雲端運算環境下檔案更新管理之安全性研究 - 政大學術集成
全文
(2) 雲端運算環境下檔案更新管理之安全性研究 A Study on the Security of Patch Management in a Cloud Computing Environment. 研究生:簡禎儀 指導老師:左瑞麟. Advisor: Ray-Lin Tso. 政 治 大. 國立政治大學 資訊科學系 碩士論文. 學 ‧. ‧ 國. 立. Student: Chen Yi Chien. y. Nat. n. er. io. sit. A Thesis submitted to Department of Computer Science al v i National Chengchi University n Ch U i e h n c g in partial fulfillment of the Requirements for the degree of Master in Computer Science. 中華民國一百零二年一月 January 2013. i .
(3) A Study on the Security of Patch Management in a Cloud Computing Environment. Abstract As cloud computing techniques advance, Virtual Machines (VM) seems to be an appropriate solution than physical machine deployment. Having multiple instances of virtual machines cause more efficient use of. 政 治 大 effectiveness. In this thesis, Virtual Machine Image Catalogue (VMIC) is 立. computing resources to achieve the aim of energy consumption and cost. ‧ 國. 學. designed for helping users search and acquire expected virtual machine images promptly. Nevertheless, security of VMIC is also a crucial task to. ‧. keep systems up-to-date and defends against security attacks. Pakiti is. sit. y. Nat. adopted to monitor patch status of physical and virtual machines, and. al. n. Keywords. io. patches.. er. schedules the warning information to remind security staffs to update the. Ch. engchi. i n U. v. Cloud security, Virtual machine image, Patch management. ii .
(4) 雲端運算環境下檔案更新管理之安全性研究. 摘要. 隨著雲端運算盛行,企業採用大量虛擬主機來取代實體機器,虛擬主 機有效率的模擬實體機器達到企業減少能源耗損與提高成本效率目. 政 治 大. 標。 文中提及虛擬主機映像檔目錄系統(VMIC)主要讓使用者能有效. 立. 率搜尋期望的檔案並獲得下載的實體位置,故本論文研究重點著重在. ‧ 國. 學. 改進安全性在原 VMIC 系統,應用 Pakiti 監控系統來掌握更新檔狀況. ‧. 於實體機器或虛擬機器環境,使資安人員能在短期間內獲得正確資. Nat. sit. n. al. er. io. 關鍵字. Ch. engchi. 雲端安全,虛擬主機映像檔,更新檔管理 . iii . y. 訊,及時升級更新檔避免攻擊災害發生。. i n U. v.
(5) Acknowledgement 終於寫到誌謝辭部分,也代表我的論文即將劃下句點。 當論文寫完的 當下,真的很開心很感動,我終於可以放下心中的大石,領取那張期待已久 的畢業證書。 從開始念書以來,因為外派瑞士工作的緣故,我的論文也擱 置了很久,非常感謝左瑞麟老師這段時間的指導,讓我能夠在回國後,順利 完成這份論文。 也非常感謝我的口試委員蔡國裕教授和葉國暉教授,針對 我的論文給予很多寶貴的建議,獲益良多。. 治 政 大 作學業兼顧。 也感謝政大的同學們,針對論文撰寫給我很多建議,節省許 立 多寶貴時間。 CERN 的朋友和國外的朋友,謝謝你們一直為我打氣。 一個 這三年來,經歷了很多事情,我的朋友們常常鼓勵我,讓我可以. ‧ 國. 學. 曾經很重要的法國人,因為你的緣故給我最大的動力在短期間完成這任務。 最後我要把這篇論文獻給我的家人,尤其是我親愛的弟弟,感謝他針對我的. ‧. 英文部分給我很多指導糾正,我的家人在這三年來給我最大的支持與鼓勵,. sit. n. er. io. al. Ch. engchi. iv . y. Nat. 謹以這三年來的成果,獻給我最親愛的家人。. i n U. v.
(6) TABLE OF CONTENTS 1 Introduction ................................................................................................................. 1 1.1 Introduction ...................................................................................................... 1 1.2 Thesis Architecture .......................................................................................... 2 2 Background and Related Work ................................................................................... 3 2.1 Cloud Computing ............................................................................................. 3 2.1.1 Cloud Service Models ........................................................................... 4 2.1.2 Cloud Computing Security ................................................................... 6 2.2 Virtualization .................................................................................................... 7 2.2.1 Virtual Machine Infrastructure ............................................................ 10 2.2.2 Virtual Machine Image Catalogue ...................................................... 12 2.2.2.1 HEPiX Virtualization Working Group ..................................... 14 2.2.2.2 Image Trust .............................................................................. 15 2.2.3 Virtual Machine Image Security ......................................................... 16 3 Virtual Machine Image Catalogue System ............................................................... 19 3.1 System Introduction ....................................................................................... 19 3.2 Virtual Machine Image Catalogue Components ............................................ 21 3.2.1 Command Line Interface .................................................................... 21 3.2.2 HEPiX Tool Subscription .................................................................... 22 3.2.3 VMIC Image Distribution ................................................................... 23 3.2.4 Glance Module and Authentication with Keystone ............................ 25 . 立. 政 治 大. ‧. ‧ 國. 學. y. Nat. sit. n. al. er. io. 3.3 Security Considerations of VMIC ................................................................. 25 4 VMIC Security Improvement ................................................................................... 27 4.1 Security Improvement .................................................................................... 27 4.2 Online Patch Management - Pakiti ................................................................ 29 4.2.1 Pakiti Architecture .............................................................................. 30 4.3 Offline Patch Management ............................................................................ 33 4.3.1 Nuwa ................................................................................................... 33 4.4 Method: Patch Management in VMIC System .............................................. 37 4.4.1 Pakiti in VMIC System ....................................................................... 38 4.4.2 Nuwa in VMIC System ....................................................................... 40 5 Implementation of VMIC Security Improvement..................................................... 42 5.1 Pakiti Client ................................................................................................... 42 5.2 Pakiti Server ................................................................................................... 43 6 Future Work .............................................................................................................. 47 7 Conclusion ................................................................................................................ 49 8 Reference .................................................................................................................. 50 . Ch. engchi. v . i n U. v.
(7) TABLES List of System Virtual Machine…………………………………………………… 11 . 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. vi . i n U. v.
(8) FIGURES Figure 2-1 Cloud Computing......................................................................... 4 Figure 2-2 Cloud computing layers. .............................................................. 6 Figure 2-3 Virtualization. .............................................................................. 8 Figure 2-4 Server virtualization..................................................................... 9 Figure 2-5 VMIC architecture and concept. ................................................ 13 Figure 2-6 VMIC image endorsing and trusting of distribution. ................. 14 Figure 3-1 the architecture and concepts of VMIC. .................................... 21 Figure 3-2 import images from other sites. ................................................. 22 Figure 3-3 image list publication. ................................................................ 23 Figure 3-4 VMIC image distribution. .......................................................... 24 Figure 3-5 Glance Module and authentication with Keystone. ................... 25. 立. 政 治 大. ‧. ‧ 國. 學. Figure 4-1 VM Communication Attack on VM2 and VM3. ....................... 27 Figure 4-2 Pakiti environment. .................................................................... 31 Figure 4-3 Flow of script analysis and rewriting......................................... 35 Figure 4-4 Batch patch virtual machine images via Mirage........................ 36 Figure 4-5 Patch management in VMIC system. ........................................ 38 Figure 4-6 Pakiti Service in VMIC.............................................................. 39 Figure 4-7 Nuwa Service in VMIC. ............................................................ 40 Figure 5-1 The Pakiti client cron script. ...................................................... 43 Figure 5-2 Hosts list on Pakiti server and this list sorts hosts by country. .. 43 Figure 5-3 security events and CVEs statistics ........................................... 44 Figure 5-4 all vulnerable CVEs on puppetmaster host. ............................... 45 Figure 5-5 package names and version of CVE-2010-2761........................ 45 Figure 5-6 CVE-2010-2761 and 2010-4410 on Red Hat. ........................... 45. n. er. io. sit. y. Nat. al. Ch. engchi. vii . i n U. v.
(9) 1 Introduction 1.1 Introduction Cloud computing is one of the most influential technologies in the Information Technology (IT) industry and is revolutionizing the way IT resources are managed and utilized in the 21st century. Cloud computing is to scale the resource up and down flexibility. Customers request the resource depends on their usage amount.. Cloud provides. 政 治 大 know the location and other details of the computing infrastructure [1]. 立. computation, software, data access, and storage resources without requiring cloud users to. ‧ 國. 學. . The University of California, Berkeley gave a broader definition of cloud computing:. ‧. cloud computing refers to both the applications delivered as services over the Internet and the The services. sit. y. Nat. hardware and systems software in the data centers that provide those services.. io. er. themselves have long been referred to as Software as a Service (SaaS). The data center hardware and software is what we will call a cloud [2]. All cloud clients can just request. al. n. v i n resources without maintenanceCeffort, be charged only when they really use such U h e nandgwill i h c resource on-demand services. In cloud computing, both software and hardware resources are distributed, which can be allocated and extended dynamically as services. To achieve better performance, the. service providers have to prepare such great number of machines which will increase business cost.. Therefore, the current trend is deploying virtual machines to reduce cost. called virtualization.. Virtualization improves scalability and optimizes hardware-resource.. With virtualization, operating systems can be run in parallel on a single central processing. 1 .
