國
立
交
通
大
學
資訊科學與工程研究所
博
士
論
文
一個隨意網路上跨層設計的通用同儕平台
A generic peer-to-peer platform based on cross-layer design in ad-hoc
network
研 究 生:郭俊利
指導教授:陳耀宗 教授
A Generic Peer-to-Peer Platform Based on Cross-Layer Design in Ad-Hoc
Networks
研 究 生:郭俊利
指導教授:陳耀宗
國 立 交 通 大 學
資 訊 科 學 與 工 程 研 究 所
博 士 論 文
中華民國一百零二年六月
A Generic Peer-to-Peer Platform Based on Cross-Layer Design in Ad-Hoc
Networks
Student: Jun-Li Kuo
Advisor: Yaw-Chung Chen
A Dissertation Submitted to
Institute of Computer Science and Engineering College of Computer Science
National Chiao Tung University In partial Fulfillment of the Requirements
for the Degree of Doctor of Philosophy
in
Computer Science
Hsinchu, Taiwan
一個隨意網路上跨層設計的通用同儕平台
學生: 郭俊利
指導教授: 陳耀宗 博士
國立交通大學資訊科學與工程研究所
摘要
「行動隨意網路」不用任何網路基礎建設佈建,即可以發展隨取需求與自成結構的網 路,因此行動隨意網路適合用於軍事、緊急救援、警消等艱困任務的環境,隨著行動隨 意網路的發展,「同儕計算」已被論證為一種管理行動無線裝置的有效方法,這類的解 法或網路架構稱為「行動隨意網路上的同儕管理系統」。然而截至目前為止,整合同儕 應用服務與行動環境的網路架構仍然存在一些問題,例如:高度封包遺失率、缺乏跨層 修復能力、低弱的服務持續性,這些缺點都會對這類網路架構造成不良的影響。而且目 前的系統都只適合少數的客戶需要特定的服務,所以我們設計一個跨層演算法以解決上 述的問題,並實作一個同儕計算平台來整合檔案分享與影音串流的應用服務,因為同時 改善緩衝機制、排程演算法、跨層結構,這個同儕計算平台可支援高度擴充性與各式各 樣的同儕軟體應用。 在這個研究中,跨層設計整合了同儕計算的跨層與路由連線的網路層,並且結合同 儕轉傳路線與連點路由途徑,如此一來,我們的方法同時擁有路由表與指向表的資訊, 加上使用第六版網際網路協定的行動路由特性,能夠達成跨層的鄰似性,這種鄰似性可 以提高封包傳輸的成功率、跨層修復能力、服務的持續性。由於上面所提及的優點,我 們稱此方法為「通用同儕行動隨意網路系統」,能夠降低封包傳輸的失敗率與網路流量 負擔,進而提升服務品質。 首先,我們研究分析很多行動隨意網路上同儕管理系統的演算法,然後設計出所提的跨層體制,這是非常適合高度擴增性和多群體的使用者。第二,我們設計緩衝機制、 排程演算法、跨層結構等元件,讓各種同儕分享軟體都能適用。第三,我們推導數學模 組和理論公式來量化系統的延遲時間和負載量,用理論的分析評估所提方法效能的極 限。最後,我們實作所提方法在網路模擬器上,論證模組與公式的正確性,經由模擬結 果討論系統效能的改善程度,必且依照模擬結果調校參數,使得系統最佳化。 總而言之,我們提出跨層式的行動隨意網路搭載同儕管理協定,也就是通用同儕行 動隨意網路系統,所有同儕分享軟體皆能適用。這套協定不僅能增進封包傳輸的成功率 與跨層的修復能力,還能提高服務的持續性,使用很低的成本即能夠發展行動多媒體分 享服務。
A generic peer-to-peer platform based on cross-layer design in ad-hoc networks
Student: Jun-Li Kuo
Advisor: Dr. Yaw-Chung Chen
Institute of Computer Science and Information Engineering
National Chiao Tung University
Abstract
Mobile ad hoc network (MANET) can be employed to develop on-demand self-organized network without the support of infrastructure. Therefore, MANET is suitable for certain hard task forces, such as military, emergency rescue, and police. With the development of MANET, P2P solution has been demonstrated to be an efficient technique for the management of wireless ad hoc nodes. P2P-MANET (P2P over MANET) has appeared in this kind of network architecture. However, there are several problems in the integration of P2P applications and mobile environment so far. High packet loss rate, low recovery, and low continuity degrade the performance of P2P-MANET. Currently the existing system is only limited in a single requirement for few particular users. Therefore, we design a cross-layer algorithm to solve the above mentioned problems, and implement a P2P platform to integrate file sharing and media streaming. We improve the methods for buffer, scheduling, and overlay to establish a P2P platform for the high scalability and the support of various P2P applications.
In this research, the cross-layer design integrates P2P overlay and routing layer, and combines P2P forwarding path and hop-by-hop routing path, such that there is the information of routing table in finger table. The characteristics of IPv6 mobile routing is used to achieve overlay proximity, which heightens packet delivery rate, recovery ability, and playback continuity. Due to above characteristics, we call the proposed scheme Generic P2P-MANET
System (GPMS). GPMS can reduce both packet failure rate and traffic overhead, which in turn improve quality of service.
First, we survey P2P-MANET algorithms, and design the cross-layer scheme, which is suitable for high scalability and large group of users. Second, we design the buffer, scheduling, and overlay, which is adaptable for all P2P cooperation. Third, we derive the mathematical model or theoretical formula to evaluate latency and overhead. Therefore, we can evaluate the limitation and basis of the performance. Finally, we use a network simulator, OMNet++, to demonstrate the correctness of model and formula. And we configure the parameters and optimize the proposed algorithms depending on the simulation results, which are used to discuss the performance and improvement.
In summary, we propose a cross-layer P2P-MANET protocol, GPMS, which is suitable for all P2P content sharing applications. The proposed scheme can improve packet delivery rate, recovery ability, and playback continuity to develop a media sharing service on mobile environment with affordable cost.
Acknowledgement
First, I thank my parents. They always encourage and support me for study. They give me a good family life and let me concentrate my attention on research. They tolerate my mistakes, forgive me, and believe for my successful graduation of Ph.D. degree. My father's consideration, my mother's love, and my sister's exhortation all help to complete the paper.
Second, I really thank my advisor, Prof. Yaw-Chung Chen. Because he teaches and guides me for the Ph.D. academia, I enjoy and learn much in my NTCU school life. He gave me valuable advice and encouraged me when I had trouble in research, he recommends me for some ways to career now, and he will help me in the future. He is a good teacher in my mind, and I see him as the great model, so I hope that I will be the successful follower of him.
Third, I sincerely thank my partner, Dr. Chen-Hua Shih. Because he always helps and encourages me in my research, I not only increase the network knowledge but also learn the skills of study and teach. Because he studied in Multimedia Communications Laboratory, I didn't feel alone in my student life and talked about everything in all ways. We have studied together for twelve years. He is not only a friend but also a teacher for me. He exists, the paper exists.
Finally, I specially express my thanks to my girl friend, Chia-Ning Lee. She gives me smile and stands me for every useful thing. She understands my ambition of research and is willing to accompany me and wait for me. She always stands by my side to bring me happiness. Her consolation and encouragement surrounds me every time and everywhere. I really treasure her love in my life. Without her love, I cannot finish my Ph.D degree.
