The Implementation of Data Security Base on Wireless Networks
全文
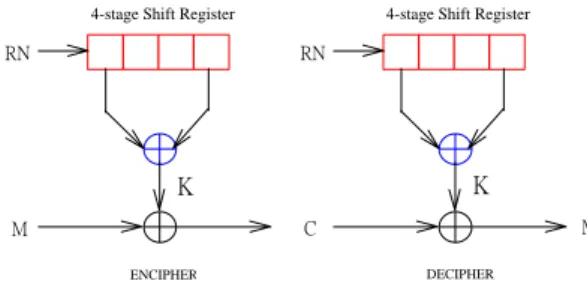
(2) the key exchange protocol between a base. There will be a message exchange for the. station and mobile node in Section II. In Section. key exchange. In the following, we shall propose. III, an example is given to explain how easy to. a key assignment protocol that can be initiated. implement the protocol, and discuses the. by either side. If the mobile node initiates the. feasibility and characteristics of our algorithm.. key assignment protocol as shown in Up-link of Figure 2, it is presented as follows.. II. DESCRIPTION OF THE NEW 1.. SCHEME. Mobile Node → Base Station (IDG). The ID number of the mobile node, the. The cryptographic system on a wireless two. mobile identifier number assigned by operating. sub-systems, one is for enciphering plaintexts to. company to a subscriber, will be encoded into. ciphertexts and the other is for deciphering. Gray code at first, then Mobile node transmits. ciphertexts to plaintexts. In order to achieve the. the ID number as IDG to Base station for the. privacy and authentication, a mobile node. authentication.. network. should. be. partitioned. into. generates a random number to be a private key, then using an exchange protocol to transmit the. 2.. Base station → Mobile node (KPUB). public key to a base station by the air. Additionally, the mobile node and base station. When the base station receives the IDG, it. will make use of some simple electronic devices. creates the public key with an Exclusive-NOR. (like a 4-stage shift register and Exclusive-OR. gate as shown in formula (1) and transmits the. gate) to authenticate each other further. As. public key to Mobile node. The KPRI is the. shown in Figure 1, letting RN (Random Number). private key of Base station.. denote a private key bit stream, M denote a. K PUB = IDG ⊕ K PRI ------------(1). plaintext bit stream and K denote a key bit stream, then referring to the Vernam cipher [7] we get a ciphertext bit stream C = EK(M) = M⊕. 3.. Mobile node → Base station (KRN). K. On the other hand, we can also get a plaintext with the same operation as M = DK(C) = C⊕K.. The mobile node deciphers the private key with the same operation expressed in. 4-stage Shift Register. RN. formula (2) and generates a random number (RN). 4-stage Shift Register. RN. to be a new private key of Mobile node. However, it also creates the new public key KRN. M. C. M ENCIPHER. as shown in formula (3), and transmits the key to. K. K. Base station eventually.. DECIPHER. Figure 1. Encipher and Decipher system. K PRI = K PUB ⊕ IDG ------------(2).
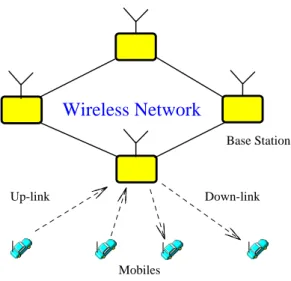
(3) K RN = RN ⊕ K PRI. ----------- (3). Because (ki+1)⊕(ki+1)=0, the decipher process is performed with the same operation as. Concurrently, if the base station initiates. shown in formula (6) and (7).. the key assignment protocol as shown in figure 2 for Down-link, it will be described as follows.. P = DK(S)=p1 p2 p3 .........., bit stream ------(6). Base station → Mobile node (KPUB). pi = (si+ki+1) mod 2, where i=1,2,3,...... ---(7). 1.. The base station translates the ID of. From the formulae (4) to (7), they can be. Mobile node into Gray code, then creates a. easily implemented in microelectronics with. public key as same as formula (1), and transmits. Exclusive-NOR gates.. the public key to Mobile node.. 2.. Mobile node → Base station (KRN). The mobile node gets the private key. Wireless Network. according to the formula (2) at first, then. Base Station. applying the formula (3) to create a new public key and transmit it to Base station. Up-link. Finally,. we. present. Encipher. Down-link. and. Decipher process of the key by modular. Mobiles. arithmetic in GF(2) as list:. Figure 2. Wireless Network 1.. Encipher process. Letting P=p1p2p3... denote a private-key bit stream and K=k1k2k3... denote a key bit. III. EXAMPLE AND IMPLEMENTATION. stream, then we generate a secret public-key bit stream S=s1s2s3... by the encipher process as shown in formula (4) and (5).. We will illustrate the implementation of our protocol on Base station and Mobile node in this section.. S = EK(P) = s1 s2 s3 .........., bit stream ------(4) Assume that the ID number of Mobile si = (pi+ki+1) mod 2, where i=1,2,3,...... ---(5). node is expressed by id1 to id4 and the private-key KPRI of Base station denoted by the. 2.. Decipher process. bit stream, then initially the ID number will be translated into Gray code by 3 Exclusive-OR.
