A Copyright Protection Scheme for Gray-Level Images Based on Image Secret Sharing and Wavelet Transformation
全文
(2) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. suitable for the application in which the modification of the image is not allowed. For example, satellite images can not allow any modification on them because it will affect their precision. Second, the scheme is secure. By applying the technique of ISS, only the user who has the secret image can retrieve the watermark. Last, the scheme is robust. The experimental results show that the scheme can withstand 5 kinds of image processing operations. The rest of this paper is organized as follows. Chapter 2 explains the DWT and the observation. Chapter 3 describes the proposed image protection scheme. Chapter 4 examines the experimental results. Finally, Chapter 5 states the conclusions.. Figure. 1. Two-level DWT decomposition of Lena.. 2. Consideration on DWT Coefficients The proposed scheme generates features from the DWT coefficients. This section briefly explains the discrete wavelet transformation and the observation on the DWT coefficients, which leads to the adoption of the LL2 subband.. Figure. 2. DWT coefficients after compression.. The DWT is identical to a hierarchical subband system. The basic idea of the DWT for an image is described as follows. An image is first decomposed into four subbands LL1, LH1, HL1, and HH1. The subbands LH1, HL1, and HH1 represent the finest scale wavelet coefficients. To obtain the next coarser scale wavelet coefficients, the LL1 subband can be decomposed similarly and divided into four subbands LL2, LH2, HL2, and HH2 . The same decomposing procedure can be applied until there is only one coefficient left in the LL subband. Fig. 1 shows the image “Lena” and it’s two-level DWT decomposition.. [14] is one kind of lossy image compression schemes in JPEG 2000. The SPIHT compression uses the characteristic of DWT to discover important coefficients that need to be preserved as well as unimportant coefficients that can be discarded. To find out which subband of DWT coefficients is reliable after SPIHT compression, the SPIHT is used to compress the image L to obtain the image L’, and then DWT is applied two times on L’ (Fig. 2 shows an example of the result). We noticed that most of the coefficients in each subband except LL2 became zero and only a small amount of coefficients were preserved after the compression. The coefficients in the LL2 subband were mostly preserved. Moreover, the change of the LL2 coefficients was slighter than that in the other subbands. Hence, the proposed scheme generates features from the coefficients in the LL2 subband.. 2.2 Observation on DWT Coefficients during Lossy Image Compression. 3. The Proposed Copyright Protection Scheme. Lossy image compression can effectively attack the features of an image with slightly decreasing the image quality. The SPIHT lossy image compression. The proposed scheme contains two phases: secret image generation and watermark retrieval. Fig. 3 shows the block diagram of the proposed. 2.1 Discrete Wavelet Transformation. Figure. 3. The block diagram of the proposed scheme.. 662.