Table of Contents
1. Introduction ... 1 1.1. Background ... 2 1.2. Problem ... 4 1.2.1. Continuity ... 5 1.2.2. Scalability ... 5 1.2.3. Mobility ... 6 1.2.4. Proximity ... 6 1.3. Motivation ... 7 1.4. Goal ... 8 2. Related Works ... 10 2.1. P2P-MANET scheme ... 10 2.1.1. DHT ... 112.1.2. AODV and OLSR ... 11
2.2. P2P-MANET taxonomy ... 13 2.3. P2P-MANET application ... 15 2.3.1. File sharing ... 15 2.3.2. Voice communication ... 16 2.3.3. Video streaming ... 18 2.4. Middleware design ... 19
2.5. IPv6 routing header ... 20
2.6. Anycast ... 21
2.7. Delivery strategy... 22
3. The Proposed Scheme ... 24
3.1. System overview ... 24
3.2. Finger plus routing table ... 25
3.3. Cross-layer scheme ... 26
3.4. Routing algorithm ... 28
3.5. GPMS design ... 30
3.6. Peer departure and mobility ... 37
3.8. Anycast algorithm ... 40 3.9. Dynamic buffer ... 43 4. Analysis ... 45 4.1. Routing complexity ... 45 4.2. Maintenance load ... 46 4.3. Routing overhead ... 46 4.4. Compared schemes ... 48 5. Results ... 50 5.1. File sharing ... 50 5.2. Voice Communication ... 53 5.3. Video streaming ... 55 5.4. Signaling overhead ... 58 6. Discussion ... 61 6.1. Conclusion ... 61 6.2. Future work ... 62 7. Appendix ... 63 Reference ... 66
List of Figures
Figure 2.1: The basic key-based forwarding scheme of DHT ... 12
Figure 2.2: The selection of routing path in AODV ... 12
Figure 2.3: The maintenance of routing table in OLSR ... 13
Figure 2.4: The network constructions of P2P-MANET protocols ... 14
Figure 2.5: The integrated network stack of MADPastry ... 16
Figure 2.6: The cross-layer architecture of CLAPS ... 18
Figure 2.7: The network layer of MP2PS ... 19
Figure 2.9: An example of IPv6 routing header ... 21
Figure 2.8: IPv6 routing header format ... 21
Figure 3.2: The proposed cross-layer scheme (GPMS) ... 25
Figure 3.1: Relationship between the logical overlay and the physical topology ... 25
Figure 3.3: The FPRT update between overlay tier and routing tier ... 27
Figure 3.4: The proposed FPRT over IPv6 routing ... 28
Figure 3.5: The pseudo packet structure of GPMS ... 30
Figure 3.6: The finite state machine or lifecycle of peer ... 31
Figure 3.7: The normal message flow of GPMS ... 31
Figure 3.8: The abnormal message flow of GPMS ... 32
Figure 3.9: The finite state machine or lifecycle of download task ... 33
Figure 3.10: The finite state machine or lifecycle of upload task ... 34
Figure 3.11: The message flow of GPMS ... 35
Figure 3.12: The overlay maintenance and recovery of GPMS ... 36
Figure 3.13: (a) The physical topology of ad hoc network; (b) The P2P overlay ... 39
Figure 3.14: (a) The stream flow via DHT over AODV; ... 39
Figure 3.16: FPRT process to service cache and query ... 41
Figure 3.17: The proposed algorithms of query process ... 42
Figure 5.1: The simulation environment ... 51
Figure 5.2: Download completion time vs. the number of nodes ... 52
Figure 5.3: Download completion time vs. the moving speed ... 52
Figure 5.4: Download completion time vs. the churn rate ... 53
Figure 5.5: The amount of voice copies increases with the number of peers ... 54
Figure 5.6: Packet failure rate vs. the number of nodes ... 54
Figure 5.7: Packet failure rate vs. the moving speed ... 55
Figure 5.8: Packet failure rate vs. the churn rate ... 55
Figure 5.9: The packet loss at v = 36 m/s ... 56
Figure 5.10: The compared network stacks ... 56
Figure 5.11: Packet failure rate vs. the number of peers ... 57
Figure 5.12: Packet failure rate vs. the moving speed ... 57
Figure 5.13: Packet failure rate vs. the churn rate ... 58
Figure 5.14: Signaling overhead vs. the number of peers ... 58
Figure 5.15: Signaling overhead vs. the moving speed ... 59
Figure 5.16: Signaling overhead vs. the churn rate ... 60
List of Tables
Table 4.1: A summary of P2P over MANET schemes ... 46
Table 4.2: The comparison of schemes ... 48
Table 5.1: The parameters of simulation... 51
1. Introduction
As technology for high quality multimedia application prevails, everyone has been able to enjoy audiovisual communications and high definition video content through the wireless network. Mobile devices have been gaining popularity along with wireless multimedia services. Mobile access to the Internet via WiFi, WiMax, 3G, or LTE data network from the fixed infrastructure is prevalent. However, generally the traditional cellular-based architecture and infrastructure-based communication are not always adequate to satisfy users' requirements [1]. The limited bandwidth of the wide area cellular networks cannot offer good service quality. In many situations, the communications between mobile hosts neither rely on any fixed infrastructure nor the access to Internet. For example, the high cost or long setup time of a system installation may be unacceptable in the disaster areas and battle fields. It motivates mobile ad hoc network (MANET)1 which can be expected to operate in the infrastructure-less environment [2].
Wireless local area network (WLAN) provides both Internet accessibility and ad hoc availability for mobile devices. For example, WiFi and WiMax can support network capability without infrastructure in the ad hoc mode [3]. The ad hoc environment features the short delay of an installation without infrastructure cost. The ad hoc solution provides a private network to support on-demand multimedia sharing. The advances in convenient access technologies and high bandwidth availability generate new opportunities to deliver high quality, on-demand, and interactive multimedia applications.
The words ad hoc imply that the network is formed in a spontaneous manner to meet an immediate demand. In MANET, two mobile nodes can communicate with each other through other intermediate nodes over wireless infrastructure-less network without the centralized
1 The creation in 1997 of an IETF working group (called MANET WG) triggered an era of research in these
administration.2 The nodes organize a cooperative network to establish communications with low setup cost and short startup delay. Store-and-forward mechanism is the basic method to transmit data in MANET. The cooperation network uses the decentralized scheme to share data in small scale for the specific purpose.
Users can share resources and files through MANET via application-layer broadcasting or multicasting. However, the inefficient flooding delivery leads to the low data rate in MANET. While the traditional server-client or one-to-many delivery model is not satisfactory to the requirement of multimedia service. A single node is impossible to handle the global load of the multimedia service, hence a decentralized approach like peer-to-peer (P2P) technology could be an appropriate solution adopted in such environment [4]. P2P solution can disperse the centralized actions in traditional network to let the edged terminals connect to each other without central control. P2P solution can alleviate single point of failure and overhead on server.
1.1. Background
Like a peer in P2P application, a mobile node simultaneously plays the roles of server, router, and client. When the mobile node acts as the role ofa server, it may be an agent, an anchor, or a repository of WLAN, and becomes the source to provide data. When the role of a mobile node is a router, it may be an intermediate node on communication, and becomes the relay to forward data. When the mobile node acts asa client, it may be an end user or a receiver, and becomes the terminal to query and download data.
Like MANET, P2P network is established as a service-oriented overlay to share data. Peers always collaborate with each other without any centralized server.3 Therefore, how to
2 A node can communicate with other nodes within its radio range directly or the ones out of its radio range
indirectly through multi-hop relay.
keep the scalability and how to deliver data efficiently are important to both P2P and mobile networks. In order to achieve high scalability and efficiency, more and more P2P applications have been implemented in wireless network in recent years, such resolutions can be called mobile P2P (MP2P), wireless P2P (WP2P), or P2P over MANET (P2P-MANET).
Both P2P and MANET share some fundamental commonalities such as decentralized and self-organized architecture due to the lack of central server, therefore MANET and P2P systems both exhibit a dynamic organization and lack information of user arrival or departure a priori. There are some similarities between MANET and P2P.
(1) A peer should collaborate with each other without a centralized server.
(2) A peer operates as both host and routing node, as well as sender and receiver in both systems.4
(3) The overlay of P2P and topology of MANET is changing frequently due to the high churn rate.5
(4) In both MANET and P2P, scalability is the basic requirement.
(5) How to deliver or route data efficiently is crucial for both P2P and MANET.
However, P2P and MANET techniques have been developed by different communities and address entirely different requirements. MANET first appeared as DARPA packet radio networks in the early 1970s. P2P systems were initiated in the middle of 1990s. P2P systems are application-oriented overlays and have evolved mainly over the wired Internet so far. By contrast MANET is spontaneous, infrastructure-less wireless networks for mobile terminals. Therefore, P2P systems are unsuitable for MANET because P2P overlay is based on TCP/IP wired network, but the links of MANET change frequently due to the mobility of its wireless nodes. The other differences between P2P and MANET also obstruct the integration of P2P
4 Each peer acts both as a client and a server, or called servant.
5 The topology means the distribution of nodes in MANET physically, and the overlay means the distribution of
and MANET.
