Allocation
and
Schleduling Algorithms for
1EE:E
802.14
and
MCNS
in Hybrid Fiber
Coaxial
Networks
Ying-D,ar Lin
Chen-Yu Huang Wei-Ming Yim
Abstmct- IEEE 802.14 and MCNS a r e two standards de- veloped for the Hybrid Fiber Coaxial (HFC) CATV net-
works. Both standards model an upstream channel as a
stream of minislots. But their philosophies on resolving collisions in the shared upstream chan.ne1 are rather dif- ferent, where IEEE 802.14 adopts the plriority+FIFO flrst- transmission rule and the n-ary tree retransmission rule, and MCNS adopts the binary exponential backoff algorithm with adjustable window sizes. Both provide reservation ac- cess, while IEEE 802.14 and MCNS also support isochronous aceess and immediate access, respectively. In this paper, we
try t o prepare a suggestion list for vend.ors on how t o allo-
cate minislots for reservation aceess and immediate access and how t o schedule the reserved bandwidth, which greatly
affect the performance of a cable network and are left open
by the standards.
Keywords: IEEE 802.14, MCNS, HFC, upstream, colla-
sion resolution, immediate access, bandwidth allocation
I . INTRODUCTION
To facilitate interoperability between cable modems and headends designed by different vendors, standardization is required. Two major associations working on the hy- brid fiber coax (HFC) networks are IEEE 8U2.14 Working
Group [l], [2], [3] and Multimedia Cable Network System
Partners Ltd. [4], [5], abbreviated as MCNS. The objective
of these two standards is t o provide d a t a communication capabilities over the HFC network and to ensure the inter- operability of conforming products built by different ven- dors. Physical and Medium Access Control (MAC) layers are specified in these standards. The MCKS standard has been approved as a standard by International Telecommu- nications Union (ITU) on March 19, 1998. IEEE 802.14 is still in its draft and expected t o be finalized in 1998.
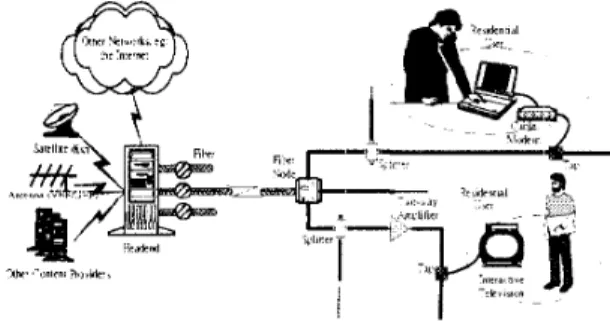
The HFC technology, followed by man.y cable companies, allows provision of upstream channels in a coaxial cable distribution network. Figure 1 represents an HFC system. ,4 fiber node which can serve 500 t o 2000 subscribers re- ceives signals sent from the headend via >a fiber. Then these signals are translated into cable signals by the fiber node and sent t o amplified tree-and-branch feeder cables. Sub- scribers can retrieve or transmit signals by connecting their coaxial terminal units (CTU), i.e. set-top boxs or cable modems, t o the taps on the network. With multiple access technologies, all subscribers within a branch can share the upstream bandwidth t o send data back t o the headend.
The HFC networks have the following important fea- tures. They certainly affect the protocol design.
Point-to-multipoint and multipoint-to-point: It is a point-to-multipoint, tree-and-branch access network in the The authors are with t h e Department of Computer and Information Corresponding author: Yirig-Dar T i n , email: Science, Satinrial Chiao Tung University, Hsinchu, Taiwan. ydlin~cis.rictu.edu.tw.
downstream direction, but a multipoint-to-point, bus ac- cess network in the upstream direction.
Inability t o detect collisions by CTU: CTU can only lis- ten t o the downstream traffic, which is different from Eth- ernet where adaptors can tell by themselves whether colli- sions occur.
Large propagation delay: According t o [l], [5], the max- imum round-trip-delay (RTD) is 0.4 ms in IEEE 802.14 and 0.8 ms in MCNS which is nnuch longer than the RTD on Ethernet. Assuming the propagation speed of 0.005 ms/km, the IEEE 802.14 and MCKS networks :may cover up t o 40 and 80 km, respectively.
Asymmetric upstream and downstream: The down- stream bandwidth is much larger than upstream's.
Non-uniform user distribution: Most of the subscribers are distributed over the last few miles of the network.
