380 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 41, NO. 4, NOVEMBER 1992
Throughput Performance of
a
Class
of
Continuous
ARQ Strategies for Burst-Error Channels
Tsern-Huei Lee, Member, IEEEAbstract-This paper studies the throughput performance of a class of continuous automatic repeat request (ARQ) strategies for burst-error channels modeled by two-state Markov chains. The operation of the investigated ARQ strategies can be described as follows. A chunk of m or fewer copies of each data block is transmitted contiguously to the receiver. Whenever a repeat request is received, the transmitter goes back to and retransmits that data block and all successive ones. However, the maximal number of copies transmitted is equal to 71 in each retransmission. It is proved that the optimal repetition sequence which maximizes the throughput efficiency among a more general set of ARQ schemes falls in the class of investigated strategies. Numerical results reveal that throughput efficiency is very likely to be maximized at ni = n .
I. INTRODUCTION
UTOMATIC repeat request (ARQ) is a common tech-
A
nique adopted to handle transmission errors which occur inevitably because of the existence of channel noise. Many researchers have devoted much effort to the design and anal- ysis of various ARQ strategies (see, for example [1]-[5]). However, most of previous results regarding the performance of ARQ strategies were based on the independent error model. This model becomes unrealistic when transmission errors occur in bursts. Instead, Markov models [8], [9] are usually used to describe the behavior of such burst-error channels.It is the purpose of this paper to analyze the throughput efficiency of a class of continuous ARQ strategies for burst- error channels modeled by two-state Markov chains. We assume all the data blocks are of fixed length, and time is divided into slots so that the duration of each slot is equal to the transmission time of a data block. The round-trip delay
r , which is defined as the time interval between the end of a
transmission and the receipt of its response, is assumed to be fixed and is equal to an integral number of slots. For simplicity, the feedback channel is assumed to be noiseless.
The Markov channel model studied here consists of one quiet state and one noisy state. In each slot, the channel is either in the quiet state or the noisy state. The transmission is a success (failure) with probability one if the channel is in the quiet (noisy) state. Let X i denote the channel state in
the ith slot so that Xi = 0 or 1 means the channel is in the quiet state or the noisy state, respectively. Then the channel model can be described as Pr[X;+1 = OlXi = 01 = p and
Manuscript received June 11, 1991; revised October 31, 1991. The author is with the Department of Communication Engineering and Center for Telecommunications Research, National Chiao Tung University, Hsinchu, Taiwan 30050, Republic of China.
IEEE Log Number 9200880.
Pr[X;+I = 1 ( X i = 11 = q . The same model was studied in [9] to evaluate the throughput performance of the classic go- back-N (GBN) ARQ scheme. It was found that the classic GBN ARQ scheme is more efficient for a Markov system than a system under the independent error model if and only if p
+
q 2 1. Similar work was done by Towsley [8].The operation of the investigated ARQ strategies is de- scribed in Section 11. Analysis of the limiting throughput efficiency of the investigated ARQ strategies is presented in Section 111. Illustrative examples are studied and the results are discussed in Section IV. Finally, some conclusions are drawn in Section V.
11. INVESTIGATED ARQ STRATEGIES The operation of the investigated ARQ strategies can be described as follows. A chunk of m ( m
2
1) of fewer copies of each data block are transmitted contiguously to the receiver. An error detection procedure is performed at the receiver on each received copy. A positive (ACK) or a negative (NAK) acknowledgment is sent to the transmitter according to whether the copy is received successfully or erroneously. The data block is considered to be successfully delivered as long as at least one of the copies is correctly received. If all the mcopies of a data block are negatively acknowledged, then, just as in the classic GBN ARQ strategy, the transmitter goes back to and retransmits that data block and all successive ones. However, the maximal number of copies transmitted is equal to n in each retransmission. It is noted that successive data blocks are considered as new ones, and hence at most m
copies are transmitted after retransmission of the negatively acknowledged data block. In general, n could be different
from m.
