Location Awareness
in Ad Hoc Wireless
Mobile Networks
A
dvances in wireless communications andsmall, lightweight, portable computing devices have made mobile computing pos-sible. One research issue that has attracted much attention recently concerns the design of a manet—a mobile ad hoc network that con-sists of a set of mobile hosts that roam at will and communicate with one another. Communication takes place through wireless links among mobile hosts, using their antennas, but such an environment sup-ports no base stations. Further, the transmission dis-tance limitation means that mobile hosts may not be able to communicate with one another directly. Hence, a multihop scenario occurs, and several hosts may need to relay a packet before it reaches its final destination. This situation requires each mobile host in a manet to serve as a router.
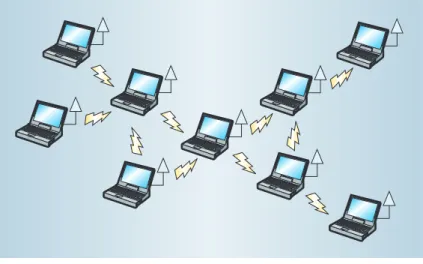
Figure 1 shows a typical manet, which works best in situations like battlefields, festival grounds, assemblies, outdoor activities, rescue actions, or major disaster areas, where users need to deploy networks immedi-ately, without the benefit of base stations or fixed net-work infrastructures. For example, when an earth-quake occurs, the lack of electricity pulls all base sta-tions offline. In this case, system administrators can easily deploy a battery-powered manet to set up a net-work environment.
The extensive manet research efforts focus on the following:
• Unicast. Manets find a routing path from a source node to a destination node. These routing proto-cols are either proactive or reactive. A proactive protocol, such as the destination-sequenced dis-tance-vector (DSDV), constantly updates the
routing table at each node to maintain a nearly global view on the network topology. In contrast, a reactive protocol makes on-demand searches for a path, which can be less costly than a proac-tive protocol when host mobility is high. Representative reactive protocols include dy-namic source routing (DSR), zone routing proto-col (ZRP), and ad hoc on-demand distance vector (AODV).1
• Collective communication. This approach in-volves more than one destination, such as multi-cast, in which the protocols are either tree based or flooding based. A tree-based protocol tries to establish a multicast tree among the multicast members that comprise a wireline network, while a flooding-based protocol simply distributes the multicast message all around the network. • Quality-of-service routing. This type of routing
supports real-time applications such as audio and video communications. The protocol must estab-lish a route that satisfies certain QoS constraints, such as delay and bandwidth. For example, a ticket-based approach avoids unwise blind flood-ing by usflood-ing tickets to limit the number of route-searching packets.
Because manets must operate in a physical geomet-ric space, they naturally need to exploit location infor-mation. Location awareness means that each mobile host uses a positioning device to determine its current physical location. If we know the mobile hosts’ loca-tions, we can accurately describe their geometric rela-tionship. Without such information, we can only represent a manet by depicting the hosts’ connectivity abstractly in, for example, a graph.
Networks composed of dynamically repositioning mobile hosts require
location awareness to provide new geographic services and to maximize
routing efficiency and quality of service.
Yu-Chee
Tseng
National Chiao-Tung UniversityShih-Lin Wu
Wen-Hwa
Liao
Chih-Min
Chao
National Central UniversityC O V E R F E A T U R E
Researchers have proposed several approaches to exploiting location information in a manet, including descriptions of how location information can assist manet routing.2-5Research has also uncovered meth-ods for providing context- and location-aware ser-vices, such as geographic messaging,6-8in a manet.
LOCATION-AWARE COMPONENTS
A location-aware computing device uses an attached receiver to catch outside signals that it uses to analyze and determine its current position. The availability of these signals can be quite different in outdoor and indoor environments.
