Electronic Commerce Studies Vol. 3, No.1, Spring 2005
Page 15-38
Consumption Externalities:
Review and Future Research Opportunities
David M. Chiang National Taiwan University
Ching-i Teng
Department of Business Administration, Chang Gung University
Abstract
An extensive literature review of consumption externalities is presented in this article. The review is classified into four sections: network externality, indirect network externality, congestion externality, and cross-consumer externality. The review of network externality is a fundamental part of this paper. In this paper, we first suggest two dimensions and provide a classification on consumption externalities. Similarities and dissimilarities among them are contrasted. We next review the literature on consumption externalities in four sections. Finally, we raise research opportunities, which can be further explored in four fields.
Keywords: consumption externalities, network externalities, cross-consumer externality, congestion externality
1. Introduction
The rise of information technologies is dramatically changing the world. In information economies, network externality acts as an engine and plays a critical role in technology competitions. It has been nearly 20 years since the emergence of network externality, providing a reasonable time period for the review of literature on this area and to find future research opportunities.
Network externality by nature is a kind of positive consumption externality. As the topic gains popularity more network-related externalities emerged. Examples of other consumption externalities include “network externality”, “positive consumption externality” (Katz & Shapiro, 1985), “positive demand externality” (Xie & Sirbu, 1995), “indirect network externality” (Gupta et al, 1999), “complementary network externality”
(Church & Gandal, 1993), “congestion externality” (Westland, 1992), and “cross-consumer externality” (Holcombe & Sobel, 2000). Some of them are interchangeable but some are not. Similar terms may confuse preliminary researchers and practitioners. A clarification on the similarities and dissimilarities amongst consumption externalities is essential for better understanding. However, no paper formally attempted to clarify and classify the literature on network externality. Therefore, an extensive review is needed to clarify their definitions and classify these past researches on consumption externalities.
This paper has three purposes. Firstly, to provide two dimensions, “positive or negative” and “direct or indirect”, to determine the four categories. These categories are: network externality, indirect network externality, congestion externality, and cross-consumer externality. We further list definitions on various consumption externalities to contrast the similarities and dissimilarities among them.
Based on the classifications above, the second purpose of this paper is to systematically review the literatures on each of the categories on consumption externalities. Amongst various consumption externalities network externality is the most popular and novel type. Network externality is a key feature of the information economy (Shaw, 2000) as it has significantly existed in many industries (Katz & Shapiro, 1986). Therefore we will review numerous papers on network externality.
The third purpose of this paper is to highlight several research opportunities on issues such as targeting, diversification, innovation diffusion, and modifications of network externality. These research opportunities can be further studied in the fields of marketing, business strategy, technology management, and industrial organization.
This paper is organized as follows. The first section introduced the importance of an extensive review on consumption externalities and the three purposes attempted by this paper. The second section provides a classification scheme and subsequently the four categories on consumption externalities. It also lists the definitions on various consumption externalities in order to identify the similarities and dissimilarities amongst them. Sections three to six review the literature on consumption externalities by the four categories mentioned above. The final section suggests some research opportunities under these four categories.
2. Classification and the Four Categories
We observe that two dimensions, namely, (1) positive or negative, and (2) direct or indirect, are frequently used in previous researches to classify various consumption externalities. We can see these two dimensions from another angle. Consumer utility function can be written as U(x, y, X), where x is this individual’s consumption on network good, y is the consumption on complementary goods, and X is the whole economy’s consumption on network good. The first dimension, positive or negative, can be the direction of X on MUx. On the other hand, the externality can be judged as direct externality when X directly influences MUx. The externality is indirect when X influence MUx through other paths.
Under these two dimensions, we have four (2x2) categories. We further name each category by their most commonly used term. Those categories are shown in Table 1. The four categories on consumption externalities
TABLE 1:
Direct Indirect
Positive Network externality Indirect network externality
Negative Cross-consumer externality Congestion externality
2.1 Network Externality
Amongst all consumption externalities, network externality is the most popular and novel one. Katz & Shapiro (1985 : 424) defined positive consumption externality as “the utility a user derives from consumption increases with the number of other users consuming the good”. They further described network externality as “positive external consumption benefits” (Katz & Shapiro, 1986:823). Similar to the definitions above, the definition of network externality provided by Economides (1996:678) is “the fact that the value of a unit of the good increases with the number of units sold”. Communication technologies are the mostly used example.
Another term to describe “positive consumption externality” is “positive demand externality”. Xie & Sirbu (1995:909) discussed positive demand externality by using electronic mail service as an example. They stated, “The value to a user of an electronic mail service depends upon how many other
users subscribe to the service”. We think the definitions on network externality, positive consumption externality, and positive demand externality are identical by nature. Amongst these terms, network externality is the one most commonly used and recognized. Accordingly, we use network externality to represent the category of “direct-positive consumption externality”.
2.2 Indirect Network Externality
Following network externality, the concept “indirect network externality” first appeared in the work by Chou & Shy (1990). Gupta et al (1999:396) later defined indirect network externality as the phenomenon where “demand for hardware products is mediated by the supply of complementary software products”. A refined definition by Le Nagard-Assayag & Manceau (2001:203) says, “The utility of the main product often depends on the availability of complementary products.” In addition, there is another term representing this similar concept. Complementary network externality (Church & Gandal, 1993:239) describes the same concept more vividly. Based on the level of prevalence, we choose indirect network externality to represent the category of “indirect-positive consumption externality”. Hardware, together with software, is the most common instance.
