Normal and Sinkless Petri Nets* RODNEY R. H O W E L L
Department of Compuiing and Information Sciences, Kansas State University, Manhattan, Kansas 66506
LOUIS E. ROSIER+
Department of Computer Sciences,
The University of Texas at Austin, Austin, Texas 78712
AND HSU-CHUN YEN
Department of Electrical Engineering,
National Taiwan University, Taipei, Taiwan, Republic of China
Received December 12, 1988; revised May 22, 1 9 9 1
W e examine both the modeling power of normal a n d sinkless Petri nets a n d the computa- tional complexities of various classical decision problems with respect to these two classes. W e argue that although neither normal nor sinkless Petri nets are strictly more powerful than persistent Petri nets, they nonetheless are both capable of modeling a more interesting class of problems. O n the other hand, we give strong evidence that normal a n d sinkless Petri nets are easier to analyze than persistent Petri nets. In so doing, we apply techniques originally developed for conflict-free Petri nets-a class defined solely in terms of the structure of the net-to sinkless Petri nets-a class defined in terms of the behavior of the net. As a result, we give the first comprehensive complexity analysis of a class of potentially u n b o u n d e d Petri nets detined in terms of their behavior. 0 1993 Academic Press, Inc.
1. INTRODUCTION
M a n y aspects of the fundamental nature of computation are often studied via formal m o d e ls, such as Turing machines, finite-state machines, a n d push-down automata (see, e.g., [HU79]). O n e formalism that has b e e n used to m o d e l parallel computations is the Petri net (PN) [Pet81, Rei85-J. As a m e a n s of gaining a better understanding of the PN m o d e l, the decidability a n d computational complexity of
* This work was supported in part by National Science Foundation Grant No. CCR-8711579. A preliminary version was presented at the 7th International Conference o n Fundamentals of Computation Theory, Szeged, Hungary, August 1989.
+ Louis Rosier passed away o n May 6, 1991.
0022~0000/93 $5.00 Copyright 0 1993 by Academic Press, Inc. All rights of reproduction in any form reserved.
2 HOWELL, ROSIER, AND YEN
typical automata theoretic problems concerning PNs have been examined. These problems include boundedness, reachability, containment, and equivalence. Lipton
[Lip761 and Rackoff [Rac78] have shown exponential space lower and upper bounds, respectively, for the boundedness problem. Also, Rabin [Bak73] and Hack [Hac76] have shown the containment and equivalence problems, respectively, to be undecidable. No tight bounds, however, have yet been established for the com- plexity of the reachability problem. The best lower bound known for this problem is exponential space [Lip76], but the only known algorithm is nonprimitive recursive [May84]. (See also [Kos82, Lam87].) Even the decidability of this problem was an open question for many years.
Early efforts to show the reachability problem to be decidable included the study of various restricted subclasses of PNs [CLM76, CRM75, GY80, Gra80, HP79, LR78, May81, MM81, MM82, Mu181, VVN81]. The only classes for which completeness results have been given concerning all four of the problems men- tioned above are one-conservative PNs [JLL77], one-conservative free choice PNs [JLL77], symmetric PNs [CLM76, MM82, Huy85], and conflict-free PNs [JLL77, HRY87, HR88] (the proofs in [JLL77] also apply to one-bounded PNs and elementary nets). Of these classes only symmetric and conflict-free PNs are potentially unbounded, and both symmetric and conflict-free PNs are defined only in terms of their structure, not in terms of their behavior. Thus, until now there has been no class of potentially unbounded PNs defined in terms of their behavior for which a comprehensive complexity analysis has been given.
Of all of the PN classes for which completeness results have been shown concerning all four of the problems mentioned above, the class for which the decision procedures are most efficient is that of conflict-free PNs. In particular, the boundedness problem is complete for polynomial time [HRY87], the reachability problem is NP-complete [JLL77, HR88], and the containment and equivalence problems are n,P-complete [HR88], where nc is the set of all languages whose complements are in the second level of the polynomial-time hierarchy [Sto77]. However, since conflict-free PNs comprise such a simple class, their modeling power is very limited. In particular, as we show in this paper, conflict-free PNs cannot model the producer/consumer problem if more than one consumer is involved and the actions of each consumer are to be modeled by separate transitions. Furthermore, the obvious generalization of conflict-free PNs to persistent PNs (see [LR78]) is not very helpful: not only is it impossible to model the above problem with persistent PNs, but the complexities of the various problems regarding persistent PNs appear to be worse than for conflict-free PNs. In particular, all four problems are PSPACE-hard [JLL77]. The known upper bounds are much worse: the best upper bound known for boundednes is exponential space [Rac78], and no primitive recursive algorithms are known for the other three problems, although they are known to be decidable [Gra80, May81, Mu181]. Even the problem of recognizing a persistent PN, although known to be decidable [Gra80, May81, Mu181 1, is not known to be primitive recursive, and is PSPACE-hard [JLL77].
More recently, Yamasaki [Yam841 has defined two other generalizations of conflict-free PNs, normal PNs and sinkless PNs. The relationship of normal PNs to sinkless PNs is analogous to the relationship of conflict-free PNs to persistent PNs; i.e., normal PNs are those PNs that are sinkless for every initial marking [Yam84], just as conflict-free PNs are those PNs that are persistent for every initial marking [LR78]. In addition, normal PNs, like conflict-free PNs, are defined in terms of the structure of the net, whereas sinkless PNs, like persistent PNs, are defined in terms of the behavior of the net. However, both normal and sinkless PNs are incomparable to the class of peristent PNs; i.e., there are persistent PNs that are not sinkless, and normal PNs that are not persistent. In this paper, we examine both the modeling power of normal and sinkless PNs and the computational complexities of the four problems mentioned above with respect to these two classes. We show that both in terms of modeling power and ease of analysis, normal and sinkless PNs compare very favorably to conflict-free and persistent PNs.
Concerning the modeling power, we first show that the producer/consumer problem mentioned above, which cannot be modeled by persistent PNs, can be modeled by normal PNs. We then examine the mutual exclusion problem. We show that although this problem cannot be modeled by sinkless PNs, a version in which a bounded number of exclusions takes place can be modeled by normal PNs (persistent PNs cannot even model one exclusion). We therefore conclude that although not all persistent PNs are sinkless, the class of problems that can be modeled by sinkless (or even normal) PNs is somewhat more interesting than that class modeled by persistent PNs.
We then examine whether the more “useful” nature of sinkless PNs causes a corresponding increase in the complexities of the classical problems (as compared to persistent PNs). We show that this is not the case; i.e., we show that for both normal and sinkless PNs, the boundedness problem is co-NP-complete, the reachability problem is NP-complete, and the containment and equivalence problems are n:-complete. Note that with the exception of the boundedness problem, the complexities of these problems are identical to those for conflict-free PNs-an extremely simple class. In fact, the techniques used in deriving these results for normal and sinkless PNs are simply more sophisticated applications of the techniques developed in [HR88] for conflict-free PNs. Thus, techniques originally developed for analyzing problems involving conflict-free PNs-a class defined solely in terms of the structure of the net-have been generalized to apply not only to normal PNs, but also to sinkless PNs-a class defined in terms of the behavior of the net. Furthermore, these results represent the first comprehensive complexity analysis of the classical problems concerning a class of potentially unbounded PNs defined in terms of their behavior.
We also examine the question of how much easier it is to recognize a normal PN than to recognize a sinkless PN. Recall that the problem of recognizing a persistent PN is not known to be primitive recursive, and is at least PSPACE-hard [JLL77], whereas a conflict-free PN can easily be recognized in polynomial time. The main problem in deciding persistence is that some sort of reachability analysis is
4 HOWELL, ROSIER, AND YEN
necessary due to the fact that persistence is a behavioral property. Since sinkless PNs are likewise defined in terms of their behavior, whereas normal PNs are defined solely in terms of their structure, one might suppose that normal PNs would be easier to recognize than sinkless PNs. However, in order to determine whether a PN is normal, a rather complex property of the graphical representation of the PN must be tested. The end result is that both the problem of determining whether a PN is normal and the problem of determining whether a PN is sinkless are co-NP-complete. We therefore conclude that in most applications, one might as well consider the entire class of sinkless PNs rather than the more restricted class of normal PNs.
The remainder of the paper is organized as follows. In Section 2, we formally define the concepts used throughout the paper. In Section 3, we compare the modeling power of normal and sinkless PNs with that of persistent PNs. Finally, in Section 4, we examine the complexities of the various problems regarding normal and sinkless PNs.
2. DEFINITIONS
Let N denote the set of nonnegative integers, R the set of rational numbers, Nk
(Rk) the set of vectors of k nonnegative integers (rational numbers, respectively),
and Nkxm (Rkxm) the set of k x m matrices of nonnegative integers (rational numbers, respectively). For a k-dimensional vector u, let o(i), 1 d i < k, denote the ith component of u. For a k x m matrix A, let A(i, j), 1 6 i < k, 1~ j < m, denote the element in the i th row and the j th column of A, and let uj denote the j th column of A. For a given value of k, let 0 denote the vector of k zeros (i.e., O(i) = 0 for i=l , . . . . k). Given k-dimensional vectors, U, u, and w, we say:
l v=w iff u(i)=w(i) for i=l,...,k;
l U~W iff u(i)aw(i) for i=l,...,k;
l v>w iff v>w and v#w; and
l u = u + w iff u(i) = o(i) + w(i) for i= 1, . . . . k.
