A Novel Scheduler for VBR traffic in IEEE 802.11
HCCA WLANs
Yaw-Wen Kuo
Department of Electrical Engineering National Chi Nun University Email:ywkuo@ncnu.edu.tw
Jin-Hsiu Tsai
Department of Electrical Engineering National Chi Nun University Email:s95323567@ncnu.edu.tw
Abstract―IEEE 802.11 standard provides a reference
design of a simple scheduler and admission control unit. The reference design is suitable for CBR traffic because a fixed TXOP is allocated to a connection during service. This paper proposes a novel scheduler for VBR traffic, where the polling list and TXOP values are dynamically updated to have multiplexing gain. Moreover, an effective admission method is also provided as well to guarantee the loss rate.
Index Terms―802.11e MAC, HCCA, QoS, scheduling.
I. INTRODUCTION
Nowadays, the wireless networks such as IEEE 802.11 WLANs [1] are deployed widely with ra-pidly increasing numbers of users all over the world. As real-time applications such as VoIP and Streaming Video are getting more common in daily life, quality of service (QoS) guarantee over wire-less networks is becoming an important issue.
IEEE 802.11 standard defines a coordination function which is called Hybrid Coordination Function (HCF) and is implemented at a QoS-aware AP (QAP). This function consists of the contention-based Enhanced Distributed Channel Access (EDCA) and the contention-free HCF Con-trolled Channel Access (HCCA). Because of the contention-free nature, HCCA can provide much better QoS guarantee than EDCA. HCCA requires a centralized QoS-aware coordinator, called Hybrid Coordinator (HC), which has a higher priority than normal QoS-aware stations (QSTAs) in gaining channel control. HC can gain control of the channel after sensing the medium idle for a PCF interframe space (PIFS) interval that is shorter than DCF in-terframe space (DIFS) adopted by QSTAs. After gaining control of the transmission medium, HC will poll QSTAs according to its polling list. In or-der to be included in HC’s polling list, each QSTA needs to make a separate QoS service reservation, which is accomplished by sending the Add Traffic
Stream (ADDTS) frame to HC. In this frame, QSTAs can give their traffic characteristics a de-tailed description in the Traffic Specification (TSPEC) field. Based on the traffic characteristics specified in TSPEC and the QoS requirements, HC calculates the scheduled service interval (SI) and transmission opportunity (TXOP) duration for each admitted flow. TXOP is a time duration that a QSTA can use each time when it was polled. Upon receiving a polling frame, the polled QSTA either responds with QoS-Data if it has packet to send or a QoS-Null frame otherwise. When the TXOP du-ration of a QSTA ends, HC gains the control of channel again and either sends a QoS poll to the next station on its polling list or releases the me-dium for EDCA if there is no more QSTA to be polled.
IEEE 802.11 provides a reference design of HCCA, where each connection is allocated a fixed TXOP and a simple admission control is derived. The reference design is based on average rate of arrival traffic, and hence is only effective for CBR applications. Some scheduling methods [3]-[5] were designed to handle VBR traffic, but no cor-responding admission control method was provided. The system efficiency or performances are im-proved, but QoS can not be guaranteed at high load without admission control. The authors in [6] pro-posed an admission control method according to the effective TXOP durations calculated derived the distribution of arrival traffic. Later on, the authors in [7] used Gaussian approximation for traffic dis-tribution to reduce the computation complexity. Because the above two schemes all allocate a fixed TXOP duration for each connection, there is no multiplexing gain. The authors in [8] designed a HCCA MAC with multiplexing gain, but the inves-tigated system only used simple FIFO service dis-cipline.
This work was supported in part by the National Science Council, Taiwan, under grant NSC 96 -2221-E-260-005.
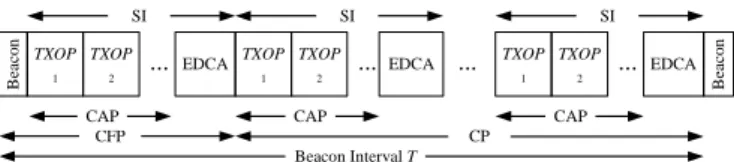
Figure 1: Relation between HCCA and EDCA
In this paper, we propose a scheduler for HCCA MAC, where the flows are served in a dynamic or-der and the allocated TXOP duration is calculated based on queue status. The remainder of this paper is organized as follows. In Section II, we describe some background information about HCCA. In Section III, we introduce the design of our HCCA MAC including the scheduler, the calculation of TXOP durations, and an admission method. Section IV contains some simulation results to demonstrate the advantages of our design. Finally, we draw conclusion in Section V.