Given these two features, three important issues, includ- ing synchronization t o compensate the large propagation delay, collision resolution t o resolve collisions in the shared upstream channel, and upstream bandwidth management t o improve throughput and access delay, in the MAC layer need t o be resolved [6], [7]. In these two standards, the bandwidth allocation and transmission scheduling algo- rithms are left open t o be designed by vendors instead of being explicitly specified. This is because allocation and scheduling do not affect interoperability. However, they are correlated with the performance of a cable network.
In this paper, the issues of how t o properly allocate the upstream bandwidth and how to schedule requests from stations are studied. We discuss these issues after we present the network operation in section 11. Section I1 also illustrates the similarities and differences between IEEE 802.14 and MCKS. We then simulate the systems by apply- ing various bandwidth allocation strategies, collision res- olution parameter settings, and transmission scheduling algorithms. Our simulation models are describted in sec- tion 111. Kumerical results are presented in section IV and section V.
Fig. 1. An TTFC network 0018-9316/98$10.00 0 1998 IEEE
U ~ , e a m
11. I E E E 802.14 VERSUS MCNS A . Normal Operation
In IEEE 802.14 and MCNS, an upstream channel is mod- eled as a stream of minislots, the smallest transmission
Management Cell. composed ofxveral Map. composed of several kinds kinds o f Information Elements
m e Information Element is uwd lo dejribe the usage of some
eontimow upstream minislow.
Stations send bandwdth iulucsts in reaest minislots and send data in
of Information Elements.
The minimum channel spacing IS ( I + a ) Rs where a is the spectral roll- off factor, and Rs IS the symbol rate
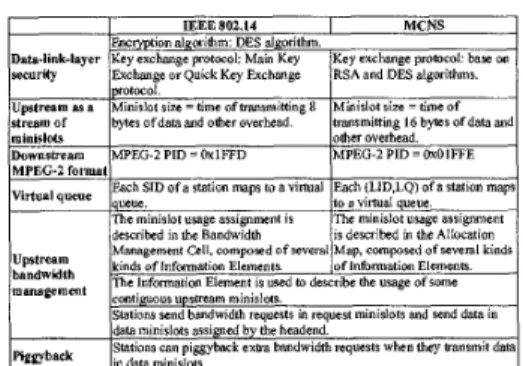
units in the upstream. The usage of upstream minislots is assigned by the headend, and basically there are two types of minislots-request minislot and data minislot. Data min- islots are used t o carry data. Request minislots are used to carry bandwidth requests made by stations for their uir- tual queues each of which is the elementary entity in the
Table 1, Key features in the physical layer of IEEE 802 14 and MCNS
~ e b s ~
MAC protocol. From time to time, the headend broad- casts a bandwidth allocation map, which contains the usage assignments of upstream minislots. Stations learn the as- signments from that map and work accordingly.
Figure 2 shows a simple state diagram for the stations of MCNS and IEEE 802.14. Initially, the station enters the
Stations a n pigpybMk exw bandwidth requests when they transmit data in data minirlots.
initialization completed
data arrival
collision finish transmitting o c c ~ (Collision Resolution) and no more pending job
request sent successfully
data arrival I
I
(Piggyback request if
Piggyback IS enabled)
i
._-
Fig. 2. A simple state diagram for stations of MCNS and IEEE
802.14
Idle state. When a data message arrives, the station enters the Collision Resolution state and repeatedly tries to send a bandwidth request to the headend until the request is suc- cessfully received and acknowledged by the headend. Then the station enters the Transmitting state. If extra data mes- sages arrive during the station's transmission, the station may enable the Piggyback mechanism and piggyback the extra bandwidth request. Once the station finishes send- ing data messages and there are no more pending jobs, the station switches back t o the Idle state.
Table 2. Similarities between the MAC layers of IEEE 802.14 and MCNS
mode and collision resolution algorithms here because they are among the issues studied here.
Immediate Access Mode in MCNS
In addition t o the normal reservation and piggyback reservation modes supported in both standards, MCNS also provides immediate access mode. When the network traffic load is low, the headend may assign a region of min- islots as immediate access minislots. This assignment, in- cluding 1) where the immediate access region starts, 2) how many minislots are in the region, 3 ) the maximum message length permitted to use the immediate access, and 4) the al- lowed starting points within the immediate access region, is encapsulated in the bandwidth allocation map multicast t o stations. That is, any immediate access transmission must start at some specific minislots in the region and must fit within a limited number of minislots. Stations can transmit not only data but also their bandwidth requests in these immediate access minislots. Depending on the transmis- sion result, a positive or negative feedback will be issued t o the station. Even if the transmission is collided, the sta- tion can retransmit its request or data in the next region of immediate access mode, i.e. no further collision resolution protocol is enforced, or give up the immediate access mode and try the reservation access mode.