(1) P2P refers to the upper layer; MANET refers to the lower layer.
(2) In P2P, the logical routing path is established on overlay; while in MANET, the physical routing path is established on MAC layer.
(3) Every peer on P2P overlay can receive the incoming streams from multiple sources, but every node in MANET has to deal with the collision of packets from different sources. A fundamental characteristic of wireless networks is the time-varying and user-dependent fading channel. Mobile devices have the limited resources and bandwidth, and the bottleneck of data traffic causes quality of service (QoS) degradation of multimedia service. QoS requirement of multimedia traffic is strict (little loss, low delay and small jitter) and the nature of MANET is dynamic (fluctuating link quality and changing topology). Therefore, the dynamic multi-hop topology and fluctuating radio quality make it difficult for MANET to support various kinds of P2P traffic with acceptable QoS.
(1) MANET degrades the maintenance of P2P overlay due to the dynamic mobility problem.
(2) P2P overlay is not proximal to MANET topology, because it leads to the inefficient streaming delivery.
(3) The unreliable wireless links lead to the out-of-order congestion of multi-source P2P voice communications.
1.2. Problem
Several problems affect adversely data delivery performance when integrating P2P and wireless networks. The challenges of P2P-MANET are concerning both P2P and MANET, thus P2P-MANET needs to accommodate continuity, scalability, mobility, and proximity to support the multimediacontentsharing services.
1.2.1. Continuity
The peers in P2P-MANET leave and join on the go; the continuity means that a peer stays in the system continuously. The word churn describes the contrary behavior, or means that peers arrives and departs from time to time. In the application layer, a user can open or close the application anytime. In some cases, a peer can inform its neighbors gracefully when it joins or leaves the system. In other cases, a peer may turn off power or encounter an accidental crash, such that it leaves without any notification. In network layer, three situations regarding the peer churn problem can be categorized:
(1) The P2P application is terminated but the user still stays in the ad hoc network.
(2) User turns off the power and leaves both the P2P application and ad hoc network.
(3) User moves to another coverage area; this case leads to an ambiguous situation in which user leaves neither P2P application nor ad hoc network.
The peer churn is often unexpected a priori, and it destroys delivery overlay and breaks routing path. The churn is the most critical factor that affects the overall performance. Therefore, an integration of P2P-MANET protocol not only defines and addresses clearly the above situations, but also considers the peer churn problem.
1.2.2. Scalability
On logical overlay, the size of P2P-MANET varies constantly due to peer churn problem. In addition, the members of P2P-MANET changes dynamically. On physical topology, the size of ad-hoc area also varies due to the self-organized infrastructure-less environment. As a result, the basic scalability is necessary for P2P-MANET data sharing service. For P2P-MANET, the main concerns are scalability and robustness. In wired P2P network, the system concern is regarding the scale of million users. However, the scale for hundred users is sufficient in P2P-MANET. The major scalability issue of P2P-MANET system is the sudden
burst crowding problem.
1.2.3. Mobility
A major difference between wired and wireless P2P systems is the mobility in P2P-MANET. The traditional P2P system doesn't consider peer mobility because it is developed on the wired network, but the P2P-MANET mobility includes device's movement and hidden terminal problem. Hence, the P2P-MANET application needs a mobility detection mechanism to serve mobile users.
In most of P2P-MANET systems, a mobility detection function is used for monitoring peers' movements and checking peers' departures. The mobility detection includes the active notification and the reactive notification. In general, the more complicated mobility detection, the better the performance (i.e. mobility prediction), but it costs higher overhead on both computing at mobile terminal and network traffic.
1.2.4. Proximity
Unlike wired P2P application, a self-organized P2P-MANET system cannot rely on any form of offline knowledge and resource. Every peer has its own domain, which leads to a challenge to interact and communicate with each other. An inefficient organization results in poor routing.
How to find a mapping from physical topology to logical overlay is a shortcut to realize and solve the proximity problem. The mapping affects significantly how to establish routing path or multicast tree, and influences directly (QoS); users care about the downloading time when using file sharing service, whereas they care about the playback quality when using real-time streaming service.
1.3. Motivation
In all infrastructure-less environments, P2P applications can be implemented in MANET due to high mobility, low underlay cost, and short initiation delay. Especially the environments may be the applications of rescue and academia. In emergency rescue application, every rescuer carries the handheld device and search around in a large area. Every rescuer shares the pictures, gathers the statistics, communicates and shows live video with each other through P2P-MANET. The P2P-MANET technology replaces the satellite telephone to provide the triple-play and low-cost communication. In campus, every teacher and student uses the education multimedia service to share the teaching materials or build a virtual classroom. Everyone uses the handheld device to hold the grouping conference or multimedia multicasting without complex setup procedure.
Therefore, we would like to design a multimedia platform to provide common P2P services including file sharing, voice communication, and video streaming for emergency rescue and academia applications. The development of platform must consider the scalability and high churn rate. Since the P2P-MANET application discussed here tends to be applied to rescue and academia applications, the problems of continuity, scalability, mobility, and proximity must be overcome. Besides the above innate problems, the delivery method should be suitable for all situations, because the rescue application is usually situated in a space of limited users and large area, while the academia application is in a space of numerous users and small area. Therefore, the proposed scheme must consider the generic design of P2P overlay, delivery strategy, and ad hoc route.
In summary, in order to achieve P2P sharing service in wireless network, we want to design a generic P2P platform to support all P2P applications on MANET with affordable cost and short setup delay for high continuity, high scalability, high mobility, and high proximity. The achievement needs the cross-layer information between P2P overlay and ad hoc topology,
i.e. the upper tier needs not only logical metrics but also physical metrics, so does for the lower tier. Therefore, we motivate a cross-layer design to enhance the P2P-MANET platform. In our published works, the P2P applications of voice communication [b] and video streaming
[c] have been workable via cross-layer scheme.
1.4. Goal
We integrate the published works to present a cross-layer approach for P2P forwarding mechanism tailored to MANET. The proposed scheme tends to accommodate the file sharing, voice communication, and video streaming with high data rate and time sensitivity on P2P-MANET. The goal is to achieve the high continuity, high scalability, high mobility, and high proximity to shorten the routing propagation delay, as well as to reduce the signaling overhead.
The proposed scheme builds a service-oriented overlay to share data without any centralized server, and constructs the generic platform, which represents a middleware that combines the context-aware search, the cooperative data management, the anycast-based query, and the mobile P2P delivery. The proposed platform is independent of upper layer for P2P applications and lower layer for MAC protocols, so it is extendable for all kinds of P2P sharing services with high scalability and mobility.
The proposed scheme integrates P2P overlay into the cross-layer scheme to manage the ad hoc topology. Through P2P overlay, a virtual network can be formed in the long-term and large-scale perspective. The cross-layer design can deal with peer arrival and departure quickly and simply to shorten the service interruption time with minimal signaling overhead. The implementation of platform needs neither the complex multimedia mixer nor the connection-oriented delivery.
As above characteristics, we call the proposed scheme Generic P2P-MANET System (GPMS), which establishes an overlay on MANET, then builds a platform on the overlay, and
provides multimedia services on the platform. GPMS consists of five algorithms, the first algorithm maintains the application layer overlay which is proximal to physical layer topology6; the second algorithm provides an efficient routing via IPv6 to achieve the high data rate7; the third algorithm handles the interaction of cross-layer messages to keep an optimized shortest routing path8; the fourth algorithm uses anycast-based query to minimize the querying overhead; and the last algorithm schedules the source selection with dynamic buffering mechanism to avoid the performance degradation.9
The integration of P2P overlay and MANET routing can update the cross-layer information to reduce signaling overhead (control overhead), speed up recovery time, and improve delivery continuity or service stability. The integration also avoids the packet duplication problem because GPMS adopts neither the flooding algorithm nor the off-the-shelf P2P systems.
6
The algorithm of overlay proximity is published in IEICE Transactions on Communications [b].
