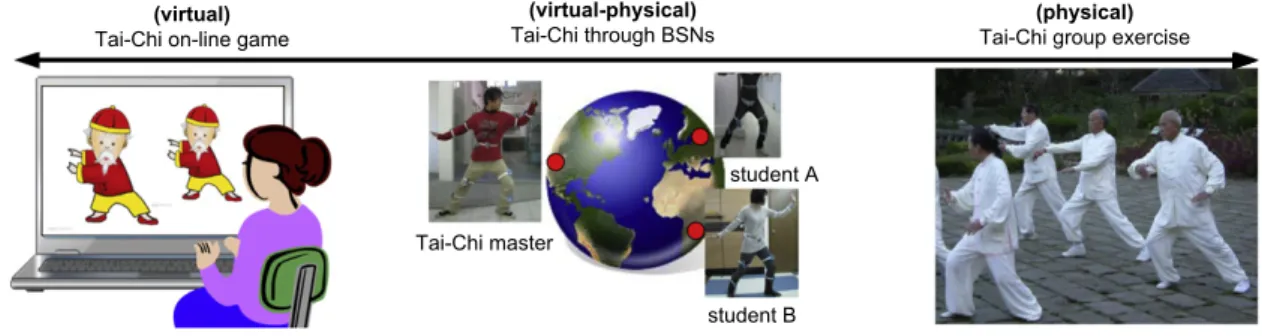
Fig. 4. Problem spectrum in cyber-and-physical world using Tai-Chi exercises as an example.
outliers through map matching and to associate with each sample the most likely road segment. ParkNet [113] exploits sensing capability of drive-by vehicles to detect the occupancy of parking spots. If lane-level vehicle information can be accurately measured, [114] develops an intelligent traffic signal control protocol to speed up car-crossing at intersections.
4.4. Social networking and gaming applications
Sensor-enhanced interaction: Traditional social networks are Web-based (e.g., Facebook, Windows Live, and YouTube). CPS-based social networking would involve more physical inputs to enrich interactions among users. CenceMe [12] allows users to share their sensing information via mobile phones (e.g., audio, motion, acceleration, and location). Therefore, users’ moods, activities, mobility patterns, locations, etc. become exchangeable information in the cyber world. Ref. [115] shows an interesting way to record and share water-drinking behaviors as socialization tools. Through sharing locations,
Micro-Blog [116] encourages social participants to share and query information with each other via smart phones. In the area of interactive games, adopting physical inputs, such as those from inertial sensors, is already popular. Information processing of inertial sensors in BSNs has been intensively studied [137–139]. In [117], a CPS-based video game is presented. A social network where participants can wear inertial sensors and practice traditional Chinese Tai-Chi over the Internet is presented in [118]. This platform allows users to share conventional information as well as sensory data in a real-time manner. InFig. 4, we show the spectrum from ‘‘virtual’’ Tai-Chi, to ‘‘cyber–physical’’ Tai-Chi, and then to ‘‘physical’’ Tai-Chi.
Networking scenarios: To collect sensing data, BSNs/WSNs are needed. Participants then use the Internet or 3G networks
to interact with each other. The use of networks should be context-aware. For example, Micro-Blog [116] tries to balance between localization accuracy and battery lifetime. A mobile phone switches between two localization modes, WiFi and GPS modes. WiFi mode is the default mode if the WiFi fingerprint does not change over time. Once it detects movement over a threshold, it switches to the GPS mode.
