Design And Performance Evaluation Of A Non-Preemptive Priority Based Access Control Scheme For IEEE 802.11 DCF Access Method
全文
(2) adaptive bandwidth management strategy not only dynamically expand and contract the contention window size according to the current load but also separate admitted inactivated real-time traffic from newly requesting access traffic and data traffic to maintain an efficient bandwidth utilization and guarantee a minimum bandwidth for data traffic. The proposed scheme is performed at each station in a distributed manner, and it can be implemented in the present IEEE 802.11 standard with relatively minor modifications. Performance for integrated traffic is examined in detail. The results show good performance improvements over the original DCF protocol. The remainder of this paper is organized as follows. In Section 2, we explain some terminology in IEEE 802.11 standard and the CSMA/CA protocol on which our proposed scheme is based. Section 3 describes the proposed scheme in detail. Simulation and its results are shown in Section 4. Section 5 concludes this paper. 2. PRELIMINARIES The IEEE 802.11 standard considers two network topologies: ad hoc and infrastructure-based. In an ad hoc configuration, the mobile terminals communicate with each other in an independent basic service set (BSS) without connectivity to the wired backbone network. In an infrastructure network, mobile terminals communicate with the backbone network through an access point (AP). The AP is a bridge supporting range extension by providing the integration points necessary for network connectivity between multiple BSSs, thus forming an extended service set (ESS). The fundamental access method of the IEEE 802.11 MAC protocol for ad hoc networks is the distributed coordination function (DCF), also known as carrier sense multiple access with collision avoidance (CSMA/CA). CSMA/CA works by a “listen before talk” scheme. In brief, to transmit a station must sense the medium to determine if another station is transmitting and must ensure that the medium is idle for the specified distributed coordination function interframe space (DIFS) duration before transmitting. Three interframe space (IFS) intervals are specified in the IEEE 802.11 standard: short IFS (SIFS), PCF-IFS (PIFS), and DCF-IFS (DIFS). The SIFS interval is the smallest IFS, followed by PIFS and DIFS respectively. As a result, PCF traffic has high priority over DCF traffic. Control frames, which wait SIFS before transmission, have the highest-priority access to the communication media. The CSMA/CA protocol allows for options that can minimize the amount of bandwidth wasted when collision occurs by using request to send (RTS), clear-to-send (CTS), data and acknowledge (ACK) transmission frames in a sequential fashion. Communications is established when one of the wireless nodes sends a short message RTS frame. The message duration, NAV, alerts all others in the medium to back off for the duration of the transmission. The receiving station issues a CTS frame which echoes the senders address and the NAV. If the CTS frame is not received, it is assumed that a collision occurred and the. RTS process starts over. After the data frame is received, an ACK frame is sent back verifying a successful data transmission. A common limitation with wireless LAN systems is the "Hidden Terminal" problem [11]. This can disrupt 40% or more of the communications in a highly loaded LAN environment [12]. It occurs when there is a station in a service set that cannot detect the transmission of another station to detect that the media is busy. The use of RTS, CTS, Data and ACK sequences can also help the prevention of the disruptions caused by this problem. Despite these precautions, collision can still occur. The collision avoidance portion of CSMA/CA is performed by a random backoff procedure. If a station with a frame to transmit initially senses the channel to be busy; then the station waits until the channel become idle for DIFS period, and then computes a random backoff time to wait before sensing again to verify a clear channel on which to transmit. If the channel becomes busy before time out, the station freezes its timer. This process is repeated until the waiting time approaches zero and the station is allowed to transmit. The idle period after a DIFS period is referred to as the contention window (CW). For more information about IEEE 802.11 standard, see [2] and [13-15]. 3. THE PROPOSED NON-PREEMPTIVE PRIORITY BASED ACCESS CONTROL SCHEME In this section, we delineate the proposed scheme in detail. The proposed scheme is simple, efficient, flexible, scalable, and also easy to implement in comparison to PCF (The PCF protocol is extremely complex and has substantial delay at low load, i.e., stations must always wait for the polling, even in an otherwise idle system). Our method can be divided into three parts: enforcing priorities for DCF access, the adaptive contention window mechanism, and the adaptive bandwidth management strategy. 3.1 Enforcing Priorities for DCF Access In WLANs, the medium access control (MAC) protocol is the key component that provides the efficiency in sharing the common radio channel among various multimedia traffic, each requiring different QoS performance; thus, imposing the necessity of priorization. In this section, we proposed a novel method to modify the CSMA/CA protocol such that station’s multi-levels priorities can be supported along with the real time applications in an ad hoc network. As mentioned earlier, the collision avoidance portion of CSMA/CA is performed through a random backoff procedure. The random backoff time is an integer value that corresponds to a number of time slots. Initially, a station computes a back-off time in the range 0-7. If a station with a frame to transmit initially senses the channel to be busy, it waits until the channel becomes idle, and then, the station decrements its backoff timer until the medium becomes busy again or the timer reaches zero. If the timer has not reached zero and the medium becomes busy, the station freezes its timer. When the timer finally decrements to zero, the station transmits its frame. If two or more stations decrement to zero at the same time, a collision will.