7 The algorithm of IPv6 routing header is published in Ad Hoc Networks [c].
8 The algorithm of cross-layer scheme is published in IEICE Transactions on Communications [e].
9 The algorithm of dynamic buffering mechanism is published in International Journal of Intelligent Systems
2. Related Works
Because GPMS involves P2P overlay, mobile network, IPv6 protocol, and multimedia delivery, we discuss the P2P-MANET scheme, P2P-MANET taxonomy, P2P-MANET application, middleware design, IPv6 routing header, IPv6 anycast, and delivery strategy one by one.
2.1. P2P-MANET scheme
P2P-MANET application must take care of the P2P overlay and the ad hoc routing protocol. P2P networks can be roughly classified as either unstructured or structured network. Unstructured networks use the flooding algorithms, while structured networks use the distributed indexes. Generally speaking, unstructured protocols are extremely resilient, but they are inefficient for querying and sharing data. On the other hand, structured protocols are efficient to maintain the overlay, but they are unstable in the mobile environments.
• Unstructured P2P networks, such as KaZaA [5] and Gnutella [6], generally use flooding to search peers and files. Gnutella use the lifespan to limit the number of visited hops for application-layer flooding. The lifespan is usually set to 1 or 2 hops in wireless network. • Structured P2P networks use the finger table or distributed hash table (DHT) to locate
peers and files. DHT has proven to be an efficient solution for a variety of scalable and robust distributed applications, for example, CAN [7], Chord [8], and Pastry [9] have been used successfully in wired P2P network.
The ad hoc routing protocols can be classified into reactive and proactive routing protocols. • In proactive or table-driven routing protocols, such as DSDV (Destination Sequenced
node maintains a routing table10 with the global information of network topology. A node immediately sends packet to the destination without the delay for route discovery. But a lot of computing cost and control overhead is needed to maintain a dynamic routing table.
• The reactive or on-demand routing protocols, such as AODV (Ad hoc On demand Distance Vector) [12] and DSR (Dynamic Source Routing) [13], every mobile node finds a routing path only when it is necessary. But the sender must broadcasts the routing request throughout the whole network to select an appropriate path to the receiver. Reactive protocols have larger delivery delay and are not efficient for heavy traffic.
2.1.1. DHT
DHT inherits a hash table, which provides the lookup function inspired by a centralized server. In P2P network, responsibility for maintaining the mapping from keys to contents is distributed among the peers, in such a way that a change causes a minimal amount of disruption. Therefore, DHT is scalable for a large number of peers to handle peer arrivals, departures, and failures.
DHT constructs an overlay, which takes advantage of resources distributed across the Internet, such as bandwidth and hard disk capacity, to provide a multimedia service. As Figure 2.1 illustrated, the key-based forwarding scheme guarantees logarithm efficiency for table size, neighboring degree, lookup latency, and delivery overhead.
2.1.2. AODV and OLSR
10 Routing table is a data structure in the form of objects stored in each mobile node. The construction of routing
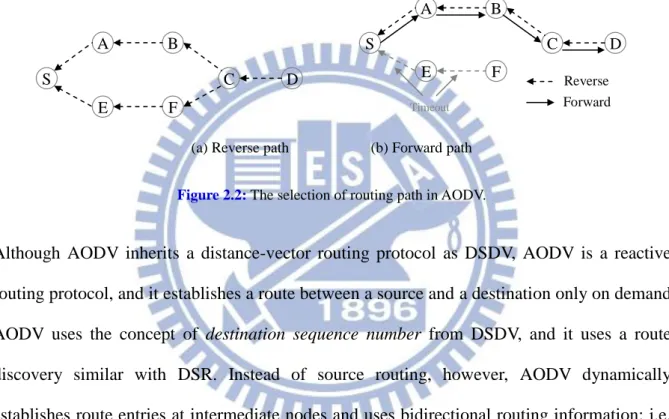
Although AODV inherits a distance-vector routing protocol as DSDV, AODV is a reactive routing protocol, and it establishes a route between a source and a destination only on demand. AODV uses the concept of destination sequence number from DSDV, and it uses a route discovery similar with DSR. Instead of source routing, however, AODV dynamically establishes route entries at intermediate nodes and uses bidirectional routing information; i.e. AODV uses the hop-by-hop routing. As Figure 2.2 (a) illustrated, the destination can set up a
reverse path via Route Request Message and Route Reply Message. Then the source and
intermediate nodes maintain the forward path via an unsolicited Route Reply Message with a fresh sequence number. Each node updates its routing information and propagates the message only if a greater destination sequence number than the previous message. The link is deleted after a timeout or a point failure in the forward path as Figure 2.2 (b) illustrated.
OLSR is a proactive link-state routing protocol, which disseminates link state information among individual nodes. OLSR is based on link state algorithm and optimizes the
lookup(54) N1 N8 N14 N21 N32 N38 N42 N48 N51 N56 K54 Finger table N8 + 1 N14 N8 + 2 N14 N8 + 4 N14 N8 + 8 N21 N8 + 16 N32 N8 + 32 N42 lookup(54) N1 N8 N14 N21 N32 N38 N42 N48 N51 N56 K54 Finger table N8 + 1 N14 N8 + 2 N14 N8 + 4 N14 N8 + 8 N21 N8 + 16 N32 N8 + 32 N42
Figure 2.1: The basic key-based forwarding scheme of DHT.
S A B C D E F S A B C D E F Reverse Forward Timeout
(a) Reverse path (b) Forward path
efficiency and economical flooding. OLSR uses the multipoint relay, which is selected for forwarding message and data. Only multipoint relay can forward data and Topology Control
Message, which is used to update the information of bidirectional link state. Thus, a routing
path is a sequence of hops from the source to destination through multipoint relays as Figure 2.3 illustrated.
2.2. P2P-MANET taxonomy
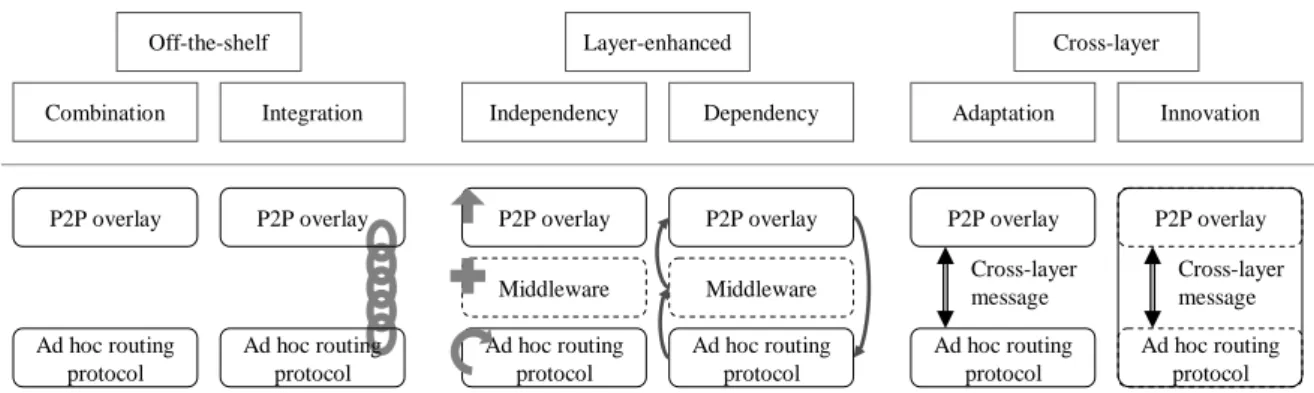
We classify the taxonomy of P2P-MANET protocols depending on the construction of network stack. Due to consideration of both P2P overlay protocol and ad hoc routing protocol, we can discuss the approach of interaction between the overlay tier and the routing tier, and categorize the existing protocols into three types: off-the-shelf scheme, layer-enhanced scheme, and cross-layer scheme.