Obviously, if m
>
r+
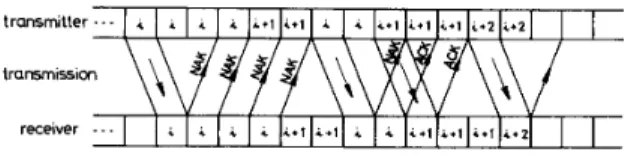
1, then an ACK for a data block may arrive at the transmitter before it exhausts all the m copies. Whenever this occurs, the transmitter will start transmitting the next data block rather than continuing with the transmission of the remaining copies. Therefore, the phrase “or fewer” is used in the description of the operation of the strategies. Fig. 1 illustrates an example for m = 4, n = 2, and T = 2. A similar situation may occur during retransmissions if n>
r+
1.We now explain why we investigate the class of ARQ strategies with the same maximal number of copies in each retransmission. Consider the more general set of continuous ARQ strategies studied in [5]. A chunk of mo or fewer copies
is transmitted contiguously to the receiver for each data block. If a repeat request is received, then at most m, copies are trans- mitted for the ith retransmission. Let f(mo, m1, m2, m3;
.
.)LEE: ARQ STRATEGIES FOR UST-ERROR CHANNELS 381
Fig. 1. An example of transmission for in = 4, R = 2, and 1' = 2. denote the average number of slots spent to successfully deliver a data block. Consider the transmission of a particular data block, and let z denote the probability of failure for the first copy of the data block. It can be shown that
f ( m o , m l , m 2 , m 3 , . " ) = d(m0;z)
+
zqmo-'' [r
+
h ( m l i m 2 , m3r ' ' ')] (l)where (2) is true (shown at the bottom of the page), and h(m1
,
m2, m3,. .
.) represents the average number ofslots spent in retransmissions. It is not hard to see that
h( ml
,
m2, m3, . .
.) can be expressed ash ( m l , m2, m3,. ' .) = d(ml; y) +yqm'-l [ T + h(m2, m3, . ' ')] (3)
where y denotes the probability of failure for the first copy in each retransmission. Notice that this probability is the same for each retransmission under the given Markov channel model. Let (m;, mT, ml;, m;, .
.
.) denote the optimal repetition se- quence which minimizes f ( m 0 , m l , m2, m3,. . .), i.e.,f(mG,mTimaim:,'.')
5
f ( m 0 i m l , m 2 , m 3 i " . )for all choices of (mo, ml
,
m2,
m3, . .
.).In particular, we have f ( m 6 , m;, ml;, m;, .
.
.)5
f ( m 6 , m l , m ~ , m s , . . . ) which implies h(m;,mE,m$,...)5
h(m1, mz,m3,...) forallchoicesof (ml,mZ,m3,...).
I f m o =m6and ml = m;, then, by ( 2 ) and (3), we get h(ml;, m j , . . .)
5
h(m2, m3,.
.
-) for all choices of (77x2, m3,..
.). Consequently,one can select m; = m; = m$ =
. .
. to minimize f ( m o , ml, m2, m3,..
.). In other words, the optimal repetition sequence that maximizes the throughput efficiency among the more general set of strategies falls in the class of strategies we investigate here.111. THROUGHPUT EFFICIENCY
L e t T =
[
-"1
denote the transition matrix of the channel state. It can be shown [12] that the k-step transition matrix is given by1.
+ 2 - ( P + q )[
q - 1 1 - q ( p + q - q k 1 - p p - 1 stad of cyclel+;pl
tmnmission 01 00 11 01 00 111 10 01 101~00 01 10 00 1 1 00 11 010.-last 'copy of retransmission Fig. 2. A typical transmission sequence for n7 = 2 , n = 3, and T = 4.
For the remainder of this paper, we will use t f j ( z , j = 0 , l ) to denote the ( i , j ) t h entry of Tk.
