IEEE TRANSACTIONS ON BROADCASTING, VOL. 54, NO. 3, SEPTEMBER 2008 517
A RED-FEC Mechanism for Video Transmission
Over WLANs
Cheng-Han Lin, Ce-Kuen Shieh, Naveen K. Chilamkurti, Chih-Heng Ke, and Wen-Shyang Hwang
Abstract—This paper proposes a Random Early Detection Forward Error Correction (RED-FEC) mechanism to improve the quality of video delivered over Wireless Local Area Networks (WLANs). In contrast to previous FEC schemes, in which the rate determination information is fed back from the receiver side, in our proposed method, the redundancy rate is calculated directly at the wireless Access Point (AP) in accordance with the network traffic load, as indicated by the AP queue length. An analytical model is developed to predict the effective packet loss rate of a video stream delivered over a WLAN with RED-FEC protec-tion. The numerical results show that the proposed RED-FEC mechanism consistently achieves higher recovery efficiency than a conventional FEC scheme under high and low network loading conditions.
Index Terms—FEC, packet loss, video quality, WLAN.
I. INTRODUCTION
I
N THE current technology age, an increasing number of In-ternet users are choosing to connect to InIn-ternet services via wireless devices such as laptop computers and PDAs. Unfortu-nately, due to attenuation, fading, scattering or interference from other active sources, wireless communication channels gener-ally suffer higher loss rates than their wired counterparts. Packet losses in wireless networks are usually recovered through the use of ARQ (Automatic Repeat reQuest) or FEC (Forward Error Correction) techniques [1]–[5]. In ARQ schemes, the missing packets are retransmitted during timeouts, or in response to ex-plicit receiver requests. By contrast, in FEC mechanisms, the sender attempts to mitigate the effects of packet losses by trans-mitting redundant packets together with the source packets such that a block can still be reconstructed at the receiver end even if some of its packets are lost during transmission. In large-scale multimedia video transmission environments, the delays incurred by retransmitting packets are substantial [6]–[9], andManuscript received September 28, 2007; revised April 1, 2008. Published August 20, 2008 (projected). This work was supported by the National Science Council (NSC), Taiwan under Contract NSC 97-2218-E-507-001.
C.-H. Lin and C.-K. Shieh are with the Department of Electrical Engi-neering, National Cheng Kung University, Tainan 701, Taiwan, R.O.C. (e-mail: jhlin5@hpds.ee.ncku.edu.tw; shieh@hpds.ee.ncku.edu.tw).
N. K. Chilamkurti is with the Department of Computer Science, La Trobe University, Victoria 3086, Australia (e-mail: n.chilamkurti@latrobe.edu.au).
C.-H. Ke is with the Department of Information Management, National Kinmen Institute of Technology, Jinning, Kinmen 892 Taiwan, R.O.C. (e-mail: smallko@kmit.edu.tw).
W.-S. Hwang is with the Department of Electrical Engineering, National Kaohsiung University of Applied Sciences, Taiwan 80778, R.O.C. (email: wsh-wang@mail.ee.kuas.edu.tw).
Color versions of one or more of the figures in this paper are available online at http://ieeexplore.ieee.org.
Digital Object Identifier 10.1109/TBC.2008.2001713
hence of the two error recovery techniques, FEC provides a more suitable approach for recovering the data losses incurred during the delivery of video streams over wireless networks.
Broadly speaking, FEC can be categorized as either Static FEC (SFEC) or Adaptive FEC (AFEC) scheme. In the former scheme, the number of redundant packets added to the source data remains constant irrespective of the network conditions, and hence the recovery performance is unpredictable. For example, whilst injecting a higher number of redundant packets improves the ability of the receiver to recover the missing packets, the additional packets may overload the wireless net-work under heavy traffic conditions. Conversely, the addition of fewer redundant packets reduces the overall network load, but may prevent recovery of the missing packets in the event of a high packet loss rate. In order to maintain a high level of resource efficiency while simultaneously guaranteeing the information accuracy required by user applications, several AFEC schemes have been introduced in recent years [10]–[16]. In such schemes, the FEC rate is tuned dynamically in order to obtain a compromise between the loss recovery rate and the current traffic load. Typical AFEC schemes tune the FEC rate on the basis of feedback information supplied by the receiver. For example, in [11], the packet error rate is measured period-ically at the receiver side and a suitable FEC rate is calculated and fed back to the sender. Meanwhile, in [12], the AFEC scheme aims to facilitate the end-to-end transport of real-time traffic by determining the FEC rate in accordance with feedback information relating to the current network delay. However, the processes involved in measuring this delay, and then calculating and feeding back an appropriate FEC rate, inevitably have a fi-nite duration, and hence the FEC rate implemented at the sender end may not accurately reflect the current network load. Since the network conditions vary continuously in wireless networks, this practice may not be suitable for wireless networks.
