An integrated location management scheme for seamless access in B3G systems
全文
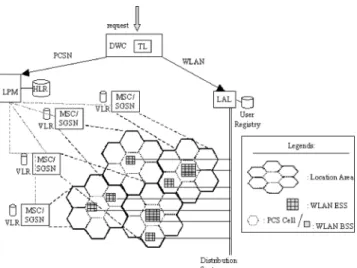
(2) CHENG et al.: AN INTEGRATED LOCATION MANAGEMENT SCHEME. 717. Fig. 1 System architecture for location management in heterogeneous wireless networks.. such as GPRS and 3G, the terminals are required to update their location information so that the system knows the residing location area (LA) of a terminal at all times. As shown in Fig. 1, the MSC/SGSN and HLR/VLR [4], [5] are designated to handle the location management in a PCS network. In addition, WLANs become more and more prevalent in the corporate offices, academic campus, and hot spots in the urban areas for local area coverage and network connectivity. A basic services set (BSS) is defined by the coverage of an access point (AP). An extended service set (ESS) consists of a set of BSSs, in which communications take place from one BSS to another. As shown in Fig. 1, the distribution system interconnects several ESSs and serves as the backbone of the WLANs. As an MT with dual-mode (i.e. PCS and WLAN modes) connection capability roams in a PCS network, it is possible that the MT may be also connected to a WLAN via an AP in some geographic areas. It is known that the coverage area of a BSS is usually smaller than that of a PCS cell. When an MT is connected to a base station in the PCS network as well as an AP in the WLAN, the location determination of the MT through the AP will obtain a more precise position. This observation motivates our work in developing an integrated location management mechanism for heterogeneous wireless networks. 2.2 Integrated Location Management The goal of the integrated location management is to determine the client’s location more precisely while reducing the cost of locating. Three major functionalities in the proposed location management are the determination of the WLAN connectivity (DWC) for an MT, the development of a local area location (LAL) scheme for WLAN, and the location prediction module (LPM) for PCS networks. They are depicted as follows.. 1. DWC for an MT: When an MT is currently connected to an ESS, it can be located in a more precise position. Therefore, the determination of the WLAN connectivity for an MT is essential. In this paper, we propose a temporal locality (TL) method that takes the interarrival time of location queries as the input parameter, and exploits a probability model to determine the current location of an MT. The basic idea of the scheme is that, if a client was known to reside in an ESS and is queried twice within a short duration, then the chance for the client to stay at the same ESS is rather high. 2. LAL for WLAN: The LAL scheme is responsible for local-area location management, which include location update and tracking. The location update is concerned with updating the location information of a mobile user in a distribution system. Once a mobile client is detected, the location information can be updated and maintained afterward. A framework for the LAL will be presented in Section 4. 3. LPM for PCS networks: If an MT is determined to be solely residing in the PCS network, our concern is to minimize the cost of location tracking by reducing the query messages to the HLR. Therefore, the LPM is developed for minimizing the cost and improving the performance of positioning procedures. It is observed that the traces of user behavior provide precious information for location prediction. Mobile clients trend to stay at particular locations, depending on different time instants. In this paper, the LPM uses a rule mining and matching scheme to explore the relationship among user behavior, time, and place. The location request is matched with the association rules mined out from the log files. 3.. Determination of WLAN Connectivity. In this section, the residence function for an MT in an ESS is formally derived. The TL method takes the inter-arrival time of location requests as the parameter to estimate whether an MT is still staying in an ESS or not. 3.1 Cost Model for DWC Consider the mechanism shown in Fig. 2. Let C p be the cost of performing the LPM in the PCS network to obtain the location information for an MT. Let Cl be the cost of performing the LAL scheme to obtain the location of an MT in WLAN. Let Cd be the cost of performing the DWC scheme. According to DWC, upon the arrival of a location request, if the previous location record indicated that an MT resided in an ESS, then the TL method is invoked to determine whether the MT still stays in an ESS or not. On the other hand, if the previous location record showed that the WLAN was not available, then the LPM scheme is invoked directly. Hence, the total cost of the proposed mechanism, Cd , can be expressed as.