A Petri net (PN, for short) is a tuple (P, T, cp, p,,), where P is a finite set of
places, T is a finite set of transitions, cp is a flow function cp : (P x T) v (T x P) -+ N,
and p0 is the initial marking p,, : P -+ N (in this paper, we only consider PNs for which the range of cp is (0, 1 }). A marking is a mapping n : P + N. A transition
t E T is enabled at a marking /J iff for every p E P, cp( p, t) < p(p). A transition t may
fire at a marking p if t is enabled at ~1. We then write p -& $, where
p’(p)=p(p)-cp(p, t)+cp(t, p) for all PEP. A sequence of transitions a=t,...t,
is a firing sequence from no (or a firing sequence of (P, T, cp, pO)) iff po-fl*pl-is . . . --% pL, for some sequence of markings pi, . . . . pL,. We also write po-Sp,. For o,.o’~T*, ~Y=t,...t,,, let c - 0’ be inductively defined as follows: Let CY~ be C. If t, E oip i, let di be rr-~, with the last occurrence of tj deleted; otherwise, let cr, = cr- , . Finally, let CJ 2 CJ’ = on.
We only consider Petri nets (P, T, cp, pO) such that the range of cp is (0, 1 }; hence, we may view them from two different perspectives. The first perspective is graph-theoretical: Pu T forms the set of vertices of a directed graph, and (u, u) is an edge iff cp(u, u) = 1. Since cp is a function on (P x T) u (TX P), the graph representation of the PN is bipartite. This graph theoretic perspective yields a natural pictorial representation for PNs. In such pictures, we adopt the convention of denoting a place by a circle and a transition by a bar; the marking p is represented by p(p) dots (or tokens) in the circle denoting each place p. The other perspective is algebraic. Suppose P contains k elements and T contains m elements. By establishing an ordering on the elements of P and T (i.e., P = {p,, . . . . pk} and
T= {t,, . . . . t,}), we define the k x m addition matrix T of (P, T, cp, pO) so that
F(i, j) = cp(tj, pi) - cp( pi, tj). Thus, if we view a marking p as a k-dimensional
column vector in which the i th component is p( pi), each column t; of T is then a k-dimensional vector such that if p A p’, then ,u’= p + 4. (Note that by this convention, the notations p(pi) and p(i) are interchangeable.) For a given alphabet
C, let Y : C* + (C -+ N) be the Parikh mapping so that for 0 EC*, aEC, Y(o)(a)
is the number of occurrences of a in G . For .Z= T, we can view y(~l(a) as an m-dimensional column vector in which the j th component is Y(u(a)(tj). Then if ,u,, -5 p, p0 + T. Y(o) = p (note that the converse does not necessarily hold).
Let .9’= (P, T, cp, pO) be a PN. The reachability set of B is the set R(g) =
{p 1 p. A p for some fr }. Let c = ul, u2, . . . . u,,, ui be a circuit in the graph of 9, and let p be a marking of 9. For convenience, we will always assume u1 is a place. Let PI(C)= {u,, u3, . . . . unPI } denote the set of places in c, and let tr(c) = u2uq . . . U, denote the sequence of transitions in c. We define p(c) = CP,Ep,(cJ p(i). We say c is
token-free in p iff ,u(c) = 0. c is said to be minimal iff pi(c) does not properly include
the set of places in any other circuit. (Note that the transitions in c are ignored in this definition.) c is said to have a sink iff for some PEER(S) and some (I and p’ such that ,U -5 p’, p(c) > 0, but p’(c) = 0. c is said to be sinkless iff it does not have a sink. 9 is said to be sinkless iff each minimal circuit of 9 is sinkless. 9 is said to be normal iff for every minimal circuit c and each transition tj,
CPiE PI(C) T(i, j) > 0; i.e., no transition can decrease the token count of a minimal circuit by tiring at any marking. We say Y is persistent if for every ,u E R(B), when any pair of distinct transitions t, and t2 are both enabled at p, t, t2 is a tiring sequence from p; i.e., no enabled transition can ever be disabled by firing some other transition. 9 is said to be conflict-free iff for every place p for which there are two or more transitions t such that q(p, t) = 1, for each such transition, cp(t, p) = 1. (This definition of conflict-freedom was given in [LR78] for PNs whose flow function has a range of (0, I}; see [CRM75, HRY87, HR88, HR89] for somewhat more general definitions.) As was shown in [Yam84], the relationship of normal PNs to sinkless PNs is analogous to the relationship of conflict-free PNs to persistent PNs: normal PNs are those PNs that are sinkless for every initial marking [Yam84], while conflict-free PNs are those PNs that are persistent for every initial marking [LR78].
6 HOWELL,ROSIER, AND YEN
with that of other classes of PNs. In order to formalize the notion of a PN modeling a particular problem, such as the producer/consumer problem or the mutual exclusion problem, we adopt a language-theoretic approach (see also [Hac75]). A modeling problem Q is given by an action language L(Q) over a finite alphabet 25 of actions such that if tl E L(Q) and Z’ is a prefix of Q, then M’ E L(Q). Thus, the action language gives all possible finite sequences of actions to be modeled. Let ,Y1 and C, be two finite alphabets, and let h : CT + 2’:. If for any strings c(, /? E Z’j+, h(cwj) = h(a) h(b), then we say that h is a homomorphism. A labeled
Petri net is a tuple (P, T, cp, ,u”, 2, h), where (P, T, cp, pO) is a PN, C is a finite
alphabet, and h is a homomorphism h : T * + Z* such that for any t E T, the length
of h(t) is at most 1; we call h the labeling ,function. We define the language of a
labeled PN, L(P, T, cp, ,uO, C, h) = {h(o) / c is a firing sequence of (P, T, cp, p”)}. In order to formally define what it means for a PN to model a problem, we would like to identify the language of a labeled PN with the action language of the problem. However, we must also ensure that for any tiring sequence CJ that models a sequence of actions that can be extended, Q can also be extended in the same manner. Therefore, we say a PN 9 models a modeling problem Q with action alphabet Z iff there is a labeled PN 9 = (Y,Z, h) such that L(Y) = L(Q) and for any string c(,c(~E L(Q), if o1 is a firing sequence of 9 such that h(a,) = r,, then there is a firing sequence 01cr2 of B such that h(a,) = z2.
Aside from examining the modeling power of various classes of PNs, we also examine the computational complexities of a number of problems concerning normal and sinkless PNs. Given a marking p of a given PN 9, the reachability
problem (RP) is to determine whether ALE R(Y). The boundedness problem (BP) is
to determine whether R(Y) is finite. The sink-detection problem is the problem of determining whether there is a minimal circuit of 9 with a sink. Given two PNs 9
and Y”, the containment and equivalence problems (CP and EP, respectively) are
to determine whether R(Y) c R(9’) and whether R(9) = R(Y), respectively. In examining the latter two problems, we use concepts from linear algebra and the theory of semilinear sets. For any vector VIE Nk and any finite set V= {vl, . . . . v,) G Nk, the set Y(v,, V) = (x 1 3c,, . . . . c, E N such that x=u~+~~~=l c, vi} is called the linear set with base v0 over the set of periods V.
A finite union of linear sets is called a semilinear .set (SLS for short). If
x =x7= 1 ai. ui for some a,, . . . . a, E R, then x is a linear combination of the vectors
in V. If a,>0 for all i, then x is a nonnegative linear combination of the vectors in
V. If in addition for some i, ai> 0, then x is a positive linear combination of the vectors in V.
3. MODELING POWER
In this section, we examine the modeling power of normal and sinkless PNs, comparing it with that of conflict-free and persistent PNs. It has already been shown that the class of conflict-free PNs is properly contained in both the classes
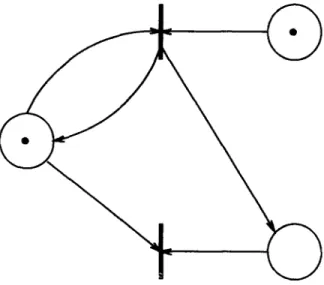
FIG. 3.1. A persistent PN that is not sinkless.