(3) occur, and each station will have to generate a new backoff time in the range 0-15. For each retransmission attempt, the. . 2 +i. . backoff time grows as ranf () ⋅ 2 •Slot_Time, where i is the number of consecutive times a station attempts to send a frame, ranf() is a uniform variate in (0,1), and x represents the largest integer less than or equal to x . For more information about CSMA/CA protocol, see [2]. The basic idea of this method is that priority access to the wireless medium is controlled through different backoff time. The shorter backoff time a mobile waits, the higher priority this mobile will get. Therefore, we first change the. 2 2 +i backoff time generation function to ranf () ⋅ for 2 2 2 +i 2 2+i high priority mobiles and + ranf () ⋅ for 2 2 . low priority mobiles. This technique divides the random backoff time into two parts: 0 ~. 2 2+i 2 2+i -1 and ~ 2 2. 2 2+i -1. The high priority mobiles use the former and the. low priority mobiles use the latter. For example, initially, the high priority mobiles generate a backoff time in the range 0-3, and the low priority mobiles generate a backoff time in the range 4-7. Thus, the former will have higher priority in contending the channel. Then, to support multiple-level priorities, the backoff time generation function is changed to. ranf () • 21+i + k • 21+i ,. where k is the level of priority. The lower k a mobile has, the higher priority this mobile will get. Consecutive time (i). 1st. 2nd. 3rd. 4th. Admitted voice traffic ( 0, 1, 1 ). 0-3. 0-7. 0-15. 0-31. Admitted video traffic ( 1, 1, 1 ). 4-7. 8-15. 16-31. 32-63. New quest/Data traffic ( 2, 2, 1 ). 8-15. 16-31. 32-63. 64-127. Backoff slot numbers Types of requests (k, m, n). Figure 1. Examples of backoff time of individual traffic.. However, for fixed backoff range, the probability of collisions in the same priority level will increase if the number of contended mobiles with the same priority increases. In other words, this scheme should have the ability to expand or contract the backoff range arbitrarily. That is, we allow different backoff ranges for different priority levels in this scheme. To this end, we change the backoff time generating function to. ranf () • 2 m+i + k • 2 n+i , where. k is the level of priority, and m and n are the parameters used to decide the number of slots in individual priority levels and the number of slots between each priority levels respectively. In this paper, the admitted voice traffic have the highest priority among all other requests, and the second priority. class is admitted activated/inactivated video traffic. The new requests and data traffic will have the lowest priority level, as an example shown in Fig. 1. Note that we give wider range to the lowest priority level since there is more traffic that contends in this priority level. It is also noteworthy that when a mobile decrements its backoff timer and the medium becomes busy, the mobile freezes its timer. This means that a mobile will raise its priority automatically after several times of transmission failure. Hence, starvation will not occur in this method. 3.2 The Adaptive Contention Window Mechanism The collision avoidance portion of CSMA/CA is performed by a variable time-spreading of the users’ access. However, collisions still occur if two or more stations select the same backoff slot, then these stations have to reenter the competition with an exponentially increasing CW parameter value, and the increase of the CW parameter value after collisions is the reaction that the CSMA/CA provides to make the access mechanism adaptive to channel conditions. This strategy avoids long access delays when the load is light because it selects an initial (small) parameter value of CW by assuming a low level of congestion in the system. However, it causes a high collision probability and channel utilization is degraded in bursty arrival or congested scenarios. In other words, this strategy might allocate initial size of CW, only to find out later that it is not enough when the load increased. The size of CW must be reallocated with a larger size, but each increase of the CW parameter value is obtained paying the cost of a collision (bandwidth wastage). Besides, after a successful transmission, the size of CW is set again to the minimum