ABSTRACT
Over the past few years there has been rapid growth in the demand for mobile communications that has led to intensive research and development of complex PCS (personal communication services) networks. Capacity planning and performance modeling are necessary to
maintain a high quality of service to the PCS subscriber while minimizing costs. Effective and practical performance models for large- scale PCS networks are currently available. Two new performance models are presented in this article which can be solved using analyti- cal techniques. The first is the so-called portable population model, based on the flow equivalent assumption (the rate of portables into
a cell equals the rate of portables out of the cell). The model provides the steady-state portable population distribution in a cell that is
independent of the portable residual time distribution, which can be used by simulations to reduce the necessary execution time by reaching the steady state more rapidly. Additionally, this model can be used t o study the blocking probability of a low (portable) mobili-
ty PCS network and the performance of portable deregistration strategies. The second model is the so-called portable movement model which can be used t o study location tracking and handoff algorithms. The model assumes that the arriving calls t o a portable form a Poisson process, and portable residual times have a general distribution. This model can be used t o study location-tracking algorithms and handoff algorithms. It is shown that under some assumptions, the analytic techniques are consistent with the simulation model.
Modeling Techniques for
Large-scale PCS Networks
Yi-Bing Lin, National Chaio Tung Universitypersonal communications services (PCS) network [l] is a wireless network that provides communication services for PCS subscribers. The service area of a PCS net- work is populated with base stations. The radio coverage of a
base station is called a cell. The base station locates a sub- scriber or portuble, and delivers calls to and from the portable by means of paging within the cell it serves. A registration area (RA) consists of an aggregation of cells, forming a con- tiguous geographical region. T o connect a phone call to a roaming portable, it is necessary to identify the portable’s RA. The strategies commonly proposed are two-level hierarchies [2] that maintain a system of home and visited databases (home location registers, or HLRs, and visitor location regis- ters, or VLRs). To order PCS services, a PCS subscriber must “enroll” with a particular PCS provider. When enrolling, the PCS subscriber gives the PCS provider the necessary informa- tion, such as credit, service type, and current location, to set
up the PCS account. This PCS account information is stored in the HLR of the PCS provider. When the PCS subscriber roams to another RA, which is likely to be owned by another PCS provider, the PCS subscriber becomes a “visitor” of that RA. The VLR of this RA is used to store the visiting PCS subscriber’s information. Upon registering with the VLR, the VLR notifies the HLR of the visiting PCS subscriber that “your subscriber is at my place.”
General models are needed to understand different aspects of large-scale PCS networks (such as user location strategies [3-51, registration strategies [6-91, handoff or automatic link transfer strategies [lo-141, and channel allocation strategies [15-181) so that the network will provide a high quality of ser- vice to mobile subscribers while minimizing the resource cost incurred by the PCS provider.
In this article we are concerned with analytic models for large-scale PCS networks. Analytic models are able to capture the behavior of a system in a concise mathematical formulation
without the high computational overheads associated with large simulations. Accordingly, we describe two analytic models that will reduce the effort involved in studying the behavior of large- scale PCS networks. The first model is called theportuble popu- lation model, and is based on the flow equivalent assumption (the rate at which portables move into a cell is equal to the rate at which they move out of the cell). This model enables deter- mination of the steady-state portable population distribution in a cell that is independent of the portable residence time distri- bution. The model can be used to study the blocking probability of low-mobility (portable) PCS networks and the performance of portable deregistration strategies. The second model is the so-called portable movement model. By assuming that the arrival of calls to a portable form a Poisson process, and portable resi- dence times have a general distribution, this model can be used to study location tracking and handoff algorithms.
The main contribution of this article is to illustrate that effective, practical models for large-scale PCS networks are available to provide essential quantitative information to net- work designers.
PCS
NETWORK PLANNING lSSUEShe PCS business has been grown very fast since 1990.
T
Worldwide and U.S. cellular subscribers growth is illustrat- ed in Fig. 1.The challenge of the PCS business is that customer demand has increased dramatically every year. Thus, sophisticated perfor- mance evaluation must be conducted to provide guidelines for PCS network planning. Several network planning issues and the modeling techniques described in this article are listed below.
ISSUE 1
As the subscriber population grows, the capacities of databases (i.e., VLRs) should be upgraded so the probability that the
H Figure 1. Cellular subscribergrowth.
database is full when a portable arrives is less than a thresh- old. This issue can be modeled by techniques 2 and 3 described in this article.