(10) unit (CPU). This parallelism utilizes hardware resources and tends to reduce overhead costs.. What cloud clients also emphasize on is service reliability and security issues. Since virtualization will be greatly used in the future, the cloud providers need to ensure that their infrastructure is secure and that their clients’ data and applications are protected. Virtual machine is extensively utilized and expected to reduce the physical machines in usage.. 政 治 大. However, deploying a virtual machine is not strict as a physical machine; its. 立. security should not be undervalued and underpaid. In this thesis, we will discuss security. ‧ 國. 學. issues with virtual machines.. ‧. 1.2 Thesis Architecture. y. Section II we introduce the current background. sit. Nat. The paper is organized as follows.. io. er. and related work of cloud computing security and virtualization. And also mentions the. al. v i n C h catalogue systemUconsists of the essential components. approach of virtual machine image engchi n. motivation to study about virtual machine image security. Section III we discuss about the. Section IV it mentions security improvement and solution of the approach. Section V discuss about the future work to achieve. Finally conclusions are drawn in section VI.. 2 .
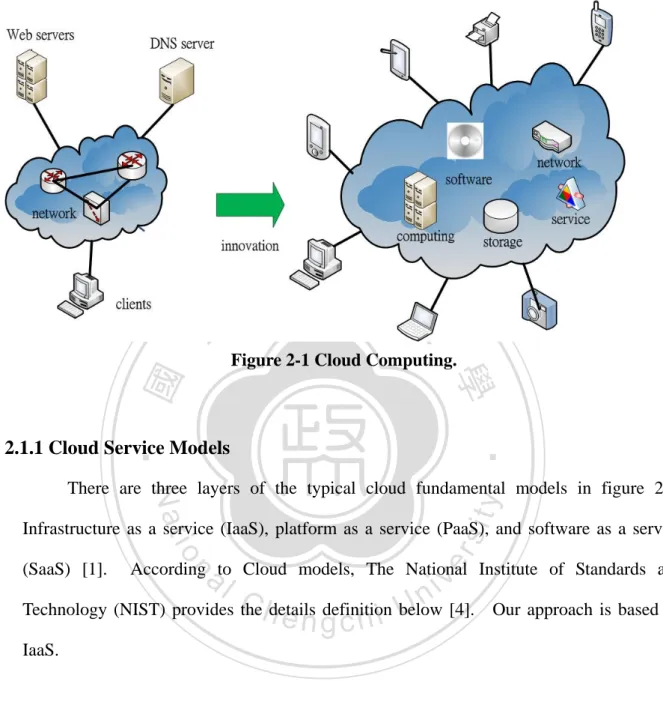
(11) 2 Background and Related Work 2.1 Cloud Computing Since Internet is coming, users can search the information via the browsers. The browsers interact with Domain Name Server (DNS) and network servers to capture the information to represent on the client’s browsers.. It is not necessary for users to. understand the middle process; users only care about the performance of service providers. 政 治As the大 result of Internet is popular and the. (servers) and service requesters (clients).. 立. bandwidth is raised, many kinds of equipments that can access the Internet are developed,. ‧ 國. 學. it means users can use not only personal computer but also other equipments to access the Internet.. Application will not be limited to read web pages or receive e-mails; users. ‧. Therefore cloud computing is caused. In figure 2-1, we can. sit. Nat. processing on the Internet.. y. want to provide electronic commerce, customization or high-performance computing. n. al. er. io. understand the cloud involves network, computing, storage and many services.. i n U. Ian. v. Foster mentioned the definitions for cloud computing in 2008, cloud computing is a. Ch. engchi. large-scale distributed computing paradigm that is driven by economies of scale in which a pool of abstracted virtualized, dynamically-scalable, managed computing power, storage, platforms, and services are delivered on demand to external customers over the Internet [3]. . 3 .
(12) 立. 政 治 大. Figure 2-1 Cloud Computing.. ‧. ‧ 國. 學. 2.1.1 Cloud Service Models. sit. y. Nat. There are three layers of the typical cloud fundamental models in figure 2-2:. io. er. Infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service. al. v i n Technology (NIST) provides C thehdetails definition below [4]. engchi U. According to Cloud models, The National Institute of Standards and. n. (SaaS) [1].. Our approach is based on. IaaS.. Infrastructure as a Service (IaaS). The capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, deployed applications, and possibly limited control of select networking components Amazon Elastic Compute Cloud. 4 .
(13) (Amazon EC2) is a typical example.. Platform as a Service (PaaS). The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming languages and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure, but has control over the deployed applications and possibly application hosting environment configurations. This kind of. 政 治 大. consumer is a software programmer.. 立. ‧ 國. 學. Software as a Service (SaaS). The capability provided to the consumer is to use the service provider’s applications running on a cloud infrastructure. The applications are. ‧. accessible from various client devices such as a web browser or mobile phones. The. sit. y. Nat. consumer does not manage or control the underlying cloud infrastructure including network,. io. al. er. servers, operating systems, storage, or even individual application capabilities, with the. v. n. possible exception of limited user-specific application configuration settings.. Ch. engchi. . 5 . i n U.
(14) 立. 政 治 大. ‧ 國. 學. Figure 2-2 Cloud computing layers [1].. ‧. 2.1.2 Cloud Computing Security. y. Nat. Cloud computing. sit. Security is one of the largest urgent concerts of cloud computing.. n. al. er. io. security, simply speaking is to refer to a number of policies, technologies, and controls. i n U. v. deployed to protect valuable data, applications, and the associated infrastructure of cloud computing.. Ch. engchi. Cloud Service provider should make effort in ensuring the data is safe and. protected [5].. Regarding the concept of cloud computing security has following. definition. Identity management Every enterprise has its specific Identity Management System to control access to information or computing resources.. Hence, cloud providers integrate the customer's. Identity Management System into their infrastructure, using federation or Single-Sign-On (SSO) technology, or according to the requirement to provide the solution. 6 .
(15) Physical and personnel security Cloud service providers ensure the physical machines are under completely security protection and that access to these machines as well as relevant customer data is not only restricted but the access record is traced. Availability Cloud service providers ensure customers are able to access the data and applications regularly. Application security. 立. 政 治 大. Cloud service providers ensure their available applications are secure via the cloud by. ‧ 國. 學. implementing testing and acceptance procedures for outsourced or packaged application code.. ‧. Privacy. y. Nat. sit. Cloud service providers ensure that all sensitive and critical data are masked (for example:. n. al. er. io. credit card numbers) and that only authorized users can access to data in its entirety. In. i n U. v. addition, digital identities and credentials must be protected.. Ch. engchi. As the convenience of cloud computing, a number of services are tended to support cloud development.. Many enterprises provide cloud applications and services.. It means. some sensitive and customer information will published on the Internet. Enterprises must ensure these data be secure not to access from irrelevant people.. Security is the important. field in IT, people always need to consider security issue to avoid the terrible accident happened, especially virtualization application in Cloud.. 2.2 Virtualization Virtualization, simply speaking is the creation of a virtual version of hardware 7 .
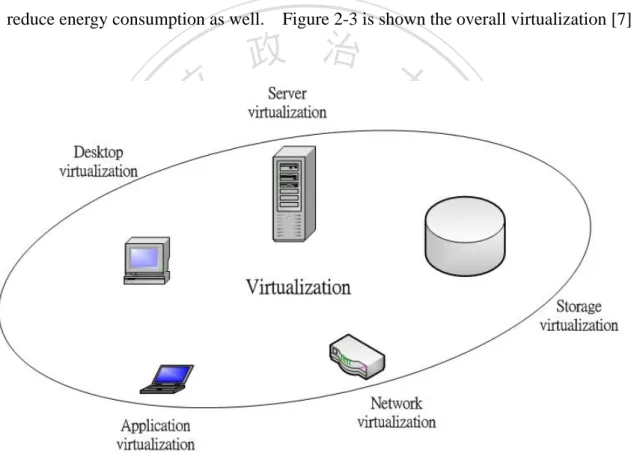
(16) platforms, operating systems, storage device, and network resources [6].. The virtualization concept was initially discussed since 1950, in recent years the popularization of server virtualization technique, it brings a brand-new data center deployment and management method to assist managers earning high efficiency and convenient management experience.. Virtualization is to upgrade resource utilization and. reduce energy consumption as well. Figure 2-3 is shown the overall virtualization [7].. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. i n U. v. Figure 2-3 Virtualization.. Enterprises trend to virtualization generally, the mostly reason is the advantage they can gain. 1) Cost reduction: to reduce procurement, maintenance cost and operating expenses. 2) Improvement of application compatibility: many services and programs can apply 8 .