value without maintaining any knowledge of the current channel status. There has been several works reported in the literature about the enhancement of the IEEE 802.11 DCF protocol to increase its performance when it is utilized in WLANs [16-20]. Most of them were on the simulation study. Some studies try to approximate the knowledge about the number of users involved in the access by exploiting the history of the system. However, it is worth observing how this investigation could result expensive, difficult to obtain and subject to significant errors, especially in high contention situations [20]. In the previous section we mentioned that our scheme has the ability to expand or contract the backoff range arbitrarily by changing the parameters k, m and n. In this section, we propose an adaptive contention window mechanism for IEEE 802.11 DCF protocol to dynamically expand and contract the contention window size according to the current load and achieve the theoretical capacity limits. Our scheme is based on the results of the capacity analysis model of IEEE 802.11 protocol originally proposed by L. Bononi et al. in [19-20], and we also use the concept introduced in [20-21]. The proposed scheme is simple and efficient, and it does not suffer from the problem of harmful fluctuation occurred in [18]. In addition, the proposed scheme is based only on carrier sensing and can be implemented in the present IEEE 802.11 standard without requiring any complicated computation or additional hardware support..
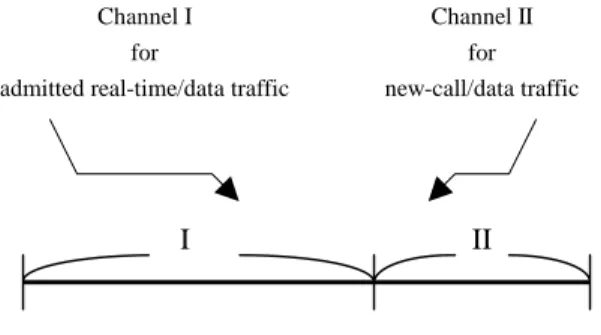
(4) In order to exploit the early and meaningful information about the actual state of congestion of the channel, we start by defining the utilization factor α of a contention window to be the number of busy slots, sb , observed in m+i the latest 2 slots divided by the size (number of slots) m+i of the current contention window ( 2 ). For the use we considered to make with, the value of α has to be updated in every backoff interval to reflect the actual state of the channel. It is intuitive to observe that the value of utilization factor, α , provides a lower bound to the actual number of stations trying to access the channel during the last contention window because some stations may transmit in the same slot. However, in order to maximum the utilization of every slot in a contention window, we still need to engineer the tight upper bound of α to help us to complete this scheme. Assume there are M stations working in asymptotic conditions in this system. The stations transmit frames whose size are i.i.d. (independent and identically distributed) sampled from a geometric distribution with parameter q . Specifically, the size of a frame is an integer multiple of the slot size, t slot , and hence the mean frame space is. t slot . To simplify the analysis, we assumed a 1− q. geometrically distributed backoff instead of the uniform sampled backoff of IEEE 802.11. That is to say, at the beginning of an empty slot a station starts the transmission of a frame with probability p , and defers the transmission with probability 1 − p . Hence , the average size of contention window is. 1+. 2 . p. ρ. below. 1 ( M ⋅ popt ) . However, such a common heuristic 2. would conduct the size of contention window to fluctuate rapidly between expansion and contraction. To avoid this behavior, we can improve upon this strategy by allowing the utilization factor of contention window to drop below. Let t f , tv and t s denote, respectively, the average frame transmission time, the average temporal distance between two consecutive successful transmission, also referred to as the average virtual transmission time, and the average time required for a successful transmission. Hence, the protocol capacity ,. the analytical model presented above. Consequently, M ⋅ popt can be used as a measure of the network contention level when the network utilizes the optimal contention window size corresponding to the ongoing network and traffic configuration. In other words, if the utilization factor, α , is bounded above by the constant, M ⋅ popt , the system will be kept in a better situation from the viewpoint of channel utilization since the lower rate of collisions will result in a significant increase in throughput and decrease in mean access