Collision
For the collision resolution algorithms, the latest draft of IEEE 802.14 combines four techniques, which are pri- oritized admission control mechanism, FIFO mechanism, n-ary tree algorithm, and the idea of multiple collision res- olution engines, into its collision resolution algorithm. The
B.
The Similarities and DifferencesThere are a few differences between IEEE 802.14 and
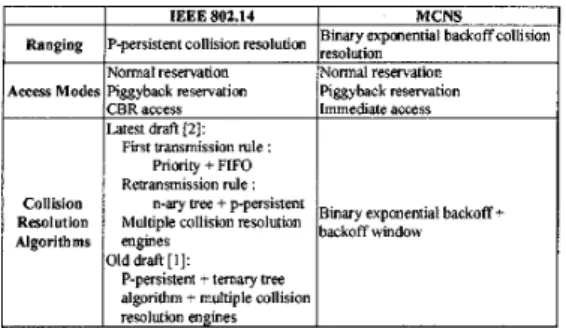
MCNS. Key features of their physical layer specifications are summarized in table 1. Similarities and differences be- tween their MAC layer specifications are illustrated in ta- ble 2 and table 3 , respectively. More detailed comparisons
IEEE802.14
mogjng ppersistent collision resolution Binary eXponSntial backoff colliswn Normal reservation Normal reservation
Access Modes Piggyback reservation Piggyback reservation Immediate a u e s s Latest draft 121:
First Wansmission rule :
Priority +FIFO Retransmission d e :
P-persistent + temary tree
algoribm + multiple collision resolution engaes
Table 3. Differences between the MAC layer:; of IEEE 802.14 and MCNS
prioritized admission control mechanism is used t o discrim- inate requests of different priorities. The FIFO mechanism is used t o prevent excessive collisions. These two mecha- nisms are used as the first transmission rule, i.e. the rule that applies t o the newly arriving requests. The n-ary tree algorithm is used t o resolve the collided requests.
In the old version of IEEE 802.14 specification (draft
a), the first transmission rule and the algorithm used t o
resolve collided requests are p-persistent and ternary tree algorithms, respectively. Both versions idlow multiple col- lision resolution engines t o work in parallel to resolve dif- ferent sets of contending stations.MCNS adopts a binary exponential backoff algorithm to resolve collisions in the request minislot contention process.
Data Backoff Start (DBS) and Data Backoff End (DBE)
in the bandwidth allocation map are used t o indicate the initial and maximum backoff window sizes, respectively. The station that wants t o send its request does not contend for any request minislots until it has deferred T contention transmission opportunities, where T is an integer randomly selected between 0 and its backoff window size.
C. Studied Issues
In these two specifications, the headend controls three factors that affect the performance of a cable network. They are 1) the usage of each upstream minislot, 2) the parameters of collision resolution procedures, and 3) the scheduling of received bandwidth requests. The upstream channel is a limited resource, therefore the more upstream minislots are assigned as request minidots, the less up- stream minislots can be assigned as data minislots. With proper settings of the collision-resolution parameters, not only less upstream minislots would be wasted on resolving collided requests but also shorter request access delay, t o be defined in section 111, can be obtained.
In this paper, we examine the following issues in IEEE 802.14 (draft 2) and MCNS:
1. Minislot allocation in the collision resolution process: How much of the upstream bandwidth should be allocated as request minislots? How to set the para.meters of collision resolution algorithms?
2. Minislot allocation for immediate access in MCNS: What is the proper time for the headend t o conduct imme- diate access allocation? How much of the upstream band-
width should be allocated as immediate access? How t o set the parameters of the immediate access?
3. The effect of the piggyback mechanism on the transmis-
sion scheduling algorithms: The probability that, a request can be piggybacked is equal t o the probability that the request arrives t o a non-empty queue of a station. Thus, the scheduling algorithm needs to reduce the data transfer delay but may also want t o reduce the request access de- lay, where the latter might be achieved by increasing the chance of piggyback.