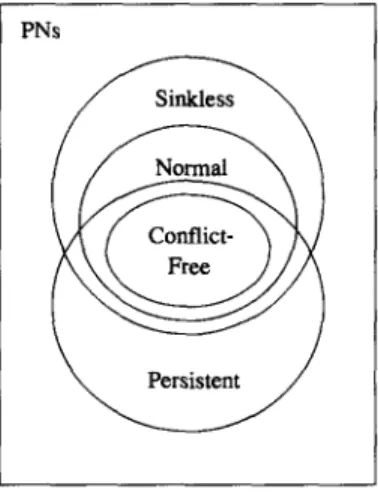
of persistent PNs [LR78] and sinkless PNs [Yam84]. Furthermore, it is clear from the definitions that the class of sinkless PNs properly includes the class of normal PNs (see also [Yam84]). On the other hand, it is not hard to see that the class of persistent PNs is incomparable to both the class of normal PNs and the class of sinkless PNs; i.e., there is a persistent PN that is not sinkless (Fig. 3.1), and there is a normal PN that is not persistent (Fig. 3.2; see also [Yam84]). These relationships are summarized by the Venn diagram in Fig. 3.3.
One of the shortcomings of conflict-free and persistent PNs is that their modeling power is severely limited. By the definition of persistence, only a very limited type of nondeterminism is allowed: if more than one transition is enabled, the next transition to fire may be nondeterministically chosen, but the firing of this transition
HOWELL, ROSIER, AND YEN
PNs PNs
I
FIG. 3.3. Relationships between Petri net classes.
cannot disable any others. Although there are modeling problems, such as a simple version of the producer/consumer problem, that can be modeled by conflict-free PNs, the severely restricted version of nondeterminism prohibits even persistent PNs from modeling many “interesting” problems. In particular, we show that neither a more general producer/consumer problem nor the mutual exclusion problem can be modeled by persistent PNs. Given these limitations of persistent PNs and the fact that there are normal PNs that are not persistent, it is natural to ask whether normal PNs can model some of the classical modeling problems that persistent PNs cannot. In this section, we show that although the mutual exclusion problem cannot be modeled even by sinkless PNs, the generalized producer/consumer problem and a version of the mutual exclusion problem in which the total number of exclusions in any computation is bounded by a fixed constant both can be modeled by normal PNs (and, hence, by sinkless PNs). On the other hand, we show that persistent PNs cannot even model one exclusion. In the next section, we will present evidence that sinkles PNs may be significantly easier to analyze than persistent PNs, but not significantly more difficult to analyze than normal PNs. These results suggest that sinkless PNs may be a more useful class of PNs than many of the classes that have been studied in the past.
We first introduce a simple version of the well-known producer/consumer problem PC,, 1. Informally, the problem involves two processes, the producer and the consumer, and an unbounded buffer. The producer iterates a loop consisting of a sequence of two actions, produce (denoted p) followed by send (denoted s). Thus, in any computation, the number of produces is never less than the number sends
and never exceeds the number of sends by more than one. Meanwhile, the consumer iterates a loop consisting of a sequence of two actions, receive (denoted r) followed
by consume (denoted c). Finally, the number of receives can never exceed the
that Y(a)(a) denotes the number of occurrences of a in a, we then define L(PC1,1) as the set of all strings in Zf,, such that for any prefix CI,
l Y(a)(s) < Y(a)(p) 6 Y(a)(s) + 1;
l Y(U)(C) d Y(U)(~) d Y(a)(c) + 1; and l Y(a)(r) < Y(a)(s).
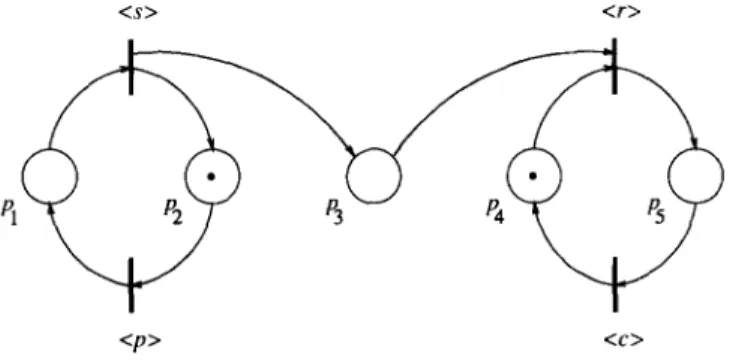
The PN shown in Fig. 3.4 is easily seen to model PC,,, and to be conflict-free. Suppose we wish to generalize the above problem to m producers and n
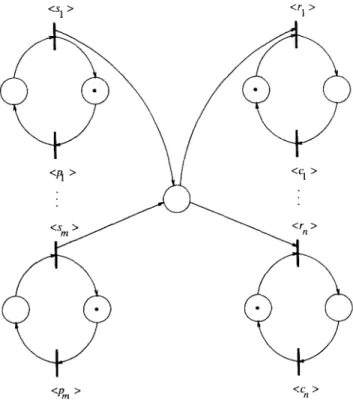
consumers. In order to be able to differentiate between actions of individual producers and individual consumers, we must define the action alphabet as C, n =
s r
[l$ i3 1’ cj ) 1 Q i < m, 1 <j< n}. We then define L(PC,,.) as the set of all strings
*
m ,n such that for any prefix a,
l Y(a)(s,) < Y(a)(p,) 6 Y(a)(s,) + 1, for 1 < id m;
l Y(a)(c,) < Y(a)(r,) Q Y(a)(cj) + 1, for 1 <j< n; and
l CJn= I Va)(rj) G CL I Y(@)(Si).
We will now show that there is no persistent PN that models PC,,,. We first reproduce the following easily shown lemma from [LR78].
LEMMA 3.1 (from [LR78]). Zf o and I+ are firing sequences of some persistent PN, then a(o’ 2 a) is also a firing sequence of that PN.
THEOREM 3.1. There is no persistent PN that models PC,,,.
Proof Suppose some persistent PN 9 models PC,,, with labeling function h.
Since p,s,r, and pIsIr, are both in L(PC,,,), there must be firing sequences oa, and aaZ of 9 such that h(a) = pIsI, h(a,) = rl, and h(a2) = r2. Since 9 is persistent, from Lemma 3.1, aa (a2 2 a,) must also be a tiring sequence of 9. Since there is no transition labeled r2 in al, h(aal (a2 1- a,)) = pIs1rIr2, which is not in L(PC,,,)-a contradiction. 1
<s> <r>
<P>
10 HOWELL, ROSIER, AND YEN
The above theorem clearly demonstrates the limitations of persistent PNs as modeling tools. We will now show that these limitations are, at least in part, eliminated by normal PNs. Consider the PN in Fig. 3.5. It is not hard to see that this PN models PC,,,.. Furthermore, it is obvious by inspection of the graph that no transition can decrease the token count of any minimal circuit, so the PN must be normal. We therefore have the following theorem.
THEOREM 3.2. For each positive m and n, there is a normal PN to model PC,,..
We have therefore seen an example of a well-known modeling problem that can be modeled by a normal PN, but not by a persistent PN. One of the fundamental building blocks for many modeling problems (e.g., readers/writers, dining philosophers) is the mutual exclusion problem. We will now examine the question of whether normal or sinkless PNs can model mutual exclusion. Informally, the n-process mutual exclusion problem ME, consists of n processes, each of which has
a critical region. Each process P, iterates a loop consisting of a sequence of two
actions: entering its critical region (denoted en,) followed by exiting its critical region (denoted ex,). Furthermore, no two processes may be in their respective
<Pm > ‘Cn >
critical regions simultaneously. Thus, the action alphabet of ME,, is C, = (en,, ex, 1 16 i< n}. We then define L(ME,) to be the set of all strings in C,* such that for any prefix a,
l Y(U(a)(ex,) d Y(~)(en,) ,< Y(V(cc)(exi) + 1, for 1 d i < n; and l Cy=, (Y(@.)(Wi) - Y(a)(ex,)) d 1.
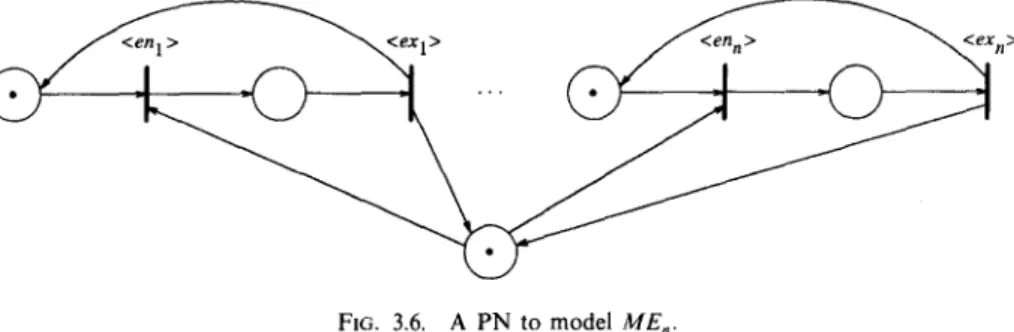
Figure 3.6 shows a PN that models ME, for any n > 2. It can be shown that this PN is neither persistent nor sinkless. In fact, the following theorem can be shown in a manner similar to Theorem 3.1.
THEOREM 3.3. There is no persistent PN that models ME,.
We now show that there is also no sinkless PN to model ME,. We first reproduce the following lemma from [Yam84].