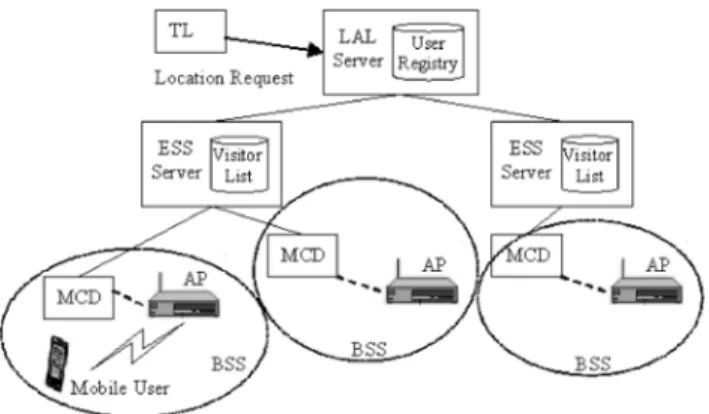
(3) IEICE TRANS. COMMUN., VOL.E88–B, NO.2 FEBRUARY 2005. 718. Fig. 3 Fig. 2. Cd = ψd · Ct + (1 − ψd ) · C p. Ct = ψt · Cl + (1 − ψt ) · (C p + Cl ). (2). in which ψt is the probability of a location hit by using the TL method (i.e. the MT is found to indeed stay in the WLAN). To make the TL method feasible, it is true that Ct < C p . The following inequality can be derived from equations (1) and (2),. in which. Cl 1 = Cp α 1 α. (3). indicates the cost ratio of Cl to C p .. 3.2 Temporal Locality Method Let R denote the random variable of the residence time of a client in an ESS. Let ε be the inter-arrival time of two consecutive location requests for a mobile client. In addition, let φ be the duration from the time when the client enters the ESS till the time when the last location request is made. The probability that the client stays in the same ESS for at least a duration of ε + φ, given that the client is known to have been in the ESS for at least a duration time φ, can be expressed by g(ε; φ) = Pr[R > ε + φ|R > φ] Pr[R > ε + φ, R > φ] = Pr[R > φ]. 1 − Pr[R ≤ ε + φ] 1 − Pr[R ≤ φ] = e−qµε. =. (1). in which ψd is the chance for the previous record to indicate that an MT was known to reside in an ESS, and Ct is the cost of using the TL method to obtain the location for the MT. Furthermore, if the determination by the TL method results in a location hit, then the locating procedure terminates with a lower cost. However, if the determination results in a location miss (i.e. the MT is not in any ESS), then the LPM procedure is required to obtain the correct location and perform the signaling. Therefore, the cost of the TL method, Ct , can be computed as. ψt >. The algorithm of the DWC.. Cost model for the system.. (4). It can be seen that g(ε; φ) is independent with φ, which preserves the memoryless property. For simplicity, denote g(ε; φ) as g(ε). If g(ε) ≥ 1/α as derived in (3), then it is worthy of applying the temporal locality prediction. To apply the TL method, a record is maintained for each user. Fields c loc and l req indicate the current an ESS identity, and the time instance of issuing the last request for the user respectively. Initially, the user is never located before and c loc is invalid. Therefore, the LPM in the PCS network is invoked directly to locate an MT at a PCS cell. After that, the TL method translates the cell position to the ESS id and the field c loc is set to the ESS accordingly, if the ESS is available in the geographic area of the PCS cell. Besides, field l req is set to the time when the current request is made. Afterwards, the TL method is invoked each time a location request arrives. The algorithm for the DWC scheme is illustrated in Fig. 3. 4.. Local Area Location Scheme. The LAL scheme is responsible for local area location management, which includes location update and tracking. The system architecture of the IEEE 802.11 based infrastructure for location management is shown in Fig. 4. Three major components in the location management mechanism are the mobile client detector (MCD), the ESS server, and the local area location (LAL) server. An MCD is an middleware embedded in each AP. Two major functionalities for an MCD are to actively detect the existence of MTs under the coverage area of a BSS, and to identify the MTs. An ESS server is associated with a visitor list for maintaining the IP and MAC addresses for all MTs in the BSSs of one ESS. The LAL server is equipped with a database called user registry in which a record is maintained for each MT that is currently connected to the IEEE 802.11 WLAN services..