Notice that, under the investigated model, the channel state variable X i can also be used as the outcome of the ith transmission so that X i = 0 or 1 means the transmission is a success or a failure, respectively. As a result, { X i } z l
represents the transmission sequence. Let us now consider a particular pair of ( m , 71). The transmission sequence can be
divided into cycles so that each cycle starts with m consecutive 1 's, i.e., an unsuccessful transmission, of the first outstanding data block (FODB). A data block becomes the FODB if at the time of its transmission, all data blocks transmitted before it will never be retransmitted. Fig. 2 shows a typical transmission sequence from m = 2, n = 3, and r = 4. For clarity, spaces
are inserted in Fig. 2. The limiting throughput efficiency of the investigated strategy, denoted by ~ ( m , n ) , is defined as
where Uk(m,n) denotes the average number of data blocks successfully delivered in slots 1 -IC. By regenerative theorems [12], ~ ( m , n ) can be computed by ~ ( m , n ) = M ( m , n ) / L ( m , n ) , where L ( m , n) and M ( m , n ) represent,
respectively, the average length of a cycle and the average number of data blocks successfully transmitted in a cycle.
Now consider a particular cycle. For convenience, we will use X i to denote the outcome of the transmission in the ith slot of the cycle. Furthermore, let X R denote the outcome of the
last copy of retransmission (in Fig. 2, R = 16 and X R = 1). To evaluate ~ ( m , n ) , we need to define the following variables.
the average length of a cycle minus
m
+
r conditioning on Xm+r = 0 or 1, respectively;the average length in a cycle con- tributed by data blocks other than the retransmitted one conditioning on X R = 0 or 1, respectively; the average number of data blocks successfully transmitted in a cycle conditioning on Xm+r = 0 or 1, respectively;
the average number of data blocks successfully delivered in a cycle, excluding the retransmitted one, conditioning on X R = 0 or 1, respectively. 7nO
5
T+
1 mo-r-2 , (1 - z ) ( l+
r )+
z ( 1 - q ) qyr+
2+
2 )+
moZqmo-r-l,
m o > r + l i=O d(m0;z) =382 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 41, NO. 4, NOVEMBER 1992
1
n - 2
(1 - q ) t & l
+
q ( l - '1) q i t t i 2 - 2 L,n(m)i = n
It is not hard to see that L ( m , n ) and M ( m , n ) can be
evaluated by
Moreover, M s ( m , n ) and M f ( m , n ) are given by
+
n+
qnrwhere
M s ( m , n ) = 1
+
a S M s n ( m )+
(1 - a s ) M f n ( 7 n ) (6)Mf(m,
.) = 1+
bsM,n(m)+
(1 - b,)Mfn(m). (7)- W m , n ) , L f ( m , n ) , M s n ( m ) , M f n ( m ) , a,, and b,. These
values have to be computed using different equations accord-
U 1 1 = 1 - (1 - p)qn-'tlo,
a12 = -(1 - p ) q " - l t f ,
a21 = -qnt;o,
a22 = 1 - qnt;,.
(12) Therefore, the remaining work is to compute the values of and
(13) ing to the relationship among m, n, and T . For example,
consider the case when m
5
T+
1 and n5
T+
1. For this case, all the m copies in each transmission (or n copies in eachretransmission) have to be sent before the transmitter receives any response. Therefore, a recursive formula for L s ( m , n )
can be obtained as
As for the C q " i o n of L s , ( ~ ) and Lfn(m), two recursive expressions can be similarly derived and the results after simplifications are
b l l L s n ( m )
+
b l n L f n ( m ) = m[1 - (1 - p ) s " - l ] b21L,n(VL)+
b 2 2 L f n ( m ) = 4 1 - (14) (15) and L s ( m , n ) = p [ n+
t;&n(m)+
t ; ; l L f n ( m ) ]+ . . .
and b2lMsr1(Vb)+
b22Mfn(VL) = 1 - qm (23)where a l l , a12, a21, a22 are given in (12) and (13) and b l l ,
b12, b21, bZ2 are given in (16) and (17).