Outdoor positioning
The Global Positioning System, the worldwide satellite-based radio navigation system, offers perhaps the easiest way to determine a device’s location. The system consists of 24 satellites in six orbital planes operating in circular, 10,900-nautical-mile orbits at an inclination angle of 55 degrees in a 12-hour period. Operating on the L-band frequencies—L1 is 1575.42 MHz and L2 is 1226.6 MHz—GPS can be used any-where near the Earth’s surface. The system’s satellites transmit navigation messages that contain their orbital elements, clocks, and statuses, which a GPS receiver uses to determine its position and thus its roaming velocity. Determining the receiver’s longitude and lat-itude requires three satellites, and adding a fourth can determine the receiver’s altitude. Using more satellites increases the accuracy of the readings, for which the error rate typically ranges in a few tens of meters.
Appropriate for outdoor use, GPS receivers can pro-vide positioning accuracy in the 15-meter range. Assistance from ground stations improves accuracy. Such systems, called differential GPSs, can reduce the error to less than a few meters. Recently, the US gov-ernment discontinued selective availability, which had intentionally degraded civilian GPS signals (http://www. igeb.gov/sa/whfactsheet.txt). Analysts expect that this ruling will increase GPS accuracy significantly.
Indoor positioning
Despite GPS’s many advantages and great accuracy, the system suffers from a significant drawback: Buildings can easily block its satellite signals. Leading candidates for indoor location identification include short-range radios and infrared sensors. Some researchers have built an indoor positioning system that uses infrared sensors.9In this system, several infrared transmitters, which can automatically send their own IDs, hang from various places on a building, such as walls, doors, rooms, and corridors. A computing device with an infrared receiver uses these signals to determine its current position. Infrared sensors offer the advan-tages of low cost and low power consumption.
Developers could use an infrared positioning sys-tem, for example, to build an automatic tour-guide system. In an exposition site such as an art gallery, the curators could attach an infrared transmitter to each piece of artwork that periodically sends out a unique ID. When they roam into the infrared transmitter’s coverage range, tourists with a PDA in hand will see a screen that automatically displays information related to the artwork.
Because infrared signals are directional and inter-vening objects can easily block them, radio-based positioning may be a more attractive alternative. Omnidirectional radio transmission offers the possi-bility of, for example, developing Bluetooth devices for short-range communication (http://www.blue-tooth.com/).
LOCATION-AWARE ROUTING PROTOCOLS
A routing protocol’s main job is to find a path from a source node to a destination node. Because of its dynamically changing topology, a manet routing pro-tocol encounters more limitations than its wireline counterpart. Manet protocols also suffer the limita-tion of scarce wireless bandwidth. One prospective approach to assist routing in a manet leverages the data available from location information.
From a graph viewpoint, routing in a manet is like finding a path—typically the shortest—from a source to a destination in a graph. However, we can use the extra location information that mobile hosts provide to exploit the geometric relationship among those hosts. Researchers have thus developed several routing-issue optimizations that feature location awareness.
Location-aided routing
The proposed location-aided routing (LAR) proto-col3uses selective flooding to exploit location infor-mation when searching for a route. On requiring a route, most traditional approaches—such as DSR,
Figure 1. Typical manet, a mobile ad hoc network consist-ing of a set of mobile hosts that roam at will and communi-cate with one another. The environment does not host base stations—communi-cation takes place through wireless links. Each mobile host serves as a router, and several hosts may need to relay a packet before it reaches its final destination.
ZRP, and AODV—initiate a route request packet, which floods throughout the entire manet. This activ-ity wastes a lot of bandwidth and can initiate a broad-cast storm10when contention and collision occur on the media-access layer.