(4) CHENG et al.: AN INTEGRATED LOCATION MANAGEMENT SCHEME. 719. system information when an MT powers off or moves outside the service area. When an MT moves outside the service area, the MCD detects such a disconnection according to the notification or after the timeout period and sends the location deregistration request to the ESS server. The ESS server then deletes the record of the MT in the visitor list, and send location deregistration request upwards to the LAL server. After LAL server updates the user registry, the ESS server and the MCD will receive the location deregistration reply respectively. 5. Fig. 4 System architecture of IEEE 802.11 based infrastructure location services.. 4.1 Detection of a Mobile Client A MCD can be implemented as the middleware for detecting the movement of the MTs and identifying the MTs. Once an MT enters the coverage area of a BSS supported by an AP, the corresponding MCD is able to actively detect such a movement. The feature of the implemented MCD is such that any mobile client, with the standard IEEE 802.11 connectivity, can be detected without the need of any client-side software installation. The second functionality of the MCD is to transfer the detected MAC address of an MT to the LAL address in the system. An LAL address is assigned to each MT for identification and location queries. In our system, the Mobile IP protocol [9] is adopted for LAL address identification. Namely, the LAL address of an MT is the IP address that keeps unchanged when a user roams around different ESSs. The MCD tackles the transformation of an MAC address to an IP address by cooperating with the foreign agent (FA) in the Mobile IP protocol. In addition, the MCD is also responsible for registration of the user location information to the ESS server. 4.2 Location Management Upon the recipient of a location registration message from the MCD, the ESS server updates the location information to the visitor list and then passes the location information to the LAL server. The visitor list is used to speed up the intraESS location query process in which the requests are made from and to BSSs within the same ESS. The LAL server not only manages the inter-ESS location information but also serves as the portal for location queries from DWC. The user registry database attached to the LAL server stores the BSS locations (i.e. APs) of all the MTs in the system. Each location query from the DWC with the identification of an MT initiates the location tracking procedures in the LAL server. Finally, the location of a mobile client can be obtained by querying the user registry. Location deregistration procedure is used to update the. Location Prediction Module for PCS Networks. The proposed LPM consists of two phases: the off-line rule mining phase and the on-line rule matching phase. The mining engine in the off-line phase is responsible for mining out new rules from the transactions log files. The operation of mining is performed periodically in time or when the number of new transactions exceeds a certain amount. A transaction specifies the time of issuing a request, location of making such a request, service type, and etc. The rule mining is performed on a per user basis. Upon the arrival of a request, the prediction module in the on-line phase matches the request with the association rules generated off-line by the mining engine. It prunes away the un-matched rule to obtain the matched rules. Based on the confidence value of matched rules, the location of the client is predicted. 5.1 Cost Model for the LPM In a regular PCS procedure, messages are sent to the HLR/HSS for requesting the routing information and then the connection request is delivered to the right PCS cell according to the information provided by the HLR/HSS. Let Cq be the cost of querying the HLR/HSS to obtain the location information, and Cn be the cost of the connection signaling to the right cell in which the mobile user resides. The total cost of a regular PCS procedure, Cr , can be expressed as C r = Cq + C n. (5). On the other hand, in the LPM scheme, connection request is sent to the predicted location first. If a location hit occurs, then the procedure terminates with a lower cost. However, if the prediction results in a location miss, the regular PCS procedure is required to obtain the correct location and perform the signaling. Therefore, the cost of the prediction-based LPM procedure, C p , can be computed as C p = ψ p · Cn + (1 − ψ p ) · (Cw + Cq + Cn ). (6). in which ψ p is the probability of a location hit and Cw is the cost of signaling procedure to the wrong cell. To make the prediction feasible, it is easy to see that C p < Cr . The following inequality can be derived from equations (5) and (6), ψp >. Cw Cq + Cw. (7).