Indirect network externality is different from network externality. The most distinct feature of indirect network externality is that the external effect of consumption on other consumers is indirect, not direct.
2.3 Congestion Externality
Consumption externalities are not all positive to consumer utility. For instance, congestion externality is negative to the utility of all users affected by congestion. Although congestion externality does not only exist on the demand side, we define the term “congestion externality” in this paper to strictly refer to congestion externality on the demand side. Congestion externality or congestion effects “have been the focus of study in queuing theory…there is a large body of related literature on models of congestion effects” (Stenbacka & Tombak, 1995:437). Due to limited length of this article, we will only discuss some papers from this area of literature.
The typical real-life examples are highway traffic congestions and information system services. “Congestion externality reflects the nuisance
caused by contention for shared resources” (Westland, 1992:993), and subsequently brings delays to consumers who line up in the queue (Ha, 1998). The capacity-sharing property or prolonged waiting time has been vividly described by the term congestion externality. Therefore, we take congestion externality to represent the category of “indirect-negative consumption externality”.
Congestion externality is different from network externality or indirect network externality, in which for congestion externality the external effect of consumption on other consumers is negative, not positive.
2.4 Cross-consumer Externality
Comparing to other consumption externalities cross-consumer externality has been far less studied. Holcombe & Sobel (2000) defined cross-consumer externality as the externality between individuals that directly lowers the level of household production given inputs constant. We intend to define cross-consumer externality as the condition when consumer’s utility changes as a result of other consumers’ presence or behavior. Without alternatives, we use cross-consumer externality to represent the “direct-negative consumption externality” category.
Similar to congestion externality, cross-consumer externality imposes negative external effect of consumption on other consumers. Cross- consumer externality, however, directly arises from other consumer’s presence or behavior even when no congestion takes place and waiting time does not increase. For example, smoking by some consumers can impose cross-consumer externality on nonsmoking consumers in the same service space. Loud talking can also have the externality. Thus, cross-consumer externality really exists in real world.
The four categories above have one feature in common: all are consumption externalities, that is, the externalities referred to in these categories all stem from other consumer’s consumption.
3. Network Externality
With the four categories of consumption externalities identified, we may now review studies in each category, respectively.
Network externality has the characteristic of the economies of scale on the demand side. It is also called “positive consumption externality” (Katz & Shapiro, 1985; Economides, 1996), or “positive demand externality” (Xie &
Sirbu, 1995). Network externality is also a self-reinforcing mechanism (Agliardi & Bebbington, 1997) or positive feedback mechanism (Shapiro & Varian, 1999a). In industries where network externality exists, they include information products, communication networks, durable goods and services. Typical examples are telephone, image phone, e-mail, videotape, computer operating system, office software, TV game player, surgical operation, computer language, and computer keyboard.
In the academics realms, a number of classic works (Oren & Smith, 1981; Oren, Smith & Wilson, 1982; Katz & Shapiro, 1985, 1986; Farrell & Saloner, 1985, 1986) led the stream of research on network externality. We will review studies on network externality in the following four subsections by their topics.
3.1 Excess Inertia and Excess Momentum
Researchers first found that network externality creates inefficiency in technology innovations. The utility from communication with other customers in the incumbent’s system is included in the switch cost. Thus, the incumbent’s customers are less willing to switch to the challenger’s system if the utility from existing communication with other customers is high. That is, the incumbent may win over the challenger even when the challenger has superior technology. David (1985) took QWERTY keyboards as an example, QWERTY keyboards are not technologically superior to Dvorak keyboards but QWERTY wins over Dvorak because of a very high switch cost of changing the typing habit. David (1985) indicated that the result is not socially optimal. Farrell & Saloner (1985:70) named the phenomenon as “excess inertia”. The efficiency of keyboards is still in debate. Details can be found in Liebowitz & Margolis (1990).
On the other hand, “excess momentum” may also take place when network externality is at work (Farrell & Saloner, 1986:940). Excess momentum describes the phenomenon where only the incumbent’s technology may achieve a socially optimal outcome but the challenger successfully captures the whole market. De Bijl & Goyal (1995) further found that excess inertia, excess momentum, or the coexistence of two technologies might take place in equilibriums regardless of homogeneous or heterogeneous consumers.
Katz & Shapiro (1992) pointed out an occasion in which excess inertia does not exist. When market grows exponentially network externality cannot restrain technology innovations. On the contrary, network externality induces
firms to introduce incompatible and immature new technologies and products. The firms get less than what they contribute to social welfare. Thus, social welfare deviates from optimum. The phenomenon is called “insufficient friction” by Katz & Shapiro (1992:55).
The literature on excess inertia and excess momentum theoretically explain why inefficiency exists in technology innovation. Future works can empirically apply their conclusions to the practice to verify, falsify, or revise their theories or explanations.
3.2 Critical Mass and Lock-in Effect
Besides excess inertia or excess momentum, the property of increasing return is another focus for researchers. Network externality builds up very high switch costs for the “installed base”. Farrell & Saloner (1986:941) defined “installed base” as “those who had previously adopted the old technology”. Thus, the firm with a larger installed base has a competitive edge to expand the firm’s market share (Shaw, 2000) and therefore, a positive feedback loop is formed. “The strong grows stronger and the weak grows weaker” (Safferstone, 1999:118) may best describe the loop. As a result, theoretically, the firm with a larger initial installed base would eventually saturate the whole market. A market characterized by network externality is also called as a “winner-take-all market”.