To address this problem, this paper proposes a Random Early Detection Forward Error Correction (RED-FEC) mechanism to improve the quality of video delivered over wireless LANs. In the proposed approach, redundant FEC packets are generated dynamically in accordance with the current network traffic load by a RED mechanism implemented at the wireless access point (AP) on the sender side. The RED mechanism is a buffer management algorithm [17] with a congestion avoidance char-acteristic, and is designed to manage the queue dynamically by randomly dropping packets with an increasing probability as the average queue size increases. In the RED-FEC mechanism proposed in this study, the wireless AP monitors the queue size and tunes the FEC rate accordingly. For example, if the queue is almost empty, more redundant packets are generated. However, as the queue length grows, the numbers of redundant packets 0018-9316/$25.00 © 2008 IEEE
518 IEEE TRANSACTIONS ON BROADCASTING, VOL. 54, NO. 3, SEPTEMBER 2008
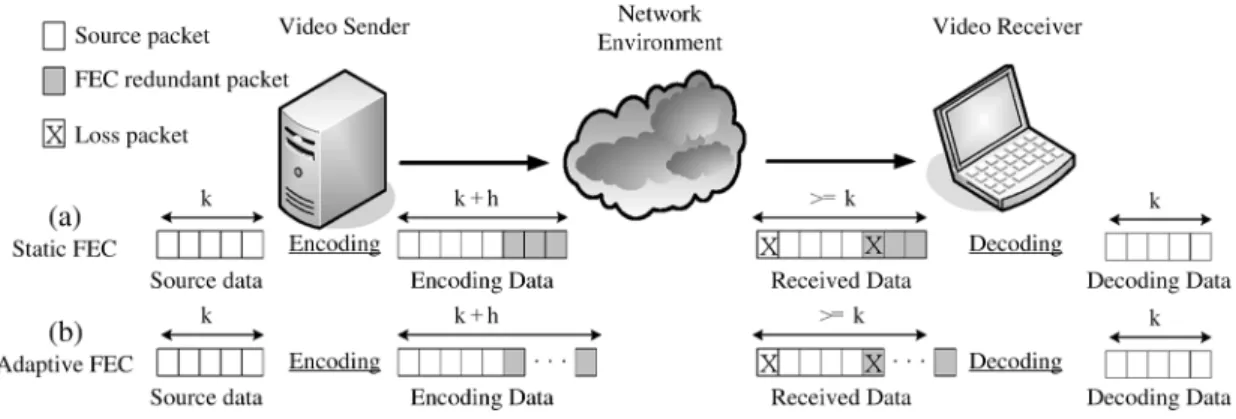
Fig. 1. (a) Static FEC; (b) adaptive FEC.
are reduced. When the queue is near to full, no redundant packet are sent with the source packets to avoid overloading the network. By adopting this approach, the RED-FEC algorithm significantly improves the quality of the delivered video data without introducing an excessive number of redundant packets into the network.
The remainder of this paper is organized as follows. Sec-tion II reviews the basic concepts of existing FEC protocols and develops an analytical model to predict the loss recovery per-formance of SFEC schemes. Section III outlines the proposed RED-FEC mechanism and extends the model presented in Sec-tion II to predict the effective packet loss rate of video trans-mitted over a WLAN with RED-FEC protection. Section IV presents the results of a series of simulations designed to val-idate the performance of the RED-FEC algorithm. Finally, Sec-tion V draws some brief conclusions.
II. FEC PROTOCOLS
The basic principle of FEC entails injecting redundant data into the original transmission data such that packet losses can be recovered without the need for retransmission. Fig. 1 shows the general case in which a block of source packets is en-coded at the sender end as packets. In this way, provided that no more than packets are lost, the source transmission packets can be successfully recovered at the receiver, irrespec-tive of whether the lost packets are source packets or FEC re-dundant packets.