LEMMA 3.2 (from [Yam84]). Let 9 = (P, T, cp, p,,) be a PN with k places and m transitions. For each w E N”‘, there is some firing sequence rs of 9 with Y(a) = w if
1. po+ T.waO, and
2. for each firing sequence a’ of 9’ and each circuit c, if Y(a’ tr(c)) d w, then
p(c) > 0, where ,a,, -5 p.
THEOREM 3.4. There is no sinkless PN that models ME2.
ProojI Let .!? = (P, T, cp, pO) be any PN that models ME, with labeling function
h. Since (enI exl)* G L(ME,), for each positive k there must exist a ek such that
h(a,)=en,ex, and o1 ... (TV is a firing sequence of 9. Consider the infinite sequence
of markings pi, p2, . . . . where ,u~-, -% pLk. As was shown in [KM69], it follows from Kdnig’s infinity lemma [Kon36] that there exist positive i and j such that
i-=zj and pLi<pji. Let z,=(T~.‘.(T~, ~~=cr~+~ . . . aj, and w = Y(T~). Then T. w > 0.
Since (en,ex,)Jen, E L(ME,), there must be a r3 such that h(z,)=en* and
P O z /I’ for some $. Since h(z,T,z,)E (en, ex,)*en, and h(r2)E (en,ex,)+, there
is no 0 firable at p’ such that Y(a) = w. Therefore, either condition (1) or condition
12 HOWELL, ROSIER, AND YEN
(2) of Lemma 3.2 must fail for (P, T, cp, $) and w. Since T. w > 0, condition (1) must hold. Thus, there must be a 0’ and a circuit c such that Y(o’ tr(c)) < w and p(c) = 0, where p’ -% p. Consider the firing sequence r = r i r2r3c’ of 9. Clearly, p0 i p. Since p(c) = 0, some subset of pi(c) is the set of places on a minimal circuit with a token count of 0 in ,u. However, since Vl(tr(c)) 6 w = Y(r,), and since t2 has already fired in r, each of the places in pi(c) must have had a positive token count at one time in t. Thus, r decreases the token count of some minimal circuit to 0, and 9” is not sinkless. 1
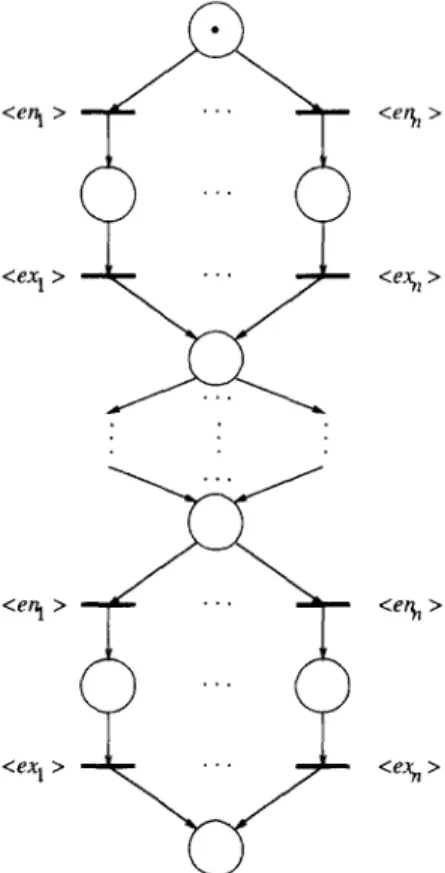
We conclude this section by noting that by using a proof similar to that of Theorem 3.1, it can be shown that there is no persistent PN to model the problem whose action language is all prefixes of eniex, and en,ex,. In contrast, there is a normal PN to model this problem. In fact, Fig. 3.7 shows a normal PN to model the problem ME:, for any positive k and n, defined so that L(MEt) =
{R 1 c1 E L(ME,) and x1=, Y(ct)(eni) < k}. Th us, normal PNs can be used to model mutual exclusion if the total number of exclusions is bounded by a fixed constant. We therefore have the following theorems,
<exl > . ,::( <ex, > . <eT > . 61 <es > <ext > . v <es >
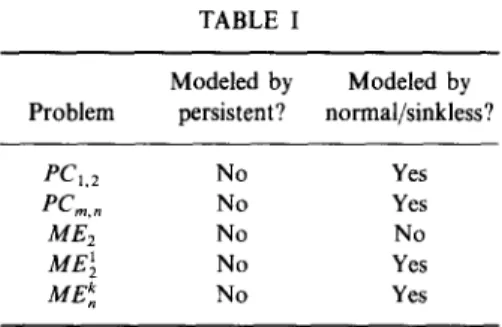
TABLE I Problem Modeled by Modeled by persistent? normal/sinkIess? PC,,* No fen,” No ME2 No MEi No ME; No Yes Yes No Yes Yes
THEOREM 3.5. There is no persistent PN to model ME:.
THEOREM 3.6. For each positive k and n, there is a normal PN to model MEf:.
The results of this section, summarized in Table I serve to demonstrate that even though the modeling power of sinkless PNs is still quite limited, even normal PNs provide a more usable version of nondeterminism than persistent PNs.
4. COMPLEXITY RESULTS
In this section, we examine the complexities of various problems involving normal and sinkless PNs. In [HR88], we developed several techniques for analyzing conflict-free PNs. These techniques relied heavily upon the structural property of conflict-freedom. In this section, we show that these same techniques also apply, albeit in a more sophisticated manner, to sinkless PNs, a class defined not in terms of structure, but in terms of behavior.
We begin by developing an important lemma (Lemma 4.3) which will be used in deriving most of the upper bounds in this section. In [HR88], we showed that for any conflict-free PN B and any marking p of 8, there is an instance of integer linear programming that has a solution iff ~1 is reachable in 9. Furthermore, we showed that this instance of integer linear programming can be guessed in polyno- mial time. It therefore followed that the reachability problem for conflict-free PNs is in NP. We will show in Lemma 4.3 that a similar fact holds for sinkles PNs. In so doing, we make use of the following lemma which follows immediately from Lemma 3.2 and was first stated in [Yam84].
LEMMA 4.1 (from [Yam84]). Zf a PN8= (P, T, rp, pO) has no token-free
circuits in every reachable marking, then R(B) = {p 1 ,a = p0 + T. x B 0 for some
XE N”}, where m is the number of transitions in T.
The above lemma gives an instance of integer linear programming whose solution set gives the reachability set of a PN. The only requirement is that no reachable marking can have a token-free circuit. In order to enable us to work with PNs
14 HOWELL, ROSIER, AND YEN
whose reachability sets contain no markings with token-free circuits, we give the following lemma.
LEMMA 4.2. Let 9 = (P, T, cp, uO) be a sinkless PN, and let 9’ = (P, T’, cp’, u) be
such that u,, --% u in 9 for some 0, T’ c T such that each t E T’ is enabled at some point in the firing of o from uO, and cp’ is the restriction of cp to (P x T’) v (T’ x P).
Then 9’ has no token-free circuits in every reachable marking.
Proof Suppose 9” has some reachable marking p’ with a token-free circuit c’.
Since $ is reachable in Y’, it must also be reachable from p in Y. Let 00’ be a firing sequence of 9 such that pLg 4-, p bl p’. Also, since c’ is a circuit in Y’, it must also be a circuit in 9. Thus, there must be a minimal circuit c of 9 such that pi(c) E pl(c’). Clearly, p’(c) = 0. Let p be any place in c, and let t be the transition following p in c’. Since t E T’, t must have been enabled at some marking p” reached in the firing of 0 from p0 in Y. Thus, p”(p) > 0, so u”(c) > 0. Since p’(c) = 0 and p’ is reachable from p”, c has a sink-a contradiction. 1
Given the above two lemmas, we can now outline our strategy for showing the RP to be in NP, and the BP to be in co-NP. This strategy will then be the basis for most of the other upper bounds shown in this paper. Let 9 = (P, T, cp, uO)
be a sinkless PN, and consider the sequence 9,) . . . . gn, where each Y,‘, =
(P, T,,, (P,,, php,) such that T,= fa, and for 1 d h<n,
l T,=T,_,u(t,,} for some t,,,$Th-, enabled at pLhp,, for l<h<n;
l (Pi is the restriction of cp to (P x Th) u (T, x P), for 0 6 h < n; and ’ ph-I auh for some ~,-,ET,*, l<h<n.
From Lemma 4.2, no & Contains a token-free circuit for any marking in R(ph).
Thus, from Lemma 4.1, there is an instance of integer linear programming Sh whose solution set describes the reachability set of ph. Furthermore, Sh can clearly be constructed from Yh in polynomial time. Also note that the initial marking of gh is given by a solution to Sh ~, . Thus, a portion of R(B) can be given by the solution set of a system S of linear inequalities over the integers, where S is constructed in polynomial time from P and a sequence of distinct transitions of 9. To formalize these ideas, let P= (pl, . . . . pk}, T= {tl, . . . . t,}, and let r = tj, ... tjn be any sequence
of distinct transitions from T. We define the characteristic system of inequalities for
B and f as S(Y,r)=&u ... US,,, where SO=(xO=pO}, Sh=(xhml(i)3
cp(p,, t,,), xh=xh-I+Ah’y,, / l<ibk}, and Ah is the kxh matrix whose COhmnS
are i- I,, . . . . ijh for 1 < h d n. The variables in S are the components of the k-dimen- sional column vectors x0, . . . . x, and the h-dimensional column vectors yh, 1 f h d n.
