Detection of Reversible Data Hiding Scheme Based
on Histogram Feature Codes
Der-Chyuan Lou
Department of Computer Science and Information Engineering, Chang Gung University,
Taoyuan, Taiwan dclouprof@gmail.com
Chen-Hao Hu, Chung-Cheng Chiu, and Te-Jen Chang
Department of Electrical Engineering, Chung Cheng Institute of Technology,
National Defense University, Taoyuan, Taiwan
chenhao.hu@gmail.com; davidchiu@ndu.edu.tw; karl591218@gmail.com
Abstract―Reversible data hiding scheme assures that
the original cover image can be totally recovered from the stego-image after the hidden messages are extracted. Those techniques are suitable for the applications of mili-tary, medical, high-energy particle physical experimental investigation and artistic purposes when any distortion to the original images is not acceptable. In 2006, Ni et al. proposed a reversible data hiding algorithm base on his-togram shifting. Utilizing the zero or minimum points of the histogram of an image and slightly modifies the pixel grayscale values to embed messages into the image. The goal of steganalysis is to identify suspected images, deter-mine whether or not they have messages embedded in them. In this paper, a novel steganalytic scheme against Ni et al.’s steganographic method based on histogram feature codes is proposed. Experimental results show that the steganalytic scheme is capable to detect the Ni et al.s’ steg-anographic method.
Index Terms―reversible data hiding, steganography,
steganalysis, histogram.
I. INTRODUCTION
Data hiding [1] is a process to conceal secret messages in a cover media and make it can’t be detectable. Reversible data hiding techniques [2-4] provide not only conceal the secret messages in a cover media but also lossless reconstruct the origi-nal cover media after the extracting of the secret messages. Reversible data hiding techniques satisfy some applications those without any distortion of the cover media, such as military, medical, high-energy particle physical experimental investi-gation and artistic purposes.
In contrary to data hiding, the goal of steganaly-sis is detecting the present of secret messages, even
determining the steganographic methods. Current steganalysis techniques [5] fall broadly into one of two categories: specific [6, 7] or universal blind steganalysis [8, 9]. Specific steganalysis can ex-amine the present of a secret message embedded by specific steganographic algorithm, or even can es-timate the embedding ratio. Universal blind stega-nalysis is a meta-detection method in the sense that it can be adjusted, after training on lots of original and stego-medias, to detect most of well-know steganographic methods. In general, steganalysis methods target a specific embedding method can give more accurate and reliable results than any universal blind steganalysis.
In 2006, Ni. et al. proposed a reversible data hid-ing algorithm based on histogram shifthid-ing [10], with low computational complexity and short exe-cution time. In this paper, we investigate the dif-ference of histogram features between cover im-ages and stego-imim-ages. Then, a novel specific steganalysis method against Ni. et al.s’ reversible data hiding algorithm is proposed. Through the pro-posed sampling and quantifying processes, the im-age histogram feature codes are encoded. Accord-ing to the histogram feature codes, the stego-images are detectable from the original ones.
II. REVIEW OF THE NI et. al.S’ REVERSIBLE DATA
HIDING SCHEME
The Ni et al.s’ reversible data hiding scheme [10] can be concluded in following steps.
minimum points Min(b) of histogram of a cover image. Deal with each pair using fol-lowing steps, one by one.
Step 2. Set minimum points as zero points. If the pixel values of these minimum points are not equal to zero, set the pixel values of minimum points be zero and record the po-sitions of these pixels as overhead book-keeping information. That is in order to re-cover these pixels in data extraction steps and get the original cover image back. Step 3. Without loss of generality, assume the pixel
values of one pair of maximum and mini-mum points P(Max(a)) < P(Min(b)). If the pixel value of a cover image P(I) = x, where
x ∈ (P(Max(a)), P(Min(b))) , then P(I) = x
+ 1. Otherwise, when P(Max(a)) > P(Min(b)), if P(I) = x, where x ∈
(P(Max(a)), P(Min(b))), then P(I) = x - 1. Step 4. Scan the cover image in some sequential
order and embedding data m (messages and overhead) by replace the pixel values of
Max(a) sequentially as follows.
● When P(Max(a)) < P(Min(b)), if m = 1 then P(Max(a)) = P(Max(a)) +1, else keep P(Max(a)) unchanged.
● When P(Max(a)) > P(Min(b)), if m = 1 then P(Max(a)) = P(Max(a)) -1, else keep P(Max(a)) unchanged.
In data extraction process, suppose all pairs of maximum and minimum points a and b are known, the multiple pairs case can be treated as the multi-ple remulti-pletion of the data extraction for one pair case. Extraction process can be concluded in following steps.
Step 1. Scan the marked image in the same sequen-tial order as the embedding procedure. If the value of a pixel is equal to a+1, a bit “1” is extracted. If the value of a pixel is equal to
a, a bit “0” is extracted.
Step 2. Scan the image again, for any pixel whose value x∈( a, b],
● When a < b, x = x - 1. ● When a > b, x = x + 1.
Step 3. If there is overhead bookkeeping informa-tion found in extracted data, set the pixel value (whose position is recorded in the overhead) as b.