A. SFEC and AFEC Mechanisms
As shown in Fig. 1(a), the SFEC mechanism generates a fixed number of redundant packets to protect the source packets in each block. Whilst implementationally straightforward, this method can not adapt dynamically to variations in the network conditions and may therefore result in network congestion or a poor loss recovery performance. The AFEC mechanism pre-sented in Fig. 1(b) overcomes this problem by dynamically ad-justing the number of redundant packets in accordance with the current network status. Previous studies have proposed the use of various network condition parameters to determine an appropriate FEC rate, including the packet error rate [11], the
transmission delay [12] and the Transmission Control Protocol (TCP) window size [13]. In general, the results have shown that such AFEC techniques provide a lower packet loss rate and a better video quality than SFEC mechanisms.
B. Analytical Model of Loss Recovery Under SFEC Mechanism
Since FEC schemes enable the recovery of data packets which would otherwise be lost, they yield an effective loss rate which is lower than the actual loss rate in the transmission network. As discussed above, in wireless networks protected by FEC schemes, provided that a minimum of packets belonging to the same block are correctly received, the entire block can be successfully recovered, irrespective of whether the received packets are source packets or FEC redundant packets . However, in developing the analytical model of the SFEC loss recovery performance, an assumption is made that for every recovered block, the receiver application receives a total of source packets, irrespective of the fact that some of the received packets may actually be redundant packets. Meanwhile, in an unrecovered block, it is assumed that the receiver application receives only the available source packets within the block, i.e. any redundant packets within the block are simply discarded.
Consider a video streaming file containing a total of video packets. Assuming that each transmission block comprises video packets, the video file is transmitted in a total of approx-imately blocks. Given an actual packet loss rate of , the probability of a block being successfully recovered is given by
(1)
where is the probability of the block being unrecovered and denotes all possible combinations of i packets suc-cessfully received in a whole block. In other words, the proba-bility that a block can not be recovered is given by
LIN et al.: A RED-FEC MECHANISM FOR VIDEO TRANSMISSION OVER WLANs 519
Since the video file comprises approximately blocks, the expected number of successfully recovered blocks can be esti-mated as
(3) while the expected number of unrecoverable blocks is given by
(4) From (3) and (4), the expected number of packets received by the receiver application can be estimated as
(5) The first and second terms in (5) give the total number of video packets received from the successfully recovered blocks and the unrecovered blocks, respectively. As shown in the first term, a successfully recovered block is assumed to yield video packets irrespective of whether the actual number of packets received is equal to or greater than . Furthermore, as shown in the second term, a block is deemed to be unrecoverable if more than packets are lost. Note that an assumption is made that just
packets are lost in an unrecovered block even if the actual number of loss packets exceeds . The equation con-siders the loss rate only in terms of the number of received video packets, i.e. the redundant packets received in the unrecovered blocks are assumed to be discarded. As a result, (5) gives a con-servative estimate of the SFEC loss recovery performance.
The expected number of packets lost during transmission is given by , and hence the effective packet loss rate for a video file delivered over a wireless link with SFEC protection is given by
(6) For a given packet loss rate, this model provides a simple means of predicting the effective packet loss rate in a wireless channel protected by a SFEC scheme.
C. Model Validation
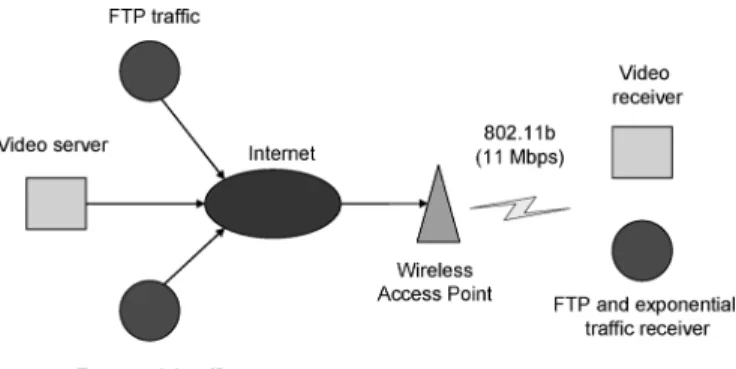
The analytical model developed in Section II was validated by comparing its results for the effective packet loss rate with those obtained from the NS-2 Network Simulator [18]. The sim-ulations are performed using the topology shown in Fig. 2, and utilized three video traces [19], including “Mobile”, “Highway” and “Akiyo”. These traces are encoded using the MPEG-4 stan-dard and are in QCIF format. Table I shows the number of video frames and packets of the video traces. Mobile (300 frames) is
Fig. 2. Simulation topology.
