A new two-dimensional code for optical code division multiple access systems
全文
(2) I. Introduction In recent years, optical communication techniques have been applied to various applications. Local area network (LAN) is one of the popular applications using optical communication techniques. As is known, the traffic model in LAN is a burst and multiple users’ one, therefore, asynchronous multiplexing schemes and multiple access techniques are necessary in such an environment. The code division multiple access (CDMA) is such a scheme that is well suited for high speed LAN’s. In CDMA systems, the spreading codes play an important role in system performance (in terms of capacity and bit error rate). Therefore, there are many investigations on code construction in order to find codes which are well suited for CDMA systems [1-12]. When we construct codes for a CDMA system, two issues should be considered. One is the correlation property and the other is the code size. The correlation property is relative to the bit error rate and the code size is connected to the capacity of the system which is the major problem for one-dimensional codes, such as OOC’s [1-5] and prime codes [6]. In order to lessen this problem, two-dimensional codes are developed to solve such limitation of one-dimensional codes [8-12]. There are number of advantages accruing from using two-dimensional coding. Firstly, both the security and the cardinality of the code family are greatly increased. The large cardinality of the two-dimensional code’s family is resulted from the integration of both patterns coded in different domains. Furthermore, since two-dimensional codes are coded in two different domains simultaneously, it is significantly increased the system‘s security level because the pulses must match in both dimensions. Secondly, to have a correlation peak, in addition to the pulse coincidence, the pulses must also match in their wavelengths. Hence, the peaks of cross-correlation and out-of-phase autocorrelation are reduced..
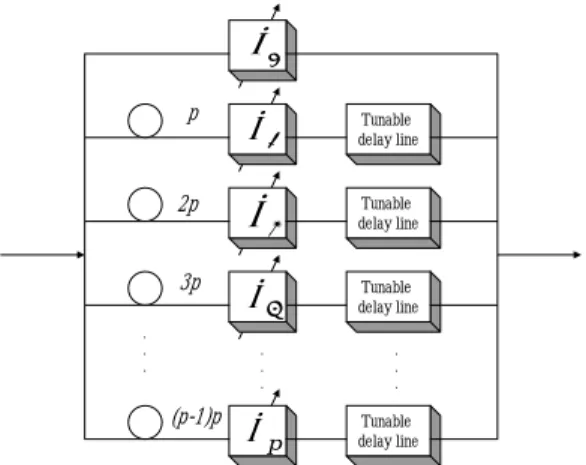
(3) The representative two-dimensional code coded in time and wavelength is the prime-hop code which is proposed by L. Tancevski et al in 1996 [12]. Each pulse of a codeword is transmitted at a different wavelength. Prime-hop codes possess a perfect needle-shaped autocorrelation function with zero sidelobe and a cross-correlation of at most one. Moreover, with a larger prime number p, the prime-hop codes have better performance and larger code size [12]. However, the code generation of prime-hop codes is usually achieved by using parallel architecture (Fig 1). In such architecture, the cost and the complexity of encoder and decoder are increased with larger code weight (p). The large amount of tapped delay lines and filters are required when a large prime number p is selected. For the aforementioned reasons, we want to construct more effective codes by reducing the code weight (removing some pulses) of prime-hop codes, resulting in such a system can be implemented by using low cost and low complexity encoder/decoder. However, we know that if decreasing the code weight with the same code length, there are two factors will influence the system performance. The first is that the threshold will decrease as the code weight reduces. As a result, fewer interfering users can cause an error. The other is that the hit probability will decrease as the code weight decreases. Consequently, more interfering users are needed to motive an error. The former factor will deteriorate the system performance, but the latter factor will improve the system performance. We are interested in which factor dominates the system performance. The outline of this paper is as follows. In section II, the code construction algorithm is described. The performance of the new codes is analyzed in section III. In section IV, we present the numerical results. At last, in section V, the conclusions of this study are summarized..
(4) λ1 p. λ2. Tunable delay line. 2p. λ3. Tunable delay line. 3p. λ4. Tunable delay line. . . .. . . .. (p-1)p. . . .. λp. Tunable delay line. Fig 1. Prime-hop code encoder. τ1 τ2. τ3. λ1. λ2. λ3. . . .. . . .. τp. λp. Fig 2. Prime-hop code decoder. II. The algorithm of code construction In this section, we illustrate how to construct the modified prime-hop codes. The construction algorithm is listed below: Step1: Select a prime number p. Step2: Write down a set of modified prime sequences Ai = {ai ,0 , ai ,1 ,..., ai ,( p −1) / 2 } , i = 0,1,.., p − 1. Each element ai , j of Ai is generated by. ai , j = [2ij]p ,. (1).