In this way, the cover image can be recovered without any distortion.
III. HISTOGRAM FEATURE CODES AND THE P RO-POSED DETECTING ALGORITHM
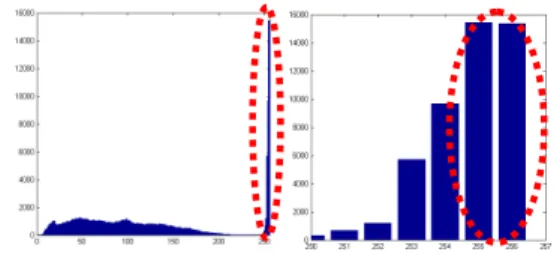
According to the histogram features of stego-images those produced by Ni et al.s’ reversi-ble data hiding scheme, two samples of the differ-ences between cover image and stego-image are shown in Fig. 1 and Fig. 2. We introduce some fea-ture codes for detection and propose the detecting method. The detection method can be simply di-vided to three steps: histogram generation, feature codes generation, and detection of suspicious im-age. The proposed scheme is shown as follows. Step 1. Histogram generation: Suppose a histogram
of a suspicious image I noted as HI and HI(x) is the number of pixel value x of the suspi-cious image, where x∈0~255.
Step 2. Feature codes generation: Code 0:
When HI(x+1)- HI(x) >= HI(x+1)*0.1 then C0 [x] = 0,
When HI(x+1)- HI(x) <= HI(x+1)*0.1 then C0 [x] = 1,
When abs(HI(x+1)- HI(x)) < (max(HI(x+1),
HI(x))*0.065 then C0 [x] = -1.
Code 1:
When x ~= xmax then C1 [x] = 0,
When x = xmax = [2, 253] && abs( (HI(xmax) - (HI(xmax+1))) < (HI(xmax+1))*0.13 &&
abs((HI(xmax-1) - (HI(xmax))) < (HI (xmax-1))*0.13 && abs((HI(xmax-1) - (HI(xmax-2))) < (HI (xmax-1))*0.13 &&
abs((HI(xmax+1) - (HI(xmax+2))) < (HI (xmax-1))*0.13
then C1 [x] = 0,
When x = xmax = [2, 253] && abs((HI(xmax) - (HI(xmax+1))) < (HI(xmax))*0.03 || abs((HI (xmax) - (HI (xmax -1))) < (HI (xmax))*0.03 then C1 [x] = 1,
When x = xmax = [0, 1] && abs( (HI(0) - (HI(1))) < (HI(xmax+1))*0.05 && abs((HI(2) - (HI(3))) < (HI (xmax+1))*0.05
then C1 [x] = 0,
When x = xmax = [0, 1] && abs((HI(xmax) -
(HI(xmax-1))) < (HI(xmax-1))*0.03 && abs(xmax
- xmax-1) = 1
then C1 [x] = 1,
When x = xmax = [254, 255] &&
abs( (HI(255) - (HI(254))) <
(HI(xmax-1))*0.05 && abs((HI(254) -
(HI(253))) < (HI (xmax-1))*0.05 then C1 [x]= 0,
When x = xmax = [254, 255] &&abs((HI(xmax) - (HI(xmax-1))) <
(HI(xmax-1))*0.03 && abs(xmax - xmax-1) = 1
then C1 [x] = 1.
Code 2:
When x ~= xmax then C2 [x] = 0,
When x = xmax = [2, 253] && abs((HI(xmax +1) - (HI(xmax+2))) < (HI(xmax+1))*0.05 &&
abs((HI(xmax) - (HI(xmax+1))) > (HI(xmax))*0.15
then C2 [x] = 2,
When x = xmax = [2, 253] && abs((HI(xmax -1) - (HI(xmax-2))) < (HI(xmax-1))*0.05 &&
abs((HI(xmax) - (HI(xmax-1))) > (HI(xmax))*0.15
then C2 [x] = 2,
When x = xmax = [0, 1] && abs( (HI(0) - (HI(1))) < (HI(xmax+1))*0.05 && abs((HI(2) - (HI(3))) < (HI (xmax+1))*0.05
then C2 [x] = 0,
When x = xmax = [0, 1] && abs((HI(xmax +1) - (HI(xmax+2))) < (HI(xmax+1))*0.05
then C2 [x] = 2,
When x = xmax = [254, 255] &&
abs( (HI(254) - (HI(255))) < (HI(xmax-1))*0.05 && abs((HI(253) - (HI(254))) < (HI (xmax-1))*0.05
then C2 [x] = 0,
When x = xmax = [254, 255] &&
abs((HI(xmax -1) - (HI(xmax-2))) < (HI(xmax-1))*0.05 then C2 [x] = 2. Code 3: When HI(x+1)- HI(x) > HI(x+1)*0.065 then C3 [x] = 0, When HI(x+1)- HI(x) < -HI(x)*0.065 then C3 [x] = 1,
When abs(HI(x+1)- HI(x)) <= (max(HI(x+1),
HI(x))*0.065 then C3 [x] = -1.