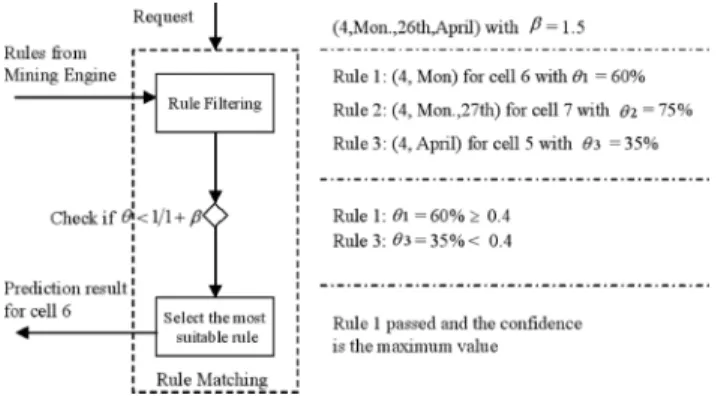
(5) IEICE TRANS. COMMUN., VOL.E88–B, NO.2 FEBRUARY 2005. 720. We assume that Cq is constant for all HLR queries, and the cost to a wrong cell and to a right cell is identical, i.e. Cw = Cn . Let Cq = βCn , then equation (7) can be re-expressed as θ>. 1 1+β. (8). 1 in which 1+β is the LPM to the regular PCS cost ratio, and θ is the confidence value of the association rule that is used to make the location prediction.. 5.2 Mining and Rule Matching Let I = {i1 , i2 , . . . , im } be a set of items. Let S be a set of transactions in the log files, where each transaction κ is a set of items such that κ ⊆ I. And, if e is a set of items in I, then e ⊆ κ defines that a transaction κ contains e. An association rule is an implication of the form X ⇒ Y, where X ⊂ I, Y ⊂ I, and X ∩ Y = ∅. The rule X ⇒ Y holds in the transactions set D with confidence θ(0 ≤ θ ≤ 1) if 100 × θ out of 100 transactions in D contain X also contain Y. The rule X ⇒ Y has support π(0 ≤ π ≤ 1) in the transaction set D if 100 × π out of 100 transaction sets in D contain X ∪ Y. In the proposed scheme, the a priori algorithm [10], [11] is adopted to mine out the association rules from transactions. The values of minimum support and minimum confidence are defined to obtain association rules. In our scheme, the output rule takes the form of “(n − 1) ⇒ l” in which n and l indicate the matching itemset and the location field respectively. It means that if the itemset (n − l) is matched, there is a probability θ such that l will occur with (n − l). Therefore, the confidence value θ of a rule can be regarded as the successful prediction probability for the MT to appear in the PCS cell l. As shown in Fig. 5, each rule is examined with the input request. Rule 2 is filtered out since the field of the 27th of the day is not consistent with the input request. Only the matched rules (Rules 1 and 3) are checked to see whether the 1 or not. The cell with the confidence value is greater than 1+β maximum confidence value and satisfying the equation (8) is returned as the prediction result. If the prediction results in null answer or if a location. Fig. 5. Flow chart of rule matching with an example.. miss occurs, the regular PCS procedure is required to obtain the current location of the client. It can be seen that a high location hit ratio improves the performance of location management bypassing the regular PCS procedure. 6.. Numerical Results. In this section, we investigate the effects of the TL method and the LPM mining schemes. These effects are demonstrated by comparing the hit probability and the cost ratio. In addition, we provide numerical evaluation to demonstrate the performance of the proposed integrated location management mechanism for heterogeneous wireless networks as well. 6.1 The TL Method in DWC In this section, we assume that the MT is known to reside in an ESS. This assumption will be released in Section 6.3. The TL hit probability ψt depends on various parameters that include the cost ratio 1/α explained in Section 3.1; the inter-arrival time ε of a location request explained in Section 3.2. We assume the inter-arrival time of the location requests has the Poisson distribution with mean 1/λ. First, we investigate the effect of changing the cost ratio 1/α, and the request ratio defined as λ/µ on the TL hit probability ψt . The size of an ESS is set to 10 × 10. The request ratio varies from 0.1 to 2.0. Four different values of the cost ratio 1/α are studied. They are 1/1.5, 1/2.0, 1/2.5, and 1/3.0. In this subsection, we consider the situation in which the MT is known to reside in an ESS. Namely, as shown in Fig. 3, the probability of “invalid record” is not accounted for here. A throughout investigation of the complete DWC scheme by taking the TL and LPM schemes altogether will be presented in Section 6.3. A location hit is counted if the condition check in equation (4) is greater than 1/α and the MT is indeed found in the ESS; otherwise, a location miss is counted. One simulation run terminates when a miss occurs and the MT is found to leave the ESS. The experimental results are obtained from the average of 5000 simulation runs in which the MT is simulated to start randomly in one of the BSSs and follows the random walk model [9] with the probability of 1/4 to choose one of four possible directions until the MT leaves the border of the ESS. Fig. 6 shows the TL hit probability ψt for L × W = 10 × 10. The TL hit probability at the low request ratio of 0.1 is 0.732 when α = 2.0. When the request ratio reaches to 2.0, the probability is 0.976 that approximates to 1. These results exemplify that the proposed TL method is capable of taking the property of temporal locality and utilizing the probability model to determine the availability of a WLAN. Based on the hit probability ψt , the TL cost Ct defined in equations (2) is computed. Fig. 7 shows the cost ratio Ct /C p versus request ratio λ/µ. As the value of α and the request ratio increases, the cost ratio decreases. When α = 3.0, the cost ratio is near 0.38 for the request ratio equal to.