Resulting from the increasing return of network externality there would be a threshold (by the number of consumers) in the incumbent’s system. Once the threshold is reached the incumbent would become a natural monopolist. No challenger may capture more than a small fraction of the market. This threshold is called the “critical mass” (Oren & Smith, 1981) and the phenomenon where consumers sustain very high switch costs is called “lock-in effect”.
To achieve the “lock-in effect”, firms keenly race in divergent directions of their R&D initiatives in order to be the only survivor to capture the whole market. The enormous R&D costs incurred and the resulted incompatibility of technologies deviate social welfare from optimality (Kristiansen, 1998). Moreover, an existing firm would adopt a more risky R&D project whereas a newcomer would adopt a less risky R&D project. The phenomenon also compromises social welfare (Kristiansen, 1996).
Since network externality foretells that the firm capturing more than the critical mass would eventually capture the whole market, should a firm adopt an initial low price strategy? With three conditions: (1) Imperfect information
on demand, (2) Asymmetric cost information and (3) Little influence by individuals on other consumers, adopting an initial low price would be an optimal strategy (Cabral, Salant & Woroch, 1999).
However, the foretold “lock-in effect” rarely happens. A number of challengers still outperform incumbents in industries characterized by network externality. Witt (1997) explained the phenomenon with an incumbent-challenger model. When a market is growing rapidly, the challenger may capture most of the newcomers to form a larger installed base than the incumbent’s. Thus, the challenger may replace the incumbent to “lock” the market, which explains the challengers’ success. Belleflamme (1998) proposed another explanation in the market of industrial technology. With heterogeneous cost structures both firms may coexist in equilibrium.
The literature of critical mass and lock-in effect has been cited in academic journals in economics, management, and information technology. Most researches addressing network externality mentioned critical mass or lock-in effect. This part of literature can be said to have the very impact on issues in and across many disciplines.
3.3 Business Strategies
Firms seek out ways to take advantage of the property of increasing return in network externality. Examples include compatibility decisions, seeking for sponsorship, encouraging “clones”, allowing piracy, providing an adapter, and planned obsolescence.
Compatibility is an important strategic decision in competition especially when network externality is at work. Firms with better prestige or a larger existing network may tend to introduce products that are incompatible with other firms’ products. The strategic action deviates social welfare from optimality (Katz & Shapiro, 1985).
Seeking for sponsorship is an alternative strategy. In competition, the firm with sponsorship may sell its products at a price lower than marginal cost in the short run to secure a larger installed base initially in the competition. The impact of sponsorship on competition may outweigh the technological performance. That is, the firm with sponsorship and inferior technology may still win out and capture the whole market. This also compromises the optimal social welfare (Katz & Shapiro, 1986).
Network externality turns some intuitively correct business strategies, such as eliminating piracy and “clones”, into incorrect decisions. Conner & Rumelt (1991) proposed that piracy in the software industry could increase
the monopolist’s profit and lower the price to benefit every party (firm, licensed users and illegal users) when network externality is at work. Conner (1995) further showed that firms in specific occasions should encourage “clones” to expand the low-end market segment when the market is characterized by network externality. Firms are better off allowing the clone to set the price level in the low-end market so the firms may then capture the high-end segment. In line with the work by Conner (1995), Xie & Sirbu (1995) illustrated that the incumbent makes profits from compatible entries when there are strong demand externalities and a small installed base.
Providing an adapter is also an alternative strategy. If an adapter is available with an agreement by the two firms then these two firms will always come to an agreement to provide the adapter, even if the firm producing high quality products prefers incompatibility. Consequently, the result is socially optimal (Baake & Boom, 2001).
For monopolists, network externality helps to build entry barrier against potential competitors. Incumbent firms could preannounce their new products and set predatory prices to deter entry (Farrell & Saloner, 1986). The incumbent could also implement “planned obsolescence” strategy. The incumbent may offer a product in the first period, and offer an incompatible product to the previous product in period two to make the previous product “obsolete”. This strategy benefits the incumbent more when stand-alone utility is larger or production cost is smaller in the second period (Choi, 1994).
In addition to planned obsolescence, the incumbent could also reserve a part of quality in the first period. When information of externality is asymmetric, the incumbent could introduce an inferior product first and then later on introduce an “upgrade” version of the same product with full quality to gain more from the customers (Padmanabhan et al., 1997).
Other strategies include licensing, diversifying into complementary goods, forming strategic alliances (Hill, 1997), taking first-mover advantage, managing customers’ expectation (Shapiro & Varian, 1999b). In addition, learning about the orientation and the timing of entry also play important roles in order to succeed (Schilling, 2002).
One recent research, Chiang & Teng (2003), show that network externality does not only foster a network’s growth, but also facilitate its collapse when it is under attack. Chiang & Teng (2003), comparing to the literature, addresses the negative side of network externality. That is a whole new angle to see network externality.
management researches. Theoretical extension with the operations research approach or empirical testing with strategic management methodology is very timely and promising.
3.4 Governors’ Policies
Since network externality causes many kinds of inefficiency in competition, what should the policy makers do to correct the inefficiency? Is it by protecting the property right or setting a standard?
First, property right is designed to protect the first-mover’s efforts and to encourage innovations. The real effect is just the contrary. Any first-mover would delay his/her entry and as a result delay the expiration date of the protection. Thus, a first-mover would have to lower its costs and provide better qualities in order to compete with the new entrants at the end of the delayed expiration of the protection period. Therefore, property right does not work to eliminate the inefficiency that network externality brings (Katz & Shapiro, 1992).
Secondly, “setting standard” seems to have the capability to stop the incompatible R&D race. In reality, standard setting policy can accelerate the R&D race, because firms struggle to make their design chosen as the government’s “standard” (Kristiansen, 1998).