Step 3. Detection procedure: The procedures of the proposed detection scheme can be divided into five steps as follows, flowchart is shown in Fig 3.
age.
B. Generate codebook Code 0 of the histogram: If code [1 -1 0] is found in codebook Code 0 C0[x], the suspicious image is determined
as a stego-image. Otherwise, continue next step.
C. Generate codebook Code 1 of the histogram: If code [1] is found in codebook Code 1
C1[x], the suspicious image is determined as
a stego-image. Otherwise, continue next step.
D. Generate codebook Code 2 of the histogram: If code [2] is found in codebook Code 2
C2[x], the suspicious image is determined as
a stego-image. Otherwise, continue next step.
E. Generate codebook Code 3 of the histogram: If code [1 X -1 X 0], [-1 1 0 1 0], and [1 0 1 0 -1] are found in codebook Code 3 C3[x],
the suspicious image is determined as a stego-image. Otherwise, the suspicious im-age is not a stego-imim-age.
IV. EXPERIMENTAL RESULTS AND CONCLUSIONS
In this section, we present the results obtained from the experiments of the proposed scheme. In the experiments, we downloaded 1,338 images from image databases [11]. All of which were transformed into an 8-bit grayscale format to act as the test cover images. The hidden messages are random bits produced by a pseudo-random-number generator. 1,338 original cover images and 1,338 stego-images are applied to the detection scheme. Let hiding pairs be equal to one - three pairs. The detection results are shown in Table 1. There are 114/1,338 cover images are determined as stego-images in all case. In one pair case, there are 1,152/1,338 stego-images are positive detected. In other case, there are 1,213/1,338 and 1,098/1,338 stego-images are positive detected relatively.
In this paper, a specific steganalysis scheme based on histogram feature codes is proposed. The steganalysis experiments show that the proposed method received good performance. The future work will focus on the detection of other reversible data hiding methods based on histogram shifting,
and the range of the pixel values of hiding bits.
ACKNOWLEDGEMENTS
This work was supported partially by the National Science Council of Republic of China under grant NSC 98-2221-E-182-066-MY2.
REFERENCE
[1] W. Bender, D. Gruhl, N. Morimoto, and A. Lu, “Techniques for data hiding,” IBM Systems
Journal, vol. 35, No. 3&4, pp.331-336, 1996.
[2] M. U. Celik, G. Sharma, A. M. Tekalp, and E. Saber, “Lossless generalized-LSB data em-bedding,” IEEE Transactions on Image
Proc-essing, vol. 14, no. 2, pp. 253-266, Feb. 2005.
[3] S. Lee, C. D. Yoo, and T. Kalker, “Reversible image watermarking based on inte-ger-to-integer wavelet transform,” IEEE Transactions on Information Forensics and Security, vol. 2, no. 3, pp.321-330, Sept. 2007.
[4] P. Tsai, Y.-C. Hu, and H.-L. Yeh, “Reversible image hiding scheme using predictive coding and histogram shifting,” Signal Processing, vol. 89, no. 6, pp. 1129-1143, June 2009.
[5] X.-Y. Luo, D.-S. Wang, P. Wang, and F.-L. Liu, “A review on blind detection for image steganography,” Signal Processing, vol. 88, no. 9, pp. 2138-2157, Sept. 2008.
[6] J. Fridrich, M. Goljan, and R. Du, “Detecting LSB steganography in color, and gray-scale images,” IEEE Multimedia, vol. 8, no. 4, pp. 22-28, Oct.-Dec. 2001.
[7] A. Westfeld and A. Pfitzmann, “Attacks on steganographic systems,” Proceedings of the
Third International Workshop Information Hiding, Dresden, Germany, Sep. 28-Oct. 1,
1999, pp. 61-76.
[8] D.-C. Lou, C.-L. Lin, and C.-L. Liu, “Univer-sal steganalysis scheme using support vector machine,” Optical Engineering, vol. 46, no. 11, pp. 117002-1~117002-10, Nov. 2007. [9] D.-C. Lou, C.-L. Lin, and J.-L. Liu, “Novel
steganalysis schemes for BPCS steganogra-phy,” The Imaging Science Journal, vol. 56, no. 4, pp. 232-242, Aug. 2008.
[10] Z. Ni, Y. Q. Shi, N. Ansari, and W. Su, “Re-versible data hiding,” IEEE Transaction on
3, pp. 354-362, March 2006.
[11] Uncompressed Colour Image Database,
http://vision.cs.aston.ac.uk/datasets/UCID/ucid. html, Oct. 2009.
(a) Chair
(b) Histogram of cover image of Chair
(c) Histogram of stego-image Chair
Figure 1. The differences between cover image and stego-image of Chair.
(a) Buildings
(b) Histogram of cover image Buildings
(c) Histogram of stego-image Buildings Figure 2. The differences between cover image and stego-image Buildings.
Figure 3. Flowchart of the proposed detection pro-cedure.
Table 1. Detection results.
Cover image Stego-image
Hiding
pairs Positive % Positive %
1 114 0.0852 1152 0.8610 2 114 0.0852 1213 0.9066 3 114 0.0852 1098 0.8206 Average ratio 0.0852 0.8627