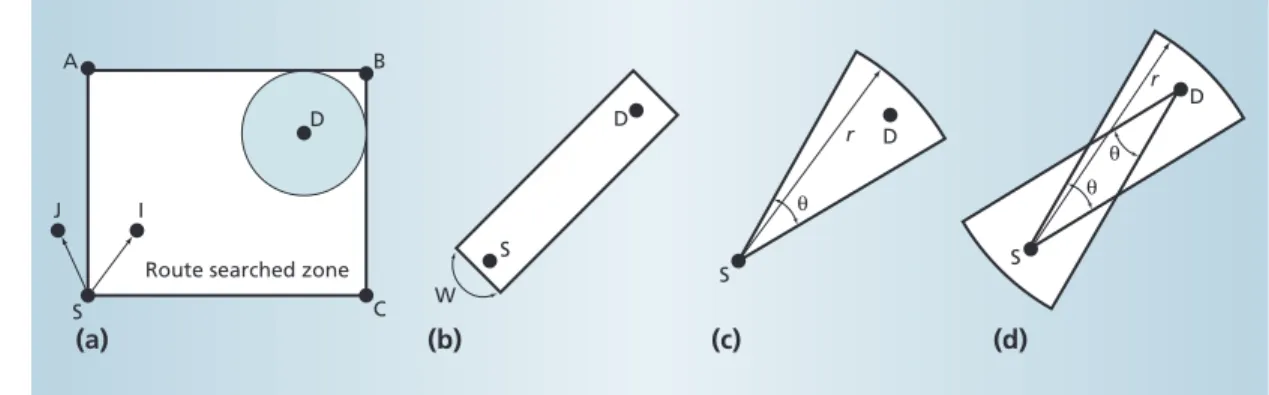
In the LAR protocol, on requiring a route from source S to destination D, instead of flooding the whole manet, the system defines a smaller forwarding zone that covers both S and D. The forwarding zone seeks the smallest rectangle that can bound S’s current location and D’s possible location. In the example shown in Figure 2a, D’s expected location is a gray circle within a rectangle that represents the route-searched zone. Host I, located in the forwarding zone, is responsible for rebroadcasting the route request packet, but host J, outside the forwarding zone, is not responsible for rebroadcasting the packet. Carefully choosing the forwarding zone saves bandwidth.3 Figures 2b, 2c, and 2d show the bar, fan, and dual-fan forwarding zone optimizations.4
Gedir
Geographic distance routing (Gedir),5a location-aware routing protocol, works in a connectionless mode to send data packets directly without establish-ing paths a priori. Researchers have proposed several approaches for using this protocol to send data pack-ets. In one approach, X always picks as Y, the next host, the receiver that has the smallest angle from X to Y and to the destination. However, this can result
in an endless loop that never reaches the destination. In the second approach, X always picks as Y the receiver closest to the destination. However, in certain situations, Y might be farther from the destination than X, creating a relationship similar to a detour. This scenario also can lead to an endless loop.
Based on these approaches, several variations, such as f-Gedir (in which “f” stands for flooding) and c-Gedir (in which c stands for concurrently sending from the source to c hosts, each of which will try to find a path based on Gedir), may further improve performance.
Grid
The Grid protocol’s core concept calls for parti-tioning the geographic area into several squares in Euclidean spaces called grids.4In each grid, one mobile host, if any, is elected the grid’s leader. Grid leaders perform routing grid by grid, while nonleaders have no such responsibility. This protocol is considered fully location-aware because it exploits location informa-tion in route discovery, packet relay, and route main-tenance. If a protocol does not use location infor-mation in all parts of route delivery, packet relay, and route maintenance, it is partially location aware.
The Grid protocol uses location information in various ways:
• Route discovery. The forwarding-zone concept confines the route-searching area. However, only grid leaders conduct route searches. The route request packets that nonleader hosts in a grid transmit will most likely be redundant because their packets will overlap with areas the grid lead-ers cover. Without this mechanism, the search can send many unnecessary route request packets. With such a filtering mechanism in place, the Grid protocol is useful in a crowded environment because of its insensitivity to host density. • Packet relay. A grid ID, rather than a host ID,
represents a route. Specifically, each entry in a routing table records the next grid that will lead to the destination. For example, in Figure 3a host A will register grid 3,2 instead of B’s address as the next hop to reach D. Because routing tables use grid IDs, they offer stronger, more resilient route maintenance.
