Study of Virtual Admission Control Scheme in Wireless LAN
全文
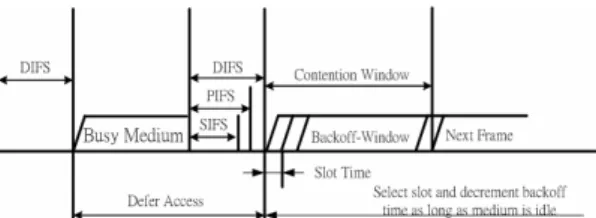
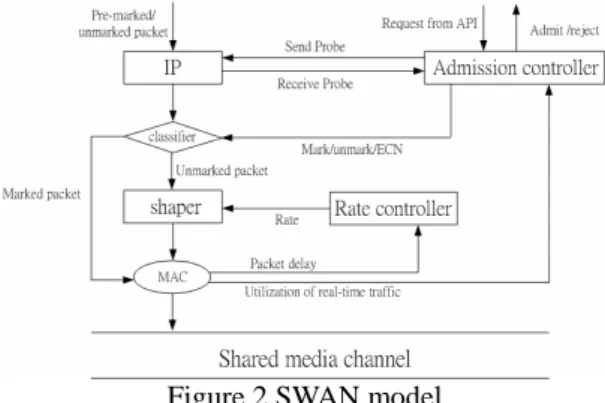
(2) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. waiting for a DIFS time duration. On the contrary, we can let the higher priority station have shorter backoff time. In [3], they use two methods, one is shorter random backoff time and the other is shorter IFSs. They divide the stations into high priority and low priority. For the high priority stations, the IFSs are changed from DIFS to PIFS and random backoff time generation function are from ranf () 22i *slot_time to ranf()22i / 2*slot_time,. Figure 2 SWAN model. tests only at the source by estimating local available bandwidth availability. The admission controller probes the network between the source and the destination to determine whether the end-to-end bandwidth is sufficient or not. Among the methods mentioned above in SWAN, the most important methods are the rate controller and the admission controller. The rate controller is used for the management of UDP and TCP best effort traffic and sender-based admission control for UDP real-time traffic. The rate controller determines the departure rate of the shaper using the AIMD (Additive Increase Multiplicative Decrease) rate control algorithm based on the feedback from MAC. The feedback information used by the rate controller represents the packet delay measured by the MAC layer. The admission controller will send probe to the IP network and make decision according to the receiving probe. SWAN is a simple, distributed and stateless network model that can support soft real-time services and service differentiation in wireless ad hoc networks. It is independent of the underlying MAC layer and can be suited for various physical and data link wireless standards. B. VS/VMAC In [10] and [11], the VS/VMAC (Virtual Source/Virtual MAC) methods are proposed based on traffic statistics. The main idea is to construct a VMAC whose behaviors are mostly like the real MAC including contention, backoff and drop mechanism, but there are some differences. For example, the collision detection is determined in real MAC by the expiration of the timer. However, the collision detection determined in VMAC is by detecting if the medium is busy or not, the packet is not actually sent. Whenever the VMAC encounters collision, it will also retry to send the packet until reaching the retry limit. The packet delay could be affected by various factors including packet transmission rates and packet sizes. The faster the packet rates, the smaller the packet size is. Higher rate of packet makes the radio channel busier and causes more collisions and, therefore, increases the average contention window. In addition, higher packet rates mean small data packets, which result in larger protocol overhead. Thus at the same bit rate, there is always a tradeoff between packetization delay and MAC delay for network applications.. In figure 2, the classifier is capable of differentiating real-time and best effort packets, forcing the shaper to process best effort traffic but not real-time packets. The shaper is similar to a leaky bucket and its goal is to delay best effort packets in conformance with the rate calculated by the rate controller. The admission controller. C. IEEE 802.11e 802.11e is working in progress and currently has been developed to Draft 8.0 in February 2004 before the thesis is completed. The purpose of 802.11e is to solve the shortcomings of the legacy MAC for QoS. The MAC of 802.11e architecture is shown in figure 3. 802.11e adds some features. where i is the number of consecutive times a station attempts to send a frame, ranf() is a uniform variation in (0,1), and x represents the largest integer number less than or equal to x. For the low priority stations, the IFSs are still DIFS and the random backoff time is 2 2i / 2 ranf () 2 2i / 2. In [9], they assume the traffic can be sorted as TCP and UDP flows and they also change the backoff generation 2i function and IFSs. The item “2 ”in the backoff 2 i generation function 2 rand ()*slot_time has been replace by Pj2i where Pj is a priority factor of the wireless terminal j. As for the IFSs, they use different DIFS, say DIFS j where. DIFS j 1 < DIFS j . Except for the modifications from the MAC specification, some other schemes are described in the following paragraphs. A. SWAN(Service Differentiation in Stateless Wireless Ad Hoc Networks) SWAN is proposed by Gahng-Seop Ahn, Andrew T. Campbell, Andras Veres, Li-Hsiang Sun in [5].The main idea is that if each mobile station can govern itself then the traffic condition in wireless medium will be much better. There are many methods mentioned in the SWAN model as shown in figure 2.. 287.