111. MODELS FOR SIMULATION STUDIES The common simulation parameters are listed in table 4. In the simulation, a MiniPDUTime, i.e. the durat,ion of one minislot, is the elementary time unit, and all simulation results are measured in the unit of MiniPDUTime.
Table 4. Common parameters in the simulation study
A. Model for Collision Resolution and Request Scheduling
We measure the throughput, request access delay (RAD),
and data transfer delay (DTD) of the simulated systems
which are applied various minislot allocation strategies and transmission scheduling algorithms. The throughput of the system is defined as what percentage of the upstream band- width is used for successful data transmission. The RAD of a request is defined as how much time a station takes t o successfully transmit the request. Once a request has been successfully transmitted to the headend, it becomes a granted request. The DTD oE a granted request is de- fined as how much extra time the headend take,s t o serve the request. RAD is used t o measure the efficiency of col- lision resolution algorithms, while DTD is used t o measure the efficiency of transmission scheduling algoritlhms. For example, in figure 3, a data message arrives at a station
at T I . After one or several request transmissioins by the station, the headend receives the request and puts it into the scheduling queue at T2 and then sends back a, feedback message which is received by the station at T3. The re- quest is then scheduled and the station is notified about when and how much it can transmit. Finally, the station finishes the transmission for the request at T4. Therefore,
the RAD is T3 -
2'1,
and the DTD is T4 - T2.B. Model f o r Immediate Access
In this model, an upstream channel is modeled as cycli- cally repeated and fixed-length frames, as shown in figure 4. The first P% of each frame is reserved for immediate ac-
cess. Any station with a pending bandwidth request may 1) try immediate access if the data message length is small
T,, receive last bit of data headend station I I I contend
*
fmish transmission T,, receive schedule transmitT, Y
data arrives positive ack.
data transmission Fig. 3. A sequence of events for request, schedule and transmission
frarne-q
r
T 3 headend'
P% (I+)%1
"1
T,T
T4T
TG
station send request-
11, data arrivesreservation data transmission immediate access region Fig. 4. Model for immediate access
enough, and the number of retransmissions does not exceed the upper limit or 2) conduct reservation access by send- ing its request at the beginning of each frame, as shown in figure 5. For the headend, it adopts first come first serve
immediate a a ~ s collision
Fig. 5. Operations of a station
(FCFS) algorithm t o schedule the requests at the beginning of each frame. In figure 4, a data message (size=K) arrives at a station at TI. If the station conducts immediate ac- cess and successfully transmits the data message at T4, the
access delay (AD) is calculated as
T4
-
T I . If reservation access is used, and the station finishes transmission atTj,
the AD is calculated as T b
-
TI-
K . The throughput ofthe system is defined as what percentage of the upstream
r
---Fix3-Rx3 6W... ... Fix3-Vat
Fig. 6. RAD of different allocation strategies in IEEE 802.14
is the first transmission rule, and the n-ary tree algorithm which is the retransmission rule. Thus, the minislot allo- cation in the collision resolution process of IEEE 802.14 (draft 2) can be further divided into two parts:
1. The initial allocation for the newly arriving requests, and
2. The collision-resolution allocation for the collided re-
que&.
The applied allocation schemes in the simulation are de- fined in table 5. Besides, we assume that the headend has the talent t o guess the proper p value in the p-persistent first transmission rule, i.e. p = min(potentia1 contention
entry range
/
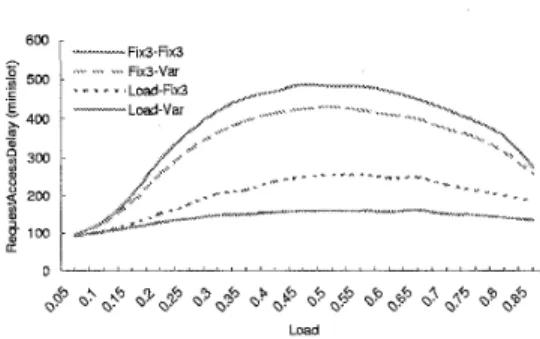
number of allocated minislots, I ) .In figure 6, four combinations of initial and collision- resolution minislot allocations are simulated. For exam- ple, the line labeled as "Fix3-Var" represents the schemes of initial and collision-resolution allocations are Fix3 and Var, respectively. We can see that the RAD is high when the load is medium. This is because when the traffic load
is high, most stations can piggyback their bandwidth re- quests instead of contending request minislots. Thus, the headend has t o allocate more request minislots when the traffic load is medium. The Load-Var has better perfor- mance the than the other allocation strategies. Also, com- paring the improvement amounts of Fix3-Var over Fix3- Fix3 and Load-Fix3 over Fix3-Fix3, we can find that the initial allocation has a greater impact on the RAD than the collision-resolution allocation.