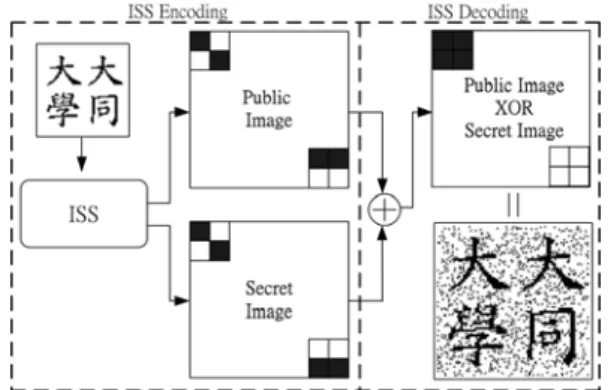
(3) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. Figure. 4. The scrambled watermark. scheme. The feature extraction in the secret image generation phase first extracts the features of the host image. Then, the watermark scrambling disarranges the watermark with a secret key. Finally, the ISS encoding generates the secret image using the features and the scrambled watermark. To retrieve the watermark, the feature extraction in the watermark retrieval phase first extracts the features of the suspect image. The ISS decoding then uses the features and the secret image to retrieve the scrambled watermark. Next, the watermark unscrambling rearranges the scrambled watermark. Finally, the watermark reduction regains the watermark. The retrieved watermark is then used to verify the copyright.. Figure. 5. The image secret sharing scheme. C’1≥C’2≥C’3≥C’4). The feature type n of this block is obtained by the following equation:. ⎧ ⎪ ⎪ n=⎨ ⎪ ⎪⎩. 1, if C '1 ≥ M > C ' 2 2, if C ' 2 ≥ M > C '3 3, if C '3 ≥ M > C ' 4 4, otherwise. (2). 3.1 The Major Parts in the Proposed Scheme. 3.1.3 ISS Encoding & Decoding. The proposed scheme contains four major parts. The following sections describe the details of them.. According to the average M and the extracted feature type n, a public block (block1) of 2 × 2 pixels is generated. Then, each pixel of the watermark can be mapped into a secret block (block2) of 2 × 2 pixels according to the pixel value of the watermark. The public blocks form the public image and the secret blocks form the secret image. Fig. 5 shows the proposed ISS scheme. Table 1 lists the mapping table used in the proposed ISS. Each generated image has a size of 2s × 2s, when the watermark has a size of s × s. The encoding process uses the extracted feature types and the watermark to generate the secret blocks of the secret image. The secret block is generated according to one of the following rules: (a) If a pixel of the watermark is white and the 2 × 2 block1 of the public image is type n (n=1, …, 4), then the corresponding secret 2 × 2 block2 in Table 1 is selected. (b) If a pixel of the watermark is black and the 2 × 2 block1 of the public image is type n (n=1, …, 4), then the corresponding secret 2 × 2 block2 in Table 1 is selected. The decoding process applies XOR operation on the block1 of the public image obtained from the suspect image and the corresponding block2 of the saved secret image generated from the original host image to retrieve the scrambled watermark. The scrambled watermark is then processed by the watermark unscrambling.. 3.1.1 Watermarking Scrambling & Unscrambling Torus-automorphism is used to scramble the watermark in the secret image generation phase and unscramble the scrambled watermark in the watermark retrieval phase. Voyatzis and Pitas [12] proposed a Torus-automorphism with a single coefficient. The transform function is represented by the following equation:. 1 ⎞⎛ xt ⎞ ⎛ xt +1 ⎞ ⎛ 1 ⎜⎜ ⎟⎟ = ⎜⎜ ⎟⎟⎜⎜ ⎟⎟ mod N ⎝ y t +1 ⎠ ⎝ k k + 1⎠⎝ y t ⎠. (1). where (xt , yt) are the coordinates in the two dimensional space, and t is the number of states. N denotes the size of the given image and k denotes the secret key, which can be arbitrarily chosen by the owner. If a pixel p is placed in the coordinates (x0 , y0), then after t states, the pixel p will be placed in the coordinates (xt , yt). Fig. 4 shows the watermark that has been scrambled five times using Eq. (1). 3.1.2 Feature Extraction Before the feature extraction, the host image is divided into non-overlapping 8 × 8 blocks and the pixels of each block are transformed to DWT coefficients. After applying DWT two times, the LL2 subband of each block has four coefficients. Let M be the average of the four coefficients and C’n (n=1, ..., 4) be the four coefficients in descending order (i.e.,. 3.1.4 Watermark Reduction When the original watermark pixel is white and the feature type is 1 or 3, some redundant noise on. 663.