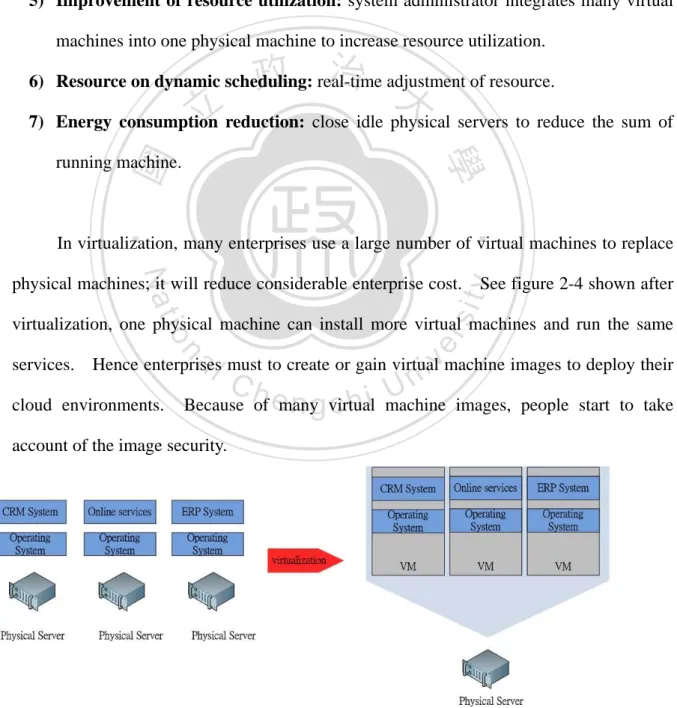
(17) on different platform. 3) Acceleration of deployment: deploying a System-in-Package service to reduce time and cost. 4) Improvement of service availability: extension of continual and stable service. Even if system failure or hardware failure, the service can recover at the short time. 5) Improvement of resource utilization: system administrator integrates many virtual machines into one physical machine to increase resource utilization.. 政 治 大. 6) Resource on dynamic scheduling: real-time adjustment of resource.. 立. 7) Energy consumption reduction: close idle physical servers to reduce the sum of. ‧ 國. 學. running machine.. ‧. In virtualization, many enterprises use a large number of virtual machines to replace. y. Nat. sit. physical machines; it will reduce considerable enterprise cost. See figure 2-4 shown after. n. al. er. io. virtualization, one physical machine can install more virtual machines and run the same. i n U. v. services. Hence enterprises must to create or gain virtual machine images to deploy their cloud environments.. Ch. engchi. Because of many virtual machine images, people start to take. account of the image security. . Figure 2-4 Server virtualization.. 9 .
(18) The following topics will introduce virtual machine image application and security. The approach is the development of a software tool to facilitate the distribution of virtual machine images between different sites.. It also points out the security improvement. according to the current system.. 2.2.1 Virtual Machine Infrastructure Follows the cloud computing applications popularly, plenty of enterprises want to reduce the assets cost but keep the available requirement; they try to use virtual machines to. 政 治 大. execute in the environment. In General, current cloud platform consists of a large number. 立. of virtual machines. A virtual machine, an efficient, isolated duplicate of a real machine [8],. ‧ 國. 學. is a software implementation of a machine that executes programs like a physical machine. Modern virtual machines are implemented with either software emulation or hardware. ‧. virtualization or (in most cases) both together [9]. Thus, a virtual machine provides a. y. Nat. sit. complete system platform that supports the environment of an operation system and expects. n. al. er. io. to run multiple operation systems at the same time on one physical machine. Our approach. i n U. v. is about the application of virtual machine image, the first draft implementation was. Ch. engchi. published at The High Energy Physics Unix Information Exchange (HEPiX) meeting, and we will also have more details of virtual machine image security below. . 10 .
(19) List of System Virtual Machine Name KVM. Developer. Operation System. Read Hat , Inc. Linux kernel. Oracle VM Oracle Corporation VirtualBox. Microsoft Windows, Mac OS X, Linux and Solaris. VMware. VMware, Inc.. Microsoft Windows, Linux, and Mac OS X. Xen. The Xen XenSource, Inc.. Ó KVM. Project Linux, and other Unix-like, *BSD, OpenSolari, Microsoft Windows. . 政 治 大 Kernel based Virtual Machine, an open-source software, is a full 立. ‧ 國. 學. virtualization infrastructure for Linux on x86 hardware containing virtualization extensions [10][11]. . ‧. . sit. y. Nat. Ó Oracle VM VirtualBox is a powerful x86 and AMD64/Intel64 virtualization. n. al. er. io. software package for enterprise. It created by software company Innotek GmbH,. i n U. v. purchased by Sun Microsystems, and now developed by Oracle Corporation. At. Ch. engchi. present, Oracle VirtualBox executes on Windows, Linux, Macintosh, and Solaris hosts [12][13]. Ó VMware , a company providing virtualization software, delivers customer-proven solutions that accelerate IT by reducing complexity and enabling more flexible, agile service delivery. VMware's desktop software runs on Microsoft Windows, Linux, and Mac OS X, while VMware's enterprise software hypervisors for servers, VMware ESX and VMware ESXi are bare-metal embedded hypervisors that run directly on server hardware without requiring an additional underlying operating. 11 .
(20) system [14][15]. Ó Xen, an open-source industry standard for virtualization, is a virtual-machine monitor providing services that allow multiple computer operating systems to execute on the same computer hardware concurrently. Xen offers an efficient and secure feature set for virtualization of x86, x86_64, IA64, ARM, and other CPU architectures. In the beginning, the University of Cambridge Laboratory developed. 政 治 大. the first versions. Since 2010, the Xen community develops and maintains Xen as. 立. free software, licensed under the GNU General Public License (GPLv2) [16][17].. ‧ 國. 學. 2.2.2 Virtual Machine Image Catalogue. ‧. The European Organization for Nuclear Research (CERN) started in 1954. It is the. sit. y. Nat. world's largest physics laboratory and its location on Swiss and French border. The famous. io. er. World Wide Web was birthed from CERN. All the time, CERN IT involves in different. al. v i n InC 2009, h eCERN i UHEPiX Virtualization Working Group n g cIThand. n. computer science's fields and is developing a different set of tools to import the cloud computing infrastructure.. published a proposal about the virtual machine image management in HEPiX conference. Simply speaking, VMIC is a catalogue of virtual machine images. It can subscribe images list from other sites and easily export an image list for other sites. Sites can choose to trust only specific endorser or even a single image. metadata are preserved for traceability.. All virtual machine images files and. A trusted endorser can maintain a set of valid. virtual machine images. The set is maintained the latest with security patches and updated regularly. All trusted virtual machine images are managed via VMIC and only trusted endorsers can publish and maintain images from VMICs [18]. Each site can setup their. 12 .
(21) personalized VMICs. Sites may decide to trust endorsers and all the virtual machine images. All endorsers and sites should comply with the security policies from the SPG. . 立. 政 治 大. ‧. ‧ 國. 學. io. sit. y. Nat. er. Figure 2-5 VMIC architecture and concept [18].. n. al. Figure 2-5 showed. v i n in C VMIC several h e nthisgdiagram chi U. scenarios of image trust are. depicted. Two endorsers from RAL and CMS have published a VMIC. A site approved those VMICs as well as its local one from a local endorser. This populates a list of virtual machines that can be used at the site. The local image distribution system can be hooked onto the local listing of approved VMIs to automatically pre-stage the images [18]. Academia Sinica Grid Center (ASGC) [19] applies VMIC as the component of their distributed cloud computing environment [20].. As shown in Figure 2-6, when a site. approves a virtual machine image from an endorser, the virtual machine image information. 13 .
(22) will be imported to the site VMIC database. Then this site can do a real subscription of an approved image. When approved images are stored in a site, it is published a new image list as well as redistribute and re-endorse those on-site images.. VMIC works with many. replications in different sites and different communication protocols such as gridftp, bit torrent Peer to Peer ...etc. Therefore sites can always pick up their best access method to subscribe images. . 立. 政 治 大. ‧. ‧ 國. 學 er. io. sit. y. Nat. al. n. v i n C hendorsing and trusting Figure 2-6 VMIC image of distribution [20]. engchi U 2.2.2.1 HEPiX Virtualization Working Group The High Energy Physics Unix Information Exchange (HEPiX) forum brings together worldwide Information Technology staffs, including system administrators, system engineers, and managers from the High Energy Physics and Nuclear Physics laboratories and institutes, to foster a learning and sharing experience between sites facing scientific computing and data challenges [21].. Its Participating sites around the world and its. organization was formed in 1991. HEPiX is a twice yearly conference in spring and fall.. 14 .