(5) where [ ]p denotes the modulo p and j=0,1,…, (p-1)/2.. {. }. Step3: Construct a set of time spreading patterns Si = si ,0 , si ,1 ,..., si , p2 −1 , i = 0,1,..., p − 1 . Each element si ,k of Si is given by. 1 si ,k = 0. if k = ai , j + 2 jp otherwise ,. (2). where j = 0,1,…,(p-1)/2 and k = 0,1,2,…,p2-1. Step4: Construct a set of hopping patterns H i = { hi ,0 , hi ,1 ,..., hi ,( p −1) / 2 }, i=0,1,…,p-1. Each element hi , j is given by. p hi , j = ai , j. if ai , j = 0 otherwise ,. (3). where j=0,1,2,…, (p-1)/2. The elements of Hi are identical to elements of the modified prime sequences Ai except that the element “0” of Ai is replaced by the prime number “p”. The hopping pattern H0 is discarded as trivial because its elements have the same value. Hence, there are only p-1 hopping patterns. Step 5: Integrate time spreading patterns and wavelength hopping patterns to form the modified prime-hop code. PHCl , m = Sl H m = { cl ,m ,0 , cl ,m ,1 ,..., cl ,m , p2 −1 }, where l=0,1,2,… p-1. and m=1,2, …, p-1, by the following equation:. h if k = am, j + 2 jp Cl ,m,k = m, j otherwise . 0. (4).
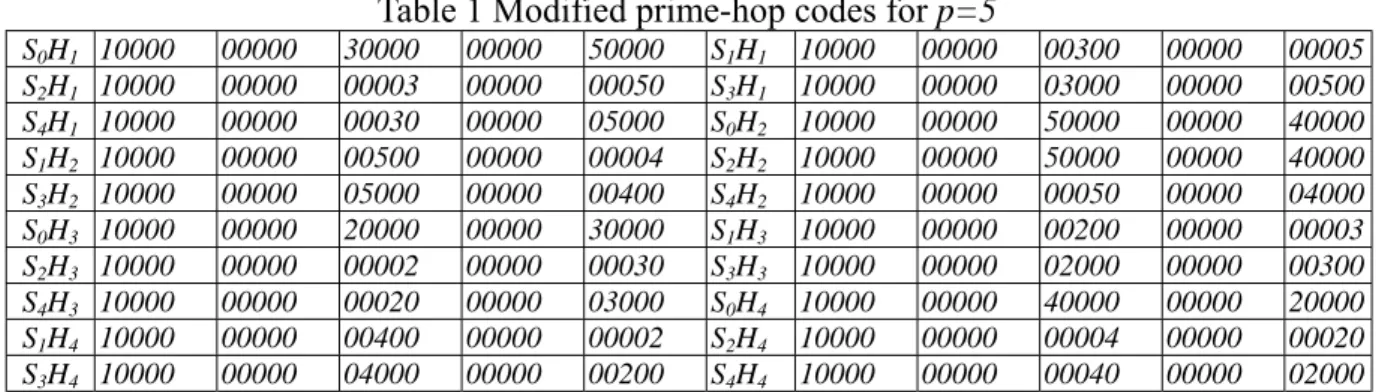
(6) We use the following example to explain the construction algorithm. Example 1: Step 1: Let the prime number p equal 5. Step 2: By following equation (1), the modified prime sequences are listed as follows:. A0 = {0, 0, 0} , A1 = {0, 2, 4} , A2 = {0, 4, 3} , A3 = {0, 1, 2} , A4 = {0, 3, 1} .. Step 3: Derive the p time spreading patters from equation (2).. S0 = {10000 00000 10000 00000 10000} , S1 = {10000 00000 00100 00000 00001} , S 2 = {10000 00000 00001 00000 00010} , S3 = {10000 00000 01000 00000 00100} , S 4 = {10000 00000 00010 00000 01000} ,. Step 4: The hopping patterns are derived from equation (3).. H 0 = {5, 5, 5} , H1 = {5, 2, 4} , H 2 = {5, 4, 3} , H 3 = {5, 1, 2} , H 4 = {5, 3, 1} .. The hopping pattern H0 is discarded as trivial because elements of H0 have identical values..