delay. Thus, when the utilization factor, α , exceeds the value of M ⋅ popt , we can expand the contention window by allocating more slots than the old contention window had. On the other hand, it is also desirable to contract the contention window when the utilization factor becomes too small, so that the wasted bandwidth is not exorbitant. A natural strategy for expansion and contraction is to allocate a new contention window size that has twice as many slots as the old one by increasing the value of m when the utilization factor exceeds the value of M ⋅ popt , and halve the size of contention window when the utilization factor becomes less than half of M ⋅ popt by decreasing the value of m . This strategy guarantees that the utilization factor of the contention window never drops. , is. tf . Also, from the tv. geometric backoff assumption, all the processes which define the occupancy pattern of the channel are regenerative with respect to the sequence of time instants corresponding to the completion of a successful transmission. Therefore, we can analytically investigate the value of the p parameter that minimizes tv , named the optimal p value, popt . In other words, popt is the p value that maximizes the protocol capacity, ρ . In [19], it is shown that popt is closely approximated by the p value that guarantees a balance, in a virtual transmission time, between collision and idle periods. Furthermore, results presented in [20] indicate that, if the stations utilize the optimal p value, i.e., popt , the collision probability is low. Hence, it reveals that M ⋅ popt is a tight upper bound of α in a system operating with the optimal channel utilization level. It is worth nothing that popt is highly affected by the M value, however, by fixing a given value for the frame size parameter q , the value of M ⋅ popt is almost constant [20], and can be computed off-line by exploiting. 1 ( M ⋅ popt ) . Specifically, we continue to double the size 2 of contention window when the utilization factor exceeds M ⋅ popt , but we halve the size of contention window when the utilization factor becomes less than. 1 1 ( M ⋅ popt ) , rather than ( M ⋅ popt ) as before. That 4 2 is , the utilization factor is therefore bounded below by. 1 ( M ⋅ popt ) . Please note that the parameters, m and 4 n , of other traffic should be adjusted at the same time while changing the value of m . 3.3 The Adaptive Bandwidth Management Strategy In section 3.1, we have mentioned that starvation will not occur in this method since a mobile will raise its priority automatically after several times of transmission failure. However, we still need guarantee a minimum bandwidth for data traffic to maintain a reasonable bandwidth usage. In this section, we propose an adaptive bandwidth management strategy. Our strategy not only tries to maximize the bandwidth utilization but also guarantee a minimum bandwidth for data traffic. In addition, this strategy is very simple and easy to implement without any extra computation. As shown in Fig. 2, the total bandwidth is divided into two parts: channel I and channel II. We allocate channel I to real-time/data traffic and channel II to new-call/data call traffic. Beside, we allow admitted real-time traffic to use.
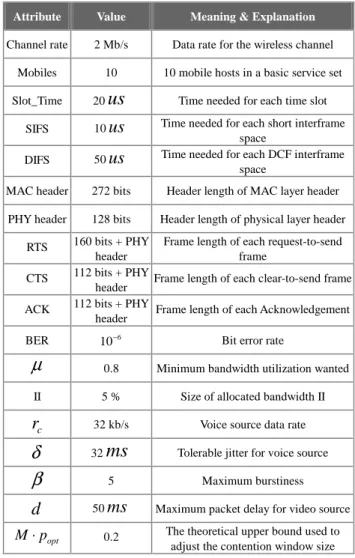
(5) bandwidth exclusively with preemptive priority over data traffic in channel I to let the real-time traffic has a larger share of pie, and data traffic sometimes has precedence for using network resources than new-call traffic in channel II to guarantee a minimum bandwidth for data traffic. The algorithm to manage the bandwidth is summarized in the following. Channel I for admitted real-time/data traffic. I. Channel II for new-call/data traffic. II. Figure 2. Proposed bandwidth partition.. Function Adaptive_Bandwidth_Management IF monitored bandwidth of data traffic < size of allocated bandwidth II THEN IF bandwidth utilization < µ THEN. nnew _ call = ndata. ELSE. nnew _ call = ndata + 1. As the pseudo-code illustrates, the monitored bandwidth of data traffic and bandwidth utilization are the measures used to manage the bandwidth. If the monitored bandwidth of data traffic becomes less than the size of allocated bandwidth II, and the bandwidth utilization is not good enough (less than the threshold value µ ), it implies that there is not so much real-time traffic. Hence, we let the new-call traffic has the same priority with data traffic by keeping the value of parameters of new-call traffic as the same as data traffic. Otherwise, we guarantee a minimum bandwidth for data traffic by delaying the new-call traffic in high load. Please note that we can also guarantee a proper bandwidth for voice/video traffic in the same way. This algorithm can be run periodically. 