(4) gates as shown in figure 3. Additionally, we can. IV. CONCLUSION. create a public key from an Exclusive-NOR gate in the base station. However, the mobile node generates the new public key KRN by using an. Because wireless networks can provide. Exclusive-NOR gate eventually. Figure 3 shows. economic and convenient services of the. that the implementation of the base station and. message (such as data and voice) transfer, they. mobile node, respectively.. will be applied in several domains like wireless LANs and WANs, wireless PBX, Digital. In this paper, we have concentrated not. Cellular Ratio and Cordless Extension Phones.. only on the privacy and authentication for. However, it is important that users need a safe. wireless communications but also considered the. and confident protocol to communicate with. feasibility of implementation. Therefore, we. each other in the open air. In this paper, we. discuss the merits of our protocol and compare. presented a cryptography protocol that not only. with the others as list.. provides privacy and authentication for wireless. (1) About the relative security and complexity, our protocol has owned all the. network but also uses a simple circuit to implement the transmission of data security.. merits of Vernam and Random Ciper [7]. (2) In. order. to. authenticate. legal. REFERENCE. registration further, we just make use of shift registers and logical gates to achieve the goal. (3) From the above illustration, it is. [1] J.E. Padgett, C.G.. Gunther and T. Hattori,. obvious that our algorithm is simple with low. “Overview. cost and low latency.. Communications”,. (4) The bit stream length of ciphertext is the same as the plaintext so that there is no overhead in transmission.. of. wireless. Personal. IEEE. Personal. Communications Magazine, pp. 28-41, Jan. 1995. [2] R. Steels, j. whitehead and W.C. Wang, “System Aspects of Cellular Ratio”, IEEE. (LSB) id4 id3. Personal Communications Magazine, pp.. Mobile Node. 80-86, Jan. 1995.. id2. ID G. K. PRI. K. [3] Richard Van Nee and Geert Awater, “ New RN. High-Rate Wireless LAN Standards”, IEEE. K. (MSB) id1. RN. PUB. Communications. Magazine,. pp.. 82-88,December 1999. (LSB) id4. [4] Sheng-Cheng Yeh and J.-S. Wu, “Integration. Base Station. id3. IDG id2 (MSB). of Video, Voice and Data Transmission. ID G K. PRI. id1. K. PUB. Service based on PRMA Wireless Networks”, Computer Communications, vol. 24, pp. 942-948, May 2001.. Figure 3. The Implementaion of Our Protocol.
(5) [5] Ashar Aziz and Whitefield Diffie, “Privacy and Authentication for Wireless Local Area Networks”, IEEE Personal Communications Magazine, pp. 25-31, First Quarter, 1994. [6] M.J. Beller, L.F. Chen and Y. Yacobi, “Privacy and Authentication on a Portable Communications System”, IEEE JSAC, Vol. 11, No. 6, Aug. 1993. [7] D.E. Denning, “Cryptography and Data Security”, Reading MA: Addison-Wesley, 1982..
(6)
數據
相關文件
Consistent with the negative price of systematic volatility risk found by the option pricing studies, we see lower average raw returns, CAPM alphas, and FF-3 alphas with higher
• Tree lifetime: When the first node is dead in tree T, the rounds number of the node surviving is the lifetime of the tree. The residual energy of node is denoted as E)), where
The Government also established the Task Force on Promotion of Vocational and Professional Education and Training in April 2018 to evaluate the implementation
LEARN CARDS WRITE MATCH TEST... How students make use
To tie in with the implementation of the recommendations of the Task Force on Professional Development of Teachers and enable Primary School Curriculum Leaders in schools of a
Wang, Solving pseudomonotone variational inequalities and pseudocon- vex optimization problems using the projection neural network, IEEE Transactions on Neural Networks 17
The temperature angular power spectrum of the primary CMB from Planck, showing a precise measurement of seven acoustic peaks, that are well fit by a simple six-parameter
This study will base on the perspective of the philological education to discuss 788 characters that were commonly used in the daily life of the early Tang era, for highlighting