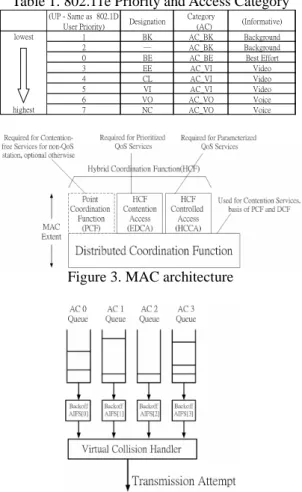
(3) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. that can support QoS and service differentiation. Conceptually speaking, the differences between 802.11e MAC and legacy MAC are the quantification of the QoS. Traffic has been differentiated into 8 priorities (also called traffic categories: TC) and these 8 TCs are mapped into 4 ACs (access categories) as list in table 1. Besides, there are multiple queues, instead of one queue in legacy MAC in order not to let the former lower priority data block the latter higher priority data as shown in figure 4. Table 1. 802.11e Priority and Access Category lowest. highest. (UP - Same as 802.1D User Priority) 1 2 0 3 4 5 6 7. Designation BK ─ BE EE CL VI VO NC. Category (AC) AC_BK AC_BK AC_BE AC_VI AC_VI AC_VI AC_VO AC_VO. (Informative) Background Background Best Effort Video Video Video Voice Voice. Figure 3. MAC architecture. number of the mobile node is increasing and the VMAC delay is always higher than the RMAC. If we use the VS/VMAC to estimate the delay of the channel, it will be more and more inaccurate. To make VS/VMAC more precise, we define a “ difference factor (D)”to indicate the ratio of the RMAC delay to the VMAC delay. With the D factor, we can use VS/VMAC to estimate the delayV closer to the delayR. D factor will have influences on how the VAC operates loosely or tightly. If the VAC operates more conservative, the admitted demands will be low and the MAC delay will not increase too much. In the simulation, we will use different D factor to see the MAC delay. B.. FP Traffic As we mentioned before, we use the best effort traffic to be upgraded as the high priority as demanded traffic to detect the MAC delay. We define this kind of traffic as “ fake priority (FP)” traffic. There are some reasons that we use best effort traffic as the high priority traffic to probe the channel status. One of the reasons is that people would rather see the connection being rejected instead of being admitted with a poor QoS. If the channel is crowded, the FP traffic will be dropped during probing instead of the real high priority data. Another reason is that if the FP traffic can be transmitted successfully, the algorithm wastes no extra resources to estimate channel status. If there is no best effort traffic, we will only use the results estimated by VS/VMAC to do VAC. C.. Figure 4. Reference implementation model. III. Virtual Admission Control. VAC Algorithm The proposed VAC algorithm regards the the FP (best effort) traffic or the VS/VMAC as the “ virtual admitted”traffic stream to measure whether the received QoS complies with the requirement of the request connection. The proposed VAC algorithm is illustrated as follows: Start. rateV = (sessionR +1)* rateR 802.11e prioritized QoS can provide service New_traffic differentiation by using traffic categories and Step 1: VS/VMAC algorithms can provide a channel if (delayR < delay_tolerance AND status estimation without loading the wireless medium. Each traffic session has its own interval D*delayV < delay_toleranc) then admit; or session time and it is not infinite. If there are else many multimedia sessions which are established go to step 2; at the same time, the estimation of the VS/VMAC Step 2: algorithm will be much inaccurate. We propose an if (delayR < delay_tolerance OR algorithm called Virtual Admission Control (VAC) D*delay < delay_toleranc) V to provide better QoS to multimedia traffics. then go to step 3; else A. D Factor reject; From our simulation [12], we found that the Step 3: delay difference (i.e. the gap between the RMAC if there exists best effort traffic and VMAC) is gradually increasing as the. 288.