Socialization and interaction platform: A social platform needs to connect many users around the world, thus demanding
huge data processing and storage capability. CenceMe [12] uses a split-level classification to process raw sensing data. A user’s mobile phone first classifies data into high-level information, called primitives. CenceMe provides an audio classifier and an activity classifier to recognize human voices and activities (including sitting, standing, walking, and running), respectively. When primitives arrive at the backend server, five complex classifiers, namely conversation classifier, social context, mobility
mode detector, location classifier, and am I hot, are designed to retrieve second-level information, called facts, to reflect users’
social behaviors, such as on-going conversations, nearby buddies, user’s mobility pattern (e.g., if he/she is in a vehicle), and location type (e.g., restaurant, library, etc., which is obtained via Wikimapia GIS databases [140]). Interestingly, the ‘am I hot’ classifier can recognize users’ social stereotypes (e.g., party animal, cultured, and healthy). Facts are stored in a database for retrieval and publishing. In Micro-Blog [116], a user can query a specific region. If there exists information in a database matching the query, the server will reply to this query. Otherwise, the server will select those phones located in this region and forward this query to them for possible responses. To encourage responses to socialized queries, a give and take scheme is adopted, where users earn/pay credits when they reply to/issue queries.
5. Features and technical challenges of CPS
In this section, we first point out some unique features of CPS applications. Then we discuss some technical challenges and progress that has been made. First, we discuss their unique features.
1. Cross-domain sensor sources and data flows: Multiple types of sensors will be adopted at the same time in intelligent CPS applications. Moreover, these cross-domain sensing data will be exchanged over heterogeneous networks.
2. Embedded and mobile sensing: Sensors are no longer static and may have high-degree mobility through carriers such as smart phones and vehicles. This implies that sensing coverage would vary over time, thus exhibiting more uncertainty. One may rely on complicated knowledge discovery mechanisms to analyze these mobile data.
3. User contribution and cooperation through give-and-take-like models: Participatory sensing would be common in CPS. However, a give-and-take-like data contribution model is needed to encourage sharing. As sharing happens more frequently, the privacy issue becomes a concern too.
4. Elastic loads requiring cloud-supported storage and computing capability: With the maturity of cloud computing, the pay-as-you-go concept is likely to be adopted in CPS to serve storage, computing, and communication needs. This allows CPS developers to focus on their own work. Similarly, users can choose the part of CPS applications that they really want, rather than over-load the system. This opens up a new research direction of load balancing for CPS over cloud platforms. 5. Accumulated intelligence and knowledge via learning and data mining technologies: Data in CPS may have high dynamics and uncertainty. Retrieving useful knowledge will rely on learning and data mining technologies. It is essential to understand the temporal and spatial correlations of these sensing data. Further, feedback from users and actuators may help us to accumulate, or even discover, unknown knowledge.
6. Rich interactions among many objects and things through the Internet (such as Internet-of-Things): A lot of sensor–sensor, sensor–actuator, actuator–actuator, actuator–user, user–user, user–object, object–object, object–thing, thing–thing, and thing–user interactions may occur in CPS applications. Such rich interactions demand flexible communication channels, like the Internet, to facilitate our applications.
Below, we review the technical challenges and progresses that have been made in these issues.
5.1. Networking issues
As CPS spans from WSNs to the Internet, a lot of interworking issues have to be resolved. TinyOS [141] deviates from the IP network architecture by addressing the lightweight and power-saving concerns. The uIP [142] includes a low-power link built on IEEE 802.15.4 for small embedded devices. IETF defines RFC 4944 (6LoWPAN) [143] for IPv6 datagrams to carry 802.15.4 frames (such as fragmentation and header compression). Ref. [144] proposes an IPv6-based network architecture to support duty-cycled link, hop-by-hop forwarding, and routing protocols. It considers multiple WSNs connected by IPv6-based border routers through IP links, including Ethernet, WiFi, GPRS, and satellites. Border routers may also implement IPv4-to-IPv6 translation. This network architecture opens an opportunity for future CPSs since cross-domain end-to-end communication among sensor nodes is possible.
5.2. Cross-domain interference avoidance
Communication reliability is critical when multiple devices co-exist (e.g., WiFi, Bluetooth, and ZigBee, all of which work on the same 2.4 GHz ISM band). Refs. [145,146] study the performance of ZigBee networks when there exist WiFi networks. Specifically, ZigBee signal is too weak to be detected by WiFi senders. A pessimistic approach is to avoid using the channels occupied by other networks. A virtual channel management scheme is proposed in [147], which allows multiple ZigBee networks coexisting by scheduling their superframes. A more dynamic approach is to allow different nodes in a WSN to use different channels at different timing [148]. This is quite resilient to node mobility. Contrarily, [149] shows how ZigBee and WiFi networks may cooperate with each other to reduce header corruption. Since WiFi packets are shorter than ZigBee packets, the former usually corrupt headers of the latter. A header redundancy mechanism, called Multiple-Headers (MH), is proposed for ZigBee. Intuitively, the first (corrupted) header can cause a WiFi transmitter to back off and the second header can improve the correct detection by a ZigBee receiver.