II. BACKGROUND INFORMATION
In a 802.11 QoS MAC, the HC may start the Controlled Access Phase (CAP) at the beginning of every SI and allocate TXOP to each flow as shown in figure 1. SI is a sub-multiple of the beacon in-terval T. Let ρi, Li, Mi, and Ridenote,
respec-tively, the Mean Data Rate, Nominal MSDU Size, Maximum Allowable Size of MSDU, and Mini-mum Physical Transmission Rate of flow i. The reference scheduler in the IEEE 802.11 [1] calcu-lates the TXOPi for the new flow i by
O denotes the overhead including CF-Poll frame,
MAC header, CRC, ACK frames, and SIFS. It will accept the new flow if the following equation can be met.
where T and Tcp denote respectively the beacon
in-terval and the time used for EDCA. If flow i is ad-mitted, its TXOP duration is fixed at TXOPi all the
time.
The reference scheduler uses equation (1) to
Figure 2: Block diagram of the proposed scheduler.
estimate the average number of traffic in one SI based on the mean data rate ρi. Because the burst
nature is not considered in the reference scheduler, serious traffic loss will occur when the burst is large.
The investigated system can modeled as a buffer-less queue system, where the packets arriv-ing in the previous SI are dropped if they cannot be served in the current SI. The authors in [6] used exact arrival process to compute the required TXOP duration to guarantee the probability of packet loss. The major issue of such implementa-tion is that we need to know the exact arrival process which unfortunately is hard to model. In [7], the Gaussian approximation for arrival traffic of each flow is proposed and proved to be suffi-ciently valid by simulation. The computation com-plex is significantly reduced, but it is sometimes too conservative from our simulation result. The two approaches are both per-flow basis and there is no multiplexing gain.
III. PROPOSED SCHEDULER AND ADMISSION CONTROL
A. Proposed Scheduler
The block diagram of our design is shown in fig-ure 2. The queue manager maintains a dedicated queue for each flow. At the end of each SI, the queue manager will count the undelivered traffic for each flow such that the system can calculate the current loss, denoted by pi, at nth SI by equation
(3).
where dropi is the amount of traffic dropped.
Moreover, at the beginning of each SI, the system
TXOP max , , where . (1) i i i i i i i i N L M O O R R SI N L ρ × = + + × = 1 , (2) i j CP j TXOP T T SI T = − ≤
∑
TXOP 1 B ea co n TXOP 2 ... EDCA TXOP 1 TXOP 2 ... EDCA TXOP 1 TXOP 2 ... EDCA ... B ea co n Beacon Interval T CFP CP SI SI SICAP CAP CAP
1 = , (3) n j j i i drop p nSI
ρ
= ×∑
will allocate TXOP duration to flows according to the polling list until all flows are served or the CAP ends. The maximum duration of CAP will be de-termined by the admission control.
Our design goal is to keep the average traffic loss of each connection within a given threshold, de-noted by PL. Since it is required to maintain
fair-ness between flows, our scheduler will update the polling list according to the measured loss rate of each flow. A flow with large loss will have high-er priority. Afthigh-er the polling list is arranged, the TXOP durations are calculated flow by flow as follows.
To guarantee the average rate, we reserved initial value TXOPiini for each flow, where TXOPiini is calculated by equation (1). Because the arrival traf-fic is dynamic, sometimes TXOPiini is larger than the actual demand. Let Ti be the time to serve the
entire backlog for flow i at the beginning of current SI. We can calculate the remaining time by equa-tion (4).
The scheduler serves the highest priority flow with TXOP duration equal to its initial value plus the remaining time. If all data is transmitted and there is some remaining time left, the scheduler will add the remaining time to the TXOP of the flow with second highest priority. Similar process continues until all flows are served. The detail procedure is shown below.
Pseudo code of scheduler
1. Calculate TXOPiini by equation (1). 2. Calculate TDremin by equation (4).
3. Let i be the highest priority flow in the polling
list.
4. The TXOP duration is calculated by
{
}
TXOP =mini Ti , (TXOP + iini TDremain) . 5. Transmit data for flow i.
6. Update TDremain = TXOP +iini TDremain−Si, where Si is the time used to serve the traffic for
flow i.