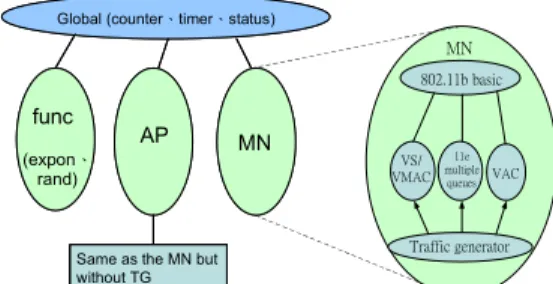
(4) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. then go to step 4; else admit; Step 4: Swtich AC of new traffic use FP traffic to probe for CET time then go to step 5; Step 5: If ( delayR_before + delayR_after )/2 < delay_tolerance then admit; else reject; End SessionR is the current session counts of the real traffic. D is the difference factor. Delay_tolerance is the delay tolerances of the demanded traffic. FP_VO is the FP traffic with the AC_VO traffic category while FP_VI is the FP traffic with the AC_VI traffic category. DelayR_before is the delayR calculated before new traffic demands and delayR_after is the delayR calculated after new traffic demands. RateV and RateR are the traffic rate input to the VMAC and RMAC respectively. Since we want to use VS/VMAC to estimate the MAC delay when a new session is admitted, we have to increase the traffic rate of the VMAC by 1 session to simulate the condition.In the first step, the sender has to check whether the previous delayR is smaller than delay_tolerance or not, and use delayV with the D factor modification to estimate the MAC delay if a new session is admitted. Step 1 is the strict condition. Step 2 is the loose condition of step 1. Step 3 checks if there exists best effort traffic. With best effort traffic, we can use the traffic to be upgraded as the high priority traffic to probe the channel for CET time. When CET time finishes, we calculate the previous MAC delayR and the delayR after the demands to see if there is sufficient resource. FP_VO is the FP traffic with the AC_VO traffic category while FP_VI is the FP traffic with the AC_VI traffic category. DelayR_before is the delayR calculated before new traffic demands and delayR_after is the delayR calculated after new traffic demands. RateV and RateR are the traffic rate input to the VMAC and RMAC respectively. Since we want to use VS/VMAC to estimate the MAC delay when a new session is admitted, we have to increase the traffic rate of the VMAC by 1 session to simulate the condition. In the first step, the sender has to check whether the previous delayR is smaller than delay_tolerance or not, and use delayV with the D factor modification to estimate the MAC delay if a new session is admitted. Step 1 is the strict condition. Step 2 is the loose condition of step 1. Step 3 checks if there exists best effort traffic.. With best effort traffic, we can use the traffic to be upgraded as the high priority traffic to probe the channel for CET time. When CET time finishes, we calculate the previous MAC delayR and the delayR after the demands to see if there is sufficient resource.. IV Performance Simulations The simulation architecture is shown in figure 5 and the simulation program is written in C. At the top of the architecture, there are some global variables to record much information about the simulation such as counters, timers and system status. The right side of figure 5 is the detailed portion of a mobile node. A mobile node consists of some parts such as 802.11 basic mechanisms, VS/VMAC, 802.11e multiple queues and the proposed VAC algorithm. Each node has its own traffic generator to simulate the background and the demanded traffic including best effort, video and voice. Global (counter、timer、status). MN 802.11b basic. func (expon、 rand). AP. Same as the MN but without TG. MN. VS/ VMAC. 11e multiple queues. VAC. Traffic generator. Figure 5. Simulation architecture In our simulation, we assume that the channel is error-free and all of the mobile nodes are in the same BSS. The buffer of each mobile node concerned is infinite (i.e. the packet will never be dropped due to buffer overflow). The session time, when a new request is admitted, is Poisson distributed with mean 2 minutes to emulate a telephone call or a short video conference call. The tolerance of CET time, setup time, is defined as 1 second. The channel rate is 11 Mbps and other parameters used in our simulation are listed in table 2. Finally, the number of mobile nodes which transmits packets is from 1 to 20. We use the RTS/CTS mechanism to solve the hidden node problem. The collision will only occur when there are at least two stations choosing the same timeslot to send packets after backoff procedure and will never occur during transmitting. Voice traffic category is modeled as 32 Kbps CBR (constant bit rate) and video traffic is modeled as 200 Kbps CBR. Best effort traffic has infinite long traffic at 350 Kbps as the background traffic. The rate of voice and video are the same as in [4]. The background traffic will influence and load the channel. Under fewer mobile nodes condition, the total required bandwidth is less than the provided bandwidth. And when the number of mobile node. 289.