We will now show that for any marking p, PER(Y) iff there is a sequence of distinct transitions t = tj, . . tin such that S(Y, T) has a nonnegative integer solution
in which x, = ~1. It is precisely this fact that allows us to apply the techniques of [HR88], developed specifically for the structurally defined conflict-free PNs, to the behaviorally defined sinkless PNs.
LEMMA 4.3, Let 9 = (P, T, cp, puo) be a sinkless PN, and let ,u be any marking of 9’. Then there is some CJ E T* such that pO 4 p
iff
there is some sequence T = tj, . . . tjnof distinct transitions in T such that $9, z) has a nonnegative integer solution in which x, = p. Furthermore, o and z can be chosen such that o = a, . . . o,,, where pO=x04$ x,2 ...a x,=p, ti, is enabled at xh-,, o,,E It,,,..., tJh>*, and y,,(h’) gives the number of times tj,,, occurs in oh, for 1 d h’ < h 6 n.
Proof: (+) Let ,u E R(9). Then for some D E T *, p,, 4 p. Let 0 = 6, . . . (I,, such that for 1 <h <n, IJ~ begins with some transition t, that does not occur in 01 “.tr,,-,, and G,, contains only transitions from the set (t,,, . . . . t,,}. Let T = tj, . . . tjn, By letting y, (h’) be the number of times tjh, occurs in oh, 1 6 h’ 6 h d n, it is easily seen that S(P, r) has a nonnegative integer solution for which p(yxgL x1 3 . . .a x, = p.
(e) We will show by induction on n that for any sequence ~~ = tj, ... tjn of n distinct transitions from T and any marking p, if S(P’, 7,) has a nonnegative integer solution for which x, = p, then p0 = x0 3 x, -J% . .a x, = p such that tjh
is enabled at xh-, , rr,, E { tj,, . . . . t,*}*, and tjhs occurs y,(h’) times in ch for 1 d h’ 6 h 6 n. The lemma will then follow.
Base. Let n = 0. Then S(9, zO) = { x0 = pO}. Clearly, the only solution to S is ,u~, and ,n,, A pO.
Induction hypothesis. Let n be some positive integer, and assume that for any sequence of distinct transitions z, _, = tj, . . . t,.-, from T and any marking p, if S(P, rnP ,) has a nonnegative integer solution in which x,- I = ,u, then ,u~ = x02x,& . ..m xnpl = ,u such that tjh is enabled at xhP,, ch E { tji, . . . . t,,} *, and tjh8 occurs y,(h’) times in c,, for 1 < h’ 6 h d n - 1.
Induction step. Let z,, = tj, .. tjn be a sequence of distinct transitions in T, ,u be any marking of 9, z,-, = tj, ... tjn-,, and T’ = ( tj,, . . . . tjn}. Then S(9, T,) = S(~,T,-~)U{X,-~(i)~~(Pi,tj~),Xn=Xn~~+T’.ynI l<i<k}. SuppOseS(~‘,~,) has a nonnegative integer solution in which the value of x, is /A. Since any solution to S(P?, 7,) is clearly a solution to S(9, r,- ,), from the induction hypothesis,
pLg=xg~ x1 02 . . .01;1 x, ~ I such that tin is enabled at xh- r, ah E { tj,, . . . . tjh} *, and tjh, occurs yh(h’) times in a,, for 1 dh’,<h<n- 1. Let a’=a,...a,pl. Since x,- I (i) 2 (p(pi, tjJ for 1 6 id k, tjn is enabled at x, _, . Thus, each t E T’ is enabled at some point in the firing of a’ from pO, so from Lemma 4.2, (P, T’, cp’, x, ~ 1 ) has no token-free circuits in every reachable marking, where rp’ is the restriction of cp
to (PxT’)u(T’xP). Since ,~=x,=x,_r+T’.y, for some yn~N”, from
Lemma 3.2, x, _ I 2 x, = p for some an E T’* containing y,(h’) occurrences of t,*, for 1 <h’<n. Thus, p,,=xO-% x,2 . . .A x, = p such that tj,, is enabled at xh ~ 1,
ahE {tj,, ...> tj*}*, and tjh, occurs y, (h’) times in ah for 1 d h’ < h < n. 1
The following corollary follows from Lemmas 4.1 and 4.2 and the proof of Lemma 4.3.
16 HOWELL,ROSIER, AND YEN
COROLLARY 4.1. Let 9 = (P, T, rp, pO) be a sinkless PN, f be a sequence of n distinct transitions from T, T’ be the set of transitions in 5, cp’ be the restriction of ‘p to (P x T’) u (T’ x P), and u be any marking of 9 such that for some nonnegative integer solution of S(S, z), x, = u. Then R(P, T’, cp’, p) = {u’ ) u’ = u + T’ x for some xEN”).
Lemma 4.3 can now be coupled with the fact that integer linear programming is in NP [BT76] to show that the RP for sinkless PNs is in NP. Since the RP is NP-hard for conflict-free PNs [JLL77], it will then follow that the RP for sinkless (normal) PNs is NP-complete. We therefore have the following theorem.
THEOREM 4.1. The RP for sinkless (normal) PNs is NP-complete.
Proof From [JLL77], the RP for conflict-free PNs is NP-hard. Since any
conflict-free PN is normal [Yam84], it follows that the RP for normal PNs is NP-hard. Since any normal PN is sinkless, we need only show that the RP for sinkless PNs is in NP. We use the following nondeterministic algorithm to decide the RP for any given PN B = (P, T, cp, ,D~) and any marking p of 9. First, guess a sequence r of n distinct transitions from T. Then construct S(y’, t) in polynomial time. Next, construct S = S(g, r) u {x,, = p}. Since integer linear programming is in NP [BT76], we can guess a solution to S and verify it in polynomial time. Clearly, S has a nonnegative integer solution iff S(g’, r) has a nonnegative integer solution in which x, = p. From Lemma 4.3, there is a r such that S(p”, z) has a nonnegative integer solution in which x, = p iff p E R(9). Therefore, the RP for sinkless (normal) PNs is NP-complete. m
In [HRY87], we showed the BP to be PTIME-complete for conflict-free PNs. However, we will now show the problem to be co-NP-complete for both normal and sinkless PNs.
THEOREM 4.2. The BP for sinkless (normal) PNs is co-NP-complete.
Proof We first show the BP for sinkless PNs to be in co-NP. We use the
following nondeterministic algorithm to decide, for any given PN B = (P, T, cp, u,,),
whether 9 is unbounded. First, guess a sequence t of n distinct transitions from T.
Then construct S(g, r) in polynomial time. Next, construct S= S(B, z) u {T’ .z >O}, where T’ is the set of rules in t. As in Theorem 4.1, we can guess a solution to S and verify it in polynomial time. Suppose S has a nonnegative integer solution, and let p be the value of x, and 1+5 be the value of z in that solution. From Lemma 4.3, p E R(9), and from Corollary 4.1, p + T’ .$ is reachable from p. Thus, since T’ $ > 0, 9 must be unbounded. On the other hand, suppose 9 is unbounded. From [KM69], there is a firing sequence (~0’ of ?? such that T. Y(o’) > 0. Let pL, 3 p. From Lemma 4.3, there is a choice of r for which there is a nonnegative integer solution of S(y’, r) in which x, has the value p, and for which all transitions in cel. appear in z. Thus, we can clearly set z to a value that gives us a nonnegative integer solution to S. Therefore, there is a choice of r for
which S has a nonnegative solution iff ?? is unbounded. It follows that the BP is in co-NP.