(4) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. Table 1. The mapping table in ISS. Feature Type n. The watermark pixel is white Pubic Secret Block1 Block2. Average Location. a. M. b,c,d. b. M. a,c,d. c. M. a,b,d. d. M. a,b,c. Block1 XOR Block2. The watermark pixel is black Pubic Secret Block1 Block2. Block1 XOR Block2. Figure. 6. The reduced watermark. Fig. 6 shows an example of the result after the watermark reduction.. 1. 3.2 Secret Image Generation Phase. a,b. M. c,d. c,d. M. a,b. a,d. M. b,c. b,c. M. a,d. a,c. M. b,d. b,d. M. a,c. The following lists the detailed steps in the proposed secret image generation phase.. Secret Image Generation Algorithm Input: a gray-level host image h (N1 × N2), a watermark l (n1 × n2 ), and a secret key. Output: a secret image s (s1 × s2) used to retrieve the watermark.. 2. b,c,d. M. a. a,c,d. M. b. a,b,d. M. c. a,b,c. M. d. Step1.Use Torus-automorphism and the secret key to scramble the watermark l into l’ Step2.Divide the host image h into non-overlapping 8 × 8 blocks h(k), k=1, 2, …, N1 / 8 × N2 / 8 and the scrambled watermark l into a binarydigit sequence l(k), k=1, 2, ..., n1 × n2. Step3.Set k to be 1. Step4.Transform the host image block h(k) into 4 DWT coefficients by two-level decomposition. Step5.Use the mapping table and the relationship between the 4 coefficients and their average to find out the feature type of block h(k), and hence the corresponding public block p(k). Step6.Map the corresponding scrambled watermark block l’(k) into the secret block s(k). Step7.Increase k by 1. If k ≦ (N1 / 8 × N2 / 8) go to step4. Step8.Save the secret key and the secret image s for the watermark retrieval phase.. 3. 4. M =a,b,c,d. a. b. c. d. The four coefficients of the LL2 subband ( a is in the top left, b in the top right, c in the bottom left, and d in the bottom right position) one of the three dotted blocks is black and the other two are white. 3.3 Watermark Retrieval Phase. one of the three dotted blocks is white and the other two are black. The following lists the detailed steps in the proposed watermark retrieval phase.. The blocks with slanted lines may be black or white depending on the XOR operation of the corresponding subblocks of block1 and block2. the background of the unscrambled watermark will be generated due to the nature of ISS. To regain the original watermark from the unscrambled watermark, a watermark reduction process is used to remove the redundant noise caused by the image secret sharing scheme. According to the generated block by XOR, one of the following two steps will be adopted: (a) when the number of white pixels of the generated block is equal to 1 or 0, the block is reduced to a black pixel. (b) when the number of white pixels of the generated block is greater than 1, the block is reduced to a white pixel.. Watermark Retrieval Algorithm Input: a gray-level suspect image h’ (N1 × N2), a secret image s (s1 × s2), and the secret key. Output: a reduced watermark lR (n1 × n2 ). Step1.Divide the host image h’ into non-overlapping 8 × 8 blocks h’(k) , k=1, 2, ..., N1 / 8 × N2 / 8 and the secret image s into non-overlapping 2 × 2 blocks s(k), k=1, 2, ..., s1 / 2 × s2 / 2. Step2.Set k to be 1. Step3.Transform the host image block h’(k) into 4 DWT coefficients by two-level decomposition.. 664.