Thirdly, the “forced licensing” policy could eliminate the inadequate incentive to slow down the incompatible R&D race. Thus, the “forced licensing” policy eliminates part of the inefficiency which network externality brings (Kristiansen, 1998).
One may concern that the literature on network externality focused on what impacts it has, not how does it have those impacts. The reason may be that the literature regarded the utility from compatibility and communication as very intuitive.
This intuition, however, lacks formal empirical evidence. Why whole economy’s consumption can affect individual’s utility from consumption? Empirical researches finding out the mechanism should be encouraged to provide the empirical foundations for network externality.
4. Indirect Network Externality
The second category of consumption externalities is indirect network externality. In services industries, hardware-software industries, and durable goods industries (Katz & Shapiro, 1985), the number of consumers does not
directly increase the utility of all of the consumers. The number of core product adopters may first stimulate the development of complementary goods (Church & Gandal, 1993; Bental & Spiegel, 1995). Then all adopters’ utility may increase indirectly because they have a larger variety of complementary goods. A variety of complementary goods (repair service, software) contributes to the main value of the core products (durable goods, hardware). Thus, the mechanism is referred to as the “indirect network externality” by Gupta et al. (1999 : 396) and “complementary network externality” by Church & Gandal (1993:239).
Inefficiency may also occur when indirect network externality exists. The hardware technology with lower software development cost would be over adopted to create inefficiency. If the regulator has relevant cost information and can regulate the price and entry for software then the inefficiency could be reduced (Church & Gandal, 1993). Will the “lock-in effect” occur when indirect network externality is at work? Agliardi & Bebbington (1997) showed that a market cannot lock in a single technology in equilibrium if the market information is imprecise.
As to business strategies, Le Nagard-Assayag & Manceau (2001) proposed that the success in the durable goods industry is determined by customers’ expectation, which can be improved by the preannouncement of new products.
On the other hand, the policy maker may set a single standard on the core product to maximize the variety of complementary goods in order to increase social welfare (Church & Gandal, 1992). This idea contradicts the traditional view that more variety (of core products) results in higher social welfare (Chou & Shy, 1990).
One may concern that indirect network externality is similar to increasing returns to scale (Helpman, 1982). Indirect network externality may involve increasing returns to scale on both demand and supply sides, and thus be related to learning effects and division of labor. The relationship of indirect network externality and sources of increasing returns to scale should be distinguished by researches on indirect network externality in the future.
5. Congestion Externality
The third category of consumption externalities is congestion externality. Congestion externality may result from the usage and sharing of scarce resources (Hellofs & Jacobson, 1999). For example, highway users during rush hour collectively create the congestion and then indirectly reduce the
utility of every user. Services with limited capacity, such as restaurants and airplanes, all exhibit congestion externality amongst consumers.
In addition to tangible services, information system service is of another focus. The information system service will be over-utilized if congestion externality is not taken into account when computing the internal transfer price. The information system on the contrary will be under-utilized if network externality is not considered. The over- or under- utilization deviates social welfare from its optimality (Westland, 1992).
The literature on congestion externality is rather little in management journals. Researches on service industries can consider incorporating congestion externality to reflect the booming of population and its impact on business practice.
6. Cross-consumer Externality
The final category of consumption externalities is cross-consumer externality. Few researches have discussed this externality. Katz & Spiegel (1996) proposed that the presence of different social classes results in cross-consumer externality. With cross-consumer externality, there can be a section of demand curve with a positive slope. Their study, however, did not focus on taking advantage of such externality.
A recent conceptually crafted paper by Holcombe & Sobel (2000) gave an analogy of production externalities and consumption externalities. They thought that cross-consumer externality, which results from other consumer’s behavior, such as smoking, is relevant to social welfare. On the other hand, interdependent utility which arises from other consumer’s consumption is NOT relevant to social welfare. The preliminary work by Chiang & Teng (2001) showed that the knowledge of cross-consumer externality helps managers to increase the correct estimation of revenues and thus make better pricing and targeting decisions.
The literature on cross-consumer externality has the potential to be the future star in management fields. Since the cities and metros get more and more crowded, citizens or consumers more likely encounter unavoidable and unpleasant interactions with others. How to deal with this externality will be an important issue in the future.
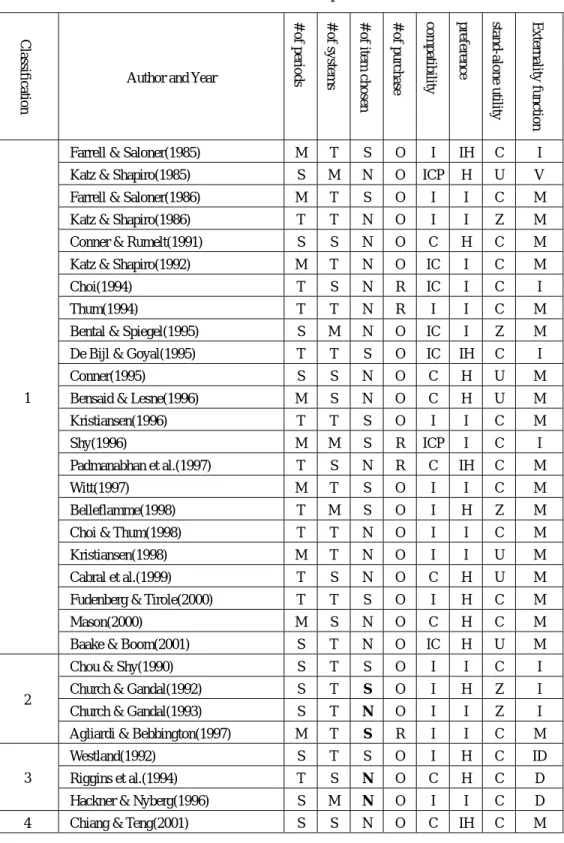
To sum up, we list the researches on consumption externality and compare their models in Table 2. Table 2 can help researchers find similar models in the literature and thus shows its value of existence.