ISSUE
2
For a low-mobility/stationary PCS systems without handover (e.g., the CT2 systems developed in Asia Pacific regions), an appropriate performance model is required for capacity plan- ning, which is different from thie modeling of high-mobility cellular systems. An example of the “appropriate model” is technique 1, which is also a perfect modeling approach for nomadic computing networks where mobile users are station- ary when they compute (survey data indicate that users sel- dom use their notebook when thley are walking or driving).
ISSUE
3
While the cellular subscriber population grows every year, the average call holding time decreases. According to CTIA’s Industry Survey, the average call holding time has been decreased from 2.24 min to 2.115 min. Thus, radio capacity planning for a PCS system should consider the change in aver- age call holding time as well as that in incoming traffic. This issue can be modeled by technique 4.
ISSUE
4
Rapid PCS customer population growth implies that PCS roaming management will generate large volumes of signaling traffic to the public switched telephone network. Thus, new roaming management protocols and evaluation methods should be developed. Techniques 2 and 3 model protocols that reduce deregistration traffic and those that reduce regis- tration traffic.
THE PORTABLE
POPULATION
MODEL
his section describes a portable population model. An
T
important fact observed from1 this model is that the steady- state portable population in a cell is insensitive to the distribu- tion of portable residence times.Let N be the expected number of portables in a cell. Sup-
pose the residence time of a portable in a cell has a general distribution F(t) with mean l/q. In the steady state, the rate at which portables move into a cell equals the rate at which they move out of the cell. The arrivals of portables can be viewed as being generated from N input streams which have the same general distribution with arrival rate q. The net input stream to a cell can be approximated as a Poisson process with arrival rate h* = Nq. Thus, the distribution for the portable popula- tion can be modeled by an MIG/- queue with arrival rate h*
H Figure 2. Population distribution.
and service rate q. Let IC,, be the steady state probability that
there are n portables in the cell. The steady-state probability
IC, that there ar e n portables in the cell can b e computed
from [19]
h*
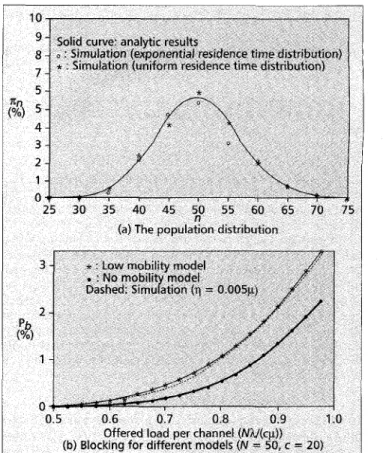
Figure 2a illustrates the population distribution when N = 50. The solid curve plots IC,, based on Eq. 2. The “0” marks
represent IC, obtained from simulation where the portable res- idence times are exponentially distributed, the
“*”
marks sim- ulation results for a uniform portable residence time distribution. The figure indicates that the population distribu- tion for a cell is insensitive to the portable residence time dis- tributions, and Eq. 2 is consistent with the simulation results.We list two modeling techniques based on the population model.
TECHNIQUE 1 : LOW MOBILITY
PCS
NETWORKEquation 2 can be used to study the blocking probabilitypb for a PCS network of portables with low mobility. The idea is as follows. First, the blocking probability Pbn is derived for a cell when there are n portables. With the low mobility assump- tion, the blocking probability for the cell is then
(3)
where c is the number of channels in a cell.
Consider a PCS network where every cell has c = 20 chan- nels. A phone call is dropped immediately if no channel is available. Suppose that the phone calls to/from a portable are a Poisson process with rate h, and the call holding time is an
Figure 3. The relationship among to ti, and t, replaced by llE[z]; that is, Nn T
exponentially distributed random variable with mean
ilk.
Fig- ure 2b plots the blocking probability P b against NhlcP., the offered load carried by a channel. The curve marked repre- sents the no-mobility model, which is a blocking system with finite sources. In this model, the number of portables N in a cell is fixed. When N >> c, the no-mobility model approaches the Erlang-B system. The curve marked * represents the low- mobility model (Le., Eq. 3) Whereinpbn in Eq. 3 is derived from the no-mobility model with population n. The dashed curve represents simulation results when the mobility q = 0 . 0 0 5 ~ . Figure 2b indicates that our low-mobility model is consistent with the simulation study, while the no-mobility model cannot accurately or appropriately predict the cell b1uckiIig probability.TECHNIQUE 2: PORTABLE REGISTRATION
In a PCS network, registration is the process by which portables inform the network of their current location (i.e., registration area or RA). Every registration area is associated with a loca- tion database, the VLR. A portable registers its location in the VLRs when it is powered on and moving between registration areas. If the VLR is full, the portable cannot access the ser- vices provided by the PCS network. When a portable leaves an R A or shuts off for a long period of time, the portable should be deregistered from the R A so that any resources previously assigned to the portable can be deallocated.