(5) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. Step4.Use the mapping table and the relationship between the 4 coefficients and their average to find out the feature type of block h’(k), and hence the corresponding public block p’(k). Step5.Apply XOR operation on the public block p’(k) and the corresponding secret block s(k) to produce the corresponding scrambled watermark block l’(k). Step6.Increase k by 1. If k ≦ (N1 / 8 × N2 / 8) go to step3. Step7.Use Torus-automorphism and the secret key to rearrange the watermark l’ into l. Step8.Use watermark reduction process to reduce the unscrambled watermark l into the reduced watermark lR.. Figure. 7. The test image “Lena” (512×512).. 4. Experimental Results We conducted a series of experiments to measure the feasibility of the proposed scheme. Fig. 7 shows the 256 gray-level host image “Lena” used in the experiment. Fig. 8 shows the watermark and the generated secret image. The commercial image processing software, Ulead PhotoImpact 7.0, was used to simulate different kind of attacks. The peak signal to noise ratio (PSNR) is used to evaluate the image quality after image processing operations. The PSNR of gray-level image is defined as follows: PSNR = 10 log10. 255 2 dB MSE. (a) (b) Figure. 8. (a) the watermark (64×64); (b) the secret image (128×128). Table 2. The experiment results.. Quality factor. MSE =. N. ∑∑ ( x i =1 j =1. ij. N. − xij' ) 2. AR(PSNR). (3). Variance. CP NP. 75%. 0.873(34.2) 0.895(36.4) 0.939(38.6). 3. 2. 1. Blurring AR(PSNR). (4). 2. Variance. where xij denotes the original pixel value, and x’ij denotes the test pixel value. The Accuracy rate (AR) is used to measure the original watermark and retrieved one. AR is defined as follows:. AR =. 50%. JPEG. The mean square error (MSE) for an N × N graylevel image is defined as follows: N. 25%. 0.860(29.3) 0.875(29.8) 0.908(34.2). 3. 2. 1. Sharpening AR(PSNR) Width&Heigh. 0.863(23.6) 0.917(29.3) 0.950(35.2). 64x64 128x128 256x256. (5). Scaling. where NP is the number of pixels in the original watermark and CP is the number of the correct pixels obtained by comparing the pixels of the original watermark with the corresponding ones of the retrieved watermark. The more closely AR approaches 1, the more closely the retrieved watermark resembles the original one. Table 2 lists the experimental results (the PSNR results denote the quality of “Lena” after image processing operations). The experiment results show. AR(PSNR) Cropped area. 0.732(24.2) 0.861(28.1) 0.926(34). 50%. 25%. 10%. 0.874. 0.938. 0.975. Cropping AR. 665.
(6) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. [3]. [4]. (a). (b). Figure. 9. (a) the test image “Tiffny”; (b) the retrieved watermark. that the retrieved watermarks are still recognizable under the attacks of the JPEG compression, the blurring, the sharpening, the scaling (except for 64 × 64), and the cropping. The accuracy rate also shows that when AR is closer to 1, the retrieved watermark is more distinct. Moreover, when the suspect image is actually a different image from the original one, the retrieved watermark will contain nothing more than noise. Fig. 9 shows the test image “Tiffny” and the retrieved watermark. The image “Tiffny” is different from our original image “Lena”. After the watermark retrieval, the accuracy rate of the retrieved watermark of “Tiffny” is 0.517. The retrieved watermark contains only noise and no information about the original watermark.. [5]. [6]. [7]. [8]. [9]. [10]. 5. Conclusions In this paper, we proposed a copyright protection scheme based on image secret sharing (ISS) and discrete wavelet transformation (DWT). The proposed scheme contains the secret image generation phase and the watermark retrieval phase. In the generation phase, the scheme extracts the features from a host image using DWT, and then uses the features and the watermark to generate the secret image using ISS. In the retrieval phase, the watermark is retrieved by combining the secret image and the features obtained from the suspect image. The accuracy rate is then used to measure the similarity between the retrieved watermark and the original one. The scheme has the following advantages: (1) it does not modify the host image because it only extracts features and does not change any pixels; (2) it is secure because of the application of the secret key and ISS, and (3) it is robust according to results of the experiment. Because the proposed scheme does not alter the host image, it is very suitable for unchangeable images such as medical images and satellite images.. [11]. [12]. [13]. [14]. References [1]. [2]. R. G. van Schyndel, A. Z. Tirkel, and C. F. Osborne, “A digital watermark” Proc. IEEE Int. Conf. Image Processing, vol. 2, pp.86-90, 1994. C.