TABLE 2:Researches on consumption externalities
Cla
ssifica
tion Author and Year
# of periods # of syste
m
s
# of item chosen # of pur
chase compa tibil ity preferen ce stand-alon e utility Extern ality fun ction
Farrell & Saloner(1985) M T S O I IH C I Katz & Shapiro(1985) S M N O ICP H U V Farrell & Saloner(1986) M T S O I I C M Katz & Shapiro(1986) T T N O I I Z M Conner & Rumelt(1991) S S N O C H C M Katz & Shapiro(1992) M T N O IC I C M
Choi(1994) T S N R IC I C I
Thum(1994) T T N R I I C M
Bental & Spiegel(1995) S M N O IC I Z M De Bijl & Goyal(1995) T T S O IC IH C I
Conner(1995) S S N O C H U M
Bensaid & Lesne(1996) M S N O C H U M
Kristiansen(1996) T T S O I I C M
Shy(1996) M M S R ICP I C I
Padmanabhan et al.(1997) T S N R C IH C M
Witt(1997) M T S O I I C M
Belleflamme(1998) T M S O I H Z M
Choi & Thum(1998) T T N O I I C M
Kristiansen(1998) M T N O I I U M
Cabral et al.(1999) T S N O C H U M Fudenberg & Tirole(2000) T T S O I H C M
Mason(2000) M S N O C H C M
1
Baake & Boom(2001) S T N O IC H U M Chou & Shy(1990) S T S O I I C I Church & Gandal(1992) S T S O I H Z I Church & Gandal(1993) S T N O I I Z I 2
Agliardi & Bebbington(1997) M T S R I I C M
Westland(1992) S T S O I H C ID
Riggins et al.(1994) T S N O C H C D 3
Hackner & Nyberg(1996) S M N O I I C D 4 Chiang & Teng(2001) S S N O C IH C M
Legends of Table 2:
Classification 1: Network externality Classification 2: Indirect network externality Classification 3: Congestion externality Classification 4: Cross-consumer externality
# of periods:S (single period), T (two periods) , M (multiple periods) # of systems:S (single system), T (two systems) , M (multiple systems)
# of item chosen:N (customers could choose none) , S (customers are forced to choose one)# of purchase:O (once-and-for-all purchase) , R (repeated purchase) compatibility:C (perfect compatibility), I (perfect incompatibility), IC (comparison between compatibility and incompatibility) , ICP (various degrees of compatibility) preference:I (identical preferences), H (heterogeneous preferences) , IH (comparison between identical and heterogeneous preferences) stand-alone utility:C (constant), U (uniformly-distributed) , Z (zero) externality function:I (increasing function), D (decreasing function), M (multiplier), V (concave function) and ID (increasing initially and decreasing later)
7. Research Opportunities
Based on the reviews and discussions above, we find that cross-consumer externality is still under-researched in managerial fields. In this section, we will highlight 10 research opportunities. By focus, these research opportunities are classified into 4 categories: targeting, diversification, innovation diffusion, and modifications of network externality.
7.1 Targeting
Let us start with the first category: targeting. Cross-consumer externality may contribute to targeting issue in the field of marketing however it is still severely under-studied. Such externality can dramatically change the traditional targeting thinking.
Does the presence of advertisements on a website affect browser’s utility or attitude toward the site? Will the advertisements increase or decrease browser’s utility or attitude toward the website? Will the forms of advertisements, such as pop-up windows, animations or simply banners, affect consumer’s cognitive or emotional responses to ads? Furthermore, what is the optimal amount of advertisements carried out on a website? These questions have been under researched.
Research Opportunity 1:What is the optimal amount of advertisements on a website?
The answers we suggest are as follows. Advertisements do lower browsers’ utility or attitude toward the website, such that the relationship is
mediated by the downloading time and the need for closing such advertisements in order to clearly see the links to content. The pop-up form windows may have better advertising effects but mostly damages browsers’ utility or attitude toward the website. The reason may be that pop-up windows do not automatically close by themselves. When advertisements show in more compulsive ways, the optimal effect of advertisements may be lower, and vice versa. Forcing browsers to see advertisements, though achieving better advertising effects, may drive them away from the website in the meantime.
Cross-consumer externality also challenges the targeting thinking in some servicing industries. In such industries, some consumers may engage in their favorite (but annoying-to-others) behavior such as smoking or making noises at other consumers’ expense. Should we adopt a policy to forbid or permit such behavior? Should we meet the preference of the majority of consumers? Should we partition our service area? How should we allocate the capacity into separate areas where different policies apply? These pose another research opportunity.
Research Opportunity 2:How should we deal with behaviors such as smoking?
Intuitive strategies such as “eliminating the cross-consumer externality” or “meeting the preference of the majority of consumers” may not guarantee the optimal payoff. The reason is that cross-consumer externality reduces some consumer’s utility, but in the mean time, increases other people’s consumer utility. If it is cheap to partition the facility to provide a space that is effectively free from externality, then partitioning the facility could be optimal and vice versa.