In IS-41 [20, 211, the registration process ensures that a portable registration in a new R A causes deregis-
tration in t he previous RA. This approach is referred to as explicit deregistration. Bellcore Per- sonal Access Communications Systems (PACS) [6] specifies that a portable should be deregistered by default after a certain time period elapses without the portable reregistering. This scheme is referred to as timeout deregistration [9]. In the above regis- tration schemes, it is important to determine (based on the amount of resources for an RA) the proba- bility
p
that a portable cannot register (and receive service) because the database is full. The popula- tion model can be used to determineP
for different registration schemes.Let M be the amount of resources available in an RA. Suppose that the portable residence times have an arbitrary distribution with mean liq, and let N be the expected number of portables in an RA; then
PED
(the probabilityp
for explicit dereg- istration) is(4)
PED
=Z z n
MSn<==where 7cn is given in Eq. 2. For the timeout scheme,
the arrivals of portables seen by the scheme is the same as the explicit deregistration (i.e., the arrival rate Nq). However, the expected portable resi- dence time E [ T ] seen by the timeout scheme is longer than llq because the scheme is only sure that a portable leaves the RA if the portable does not send a reregistration message within a timeout period T. For exponential portable residence time distribution, E [ T ] can be expressed as
OVEMENT
MODEL
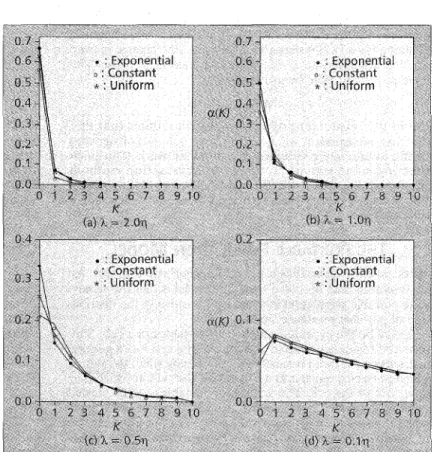
ere we describe a portable movement model [22] to study the patterns of incoming calls and portable movement. The probability a ( K ) that a portable moves across K RAs between two phone calls is derived assuming that the incom- ing calls to a portable are a Poisson process, and the time the portable resides in an R A has a general distribution. This study indicates that for a portable with different RA residence time distributions (such as exponential, constant, and uniform distributions) the a(K) distributions are similar if the portable mobility is high, and the
a(K)
distributions are very different if the portable mobility is low.L e t t, b e t h e time interval between two consecutive p h o n e calls t o a p o r ta b le p. Suppose t h at t h e p o r ta b le resides in an RA Ro when the first phone call arrived. After the phone call, p visits another K RAs, a n d p resides in the ith R A for a time period t,(O I i
<
K ) . Let t , be the time interval between the arrival of the first phone call and the time when p moves out of Ro. The relationship among t,, t, and t, is shown in Fig. 3.We make the following assumptions:
The phone calls to a portable are a Poisson process. In other words, t, is exponentially distributed with mean E[tJ = 1IL.
ti are independent and identically distributed random variables with a general density function f ( t J , and mean
The probability
a(K)
that p moves across K RAs between E[ti] = l/q.two phone calls is a( K ) = 3
h[t, + t l
+...+
t K - 1 < t , r; t, + f l+...+
t K ] K 2 1 (5)Pr[tc < t m ] K = O
a ( K ) =
where
f
*
(4
= jt:f-"f(t)dt (7)is the Laplace-Stieltjes Transforim for f ( t J . Equation 6 is gen- eral enough to accommodate any portable mobility patterns. (i.e., arbitrary f(t,) functions). Note that the Laplace pairs for many functions are already available [24, 251.