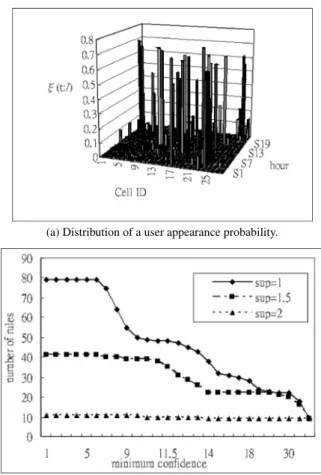
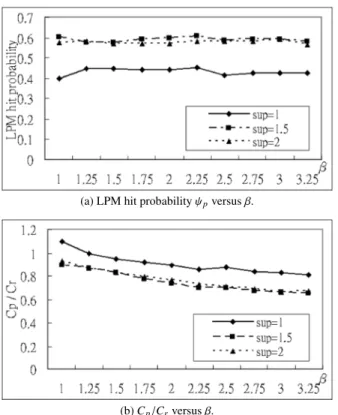
(6) CHENG et al.: AN INTEGRATED LOCATION MANAGEMENT SCHEME. 721. Fig. 6. Fig. 7. TL hit probability ψt versus request ratio.. TL to LPM cost ratio Ct /C p versus request ratio.. (a) Distribution of a user appearance probability.. (b) Number of rules mined out versus minimum confidence. Fig. 8. 1. It justifies that the TL method can be useful when the temporal locality exists and the cost of locating an MT by LAL is less than that by the PCS procedure. In addition, the cost ratio is reduced further when the size of an ESS is bigger. 6.2 The Rule Mining and Matching Scheme in the LPM Association rules are mined out by using the mining algorithm based on the log file. To simulate the temporal locality, the log file consists of the synthetic data that follows the distribution shown in Fig. 8(a). The probability for an MT to appear at a time t and at a cell l is given by ζ(t, l). Totally, 24 hours and 28 cells are considered. Namely, 1 ≤ t ≤ 24, and 1 ≤ l ≤ 28. Given any hour t, we assume the probability for the user to appear at one or two out of 28 cells is much higher than that at other cells. Therefore, the value of ζ(t, l) with much higher value ranges from 0.4 to 0.7, while the other values of ζ(t, l) ranges from 0 to 0.05, so that. Based on the distribution of ζ(t, l), 1,00,000 transactions are generated in the log file to simulate the movement of the MT for the schedule of a day. The number of rules mined out from the log file depends on the values of minimum support and minimum confidence as illustrated in Fig. 8(b). Three curves are shown in which the values of minimum support are set to 1, 1.5, and 2 respectively. As the value of minimum confidence increases,. LPM experiment settings.. the number of rules decreases. It is because, as the value of the minimum confidence increases, fewer rules have the confidence value θ exceeds the minimum confidence. For example, consider the case in which the minimum support is 1. The numbers of rules are 79, 50, and 32 for the minimum confidence equals to 0.05, 0.10, and 0.15 respectively. When the number of rules equals 50, the average number of rules for each hour is about 2.1. In the following experiments, the minimum confidence value is set to 0.10. The LPM hit probability ψ p and the LPM cost C p de1 and the associapend primarily on the LPM cost ratio 1+β tion rules. We investigate the effect of changing the value of on the LPM hit probability ψ p . Setting the minimum support value to 1, 1.5, and 2, Figs. 9(a) and 9(b) show ψ p and C p /Cr versus β respectively. It can be seen that ψ p reaches a higher value when minimum support value is bigger. On the average, ψ p is about 0.6 for the cases when the minimum support value = 1.5 and 2. In all three cases, C p /Cr is less than 1 when β is greater than 1.25. The experiments illustrate that the proposed LPM scheme is capable of utilizing the data mining techniques and taking the association rules to match the location request. Consequently, the LPM cost C p is less than the regular PCS procedure cost Cr ..