(10)
1
[
i = O n-3+
pt;;;l+
(1 - p ) ( l - q )+
n+
(1 - p ) q n - l r qit;,2-zLfn(m)
LEE: ARQ STRATEGIES FOR UST-ERROR CHANNELS 383 TABLE I
EQUATION REFERENCES FOR DIFFERENT CASES
in and n
EqCations m < r + l 7J/ > T f 1
Results for the other cases are presented in Table I. The equations used in Table I are listed below.
n-r-2
+
,('+
1)+
(1 - ,)(I - 4 ) 4%-+
2 + 2 ) i=O r-1+
n ( 1 - p ) q n - r - l ( l - 4)CrlZ i=O+
(1 - ,)sn-l(n+
r ) n-r-2+
(1 - q ) ( r+
1)+
4 ( 1 - 4 )+
nq"-'(l - 4 ) qi+
q n ( n+
') (25) 4%+
2+
4
i=O r-1 i=O qi(r+
2+
2 )+
m ( 1 - p)qm-'-l(1 - 4 ) i=O i=O (26) i=O r-1 i=O+
(1 - ~ ) f - ' - ~ ( l - 4 ) qit;ti (28) i=l n-r-2 a21as+
a22bs = [(l - 4 )+
4(1 - 4 )oil
G oi=O
r
In the above equations,
bil,
b',,,bil,
andbi2
are given by m-r-2 _I i=l m-r-2 7 V - 1 . - - (1 - p)q"-'-2( 1 - 4 )E
qit;;,Z (33) i = l384 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 41, NO. 4, NOVEMBER 1992 0 . 4 - c
$
0.3- .- .I -r r m-7-2 \,'.
\. \.P=O.9 \'.
i = ls
.$
0.2-2
7
0.1 2 .- c c c L L I - -0 - and-
r m-r-2 bh2 = 1 -L
(1 - 4 ) + q ( 1 - 4 ) qt t;;l i=O'1
r-1 (34) (35)One can easily verify that, for the classic GBN ARQ scheme, we have
the same as [9, Eq. (2.10)]. Futhermore, when p
+
q = 1, which corresponds to the independent error model, we get, after some computations,1 - qn
m(1 - q n )
+
( n+
r)qmTl(m,n) =
which can also be obtained using the computation algorithm presented in [ 5 ] .
It should be pointed out that the above derivations can not be
applied to compute the throughput efficiency for cases when
m = CO or n = CO. The reason is that when m = CO or
n = CO, we will get L ( m , n ) = M ( m , n ) = m. The author
derived in
[lo]
the recursive formulas and the resulting set of equations for these cases.IV. NUMERICAL RESULTS
The performance of the investigated ARQ schemes depends on the round-trip delay T and the values of the parameters
m,n,p, and q. The values of p and q are determined by the transmission channel. The classic GBN scheme may have the best throughput performance among the investigated class of ARQ schemes. This is usually the case for small round-trip delays andlor quiet channels, i.e., channels having large p and small q . However, the performance of the classic GBN scheme could be far worse than that of the optimal investigated scheme when round-trip delay is large andlor the channel is noisy. In other words, a significantly better performance than the classic GBN scheme offers can be achieved if one select appropriately the values of m and n. A n interesting result of our experiments is that the throughput efficiency is maximized at m = n. Since the optimal values of m and n are identical in our examples,
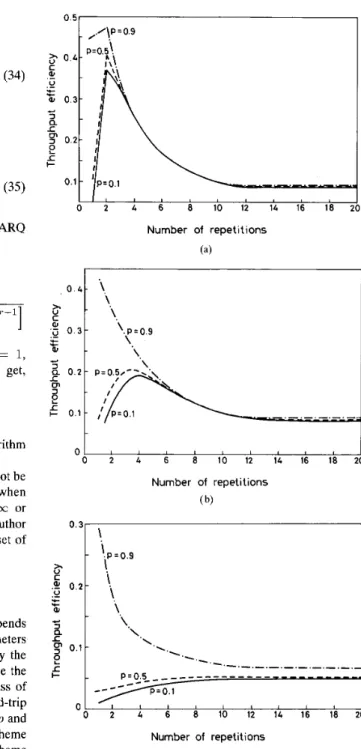
we will restrict our study in such strategies for simplicity. Figs. 3(a)-(c) illustrate the throughput efficiency versus number of repetitions m (and n ) for T = 10 under dif- ferent channel conditions. The case m = 1 corresponds to the classic GBN scheme. One can see from these figures
0.5 ,./\p=0.9 2 0.4- C U .- - .- * r 01 0.3- 3 a -f c
!?