If ti is exponentially distributed, then from Eq. 6,
r
f * ( h ) = - q + h ' and.[
-q-qr
K 2 1-
1-- 1-e h 1-1[1-2[-[$]] h K = O q K h K T 11
5
K = O (q+
Z)K+' a ( K ) = K = OThe intuition behind Eq. 8 is the following. Since to is exponentially distributed, the ''excess life" t, has the same dis- tribution as to [23]. Since both tc and tm are exponentially dis- tributed,
which is consistent with the case K = 0 in Eq. 8. Now consider
K > 0. When the portable moves into R j , the remaining time before the second phone call has the same distribution as t, (due to the memoryless property of an exponential distribu- tion). If the portable does not receive the second phone call before it enters R , , then the probability that the portable
receives the second call before it leaves Ri is q = h/(q
+
h). Thus,a Q
has a geometric distributionThe result is the same as the case K 2 1 in Eq. 8.
For the constant portable rlesidence time distribution with mean q,S;(h) = e-"?, and
( K - I ) h
l:[l-."\
e-7-
K > lFor the uniform portable residence time distribution in the range [0, 2/q],f*(h) = q/2h(l -- e-2h/?), and
TECHNIQUE 3: LOCATION TRACKING
In a PCS system, the R A of a called portable must be deter- mined before a connection can be established. Due to the mobility of portables, the HLR is required to store the loca- tion (i.e., address of the visited RA) of a portable. The loca- tion record is modified when the portable moves to another RA. Every R A is associated with a VLR. (A VLR may serve one or more RAs. For demonstration purposes, we assume that each VLR serves an RA.) In IS-41, when a portable moves from an RA to another RA, it registers at the VLR of the new RA, and its new location is reported to the HLR.
A technique called location forwarding was proposed to reduce the location update cost in a PCS network [SI. The idea is described as follows. When a phone moves to a new RA, no message is sent to update the HLR. Instead, a mes- sage is sent to the old R A to create a forwarding pointer to th e new RA. The cost of creating a forwarding pointer is assumed to be more economical than the modification of the location record at the HLR. When an incoming call arrives, the forwarding pointers are traced to find the actual location of the phone.
Suppose that during two incoming calls, the phone moves to new RAs K times, and the number of forwarding pointers traced to find the actual location is k . Then the cost saved in the location forwarding (compared with the IS-41 scheme) is
K operations to update the HLR. On the other hand, the
extra penalty paid in the location forwarding is k operations to trace the forwarding pointers when a portable is located. Since the phone may revisit an RA, we have k 2 K. Thus, the key issue of modeling location forwarding is to derive the val- ues f o r k and K. The K distribution can be derived based on
the portable movement model (i.e., Eq. 5). The derivation of k can be done by using a two-dimensional random walk with reflecting barriers.
TECHNIQUE 4: HAND-OFF ALGORITHMS
As noted earlier, when a portable moves from one cell to another while a call is on progress, the call requires a new channel (in the new cell) to continue. If no channel is avail- able in the new cell, the call will be dropped or forced termi- nated. The forced termination probability is an important criterion in the performance evaluation of the PCS network. Forced termination of an ongoing call is considered less desir- able than blocking of a new call attempt. Several handoff schemes have been proposed (see [12] for a survey) to reduce forced termination. Performance modeling of the handoff schemes has been intensively studied. I n most modeling efforts (either analytic analysis or simulation) [lo-12, 14, 261,
a single cell is studied by assuming that both new call attempts and handoff calls are Poisson processes with arrival rate
A,
and Ah, respectively. Then modeling techniques a r e used t o simulate t he behavior of a specific handoff scheme with aggregate call arrivals where out- put measures such asp, (the new call blocking probability ), p f (the forced ter- mination probability), and pnc (the prob- ability that a call cannot complete due to blocking or forced termination) are derived. In this model, h h cannot be arbitrary selected. Rather, hh, p,, and p f are affected by each other and by the portable mobility rate q. Based on the portable movement model described in this section, a simple relationship amongh h , p,, pf, and q can be derived using the following idea [ll].
Figure 5. The comparison of pnc for
analytical results and simulation results (q equals the call completion rate, and the number of channels in a cell is 10).
Suppose that a portable moves across K cell boundaries during a call holding time, assuming that the call is complet- ed; that is, K is the number of handoffs before the call i s com- pleted. The call is referred to as a K-handoff call. If we modify our portable movement model such that tc represents a call holding time (and h is replaced by p in Eq. 6), then a ( K ) is the probability of a K-handoff call. For a K-handoff call, let j be the number of portable moves before the call i s blocked or successfully terminated, where J 5 K. The probability
a(K)
can be used to derive the expected number E[JI. The idea is the following. We first express the conditional probability Pr[J
= j l K = k ] as a function ofpf Then Pr[J = j l K = k ] is used to derive E[JlK = k ] , the expected number of I for a k-hand- off call.
k
E [ J I K = k ] = j P r [ J = j I K = k ] =
j = O Pf
Finally, E[Jl is derived by using E[JIR = k ] and
a@):
where S; is defined in Eq. 7. By assuming homogeneous cells in a PCS network, hh is expressed as
(9) Thus, we may derivep, andpfby an iterative process [IO]: Select an initial Ah value to obtainp, an d p f fo r a particular handoff strategy (analytical models have been developed to derive po and pf for the nonprioritized, guard channel, and queuing priority schemes [ll]). Then Eq. 9 is used to compute the new hh value which is used to obtain new values forp, and
&.