(23) HEPiX Virtualization Working Group is one session of HEPiX, it was made in the spring 2009 HEPiX. HEPiX Virtualization Working Group is to investigate the implications use-cases and requirements of sites that where at the time expected to come from the relatively new technology of Virtual Machine technology. Main focus is to provide sites a way to control and mange Virtual Machine Image’s provided by experiments, and run them in trusted environments with in the current computing environment provided under Grid computing. There are two objectives of HEPiX Virtualization Working Group; one is to. 政 治 大. produce a framework to securely run Virtual Machine Images across multiple sites. 立. supporting High Energy Physics, the other is that sites need to control over Virtual Machine. ‧ 國. 學. Image selection [22]. VMIC was published on HEPiX conference in 2009 and cooperate with HEPiX Virtualization Working Group. The HEPiX Virtualization Working Group. sit. n. al. er. io. 2.2.2.2 Image Trust. y. Nat. . ‧. applications are VMIC, StratusLab[23], and Repoman [24]. . i n U. v. All images published or subscribed must trust the security policy, VMIC security. Ch. engchi. policy is based on EGI Security Policy Group (SPG).. The details of image trust will be. introduced below. EGI.eu is a not-for-profit foundation established under Dutch law to coordinate and manage the European Grid Infrastructure (EGI) federation on behalf of its participants: National Grid Initiatives (NGIs) and European International Research Organizations (EIROs) [25].. EGI.eu is to promote collaborative work within the. community and to integrate the computing resources provided by the different members of the EGI federation. EGI Security Policy Group (SPG) is based on EGI Infrastructure to support all strategy and policy documents and papers that its daily activities in grid operations, software quality, security and user communities. SPG also supports HEPiX in 15 .
(24) security policy for the Endorsement and Operation of Virtual Machine Images [26].. SPG defines the following terms. - Endorser: A role, held either by an individual or a team, who is responsible for confirming that a particular virtual machine image has been produced according to the requirements of this policy and states that the image can be trusted. An Endorser should be one of a limited number of authorized and trusted individuals appointed either by the Infrastructure. 政 治 大. Organization, a Virtualization Organization (VO) or a resource centre. The appointing. 立. body must assume responsibility for the actions of the Endorser and must ensure that he/she. ‧ 國. 學. is aware of the requirements of this policy.. ‧. - Virtual Machine operator: A role, held either by an individual or a team, who is responsible. y. Nat. sit. for the security of the virtual machine during its operation phase, from the time it is. al. n. the virtual machine.. er. io. instantiated, until it is terminated. Typically this addresses individuals with root access on. Ch. engchi. i n U. v. - Third party: An external entity other than the resource centre where the virtual machine is operated [27]. . 2.2.3 Virtual Machine Image Security Virtualization the companies' IT infrastructure lets owners reduce IT costs while increasing the efficiency, utilization, and flexibility of their existing assets. Around the world, companies of every size benefit from virtual machine virtualization. Virtual machines let people share the current resources of a single physical computer across multiple virtual 16 .
(25) machines for maximum efficiency.. Those resources are shared across multiple virtual. machines and applications. To get more and more benefits, the companies use large number virtual machines. The virtual machine as a forensic tool in security field, the Operation system can be booted into a virtual machine, the investigator can perform investigation works in a live system, directly and repeatedly, and the efficiency is improved [28]. Creating virtual machine images it to simplify the whole installation process, the related software involves operation system, applications, security patches. Due to the federation. 政 治 大. cloud concept, these images should be created, trusted, transferred and submitted between. 立. sites and sites. At the same time, people start to take account of virtual machine image. ‧. ‧ 國. 學. security issue.. A cloud service provides three types of resources: a set of virtual machine images, a set. y. Nat. sit. of computer servers for virtual machine images environment, and a storage space to store the. n. al. er. io. related data. While reducing cost is a primary motivation and objective for moving towards. i n U. v. a company or a cloud provider, reducing responsibility for security or privacy should not be.. Ch. engchi. Virtual machine images are unique and special entities in the cloud. The security and integrity of such images are the foundation for the overall security of the cloud because Virtual machine images need high integrity, because they determine the initial states of running virtual machines, including their security states. Second, many of the virtual machine images are designed to be shared by different and often unrelated users. On the other hand, sharing of virtual machine images poses privacy and safety issues.. An endorser should be one of a limited number of authorized and trusted individuals appointed either by sites, can create and publish image files with no limit. Therefore, the 17 .
(26) endorsement of a virtual machine image should be defined by the standard and trust third party or policy. Images are referenced by an image list which contains a secure hash (SHA512) signed using x509 technology. These image lists are published, and interested sites subscribe to the lists in a catalogue at the site. When an instantiation request for an image is received, the image validity is checked. If the image list is valid, the image is contextualized and then instantiated. Images that do not pass validation are not instantiated [29].. 立. 政 治 大. Sharing virtual machine images is a common action in some cloud computing. ‧ 國. 學. environments. Such techniques mainly focus on two aspects of security: 1) security of running instances, and 2) integrity and privacy of customer data [30]. Image repositories,. ‧. the real deposition of image files must be carefully managed and controlled to avoid security. y. Nat. Since an image can contain proprietary source code and sensitive data, the. sit. problem.. n. al. er. io. provider of an image will face risks [31]. In opposition to an attacker may attempt to supply. i n U. v. a virtual machine image containing malware and risks to users of a cloud computing system. Ch. engchi. [32]. Virtual machines and applications need to be secured in IaaS Clouds. Following policies and procedures, hardening of the operating system and applications should occur to procedure virtual machine images for deployment.. Care must also be taken to make. adjustments for the virtualized environments in which the images run. So managing virtual machine images carefully is also import to avoid accidently deploying images containing vulnerabilities [31].. 18 .
(27) 3 Virtual Machine Image Catalogue System Since production of image files rise steadily, sharing virtual machine images has become a simple case around the world.. Users could easily construct a new virtual machine. by using shared images; however, to find the suitable image file entails a lot of work. Therefore, it is an essential requirement to assist people getting their wanted image files from numerous resources. In this thesis, we propose the Virtual Machine Image Catalogue system. 政CERN治and HEPiX 大 Virtualization Working Group. (VMIC) to fulfill the requirement.. 立. published this conception of image catalogue system on HEPiX fall meeting in 2009, and. ‧ 國. 學. realized a draft system and web interface to provide simple service. In 2011, CERN and ASGC started to cooperate with this virtual machine image catalogue project to improve. ‧. Nat. sit. introduce the system structure of VMIC and the functionalities.. n. er. io. 3.1 System Introduction. al. y. original system and add new functions to reach high performance; in this chapter, we will. i n U. v. The Virtual Machine Image Catalogue system (VMIC) is to implement a useful. Ch. engchi. software tool to facilitate the management of internal images and the image distribution between different sites. The images are pre-cached in the compute nodes.. Users expect. to search all useful virtual machine image information on the catalogue, find the exact location to download those files. The system is based on Scientific Linux CERN6 (SLC6) a Linux distribution build within the framework of Scientific Linux which rebuilt from the freely available Red Hat Enterprise Linux 6 (Server) product sources under terms and conditions of the Red Hat EULA [32]. This system is developed in Python language and uses OpenStack software to manage virtual machine, user accounts and passwords. 19 . OpenStack is open-source.