TABLE I
THEAMOUNTS OFVIDEOFRAMES ANDPACKETS OF THEVIDEOSOURCES
a motion type video, while Highway (2000 frames) and Akiyo (300 frames) are static video type. In the simulations, the video is streamed at the rate of 30 frames/sec, where each frame divided into 1000 bytes of transmission unit. The traces were transmitted using RTP/UDP/IP packets and are multicasted. Each transmission block comprises of eight packets. To sim-ulate a noisy environment, two additional traffic flows were also introduced. One of these is FTP traffic, transmitted using TCP packets, and another one is exponential traffic, transmitted using UDP packets. In our experiment we assume that the wired segment of the video delivery path was free of packet losses.
Figs. 3(a)–3(d) graphs shows the effective packet loss rate results obtained using the analytical model and the NS-2 simulator. The graphs are plotted against the actual packet loss rate for four different FEC redundancy rates. As shown in the legend, indicates the addition of a single redundant packet to the block, and is the insertion of two redun-dant packets, and so on. As expected, even in different types of video trace, the results show that the effective packet loss rate increases with the increasing packet loss rate. Furthermore, for a given packet loss rate, a higher FEC rate results in a lower ef-fective packet loss rate, and thus gives rise to an improved trans-mission quality. The results of the analytical model are in partic-ularly close to results obtained with those of the NS-2 simulator at low packet loss or at high values of the FEC rate. Moreover, the simulation results from static type video are more close to the analytical results than the results from the motion type video. As described in Section II, the analytical model described in (5) estimates the effective packet loss on a “best-case” basis. A de-viation of the predicted effective packet loss rate from the sim-ulated value is therefore to be expected under high packet loss rates or low FEC rates.
524 IEEE TRANSACTIONS ON BROADCASTING, VOL. 54, NO. 3, SEPTEMBER 2008
V. CONCLUSION
This paper has proposed a RED-FEC mechanism to improve the quality of video delivered over WLANs. Unlike previous AFEC schemes in which the FEC rate is determined on the basis of feedback information supplied by the receiver side, in the RED-FEC mechanism proposed in this study, an appro-priate FEC rate is determined by the wireless access point based upon an assessment of the current network traffic load. In the proposed approach, the RED-FEC algorithm tunes the number of redundant FEC packets in accordance with the access point queue length in such a way that the redundant packets injected for loss recovery purposes do not result in network congestion. Comparing the performance of the proposed RED-FEC scheme with that of the SFEC mechanism, it is found that the former demonstrates consistently higher recovery efficiency. Signifi-cantly, this performance improvement is obtained without in-jecting an excessive number of redundant packets into the net-work, and thus the overall network performance is improved.
REFERENCES
[1] M. Elaoud and P. Ramanathan, “Adaptive use of error-correcting codes for real-time communication in wireless networks,” in IEEE
Conf. Computer and Communications, INFOCOM1998, Apr. 1998,
vol. 2, pp. 548–555.
[2] H. Seferoglu, Y. Altunbasak, O. Gurbuz, and O. Ercetin, “Rate dis-tortion optimized joint ARQ-FEC scheme for real-time wireless multi-media,” in IEEE Conf. Computer and Communications, ICC2005, May 2005, vol. 2, pp. 1190–1194.
[3] I. Joe, “A novel adaptive hybrid ARQ scheme for wireless ATM net-work,” J. Wireless Networks, vol. 6, pp. 211–219, July 2000. [4] J. Paavola, H. Himmanen, T. Joela, J. Poikonen, and V. Ipatov, “The
performance analysis of MPE-FEC decoding methods at the DVB-H link layer for efficient IP packet retrieval,” IEEE Trans. Broadcasting, vol. 53, pp. 263–275, March 2007.
[5] H.-L. Lou, M. J. F.-G. Garcia, and V. Weerackody, “FEC scheme for TDM-OFDM based satellite radio broadcasting system,” IEEE Trans.
Broadcasting, vol. 46, pp. 60–67, March 2000.
[6] A. Nafaa, T. Ahmed, and A. Mehaoua, “Unequal and interleaved FEC protocol for robust MPEG-4 multicasting over wireless LANs,” in
IEEE Conf. Computer and Communications, ICC2004, June 2004,
vol. 3, pp. 1431–1435.
[7] K. Park and W. Wang, “QoS-sensitive transport of real-time MPEG video using adaptive forward error correction,” in IEEE Conf.
Mul-timedia Computing and Systems, MMCS1999, June 1999, vol. 2, pp.
426–432.
[8] P. Lettieri, C. Schurgers, and M. Srivastava, “Adaptive link layer strate-gies for energy efficient wireless networking,” J. Wireless Networks, vol. 5, pp. 339–355, Sep. 1999.