(7) Step5: Finally, we generate p(p-1) distinct code sequences, called as modified prime-hop codes, by integrating p-1 wavelength hopping patterns and p time spreading patterns. The modified prime-hop codes for p = 5 are listed in Table 1. From Table 1, it is clearly shown that the modified prime-hop codes have pulses only in even-number blocks. As a result, the modified prime-hop codes have the same code length p2 but less code weight (p+1)/2 in compared with the original prime-hop codes. Moreover, through theorems proposed in [12], it is shown that the autocorrelation constrain λa of prime-hop codes is zero and cross-correlation constraint λc of prime-hop codes is 1. Due to the process of removing some pulses doesn’t increase the values of autocorrelation and cross-correlation, consequently, the modified prime-hop codes have the same code correlation properties with prime-hop codes.. Table 1 Modified prime-hop codes for p=5 S 0H 1 S 2H 1 S 4H 1 S 1H 2 S 3H 2 S 0H 3 S 2H 3 S 4H 3 S 1H 4 S 3H 4. 10000 10000 10000 10000 10000 10000 10000 10000 10000 10000. 00000 00000 00000 00000 00000 00000 00000 00000 00000 00000. 30000 00003 00030 00500 05000 20000 00002 00020 00400 04000. 00000 00000 00000 00000 00000 00000 00000 00000 00000 00000. 50000 00050 05000 00004 00400 30000 00030 03000 00002 00200. S1H1 S3H1 S0H2 S2H2 S4H2 S1H3 S3H3 S0H4 S2H4 S4H4. 10000 10000 10000 10000 10000 10000 10000 10000 10000 10000. 00000 00000 00000 00000 00000 00000 00000 00000 00000 00000. 00300 03000 50000 50000 00050 00200 02000 40000 00004 00040. 00000 00000 00000 00000 00000 00000 00000 00000 00000 00000. 00005 00500 40000 40000 04000 00003 00300 20000 00020 02000. III. Performance analysis In this section, we analyze the performance of the system with modified prime-hop codes. Here, we assume that the performance deterioration is only due to the multiple access interference (MAI) without the negative effects of thermal noise and shot noise in the photodetection process. Moreover, for simplification, the Poisson characteristic of the optical direct detection process is not considered. We also assume that the receivers are already synchronized with the transmitters. In addition, chip synchronization is also assumed here for the sake of mathematical convenience..
(8) In an optical CDMA system using on-off keying modulation only bit “1” is encoded by the signature code sequence. Therefore, an error occurs only when the accumulative MAI at a particular user whose transmitting data bit is “0” reaches over the decision threshold. In a system with modified prime-hop code whose prime number is p, the pulses in a codeword are transmitted at different wavelengths. Hit (or the MAI) happens only when the pulse belonging to a particular user overlaps with the pulse of the desired user and their wavelengths are also the same. Since the cross-correlation constraint of modified prime-hop codes is equal to one, two codewords cannot hit more than once during a data bit interval. However, the code patterns of modified prime-hop codes use only a portion of available wavelengths. The exact value of hit probability depends on the code patterns used by the desired user and interfering users. Consequently, it is difficult to compute the exact distribution of hit. In order to simplify the computational complexity, we use the average hit instead of the exact hit to analyze the system performance. The average hit is defined as the mean value of the exact distribution of hits in a full load environment and can be obtained through the computer program with the exhausted method. Table 2 lists the average values of hit for prime number p ≤ 41 . Through this section, we use these values to approximate the performance of modified prime-hop codes. Let p denote the average hit. Then, the probability that a pulse of a particular user hitting with one of the pulses of the desired user is given by:. q=. p , 2L. (5). where the factor 1/2 accounts for the probability that the interferer is transmitting a “1” and L is the code length equal to p2. The number of users that interfere with the desired user has a.