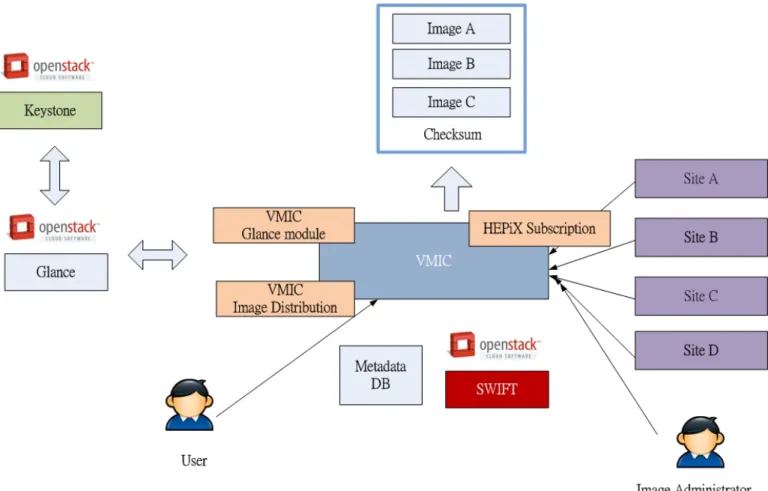
(28) software for building private and public clouds, in other words, OpenStack is a cloud operating system that controls large pools of compute, storage, and networking resources throughout a datacenter, all managed through a dashboard that gives administrators control while empowering their users to provision resources through a web interface [33]. Glance OpenStack in this system is to provide services for discovering, registering, and retrieving virtual machine images.. And virtual machine images made available through Glance can. be stored the object-storage systems such as OpenStack Swift. The system integrates with. 政 治 大. HEPiX Virtualization Working Group tools to create and subscribe image lists. Depends. 立. on the result of subscription, the approach will add images when images are subscribed or. ‧ 國. 學. remove images when images are unsubscribed. Keystone is an OpenStack project that provides Identity, Token, Catalog and Policy services [37]. VMIC project uses OpenStack In Glance, there are several storage. y. Nat. Swift is one of them.. VMIC will. sit. backend to use by default when storing images.. ‧. Keystone to manage user accounts and passwords.. al. n. Swift.. er. io. preserve a copy of each image in the VMIC Image archive. The image archive will use. i n U. v. For Glance, when the image is registered it is created a new entry in the image. Ch. engchi. service and a new image copy in the Glance store method.. Figure 3-1 is shown the. architecture and concepts of virtual machine image catalogue (VMIC) [34].. Image. administrator use VMIC or HEPiX tool to image lists with updated images, before publishing those image lists, image administrator uses HEPiX tool to subscript the image list and gets checksum to append the image file. Image information and metadata will save in OpenStack Glance and OpenStack Swift via Glance Application Programming Interface (API).. And Keystone will be used for the authentication with Glance server.. So users can search images and list all available images with VMIC.. And then they can. get the image’s location to download it. More details of this architecture and concepts 20 .
(29) will be explained later. . 政 治 大. 立. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. . Ch. i n U. v. Figure 3-1 the architecture and concepts of VMIC.. engchi. 3.2 Virtual Machine Image Catalogue Components 3.2.1 Command Line Interface The VMIC CLI is a simple interface to manage images and image list information; users could easily execute the related commands by following the instructions.. The. VMIC CLI tool will be used to interact with OpenStack Glance image service using the Representational. State. Transfer. (RESTAPI). provided.. According. to. different. data-interchange format, there are current three formats of metadata; eXtensible Markup. 21 .
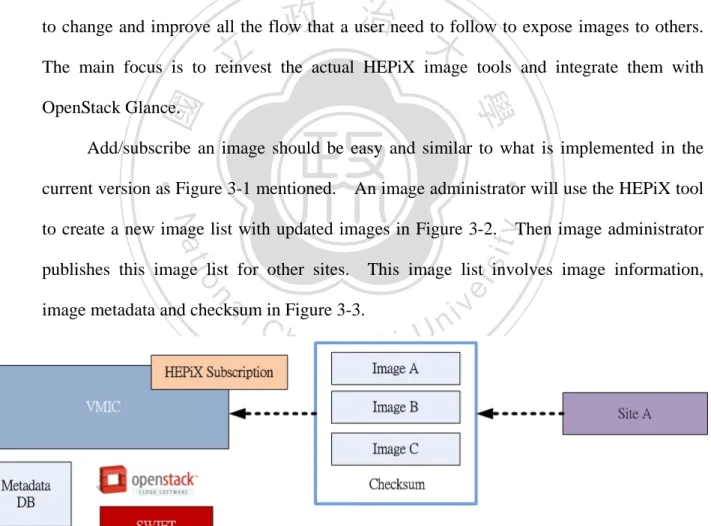
(30) Language (XML), Javascript Object Notation (JSON) and Yet Another Markup Language (YAML).. Hence image administrator is possible to create three kinds of image formats. depends on his requirement.. In short, the VMIC CLI is used for people to get trusted. images easily from the available image list.. 3.2.2 HEPiX Tool Subscription Deutsches Elektronen-Synchrotron (DESY) [35] from Germany developed a set of tools that allows sites to distribute and subscribe images.. With VMIC this system wants. 政 治 大. to change and improve all the flow that a user need to follow to expose images to others.. 立. The main focus is to reinvest the actual HEPiX image tools and integrate them with. ‧ 國. 學. OpenStack Glance.. Add/subscribe an image should be easy and similar to what is implemented in the. ‧. current version as Figure 3-1 mentioned. An image administrator will use the HEPiX tool. y. Nat. Then image administrator. sit. to create a new image list with updated images in Figure 3-2.. n. al. er. io. publishes this image list for other sites. This image list involves image information, image metadata and checksum in Figure 3-3.. Ch. engchi. i n U. v. Figure 3-2 import images from other sites.. 22 .
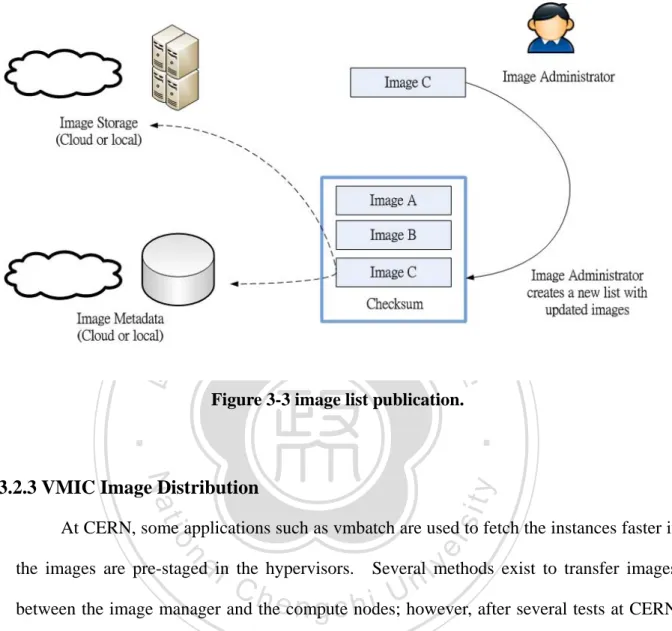
(31) . 立. 政 治 大 . ‧ 國. 學 Figure 3-3 image list publication.. ‧ y. Nat. sit. 3.2.3 VMIC Image Distribution. n. al. er. io. At CERN, some applications such as vmbatch are used to fetch the instances faster if. i n U. v. the images are pre-staged in the hypervisors. Several methods exist to transfer images. Ch. engchi. between the image manager and the compute nodes; however, after several tests at CERN they concluded that the BitTorrent protocol is the best option. BitTorrent is a protocol that underpins the practice of peer-to-peer file sharing and is used for distributing large amounts of data over the Internet [36]. A BitTorrent node is as a seed, more seeds can get faster speed of download.. When every VMIC (BitTorrent node) keep an image list, image. metadata in the Database and image files in Glance server. RTorrent as a BitTorrent client can catch image files on high performance and faster speed. So VMIC image distribution is used this protocol for image distribution.. 23 .
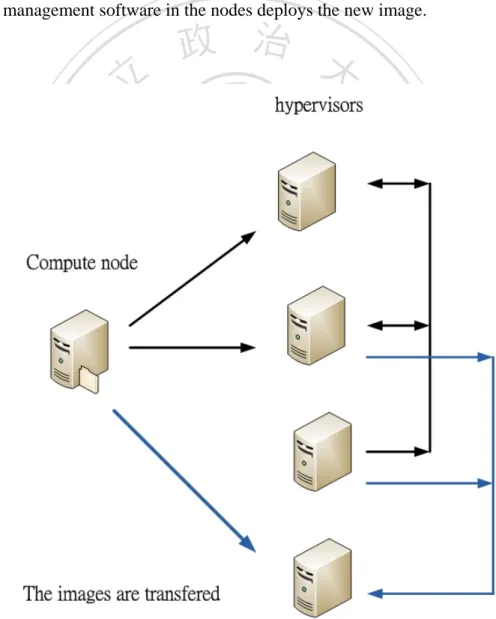
(32) Figure 3-4 is the steps of image distribution: a) The compute node queries VMIC for the image list. b) The image integrity is verified. c) Check which images are for the node. d) Download the torrent files for the desired images. e) Rtorrent downloads the images. f) Image management software in the nodes deploys the new image. . 立. 政 治 大 . ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. i n U. v. Figure 3-4 VMIC image distribution.. 24 .
(33) 3.2.4 Glance Module and Authentication with Keystone In Figure 3-5, when a user does some action of an image such as: added, removed or updated, the VMIC will preserve a copy of each image in the VMIC image archive by using Swift and in the Glance store method. which is used for the authentication.. In VMIC, Glance is integrated with Keystone. When editing the Keystone configuration files, it can. set images permission and owner attribute according to different requirements.. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. i n U. v. Figure 3-5 Glance Module and authentication with Keystone.. 3.3 Security Considerations of VMIC We have mentioned some virtual machine image security in 2.2.4, the VMIC is a catalogue system and to store virtual machine image metadata in Glance Swift. For cloud economical consideration, the VMIC will be used for different sites, different countries. More images transfers between each other, more attentions we have to pay on security. 25 . .