5.3. QoS and cloud computing
Ref. [150] identifies some QoS requirements while designing a CPS: (1) service-oriented architecture (SOA), (2) Qos-aware communications, (3) resource management, and (4) QoS-Qos-aware power management. A SOA helps decompose CPS functionality into small, distinct units, i.e., services. It may facilitate rapid and scalable development of CPS applications through reusable services. Application-aware QoS should be defined for cross-layer communications. Because future CPSs must adapt to highly dynamic and unpredictable environments, self-management policies are needed to allocate resources (e.g., CPU time, memory, bandwidth, and energy) in an autonomous manner for high-level QoS requirements.
How to minimize energy consumption and maximize QoS is a challenge to future CPSs. We believe that cloud computing techniques can greatly help in this aspect. Two key enabling technologies for cloud computing are ubiquitous connectivity and virtualization. Virtualization technologies allow dynamic provisioning of resources by service isolation, thus enabling auto-scaling and auto-managing capabilities. With a ‘‘pay as you go’’ model, cloud computing services have three types: (1) Infrastructure as a Service (IaaS), (2) Platform as a Service (PaaS), and (3) Software as a Service (SaaS). IaaS isolates the lower-layer ‘‘real machines’’ for users’ cloud infrastructures (e.g., IBM Blue Cloud and Amazon EC2). PaaS provides ‘‘virtual platforms’’ and service APIs to facilitate application development (e.g., Microsoft Windows Azure and Google App Engine). SaaS provides a set of applications and softwares with manageable QoS (e.g., Google APPs).
Cloud computing is a vivid area especially when CPS applications are involved. To relieve the waste of network bandwidth due to communications between virtual machines (VMs) for data-intensive applications, [151] proposes a decentralized affinity-aware migration technique that monitors fingerprints of traffic exchanges between VMs and
dynamically adjusts/migrates VM placement for communication optimization. For quick recovery from mid-query faults in a distributed database, [152] divides each query into subqueries in MapReduce such that each subquery can be rerun on a different node.
5.4. Location-based services and beyond
‘‘Locations’’ are the first-class knowledge in many CPS applications. While GPS is widely used in outdoor environments, there are increasing demands for indoor positioning technologies. Earlier systems, such as Bat [153] and Cricket [154], are for small-scale environments. Pattern-matching techniques [155–157], which are based on existing WLAN infrastructures, can scale up more easily. To conquer the signal fluctuation problem, researchers have started to use inertial sensors to assist indoor positioning. In [158,159], foot-mounted inertial sensors are adopted. In particular, [159] considers a 2.5D building
model, which includes multiple floors and stairways.
Rather than coordinate-based locations, [160] considers more meaningful logical locations (e.g., Starbucks and Wal-mart). By periodically learning the walking trails of individuals and when and where they encountered each other, [14] proposes an Escort Service. The walking trails of a user, consisting of displacement, direction, and time, are measured by accelerometer and compass sensors on the his/her mobile phone and reported to a central server. To reduce localization drift, audio beacons are randomly deployed in public buildings as reference points. Encounters among users are detected by periodical announcements from mobile phones. The central server maintains a global view of users’ movement and encounter patterns.
For property protection, Brickhouse [161] and Liveview [162] provide asset tracking using GPS. Tracking stolen vehicles by small embedded wireless tags consisting of vibration dosimeter, 3-axis accelerometer, 3-axis gyroscope, and GSM/GPRS modem is reported in [163].