In addition to the policy on consumer behaviors, cross-consumer externality also reduces incentives to serve more consumers. Should we serve as many consumers as possible? Should we serve every consumer with as little service space as possible? Should we lower our price to attract more consumers to fill up the service capacity? This presents our third research opportunity.
Research Opportunity 3 : Should we serve as many consumers as possible?
The conventional wisdom urging us to serve as many consumers as possible may be incorrect when cross-consumer externality is at work. Serving more consumers may lower every consumer’s utility from the service as a result of crowded space and shared staff’s services. Thus, it may be better to set higher prices and serve fewer consumers when considering cross-consumer externality. We may reduce our number of seats to increase
the space shared by every patron. In doing so, we may charge every patron at a higher price in exchange for a more spacious seat to relax. As a result, a lower price will attract more consumers to fill up the service capacity, which may be less profitable in the context of cross-consumer externality. The above arguments in this paragraph may become more significant when consumers are more sensitive to other consumers’ annoying behavior.
In addition to cross-consumer externality, network externality plays an important role in targeting. The characteristic of increasing return urges firms to build a large installed base as soon as possible. Since the resources are usually limited in the short run, what kind of consumers should a firm target as its first priority? It has been an unsolved problem thus far but a promising opportunity to researchers.
Research Opportunity 4:What consumers should be targeted first in the context of network externality?
We suggest that the answers may be consumers who are message senders rather than message receivers. This is because message senders forward useful and interesting information to others in communication while message receivers passively receive the information. In theory, message senders offer others larger positive network utility than message receivers.
7.2 Diversification
We next propose research opportunities around the issue of diversification in the field of business strategy. Indirect network externality “has largely been ignored in the marketing science literature” (Gupta et al, 1999 : 396). We assert that indirect network externality is also under-researched in the field of business strategy, especially around the topic of diversification.
It is very important to create a strong core business. However, “when it becomes necessary for a business to expand its core, the best results are likely to be obtained by adjacency expansions, and reinforce the strength of the profitable core” (Beam, 2001:148). Amongst adjacent expansions, however, which one is most promising? Is it better to diversify into producing complementary goods? Although complementary goods may not be entirely adjacency expansions, should we diversify into non-adjacent but complementary goods or diversify into adjacent but non-complementary goods?
Research Opportunity 5 : Is it better to diversify into producing complementary goods?
Theoretically, it is better to diversify into complementary goods when indirect network externality is stronger. When indirect network externality is very strong, the advantage of diversifying into complementary but non-adjacent goods may exceed the advantage of diversifying into adjacent but non-complementary goods. The reason is that the control of complementary goods may reinforce the strength of the company in the markets characterized by indirect network externality. The power of market characteristics can outweigh the benefit of having experience in producing similar goods.
7.3 Innovation Diffusion
We go on to discuss research opportunities around the issue of innovation diffusion in the field of technology management. Comparing to cross-consumer externality and indirect network externality, network externality is a very important topic worth of further researches in the field of technology management.
Abrahamson & Rosenkopf (1993) propose that bandwagons could prompt most organizations to collectively adopt an innovation, even when most of them expect that this adoption could yield negative returns. Why does it happen? Can the phenomenon be explained by network externality? Will their conclusion be more significant when network externality is stronger?
Research Opportunity 6:Does network externality prompt organizations behave like a collective?
Their result can be rationalized by the property of network externality. Innovation with strong network externality may initially show a negative payoff, but result in grand positive returns when more participants adopt the innovation. The property offers incentives for firms to behave as a collective. That is, bandwagons can prompt most organizations to collectively adopt an innovation especially when the innovation carries strong network externality. We expect that their conclusion will be more significant when network externality is stronger.
It has been neglected hitherto that consumers can adopt more than one technology at the same time. When consumers adopts more than one technology, will competition between technologies intensify? Will the strength of network externality affect the answer of the question above?
Research Opportunity 7:Will the competition become less intense when consumers can buy from more than one firm?
may not be “choosing the better one” anymore. Consumers therefore buy the additional one when it is worth the price. Intuitively, the competition becomes less intense. The strength of network externality, however, makes the above argument more significant. When more consumers adopt a specific technology, the value to all adopters is higher. Thus, both technologies may easily become worthy to buy. The competition is, therefore, weakened.
7.4 Modifications of Network Externality
Finally, we submit research opportunities around modifications of network externality in the field of industrial organization. In addition to the field of technology management, network externality is also an important topic in the field of industrial organization. Several ways are proposed to modify the setting of network externality in order to more appropriately reflect the reality. First, Metcalfe’s Law (Gilder, 1993) asserted that network value is proportional to the square of network size. However, it is too strong to assume that network externality is anonymous. To be specific, not every stranger can provide positive value to a consumer. Thus, Hanson (2000) suggested that Metcalfe’s Law should be modified to reflect the value of communication between individuals.
Belleflamme (1998) suggested that network externality exists only locally. Now a question results. What difference does it make when network externality is anonymous or only exists locally?
Research Opportunity 8:What is the difference between anonymous externality and local interaction?
When network externality exists only locally, the network can be regarded as several small networks. As a result, the lock-in effect may take place only in a limited space. Moreover, the network value is dramatically lower when network externality exists only locally, compared to the network value when network externality is anonymous.
The second modified setting of network externality is to consider the strength of network externality. In practices, the value of communication among consumers may not behave in an exist-or-not manner. Communication with good friends provides more value to consumers than communication with nodding acquaintances. Accordingly, will a technology that enhances consumers’ affiliation diffuse more successfully than a technology without that property? Will consumers change to another system all together because of stronger affiliation ties after adopting the technology for a period of time?
technology diffusion?