(34) events. Image metadata and image repository should be secured and stored in a safe place. Security patches of images should be updated regularly to avoid attacking. A reliable system is needed to help image administrator or users to check the safety of running and dormant virtual machine. We will propose some solutions in the next section.. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. 26 . i n U. v.
(35) 4 VMIC Security Improvement We have already mentioned about the whole system architecture of VMIC and pointed out its potential security problem.. VMIC is a convenient tool for users to list trusted virtual. machine image files; however, how to maintain information security will be a great challenge for the moment.. We expect the following research is able to improve VMIC system current. situation to protect users and image administrators.. 4.1 Security Improvement. 立. 政 治 大. By now, many industries began to use plenty of virtual machines to replace the. ‧ 國. 學. requirement of physical machines in cloud computing environment. machine can create multiple virtual machines to run specific programs.. Each physical So that industries. ‧. Since virtual machines are. Nat. y. could reduce enormous procurement and gain much efficiency.. n. al. er. However, this phenomenon makes users to ignore the security of. io. when system crashes.. sit. easily to be created and reset, creating a new virtual machine seems to be the prior way. i n U. v. virtual machines and reveal vulnerabilities for hackers to attack.. Ch. engchi. When a virtual machine. is infected by attackers, the attack may expand to other virtual machines via sharing memory, the connection of Internet or share resources.. In Figure 4-1, the attack is caused. by first virtual machine and expands to others.. Figure 4-1 VM Communication Attack on VM2 and VM3 [38].. 27 .
(36) Besides, not only physical machines are vulnerable but also virtual machines are as well.. For instance, there was some security incidents happened in Amazon EC2 when. users use cloud resource.. During the development of VMIC project, its original. environment tends to internal not the public. But VMIC will apply to the distributed cloud computing in global organizations or international corporations everywhere in coming future, security mechanism should be considered. Security staffs must keep trace of all machines involve of virtual machines to ensure their status is monitored and maintained well.. 政 治 大. When they are attacked, security staffs must have the ability to. 立. minimize losses in time when hackers attack.. ‧ 國. 學. We have mentioned virtual machine security events in 3-3, virtual machine image. ‧. metadata and image repository must be placed in a safe environment, and security patches. y. Nat. sit. from vendors should be updated regularly to avoid targeting attacks; moreover, some. n. al. er. io. monitoring tools (Shavlik HfnetchkPro, eEye Retina, Microsoft SUS or Pakiti) could assist. i n U. v. system administrators or security staffs to manage virtual machines when they are running.. Ch. engchi. Sometimes some unexpected problems appear after machines run for a period of time. At first these problems cannot detect, but afterwards they have vulnerabilities in computer applications that provide the attacker access to the system. A patch is a piece of software designed to fix problems includes security vulnerabilities, bugs and improve the usability or performance.. The problem is caused by poorly designed patches. After a patch has. been released by vendors, security staffs must notice and update the systems using this patch to keep off viruses, rootkits or worms.. Briefly speaking, Security patches are the. primary method of fixing security vulnerabilities in software [39]. 28 . In whole process,.
(37) security staffs must ensure to own the patch is up-to-date before updating. If a new machine increases suddenly in original system, security staffs have to examine their system status involves security patches are the newest as well. It is essential for security staffs to continue analyzing and monitoring all machines are far from vulnerabilities; moreover, they must notice all patches release from vendors and update at the short time.. Many security. vulnerabilities were caused by security staffs ignore to update security patches and let attackers can access to the systems with a malicious code. For this reason, an efficient. 政 治 大. tool is needed to monitor the patch status and report patches of all machines, such as Pakiti,. 立. In next section, we will discuss patch management tools in detail, and point out. 學. ‧ 國. Nuwa.. how to use it to improve the current VMIC system.. ‧. 4.2 Online Patch Management - Pakiti. y. Nat. sit. A growth of large scale grid and cloud infrastructures are in operation around the. n. al. er. io. world, which means that security staffs must be careful of the following security risk.. i n U. v. Unpatched security vulnerabilities are often misused by wicked attackers to control. Ch. engchi. machines or cause other harm to computers and other legal users. Security patch updates become one of the main causes of security incidents to affect computing infrastructures. Hence, having a proper and instant patch management is crucial to keep the system in safety and to resist common attacks targeting known weak spots. Pakiti [40] is a system that provides a monitoring and notification mechanism to check the patch status of machines.. Pakiti was originally designed by Steve Traylen in 2004 at the Rutherford Appleton Laboratory (RAL) UK.. In the beginning, it provided a simple client and server to enable 29 . .
(38) the team to detect the nodes where patches were missing.. Romain Wartel (RAL/CERN). took over this basic tool and transformed into Pakiti, hosted on SourceForge. EGEE Operational Security Coordination Team (OSCT) adopted this tool to start to monitor the security patch status of its more than 200 sites.. For the moment, Pakiti is used by plenty. of research organizations and computing infrastructures around the world.. 4.2.1 Pakiti Architecture. 政 治 大. Pakiti is a client/server model, where clients and servers are exchanging information. 立Once installed Pakiti service, Pakiti client will send the list of. using HTTP(S) protocol.. ‧ 國. 學. installed packages to the relevant Pakiti server(s) every night, then. Pakiti server compares. the versions against versions which Pakiti server obtains from packages repositories and. ‧. Open Vulnerability and Assessment Language (OVAL) [42] definitions from MITRE [43]. y. Nat. sit. who applying systems engineering and advanced technology to critical national problems.. n. al. er. io. OVAL is an XML language allowing specifying vulnerability, and OVAL identifies a. i n U. v. complete set of conditions that describe at least the version of software components.. Ch. engchi. OVAL is supported by RedHat, SuSe and Microsoft such as some large OS vendors. These vendors issue up-to-date version on each release of security patches.. The main. procedure of Pakiti can be defined as follows (see Figure 4-2). (1) The hostname of Pakiti server is giving in the client configuration and verified during the SSL/TLS handshake in order to reduce the risk of leaking sensitive information.. The cron jobs update scripts are run regularly, so all the information. is sent from Pakit client to the Pakiti server using HTTP POST over HTTPS. (2) When Pakiti server receives client’s patches information, these data will save in Pakiti DB such as Mysql. 30 .
(39) (3) After receiving information from clients, Pakiti server will make a list on the website. (4) Up-to-date patches information is provided according to packages repositories or CVEs by cron jobs. (5) By another way, Pakiti clients do not send information to server directly. They transfer patches information to Nagios this monitoring tool. (6) When Nagios server catches these patches information, it will send them to Pakiti server.. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. i n U. v. Figure 4-2 Pakiti environment.. Pakiti uses a Web page provides a list of the registered systems and the list of the pending patches for them.. This helps security staffs to keep multiples machines. up-to-date and prevent unpatched machines to be kept silently on the network. In addition, 31 .
(40) a security module in Pakiti is able to distinguish security fixes from normal bug fixes/product improvement for all Linux distributions which has packages repositories based on rpm (yum) or dpkg (apt) and has different location for normal and security updates.. For Linux distributions based on the RedHat, Pakiti is able to check packages. against the Common Vulnerabilities and Exposures (CVEs) [44]. In the next release Linux distros based on SuSE will be also checked. Debian based distros are also a candidate, but Debian currently does not provide approved data in CVE format [41].. 立. 政 治 大. CVE (Common Vulnerability and Exposure) is an international security organization,. ‧ 國. 學. the most credible to expose security weaknesses and publish news. For the moment, CVE cooperates with many global organizations and product manufacturers. CVE is a unified. ‧. vulnerability number of format and report message from firewall, antivirus software,. y. Nat. Each published. sit. intrusion detection systems, and system vulnerability scanning tools.. n. al. er. io. weakness has only CVE number (for example, CVE-2008-0234), to ensure this weakness is already identified and described.. Ch. unified with the standard numbers.. i n U. v. Each independent weakness number databases are. engchi. By now, Pakiti has been utilized by many organizations in the world especially EGI Computer Security and Incident Response Team (CSIRT) on daily basis. According to the result of the risk assessment, EGI CSIRT uses it to monitor all related sites.. When EGI. CSIRT finds these sites are running the vulnerable software, they contact site managers and ask to apply the updates immediately.. If site managers ignore notifications without. updating security patches in time, EGI CSIRT will follow the critical vulnerabilities handling procedure to suspend these sites to avoid unstoppable risks. Every day the EGI Pakiti server receives more than 2300 reports from EGI 32 .