• Route maintenance. This approach offers routes highly resilient to host mobility. For example, in Figure 3b, when host A roams away, the system
D S θ r D S θ r θ S S I J A
Route searched zone
(a) (b) (c) (d)
B
C W
D D
Figure 2. The location-aided routing (LAR) protocol uses selec-tive flooding to search for routes. Forwarding zone optimizations confine the route-searching area: (a) rectangle, (b) bar W, (c) fan, and (d) dual fan; r and θ are tunable parameters. 0 1 2 3 4 5 S A B C D A S B C D 0 1 2 3 0 1 2 3 4 5 0 1 2 3 Leader Nonleader
Figure 3. A routing example in the Grid protocol. (a) Routing tables offer stronger, more resilient route maintenance because they use grid IDs to represent a packet-relay route. (b) Route maintenance is highly resilient to host mobility because the system elects a new leader when the current leader roams out of the defined grid.
elects another host in grid 2,2 as the new leader to take over the packet-relaying job. In protocols such as DSR, ZRP, AODV, and LAR, when an inter-mediate host in a route roams outside its neigh-bors’ range, the route breaks. Longer routes are especially vulnerable to this outcome. However, with the Grid protocol, even if S roams out of its original grid, the route can persist. For example, in Figure 3b, when S moves to grid 1, 0, another host in grid 1,1 can serve as the new leader.
The maintenance jobs this protocol requires include leader election and routing table handoff. In each grid, the host must run a leader election protocol to main-tain its leader. Also, when a leader roams off its orig-inal grid, a simple handoff procedure, implemented via broadcast, must take place to pass the routing table to the next leader. Grid can survive a much longer route life than other protocols while remaining less vulnerable to host mobility. Because it identifies lead-ers and nonleadlead-ers, Grid can handle high volumes of control traffic while remaining insensitive to host den-sity, making it scalable to larger networks.
Zone-based two-level routing
The two-level zone-based peer-to-peer protocol resembles Grid but adopts a hierarchical approach.2 As Figure 4 shows, this protocol divides the manet’s geographic area into several zones. Through a GPS receiver, each mobile host knows its current position and thus its zone ID.
The protocol adopts a proactive approach in which it distributes link states from time to time throughout the network. To save bandwidth, the protocol uses a two-level hierarchy to send two types of link-state packets: intrazone and interzone. When any change in connectivity occurs inside a zone, a link-state pro-tocol propagates the change in link states, but it lim-its the propagation to within the zone lim-itself. For example, in Figure 4a, if link B,C breaks, the system informs only the Zone 8 hosts.
A host is called a gateway if it connects to one or more hosts in other zones. The existence of gateways defines the connectivity between two zones. For example, Figure 4b reflects the interzone connectivity in Figure 4a. When a change in the connectivity between two zones occurs, gateways broadcast the information from zone to zone throughout the net-work. Thus, a local change in link states causes global flooding only if it changes interzone connectivity. For example, in Figure 4a, a break in link A,B does not change the interzone connectivity. The protocol prop-agates the interzone routing information only if a break occurs in both links A,B and A,C.
A host uses information exchange to maintain inter-zone and intrainter-zone routing tables. To search for a
route to a destination host, a source host first queries its intrazone routing table. If an entry exists, the host will route data packets locally. Otherwise, the host broadcasts a location request packet to all other zones via gateways, querying the destination’s current zone. Once it discovers this zone, the host can send data packets first through interzone routing, then through intrazone routing.
Protocol comparison
Generally, a manet routing protocol must address three issues: route discovery, packet relay, and route maintenance. Depending on whether we use location information for each of these issues, we classify these routing protocols as non-location aware, partially location aware, or fully location aware. Table 1 com-pares existing protocols based on this classification.
LAR is location aware only in terms of route dis-covery. Gedir adopts a connectionless mode and thus does not try to discover and maintain routes, but it is location aware in forwarding data packets. Grid is location aware in all three aspects. The two-level pro-tocol is location aware in discovering and maintain-ing routes but differs from the other protocols because it adopts a proactive approach.
LOCATION-AWARE SERVICES
Potential location-awareness applications include the following:11
• Navigation and direction-giving. These applica-tions offer travelers directional guidance—a ser-vice especially valuable to the automobile industry.