The process iterates until the value for Ah converges. Figure 5 comparesp,, (the probability that a call cannot complete due to blocking or forced termination) for the ana- lytical and simulation results. The curves indicate that the analytical results are consistent with the simulation experiments.CONCLUSIONS
his article described analytic approaches in developing
T
practical models for large-scale PCS networks. Based on the flow equivalent assumption (the rate of portables moving into a cell equals the rate of portables moving out of the cell), a portable population model was described. The model pro- vides the steady-state portable population distribution in a cell that is independent of the portable residence time distribu- tion, which can be used by simulations to reduce the necessaryexecution time by reaching the steady state more rapidly. Additionally, this model can be used to study the blocking probability of a low-mobility (portable) PCS network and the performance of portable deregistration strategies.
Then we described a model for
portable movement. The model assumes that the arrival calls to a portable form a Poisson process, and portable resi- dence times have a general distribution. This model can be used to study loca- tion-tracking and handoff algorithms.
We showed that under some assump- tions, the analytical techniques produce results consistent with those of the sim- ulation experiments.
ACKNOWLEDGMENTS Ian Akyildiz provided valuable ideas and comments that have significantly improved the quality of this article. This article is an extension of Chapter 17, The State of the Art in Perfor- mance Modeling and Simulation. This work was supported in part by National Science Council, Contract No. NSC 86-2213-E- 009-074.
REFERENCES
[ I 1 D. C. Cox, "Wireless Personal Communications: What Is It?" /€E€ Pers. Commun., Apr. 1995, pp. 20-35.
[21 Y.-B. Lin and S . K. DeVries, "PCS Network Signaling Using 55.7," /E€€
Pers. Commun. Mag., June 1995, pp. 44-55.
[31 1. S. M. Ho and I. F. Akyildiz, "Local Anchor Scheme for Reducing Sig- naling Cost i n Personal Communication Networks," /EE€/ACM Trans. Networking, Oct. 1996.
[U] J. 5. M. Ho and I. F. Akyildiz, "Mobile User Location Update and Paging under Delay Constraints," ACM-Baltzer J. Wireless Networks, vol. 1, no. 151 R. Jain e t al., "A Caching Strategy t o Reduce Network Impacts of PCS,"
/€€€JSAC, vol. 12, no. 8, 1994, pp. 1434-45.
[61 Bellcore, "Generic Criteria for Version 0.1 Wireless Access Communica- tions Systems (WACS and Supplements," Tech. Rep. TR-INS-001313, Issue 1, 1994.
[71 J. S. M. Ho and I. F. Akyildiz, "On Location Management for Personal Communications Networks," /€E€ Commun. Mag., Sept. 1996.
[8] I, F. Akyildiz and J. S. M. Ho, "Dynamic Mobile User Location Update for
Wireless PCS Networks," ACM-Baltzer J. Wireless Networks, vol. 1, no. 1, 1995, pp. 187-96.
[9] P. Porter e t al., "The Terminal RegistrationiDeregistration Protocol for Personal Communication Systems," Proc. Wireless '93, July 1993. IO] D. Hong and S . S . Rappaport, "Traffic Model and Performance Analysis
for Cellular Mobile Radio Telephone Systems with Prioritized and Non- Protection Handoff Procedure," /€€€ Trans. Vehic. Tech., vol. VT-35, no.
1 I ] Y.-B. Lin, S. Mohan, A. Noerpel, "Queueing Priority Channel Assign- ment Strategies for Handoff and Initial Access for a PCS Network," /€€€ Trans. Vehic. Tech., vol. 43, no. 3, 1994, pp. 704-12.
121 S. Tekinay and B. Jabbari, "Handover Policies and Channel Assignment Strategies in Mobile Cellular Networks, /€E€ Commun. Mag., vol. 29, no. 11, 1991.
