Paper: a study on the certification of the information security management systems
全文
數據


相關文件
volume suppressed mass: (TeV) 2 /M P ∼ 10 −4 eV → mm range can be experimentally tested for any number of extra dimensions - Light U(1) gauge bosons: no derivative couplings. =>
We explicitly saw the dimensional reason for the occurrence of the magnetic catalysis on the basis of the scaling argument. However, the precise form of gap depends
Define instead the imaginary.. potential, magnetic field, lattice…) Dirac-BdG Hamiltonian:. with small, and matrix
incapable to extract any quantities from QCD, nor to tackle the most interesting physics, namely, the spontaneously chiral symmetry breaking and the color confinement..
• Formation of massive primordial stars as origin of objects in the early universe. • Supernova explosions might be visible to the most
Miroslav Fiedler, Praha, Algebraic connectivity of graphs, Czechoslovak Mathematical Journal 23 (98) 1973,
Radiographs of Total Hip Replacements 廖振焜 林大弘 吳長晉 戴 瀚成 傅楸善 楊榮森 侯勝茂 2005 骨科醫學會 聯合學術研討會. • Automatic Digital PE
(Another example of close harmony is the four-bar unaccompanied vocal introduction to “Paperback Writer”, a somewhat later Beatles song.) Overall, Lennon’s and McCartney’s
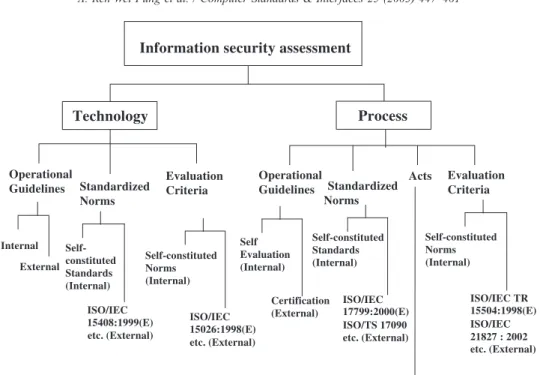
![Fig. 8. The use of ISO/IEC 17799 in various industry information security management standards [17] .](https://thumb-ap.123doks.com/thumbv2/9libinfo/7723794.147115/13.816.127.682.552.963/fig-iso-various-industry-information-security-management-standards.webp)