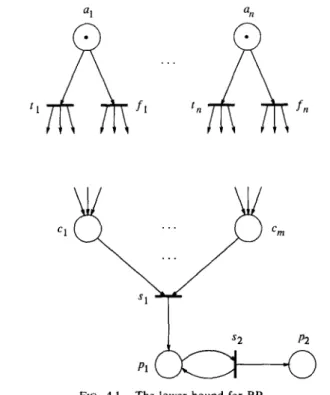
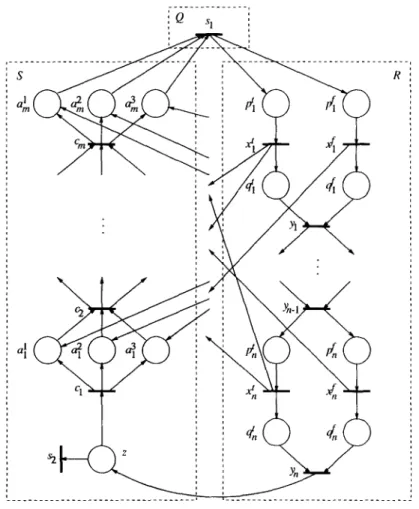
We now show that the BP for normal PNs is co-NP-hard. We show this by reducing 3SAT to the complement of BP. Let C = (C, , . . . . C, } be the set of clauses and V= (xi, . . . . x,} be the set of variables in an arbitrary instance of 3SAT, where C;= {ail, cli2, ai3} and C~~E {x, X 1 XE V} for 1 di<m, 1 <j<3. We construct a normal PN B = (P, T, cp, p,,) (shown in Fig. 4.1) such that 9 is unbounded iff C is satisfiable (i.e., if there is an assignment of truth values to V such that AyE, V;=, tlii is true). For each variable xj, let uj be a place for which ~~(a,) = 1. We then define transitions tj and fi for 1 <j < n. tj and fj both have aj as an input place; thus, since
uj will not be the output place of any transition, tj and f, cannot both fire in any firing sequence. For each clause Cj, let ci be a place such that p,,(ci) = 0. For
1~ i < m and 1 < j d n, tj will have ci as an output place iff xj E Ci, and fi will have cj as an output place iff Xj~ Ci. Since no ci will be an output place for any other transitions, all of the cis can become simultaneously positive iff C is satisfiable. Finally, we define the transitions s1 and s2 and the places pi and p2 as shown in Fig. 4.1. The resulting PN is clearly normal, and is unbounded iff C is satisfiable. Therefore, the BP is co-NP-complete for sinkless (normal) PNs. 1
We can also use Lemma 4.3 to show the sink detection problem for PNs to be NP-complete.
18 HOWELL,ROSIER, AND YEN
THEOREM 4.3. The sink detection problem ,for PNs is NP-complete.
Proof Our nondeterministic algorithm for this problem is similar to those for
the RP and the BP. Given 9 = (P, T, cp, pO), we guess z = t,, . . . tjn and a minimal circuit c. We can clearly verify in polynomial time that c is a circuit. Furthermore, we can verify that c is minimal by verifying for each pair of places p and p’ in pi(c) and each transition t in T that cp( p, t) = cp(t, p’) = 1 only if p, t, p’ is a segment of c; this verification can clearly be done in polynomial time. We then guess an integer
m, 1 d m < n, and a marking p such that p(c) = 1 and p(p) = 0 for all p ef pi(c). We then construct S=S(B,r)u{x,(c)=O, ydy,,x,~,+A,.y>,~}), where A,,, is the matrix whose columns are t,,, . . . . i,m. We claim that there is some choice of z, c, m, and ,n for which S has a nonnegative integer solution iff 9 has a sink.
First, suppose that for some choice of z, c, m, and p, S has a nonnegative integer solution. In order to derive a contradiction, assume 9 is sinkless. From Lemma 4.3, there is a nonnegative integer solution of S such that pLo = x,, 2 x, 3 . . -% x,, and each t,, is enabled at x,,, for some g1 . on E T*. Consider 9’ =
(P, T’, (p’,x,,-,), where T’= {ti,, . . . . tjm} and cp’ is the restriction of cp to (P x T’) u
(T’ x P). Since each transition in T’ is enabled at some point in the firing of 01 .“O,-1 from pO, from Lemma 4.2, 9’ has no token-free circuits in every reachable marking. Thus, from Lemma 4.1, there is some g E T’* such that
0
x, ~ , -+ x, ~ 1 + T’ . y = p’ for some p’. Since T’ = A,, p’ > p, and hence, p’(c) > 0. Since y d y,, Lemma 4.2 also guarantees that there is some CJ’ E T’* such that p’ql’+ T’.(y,- y)=xm. Thus, PO- 6,...rTm-,” P’ “‘Urn+, .‘cT” + X”, where x,(c) = 0. Thus, 9 has a sink-a contradiction. Therefore, if there is some choice of z, c, m, and p such that S has a nonnegative solution, 9’ must have a sink.
Now suppose 9 has a sink. Then there exist ~1’ and p” and a minimal circuit c such that p’(c) > 0, p”(c) =O, and p0 -% 11’s p” for some CJ~’ E T*. From Lemma 4.3, there is a z, of m transitions, m > 0, such that S(9, zI) has a nonnegative integer solution in which x, = $. We may assume without loss of generality that m 2 1, since at least one transition t must be enabled at p0 (because $#$‘). Since $(c)>O, x,(c) 3~ for some p such that p(c)= 1 and p(p)=0
for all p 4 pi(c). By proceeding as in Lemma 4.3, it is not hard to see that there is a z2 of n -m transitions, n >, 1, such that S(Y’, z, r2) has a nonnegative solution in which x, = $’ and x,~ , + A,,, y = p’, where A, is the addition matrix formed from the transitions in z1 and y< y,. Thus, S=S(Y,t,r,)u (x,(c)=O, y<y,,
x,-,+A; y>, p} has a nonnegative integer solution. Therefore, there is some
choice of z, c, m, and p for which S has a nonnegative integer solution iff 9 has a sink. We will now show the sink detection problem to be NP-hard. We again use a reduction from 3SAT. Let C = (C,, . . . . C,} be the set of clauses and
v= (x1, . ..) x,} be the set of variables in an arbitrary instance of 3 SAT. Consider again the PN 9 constructed in the proof of Theorem 4.2 (Fig. 4.1). We construct 9’ from 9 by adding a transition s3 with input place p, and no output places. Thus 9” has a sink iff p1 can become positive iff C is satisfiable. Therefore, the sink detection problem is NP-hard. 1
THEOREM 4.4. The problem of determining whether a PN is normal is co-NP- complete.
ProoJ: In order to show that a given PN .Y = (P, T, cp, p,,) is not normal, we need to find a m inimal circuit c and a transition tj such that CP,E p,(cj T(i, j) < 0. The proof of Theorem 4.3 shows how we can guess a m inimal circuit c and verify that it is m inimal in polynomial time. Clearly, we can also guess a transition t, and verify that C,, E pl(c) T(i, j) < 0 in polynomial time. Thus, the problem is in co-NP.
We will now show the problem to be co-NP-hard. We do this via a reduction from 3 UNSAT (the complement of 3 SAT). Let C = {C,, . . . . C,} be the set of clauses and V= (x,, . . . . x,} be the set of variables in an arbitrary instance of 3 UNSAT, where Ci= {cli,, aiz, ai3} and aijE {x,X 1 XE V) for 1 Gidm, 1 <j<3. We construct a PN 9 = (P, T, q, pO) (shown in Fig. 4.2) that is normal iff C is not
20 HOWELL, ROSIER, AND YEN
satisfiable. In considering whether a PN is normal or not, it is convenient to view the PN as simply a directed bipartite graph; places and transitions are differentiated only in connection with their respective roles regarding minimal circuits. The initial marking is therefore irrelevant and will be chosen to be the zero marking. The graph will contain a special place z such that 9 will be normal iff z is not on a minimal circuit. Our objective will then be to show that z is on a minimal circuit iff C is satisfiable. The graph will consist of three components Q, R, and S, each of which will be acyclic. Furthermore, the three components will be interconnected in such a manner that any cycle in the graph must contain vertices from each of the three components. We will first describe each of the three components, then describe how they are interconnected.
Q is the simplest of the three components, consisting of only a single transition si. Component R is defined in terms of the set V. For each xj E V, R contains the places pj, p!, ?f , and qf, and the transitions XI, XT, and yj. These places and transitions are mterconnected as shown in Fig. 4.2 so that R is acyclic, and any path within R contains at most one of the two transitions xi and .x; for each j. Component S is defined in terms of the set C. For each C, E C, S contams the places a,!, a;, and a:, plus the transition c,. In addition, S contains the place z and the transition s2. The places and transitions are interconnected as shown in Fig. 4.2 so that S is acyclic, and any path within S contains at most one of the places a,l, uf, and a;’ for each i.
We now add edges to the graph to interconnect the three components. We first add the edges (sl, P:), (sly P{), (Y,, z), (a;, sl), (ai, sl), and (ai, sl). These edges have the effect of creating a number of circuits, each of which contains s, , z, exactly one of xj or xi for each variable xj, and exactly one of at, uf , or UT for each clause Ci. Next, we add additional edges from R to S, each of which “short-circuits” some of the previously created circuits. For each literal aik in each clause in C, we add the edge (xf, UC) if aik =xj, or the edge (xj, ur) if aik = Xi. Thus, none of these newly created circuits contains z, but all contain s, .
We will now show that the PN 9 constructed above is normal iff z is not on a minimal circuit. If 9 is normal, z clearly must not be on any minimal circuit c, since transition s2 would then have an input place in pi(c) but no output place in pi(c). On the other hand, suppose z is not on a minimal circuit. In order to derive a contradiction, assume there is some minimal circuit c and some transition t such that t has an input place in pi(c) but no output place in pi(c). Notice that z is the only place in 9 that is an input place to more than one transition. Since z 4 pi(c), this implies that t is in the circuit c. Therefore, t must have an output place in pl(cta contradiction. Thus, 9 is normal iff z is not on a minimal circuit.