5.5. Monitoring services and beyond
CPS-based monitoring services would extend to cross-WSN and cooperative models. Carriers of sensors will include mobile phones, vehicles and many other tools. Ref. [164] discusses atmospheric pollution monitoring using vehicular sensor networks. Monitoring of carbon dioxide concentration is demonstrated in [165]. Bikenet [112] enables cooperative monitoring with the assistance of cyclists. Mobieyes [166] is for urban monitoring by vehicles.
CPS will play an important role in energy and green technologies, too. Traditionally, electricity companies can only use past experiences or very limited on-line information to adjust their electricity distribution policy. Using pervasive power meters and sensor networks deployed at factories, communities, and even houses, finer electricity distribution policies may be developed. This is known as smart grid (or power grid) [11,167,168]. Ref. [11] discusses a smart grid test bed built in Korean. It uses ZigBee smart tags to monitor and control the power usage. The reliability issue in an electric power grid is addressed in [167].
5.6. Security and privacy challenges
Since sensing data is no longer owned by local devices, security and privacy issues become more critical in CPS. Ref. [168] discusses security requirements and solutions in a smart grid. Individual information should be contributed to the public more carefully. Current approaches can generally be categorized into three types. The first type is to determine the degree of privacy by users’ willingness. In the community-based traffic monitoring application [169], a phenomenon distribution is constructed to predict the phenomenon values of unresolved locations. A utilitarian data collection model is adopted, where people with higher demands should contribute more sensing data. The second type is using some techniques to mask the original data. A common approach is the perturbation-based techniques [170,171]. The main idea is to mask the original data with noise, which can be canceled out during aggregate calculations. However, perturbation-based techniques always suffer from errors. The third type is a combination of the previous two approaches. In [13], a vehicular participatory sensing model is proposed for privacy-preserving map reconstruction by linear regression. A user can control the degree of privacy by controlling the amount of aggregation involved in feature extraction. It has two objectives: (1) to minimize the modeling error and (2) to maximize the reconstruction (breach) error.
6. Conclusions
We have reviewed what has been researched in MANET and WSN and how they drive the progress of CPS.Table 4
shows a qualitative comparison of them. While the society of WSN focuses more on the designs of sensing, event-handling, data-retrieving, communication, and coverage issues, the society of CPS focuses more on the development of cross-domain intelligence from multiple WSNs and the interactions between the virtual world and the physical world. A CPS application may bridge multiple remote WSNs and take actuation actions. We have seen a lot of successful vehicle- and mobile phone-based CPS services. Data from such applications is also expected to be continuous streaming data at a very large volume, so storing, processing, and interpreting these data in a real-time manner is essential. Important factors to the
Table 4
A qualitative comparison of MANET, WSN, and CPS.
Networks/features MANET WSN CPS
Network formation Random deployment ✓ ✓ ✓
Dynamic topology ✓ ✓
Internet-supported networking ✓ ✓
Time-varying deployment ✓
Interconnection among multiple networks ✓
Communication pattern Query-response flows ✓ ✓ ✓
Arbitrary communication flows ✓ ✓
Cross-network communication flows ✓
Power management Opportunistic sleep ✓ ✓
Multiple sleep modes of nodes ✓
Power management techniques for both sensors and central servers ✓
Network connectivity and coverage Connectivity ✓ ✓ ✓
Coverage ✓ ✓
Heterogeneous coverage and coverage ✓
Knowledge mining Data mining and database management ✓ ✓
Multi-domain data sources ✓ ✓
Data privacy and security ✓
Quality of services Networking QoS ✓ ✓ ✓
Multiple data resolution ✓ ✓
Table 5
Important factors in designing different CPS applications.
Applications/factors Health care Navigation and rescue ITS Social networking and gaming
Network formation ✓
Data gathering ✓ ✓ ✓ ✓
Query and reply ✓ ✓ ✓ ✓
Sensing coverage ✓
Network connectivity ✓ ✓
Node mobility ✓ ✓
Heterogeneous networks ✓ ✓ ✓ ✓
Knowledge discovery ✓ ✓ ✓ ✓
Security and privacy ✓ ✓
success of CPS include management of cross-domain sensing data, embedded and mobile sensing technologies, elastic computing/storaging technologies, and privacy and security designs. We have also reviewed platforms for health care, navigation and rescue services, ITS, and social networking and gaming, and pointed out the challenges in theses systems. InTable 5, we summarize important design factors in different applications. Through these reviews, we hope to stimulate more technological development and progress for future CPS applications.