7. Remove flow i from the polling list.
8. If the polling list is nonempty, go to step 2; otherwise, stop HCCA and perform EDCA.
B. Admission Control
Admission control is indispensable to networks. In addition to guarantee QoS for HCCA users, it is also important to let EDCA users share the band-width well. This paper proposes an effective ad-mission control method for the above scheduler to complete the MAC design. From the simulation result, we can see that the resulting loss rate is close to the target. It means that we can allocate the resource well and EDCA users can share more bandwidth.
Because our scheduler serves flows according to current loss rate, the loss rates for all flows will be even after a long run. The key to admission control is to determine the duration of CAP. The amount of traffic for flow i in one SI can be modeled by a random variable Xi. According to Lyapunov's
cen-tral limit theorem, the summation of independent random variables will converge to a Gaussian ran-dom variable. Therefore, we model the aggregated traffic in one SI by Y=N( , ).µ σ Let µi and σi be
re-spectively the mean and standard variation of Xi,
and we have
Similar to the analysis in [7], let c=µ+α*σ be the amount of resource we reserved. We can calculate the loss rate by
To simply the computation, this paper approx-imates the loss by p Q(c-µ) Q( )α
σ
≈ = . For a
given PL, we can search the optimal value for α by
looking up the table of Q function. After c is de-termined, the number of packets can be estimated by N =c L/ where L is the Nominal MSDU Size. Finally, the required CAP is determined by
(
)
= CAP- TXOP (TXOP ) .
(4) ini ini remain i i i TD
∑
+∑
− T + 2 , . (5) i i µ µ σ σ = =∑
∑
2 2 2 -( - ) 2 -2 ( - ) ( ) (( - ) ) (6) ( ) - ( ) - ( ) , 2 1 where ( ) . 2 Y c y x Y c f y dy E Y c p E Y c c c Q e Q Q e dx µ σ αµ
µ
σ
µ
σ
µ π
µ
σ
α
π
∞ + ∞ = = = + =∫
∫
where n and Tpoll are the number of flows and the
transmission time of polling frame. The admission test is simply checking if equation (8) holds.
It is worthy to point out that we assume equal PHY rate here. For the case with different PHY rate, we need to normalize the parameters in equation (5), and the rest procedure is the same.
TABLE 1. INPUT PARAMETERS AND VALUES
Parameter Value
PL 0.1
PHY rate 216Mbps
Service Interval (SI) 100 ms
TCP/T 0.5 Slot time 9 µs SIFS 16 µs DIFS 34 µs Tpoll 9.33 µs CWmin 15 Per-packet overhead 35.93 µs
IV. PERFORMANCE EVALUATION
In this section, we evaluate the proposed schedu-ler and admission control method. We assume that there are some QSTAs and each QSTA has one downlink flow. Each real-time flow is modeled as a Poisson process and the packet length varies ac-cording to the exponential distribution with mean packet size equal to the nominal MSDU size. Some parameters are listed in Table 1. We also run the same simulation for the reference scheduler and the method in [7].
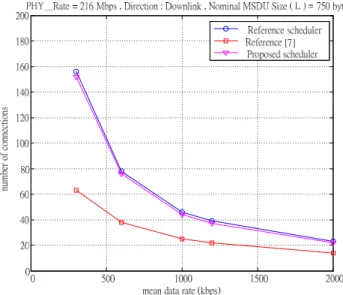
In the first test, for a given traffic parameters, we find out the maximum number of admitted flows as shown in Figure 3 and 4 for different L. We can see that the proposed scheduler performs very well and the results are very close to that of the reference scheduler. It also demonstrates the effect of
Figure 3: The number of admitted flow for L=750 bytes.
Figure 4: The number of admitted flow for L=1000 bytes.
multiplexing gain that we can even double the sys-tem capacity for low rate traffic. If we compare the results for different L, we can see that the system can admit more flows at large L because the proto-col overhead is smaller. This problem can be elim-inated if the frame aggregation feature in IEEE 802.11n [9] is used.
Next, we check how well the QoS can be guar-anteed. The results are plotted in figure 5 and 6. As expected, the loss rate of the reference scheduler is worst and far away from the required PL. The loss
rate of our scheduler is higher than that of reference [7]; nevertheless, the requirement is still guaranteed. From the point of fair resource management, we think our scheduler is better
CAP= + * ( SIFS ), (7)
PHY Rate poll
c n O+ +T CAP . (8) CP T T SI T − ≤
Figure 5: The loss rate for L=750 bytes.