(7) IEICE TRANS. COMMUN., VOL.E88–B, NO.2 FEBRUARY 2005. 722. (a) LPM hit probability ψ p versus β.. Fig. 10. DWC probability ψ p versus request ratio.. (b) C p /Cr versus β. Fig. 9. LPM performance.. 6.3 The Integrated Location Management In Section 6.1, an assumption is made about the residence of an MT in an ESS so that the TL hit probability ψt is evaluated. Here, we consider the DWC probability ψd that indicates the probability for a user to stay in an ESS upon the arrival of a location request. The value of ψd depends on the distribution of ESSs in the geographical areas. In the simulation, we assume ESSs are deployed in 7 out of 28 cells as shown in Fig. 1. To match the transactions in the log file, the cells with top seven peaks of ζ(t, l) in Fig. 8(a) are considered to be the places for ESSs. If the MT was known to reside in a cell that has an ESS inside, then the current location request shall be handled by the TL method to determine whether the MT is still in the ESS or not. Therefore, the probability ψd is calculated as the number of requests that shall be handled by the TL method over the total number of location requests. Fig. 10 shows the probability ψd for L×W = 10×10. It can be seen that, for the geographical area shown in Fig. 1, in approximately 45% of the time, the user is found to reside in an ESS. It means the integrated location management mechanism is able to locate an MT more precisely in 45% of the overall requests. It can also be observed that the probability ψd is less sensitive to the changes of α when the request ratio is greater than 0.5. The overall cost ratio Cd /Cr is calculated based on equations (1), (2), (5), and (6) as a function of α and β. Fig. 11 shows Cd /Cr versus request ratio for β = 2 in which L × W = 10 × 10 and minimum support is set to 1.0. Four curves in the figure show the value of Cd /Cr versus request. Fig. 11 Overall DWC to the regular PCS cost ratio Cd /Cr versus request ratio for 10 × 10.. ratio when α = 1.5, 2.0, 2.5 and 3.0 respectively. It justifies that the proposed location management mechanism achieves a lower cost than the regular PCS procedure does. 7.. Conclusion. In this paper, we introduce an integrated location management mechanism for heterogeneous wireless networks that include PCS networks and WLAN. Three major functionalities of the location management mechanism are the DWC for an MT, the LAL scheme for the WLAN, and the LPM for PCS networks. It is demonstrated that the TL method used in the DWC is capable of taking the property of temporal locality and utilizing the probability model to determine the availability of a WLAN. The location management for WLAN is realized through the LAL scheme. In addition, based on the data mining technique, the LPM scheme for PCS networks is developed. In summary, the numerical results demonstrate that the integrated location management mechanism not only determines the location of the MT more precisely but also reduces the cost of locating. References [1] A. Bhattacharya and S.K. Das, “LeZi-update: An informationtheoretic approach to track mobile users in PCS networks,” Proc. Ann. International Conference on Mobile Computing and Networking, pp.1–12, Aug. 1999. [2] T.X. Brown and S. Mohan, “Mobility management for personal.