*. m i s only applies to the collision-rerolurion allocation of IEEE 802 14
**: TXis only applies lo the initial allocation of IEEE 802 14.
bandwidth is used for successful data transmission. AD ' w * + This polynomial expression i s the approximsrion ofthe curve "Fix3-FixY in figure 6 and is obtained through mathemarical package Origin and throughput are used t o measure the performance of
the allocation strategies for immediate access. Table 5. Minislot allocation strategies in collision resolution of IEEE 802.14 (draft 2)
I v . MINISLOT ALLOCATION IN I E E E 802.14 AND MCNS
A . Collision Resolution in IEEE 802.14
The collision resolution algorithm adopted in IEEE 802.14 (draft 2) consists of the p-persistent algorithm which
B. Collision Resolution in MCNS
MCNS runs binary exponential backoff to resolve colli- sions in request minislots. However, it allows flexibility in
specifying the backoff start and end window sizes. Here we investigate how t o allocate request minislots and how to ad- just the backoff window under Ethernet-like and random- select types of collision resolution, as defined in table 6.
Request minislot allocation strategies
For random-select type of collision resolution, the simu- lation results of throughput and RAD are shown in figure 7
and figure 8, respectively. When the load is high, most re- quests are piggybacked through the scheduled data trans- mission instead of contending request minislots. Hence, some request minislots are wasted and the throughput is not proportionally increased. The performance of Fix8, in terms of RAD, is the best among these allocation schemes. For random-select type of collision resolution with window size fixed at 8, we can just allocate 8 minislots in every clus- ter. Note that when the load is above 0.75, the RAD of Fix12 is not accurate because almost all requests are sent t o the headend through piggyback instead of contending reaiiest minislots.
Name I Description
Ethernet like IBackoff start window size IS S and backoff end wiidow size IS E (S#E)
Randoin-select lBoth backoff start and end window sizes are equal to some W.
Table 6 . Two types of backoff window setting in collision resolution
of MCNS 100% 90% 80% 70% 2 60%
5
50%-
$ w/c 30%Fig. 7. Throughput for different numbers of allocated request min- islots in MCNS (adopting random-select type of collision resolu- tion)
&I lo i
+
Fix3--b Fix6 Fix8
Fig. 8. RAD of different numbers of allocated request minislots MCNS (adopting random-select type of collision resolution)
For the Ethernet-like type of collision resolution with backoff start, S, and backoff end, E , the simulation results
of throughput and RAD under 6 minislot allocation strate- gies, defined in table 7, are shown in figure 9 and figure 10,
respectively. The SE scheme which resolves collisions effi- ciently performs the best among these allocation strategies. On the other hand, the E and MeanSE schemes that allo- cate too many request minislots lead t o lower throughput. Because there is no idea about how many stations collided within one minislot, allocating as many request minislots
as possible, i.e. the SE scheme, is a efficient strategy t o quickly resolve collisions. Therefore, the SE scheme per- forms better than Dbl and EXD schemes.
How to allocate?
1
Nornially, the headend allocates S request minnlots in eachIf there were C collisions in last niinislot duster. the headend
I
Exp ristot'c1'"; ~If there were C collisions in last minislot duster, the headend allocates niax 2', E minislots in this minislot cluster.
Nomiallv. the headend allocates S remest minislots at each niinislot cluster.