First, the off-the-shelf scheme usually puts up the ready-made tools for a specific proposal, such as file sharing or video streaming. A well-known P2P overlay protocol can be combined with an ad hoc routing protocol to form the off-the-shelf scheme, which is easy to implement with affordable cost. The scheme can be divided into two classes: combination and
integration. The combination only considers the conformability of overlay tier and routing tier;
on the other hand, the integration fetches the features of P2P service and integrates with MANET. Data or message A B F C E G 2 3 3 1 1 1 4
Dest. Next Cost
B B 2
C C 3
E C 4
F C 4
G C 8
Dest. Next Cost
B B 2 C C 3 E C 4 F C 4 G C 8 A's table Multipoint relay
Second, the layer-enhanced scheme generally modifies either overlay protocol for mobile environment or routing protocol for P2P service. The modification of overlay usually costs additional recovery overhead; the modification of ad hoc routing usually costs specific point-to-point overlay path. This kind of scheme often depends on the existing protocols to enhance the QoS of P2P service. Although the modification can improve P2P system efficiency, it may change the network protocols and decrease its popularity. The scheme also can be categorized into two classes: independency and dependency. The independency considers the enhancement of one-sided tier, the overlay is independent of the routing algorithm; on the other hand, the dependency considers the coordination and enhancement of both tiers, the overlay is dependent on the routing algorithm.
Third, the cross-layer scheme mainly breaks the network stack to provide an interaction between the overlay tier and the routing tier via the additional cross-layer messages. The cross-layer messages usually include the information of overlay proximity and routing path. The scheme has a complex cross-layer algorithm and is incompatible with other P2P systems. The scheme can also be divided into two classes: adaptation and innovation. The adaptation regards adding the cross-layer messages on the original overlay tier or routing tier to adapt the cross-layer design; the innovation regards the novel cross-layer design for P2P-MANET.
As Figure 2.4 illustrated, P2P-MANET protocols can be classified into three categories based on their network constructions. In the Appendix below, we survey and classify the
Off-the-shelf P2P overlay Ad hoc routing protocol Combination Integration P2P overlay Ad hoc routing protocol Layer-enhanced Independency Dependency Cross-layer Adaptation Innovation P2P overlay Ad hoc routing protocol Cross-layer message P2P overlay Ad hoc routing protocol Cross-layer message P2P overlay Ad hoc routing protocol Middleware P2P overlay Ad hoc routing protocol Middleware
existing protocols via the categorization. We also list these protocols with their proposal date in order, and discuss solutions for the problems of continuity, scalability, mobility, and proximity.
2.3. P2P-MANET application
For the orientation of service, the P2P-MANET application is similar to wired P2P application. The application can be divided into three kinds: file sharing, voice communication, and video streaming.
2.3.1. File sharing
The kind of file sharing is the first application of wired P2P service. The file searching is completed quickly via the P2P overlay, which is constructed by finger table. The mobile P2P application inherits the advantage to develop the file sharing function.
M-CAN (Mobile-CAN) [14] is a modification based on CAN, which provides the P2P functions of registering, grouping, file transmission, caching, as well as the DHT functions. Every node is registered on one or several nearby super nodes, which are organized by CAN. The goal of M-CAN is to provide a fast lookup for file sharing on ad hoc network. The super node must index all neighborhood available files and handle all lookups, so the overhead of super node is obviously high.
MADPastry (Mobile AD hoc Pastry) [15] combines the DHT overlay, Pastry, and the ad hoc routing protocol, AODV, to reduce the overhead of peer lookup and routing maintenance. MADPastry uses Pastry proximity awareness to reduce the overhead without flooding. MADPastry is implemented at the network layer. MADPastry maintains three routing tables:
Pastry routing table, Pastry leaf set, and AODV routing table; those tables complete the indirect routing. Pastry routing table indexes and hashes the mobile nodes; Pastry leaf set
These routing tables can be updated via overhearing data packets, and the routing path without data flow is not monitored. The extension of MADPastry integrates three routing tables to provide interfaces to P2P application layer and MAC layer as Figure 2.5 illustrated. Its motivation is to avoid AODV route discovery, minimize overlay maintenance, and maximize available packet information. Because Pastry is suitable for the wired network, MADPastry performs poorly at high speed.
M-Chord (Mobile-Chord) [16] is a modification based on Chord. M-Chord is very similar to M-CAN and is inspired from the hierarchical architecture of M-CAN. M-Chord also uses the super node to associate with the ordinary nodes and manage the file indexes. Every super node needs to maintain the routing finger table and sharing files directory to achieve Chord's lookup and file sharing. The joining/leaving/routing/updating process of peer follows Chord and is similar with M-CAN. M-Chord combines the real and virtual split strategies to achieve a load balance and low overlay overhead.
2.3.2. Voice communication
The application connection of voice communication or group conference is established via Session Initiation Protocol (SIP) based on flooding-based multicast. A peer always floods the received data to other peers immediately. The hierarchy-based or cluster-based architecture is used to improve the efficiency of flooding delivery.
Pastry
Pastry leaf set Pastry routing table
AODV
AODV routing table
Ne tw o rk la y er Application layer MAC layer interface interface
Skype [17] can hold the voice communication or group conference through Internet.11 It classifies peers into two types: super peer12 and ordinary peer. The super peer is responsible for building P2P overlay and optimizing the routing path. Hence, a super peer is like a leader, which synchronizes voice data then sends it to ordinary peers through multicast.
Audio Conferencing Testbed (ACT) [18] is based on OLSR to set up a one-to-one or many-to-many communication in WiFi MANET. ACT uses the minimum spanning tree13 to minimize the latency of audio dissemination to the whole network. Every peer must maintain its minimum spanning tree to deliver data by itself. ACT predicts the disconnection and mobility to shorten the service interruption time.
CLAPS (Cross-Layer And P2P based Solution) [19] inherits the tree-based overlay and OLSR extension from MOST14 for real-time video streaming. CLAPS assumes that the physical routing topology can be provided by OLSR, which sends cross-layer message to optimize the overlay. The source peer maintains a minimum spanning tree as its overlay. The minimum cost is computed via link distance packaged in cross-layer message, and the spanning tree is recomputed periodically to keep the overlay proximity. To optimize the overlay proximity and avoid the overlap path in ad hoc routing, the candidate peers are selected as relay nodes on multicast paths according to the equal link distance. The cross-layer architecture of CLAPS is shown in Figure 2.6. In the simulation, CLAPS adopts UDP as transport layer protocol and WiFi as MAC layer protocol.
11 Skype cannot work if MANET cannot access Internet.
12 Any peer with a public IP address having sufficient CPU, memory, and network bandwidth is a candidate to
become a super peer.
13
Broadcast tree is the buzzword in ACT.
14 MOST (Multicast Overlay Spanning Tree Protocol) extends the OLSR unicast to support multicast routing. It
is a multicast routing protocol, not an overlay protocol. Although MOST uses the minimum spanning tree as its overlay, it does not consider P2P issues. However, the overlay of CLAPS is inspired from the spanning tree of MOST due to the multicast purpose.
2.3.3. Video streaming
Both live streaming and video on demand (VoD) are the applications of video distribution. However, supporting live streaming is more difficult than supporting VoD due to the instant factor.15 The audiences cannot tolerate any sensible lags in such live programs. Therefore, how to continue the stream smoothly and deliver it efficiently among the peers is important to use P2P solution.
Smart Gnutella [20] enhances the original Gnutella for MANET and the real-time application.16 Smart Gnutella inherits the ultrapeer from the wired Gnutella. The ultrapeer must manage the neighborhood leaf peers and support the multicast communication in Smart Gnutella. In order to meet the wireless and mobile environment, Smart Gnutella defines three message types (ping/pong, welcome, and broadcast) and four node states (full, stable,
connecting, and idle). The application-layer QoS can be monitored via ping/pong; the peer
discovery and connection maintenance can be established via welcome; the node states can be updated via broadcast.
As Figure 2.7 illustrated, MP2PS (Mesh-based P2P Streaming) [21] provides real-time
15 The live streaming service usually provides the live sports games, the first-hand stock information, or the
latest news.
16Gnutella is designed for file sharing in the wired network. Smart Gnutella is designed for QoS-sensitive
collaborative virtual environment on MANET.