0.2-e
1 -I- 0.1 - I , 0 2 4 6 8 10 12 14 16 18 i Number of repetitions (a) 0 I 1 I 1 I 0 2 4 6 8 10 12 14 16 18 20 Number of repetitions ( b) '.P.0.9 1. \. \. I I I I I 1 1 2 4 6 8 10 12 14 16 18 20 Number of repetitions (c)Fig. 3. Throughput efficiency versus number of repetitions for r = 10.
(a) q = 0.1. (b) q = 0.5. (c) q = 0.9.
that the throughput performance of the classic GBN scheme can be significantly improved for quite noisy channels (see the curves for p = 0.1) if the number of repetitions is appropriately selected. Moreover, the throughput efficiency quickly converges to a constant, namely ~ ( c o , CO), as m
increases. In Fig. 3(c), the curve for p = 0.1 can be shown [5] is monotonic increasing with ~ ( c o , CO) = 0.05. According
LEE: ARQ STRATEGIES FOR UST-ERROR CHANNELS 385 >.
2
‘3 0 . 4 - .- .I -+ c-2
P
L 0=
0.2- L \. P =0.9t
‘p=o.l 0 1 I I 0 2 4 6 8 10 12 14 16 Number of repetitions (a) \P = 0.9 .- \. U 0 . 4 .- .I -*-f
i
i.t
/p=o.l 0 1 I I II
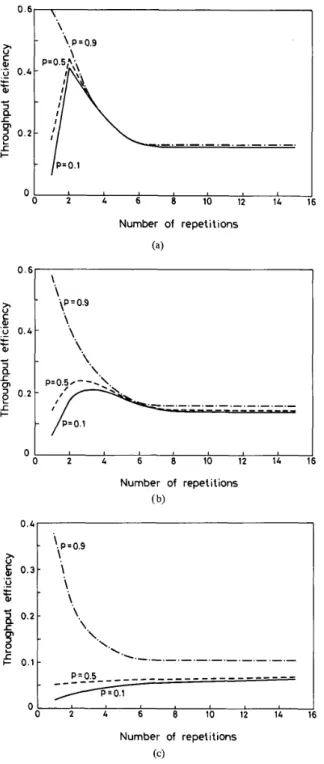
0 2 4 6 8 10 12 14 16 Number of repetitions ( b) I 1 0 2 4 6 8 10 12 14 16 Number of repetitions (c)Fig. 4. Throughput efficiency versus number of repetitions for T = 5. (a) q = 0.1. (b) q = 0.5. (c) q = 0.9.
to our numerical results, the curve for p = 0.5 is also monotonic increasing with ~ ( C O , m) 0.0517. In fact, from the curves we plotted in Figs. 3(a)-(c), one can see that
V(m, m ) seems to be a monotonic function of m when m
2
T+
1. However, it is difficult to prove this formallyFig. 5. Comparison of throughput efficiencies of various ARQ schemes for
T = 10 and p = 0.08.
for T = 5 are very similar to those for T = 10 and are presented in Figs. 4(a)-(c).