(8) CHENG et al.: AN INTEGRATED LOCATION MANAGEMENT SCHEME. 723. [3]. [4] [5] [6]. [7]. [8]. [9] [10]. [11]. [12]. communications systems,” IEEE Trans. Veh. Technol., vol.46, no.2, pp.269–278, May 1997. I.F. Akyildiz and W. Wang, “A dynamic location management scheme for next-generation multitier PCS systems,” IEEE Trans. Wirel. Commun., vol.1, no.1, pp.178–189, Jan. 2002. EIA/TIA, “Cellular radio telecommunication intersystem operation,” Technical Report IS-41 Revision C, EIA/TIA, 1995. Y.-B Lin, “Reducing location update cost in a PCS network,” IEEE/ACM Trans. Netw., vol.5, no.1, pp.25–33, Feb. 1997. Y.-B. Lin, “Determining the user locations for personal communications services networks,” IEEE Trans. Veh. Technol., vol.43, no.3, pp.466–473, Aug. 1994. T. Liu, P. Bahl, and I. Chlamtac, “Mobility modeling, location tracking, and trajectory prediction in wireless ATM networks,” IEEE J. Sel. Areas Commun., vol.16, no.6, pp.94–102, Aug. 1998. P.G. Escalle, V.C. Giner, and J.M. Oltra, “Reducing location update and paging costs in a PCS network,” IEEE Trans. Wirel. Commun., vol.1, no.1, pp.200–209, Jan. 2002. C. Perkins, “IP mobility support for IPv4,” IETF RFC 3344, Aug. 2002. R. Agrawal and R. Srikant, “Fast algorithm for mining association rules,” Proc. 20th VLDB Conference, Santiago, Chile, pp.487–499, Sept. 1994. S. Orlando, P. Palmerini, and R. Perego, “Enhancing the apriori algorithm for frequent set counting,” 3rd International Conference on Data Warehousing and Knowledge Discovery, pp.71–82, 2001. J.M. Gil, C.Y. Park, C.S. Hwang, D.S. Park, J.G. Shon, and Y.S. Jeong, “Restoration scheme of mobility databases by mobility learning and prediction in PCS networks,” IEEE J. Sel. Areas Commun., vol.19, no.10, pp.1962–1973, Oct. 2001.. Sheng-Tzong Cheng received the B.S. and M.S. degrees in Electronic Engineering from the National Taiwan University, Taipei, Taiwan, in 1985 and 1987, respectively. He received the MS and PhD degrees in Computer Science from the University of Maryland, College Park, MD, in 1993 and 1995, respectively. He is currently an associate professor in the department of Computer Science and Information Engineering, National Cheng Kung University, Tainan, Taiwan. His research interests are in design and performance analysis of mobile computing, wireless communications, and multimedia.. Chih-Hsiung Tseng received the B.S. degree in Statistics and Information Science from Fu Jen Catholic University, in 2000, the M.S. degree in Mathematic Science from Aletheia University, Taiwan, in 2002. He is currently working toward the Ph.D. degree in the Department of Computer Science and Information Engineering, National Cheng Kung University, Tainan, Taiwan. His research interests include wireless communications, mobile agent and smart home networking.. Ming-Tzung Hsieh received the B.S. degree in Applied Mathematics from Tatung Institute of Technology, Taipei, Taiwan, in 1989, and the M.S. degree in Computer Science and Information Engineering from National Chiao Tung University, Hsinchu, Taiwan, in 1991. He is currently working toward the PhD degree in Computer Science and Information Engineering at National Cheng Kung University, Tainan, Taiwan. His research interests include wireless communication networks and mobile computing..
(9)
數據

相關文件
Other than exploring the feasibility of introducing a salary scale for KG teachers, we also reviewed the implementation of the Scheme in different areas including funding
In this talk, we introduce a general iterative scheme for finding a common element of the set of solutions of variational inequality problem for an inverse-strongly monotone mapping
The difference resulted from the co- existence of two kinds of words in Buddhist scriptures a foreign words in which di- syllabic words are dominant, and most of them are the
• developing coherent short-term and long-term school development plan that aligns the school aims, the needs, interests and abilities of students in accordance with the
Experiment a little with the Hello program. It will say that it has no clue what you mean by ouch. The exact wording of the error message is dependent on the compiler, but it might
Since the sink is aware of the location of the interested area, simple greedy geographic routing scheme is used to send a data request (in the form of
In this thesis, we have proposed a new and simple feedforward sampling time offset (STO) estimation scheme for an OFDM-based IEEE 802.11a WLAN that uses an interpolator to recover
According to the problem statement and literature reviews, several functionalities are identified for the proposed CBI-PSP, including: (1) a knowledge classifications scheme