行政院國家科學委員會專題研究計畫 成果報告
應用基因演算法於浮水印之最佳化
計畫類別: 個別型計畫 計畫編號: NSC91-2219-E-151-002-執行期間: 91 年 08 月 01 日至 92 年 07 月 31 日 執行單位: 國立高雄應用科技大學電子工程系 計畫主持人: 潘正祥 報告類型: 精簡報告 處理方式: 本計畫可公開查詢中
華
民
國 92 年 9 月 29 日
行政院國家科學委員會專題研究計畫成果報告
應用基因演算法於浮水印之最佳化
Application of Genetic Algorithms for the Optimization of
Digital Watermarking
計畫編號:NSC 91-2219-E-151-002
執行期限:91 年 8 月 1 日至 92 年 7 月 31 日
主持人:潘正祥
國立高雄應用科技大學電子工程系
E-mail: jspan@cc.kuas.edu.tw
一、中文摘要 本計畫提出一種在轉換域下植基於遺傳演算法之浮水印技術,其對一般之浮 水印攻擊具強健性並且含浮水印之影像品質亦被改善。 以遺傳演算法為基礎之浮水印技術很容易實作完成,我們評估遺傳演算法之 適應函數,含加入浮水印後之影像品質及總和各項攻擊之正規交互相關係數,實驗 結果證明其可抗各式各樣之浮水印攻擊並改善浮水印之影像品質。 關鍵詞:浮水印、版權保護、正規交互相關係數、遺傳演算法 Abstr actAn innovative watermarking scheme based on genetic algorithms (GA) in the transform domain is proposed. It is robust against watermarking attacks, which are commonly employed in literature. In addition, the watermarked image quality is also considered. In this paper, we employ GA for optimizing both the fundamentally conflicting requirements.
Watermarking with GA is easy for implementation. We also examine the effectiveness of our scheme by checking the fitness function in GA, which includes both factors related to robustness and invisibility. Simulation results also show both the robustness under attacks, and the improvement in watermarked image quality with GA.
Ke Key wor ds : Watermarking、Copyright Protection、
NC、Genetic Algorithm
二、緣由與目的
With the widespread use of Internet and the development in computer industry, the digital media, including images, audios, and video, suffer from infringing upon the copyrights with the digital nature of unlimited copying, easy modification and quick transfer over the Internet. In this paper, we concentrate our research topic on image watermarking for copyright protection.
Digital watermarking for images is one way to embed the secret information, or the
watermark, into the original image itself to protect the ownership of the original
sources [1]. Typical schemes were based on transform-domain techniques with discrete cosine transform (DCT) [2], spatial-domain techniques [3], and VQ domain techniques [4], to embed the watermark into certain coefficients. We make use of the genetic algorithm (GA) [5] into our DCT-based watermarking system to optimize the watermarked image quality along with the robustness of the watermark under intentional attacks.
Let the input image be X with size M×N. Our goal is to embed a robust watermark into DCT of X , and have a watermarked reconstruction X′ after optimization.
Assume that the binary-valued watermark to be embedded is W , having size
W
W N
M × . We perform the 8×8 block DCT on X first and get the coefficients Y .
Afterwards, we are able to embed the watermark in the DCT domain. A pseudo-random number traversing method 錯誤! 找不到參照來源。 is applied to permute the watermark to disperse its spatial relationships; with a pre-determined key,
0
key , in the pseudo-random number generating system, we have the permuted watermark W ,P
(
,key)
. permuteW 0WP = (1)
And we use WP for embedding the watermark bits into the DCT coefficients.
To embed the binary watermark into the original source, we need to adopt some relationships, or the polarities, P , between Y and W . Assume that the P 64 DCT coefficients in the 8×8 block (m,n) of X can be represented by
{
( )}
, 1 8,1 8. 63 0 ) , ( ) , ( M N k n m n m = Y k ≤m≤ ≤n≤ =U
Y (2) The frequency set, F , will be chosen
randomly to embed W . For each P 8×8 image block, only
(
MMWNNW)
⋅ ⋅
×
64 coefficients will be included in the frequency set, F , and it can be expressed by
{
}
UU
8 8 1 1 ) , ( ) , ( ( ) ( ) M N m n n m n m i Y k F = = = = F (3)where k=1,2,L,63 , and i=0,1,L,
(
64⋅MMW⋅N⋅NW −1)
are the randomly selected(
MN)
N MW W ⋅⋅ ⋅ 64bands in the frequency set out of the 63 DCT coefficients (except for the DC coefficient) in each block. However, randomly selecting the bands might cause the degradation in watermarked image quality and its robustness. Therefore, we apply
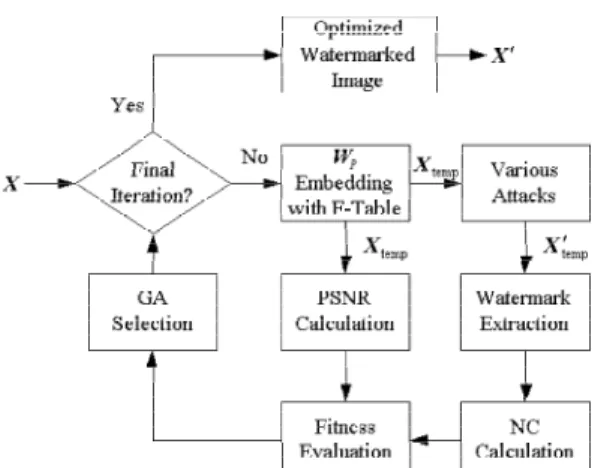
shown in Fig. 1.
Fig. 1 The block diagram for watermark embedding with GA.