MOST UDP Live video application
OLSR WiFi
Link distance
streaming with scalability and availability over MANET.17 MP2PS adopts mesh-based live streaming application, Joost,18 and no retransmission on wireless network, UDP, and on-demand ad hoc routing protocol, AODV.
2.4. Middleware design
The middleware between application layer and MAC layer is proposed to provide a mobile P2P platform [22]. The middleware is an integrated dependency of overlay tier and routing tier, and it is independent of P2P service and wireless technology [23]. The different kinds of P2P applications and wireless accessibilities are workable and compatible under the middleware. For example, MAPCP (MANET Anonymous P2P Communication Protocol) [24] is a middleware between the P2P applications and ad hoc routing protocols. MAPCP consists of two phases and two tables: a destination table records the results of query in the query phase, and a path table records the information of multiple paths in the data transmission phase. P2P-HWMP (P2P over Hybrid Wireless Mesh Protocol) [25] exploits the route discovery functionality and information provided by the underlying routing layer to improve the P2P search performance, and it collates the routing information to get the overlay proximity.
Therefore, a middleware platform should consider the additional adaptability, extensibility, and interoperability besides the issues of continuity, scalability, mobility, and proximity.
17 MP2PS suggests a protocol stack for multimedia streaming, and its mesh overlay doesn't consider the
proximity. The ready-made protocols don't consider the streaming continuity.
18 Joost is a Video-on-Demand P2P system for distributing TV content, created by Skype and KaZaA founders.
Its P2P protocol shares the library with Skype.
Joost UDP AODV
IP WiFi
• Adaptability: P2P overlay is self-organized and independent of routing topology, it is also self-organized without any central administration or control. The wired P2P forwarding protocol leads to the far routing problem19 due to the lack of overlay proximity, i.e. an inefficient organization leads to a poor P2P routing. Therefore, the mobile P2P resolution must be adaptable for dynamic environment.
• Extensibility: How to integrate with P2P overlay and routing topology to deal with a general purpose system is important in the mobile P2P solution. The extensibility describes the generic integration of P2P application on mobile device, but the mobile P2P scheme are often inherited from wired P2P scheme. Therefore, the mobile P2P solution must improve the extensibility to increase the popularity and flexibility.
• Interoperability: The mobile P2P applications should be service-oriented, but they are usually developed for a specific service in the heterogeneous wireless network. The mobile P2P application usually has an innate hardware limitation and binds the wireless technology, such that the heterogeneity limits the interoperability. Therefore, the mobile P2Psolution must provide a platform to improve the interoperability.
2.5. IPv6 routing header
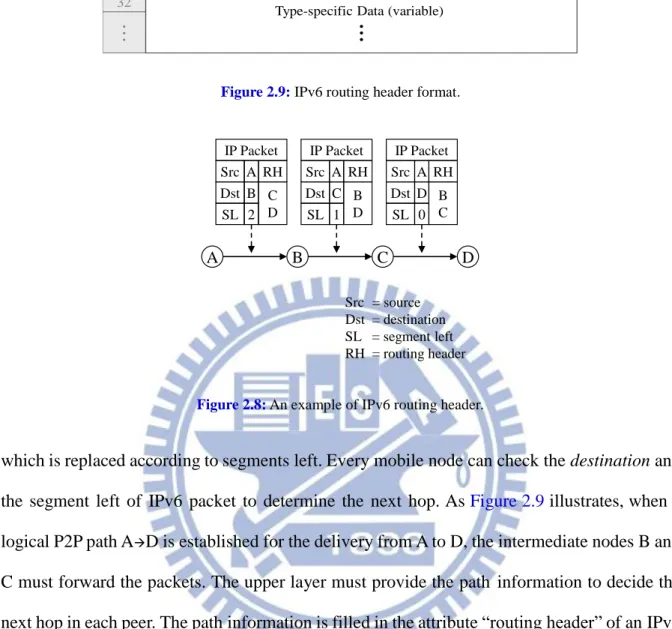
IPv6 packets consist of control information for addressing and routing, and a payload for user data. The control information in IPv6 packets is subdivided into a mandatory fixed header and optional extension headers. Extension headers carry optional network layer information, which forms a chain via Next Header. Routing Header is one of the extension headers and the type of Next Header is 43. The Routing Header is used to direct a packet to one or more intermediate nodes before being sent to its destination via two attributes, segments left and
type-specific data as illustrated in Figure 2.8. Type-specific data is an array of routing headers,
19 The far routing problem means a routing path through several redundant hops, which leads to a non-optimized
which is replaced according to segments left. Every mobile node can check the destination and the segment left of IPv6 packet to determine the next hop. As Figure 2.9 illustrates, when a logical P2P path AD is established for the delivery from A to D, the intermediate nodes B and C must forward the packets. The upper layer must provide the path information to decide the next hop in each peer. The path information is filled in the attribute “routing header” of an IPv6 packet, and every mobile node checks the destination so as to forward the packet to the next node.
2.6. Anycast
Besides routing header that is used to speed up and stabilize data delivery, anycast is another feature of IPv6 to reduce the querying overhead. Anycast is an addressing androuting method based on IP network [26]. Unlike one-to-one unicast, one-to-all broadcast, or one-to-many
multicast, anycast adopts the one-to-one-of-many delivery. A sender queries or sends data to
an unspecified receiver, whose forwards such data to other receivers in the anycast group.
A B C D IP Packet Src Dst RH A B C D SL 2 IP Packet Src Dst RH A C B D SL 1 IP Packet Src Dst RH A D B C SL 0 Src = source Dst = destination SL = segment left RH = routing header
Figure 2.8: An example of IPv6 routing header.
0 ~ 7 8 ~ 15 16 ~ 23 24 ~ 31 Bits 0 32 . . .
Next header = 17 Extension length Routing type = 0 Segments left
Type-specific Data (variable)
.. .
Anycast originates from IPv6 for service-orientated applications to decrease network traffic and shorten response delay. An anycast address can be assigned in an anycast group, in which the receivers with the same anycast address should receive the same packets. Although the source should send a query to the nearest destination among an anycast group of multiple receivers, the nearest destination is not constant via different routing principles or arbitrary routing paths. Therefore, anycast is suited to connectionless protocols generally built under UDP.
2.7. Delivery strategy
In MANET, how to route IPv6 packets as quick as possible is important, however, how to deliver the application data for qualities of services is essential in P2P network. In the file sharing perspective, how to quickly fill up the buffer is an important issue. In the voice communication perspective, how to maintain the continuous link and handle incoming/ outgoing queue is the necessary. From live streaming system's viewpoint, nevertheless, how to buffer the arriving data before playback deadlines is more crucial than filling up the buffer, although the latter is essential.
In order to represent a delivery flow, a general buzzword “chunk” means a piece of data, such as one file block or one video segment. In other words, a chunk is the smallest unit of application data. Each chunk owns a sequence number (SN) to represent the order of playback. The sequence numbers are used to avoid the blank file gap or disordered video frames. Therefore, how to deliver the application data for qualities of services becomes an issue of gathering necessary chunks. The issue is called chunk scheduling, which is integrated into the
delivery strategy in the P2P network in addition to coordination with upload strategy.
A mobile platform for generic P2P applications should consider time sensitive data, time-shifting buffer, and long lasting traffic. In P2P live streaming, peer leaving still causes some chunks not available, also the outmoded chunks become the useless chunks. The video
chunks are only alive for a short time which is about 250 second in the whole network. The data in live streaming buffer changes quickly, and the buffer can be regarded as a finite FIFO (first-in-first-out) circular queue. The buffer is shifting regularly as time passing as the contents are modified in accordance with the proceeding of playback. This buffer will be used to temporarily store the chunks for immediate playback. For example, media playback bit rate of PPLive is 380 kbps and peers often reserve 200 seconds for buffer [27]. Therefore, the buffer size is often no greater than 10 MB, which usually could provide 3 minutes IPTV program for playback. The live voice or video data always come in a continuous stream form, i.e.
consecutive segments. The downloading bit rate should not necessarily be high as long as
chunks arrive at a stable rate. In general, the downloading bit rate of a peer with a stable source often equals to the playback bit rate.