If a technology can enhance consumers’ affiliation, its adopters will derive more value from the technology and become faithful supporters of that technology. We suppose such technology can diffuse more successfully than others without that property. Network externality builds the user base, however, it can destroy the user base with the same force. Consumers who are effectively tied together may have a collective behavior. They may support a specific technology if they are satisfied but they together may also abandon it if they are stranded by it.
Finally, consider the “finite attention” of consumers. Everyone has only limited time and energy to communicate. What is affected by considering “finite attention”?
Research Opportunity 10: What is different by considering “finite attention”?
The attention span imposes an upper limit to the value which network utility brings and thus imposes an upper limit to the overall network value. When users’ attention span is smaller, little lock-in effect takes place and the overall network value gets smaller.
We believe that research opportunities above should be further explored. Following the classification alone, we now can draw a clearer picture of various consumption externalities. Amongst all consumption externalities, network externality has been a hot topic for years and still shows the potential for future research. On the other hand, cross-consumer externality may be the future star in the field of marketing.
Empirical evidences in the literature on consumption externalities are less than works on theoretical advances. Empirical researches, however, play an important role both in the past and in the future. Empirical evidences (e.g. Gupta et al., 1999; Oren & Smith, 1981; Sembenelli & Vannoni, 2000) made substantial progresses in testing and developing theories on solid empirical grounds. It is fertile to empirically prove, falsify, or revise a variety of theories on consumption externalities.
Recent remarkable researches, in the field of industrial organization, show the research potential of externality. Sembenelli & Vannoni (2000) revealed that R&D and advertising are investments generating externalities, which can be efficiently exploited in adjacent industries. Carter & Wright (1999:1) unveiled that “network externalities allow the incumbent to use the terms of interconnection to maintain its dominant position”. Steen (2002:3) further showed “how vertical industry linkages may work as channels for externalities”. Farr, Tremblay & Tremblay (2001) had the conclusion that
“advertising restrictions benefit producers by limiting competition and generating higher industry profits”. Collectively those researches show the ongoing research stream on externalities.
References
Abrahamson, E., L. Rosenkopf 1993. Institutional and competitive bandwagons: Using mathematical modeling as a tool to explore innovation diffusion. Academy of Management Review, 18 (3):487-517. Agliardi, E., & M. S. Bebbington 1997. Self-reinforcing mechanisms and
market information. European Journal of Operational Research, 96 (3): 444-454.
Baake, P., & A. Boom 2001. Vertical product differentiation, network externalities, and compatibility decisions. International Journal of Industrial Organization, 19 (1,2):267-284.
Beam, H. H. 2001. Profit from the core: Growth strategy in an era of turbulence. Academy of Management Executive, 15 (3):147-149.
Belleflamme, P. 1998. Adoption of network technologies in oligopolies. International Journal of Industrial Organization, 16 (4):415-444.
Bensaid, B., & J.-P. Lesne 1996. Dynamic monopoly pricing with network externalities. International Journal of Industrial Organization, 14 (6): 837-855.
Bental, B., & M. Spiegel 1995. Network competition, product quality, and market coverage in the presence of network externalities. Journal of Industrial Economics, 43 (2):197-208.
Cabral, L. M. B., D. J. Salant, & G. A. Woroch 1999. Monopoly pricing with network externalities. International Journal of Industrial Organization, 17 (2):199-214.
Carter, M., & J. Wright 1999. Interconnection in network industries. Review of Industrial Organization, 14 (1):1-25.
Chiang, D. M., & D. C. Teng 2001. Pricing strategies with network externalities between two groups of customers. NTU Management Review, 12 (1):1-36.
Chiang, D. M., & D. C. Teng 2003. Installed base collapsing strategies with network externality. Journal of Management, 20 (5):829-857..
Choi, J. P. 1994. Network externalities, compatibility choice, and planned obsolescence. Journal of Industrial Economics. 42 (2):167-182.
Choi, J. P., & M. Thum 1998. Market structure and the timing of technology adoption with network externalities. European Economic Review, 42
(2):225-244.
Chou, C.-F., & O. Shy 1990. Network effects without network externalities. International Journal of Industrial Organization, 8 (2):259-270.
Church, J., & N. Gandal 1992. Network effects, software provision, and standardization. Journal of Industrial Economics, 40 (1):85-103.
Church, J., & N. Gandal 1993. Complementary network externalities and technological adoption. International Journal of Industrial Organization, 11 (2):239-260.
Conner, K. R., & R. P. Rumelt 1991. Software piracy: An analysis of protection strategies. Management Science, 37 (2):125-139.
Conner, K. R. 1995. Obtaining strategic advantage from being imitated: When can encouraging “clones” pay? Management Science, 41 (2): 209-225.
David, P. A. 1985. Clio and the economics of QWERTY. American Economic Review, 41 (4):332-337.
De Bijl, P. W. J., & S. Goyal 1995. Technological change in markets with network externalities. International Journal of Industrial Organization, 13 (3):307-325.
Economides, N. 1996. The economics of networks. International Journal of Industrial Organization, 14 (6):673-699.
Farr, S., & C. H. Tremblay, & V. J. Tremblay 2001. The welfare effect of advertising restrictions in the U.S. cigarette industry. Review of Industrial Organization, 18 (2):147-160.
Farrell, J., & G. Saloner 1985. Standardization, compatibility, and innovation. Rand Journal of Economics, 16:70-83.