Once the bands in the frequency set are selected in the training process, we designate the mapping between i and k in Eq. (2) as the secret key, key . Next, 1
we generate a reference table, R=
{ }
R(i), i∈F , with the DCT coefficients Y byusing the factors between the DC and AC coefficients, which is denoted by . ] 63 , 1 [ , ) ( ) 0 ( ) ( 8 8 1 1 ( , ) ) , (
∑∑
= = ∈ = M N m n mn n m i i Y Y i R (4)We use the DC value of every block, e.g., Y(m,n)(0) in Y(m,n) of block (m,n), as a reference value, and produce the relationships among the DC value of one block, the current AC coefficients, and the F-table for further operation with W . Consequently, P
we can calculate the polarities,
UU U
{
}
8 8 1 1 ) , ( ( ) M N m n i n m i P = = ∈ = MFP , of the DCT coefficients in the
middle-frequency set by
(
)
⋅ ≥ ∈ = otherwise; , 0 , ), 0 ( ) ( ) ( if , 1 ) ( ( , ) ( , ) ) , ( F i Y i R i Y i Pmn mn mn (5) − ∈ = = ∈ = = + ∈ = = = ′ otherwise. , 1 ) ( , , 1 ) ( ) ( if ), ( , , 1 ) ( and 0 ) ( if , 1 ) ( , , 0 ) ( ) ( if ), ( ) ( ) , ( ) , ( ) , ( ) , ( ) , ( ) , ( ) , ( ) , ( ) , ( ) , ( ) , ( i Y i i W i P i Y i i W i P i Y i i W i P i Y i Y n m n m P n m n m n m P n m n m n m P n m n m n m F F F (6)Y remains unchanged if i∉F . After embedding with the polarities in every GA
iteration, we are able to perform inverse DCT on
UUU
{
}
8 8 1 1 63 0 ) , ( ( ) M N m n k n m k Y = = = ′ = ′Y , and get the
watermarked image of the current iteration, Xtemp. Then, we apply the attacking schemes on Xtemp and extract the watermarks from Xtemp′ with their normalized cross-correlation (NC) values 錯誤! 找不到參照來源。. According to the definition of GA, we need to assign the fitness function in the lth iteration with
(
)
∑
= ⋅ + = p h l h l h p l l f 1 , , 1 NC PSNR λ . (7)Where p and λ are the number of attacking schemes and the weighting factor h,l for the NC values, respectively [4]. Completing the whole procedures in each iteration, we feedback the selected bands with the largest fitness value of current iteration for further training with the mutation, crossover, and selection procedures in GA.
In extracting the watermarks, we calculate the DCT of the watermarked image after attacking Y′, in the optimized X′, with the reference table in Eq. (3),
′ ⋅ ≥ ′ = ′ otherwise. , 0 ; ) 0 ( ) ( ) ( if , 1 ) ( ( , ) ( , ) ) , ( , n m n m n m P Y i R i Y i W (8)
U UU
1 0 1 0 ) , ( , ( ). − = − = ∈ ′ = ′ MW M W N N m n i n m P P W i F W (9)Then, we use key to acquire the extracted watermark 0 W′ from WP′.
三、結果與討論
In our simulation, we take the well-known test image, Lena, with size 512×512, as the original source. We have the embedded watermark, rose, with size 128×128. Hence, the number of bits to be embedded in one block is 2 64 4
2
512
128 ⋅ = . Next, taking
the frequency set in [2] to be the initial F , i.e.,
{
Y(m,n)(14),Y(m,n)(15),Y(m,n)(16),Y(m,n)(27)}
,∀m,n,=
F in our simulation. We apply three
attacking methods, namely, low-pass filtering, median filtering, and JPEG compression with quality factor 80%. Then, the resulting PSNR of the watermarked image, and the three NC values after attacking, work together to evaluate the fitness function. Hence, we use p=3 and λh,l =10,∀h,l, in Eq. (6) for simplicity in our simulation.
The fitness value in GA increases with the increase in iteration numbers. And we can see the improvements in both the watermarked image quality, from 30.19 dB to 34.79 dB, and the NC values, from 0.5300 to 0.7426, if we take the LPF attack for instance. Therefore, GA provides an effective means for watermarking, with the carefully determined fitness function. Experimental results demonstrate our proposed method can improve the method presented in [2].
四、計畫成果自評
A genetic and robust algorithm for DCT-based watermarking has been presented. It is robust because we make use of GA to train the frequency set for embedding the watermark. In addition to the robustness of the proposed algorithm, we also improve the watermarked image quality with the aid of GA. Simulation results reveal that if we just borrow the concepts of existing algorithms, both the watermarked image quality and the NC values of the extracted watermarks after certain attacks will be
techniques, we are able to claim its robustness and superiority over the existing algorithm with the proposed techniques. In comparison with the existed methods, embedding with our scheme can get better-watermarked image qualities and the higher NC values in the extracted watermarks.
This work entitled “Genetic Watermarking Based on Transform-Domain Watermarking” has been accepted for publication on Pattern Recognition.
五、參考文獻
[1] S. Katzenbeisser and F. Petitcolas, Information Hiding – Techniques for Steganography and Digital Watermarking, Artech House, Norwood, 2000.
[2] C. T. Hsu, and J. L. Wu, Hidden Digital Watermarks in Images, IEEE Trans. Image Proc., 8 (1999), 58-68.
[3] C. I. Podilchuk and W. J. Zeng, Image-Adaptive Watermarking Using Visual Models, IEEE Journal on Selected Areas in Communications, 16 (1998), 525-539.
[4] Z. M. Lu and S. H. Sun, Digital Image Watermarking Technique Based on Vector Quantisation, Electron. Lett., 36 (2000), 303-305.
[5] D. E. Goldberg, Genetic algorithms in search, optimization and machine learning, Addison-Wesley, Reading, Massachusetts, 1992.