Acknowledgements
Y.-C. Tseng’s research is co-sponsored by MoE ATU Plan, by NSC grants 97-3114-E-009-001, 97-2221-E-009-142-MY3, 98-2219-E-009-019, and 98-2219-E-009-005, 99-2218-E-009-005, by ITRI, Taiwan, by III, Taiwan, by D-Link, and by Intel.
References
[1] I. Akyildiz, W. Su, Y. Sankarasubramaniam, E. Cayirci, A survey on sensor networks, IEEE Commun. Mag. 40 (8) (2002) 102–114. [2] S. Basagni, M. Conti, S. Giordano, I. Stojmenovic, Mobile Ad Hoc Networking, John Wiley and Sons, Inc., 2004.
[3] Terrestrial ecology observing systems, center for embedded networked sensing.http://research.cens.ucla.edu/.
[4] S. Upadhyayula, V. Annamalai, S.K.S. Gupta, A low-latency and energy-efficient algorithm for convergecast in wireless sensor networks, in: Global Telecommunications Conf., 2003, pp. 3525–3530.
[5] C. Intanagonwiwat, R. Govindan, D. Estrin, Directed diffusion: a scalable and robust communication paradigm for sensor networks, in: MobiCom, 2000, pp. 56–67.
[6] L. Han, S. Potter, G. Beckett, G. Pringle, S. Welch, S.-H. Koo, G. Wickler, A. Usmani, J.L. Torero, A. Tate, FireGrid: an e-infrastructure for next-generation emergency response support, J. Parallel Distrib. Comput. 70 (11) (2010) 1128–1141.
[7] H.-C. Lee, A. Banerjee, Y.-M. Fang, B.-J. Lee, C.-T. King, Design of a multifunctional wireless sensor for in-situ monitoring of debris flows, IEEE Trans. Mob. Comput. 59 (11) (2010) 2958–2967.
[8] X. Wang, G. Xing, Y. Zhang, C. Lu, R. Pless, C. Gill, Integrated coverage and connectivity configuration in wireless sensor networks, in: Int’l Conf. Embedded Networked Sensor Systems, 2003, pp. 28–39.
[9] M. Ma, Y. Yang, SenCar: an energy-efficient data gathering mechanism for large-scale multihop sensor networks, IEEE Trans. Parallel Distrib. Syst. 18 (10) (2007) 1476–1488.
[10] G. Xing, T. Wang, Z. Xie, W. Jia, Rendezvous planning in wireless sensor networks with mobile elements, IEEE Trans. Mob. Comput. 7 (12) (2008) 1430–1443.
[11] J. Lee, D.-K. Jung, Y. Kim, Y.-W. Lee, Y.-M. Kim, Smart grid solutions, services, and business models focused on telco, in: IEEE/IFIP Network Operations and Management Symp. Workshops, 2010, pp. 323–326.
[12] E. Miluzzo, N.D. Lane, K. Fodor, R. Peterson, H. Lu, M. Musolesi, S.B. Eisenman, X. Zheng, A.T. Campbell, Sensing meets mobile social networks: the design, implementation and evaluation of the CenceMe application, in: Int’l Conf. Embedded Networked Sensor Systems, 2008, pp. 337–350. [13] H. Ahmadi, N. Pham, R. Ganti, T. Abdelzaher, S. Nath, J. Han, Privacy-aware regression modeling of participatory sensing data, in: Int’l Conf. Embedded
Networked Sensor Systems, 2010, pp. 99–112.