Buffer control is indispensable to a P2P network, and it is also one component of P2P system to avoid jitter. Buffer mitigates the possible challenges because of high churn rate. In general, a churn problem often causes an interruption or a break of data delivery; hence, the buffered data can deal with the urgent chunk scarcity problem before the overlay recovery.
3. The Proposed Scheme
In our published works, the P2P applications of video [c] and voice [b] live streaming are
supportable in MANET. We use the base to propose a generic platform, including the IPv6 routing [c] and cross-layer design [e]. The proposed scheme, GPMS, is a cross-layer
middleware under application layer and above MAC layer. The middleware design allows generic P2P services on WiFi or WiMax network. As Figure 3.1 illustrated, GPMS builds a relationship between the logical overlay and the physical topology. The proposed scheme contributes to the multiple real-time P2P applications on mobile network, the overlay proximity and efficient routing, and the on-demand self-organization.
3.1. System overview
As Figure 3.2 illustrated, GPMS is a cross-layer middleware of overlay layer, transport layer, and network layer.
IPv6 for network layer: Anycast is used for service querying, and the extended routing
header is used for hop-by-hop routing. Therefore, GPMS uses IPv6 as the network layer protocol [c].
UDP for transport layer: UDP can use a datagram socket to establish end-to-end
communication in MANET. Its connectionless characteristics including lightweight and datagram without acknowledgment, retransmission, and timeout, are suitable for wireless P2P real-time services. Importantly, UDP is suitable for IPv6 anycast and mobile hop-by-hop routing.
P2P for overlay layer: P2P overlay is used to identify, index, and manage mobile nodes [e].
support multiple services.20
Platform for application layer: Generic P2P applications including file sharing, voice
communication, and video streaming are applied on the platform. According to the service type of FPRT, various routing paths are derived on the overlay, and the proposed scheduler combines the dynamic buffer to deliver all kinds of data.
3.2. Finger plus routing table
Because FPRT caches the service type and routing information, GPMS can support multiple
20 FPRT is extended from EDHT of COME-P2P [c] which is published in Ad Hoc Networks.
Overlay layer Transport layer Application layer Network layer MAC layer Scheduler Dynamic buffer Anycast Routing header IPv6 FPRT UDP WiFi/ WiMax Platform
Figure 3.1: The proposed cross-layer scheme (GPMS).
B A D C Ad hoc topology Network routing GPMS overlay Data stream Overlay Intermediate node GPMS Peer
Mobile node with GPMS Mobile node
multimedia services and route data through overlay and ad hoc network simultaneously, and the cached information is called path information. Path information is used to maintain FPRT and cross-layer scheme, and provides the information of overlay tier and routing tier simultaneously. Because FPRT must be aware of IPv6 routing principle, the attributes of FPRT include the related information of IPv6 header.
The FPRT is used to construct the P2P overlay. FPRT takes the advantage of path information, and FPRT is shared as the combination of finger table and routing table on overlay tier and routing tier respectively in GPMS. Path information is for UDP and IPv6 routing to derive a local path between two peers through multiple intermediate nodes. An intermediate node without GPMS still uses its routing table and ignores FPRT. Every mobile peer maintains its FPRT to know its members via the reactive notification of arrival or departure and the proactive detection of movement, so the path information is updated to accommodate the peers' mobility and churn. As a result, GPMS achieves the high overlay proximity.
The high overlay proximity improves the high routing scalability, so the path information can be used in a routing protocol in the proposed cross-layer scheme. GPMS doesn't need the flooding scheme of routing discovery. It uses the extended routing header in IPv6 to forward packets hop by hop, so the ad hoc routing protocol is replaced by the membership of overlay, such that the overhead is little. Because the next hop field21 of IPv6 is based on the path information of FPRT, the overlay proximity leads to high routing efficiency.
3.3. Cross-layer scheme
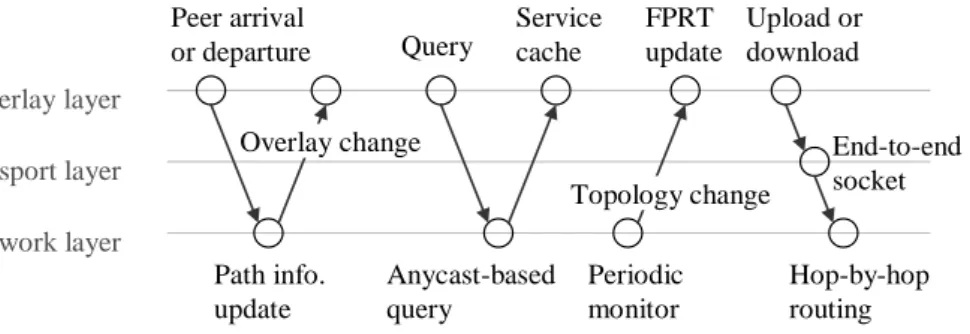
GPMS uses the cross-layer messages to implement the proposed middleware. When overlay tier or routing tier has actions or events, FPRT is informed to update for overlay proximity and routing efficiency. Because FPRT is shared in overlay tier and routing tier, the actions must be considered as Figure 3.3 illustrated. For example, the arrival or departure of peers may lead to
the redirection of routing path, which must change the overlay; therefore, the FPRT must be updated for the peer churn to achieve the overlay stability and scalability.
In GPMS, FPRT must cache P2P service type and file query to support multiple P2P applications. When a peer queries a P2P service, an anycast resolution is initiated to search on MANET, and the results of query will be cached in the intermediate peers. Since each mobile peer is similar to the router on a local wireless network, the service priority and anycast addressing are enabled to route packets possibly. A group of peers sharing the same content, it is like a swarm22 that shares the same IPv6 anycast address.
Besides the reactive notifications of arrival and departure, each peer periodically monitors the neighbors to detect the movement or failure proactively. The network layer essentially broadcasts Hello Message periodically to keep alive, so the accumulation of Hello Message is used as a metric of peer mobility to update FPRT for overlay and routing optimization. Since
Hello Message is provided essentially in MANET, the cross-layer approach doesn't cause
additional overhead.
When delivering content that includes file or multimedia stream, an end-to-end UDP socket is created to support the hop-by-hop routing path. In our proposed scheme, the attribute “next hop” of IPv6 is used to forward packets to the destination. The extended routing header in
22 Swarm originates from BitTorrent, and it means a kind of mesh overlay managing network of peers. The main
advantage of the swarming content delivery is its ability to effectively utilize the outgoing bandwidth of participating peers as the group size grows.
Overlay layer Transport layer Network layer Peer arrival or departure Overlay change Path info. update Query Service cache Periodic monitor Anycast-based query FPRT update Topology change Upload or download End-to-end socket Hop-by-hop routing
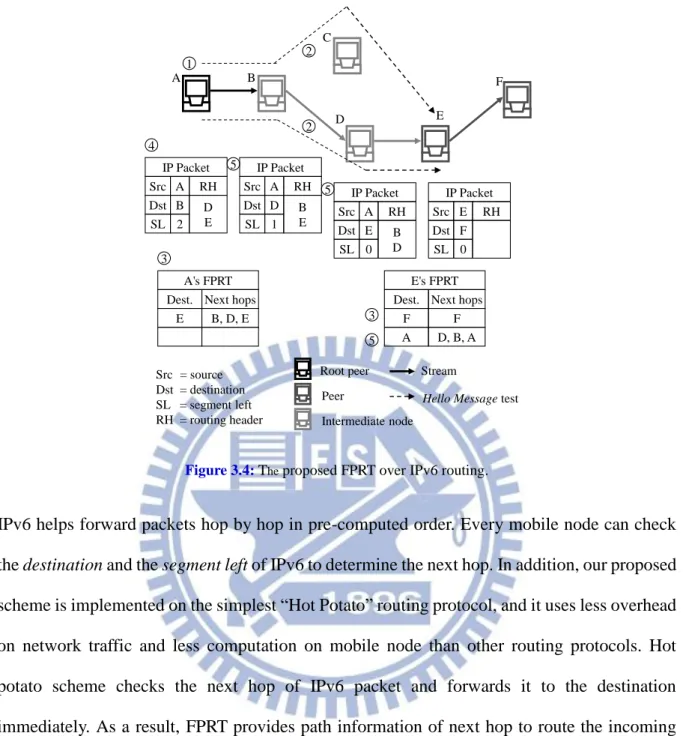
IPv6 helps forward packets hop by hop in pre-computed order. Every mobile node can check the destination and the segment left of IPv6 to determine the next hop. In addition, our proposed scheme is implemented on the simplest “Hot Potato” routing protocol, and it uses less overhead on network traffic and less computation on mobile node than other routing protocols. Hot potato scheme checks the next hop of IPv6 packet and forwards it to the destination immediately. As a result, FPRT provides path information of next hop to route the incoming packets in our proposed scheme. Although the limitation of GPMS is that only IPv6-enabled nodes can work, nowadays most of the modern routers provide dual stack for routing both IPv4 and IPv6 packets.