4. SIMULATIONS AND PERFORMANCE EVALUATION In this section, we evaluate the performance of the proposed scheme. 4.1 Simulation Model The simulation models are built using the Simscript tool [22]. The model represents an ad hoc network, where all stations in the BSS (Basic Service Set) are capable of directly communicating with all other stations in the BSS. Several assumptions have been made to reduce the complexity of the model. First, the “hidden terminal” and “exposed terminal” problems [11] are not addressed in the simulation model. Second, no mobiles operate in the “power-saving” mode. Third, no interference is considered from nearby BSSs. Finally, the probability that the frame is transmitted successfully is calculated as: p r {success} =. (1 − BER ) n , where n is the number of bits transmitted in the frame and BER denotes bit error rate. Three types of traffic are considered in the simulation. 1. Pure data The arrival of data frames from a mobile’s higher-layer to MAC sublayer is Possion. Frame length is assumed to be exponentially distributed with mean length 1024 octets. 2. Voice traffic Voice stream is characterize by two parameters ( γ c , δ ), where γ c is the rate of the source and δ is the maximum tolerable jitter (packet delay variation) for this stream. Frames of voice traffic that are not successfully transmitted within its maximum jitter constraint is assumed to be lost. The voice stream is modeled as an two state Markov on/off process, where stations are either transmitting (on) or listening (off). The amount of time in the off or on state is exponentially distributed, where the mean value of the silence (off) period is 1.5 s, and the mean value of the talk spurt (on) period is 1.35 s. Each connection duration is exponentially distributed with mean time 3 minutes. 3. Video traffic Video stream is characterized by three parameters ( rv , β , d ), where rv is the average rate of the source, β is the maximum burstiness of the source, and d is the maximum tolerable delay (packet transfer delay) for this stream. We use a Source Model in [23]. The bit rate of a single source for the nth frame, λ (n ) , is defined by the recursive relation: λ (n ) = aλ ( n − 1) + bw( n ) [bit/pixel], where a =0.8781, b =0.1108, and w(n ) is a sequence of independent Gaussian random variables which have mean 0.572 and variance 1. Like voice frames, video frames that are not successfully transmitted within its maximum tolerable delay, d , is assumed to be lost. Assume video, voice and data are mixed in the ratio of 1:1:1. Performance is measured in terms of average access delay, loss probability, bandwidth utilization, etc. The default values used in the simulation are listed in Table 1. The values for the simulation parameters are chosen carefully in order to closely represent the realistic scenarios as well as make the simulation feasible and reasonable. 4.2 Simulation Results We compare the proposed scheme with the conventional IEEE 802.11 DCF protocol, and the simulation results are shown below in the form of plots. Figure 3 and 4 show the value of utilization factor, α , and the collision probability versus the offered load for the proposed scheme and conventional DCF protocol. As shown in the figure, we can see that the value of utilization factor of conventional DCF protocol increase steadily as the load increases, and generally greater than the values of proposed scheme. On the other hand, the collision probability of the conventional DCF protocol degrades severely when the offered load become larger than 0.5 in contrast to the smoothness of the proposed scheme. Understandably, the decrease of the collision probability is achieved by our adaptive contention window mechanism. Since the value of utilization factor is bounded below by a constant. The collision probability will.