We conclude the proof by showing that z is on a minimal circuit iff C is satisfiable; it will then follow that 9 is normal iff C is not satisfiable. First suppose z is on a minimal circuit c. Since any circuit containing z must contain exactly one of xf or i;i’ for each variable xj, consider the truth assignment such that xj is true
iff x; is m c. Let ci be an arbitrary clause in C. Since any circuit containing z contains exactly one of ~1, at, or a:, let a: be on c. Suppose uik = xi (the case in
which aik =3j is symmetric). Then there is an edge from xjf to a:. Since c is a minimal circuit, xJ must be on c, so aik has been assigned a value of true. Thus, each clause evaluates to true, so C is satisfiable. Conversely, suppose C is satisfiable. Then for any satisfying assignment, there must be some circuit containing xi if xj
is true in that assignment, xif if xj is false in that assignment, some place at such
that aik is true with that assignment for each clause C;, and the place z. In order to derive a contradiction, assume c is not minimal. Then there must be some edge from a transition in R, say (without loss of generality) xi, to some place in S, say a:, such that pf (and hence xJ) and u: are both on c. Since x,’ and a; are both on c, xi and ai must both evaluate to true. However, since there is an edge from xi to a:, ai = Zj-a contradiction. Therefore, z is on a minimal circuit iff C is satisfiable, and hence, 9’ is normal iff C is not satisfiable. 1
We conclude this section by showing the CP and EP for normal and sinkless PNs to be ZZl-complete, where n: is the class of languages whose complements are in the second level of the polynomial-time hierarchy (see, e.g, [Sto77]). The strategy we use is again similar to that developed in [HR88] (see also [HRHY86, Huy863). Recall that sinkless PNs have effectively computable semilinear reachability sets [Yam84]. We use Lemma 4.3 to give an upper bound on the size of the SLS representation of the reachability set of a given sinkless PN. Although the CP and EP for SLSs are known to be Z7:-complete [Huy82], the bound on the size of the SLS representation of the reachability set must be at least exponential in the sizes of the PNs even for conflict-free PNs (see [HR88]). However, as is the case with conflict-free PNs [HR88], we can show that for sinkless PNs the SLS representa- tion can be chosen to have a high degree of symmetry. Proceeding as in [HR88], we use this symmetry to show the CP (and, hence, the EP) to be in n:. Since the EP is known to be Z7;-hard for conflict-free PNs [HR88], the CP and EP will have then been shown to be Z7:-complete for sinkless and normal PNs. The following lemma gives an SLS representation of the reachability set of a sinkless PN. The strategy follows that developed in [HR88].
LEMMA 4.4. Let 9 = (P, T, cp, p,,) be a sinkless PN with k places and m transi-
tions such that no component of p,, is larger than n > 1. Then there exist constants
cl, c2, dI, and d,, independent of k, m, and n, such that R(Y)= UrGB 8(p, p,),
where /I is the set of all reachable markings with no component larger than
(c, .k.m.n)“z’k.“‘, and pp is the set of all 6 E Nk such that:
1. forsome JET*, pAp+o;
2. 6 has no component larger than (d, . k .rn .n)d2’k’m;
3. ifp(i)=O, then 6(i)=O, for 1 <i<k; and
4. 6 # 0.
Proof: Clearly, lJMEB 9(~, p,) c R(B). We therefore only need to show that
22 HOWELL, ROSIER, AND YEN
that p’(i) = 0 if p(i) = 0, ~‘(1’) = 1 otherwise. From Lemma 4.3, there is some sequence T of m’ <m distinct transitions from T such that S(9, r) has a solution in which x,, = p. Let 22 denote this solution, and let T’ be the set of transitions in 2. Clearly, the system S = S(9, r) u {x m, 2 @} must have .jZ in its solution set. Let pL1 be the value of x,, in some minimal solution j 6 i. Also, let d E T’* be the firing sequence given by 2 according to Lemma 4.3, and let co E T’* be the firing sequence likewise given by 9. Thus, p0 -% p, d p, each transition in T’ is enabled at some point in co, and Y(cr,,) < Y(o) (in this proof, Y is defined in terms of T’, not T). Furthermore, since p’ f pi 6 p, pi(i) = 0 iff ~(1’) = 0, 1 d i d k. From results in [Huy82, VzGS78] involving integer linear programming, there exist constants c, and c2 such that no component of 11, is larger than (c, . k. rn. .)cz-k ‘m. Note that since n > 1, c, and c2 are independent of p’, and hence of p. If we now assign the values of ci and c2 to the constants (of the same name) in the definition of p given in the statement of the lemma, then p, E 8.
We will now show that p E D%(p, , pfl,); i.e., we will exhibit a series of vectors 6,) . . . . 6, such that each 6i~ pp, and ,u, + Cj=, 6, = p. Since each 6, E pr,, there will be some firing sequence ci from ~1, such that T’ Y(a,) = 6,. Furthermore, since each 6, > 0, it will be the case that cl0 2 p, 41, .. .a p,+ , = p. We already have that p,, -% ~1 and CL,, -% p,, where Y(o,) < Y(a) and pi <p. It will therefore be sufficient to show that for any i 2 1, if cl,, 2 pi -% ..A pu, < ,u, where pu, d pi and xi;; Y(oh) < Y(Q), then there is a 6;~ pr, and a ei in T’* such that piA pLi+6i=pi+, fp and Ck=, Y(a,) 6 Y(U). We use the fact that every transition in T’ is enabled at some point in the firing of e0 from pO; thus, from Lemma 4.2, no marking reached from 11, via transitions from T’ has a token-free circuit whose transitions all belong to T’. Let pi be such that p()sp,3... a pi<pL, where ~1~ <pj and CL=; Y(a,) < Y(e); i.e., ,u, is reached from 11, via transitions in T’. It therefore follows from Lemma 4.2 that no marking reachable from p, via transitions in T’ has a token-free circuit whose transitions all belong to T’. Since P==~~+ T’. Y(o) and pr=pO+ T’. (Cl=\ Y(a,)), ,D = pi + r’ . (Y(a) - CL=‘, (Y(a,))). Hence, from Lemma 3.2, p, A p, where Y(a’) = Y(o) - Cj,=‘, (Y(o,)). Since p > pi, T’ Y(a’) > 0. Thus, s’= (x = Y(o’), y = p - p,) is a nonnegative integer solution to the system s’ = { 7’ .x = y, y > 0). Let i’ < i be some minimal solution to S’, and let iji be the value of x and hi be the value of y in i’. From [Huy82, VzGS78], no component of ai exceeds (d, .k.m.n)“‘k’” for some constants d, 5nd d, independent of k, m, and n. Let d, and d2 be the values of the constants (of the same name) in the delini- tion of p, given in the lemma. From Lemma 3.2, there exist (T, and p,+, such that pi 2 pi+, = p, + 6, d p, and Y(a,) = $, < Y(a’) = Y(o) -xi:‘, Y(cJ,). Thus, XL=, Y(o,)< Y(a), and since p, <pi, 6;~p,,. It therefore follows that PEaPI? Pfl,). I
The property of conflict-free PN reachability sets that allowed the CP to be shown to be in UC in [HR88] is that their SLS representations have a certain symmetry. In particular, for any two markings p and p’ of a conflict-free
PN 9 = (P, T, cp, p,,) such that p(i) = 0 iff p’(i) = 0, if p A p + v for some 0 E T*
and some u 2 0, then there is some 6’ E T* such that ,u’ 2 p’ + u. The following lemma shows that a similar symmetry extends to sinkless PNs.
LEMMA 4.5. Let p and p’ be reachable markings of a sinkless PN B =
(P, T, cp, pO) with k places such that p(i) = 0 iff p’(i) = 0. For any vector v E Nk such
that v(i) = 0 if ,u(i) = 0, if there is a CJ E T* such that ,u -% p + v, then there is a
CT’ E T* such that p’ -% p’ + u.
Proof: Suppose there is a (T E T* such that ,u -% p + u, but no c’ E T * such that
p’ z p’ + v. From Lemma 3.2, there is a IS” E T* and a circuit c in 9 such that Y(g)’ tr(c)) < Y(u(a) and p”(c) = 0, where p’s ,u”, Let c’ be a minimal circuit of 9 such that pl(c’) ~pl(c), and let pi~pl(c’). Since p”(c’)=O and S is sinkless, ,u’(c’) =O, and hence, p(c))=0 and (,u + u)(c’) =O. Since each transition in tr(c’) occurs in 0, pi must have been nonzero at some point in the firing of (T from p. At this point,, c’ is not token free. Therefore, 9 has a sink-a contradiction. 1
Now that we have given a convenient SLS representation of the reachability set of a sinkless PN and shown the symmetry therein, we can outline our strategy for showing the CP and EP to be in Z7:. Again, this strategy was first developed for the structurally defined conflict-free PNs in [HR88], borrowing some techniques from [Huy86];. we will use Lemmas 4.4 and 4.5 to show that this strategy also applies to the behaviorally defined sinkless PNs. Let SL, = (JllEP, Y(,u, p:) and % = UPE/?2 Z(p, p:) be the SLS representations given by Lemma 4.4 for the sinkless PNs Yr and 9, respectively. In order to show that R(Y1) & R(pl), our algorithm will prove the existence of a p E SL, - SL,. (Note that since the SLS representations are exponential in the sizes of the PN representations, the SLS representations cannot be generated by the algorithm.) Let ALE SL,. Then p E 9(p,, pi,) for some p, E /I,. If, in addition, p E SL,, then p E Z(pLz, p$) for some p1 E/I~. Note from the definition of the SLS representations in Lemma 4.4 that for any place pi, p, (i) = 0 iff p(i) = 0 iff p2 (i) = 0. Furthermore, we may assume without loss of generality that p, E R(Y1); otherwise, we will have found a witness to the fact that R(Y1) @ R(p2). Thus, from Lemma 4.5, p:, = pi,, where p:, is as defined in Lemma 4.4. So to show the existence of a p E SL, - SL,, it is sufficient to show the existence of a ,U E Z(p,, p:,) - lJrztPi Y(pZ, ~2,) for some p, E /?, , where 8; = (p’ E /j2 1 p’(i) = 0 iff p, (i) = 0). Note that once p, is chosen, we are only concerned with two period sets, p:, and p:,.