3.4. Routing algorithm
Hot Potato routing protocol can forward packet quickly without complicated and lengthy computation, and produce less overhead during routing packet. The routing path will not be
A B
C
D E
F
A's FPRT Dest. Next hops
E B, D, E
E's FPRT Dest. Next hops
F A F D, B, A IP Packet Src Dst RH A B D E Root peer Peer Intermediate node Stream
Hello Message test
SL 2 IP Packet Src Dst RH A D B E SL 1 IP Packet Src Dst RH A E B D SL 0 IP Packet Src Dst RH E F SL 0 Src = source Dst = destination SL = segment left RH = routing header 1 2 2 3 4 3 5 5 5
changed until the path information is changed. Figure 3.4 illustrates how to forward the stream via the proposed FPRT and IPv6 routing. In the topology, node A is a peer which multicasts a streaming data; node B, C, D are the intermediate nodes; node E and F are the receivers.
(1) A logical P2P path A E F is established in the P2P overlay via the FPRT lookup.
(2) After the latency estimation, a physical routing path ABDE is selected because path ABDE is shorter than path ABCE, path ABCDE and so on.
(3) The path information is updated in the FPRT and used to decide the next hop in each peer.
(4) The path information is filled in the attribute “routing header” of IPv6 packet to speed up and stabilize data delivery.
(5) Every mobile node checks the destination of IPv6 packet and forwards it to the next node. Because the FPRT provides the overlay proximity, the path information can be used for the hop-by-hop wireless IPv6 routing. Every mobile node is considered as a P2P router and follows the routing header of IPv6 packet. The optimal routing path in FPRT can be derived in advance to avoid the non-optimized end-to-end path via the cross-layer design. Instead of an on-demand routing in the intermediate node, the cross-layer IPv6 routing not only avoids the non-optimized end-to-end path, but also hastens and stabilizes the large-size video stream. The integration with Hot Potato routing protocol can forward packet quickly without complicated and lengthy computation, and produce less overhead to facilitate efficient routing over MANET.
The inter-layer packet is replaced with the proposed combination of packet headers as Figure 3.5 illustrated. Because the packet format is based on IP under UDP,23 and the cross-layer approach is workable without any modification.
23 As Figure 3.5 illustrated, the pseudo packet structure of GPMS can be seen as the combination of UDP and IP
3.5. GPMS design
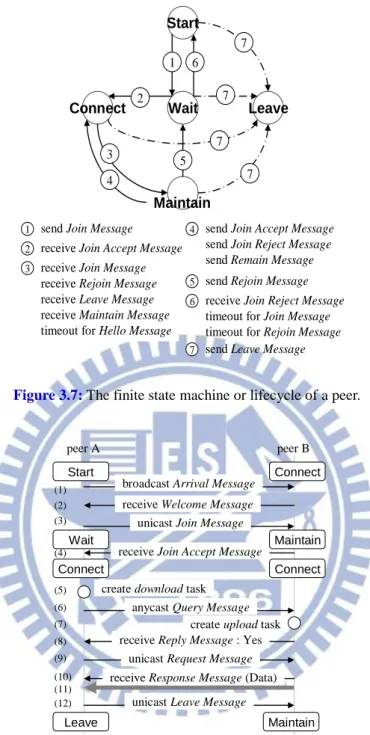
At the beginning, a peer joins the P2P network, and it maintains its neighborhood overlay via exchanging signaling messages with other peers until leaving P2P network. The lifecycle of peer represents the self-organization of overlay, and the finite state machine is driven via such messages to design for the lifecycle and behaviors. As Figure 3.6 illustrated, every peer should go through the states: start, wait, connect, maintain, and leave. Every current state should deal with the exact messages to avoid errors, which may crash the overlay.
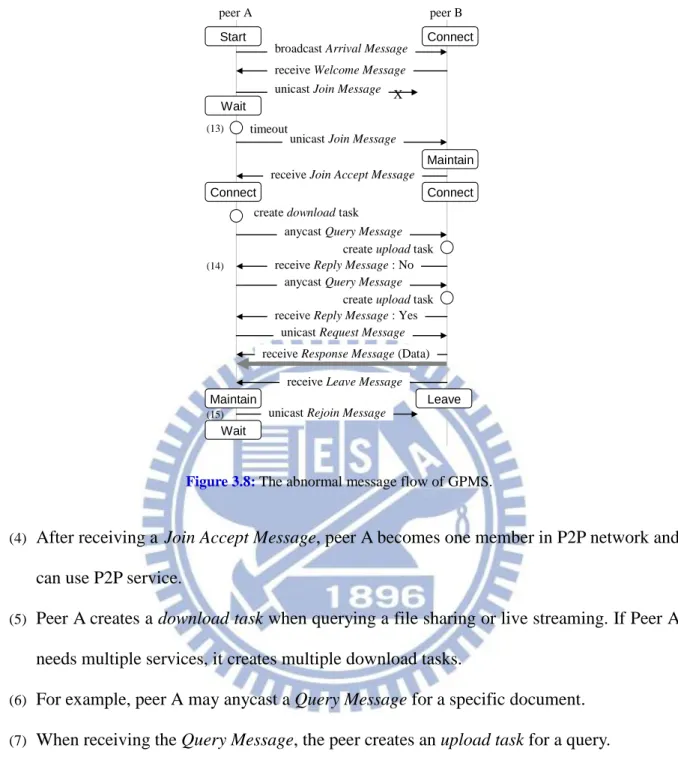
Based on Figure 3.6, we give a normal example asin Figure 3.7, in which peer A plays the role in such example. Peer A is a newly joined peer in the P2P network, the joining process and querying process are described as the follows:
(1) First, because peer A knows neither any peer nor the overlay, it broadcasts Arrival
Message to search the neighbors. The Arrival Message has the source address and routing
trace. 0 ~ 7 8 ~ 15 16 ~ 23 24 ~ 31 Bits 0 32 64 96 128 160 192 224 256 288 320 . . . Next header = 43 UDP payload length
Destination address Source address
Hop limit
Source port Destination port
Length Checksum
Data Peer ID
Next header = 17 Extension length Routing type = 0 Segments left Version = 6 Traffic class Flow Label
Routing address [1] Routing address [2]
.. .
Service ID Packet ID
(2) If an intermediate node receives an Arrival Message, it doesn't know such message and rebroadcasts to search some peers. When a peer receives an Arrival Message, it sends
Welcome Message to peer A via the source address and routing trace, and it stops
rebroadcasting. The Welcome Message has the destination address and routing trace.
(3) After receiving the Welcome Message, peer A unicasts a Join Message to select its member.
create upload task
Start Connect
Leave
broadcast Arrival Message receive Welcome Message unicast Join Message Wait
receive Join Accept Message
anycast Query Message Connect
receive Reply Message : Yes unicast Request Message receive Response Message (Data) create download task
Maintain Connect
unicast Leave Message
Maintain peer A peer B (1) (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) (12)
Figure 3.6: The normal message flow of GPMS.
Start
Connect Wait Leave
send Join Message receive Join Message receive Rejoin Message receive Leave Message receive Maintain Message timeout for Hello Message
Maintain
receive Join Reject Message timeout for Join Message timeout for Rejoin Message send Rejoin Message
send Leave Message
1 2 3 4 5 6 7 1
receive Join Accept Message 2
3
send Join Accept Message send Join Reject Message send Remain Message 4 5 6 7 7 7 7