(6) be kept under the threshold.. 0.16 0.14. Attribute. Value. Meaning & Explanation. Channel rate. 2 Mb/s. Data rate for the wireless channel. Mobiles. 10. 10 mobile hosts in a basic service set. Slot_Time. 20. us. Time needed for each time slot. 0.12 0.1 0.08 0.06 0.04 0.02 0. Time needed for each short interframe space Time needed for each DCF interframe space. 10 us. SIFS. Collision Probability. Table 1. Default attribute values used in the simulation.. DIFS. 50 us. MAC header. 272 bits. Header length of MAC layer header. PHY header. 128 bits. Header length of physical layer header. 0. 0.1. 0.2. 0.3. 0.4. 0.5. 0.6. 0.7. 0.8. 0.9. 1. Offered Load Proposed scheme. Conventional-DCF. Figure 4. The collision probability versus offered traffic. 20. ACK BER. 10 −6. Bit error rate. µ. 0.8. Minimum bandwidth utilization wanted. II. 5%. Size of allocated bandwidth II. rc. 32 kb/s. δ β. 32. 18. Average access delay [ms]. CTS. 160 bits + PHY Frame length of each request-to-send header frame 112 bits + PHY Frame length of each clear-to-send frame header 112 bits + PHY Frame length of each Acknowledgement header. 16 14 12 10 8 6 4 2 0 0. 0.1. 0.2. 0.3. 0.4. 0.5. Voice source data rate. Proposed scheme. ms. 0.6. 0.7. 0.8. 0.9. 1. Offered Load Conventional-DCF. Tolerable jitter for voice source. Figure 5. Average access delay of voice traffic. 5. Maximum burstiness. d. 50 ms. Maximum packet delay for video source. M ⋅ popt. 0.2. The theoretical upper bound used to adjust the contention window size. 20. Figures 5 and 6 show average access delay of voice and video traffic respectively. Note that the average access delay of the proposed scheme remains low when the offered load is high, but the conventional DCF protocol shows sharp rise as the load increases. For voice and video −2 traffic, the allowable loss probability is about 10 [24] −3 and 10 [25] respectively. With this criterion, the proposed scheme can tolerate an offered load of 0.9. The simulation results indicate that the proposed scheme can be used to transmit high priority real-time applications such as voice and video traffic.. 18. Average access delay [ms]. RTS. 14 12 10 8 6 4 2 0 0. 0.1. 0.2. 0.3. 0.4. 0.5. 0.6. 0.7. 0.8. 0.9. 1. Offered Load Proposed scheme. Conventional-DCF. Figure 6. Average access delay of video traffic.. 120. 0.4. Average access delay [ms]. 0.35 0.3. Utilization factor. 16. 0.25 0.2 0.15 0.1. 100 80 60 40 20. 0.05 0. 0 0. 0.1. 0.2. 0.3. 0.4. 0.5. 0.6. 0.7. 0.8. 0.9. 1. Offered Load Proposed scheme. Conventional-DCF. Figure 3. The value of utilization factor versus offered traffic.. 0. 0.1. 0.2. 0.3. 0.4. 0.5. 0.6. 0.7. 0.8. 0.9. 1. Offered Load Proposed scheme. Conventional-DCF. Figure 7. Average access delay of data traffics..