If there were collisions in last minislot cluster, the headend
Table 7. Minislot allocation strategies in collision resolution of MCNS
100% 90% 80% 70% '5, 60% ? 50%
E
40% 30% 20%Fig. 9. Throughput of various minislot allocation strategies in MCNS (adopting Ethernet-like type of collision resolution)
600 - 500 400 - +S +Dbl -4- Exp MeanSE E S E 300 ~ 200 100
Fig. 10. RAD of various minislot allocation strategies in MCNS (adopting Ethernet-like type of collision resolution)
E
Backoff window settings
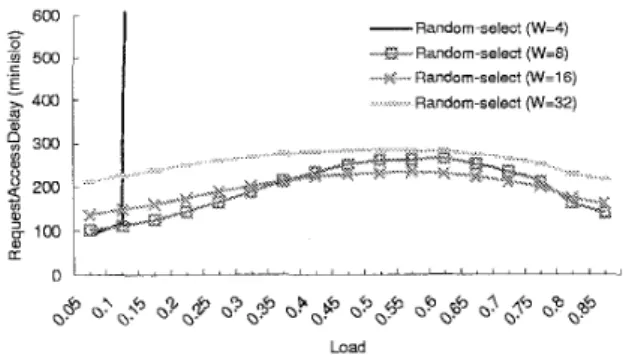
In this simulation, the headend adopts the Fix6 initial minislot allocation strategy and applies random-select and Ethernet-like window settings. From figure 11, we find that the window size should be enlarged when the load is medium and shrunk when the load is light or very heavy under the random-select type of collision resolution. Note that over-sized window , such as the W32, only results in lower utilization of request minislots; consequently, the re- quest opportunities are deferred and the RAD is therefore larger. 600
-
p 400I
-
Random select (W=4) -E*- Random-seled (W=8) \ Random-select (W=l6) Random-select (W=32)Fig. 11. RAD of different window sizes for the random-select type of collision resolution in MCNS (adopting Fix6 allocation) For the Ethernet-like type of collision resolution, the headend should not assign a backoff start window size that is too small t o avoid the collision at first transmissions and a backoff end window size that is too large to avoid defer- ring the transmission unnecessarily. As shown in figure 12, the window size range of 4 t o 32 is the best.
Fig. 12. Th e RAD of different Ethernet-like type of collision resolu-
tion in MCNS (adopting Fix6 allocation)
Comparing these two backoff window setting strategies, from figure 13, the fine-tuned random-select setting, which
sets a smaller window at light and heavy load, and a large window at medium load, performs better than the Ethernet-like setting. Basically speaking, the random- select setting tries t o avoid collisions at the first trans- mission, but the Ethernet-like setting aims at efficiently resolving collisions.
C. Immediate Access in MCNS
MCNS offers immediate access mode t o access upstream
600 I
-
r"'
2 400i
300 1
Fig. 13. RAD of fine-tuned random-select and Ethernet-like in
MCNS
access region and the maximum message length permitted to use this access region. We investigate the performance of cable networks under the following three configurations: 1. Different sizes of immediate access regions
2. Different maximum message lengths
3. Different numbers of retries for immediate access
Size of immediate access regions
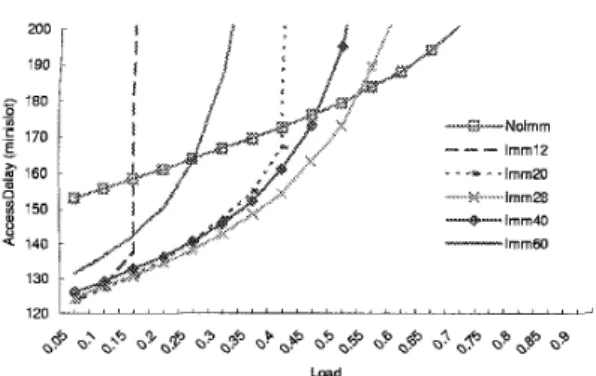
From figure 14, we can find that the headend should turn
off the immediate access mode when the load is heavy. In other words, the bandwidth should be allocated t o the reservation-based transmission when the load is heavy. From figure 15, we can find that the size of immediate ac- cess regions should be dynamically adjusted. Designating too much bandwidth for immediate access is not efficient because there might not be so many messages qualified to use the immediate access regions. On the other hand, under-sized immediate access regions lead t o severe colli- sions and, in turn, wasted the bandwidth. Observed from the simulation results, the headend should designate 28% and 0% of upstream bandwidth for immediate access when the load is under 0.55 and above 0.55, respectively.
x .. .y
Fig. 14. Throughput for different sizes of immediate access regions in MCNS
Maximum message length
From figure 16, we can find that setting a smaller value of maximum message length, when the load is heavy, has an effect on preventing messages from contending immedi- bandwidth. The headend can determine the immediate ate access regions. Hence, severe collisions can be avoided.
Fig.
I90
j
j
j!
130
15. AD for different sizes of immediate access regions in MCNS
On the other hand, when the load is light, setting a larger value of maximum message length leads to higer utiliza- tion of immediate access bandwidth and the AD is there- fore lower. In this simulation, the headend should assign the maximum message length as 5, 4, 2 when the load is under 0.15, between 0.15 and 0.35, between 0.35 and 0.6, respectively. For the load over 0.6 or 0.7, immediate access regions should be closed.