1 2 3 4 5 6 7 8 9 1 2 3 4 5 6 7 8 B C A 9
Figure 4. The zone-based two-level routing protocol. The protocol uses a two-level hierarchy to manage manet network traffic by dividing the geographic area into (a) low-level intrazone connectivity and (b) high-low-level interzone connectivity.
Table 1. Comparison of location-aware routing protocols.
Scheme Route discovery Packet relay Route maintenance
DSR, AODV, No No No
ZRP
LAR Yes (on-demand) No No
Gedir Connectionless Yes Connectionless
Grid Yes (on-demand) Yes Yes
Two-level Yes (proactive) No Yes (proactive)
• Geographic messaging. This application sends a message to anyone within a specified area. For example, the system could send an emergency message to people in a train station, stadium, or shopping mall. Researchers have also developed an architecture for geocasting via the Internet. • Geographic advertising. Typically,
advertise-ments depend on location. For example, a par-ticular sale will interest only people within a certain distance of the merchant’s location. Thus, the sender only needs to transmit the advertise-ment—which can be regarded as a broadcast message—to hosts within a set distance. • Who-is-around service. This application
deter-mines who currently occupies a specific geo-graphic area.
• Neighbor-and-service discovery. For a mobile device or home appliance that contains a wireless communication protocol such as Bluetooth, find-ing out who its neighborfind-ing devices are and what services those neighbors provide is essential. • Source-position identification. Emergency and
rescue services have a vital need to know the cur-rent location of any host that sends an emergency message. For example, the US government recently mandated that providers of personal communication systems must, in the near future, add location-identification capability to their 911 services. Likewise, when a law enforcement agency tracks illegal activities, determining the current geographic position of the host that is sending the suspect’s messages is essential. Several approaches use manets to provide geo-graphic services.
Geocast
Geocast sends a message to all mobile hosts within a designated geographic area, called a geocast region.
This approach differs from traditional multicast in that the destination address is not a multicast IP. The first geocast protocol uses two approaches.6 One approach resembles unicast3in that it confines the propagation of geocast messages within a forwarding zone. The other approach looks at the distance from a host to the center of the geocast region. On receiv-ing a geocast message from Y, host X forwards the message only if X is closer to the center than Y. This approach significantly reduces traffic without sacri-ficing the delivery rate of geocast messages.
Geotora
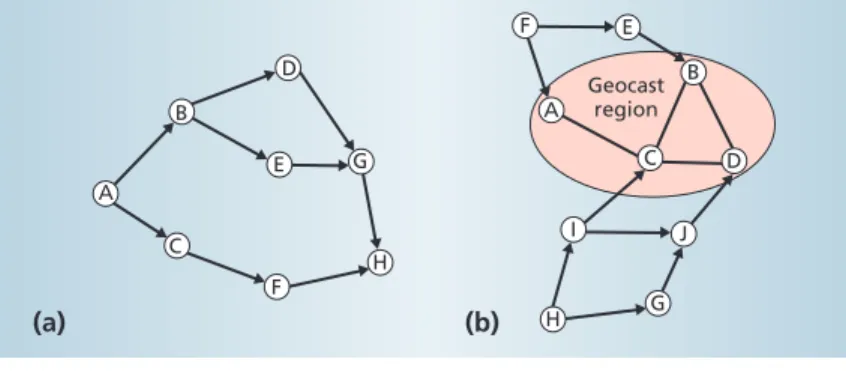
The Geotora protocol,7also used for geocasting, derives from the temporally ordered routing algorithm protocol.12 Designed for unicast, TORA has an intriguing multipath property. With respect to each destination, TORA maintains a directed acyclic graph with the destination as the graph’s sink. To maintain the DAG, the network associates height with each host. The manet directs links from a larger height to a smaller height, and the sink host always has the low-est height in the manet. To deliver a packet to the sink host, a host forwards the packet to any host with a lower height.
Figure 5a shows a DAG with H as the sink. Given its distinctive multipath property, TORA is well suited to highly dynamic manets. Geotora uses a slightly modified DAG. Any host within the geocast region has the same lowest height, so links between hosts in the geocast region should have no direction. Outside the geocast region, maintaining the DAG is similar to TORA, as Figure 5b shows.