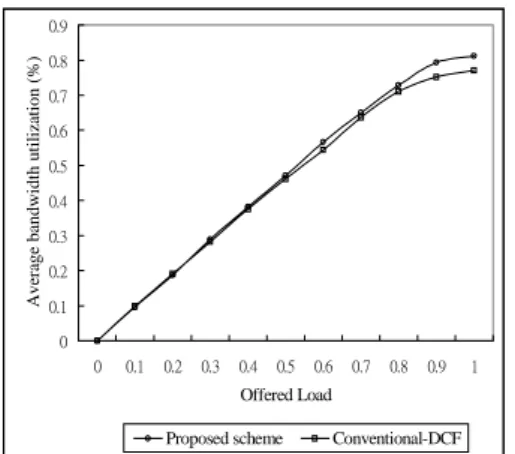
(7) Figure 7 shows the average access delay of data traffic under multimedia traffic condition. As expected, the average access delay of data traffic in the proposed scheme is worse than the conventional DCF protocol since it is of low priority. However, the lower priority traffic can have the bandwidth it needs in light load, so it is not wasted. Besides, we still might guarantee a minimum bandwidth for data traffic to maintain a reasonable bandwidth usage by using the function of adaptive bandwidth management in section 3.3.. [2]. [3]. [4] Average bandwidth utilization (%). 0.9 0.8 0.7 0.6. [5]. 0.5 0.4 0.3 0.2. [6]. 0.1 0 0. 0.1. 0.2. 0.3. 0.4. 0.5. 0.6. 0.7. 0.8. 0.9. 1. Offered Load Proposed scheme. Conventional-DCF. Figure 8. Average bandwidth utilization.. Figure 8 presents the average bandwidth utilization as a function of the offered load. Average bandwidth utilization is the percentage of the bandwidth actually being used in the total bandwidth. As illustrated in Fig. 8, the average bandwidth utilization is higher for the proposed scheme in a highly loaded system. It reveals a better performance for our proposed scheme under heavy load because the lower rate of collision probability results in a significant increase in throughput and decrease in mean access delay.. [7]. [8]. [9]. 5. CONCLUSIONS The design of priority-sensitive network protocols continues to be an important problem, and broadband wireless links constitute a subclass where prioritization is key to optimizing overall performance. In this paper, we proposed a pragmatic non-preemptive priority based access control scheme built on well-know protocols and offered easily implemented and yet flexible criteria for traffic prioritization in a wireless environment. We also demonstrate the performance in a quantitative way. The new generation wireless technologies should support universal wide-band access to a variety of services such as cordless telephony, Internet access, multimedia conference, remote audio, and flexible positioning of audio system. This means that various QoS requirements are needed in the future. Thus, multilevel priorities, bandwidth allocation, connection admission control, and traffic policing all need to be considered together to satisfy various QoS flows in the future networks.. [10]. [11] [12]. [13]. [14] [15]. [16]. 6. REFERENCES [1]. ETSI TC-RES, "Radio Equipment and Systems (RES); High Performance Radio Local Area Network. [17]. (HIPERLAN); Functional Specification," ETSI, 06921 Sophia Antipolis Cedex , France, draft prETS 300 652, July 1995. Wireless Medium Access Control and Physical Layer WG, IEEE Draft Standard P802.11, "Wireless LAN," IEEE Stds. Dept, D3, Jan. 1996 Marc Chelouche, Serge Hethuin, and Louis Ramel, "Digital Wireless Broadband Corporate and Private Network: RENT Concepts and Applications," IEEE Commun. Mag., vol. 35, no. 1, pp. 42-51, Jan. 1997. K. Y. Eng, M. J. Karol, M. Veeraraghavan, E. Ayanoglu, C. B. Woodworth, P. Pancha, and R. A. Valenzuela, "BAHAMA: A Broadband Ad-Hoc Wireless ATM Local-Area Network", Conference Record of ICC’95, pp. 1216-1223. Yu Wang and Brahim Bensaou, “Priority Based Multiple Access for Service Differentiation in Wireless Ad-Hoc Networks,” Conference Record of MWCN 2000, pp. 14-30. P. H. Chuang, H. K. Wu, and M. K. Liao, ”Dynamic QoS Allocation for Multimedia Ad Hoc Wireless Networks,” Conference Record of Computer Communications and Networks, pp. 480-485, October 1999. J. L. Sobrinho and A. S. Krishnakumar, “Quality-of-Service in Ad Hoc Carrier Sense Multiple Access Wireless Networks,” IEEE Journal on Selected Areas of Communications, vol. 17, no. 8, pp. 1353-1368, August 1999. J. L. Sobrinho and A. S. Krishnakumar, "Distributed multiple access procedures to provide voice communications over IEEE 802.11 wireless networks," Conference Record of GLOBECOM’96, pp.1689-1694. D. J. Deng and R. S. Chang, “A Priority Scheme for IEEE 802.11 DCF Access Method,” IEICE Trans. Commun., vol. E82-B, no. 1, January 1999, pp. 96-102. C. R. Lin, “Multimedia Transport in Multihop Wireless Networks,” IEE Proc. Commun., vol. 145, no. 5, pp. 342-345, October 1998. Andrew S. Tanenbaum, Computer Networks, 3rd ed., Prentice Hall, pp. 263-264, 1996. The Wireless LAN Alliance, “The IEEE 802.11 Wireless LAN Standard,” http://www.wlana.com/intro/standard/index.html. R.O. LaMaire et al., "Wireless LANs and Mobile Networking: Standards and Future Directions," IEEE Commun. Mag., vol. 34, no. 8, pp. 86-94, Aug. 1996. Rifaat A. Dayem, Moble Data and Wireless LANs Technology, Prentice Hall, pp. 190-201, 1997. Brian P. Crow, Indra Widjaja, Jeong Geun Kim, and Prescott T. Sakai, “IEEE 802.11 Wireless Local Area Networks,” IEEE Commun. Mag., vol. 35, no. 9, pp. 116-126, Sep. 1997. J. Weinmiller, H. Woesner, and A. Wolisz, “Analyzing and Improving the IEEE 802.11-MAC Protocol for Wireless LANs,” Proceedings of MASCOTS’96, pp. 200-206. G. Bianchi, L. Fratta, and M. Oliveri, “Performance.