Farrell, J., & G. Saloner 1986. Installed base and compatibility: Innovation, product pre-announcements, and predation. American Economic Review, 76:940-955.
Fudenberg, D., & J. Tirole 2000. Pricing a network good to deter entry. Journal of Industrial Economics, 48 (4):373-390.
Gilder, G. 1993. Metcalfe’s law and legacy. Forbes ASAP, Sept 13th.
Gupta, S., D. C. Jain, & M. S. Sawhney 1999. Modeling the evolution of markets with indirect network externalities: An application to digital television. Marketing Science, 18 (3):396-416.
Ha, A. Y. 1998. Incentive-compatible pricing for a service facility with joint production and congestion externalities. Management Science, 44 (12), p1:1623-1636.
Hackner, J., & S. Nyberg 1996. Vanity and congestion: A study of reciprocal externalities. Economica, 63 (249):97-111.
Hanson, W. 2000. Principles of Internet Marketing. Cincinnati. South Western College Publishing.
Hellofs, L. L., & R. Jocobson 1999. Market share and customers’ perceptions of quality: When can firms grow their way to higher versus lower quality? Journal of Marketing, 63 (1):16-25.
Helpman, E. 1982. Increasing returns, imperfect markets, and trade theory. in A. W. Jones and P. B. Kenen, ed., Handbook of International Economics. Amsterdam. North-Holland.
Hill, C. W. L. 1997. Establishing a standard:Competitive strategy and technological standards in winner-take-all industries. Academy of Management Executive, 11 (2):7-25.
Holcombe, R. G. and R. S. Sobel 2000. Consumption externalities and economic welfare. Eastern Economic Journal, 26 (2):157-170.
Katz, E., & U. Spiegel 1996. Negative intergroup externalities and market demand. Economica, 63 (251):513-520.
Katz, M. L., & C. Shapiro 1985. Network externalities, competition, and compatibility. American Economic Review, 75:424-440.
Katz, M. L., & C. Shapiro 1986. Technology adoption in the presence of network externalities. Journal of Political Economy, 94:822-841.
Katz, M. L., & C. Shapiro 1992. Product introduction with network externalities. Journal of Industrial Economics, 40 (1):55-83.
Kristiansen, E. G. 1996. R&D in markets with network externalities. International Journal of Industrial Organization, 14 (6):769-784.
Kristiansen, E. G. 1998. R&D in the presence of network externalities: Timing and compatibility. Rand Journal of Economics, 29 (3):531-547. Le Nagard-Assayag, E., & D. Manceau 2001. Modeling the impact of product preannouncements in the context of indirect network externalities. International Journal of Research in Marketing, 18 (3):203-219.
Liebowitz, S. J., & S. E. Margolis 1990. The fable of the keys. Journal of Law and Economics, 33 (1):1-25.
Mason, R. 2000. Network externalities and the Coase conjecture. European Economic Review, 44 (10):1981-1992.
Oren, S. S., & S. A. Smith 1981. Critical mass and tariff structure in electronic communications markets. Bell Journal of Economics, 12 (Autumn):467-487.
Oren, S. S., S. A. Smith, & R. Wilson 1982. Nonlinear pricing in markets with interdependent demand. Marketing Science, 1:287-313.
and new releases: A rationale for sequential product introduction. Journal of Marketing Research, 34 (4):456-472.
Riggins, F. J., C. H. Kriebel, & T. Mukhopadhyay 1994. The growth of interorganizational systems in the presence of network externalities. Management Science, 40 (8):984-998.
Safferstone, M. J. 1999. Book review: Information rules: A strategic guide to the network economy. Academy of Management Executive, 13 (1): 117-118.
Schilling, M. A. 2002. Technology success and failure in winner-take-all markets: The impact of learning orientation, timing, and network externality. Academy of Management Journal, 45 (2):387-398.
Sembenelli, A., & D. Vannoni 2000. Why do established firms enter some industries and exit others? Empirical evidence on Italian business groups. Review of Industrial Organization, 17 (4):441-456.
Shapiro, C., & H. R. Varian 1999a. Information Rules: A Strategic Guide to the Network Economy. Boston. HBS Press.
Shapiro, C., & H. R. Varian 1999b. The art of standard wars. California Management Review, 41 (2):8-32.
Shaw, M. J. 2000. Book review: Information rules: A strategic guide to the network economy. Academy of Management Review, 25 (2):441-443. Shy, O. 1996. Technology revolutions in the presence of network externalities.
International Journal of Industrial Organization, 14 (6):785-800.
Steen, F. 2002. Vertical industry linkages: Sources of productivity gains and cumulative causation? Review of Industrial Organization, 21 (1):3-20. Stenbacka, R. & M. M. Tombak 1995. Time-based competition and the
privatization of services. Journal of Industrial Economics, 43 (4): 435-454.
Thum, M. 1994. Network externalities, technological progress, and the competition of market contracts. International Journal of Industrial Organization, 12 (2):269-289.
Westland, J. C. 1992. Congestion and network externalities in the short run pricing of information system services. Management Science, 38 (7): 992-1009.
Witt, U. 1997. "Lock-in" vs. "critical masses" -- industrial change under network externalities. International Journal of Industrial Organization, 15 (6):753-773.
Xie, J., & M. Sirbu 1995. Price competition and compatibility in the presence of positive demand externalities. Management Science, 41 (5):909-926.
The authors would like to thank the National Science Council of the Republic of China, Taiwan for financially supporting this research under Contract No. NSC-92-2416-H-182-007
Correspondence and reprint requests should be made to Ching-i Teng