(41) production sites.. Only Authorized EGI CSIRT members and site security staffs can check. the result through a web interface (https://pakiti.egi.eu/). An alerting email will also be sent to EGI CSIRT if a critical vulnerability has been detected. Until 2012, Pakiti server has collected about 400,000 reports from 22,000 nodes of 335 production sites over 6 months period [45]. Moreover, Pakiti is enough to be integrated into an existing monitoring infrastructure. There are two ways from Pakiti server receive all information from clients.. First is. traditional way that the client sends the data directly to the server using HTTPS.. Second. 立. 政 治 大. is the client prints the data to its standard output, to let another monitoring tool such as. ‧ 國. 學. Nagios [46] transfer the data to the server using another messaging mechanism.. ‧. 4.3 Offline Patch Management. sit. y. Nat. By now, there are many kinds of commercial or non-commercial software to manage. io. al. er. patches on the market, however, most of them are focus on online system not offline system.. n. Nuwa is researched in an offline manner.. Ch. engchi. i n U. v. 4.3.1 Nuwa American North Carolina State University and IBM have invented a new way to update system patches in cloud virtual machines even if those system programs are offline. The new patch management tool developed by them is called Nuwa [47].. It not only. protects virtual machines from malicious attacks but also ensures these virtual machines always receive important security upgrades. Nuwa avoids the expensive virtual machines start and stop time, it ensures when a virtual machine image is ready to be started, it has the up-to-date patches installed. In addition, the researchers have determined that offline. 33 .
(42) application of security patches is more than four times faster than online patch application. Current patch management systems are designed for computers that are online and they do not work for dormant computers. Nuwa is developed automatically analyzes the ‘script’ that dictates how a security patch is installed, and then automatically re-writes the script to make it compatible with an offline system.. Usually patch scripts are written in shell scripts. In fact, patching an offline virtual. 政 治 大 When presented with a patch, Nuwa first performs safety analysis 立. machine image, one thing needs to care about is the changes made to the file system in the virtual machine image.. ‧ 國. If all scripts are safe, Nuwa utilizes. 學. on the patch scripts included in the original patch.. simple emulation-based patch directly to perform offline patch.. If some scripts are unsafe,. ‧. Nuwa applies various rewriting techniques to these scripts, and performs safety analysis on. sit. y. Nat. the rewritten scripts. If these rewriting techniques can successfully convert the unsafe. io. al. er. scripts to safe one, Nuwa will utilize simple emulation-based patch with the rewritten patch. iv n The U patch host can mount and access an. n. to finish offline patch. Emulation-based patch is to perform the file replacement actions. Ch. engchi. from another host, referred to as the patch host.. offline virtual machine images as a part of its own file system.. Using the chroot [48]. system call to change the root file system to the mount point, the patch host can emulate an environment required by the patch process on a running virtual machine and perform the file system actions originally developed for patching a running virtual machine.. Therefore. if some scripts are unsafe, Nuwa applies various rewriting techniques to successfully convert the unsafe scripts to safe ones. Figure 4-3 shows the rewriting techniques that Nuwa applies before executing each patch script.. Rewriting a script can change the. results of safety analysis, so Nuwa returns safety analysis after applying these techniques.. 34 .
(43) If safety analysis proves that all command lines in the script are safe, then the rewritten script is executed offline.. Otherwise, Nuwa resorts to online patch.. 立. 政 治 大. ‧ 國. 學. Figure 4-3 Flow of script analysis and rewriting[47].. ‧ sit. y. Nat. Nuwa utilizes and improves Mirage [30] techniques that developed by IBM, that is. io. er. used for performing efficient offline introspection and manipulation of a large collection of. al. v i n C h exists that allows A program already e n g c h i U cloud computing systems to operate n. virtual machine images, to allow cloud administrators to patch multiple virtual machines simultaneously.. more efficiently by saving one version of a computer file that is used by multiple virtual machines, rather than saving the same file repeatedly for each individual virtual machine. Nuwa takes advantage of this technology and, by patching one file, can ultimately protect all of the virtual machines that use that file. Figure 4-4 shows the two phases of batch patch via Mirage.. Phase 1 performs the loop-invariant operation: Nuwa extracts the. patch’s files and imports them into Mirage. for each file.. The result is a list of content identifiers, one. In phase 2, Nuwa iterates over the images. For each image, Nuwa mounts. the image with Vmount, rewrites and executes the pre-installation scripts, emulates the. 35 .
(44) “unpack” step of the package manager (e.g., dpkg), using the Mirage file system attribute to set the contents of the patch’s files, rewrites and executes the post-installation scripts, and checks in the modified virtual machine image. If script rewriting ever fails to produce a safe script, then Nuwa resorts to online patch. North Carolina State University and IBM have successfully tested and evaluated Nuwa on the IBM Research Compute Cloud, a compute cloud that is used by IBM researchers worldwide.. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. i n U. v. Figure 4-4 Batch patch virtual machine images via Mirage[47].. As the result, Nuwa is a novel tool to enable efficient patch of offline virtual machine images.. It uses safety analysis and script rewriting techniques to convert patches, or more. specifically the installation scripts contained in patches, which were originally developed for online updating, into a form that can applied to virtual machine images offline. advantage will be useful to improve online or offline virtual machine image security 36 . Its.
(45) patches.. 4.4 Method: Patch Management in VMIC System To be brief, Pakiti is an open source lightweight system that helps to monitor security patches status and informs authorized members to handle critical patches carefully. Nuwa is applied in checking security patches in dormant virtual machines.. Those functionalities. could make contribution on the existing VMIC system to improve its security mechanism.. 立. 政 治 大. According to previous VMIC introduction in 3-1, image administrators use VMIC or. ‧ 國. 學. HEPiX tool to create image lists with updated images, before publishing those image lists,. ‧. image administrator can use HEPiX tool to subscribe the image list and gets checksum to. And Keystone will be used for the. er. io. sit. Nat. Glance and OpenStack Swift via Glance API.. y. append the image file. Image information and metadata will be saved in OpenStack. authentication of image administrators with Glance server. After that, users can search. n. al. Ch. i n U. v. trusted images and list all available images with VMIC to download those images from current locations.. engchi. The problem is that there is no security mechanism to help image. administrators to check security patches of image files.. Following this explanation, we. expect to use patch management service to trace all virtual machines before image administrators subscribe the image list with HEPiX tool and publish with VMIC. In Figure 4-5 showed the ideal security patch management service in VMIC environment.. 37 .
(46) . 政 治 大. 立. ‧. ‧ 國. 學. Nat. n. al 4.4.1 Pakiti in VMIC System. er. io. sit. y. Figure 4-5 Patch management in VMIC system.. Ch. engchi. i n U. v. To evaluate the effect of the proposed approach, VMIC service and HEPiX virtualization working group tool are installed in one dedicated machine.. Another. standalone is for Pakiti server to monitor all virtual machine patches status. Pakiti client is installed in each virtual machine that will be subscribed by HEPiX virtualization working group tool and registered in VMIC.. 38 .
(47) 立. 政 治 大. ‧. ‧ 國. 學 Figure 4-6 Pakiti Service in VMIC.. n. er. io. al. sit. y. Nat. The procedure of this approach below in Figure 4-6:. i n U. v. (1) Each virtual machine installs Pakiti client on the host and it connects Pakiti server via SSL/TLS and HTTPS. Ch. engchi. (2) Pakiti server makes a patch status list every day from each Pakiti client, the current patch information is from CVEs and software’s repositories (3) Before Image administrators subscribe virtual machine images, each Pakiti client should transfer their patches information to Pakiti server to ensure security patches are up-to-date (4) Image administrators use HEPiX virtualization working group tool to subscribe an image list (5) Image information and metadata is stored with VMIC 39 .
(48) (6) Users can choose and download safe virtual machine images from VMIC. 4.4.2 Nuwa in VMIC System In this approach, VMIC service and HEPiX virtualization working group tool are installed in one dedicated machine.. Nuwa is installed in OpenStack File system to do. safety analysis and script rewriting to check security patch status.. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. i n U. v. Figure 4-7 Nuwa Service in VMIC.. engchi. The procedure of this approach below in Figure 4-7: (1) Nuwa is installed in OpenStack File system, for example: Swift (2) Image administrators use HEPiX virtualization working group tool subscribe virtual machine images (3) Image administrators use HEPiX tool to subscribe an image list (4) Image information and metadata is registered and stored in File System of (5) Nuwa will do safety analysis and script rewriting. 40 . VMIC.
(49) (6) Users can choose and download safe virtual machine images from VMIC. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. 41 . i n U. v.