(8) [18]. [19]. [20]. [21]. [22] [23]. [24]. [25]. Evaluation and Enhancement of the CSMA/CA MAC Protocol for 802.11 Wireless LANs,” Proceedings of PIMRC’96, Taipei, Taiwan, pp. 392-396. L. Bononi, M. Conti, and L. Donatiello, “Design and Performance Evaluation of a Distributed Contention Control (DCC) Mechanism for IEEE 802.11 Wireless Local Area Networks,” Proc. Workshop WOWMOM’98, MOBICOM’98, Dallas, Texas, pp. 1-10, October 1998. F. Cali, M. Conti, and E. Gregori, “IEEE 802.11 Wireless LAN: Capacity Analysis and Protocol Enhancement,” Proc. INFOCOM’98, San Francisco, CA, pp. 142-149, March 1998. L. Bononi, M. Conti, and E. Gregori, “Design and Performance Evaluation of an Asymptotically Optimal Backoff Algorithm for IEEE 802.11 Wireless LANs,” Proceedings of the 33rd Hawaii International Conference on System Sciences 2000, pp. 1-10. T. H. Cormen, C. E. Leiserson, and R. L. Rivest, Introduction to Algorithms, McGraw-Hill, pp. 367-375, 1990. CACI Products Company, Simscript II.5, California 92037, Sep. 1997, http://www.caciasl.com/. B. Maglaris et al., “Performance Models of Statistical Multiplexing in Packet Video Communications,” IEEE Trans. on Commun., vol. 36, no., 7, pp. 834-844, July 1998. D. J. Goodman et al., "Efficiency of packet reservation multiple access," IEEE Trans. on Vehicular Technology, vol. 40, no. 1, Feb. 1991. D. Raychaudhuri and N. D. Wilson, "ATM-Based Transport Architecture for Multiservices Wireless Personal Communication Network," IEEE JSAC. vol. 12, no. 8, Oct. 1994..
(9)
數據
相關文件
This discovery is not only to provide a precious resource for the research of Wenxuan that has a long and excellent tradition in Chinese literature studies, but also to stress
Performance metrics, such as memory access time and communication latency, provide the basis for modeling the machine and thence for quantitative analysis of application performance..
Data larger than memory but smaller than disk Design algorithms so that disk access is less frequent An example (Yu et al., 2010): a decomposition method to load a block at a time
In this thesis, we have proposed a new and simple feedforward sampling time offset (STO) estimation scheme for an OFDM-based IEEE 802.11a WLAN that uses an interpolator to recover
Through the enforcement of information security management, policies, and regulations, this study uses RBAC (Role-Based Access Control) as the model to focus on different
This study chose a qualitative research method to explore more in-depth information access strategy for the establishment of many commodities, institute of emphasis from
[16] Goto, M., “A Robust Predominant-F0 Estimation Method for Real-time Detection of Melody and Bass Lines in CD Recordings,” Proceedings of the 2000 IEEE International Conference
LAN MAN Standards Committee of the IEEE Computer Society(1999), “ Wireless LAN Medium Access Control(MAC) and Physical Layer(PHY) Specifications,” International Standard ISO/IEC