When using this modified DAG, geocasting requires two phases. First, it performs an anycast from the source to any host in the geocast region. Once the geo-cast message reaches a host in the geogeo-cast region, flooding takes place to distribute the message to all hosts in the geocast region.
Geogrid
The Geogrid protocol,8a modification of the Grid protocol, does not try to establish a spanning tree or routing path prior to geocasting. Instead, the protocol adopts a connectionless mode.
Geogrid uses two methods for distributing geocast messages. Flooding-based geocasting allows any grid leader in the forwarding zone to rebroadcast the mes-sages. Ticket-based geocasting allows only ticket-hold-ing grid leaders to rebroadcast. Issuticket-hold-ing tickets avoids blind flooding.
There are several trade-offs between the Geogrid and Geotora approaches. Geogrid is preferable to the forwarding-zone approach because it prohibits non-leader hosts from rebroadcasting packets. Geogrid uses a connectionless mode, while Geotora uses a
con-Geocast region A C B F E G H J G H I F E D A B C D
Figure 5. Two directed acyclic graphs: (a) a DAG with H as the sink and (b) a modified DAG in Geotora with the pink zone as the geocast region. The manet directs links from a larger height to a smaller height, and the sink host always has the lowest height in the manet. To deliver a packet to the sink host, a host forwards the packet to any host with a lower height.
nection-oriented mode. Maintaining routes in Geotora can be costly if host mobility is high, but it is worthwhile if the system needs to send large amounts of data.
Location-aware tour-guide systems
As an alternative to providing tours led by staff, some museums and art galleries offer audio guides for tourists to use as they view the exhibits. Although they save staff resources, such audio guides lack multime-dia capability and cannot interact with tourists. Further, the tourists must know what room they cur-rently occupy so that they can listen to the correct pro-gram for that exhibit.
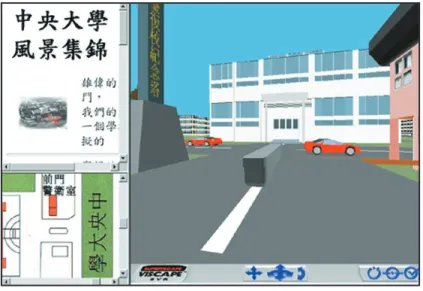
The National Central University has prototyped a location-aware and context-aware tour-guide system for its campus. The system consists of a GPS receiver connected to a laptop PC’s RS-232 port. The software part of the tour guide system, implemented in Java, consists of three components:
• 2D map. A blinking cursor on the guide’s 2D campus map shows the user’s current position. The cursor moves automatically as the user moves.
• 3D virtual world. Users can track their move-ment through a 3D virtual world implemove-mented in VRML. In addition, users can take a virtual tour, via mouse, to discover interesting sites and related information from their current position. • Web information. Because graphic interfaces
sometimes cannot provide the in-depth infor-mation that text can, we implemented an inter-face that displays Web pages through a browser. As the user moves, the guide can automatically display a Web page related to the user’s current position.
The guide system integrates these components as multiple frames in a unified interface that the user can view through a browser, as Figure 6 shows. With manet support, tourists can also interact with other tourists to share their experience online. The guide stores the Web pages locally on the notebook’s hard disk. Users with access to a mobile phone can retrieve remote information through the Internet. Experience gained building the tour-guide system may be directed toward new research into mapping from geographic locations to Web pages.
B
ecause wireless networks can operate in a 3D physical environment, exploiting mobile hosts’ location information is both natural and in-evitable. Emerging geographic services based on manets must confront several challenges, including how to increase positioning accuracy and how to establish aconnection from location information to the vast body of Web data, as in the tour-guide system. ✸
References
1. E.M. Royer and C-K. Toh, “A Review of Current Rout-ing Protocols for Ad Hoc Mobile Wireless Networks,”
IEEE Personal Comm., Apr. 1999, pp. 46-55.