500 450 400 Z 350 E 300 5 250
-
i
2003
150 100 50 100% SWh - 80% - 70% - 60% 9 5w. ,: No retry I'what we have discussed earlier, there are more potential contenders for request minislots when the load is medium. We can find that when the load is medium, IEEE 802.14's RAD is lower than MCNS's, as shown in figure 20. That is because the first transmission rule can avoid too many requests contending the same minislot cluster. The differ- ence of the RAD between IEEE 802.14 and MCNS is small when the load is light or heavy.
Fig. 16. AD for different values of maximum message length
Number of retries
Investigating our previous simulation results, we find that with the explosion of the AD for immediate access at heavy traffic load, the overall AD gets extremely high. We expect that setting the retry limit on the immediate access might alleviate the problem. From figure 17, it is observed that the difference of AD between between various retry limits is not notably when the load is low. However, when the load starts t o increase, setting a smaller retry limit can prevent AD from increasing dramatically and the sys- tem should eventually turn off the immediate access mode when the load is high enough (>0.7). No retry for imme- diate access seems t o be a good policy. Note that, from figure 18, the throughput is mainly constrained by the size of immediate access regions instead of retry limit.
D.
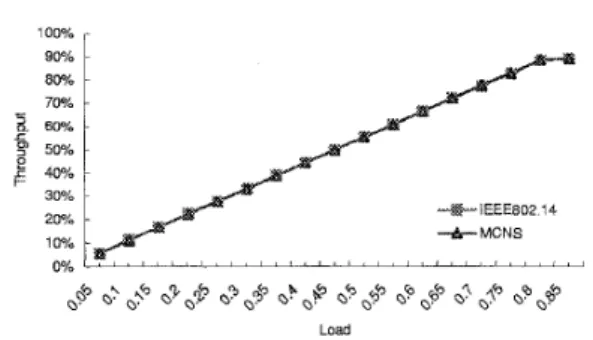
ComparisonsWe now examine the RAD and throughput of IEEE 802.14 and MCNS under their fine-tuned parameter set- tings and the same minislot allocation strategy-Fix6. Fig- ure 19 shows that they have the same throughput. As
V.
SCHEDULING
IN IEEE 802.14 AND MCNSIn IEEE 802.14 and MCNS cable networks, the head- end not only allocates request minislots but also schedules upstream data transmissions. Here we investigate how dif- ferent scheduling disciplines, as defined in table 8, affects the performace of data transmission. From figure 21 and figure 22, we find that the system adopting shortest job first
(SJF) has the lowest DTD, but its RAD is the worst. And vice versa for longest job first (LJF). This phenomenon is due t o that when the system has small DTD, the queue at a
station has a higher probability of being empty, hence, the probability that a station can piggyback its request is also small. Hence, we introduce a modified SJF discipline which distributes scheduled data minislots t o increase the proba- bility for a station t o piggyback its request. For example, the headend may grant 30 minislots for some station. These
granted minislots might be distributed over minislots num- bered from 20 t o 29,40 t o 49, and 60 t o 69, instead of from 20 to 49 contiguously. As what we expected, the RAD does get reduced, while the DTD gets increased. The modified
100% 70% 60% 3 50% 30% 20% 1 PA 0% 300 p 250 E 200 a, 150
5
100-
-
'3 2 5 0 - 0Fig. 19. Throughput of IEEE 802.14 and MCNS. (IEEE 802.14 adopts Fix6-Var. MCNS adopts Fix6.)
- ~ -S-ModihedSlF ...x* S I F - & U F - ' " " " " " " " " ' " " ' " " " ' ~ ' 300 I
Fig. 20. RAD of IEEE 802.14 and MCNS. (IEEE 802.14 adopts Fix6-Var. MCNS adopts Fix6.)
VI.