[14] I. Constandache, X. Bao, M. Azizyan, R.R. Choudhury, Did you see Bob?: Human localization using mobile phones, in: MobiCom, 2010, pp. 149–160. [15] E.A. Lee, Cyber physical systems: design challenges, in: Int’l Symp. on Object/Component/Service-Oriented Real-Time Distributed Computing, 2008. [16] Motes, smart dust sensors, wireless sensor networks.http://www.xbow.com/.
[17] Texas Instruments CC2431.http://www.ti.com/. [18] Jennic JN5121.http://www.jennic.com/.
[19] ZigBee specification version 2006, ZigBee document 064112.
[20] IEEE standard for information technology - telecommunications and information exchange between systems - local and metropolitan area networks specific requirements part 15.4: wireless medium access control (MAC) and physical layer (PHY) specifications for low-rate wireless personal area networks (LR-WPANs), 2003
[21] F. Cuomo, E. Cipollone, A. Abbagnale, Performance analysis of IEEE 802.15.4 wireless sensor networks: an insight into the topology formation process, Comput. Netw. 53 (18) (2009) 3057–3075.
[22] P. Baronti, P. Pillai, V.W. Chook, S. Chessa, A. Gotta, Y.F. Hu, Wireless sensor networks: a survey on the state of the art and the 802.15.4 and ZigBee standards, Comput. Commun. 30 (7) (2007) 1655–1695.
[23] M.R. Garey, D.S. Johnson, Computers and Intractability: A Guide to the Theory of NP-Completeness, W.H. Freeman, 1979. [24] A. Czumaj, W.-B. Strothmann, Bounded degree spanning trees, in: European Symp. Algorithms, 1997.
[25] J. Konemann, R. Ravi, A matter of degree: Improved approximation algorithms for degree-bounded minimum spanning trees, in: ACM Symp. Theory of Computing, 2000.
[26] J. Konemann, A. Levin, A. Sinha, Approximating the degree-bounded minimum diameter spanning tree problem, Algorithmica 41 (2) (2004) 117–129. [27] M.-S. Pan, C.-H. Tsai, Y.-C. Tseng, The orphan problem in ZigBee wireless networks, IEEE Trans. Mob. Comput. 8 (11) (2009) 1573–1584.
[28] G. Bhatti, G. Yue, A structured addressing scheme for wireless multi-hop networks, Technical Report, Mitsubishi Electric Research Labs Cambridge, MA, 2005.
[29] E. Ould-Ahmed-Vall, D.M. Blough, B.S. Heck, G.F. Riley, Distributed unique global ID assignment for sensor networks, in: Int’l Conf. Mobile Ad Hoc and Sensor Systems, 2005.
[30] M.-S. Pan, H.-W. Fang, Y.-C. Liu, Y.-C. Tseng, Address assignment and routing schemes for ZigBee-based long-thin wireless sensor networks, in: Vehicular Tech. Conf., 2008, pp. 173–177.
[31] C. Wan, S. Eisenman, A. Campbell, J. Crowcroft, Siphon: overload traffic management using multi-radio virtual sinks in sensor networks, in: Int’l Conf. Embedded Networked Sensor Systems, 2005, pp. 116–129.
[32] Y. Yu, B. Krishnamachari, V.K. Prasanna, Energy-latency tradeoffs for data gathering in wireless sensor networks, in: INFOCOM, 2004.
[33] G. Lu, B. Krishnamachari, C.S. Raghavendra, An adaptive energy-efficient and low-latency MAC for data gathering in wireless sensor networks, in: Int’l Parallel and Distributed Processing Symp., 2004.
[34] B. Hohlt, L. Doherty, E. Brewer, Flexible power scheduling for sensor networks, in: Int’l Symp. Information Processing in Sensor Networks, 2004, pp. 205–214.
[35] A. Keshavarzian, H. Lee, L. Venkatraman, Wakeup scheduling in wireless sensor networks, in: Int’l Symp. Mobile Ad Hoc Networking and Computing, 2006, pp. 322–333.
[36] S. Gandham, Y. Zhang, Q. Huang, Distributed minimal time convergecast scheduling in wireless sensor networks, in: Int’l Conf. Distributed Computing Systems, 2006.