-C. Wang, S.-C. Tai, and C.-S. Yu, “Repeating image watermarking technique by the visual. 666. cryptography,” IEICE Trans. Fundamentals. Signal processing, vol.E83-A, pp.1589-1598, 2000. M. Kutter, F. Jordan, F. Bossen, "Digital signature of color images using amplitude modulation," Proc. of SPIE storage and retrieval for image and video databases, San Jose, USA, no. 3022-5, pp. 518-526, February 13-14, 1997. Inoue H., Miyazaki A., Yamamoto A. and Katsura T., “A Digital Watermark Technique Based on the Wavelet Transformation and Its Robustness on Image Compression and Transformation,” IEICE Trans. Fundamentals of Electronics, Communications and Computer Sciences, vol. E82-A no. 1 pp. 2–10, Jan. 1999. M. Iwata, K. Miyake and A. Shiozaki, “Digital watermarking method to embed index data into JPEG images,” IEICE Trans. Fundamentals, vol.E85-A, no.10, pp.2267-2271, Oct. 2002. S. Pereia and T. Pun, “Robust template matching for affine resistant image watermarks,” IEEE Trans. Image Processing, vol. 9, pp. 1123-1129, 2000. Ming-Shing Hsieh, Din-Chang Tseng, and YH Huang, “Hiding digital watermarks using multiresolution wavelet transform,” IEEE Trans. Industrial Electronics, vol.48, no.5, pp.875-882, Oct. 2001. M. Kuribayashi and H. Tanaka, “A new digital watermarking scheme applying locally the wavelet transform,” IEICE Trans., Fundamentals, vol. E84-A, no. 10, pp. 2500-2507, 2001. SH Wang and YP Lin, “Wavelet tree quantization for copyright protection watermarking,” IEEE Trans. Image Processing, Feb. 2004. FOTOPOULOS, V. and SKODRAS, AN: “A New Fingerprinting Method for Digital Images”, Proc. First IEEE Balkan Conference. Signal Processing, Communications, Circuits and Systems, Istanbul, Turkey, June 1-3, 2000. C.C. Chang and J.C. Chuang, “An image intellectual property protection scheme for gray-level images using visual secret sharing strategy,” Pattern Recognition Letters, vol. 23, pp. 931-941, June 2002. Chin-Chen Chang, Ju-Yuan Hsiao and Chi-Lung Chiang, “An Image Copyright Protection Scheme Based on Torus Automorphism,” First International Symposium on Cyber Worlds (CW'02) November 06 08, 2002. Johnson, NF, Duric, Z., and Jajodia, S, “On Fingerprinting Images for Recognition,” Submitted to Fifth International Workshop on Multimedia Information Systems (MIS'99), Palm Springs, CA, USA, 21-23 October 1999. Said, A. and Pearlman, WA, “A new fast and efficient image codec based on set partitioning in hierarchical trees,” IEEE Trans on Circuits and Systems for Video Technology, 6, pp.243-250, 1996..
(7)
數據



相關文件
Lin Xueling, A Study on the Literary Images and Narrative Persuasion in Dunhuang Telling and Singing Literature "Qiu Yin Yi Ben". Hung Ifang, The Content and
The Hilbert space of an orbifold field theory [6] is decomposed into twisted sectors H g , that are labelled by the conjugacy classes [g] of the orbifold group, in our case
Lin, A smoothing Newton method based on the generalized Fischer-Burmeister function for MCPs, Nonlinear Analysis: Theory, Methods and Applications, 72(2010), 3739-3758..
• It is a plus if you have background knowledge on computer vision, image processing and computer graphics.. • It is a plus if you have access to digital cameras
A Very good. You are able to apply your understanding of how endogenetic processes leading to the formation of major landform features along plate boundaries to explain the
However, the SRAS curve is upward sloping, which indicates that an increase in the overall price level tends to raise the quantity of goods and services supplied and a decrease in
• It is a plus if you have background knowledge on computer vision, image processing and computer graphics.. • It is a plus if you have access to digital cameras
• It is a plus if you have background knowledge on computer vision, image processing and computer graphics.. • It is a plus if you have access to digital cameras