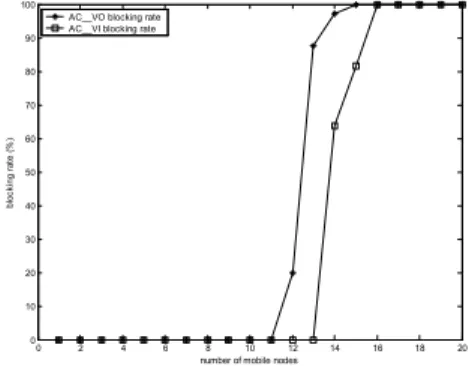
(5) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. increases, the demanded bandwidth is larger than the provided and the channel will go into saturation. We want to see if the prioritized QoS and the VAC mechanism work or not under over-load and non over-load conditions.. 4. 16. x 10. AC__VO with VAC AC__VO without VAC AC__VI with VAC AC__VI without VAC. 14. 12. delay (in us). 10. Table 2. Simulation arameters Slot time 20 us SIFS 10 us DIFS 50 us PHY Header 192 us AirPropagationTime 1 us CWmin 31 CWmax 1023 RetryLimit 4 PacketSize 1500 bytes Length of RTS PHY Header+20 bytes Length of CTS PHY Header+14 bytes Length of Ack PHY Header+14 bytes. 8. 6. 4. 2. 0. 0. 2. 4. 6. 8 10 12 number of mobile nodes. 14. 16. 18. 20. Figure 7. Delay comparison of VAC and none-VAC with thd_voice =30ms and thd_video = 50ms Besides, the relationships between blocking rate and request demands counts are shown in figures 9 and 10. For example, the blocking rate of voice and video will increase from 11 nodes and 13 nodes respectively as shown in figure 9. In figure 9 the delay threshold of voice and video is The results of using VAC are shown in the 20ms and 30ms. Take figures 9 and 10 for following. We change the delay threshold of voice comparison, the voice delay threshold is 20ms and video to see the results. In the following and 30ms, respectively. The blocking rate is simulation, we use thd_voice and thd_video to increasing from 11 to 15 nodes. The smaller the represent the delay threshold of voice and video delay threshold is, the faster the blocking rate respectively. For example, “ thd_voice = 10ms” increases. Also take a look at the requested means that the delay tolerance of voice is no more demands counts in figure 7, before the blocking than 10ms. From figures 6 and 7, we found that rate increases the VAC algorithms have admitted the specific QoS can be maintained by restricting about 70 requests (voice requests + video requests) the requested demands. It is the tradeoff between and do not have much influences on the MAC the connection number and the QoS but, in fact, delay. we can admit small number of requests and do not deteriorate the QoS too much. Without admission control, the delay will increase to an unacceptable degree that all of the applications, including background traffic, will be with poor QoS. 100. AC__VO blocking rate AC__VI blocking rate. 90 80. blocking rate (%). 70. 4. 16. x 10. AC__VO with VAC AC__VO without VAC AC__VI with VAC AC__VI without VAC. 14. 60 50 40 30 20. 12. 10. delay (in us). 10 0. 0. 2. 4. 6. 8. 14. 16. 18. 20. Figure 9. Blocking rate with thd_voice = 20ms and thd_video = 30ms. 6. 4. 100. 2. AC__VO blocking rate AC__VI blocking rate. 90 0. 8 10 12 number of mobile nodes. 0. 2. 4. 6. 8 10 12 number of mobile nodes. 14. 16. 18. 20. 80 70. blocking rate (%). Figure 6. Delay comparison of VAC and none-VAC with thd_voice =20ms and thd_video = 30ms. 60 50 40 30 20 10 0. 0. 2. 4. 6. 8 10 12 number of mobile nodes. 14. 16. 18. 20. Figure 10. Blocking rate with thd_voice = 30ms and thd_video = 50ms. 290.