CONCLUSION
The effects induced by applying various strategies for minislot allocation, collision resolution parameter setting, and transmission scheduling in IEEE 802.14 and MCNS cable networks are studied in this paper. From the simula- tion results, we conclude that many allocation algorithms should be load-dependent and the scheduling algorithms are influenced by the piggyback mechanism where there is a tradeoff between request access delay and data transfer delay. We now summarize the major results and sugges- tions for the vendors of cable headends and modems. 1. Avoid collision in the first place : It is observed that the initial allocation is more important than the collision- resolution alloca.tion for both IEEE 802.14 and MCNS. The initial allocation, however, should depend on traffic load. Due t o the piggyback effect, the demand for request min-
Table 8. Scheduling algorithms upstream d a t a transmission
600 0 500 - 400 5 300 g m
I
;
zoo 3 = 100 0 4%-ModifiedSlF ....* WF t L J Fislots under medium load is higher than under light and heavy load. The first transmission rule can be combined with the initial allocation t o effectively reduce the chance of collisions. For IEEE 802.14 and MCNS, the first trans- mission rules are priority FIFO and backoff window, re- spectively. The backoff window in MCNS can be fixed or variable in a binary range.
2. Resolve collisions quickly : Contrast to the initial alloca- tion, the collision-resolution allocaiton should not depend on traffic load. Instead, it should depend on the number of observed collisions. Variable collision-resolution allocation combined with load-dependent initial allocation achieves the best result. Interleaved multiple collision resolution en- gines can be executed under medium traffic load, i.e. high demand for request minislots.
3. Allocate the right size of MCNS immediate access re- gions at the right time : The percentage of immediate ac- cess regions within an upstream channel should also depend on traffic load. It should be lowered as load increases and closed under heavy load. The maximum size of messages permitted to use immediate access regions can be lowered too as load increases. It has the effect t o decrease the chance of collisions in immediate access regions. Finally, no retry is suggested for messages collided in the first try in immediate access regions. They can redirect themselve t o use the reservation access.
4. Distribute the schedule for a single request into several
pieces : Contrast to collision resolution, it is not necessary
t o schedule data transmission for a request as quickly as possible. For a station, the sooner the data transmission is finished, the less likely the next request can be piggy- backed. Thus there is a tradeoff between data transfer delay and request access delay. Fortunately, distributing the schedule for a single request into several pieces such that the requested data transmission is broken into sev- eral bursts can increase the chance for a new request t o be piggybacked.
REFERENCES
[2] 1T:T:T:: IEEE Project 8OZ.l4/a Draft 3 Revision 1, Apr. 1998.
[3] “IEEE 802.14 cable TV working group,”
tittp://v,ww.walkingdog.com/. .
[/I] “Data over cable service interface specifications,” http://wu.w.cablemodem.com/.
[5] Cable Television Laboratories, Inc., Data-Over-Cable Service In- terface Specifications-Radio h q u e n c y Interface Specification,
Oct. 1997.
[6] Chen-Yu IIuang and Ying-Dar Lin. “Comparing IEEE 802.14 and MCTS standards for hybrid fiber coaxial networks,” submitted for publication.
[7] Ying-Dar Lin, “On IEEE 802.14 medium access control protocol,” t o appear in IEEE Communications Surveys, Sep. 1998.
[8] John 0. Limb and Dolors Sala, “A protocol for efficient transfer of d a t a over hybrid fiberlcoax systems,” IEEE/ACM Thnsactions
on Networking, vol. 5, no. 6 , pp. 872-881, Dec. 1997.
[9] Ying-Dar Lin, Chia-Jen Wu, and Wei-Ming Yin, “PCUP: Pipelined cyclic upstream protocol over hybrid fiber coax,” IEEE Network Magazine, vol. 11, no. I , pp. 24-34, January/February 1997.
network management, speed LATs/MANs/\
Y i n g - D a r L i n received the Bachelor’s degree in Computer Science and Information Engi- neering from Xational Taiwan University in 1988, and the M.S. and Ph.D. degrees in Com- puter Science from the University of Califor- nia, Cos Angeles in 1990 and 1993, respectively.
He joined the faculty of the Department of Computer and Information Science at National Chiao Tung University in August 1993 and is now Associate Professor. His research inter- ests include traffic characterization, service and distributed multimedia applications, and high- VANS. Dr. Lin is a member of ACM and IEEE.
C h e n - Y u H u a n g received B.A. and M.S. in Computer and Information Science from Na- tional Chiao Tung Cniversity in 1996 and 1998, respectively. His research interests include high-speed LASS and interactive CATV pro- tocols design. He is now on a twc-year duty in
W e i - M i n g Y i n received B.A. and M.S. in
Computer and Information Science from Na- tional Chiao Tung University in 1995 and 1997, respectively. He is now a Ph.D. student in the same department. His current research inter-
’
-:
’ [ -