(50) 5 Implementation of VMIC Security Improvement Patch management is assumed to improve current security environment in VMIC according to previous descriptions. Pakiti is an open source to download from its official website (http://pakiti.sourceforge.net/) freely. Nuwa is invented by American North Carolina State University and IBM, and is integrated with the Mirage image library, which stores identical files once and treats images as logical views on this collection of file.. By now,. 政 治 大 Since Nuwa is a commercial tool. Nuwa is applied in IBM Research Compute Cloud (RC2).. 立. that belongs to IBM, it is not an open source to retrieve resource or source code with ease.. ‧ 國. 學. In this thesis, Nuwa will not be implemented without charge. In this implementation patch management will focus on Pakiti application.. ‧. client program is running at local clients.. EGI CSIRT is utilized by Pakiti server and the. When client scripts run regularly, the total reports. y. Nat. sit. will be shown on EGI Pakiti server which is authenticated by HTTPS.. The version 3.0 of. n. al. er. io. EGI CSIRT Pakiti server is chosen to design for the environments with the 10.000+ hosts and. i n U. v. should provides capabilities to be easily integrated into the existing monitoring infrastructures.. Ch. engchi. 5.1 Pakiti Client Pakiti Client runs a simple script as a cron job every day; the Pakiti client software can be downloaded from EGI CSIRT websites and the parameters are modified to fit for this implementation.. When unpacking downloaded client software, there are two. directories, etc and opt in current path. The primary Pakiti client script is in opt directory and the client cron script is in etc.. The client cron script (Figure 5-1) is stored in. /etc/cron.daily and Pakiti client will be lunched every day.. 42 .
(51) Figure 5-1 The Pakiti client cron script.. 5.2 Pakiti Server Since the EGI CSIRT Pakiti server is authenticated by HTTPS, so personal. 政 治 大. certificates should be imported to the browser in advance and the Distinguished Name (DN). 立. is registered to Access Control List (ACL) on EGI CSIRT Pakiti server.. The user have to. ‧ 國. 學. login by personal certificate such as “C=TW/ O=AS/ OU=GRID/ CN=Chen Yi Chien 124172” for access control of the Pakiti server. After accessing the main page, hosts can. ‧. Nat. y. be searched by different classifications on the top toolbar. Hosts are searched by sites and The web page lists all current. sit. the country as Taiwan is chosen with the pull-down menus.. n. al. er. io. site names that register country information as Taiwan (See Figure 5-2).. i n U. If the security. v. patches are out-of-date, the warning information in red will be displayed to remind security staffs.. Ch. engchi. Only vulnerable hosts will be shown on this list not all hosts. It helps security. staffs to point out problem immediately.. Figure 5-2 Hosts list on Pakiti server and this list sorts hosts by country.. 43 .
(52) For more details of the vulnerable site, click on the site name.. In Figure 5-3,. puppetmaster is the hostname which has 2 security vulnerabilities and 5 related CVE events. Clicking the hostname to access security patch warning in Figure 5-4, there are all CVE numbers of this vulnerable hostname and all warning security packages need to be updated. In this case, there are five CVE numbers (2010-2761, 2010-4410, 2011-1487, 2011-2939 and 2011-3597) affected by puppetmaster host. These security patches are shown in the left since many Perl packages need to be updated. CVE-2010-2761 is clicked to get the. 政 治 大. package names and versions in Figure 5-5.. 立. The Pakiti server is user-friendly to provide the URL for security staffs to connect the. ‧ 國. 學. official CVE website to search solutions. For example, when CVE-2010-2761 in bold URL on the top is clicked; this main page will connect to Red Hat official website.. In. ‧. Nat. This page provides bug information and useful RPM to. sit. our host machine for update.. y. Figure 5-6, CVE-2010-2761 and CVE 2010-4410 indicate some related Perl packages on. n. al. er. io. download for updating.. Ch. engchi. i n U. v. Figure 5-3 security events and CVEs statistics.. 44 .
(53) . 政 治 大. Figure 5-4 all vulnerable CVEs on puppetmaster host.. 立. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. i n U. v. Figure 5-5 package names and version of CVE-2010-2761.. Figure 5-6 CVE-2010-2761 and 2010-4410 on Red Hat.. 45 .
(54) In above case, Pakiti client software is installed on a local host (puppetmaster) and EGI CSIRT Pakiti server monitors vulnerable sites.. For this experiment, no security patch. is updated in advance, so security patches on puppetmaster should be out-of-date.. When. Pakiti server collects client information and publishes on its website, puppetmaster is displayed on the list and the server provides some details of CVEs for finding solutions to fix these security patches problem. In conclusion, Pakiti provides a solution to keep security patches up-to-date; as a. 政 治 大. result, Pakiti clients should be installed in physical machines or virtual machines when. 立. those machines register in VMIC system.. This improvement facilitates machines to. ‧ 國. 學. receive the latest patches in VMIC. So before users download virtual machine images from VMIC, Pakiti server has been monitored security patches and reported to security staffs in. ‧. advance, to guarantee virtual machines images in VMIC are safe.. n. er. io. sit. y. Nat. al. Ch. engchi. 46 . i n U. v.
(55) 6 Future Work The purpose of this research expresses Pakiti improves security in VMIC because of security patches monitoring.. However, not all physical or virtual machines have been in a. running state, security staffs should be pay much attention to those dormant machines In order to ensure all virtual machines images to defend all attacks, Pakiti should be applied to monitor the states of dormant machines such as Nuwa. Nuwa is different than. 政 治 大. Pakiti server to check security patches during registering to VMIC.. 立. When images and. image lists are subscribed by HEPiX tool and registered to VMIC, all image files are stored in. ‧ 國. 學. VMIC file system.. After that, Nuwa will do the safety analysis and script rewriting in. VMIC file system (OpenStack Swift), Nuwa is valuable to trace those offline virtual machine. ‧. images and update their security patches in time.. As the result, Nuwa not only examines. y. Nat. sit. online virtual machines but also offline virtual machines in current VMIC environment.. On. n. al. er. io. the other hand, a friendly web interface for VMIC is needed, not only users but also image. i n U. v. administrators can search or manage virtual machines via this web interface.. Ch. engchi. There are some enhancements for VMIC in progress.. OpenStack has its specific. dashboard (Horizon) [49] to connect all OpenStack components via API.. VMIC could. integrate with OpenStack dashboard in web services based system, and provides identity management services to protect user accounts and passwords are required for authentication and authorization [50] [51] [52].. Or it is better to provide one-time password authentication. which utilizes dynamic password facilitates to enhance the security of password [53].. When. VMIC web interface provides an entrance with user accounts and passwords, secure password recovery is valuable and essential for VMIC to protect user's sensitive information or avoid malicious attackers [54] [55] [56]. 47 .
(56) In the future, security staffs must strengthen its security in offline patch management, identity management and password recovery schemes in VMIC.. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. 48 . i n U. v.
(57) 7 Conclusion This paper has investigated the security improvement of current VMIC system to strengthen its patch management and monitoring to avoid malicious attacks.. Pakiti collected. patch reports from its clients and published via web pages. As a result, security staffs could control all virtual machines’ patch status timely and updated them.. According to the result,. Pakiti was able to monitor plenty of machines effectively but did not increase servers’. 政 治 大. overloading. In addition, Pakiti is an open source for customization to apply in customers’. 立. However, VMIC has already improved partial security functions; it. 學. ‧ 國. current environments.. still has some security subjects needed further researches, for instance, offline patch management, identity management and password recovery schemes.. ‧. will be focused on these security improvements.. n. er. io. sit. y. Nat. al. Ch. engchi. 49 . i n U. v. The future researches.
數據
![Figure 2-2 Cloud computing layers [1].](https://thumb-ap.123doks.com/thumbv2/9libinfo/8330827.175472/14.892.137.803.160.818/figure-cloud-computing-layers.webp)
相關文件
家長 聯絡網 親子活動 A教學管理 B學務管理 C輔導管理 D環境管理 E行政管理
利用 Microsoft Access 資料庫管理軟體,在 PC Windows 作業系 統環境下,將給與的紙本或電子檔(如 excel
1) Ensure that you have received a password from the Indicators Section. 2) Ensure that the system clock of the ESDA server is properly set up. 3) Ensure that the ESDA server
School year setting is designed for defining current school year of the system. School should update this information at the beginning of each school year before importing
Note that if the server-side system allows conflicting transaction instances to commit in an order different from their serializability order, then each client-side system must apply
However, if the EAP Identity does match a client Identifier and the CredentialState is Accepted the EAP server proceeds with the authentication process and verifies the credential
• Given a (singly) linked list of unknown length, design an algorithm to find the n-th node from the tail of the linked list. Your algorithm is allowed to traverse the linked
• The Health Information Technology for Economic and Clinical H ealth (HITECH) Act seeks to improve American health care deli very and patient care through an unprecedented
![Figure 2-5 VMIC architecture and concept [18].](https://thumb-ap.123doks.com/thumbv2/9libinfo/8330827.175472/21.892.219.674.276.783/figure-vmic-architecture-and-concept.webp)
![Figure 2-6 VMIC image endorsing and trusting of distribution [20].](https://thumb-ap.123doks.com/thumbv2/9libinfo/8330827.175472/22.892.184.778.405.838/figure-vmic-image-endorsing-trusting-distribution.webp)