Consider two sets 9?( p,, p 1 ) and u ~2 E B Y(p2, pz). In order to show the existence of a ~~~~~~~~~~~~~~~~ Z(p,, pZ), we will consider two cases. First, suppose that every vector in p, is a positive linear combination of the vectors in p2. In [HRB], we showed that in this case there must be a PE JZ’(p,, p,) - U C12EP 9’(pLz, pZ) whose size is polynomial in the sizes of the elements of pr, p2, 8, and pr and exponential in the dimension of these vectors; i.e., the witness is small enough to be written down in space polynomial in the sizes of the representations of the PNs from which the SLSs are derived. O n the other hand, suppose some
24 HOWELL, ROSIER, AND YEN
vector in p1 is not a linear combination of the vectors in pZ. We also showed in [HR88] that in this case, Y(pl, p,) cannot be contained in U,,2EB Y(pL2, p2). We now reproduce the relevant lemmas from [HR88].
LEMMA 4.6 (from [HR88]). Let p,, p2, and fl be finite subsets of Nk, p, E Nk,
and n E N such that no integer in pI, pz, fl, or u, exceeds n. If every vector in p I is a positive linear combination of vectors in p2 and p E 9(p1, p,) - Urzeli Y(p2, pz),
then there is a ,u’ with no component larger than k(n + 1)2k+ ’ + n such that
P'EaPl, PII-U,,.$%b P2).
LEMMA 4.7 (from [HR88]). Let 6, ,u, E Nk such that 6 #O, and let p and b he finite subsets of Nk. Zf 6 is not a positive linear combination of the vectors in p, then
thereisannENsuch that~L1+n6~U,.B$P(~,p).
We are now ready to show the CP and EP for sinkless and normal PNs to be ZZC-complete.
THEOREM 4.5. The CP and EP for sinkless (normal) PNs are II;-complete.
Proof Since these problems for conflict-free PNs are known to be I7:-hard, we
need only show the problems for sinkless PNs to be in nc. Recall that Z7; is the set of all complements of languages that can be recognized by a polynomial-time- bounded nondeterministic Turing machine with an NP oracle (see [Sto77]). We will now briefly describe an algorithm for noncontainment; a similar algorithm works for inequivalence. The algorithm we describe is exactly that given in [HR88] for conflict-free PNs; the fact that it works for sinkless PNs, as we will now show, follows from Lemmas 4.447.
Let 9, and g2 be two given sinkless PNs, each having k places, and let =I = Up,cB, ~(cL~, P:,) and Sb= UpzGBz 9(pLz, pz,) be their respective SLS representations given by Lemma 4.4. We wish to establish whether there is a ~~SL,-SL,.Considerany~~SL,;i.e.,thereisa~~~B,suchthat~~~(~*,,p:,).
Let fl;={pI ALE* and p(i)=0 iff pL(i)=O}. Since for any s~p:,,6(i)=O if p2 (i) = 0, if p E SL2, p must be in U 112 E ,<; 9&, ~2,). Likewise, we can conclude that
PI(i) = 0 iff p(i) = 0 iff p*(i) = 0 for any ,u2 E /?;. Without loss of generality, assume
p, E SL, (otherwise, we have pL1 E SL, - SL,). From Lemma 4.5, for any pLZ~p;,
pE2 = p:,. Thus, in order to show that p 4 SL,, it suffices to show that
P4 Up*Ep, =!w*, P:J.
Our algorithm for noncontainment therefore operates as follows. We first nondeterministically choose one of two cases. In the first case, we guess a vector p subject to the size constraints given by Lemmas 4.4 and 4.6. Since the RP is in NP, we can verify that p E R(9r)). Using an NP oracle, we can then verify that p $ R(9*). In the other c,ase, we guess p, and 6 subject to the size constraints given in Lemma 4.4. Again, we can verify that p, E R(pl)). Using the techniques of Theorems 4.1 and 4.2, it is easily seen that membership in p:, is in NP; hence, we can verify that 6 E pi,. From Caratheodory’s theorem for cones (see, e.g., [SW70]),
if 6 is a positive linear combination of vectors in pi,, then it is a positive linear combination of at most k linearly independent vectors from p:,. The question of whether 6 is a positive linear combination of vectors in .$, is therefore in NP. Hence, we use an NP oracle to verify that 6 is not a posmve linear combination of vectors in p:,. From Lemmas 4.6 and 4.7, this algorithm has an accepting computation iff R(gI) 5Z R(Y*). 1
REFERENCES
[Bak73] H. BAKER, “Rabin’s Proof of the Undecidability of the Reachability Set Inclusion Problem of Vector Addition Systems,” Memo 79, MIT Project MAC, Computer Structure Group, 1973.
[BT76] I. BOROSH AND L. TREYBIG, Bounds on positive integral solutions of linear Diophantine equations, Proc. Amer. Math. Sot. 55 (1976), 299-304.
[CLM76] E. CARDOZA, R. LIPTON, AND A. MEYER, Exponential space complete problems for Petri nets and commutative semigroups, in “Proceedings, 8th Annual ACM Symposium on Theory of Computing, 1976,” pp. 50-54.
[CRM75] S. CRESPI-REGHIZZI AND D. MANDRIOLI, A decidability theorem for a class of vector addition systems. Inform. Process. Lett. 3 (1975), 78-80.
[Gra80] J. GRABOWSKI, The decidability of persistence for vector addition systems, Inform. Process. Lat. 11 (1980), 20-23.
[GY80] A. GINSBURG AND M. YOELI, Vector addition systems and regular languages, J. Comput. System Sci. 20 (1980), 277-284.
[Hac75] M. HACK, “Petri Net Languages,” Memo 124, MIT Project MAC, Computer Structure Group, 1975.
[Hac76] M. HACK, The equality problem for vector addition systems is undecidable, Theoret. Comput. Sri. 2 (1976), 77-95.
[HP793 J. HOPCROFT AND J. PANSIOT, On the reachability problem for 5-dimensional vector addition systems. Theoret. Comput. Sci. 8 (1979), 135-159.
[HR88] R. HOWELL AND L. ROSIER, Completeness results for conflict-free vector replacement systems, J. Comput. System Sci. 37 (1988), 3499366.
[HR89] R. HOWELL AND L. ROSIER, Problems concerning fairness and temporal logic for conflict- free Petri nets, Theoret. Comput. Sci. 64 (1989), 305-329.
[HRHY86] R. HOWELL, L. ROSIER, D. HUYNH, AND H. YEN, Some complexity bounds for problems
[HRY87] [HU79] CHuyS21 CHuy85 1 CHUYS61 [JLL77] [Kon36]
concerning tinite and 2-dimensional vector addition systems with states, Theoret. Comput. Sci. 46 (1986), 107-140.
R. HOWELL, L. ROSIER, AND H. YEN, An O(n’.j) algorithm to decide boundedness for conflict-free vector replacement systems, Inform. Procexv. Lett. 25 (1987), 27-33.
J. HOPCROFT AND J. ULLMAN, “Introduction to Automata Theory, Languages, and Com- putation,” Addison-Wesley, Reading, MA, 1979.
D. HUYNH, The complexity of semilinear sets, Elektron. Inform. Kybernet. 18 (1982), 291-338.
D. HUYNH, The complexity of the equivalence problem for commutative semigroups and symmetric vector addition systems, in “Proceedings, 17th Annual ACM Symposium on Theory of Computing, 1985,” pp. 405412.
D. HLJYNH, A simple proof for the x:,’ upper bound of the inequivalence problem for semi- linear sets, Elektron. Inform. Kybernet. 22 (1986), 147-156.
N. JONES, L. LANDWEBER, AND Y. LIEN, Complexity of some problems in Petri nets,
Theoret. Comput. Sri. 4 (1977), 277-299.
D. KGNIG, “Theorie der Endlichen und Unendlichen Graphen,” Akademische Verlagsgesellschaft, Leipzig, 1936.