(6) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. V Conclusions In this paper, we propose VAC to do admission control by using the heuristics of traffic probe over the algorithm of 802.11e multiple queue architecture. The main concept is that whenever there is a traffic demand for some mobile stations, and the station will estimate the current QoS parameter by using traffic stream with FP priority or the VS/VMAC to see if there is enough bandwidth in the wireless channel. If the current resources are not sufficient then the demand will be rejected or admitted otherwise. Thus, the provisioning of QoS is achieved by self-governing mechanism. In order to estimate the current delay but not to load the wireless medium, we use VS/VMAC algorithm with D factor to estimate the current channel status as precise as possible. The experimental results show that the total admitted new requests with VAC is better than conventional WLAN. And the delay of VAC is much better than that without VAC. The reason is that, all requested demands will be admitted immediately and they will have much influences on the wireless QoS without VAC. In this paper, we only consider the admission control of new connections. However, in addition to providing new connection requests, an AP has to handle the handoff connections. Therefore, it is interesting to consider the admission control by using the QoS-aware in a multiple AP environment.. Acknowledgements This research is supported in part by the grants from the Ministry of Transportation and Communications (MOTC-SATO-93-14) and the National Science Council (NSC 93-2213-E-008-034).. Best-Effort Traffic in Stateless Wireless Ad Hoc Networks (SWAN)", IEEE Transactions on Mobile Computing, Vol.1, No.3, Pages:192-207, Jul. 2002 [6].D. Pong and T. Moors, "Call Admission Control for IEEE 802.11 Contention Access Mechanism", Proc. Globecom 2003, Pages: 174-8, Dec. 1-5, 2003 [7].http://www.merl.com/reports/docs/TR2003-12 2. pdf , ” A New Measurement- Based Admission Control Method for IEEE802.11” ,Mi t s u bi s h i Electric Research Laboratory, 2003 [8].http://www.research.avayalabs.com/techreport /ALR-2002-021-pa pe r . p df ,“ A New Admission Control Metric for VoIP Traffic in 802.11 Networks” [9].I. Aad, and Claude Castelluccia, “ Differentiation Mechanisms for IEEE 802.1.” , Pr oc . I EEE I n f oc om 2001 , Pages:209-218, Apr. 2001 [10].Andras Veres, Andrew T. Campbell, Michael Barry, "Supporting Service Differentiation in Wireless Packet Networks Using Distributed Control", IEEE Journal on selected areas in communications, Vol.19, No.10, Pages: 2081-2093, Oct. 2001 [11].Barry, M., Campbell, A.T , A. Veres , "Distributed Control Algorithms for Service Differentiation in Wireless Packet Networks", IEEE Infocom 2001, Vol.1 , Pages:582-590, Apr. 2001 [12].Yuan-Long Lee, A Study of Virtual Admission Control in Wireless LAN, master thesis, Dept. of Communication Engineering, National Central University, June, 2004.. REFERENCES [1].http://grouper.ieee.org/groups/802/11/index. html [ 2] . M. Vi s s e ra n d M. El Za r k i ,“ Voice and data transmission over an 802.11 wireless network” ,Pr oc e e di n g sofPI MRC,Tor on t o, Canada, Sept. 1995. [3].Dr-Jiunn DENG, Ruay-Shiung Chang, "A Priority Scheme for IEEE 802.11 DCF Access Method", IEICE Trnasactions on Communications, Vol.E82-B, No.1, Pages:96-102, Jan. 1999 [4].Gahng-Seop Ahn, Andrew T. Campbell, Andras Veres, Li-Hsiang Sun, "SWAN: Service Differentiation in Stateless Wireless Ad Hoc Networks", Proc. IEEE Infocom 2002, Jun. 2002 [5].Gahng-Seop Ahn, Andrew T. Campbell, Andras Veres, Li-Hsiang Sun, "Supporting Service Differentiation for Real-Time and. 291.
(7)
數據
相關文件
According to the regulations, the employer needs to provide either a mobile or landline phone number at which the employer (or a contact person) can be reached.. If
A theoretical and reflexive study on cultivating literacy of mathematical culture by using lesson plans from humanistic mathematics.. Taiwan Journal of Mathematics Education,
If the bootstrap distribution of a statistic shows a normal shape and small bias, we can get a confidence interval for the parameter by using the boot- strap standard error and
If growing cities in Asia and Africa can provide clean, safe housing, the future of the people moving there should be a very good one... What is the main idea of the
• Guidelines can help commissioners and purchasers to make informed decisions and provide managers with a useful framework for assessing treatment costs...
Programming languages can be used to create programs that control the behavior of a. machine and/or to express algorithms precisely.” -
In case of non UPnP AV scenario, any application (acting as a Control Point) can invoke the QosManager service for setting up the Quality of Service for a particular traffic..
Model checking: residuals can be obtained by 1-step ahead forecast errors at each time point, (observations minus the fitted value) Then if the model is adequate, residuals should