Fig. 5 illustrates the comparison among the selective-repeat, the classic GBN ( m = n = l ) , The Sastry’s ( m = 1, n = m) [ 2 ] , the Moeneclaey-Bruneel’s ( m = n = CO) [4], and the optimal one selected from the investigated schemes for T = 10 and p = 0.8. The limiting throughput efficiency for the selective-repeat ARQ strategy is equal to (1 - q ) / ( 2 - p - 4 ) . One can see that the optimal investigated scheme can provide a considerable improvement over other related schemes.
V. CONCLUSION
We have analyzed in this paper the limiting throughput efficiency of a class of continuous ARQ strategies with re- peated transmissions for burst-error channels modeled by two-state Markov chains. It was shown that the through- put efficiency can be significantly improved by transmitting multiple copies contiguously to the receiver, especially un- der high error rate conditions. Numerical results show that the throughput efficiency is very likely to be maximized at m = n, a confirmation of the results for the indepen-
dent error model [ 5 ] . This is important because a strategy with m
#
n requires more logic than the one with m = n.REFERENCES
[ l ] D. Towsley, “The stutter go-back-N ARQ protocol,” IEEE Trans.
Commun., vol. COM-27, pp. 869-875, June 1979.
[2] A. R. K. Sastry “Improving automatic repeat-request (ARQ) perfor- mance on satellite channels under high error rate conditions,” IEEE Trans. Commun., vol. COM-23, pp. 436-439, Apr. 1975.
[3] J. M. Morris, “On another go-back-N ARQ technique for high error rate conditions,” IEEE Trans. Commun., vol. COM-26, pp. 187- 189, Jan. 1978.
[4] M. Moeneclaey and H. Bruneel, “Efficient ARQ scheme for high error rate channels,” Electron. Lett., vol. 20, pp. 986-987, Nov. 1984. [5] H. Bruneel and M. Moeneclaey. “On the throughput performance of
some continuous ARQ strategies with repeated transmissions,” IEEE Trans. Commun., vol. COM-34, pp. 244-249, Mar. 1986.
161 E. N. Gilbert, “Caoacitv of a burst-noise channel.” Bell Svst. Tech. J..
L 1
386 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 41, NO. 4, NOVEMBER 1992 [7] L. N. Kana1 and A. R K. Sastry, “Models for channels with memory and
their applications to error control,” Proc IEEE, vol. 66, pp. 724-744, July 1978
[8] D Towsley, “A statistical analysis of ARQ protocols operating in a nonindependent error environment,” IEEE Trans. Commun., vol. COM- 29, pp. 971-981, July 1981.
[9] C. Leung, Y. Kikumoto, and S.A. Sorenson, “The throughput effi- ciency of the go-back-N ARQ scheme under Markov and related error structures,” IEEE Trans. Commun., vol. 36, pp. 231-234, Feb. 1988. [ lo ] T. H. Lee, “Throughput performance of a set of continuous ARQ strate-
gies for Markov channels,” 1. Chinese Inst Eng., vol. 13, pp. 655-663, 1990.
[I11 -, “Throughput efficiency of Some ARQ strategies under Markov error models,” Electron. Lett., vol. 25, pp. 1347-1349, 1989. [12] D. R. c o x and H. D. Miller, The Theory of Stochastic Processes. Lon-
don, U.K.. Chapman and Hall, 1965.
Tsern-Huei Lee (S’86-M’87) received the B.S. degree from National Taiwan University, Taiwan, Republic of China, in 1981, the M.S. degree from the University of California, Santa Barbara, in 1984, and the Ph D. degree from the University of South- ern California, Los Angeles, in 1987, all in electrical engineering
Since 1987, he has been a member of the fac- ulty of National Chiao Tung University, Hsinchu, Taiwan, Republic of China, where he is a Professor of the Department of Communication Engineering and a member of Center for Telecommunications Research. He received an Outstanding Paper Award from the Institute of Chinese Engineers in 1991. His current research interests are in communication protocols and broadband