Figure 6: The loss rate for L=750 bytes.
because the resulting loss rate is close to PL. It
means that we just allocate enough resource to HCCA and the EDCA users can get more band-width.
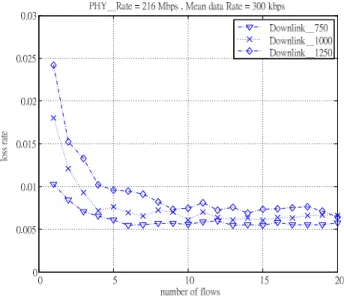
In our admission control, we used Lyapunov's central limit theorem that is effective for summa-tion of numerous random variables. In our final test, we want to verify whether our method is practical. We fixed the mean data rate and vary the number of flows. Figure 7 shows that the approximation error for low data rate is high if there are few flows in system. If the number of flows is large than 5, the target can be met. Figure 8 shows the result for high data rate and the loss rate converges more quickly. For high throughput WLAN networks, it will serve many users, and our
Figure 7: The loss rate for 300 kbps data rate.
Figure 8: The loss rate for 2 Mbps data rate.
scheduler is a good and reasonable solution. To solve the approximation error issue, we can reserve a minimum duration for CAP such that the HCCA can have enough resource for the case with few flows.
V. CONCLUSION
This paper proposed a scheduler with admission control for HCCA MAC. Simulation results have shown that the proposed scheduler can significantly increase the number of admitted flows and use the resource efficiently. The design in uplink part is different from that of downlink because the AP has no information of QSTA’s queue status at the be-ginning of SI. Some schemes have information
ex-lo ss r at e 0 500 1000 1500 2000 10-3 10-2 10-1
mean data rate (kbps)
lo
ss
r
at
e
PHY__Rate = 216 Mbps , Direction : Downlink , Nominal MSDU Size ( L ) = 750 bytes
Reference scheduler Reference [7] Proposed scheduler
change mechanism and predict the queue length. We plan to develop the uplink scheduler in the sim-ilar way proposed in this paper. The performance is under investigation.
REFERENCE
[1]IEEE Standard for Information technolo-gy-Telecommunications and information ex-change between systems-Local and metropoli-tan area networks-Specific requirements – “Part 11: Wireless LAN Medium Access Con-trol (MAC) and Physical Layer (PHY) Speci-fications,” 2007.
[2]Skyrianoglou, D.; Passas, N.; Salkintzis, “ARROW: An Efficient Traffic Scheduling Algorithm for IEEE 802.11e HCCA,” IEEE Trans. Wireless Comm., vol. 5, no. 2, pp. 3558 – 3567, Dec. 2006.
[3]A.Grilo, M.Macedo, and M.Nunes,”A sche-duling Algorithm for Qos Support in IEEE 802.11e Networks,” IEEE Wireless Communi-cation Magazine,vol.10 no3, pp-36-43, June 2003.
[4]Bin Muhamad Noh, Z.A.; Takahiro Suzuki; Shuji Tasaka”Packet scheduling for user-level QoS guarantee in audio-video transmission by IEEE 802.11e HCCA,” in Proc. IEEE TEN-CON 2007.
[5]Kyung Mook Lim; Kang Yong Lee; Kyung
Soo Kim; Seong-Soon Joo, “Traffic Aware HCCA Scheduling for the IEEE 802.11e Wire-less LAN,” in Proc. IEEE ICME 2007, pp.:963 - 966, July 2007.
[6]W.F.Fanetal,.” Admission Control for Variable Bit Rate Traffic in IEEE 802.11e WLANs,” in Proc. IEEE LANMAN 2004, pp.61-66.
[7]Y.W. Huang, T.H. LEE and J.R.Hsieh, ”Gaus-sian Approximation Based Admission Control for Variable Bit Rate Traffic in IEEE 802.11e WLANs,” in Proc. IEEE WCNC 2007.
[8]D. Gao, J. Cai, and C. W. Chen, “Admission Control Based on Rate-Variance Envelop for VBR Traffic Over IEEE 802.11e HCCA WLANs,” IEEE Trans. Vehicular Technology, vol. 57, no. 3, May 2008.
[9]IEEE 802.11-04/889, “TGnSync Proposal
Technical Specification,”