[9] J. C. Bolot and A. Vega-Garcia, “The case for FEC-based error control for packet audio in the Internet,” in Proc. ACM Multimedia Systems, Nov. 1996, pp. 429–439.
[10] I. V. Bajic, “Efficient cross-layer error control for wireless video mul-ticast,” IEEE Trans. Broadcasting, vol. 53, pp. 276–285, March 2007. [11] K. Takahata, N. Uchida, and Y. Shibata, “Packet error and frame rate controls for real time video stream over wireless LANs,” in Proc.
Dis-tributed Computing Systems Workshops, ICDCSW2003, May 2003, pp.
594–599.
[12] K. Park and W. Wang, “AFEC: An adaptive forward error correction protocol for end-to-end transport of real-time traffic,” in Proc.
Com-puter Communications and Networks, ICCCN1998, Oct. 1998, pp.
196–205.
[13] A. Chockalingam and M. Zorzi, “Wireless TCP performance with link layer FEC/ARQ,” in IEEE Conf. Computer and Communications,
ICC1999, Jun. 1999, pp. 1212–1216.
[14] H. Ma and M. E. I. Zarki, “A new transport protocol for broadcasting/ multicasting MPEG-2 video over wireless ATM access networks,” J.
Wireless Networks, vol. 8, pp. 317–380, July 2002.
[15] C.-H. Ke, N. Chilamkurti, G. Dudeja, and C.-K. Shieh, “A new adaptive FEC algorithm for wireless LAN networks,” in Proc. Networks and
Communication Systems, IASTED2006, Mar. 2006, pp. 425–428.
[16] M. Tun, K. K. Loo, and J. Cosmas, “Error-resilient performance of Dirac video codec over packet-erasure channel,” IEEE Trans.
Broad-casting, vol. 53, pp. 649–659, Sept. 2007.
[17] S. Floyd and V. Jacobson, “Random early detection gateways for congestion avoidance,” IEEE/ACM Trans. Networking, vol. 4, pp. 397–413, Aug. 1993.
[18] “NS-2 Simulator,” [Online]. Available: http://hpds.ee.ncku.edu.tw/ smallko/ns2/ns2.htm
[19] “YUV Video Sequences,” [Online]. Available: http://trace.eas.asu.edu/ yuv/index.html
[20] Q. Ni, L. Romdhani, and T. Turletti, “A survey of QoS enhancements for IEEE 802.11 Wireless LAN,” J. Wireless Communications and
Mo-bile Computing, vol. 4, pp. 547–566, Aug. 2004.
Cheng-Han Lin is currently a Ph.D. candidate
studying in the Department of Electrical Engi-neering, National Cheng Kung University, Tainan, Taiwan. Lin received his MS and BS degree from the Electrical Engineering Department of National Chung Cheng University in 2002 and 2004. His current research interests include wireless MAC protocols, multimedia communications, and QoS network.
Ce-Kuen Shieh is currently a professor teaching in
the Department of Electrical Engineering, National Cheng Kung University. He received his PhD, MS, and BS degrees from the Electrical Engineering Department of National Cheng Kung University, Tainan, Taiwan. His current research areas include distributed and parallel processing systems, com-puter networking, and operating systems.
Naveen Chilamkurti is currently a lecturer teaching
in the Department of Computer Science and Com-puter Engineering, La Trobe University, Australia. He is a Senior Member of IEEE and has published about 40 conference papers and two journal papers. He has a PhD from La Trobe University. His cur-rent research areas include wireless Multimedia, Multicast Congestion Control, Multicast Security, Reservation Protocols, TCP/IP Congestion Control, High-Speed Networks, IPv6 Security and Authenti-cation.
Chih-Heng Ke received his B.S. and Ph.D degrees in
Electrical Engineering from National Cheng-Kung University, in 1999 and 2007. His is an assistant professor of Computer Science and Information En-gineering, National Kinmen Institute of Technology, Kinmen, Taiwan. His current research interests include multimedia communications, wireless net-work, and QoS network.
Wen-Shyang Hwang received B.S., M.S., and Ph.D.
degrees in Electrical Engineering from National Cheng Kung University, Taiwan, in 1984, 1990, and 1996, respectively. He is currently a professor of Electrical Engineering, and the chairman of department of computer science and information engineering in National Kaohsiung University of Applied Sciences, Taiwan. His current research interests are in the fields of multimedia wireless communication, wireless mesh networks, storage area networks, WDM Metro-ring networks, perfor-mance evaluation, software design for embedded systems, Internet QoS, and Internet applications. He is a member of IEEE.