[37] H. Choi, J. Wang, E.A. Hughes, Scheduling for information gathering on sensor network, Wirel. Netw. 15 (2009) 127–140.
[38] IEEE standard for information technology - telecommunications and information exchange between systems - local and metropolitan area networks specific requirements part 15.4: wireless medium access control (MAC) and physical layer (PHY) specifications for low-rate wireless personal area networks (LR-WPANs)(revision of IEEE Std 802.15.4-2003), 2006
[39] Y.-C. Tseng, M.-S. Pan, Quick convergecast in ZigBee beacon-enabled tree-based wireless sensor networks, Comput. Commun. 31 (5) (2008) 999–1011. [40] W.R. Heinzelman, A. Chandrakasan, H. Balakrishnan, Energy-efficient communication protocol for wireless microsensor networks, in: Hawaii Int’l
Conf. on System Sciences, 2000.
[41] W.B. Heinzelman, A.P. Chandrakasan, H. Balakrishnan, An application-specific protocol architecture for wireless microsensor networks, IEEE Wirel. Commun. 1 (4) (2002) 660–670.
[42] L. Zhao, X. Hong, Q. Liang, Energy-efficient self-organization for wireless sensor networks: a fully distributed approach, in: Global Telecommunications Conf., 2004, pp. 2728–2732.
[43] O. Younis, S. Fahmy, HEED: A hybrid, energy-efficient, distributed clustering approach for ad hoc sensor networks, IEEE Trans. Mob. Comput. 3 (4) (2004) 366–379.
[44] Z. Zhang, M. Ma, Y. Yang, Energy-efficient multihop polling in clusters of two-layered heterogeneous sensor networks, IEEE Trans. Comput. 57 (2) (2008) 231–245.
[45] K. Xu, H. Hassanein, G. Takahara, Q. Wang, Relay node deployment strategies in heterogeneous wireless sensor networks, IEEE Trans. Mob. Comput. 9 (2) (2010) 145–159.
[46] H.J. Choe, P. Ghosh, S.K. Das, QoS-aware data reporting control in cluster-based wireless sensor networks, Comput. Commun. 33 (11) (2010) 1244–1254.
[47] R. Cristescu, B. Beferull-Lozano, M. Vetterli, R. Wattenhofer, Network correlated data gathering with explicit communication: NP-completeness and algorithms, IEEE/ACM Trans. Netw. 14 (1) (2006) 41–54.
[48] K. Yuen, B. Liang, B. Li, A distributed framework for correlated data gathering in sensor networks, IEEE Trans. Veh. Technol. 57 (1) (2007) 578–593. [49] K.-W. Fan, S. Liu, P. Sinha, Structure-free data aggregation in sensor networks, IEEE Trans. Mob. Comput. 6 (8) (2007) 929–942.
[50] E. Fasolo, M. Rossi, J. Widmer, M. Zorzi, In-network aggregation techniques for wireless sensor networks: a survey, IEEE Wirel. Commun. 14 (2) (2007) 70–87.
[51] K. Akkaya, M. Younis, A survey on routing protocols for wireless sensor networks, Ad Hoc Networks 3 (3) (2005) 325–349.
[52] A. Marcucci, M. Nati, C. Petrioli, A. Vitaletti, Directed diffusion light: low overhead data dissemination in wireless sensor networks, in: Vehicular Tech. Conf., 2005, pp. 2538–2545.
[53] M. Chen, T. Kwon, Y. Choi, Energy-efficient differentiated directed diffusion (EDDD) in wireless sensor networks, Comput. Commun. 29 (2) (2006) 231–245.
[54] K. Casey, R. Neelisetti, A. Lim, RTDD: a real-time communication protocol for directed diffusion, in: Wireless Communications and Networking Conf., 2008, pp. 2852–2857.
[55] S. Ratnasamy, B. Karp, L. Yin, F. Yu, D. Estrin, R. Govindan, S. Shenker, GHT: a geographic hash-table for data-centric storage, in: ACM Int’l Workshop Wireless Sensor Networks and Their Applications, 2002, pp. 78–87.