(9) binomial distribution with parameters N-1 and q, where N is the total number of users. Let PI(I=i) denote the probability of i interfering users, we have. N − 1 i N −1− i PI ( I = i ) = , i = 0,1,..., N -1 q (1 − q) i . (6). The approximation bit error rate is given by. Pe =. 1 ∞ ∑ PI ( I = i) 2 i =Th. (7). Substituting eqn.(6) into (7), we derive the Pe in form of. 1 N −1 N − 1 p Pe = ∑ 2 ( p +1) / 2 i 2 L . i. p 1 − 2L . N −1− i. (8). Table 2 Average hit of modified prime-hop codes The average hit Prime number Average value Prime number Average value Prime number 1.947 4.966 p=5 p=17 p=31 2.46 5.486 p=7 p=19 p=37 3.477 6.489 p=11 p=23 p=41 3.98 7.991 p=13 p=29. Average value 8.491 9.985 10.987. IV. Numerical Analysis and Simulation Results In this section, the numerical analysis and simulation results of the proposed schemes are given. Firstly, we compare the simulation probability of bit error of the proposed scheme with the bit error probability derived from eqn.(8). The simulation curve is shown in Fig.3. It is shown that the curve of the approximation analysis is very close to the simulation one. Hence,.
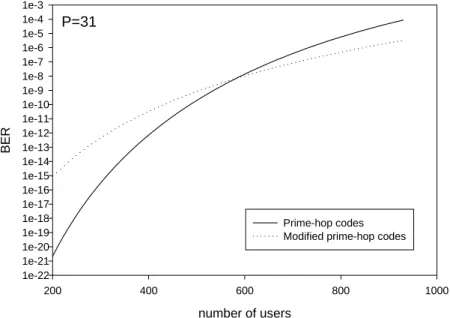
(10) the validity of our theoretical analysis is verified. In Fig.4, we show the variation in the system performance with modified prime-hop codes for different prime numbers. It is shown that the systems with larger prime number have better performance. This property is similar to that of the prime-hop codes [12]. Finally, we compare the performance of our proposed scheme with that of prime-hop codes. As illustrated in Fig.5 and Fig.6, we find that modified prime-hop codes perform better than original prime-hop codes when the traffic load is heavy. We have mentioned in the beginning of this paper that there are two factors influence the system performance resulting from reducing the code weight. The first is that the threshold will decrease as the code weight reduces. As a result, fewer interfering users can cause an error. The other is that the hit probability will decrease as the code weight decreases. Consequently, more interfering users are needed to motive an error. The numerical results in Fig.5 and Fig.6 show that the latter dominates the system performance when the traffic load is heavy. This result satisfies our expectancy that the system can be implemented with low complexity encoder/decoder and, in the meanwhile, maintains good system performance. From Fig.5 and Fig.6, we find that the cross point is under the maximum BER required in optical CDMA system (10-9) when p>=37. Table 3 shows the system hardware requirement and maximum number of simultaneous users for systems with prime-hop codes and modified prime-hop codes. From Table 3, it is shown that the proposed scheme can accommodate more users than the system with prime-hop codes when selecting proper prime number.. V. Conclusions In this paper, we have proposed a new two-dimensional code, which we term as modified prime-hop codes. The modified prime-hop codes are constructed by adjusting the code weight of prime-hop codes to a reasonable value. From our results, it is shown that the.
(11) modified prime-hop codes are more efficient than original prime-hop codes because of many advantages, including low complexity of hardware implementation, low power loss and better performance. Moreover, more simultaneous users can be accommodated in the system with modified prime-hop codes. 1e-1. p=7. BER. 1e-2. 1e-3. 1e-4 Theoretical simulation 1e-5 5. 10. 15. 20. 25. 30. 35. 40. 45. number of users. Fig.3 Simulation results of modified prime-hop codes for p = 7 compared to the analytical approximation.. 1e-1 1e-2. P=11. P=13 P=17. 1e-3. P=19. 1e-4. P=23 P=29. 1e-5. BER. 1e-6 1e-7 1e-8. P=11 P=13 P=17 P=19 P=23 P=29. 1e-9 1e-10 1e-11 1e-12 1e-13 1e-14 0. 200. 400. 600. 800. 1000. number of users. Fig.4 BER calculations for modified prime-hop codes for various prime numbers..