[I31 5. Tekinay and B. Jabbari, "A Measurement Based Prioritization Scheme for Handovers in Cellular and Microcellular Networks," /E€€ JSAC, Oct. 1992, pp. 1343-50.
[I41 C. H. Yoon and K. Un, "Performance of Personal Portable Radio Tele- phone Systems With and Without Guard Channels," /E€€ JSAC, vol. 11, no. 6, Aug. 1993, pp. 911-17.
[ I 5 1 5 . M . Elnoubi, R. Singh, S . C. Gupta, "A New Frequency Channel Assignment Algorithm in High Capacity Mobile Communications Sys- tems," /€E€ Trans. Vehic. Tech., vol. VT-31, no. 3, 1982, pp. 125-31. 1161 T. J . Kahwa and N. D. Georganas, "A Hybrid Channel Assignment
Scheme in Large-scale, Cellular-Structure Mobile Communication Sys- tems," /E€€ Trans. Commun., vol. COM-26, no. 4, Apr. 1978, pp. 432-38. [I71 5 . 5 . Kuek and W. C. Wong, "Ordered Dynamic Channel Assignment
Scheme with Reassignment in Highway Microcells," /€€E Trans. Vehic. Tech., vol. 41, no. 3, 1992, pp. 271-77.
1181 M . Zhang and T.-S. Yum, "Comparisons of Channel-Assignment Strate-
gies i n Cellular Mobile Telephone Systems," I€€€ Trans. Vehic. Tech., vol. 38, no. 4, 1989, pp. 211-15.
4, 1995, pp. 413-26.
I191 L. Kleinrock, Queueing Systems: Volume /-Theory, New York Wiley, 1976.
[20I Bellcore, ”Network and Operations Plan for Access Services t o Personal Communications Services Systems,” issue 2, Tech. Rep. SR-TSV-002459, 1992.
[21] EINTIA, “Cellular Radio-Telecommunications Intersystem Operations,” Tech. Rep. IS-41 rev. B, 1991.
[22] I . F. Akyildiz, S. M . Ho, and Y.-B. Lin, “Movement-Based Location Update and Selective Paging for PCS Network,” IEEEIACM Trans. Net- working, Aug. 1996.
[23] S. M. Ross, Stochastic Processes, John Wiley & Sons, 1983.
/24] E. J. Muth, Transform Methods with Applications to Engineering and [25] E. J. Watson, Laplace Transforms and Applications, Birkhauserk, 1981. [26] G. J. Foschini, B. Gopinath, and Z. Milijanic, “Channel Cost of Mobili-
ty,“ lEEE Trans. Vehic. Tech., vol. 42, no. 4, Nov. 1993, pp. 414-24.
Operations Research, Upper Saddle River, NJ: Prentice Hall, 1977.
BIOGRAPHY
YI-BING LIN [ S M ] received his B.S.E.E. degree from National Cheng Kung uni- versity in 1983, and his Ph.D. degree in computer science from the Univer- sity of Washington i n 1990. Between 1990 and 1995, he was w i t h the Applied Research Area at Bell Commuriications Research (Bellcore), Morris-
town, New Jersey. In 1995, he was appointed full professor of the Depart- ment of Computer Science and Information Engineering, National Chiao Tung University. In 1996, he was appointed deputy director of the Micro- electronics and Information Systems Research Center, NCTU. His current research interests include design and analysis of personal communications services networks, mobile computing, distributed simulation, and perfor- mance modeling. He i s an associate editor of the ACM Transactions on Modeling and Computer Simulation, a subject area editor of the Journal o f Parallel and Distributed Computing, an associate editor of the lnternational Journal in Computer Simulation, an associate editor of lEEE Network, an associate editor of SIMULATION magazine, an area editor of ACM Mobile Computing and Communication Review, a columnist for ACM Simulation Digest, a Departrhent Editor for lEEE Personal Communications, a member of the editorial board of the lnternational Journal o f Communications, a member of the editorial board of Computer Simulation Modeling and Anal- ysis, Program chair for the 8th Workshop on Distributed and Parallel Simu- lation, General Chair for the 9 t h Workshop on Distributed and Parallel Simulation, Program Chair for the 2nd International Mobile Computing Conference, p u b l i c i t y chair of ACM Sigmobile, Guest Editor for t h e ACMIBaltzer WlNET special issue on Personal Communications, and Co- Guest Editor for /E€E Transactions on Computers special issue on Mobile Computing. Dr. Lin’s email address is liny@csie.nctu.edu.tw.