2. M. Joa-Ng and I-T. Lu, “A Peer-to-Peer Zone-Based Two-Level Link-State Routing for Mobile Ad Hoc Net-works,” IEEE J. Selected Areas in Comm., vol. 17, no. 8, 1999, pp. 1415-1425.
3. Y-B. Ko and N.H. Vaidya, “Location-Aided Routing (LAR) in Mobile Ad Hoc Networks,” Proc. ACM/IEEE
Int’l Conf. Mobile Computing and Networking, IEEE
Press, Piscataway, N.J., 1998, pp. 66-75.
4. W-H. Liao, Y-C. Tseng, and J-P. Sheu, “GRID: A Fully Location-Aware Routing Protocol for Mobile Ad Hoc Networks”; http://citeseer.nj.nec.com/310846.html. 5. X. Lin and I. Stojmenovic, “Gedir: Loop-Free Location
Based Routing in Wireless Networks”; http://citeseer.nj. nec.com/cidcontext/4713431.
6. Y-B. Ko and N.H. Vaidya, “Geocasting in Mobile Ad Hoc Networks: Location-Based Multicast Algorithms,”
Proc. IEEE Workshop Mobile Computing Systems and Applications, IEEE Press, Piscataway, N.J., 1999, pp.
101-110.
7. Y-B. Ko and N.H. Vaidya, “Geotora: A Protocol for Geocasting in Mobile Ad Hoc Networks,” tech. report 00-010, Dept. of Computer Science, Texas A&M Univ., Mar. 2000; http://citeseer.nj.nec.com/context/1177604/ 328536.
8. W-H. Liao et al., “Geogrid: A Geocasting Protocol for Mobile Ad Hoc Networks Based on GRID,” J. Internet
Technology, vol. 1, no. 2, 2000, pp. 23-32.
Figure 6. Integrated interface of a location-aware tour-guide system. The system’s core components include a 2D map, 3D virtual world, and Web-page display applet.
9. G.D. Abowd et al., “Cyberguide: A Mobile Context-Aware Tour Guide,” J. Wireless Networks, vol. 17, no. 8, 1997, pp. 421-433.
10. S-Y. Ni et al., “The Broadcast Storm Problem in a Mobile Ad Hoc Network,” Proc. ACM/IEEE Int’l Conf. Mobile
Computing and Networking, IEEE Press, Piscataway,
N.J., 1999, pp. 151-162.
11. J.C. Navas and T. Imielinski, “Geographic Addressing and Routing,” Proc. ACM/IEEE Int’l Conf. Mobile
Computing and Networking, IEEE Press, Piscataway,
N.J., 1997, pp. 66-76.
12. V.D. Park and M.S. Corson, “A Highly Adaptive Dis-tributed Routing Algorithm for Mobile Wireless Net-works,” Proc. IEEE Infocom 1997, IEEE Press, Piscat-away, N.J., 1997, pp. 1405-1413.
Yu-Chee Tseng is a full professor in the Department of Computer Science and Information Engineering, National Chiao-Tung University, Taiwan. His re-search interests include wireless communication, net-work security, parallel and distributed computing, and computer architecture. Tseng received a PhD in com-puter and information science from Ohio State Uni-versity. He is a member of the IEEE Computer Society
and the ACM. Contact him at yctseng@csie.nctu.edu. tw.
Shih-Lin Wu is a PhD candidate in the Department of Computer Science and Information Engineering, National Central University, Taiwan. His research interests include mobile computing, wireless commu-nication, and parallel and distributed computing. Wu received a BS in computer science from Tamkang Uni-versity.
Wen-Hwa Liao is a PhD candidate in the Department of Computer Science and Information Engineering, National Central University, Taiwan. His research inter-ests include wireless network protocol design, mobile computing, and parallel and distributed computing. Liao received an MS in computer science and informa-tion engineering from Nainforma-tional Central University. Chih-Min Chao is a PhD candidate in the Depart-ment of Computer Science and Information Engi-neering, National Central University, Taiwan. His research interests are in the area of wireless commu-nication. Chao received an MS in computer science from National Tsing Hua University.