(12) BER. 1e-3 1e-4 P=31 1e-5 1e-6 1e-7 1e-8 1e-9 1e-10 1e-11 1e-12 1e-13 1e-14 1e-15 1e-16 1e-17 1e-18 1e-19 1e-20 1e-21 1e-22 200. Prime-hop codes Modified prime-hop codes. 400. 600. 800. 1000. number of users. Fig.5 BER versus the number of users for p = 31. 1e-6. P = 37 1e-7 1e-8. BER. 1e-9 1e-10 1e-11 1e-12 Prime-hop codes Modified prime-hop codes. 1e-13 1e-14 600. 700. 800. 900. 1000. 1100. number of users. Fig.6 BER versus the number of users for p = 37. Table 3 Given BER<=10-9, maximum number of users can be accommodated in systems employing prime-hop codes and modified prime-hop codes Modified prime-hop codes Prime-hop codes Prime Max number of Hardware requirement Max number of Hardware requirement number users filters tapped delay users filters tapped delay lines -9 (BER<=10-9) (BER<=10 ) lines P=23 182 24 24 231 46 46 P=29 407 30 30 446 58 58 P=31 508 32 32 536 62 62 P=37 898 38 38 866 74 74.
(13) VI. References [1]. J. A. Salehi, “Code division multiple-access techniques in optical fiber networks― Part I: Fundamental principles,“ IEEE Trans. Commun., vol. 37, pp. 824-833, Aug. 1989.. [2]. J. A. Salehi and C. A. Brackett, “Code division multiple-access techniques in optical fiber networks― Part II: System performance analysis,“ IEEE Trans. Commun., vol. 37, pp. 834-842, Aug. 1989.. [3]. F. R. K. Chung, J. A. Salehi, and V. K. Wei, “Optical orthogonal codes: Design, analysis, and applications,“ IEEE Trans. Inform. Theory, vol.37, pp.595-604, May. 1989.. [4]. S. V. Maric, M. D. Hahm, and E. L. Titlebaum, “Construction and performance analysis of a new family of optical orthogonal codes for CDMA fiber-optic networks,” IEEE Trans. Commun., vol. 43, no. 2/3/4, Feb/March/April. 1995. [5]. S. V. Maric, Z. L. Kostic, E. L. Titlebaum, “New family of optical code sequences for use in spread-spectrum fiber-optic local area networks,” “Communications, IEEE Trans. Commun., vol. 41, pp. 1217-1221, Aug, 1993.. [6]. A. A. Shaar and P. A. Davis, “Prime sequences: Quasi-optimal sequences for or channel code division multiplexing,“ Electron. Lett., vol.19, no.21, pp.888-890, Oct. 1983.. [7]. J. G.. Zhang, W. C. Kwong, and A. B. Sharma, “Effective design of optical fiber code-division multiple access networks using the modified prime codes and optical processing,” International Conference on Communication Technology Proceedings, pp. 392 -397 vol.1. 2000.. [8]. H. Fathallah, L. A. Rusch and S. LaRochelle, “Passive optical fast frequency-hop CDMA communications system,” IEEE J. Lightwave Technol., vol. 17, no.3, pp.397-405, Mar. 1999.. [9]. G. C. Yang, and W. C. Kwong, “Performance comparison of multiwavelength CDMA and WDMA+CDMA for fiber-optic networks,” IEEE Trans. Commun., vol. 45, no.11, pp. 1426-1434, Nov. 1997..
(14) [10] E. Park, A. J. Mendez, and E. M. Gasmeiere, “Temporal/spatial optical CDMA networks,” IEEE Photon. Technol. Lett., vol.4, pp. 1160-1162, Oct. 1992. [11] E. S. Shivaleela, K.N. Sivarajan, and A. Selvarajan, “Design of a new family of two-dimensional codes for fiber-optic CDMA networks,” J. Lightwave Technol., vol.16, no.4, pp.501-508, April, 1998. [12] L. Tancevski, I. Andonovic, M. Tur, and J. Budin, “Hybrid wavelength hopping/time spreading code division multiple access systems,” IEE Proc-Optoelectron., vol. 143, no. 3. June. 1996..
(15)
數據

相關文件
(ii) “The dismissal of any teacher who is employed in the school – (a) to occupy a teacher post in the establishment of staff provided for in the code of aid for primary
An additional senior teacher post, to be offset by a post in the rank of APSM, is provided to each primary special school/special school with primary section that operates six or
An additional senior teacher post, to be offset by a post in the rank of CM or APSM as appropriate, is provided to each primary special school/special school with
An additional senior teacher post, to be offset by a post in the rank of CM or Assistant Primary School Master/Mistress (APSM) as appropriate, is provided to each primary
(ii) “The dismissal of any teacher who is employed in the school – (a) to occupy a teacher post in the establishment of staff provided for in the code of aid for primary
[r]
[r]
本《資助學校資助則例》